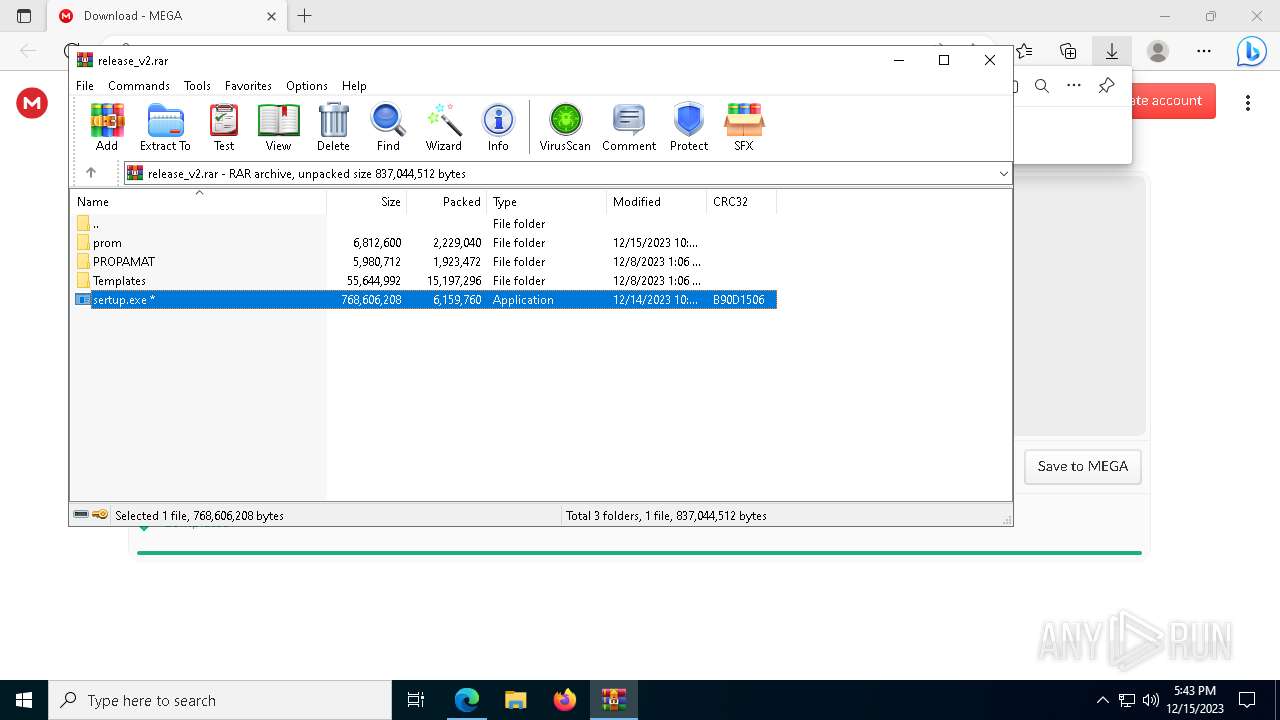
| URL: | https://mega.nz/file/qeJigYgS#nAbNnRdchIIQWsoMmyU1g7xPq27WKr9tRaTl45r2bQ0 |
| Full analysis: | https://app.any.run/tasks/10a8a883-0a6a-4c0e-baf7-11d4088d7a9a |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | December 15, 2023, 17:43:09 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | EA695B7B41BF6FEC0BB672859B44C012 |
| SHA1: | 14B192B8965832F0D8CA3D11D41E965BE6C69AC2 |
| SHA256: | B75B1CBD117078143E01D95A2034724E09B789F5D81DEF58FB71228E943D8917 |
| SSDEEP: | 3:N8X/iqUCT2GABnVyNVi71OKRCcn:2atjnPBRB |
MALICIOUS
Connects to the CnC server
- sertup.exe (PID: 8188)
- uLCMASuMhGcuMhXEKkvX7yWV.exe (PID: 2280)
- dPptxYjvjE1mY9Vpid_m1HEK.exe (PID: 4052)
- gJISphbSzATOOH2QAdr2T6sv.exe (PID: 7344)
- svchost.exe (PID: 5220)
- explorer.exe (PID: 4428)
- 9E48.exe (PID: 7604)
- explorer.exe (PID: 7160)
- 戶扄䕣瘷㘶㘷䘷 (PID: 7964)
- explorer.exe (PID: 7720)
- Jz_6zt7_xunltvjRlbslBSjv.exe (PID: 1460)
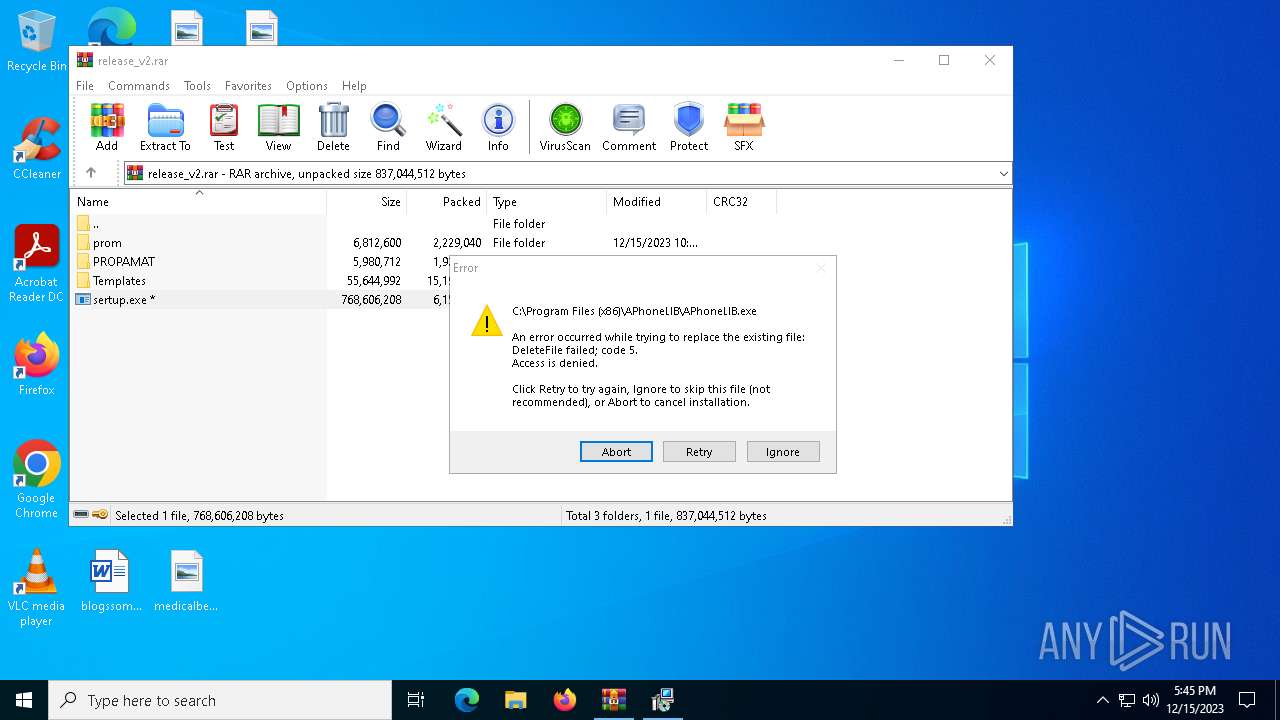
- APhoneLIB.exe (PID: 8096)
- AppLaunch.exe (PID: 4108)
- AppLaunch.exe (PID: 7040)
Actions looks like stealing of personal data
- sertup.exe (PID: 8188)
- dPptxYjvjE1mY9Vpid_m1HEK.exe (PID: 4052)
- gJISphbSzATOOH2QAdr2T6sv.exe (PID: 7344)
- 9E48.exe (PID: 7604)
- explorer.exe (PID: 7720)
- 戶扄䕣瘷㘶㘷䘷 (PID: 7964)
- AppLaunch.exe (PID: 7040)
- AppLaunch.exe (PID: 4108)
- Jz_6zt7_xunltvjRlbslBSjv.exe (PID: 1460)
PRIVATELOADER has been detected (SURICATA)
- sertup.exe (PID: 8188)
- dPptxYjvjE1mY9Vpid_m1HEK.exe (PID: 4052)
Drops the executable file immediately after the start
- sertup.exe (PID: 8188)
- _FG1Ws5eSolmsQKf_unB3Z1m.exe (PID: 6344)
- 7sUNl21hNDURJUs7KNZ0DZ3W.exe (PID: 832)
- APhoneLIB.exe (PID: 428)
- cmd.exe (PID: 7640)
- _FG1Ws5eSolmsQKf_unB3Z1m.tmp (PID: 5372)
- Jz_6zt7_xunltvjRlbslBSjv.exe (PID: 1460)
- dPptxYjvjE1mY9Vpid_m1HEK.exe (PID: 4052)
- d2a5TYKsBWxt3QBj0gdajIKB.exe (PID: 6268)
- AFFC.exe (PID: 5080)
- AFFC.exe (PID: 4632)
- B230.exe (PID: 5692)
- AFFC.tmp (PID: 6600)
- B790.exe (PID: 7708)
- updater.exe (PID: 6016)
LUMMA has been detected (SURICATA)
- gJISphbSzATOOH2QAdr2T6sv.exe (PID: 7344)
- 戶扄䕣瘷㘶㘷䘷 (PID: 7964)
STEALC has been detected (SURICATA)
- uLCMASuMhGcuMhXEKkvX7yWV.exe (PID: 2280)
Create files in the Startup directory
- Jz_6zt7_xunltvjRlbslBSjv.exe (PID: 1460)
Uses Task Scheduler to run other applications
- Jz_6zt7_xunltvjRlbslBSjv.exe (PID: 1460)
- tJ05KXjm8vYA45jrFU7DoxTI.exe (PID: 3572)
- explorer.exe (PID: 4428)
Uses Task Scheduler to autorun other applications
- Jz_6zt7_xunltvjRlbslBSjv.exe (PID: 1460)
RISEPRO has been detected (SURICATA)
- Jz_6zt7_xunltvjRlbslBSjv.exe (PID: 1460)
Runs injected code in another process
- Uyal5Nnv9ND6NmWtJqSL9CPH.exe (PID: 2984)
Creates a writable file in the system directory
- svchost.exe (PID: 5448)
- powershell.exe (PID: 6880)
TOFSEE has been detected (SURICATA)
- svchost.exe (PID: 5448)
Application was injected by another process
- explorer.exe (PID: 4428)
Changes the autorun value in the registry
- tJ05KXjm8vYA45jrFU7DoxTI.exe (PID: 3572)
SMOKE has been detected (SURICATA)
- explorer.exe (PID: 4428)
- explorer.exe (PID: 7720)
- explorer.exe (PID: 7160)
AMADEY has been detected (SURICATA)
- tJ05KXjm8vYA45jrFU7DoxTI.exe (PID: 3572)
MINER has been detected (SURICATA)
- svchost.exe (PID: 5220)
Adds path to the Windows Defender exclusion list
- explorer.exe (PID: 4428)
REDLINE has been detected (SURICATA)
- 9E48.exe (PID: 7604)
- AppLaunch.exe (PID: 4108)
- AppLaunch.exe (PID: 7040)
Steals credentials from Web Browsers
- explorer.exe (PID: 7720)
- 9E48.exe (PID: 7604)
- Jz_6zt7_xunltvjRlbslBSjv.exe (PID: 1460)
- AppLaunch.exe (PID: 4108)
- AppLaunch.exe (PID: 7040)
Unusual connection from system programs
- explorer.exe (PID: 7720)
RISEPRO has been detected (YARA)
- Jz_6zt7_xunltvjRlbslBSjv.exe (PID: 1460)
TOFSEE has been detected (YARA)
- svchost.exe (PID: 5448)
SOCKS5SYSTEMZ has been detected (SURICATA)
- APhoneLIB.exe (PID: 8096)
REDLINE has been detected (YARA)
- AppLaunch.exe (PID: 7040)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 7904)
- _FG1Ws5eSolmsQKf_unB3Z1m.tmp (PID: 5372)
- AFFC.tmp (PID: 6600)
- B790.exe (PID: 7708)
Reads the BIOS version
- sertup.exe (PID: 8188)
- Jz_6zt7_xunltvjRlbslBSjv.exe (PID: 1460)
- 9E48.exe (PID: 7604)
Checks for external IP
- sertup.exe (PID: 8188)
- dPptxYjvjE1mY9Vpid_m1HEK.exe (PID: 4052)
- Jz_6zt7_xunltvjRlbslBSjv.exe (PID: 1460)
Connects to the server without a host name
- sertup.exe (PID: 8188)
- uLCMASuMhGcuMhXEKkvX7yWV.exe (PID: 2280)
- dPptxYjvjE1mY9Vpid_m1HEK.exe (PID: 4052)
- tJ05KXjm8vYA45jrFU7DoxTI.exe (PID: 3572)
- B230.exe (PID: 5692)
- svchost.exe (PID: 5448)
Reads security settings of Internet Explorer
- sertup.exe (PID: 8188)
- dPptxYjvjE1mY9Vpid_m1HEK.exe (PID: 4052)
Checks Windows Trust Settings
- sertup.exe (PID: 8188)
- dPptxYjvjE1mY9Vpid_m1HEK.exe (PID: 4052)
Process requests binary or script from the Internet
- sertup.exe (PID: 8188)
- dPptxYjvjE1mY9Vpid_m1HEK.exe (PID: 4052)
- explorer.exe (PID: 4428)
- B230.exe (PID: 5692)
Reads the Windows owner or organization settings
- _FG1Ws5eSolmsQKf_unB3Z1m.tmp (PID: 5372)
- AFFC.tmp (PID: 6600)
Reads the date of Windows installation
- 7sUNl21hNDURJUs7KNZ0DZ3W.exe (PID: 832)
- tJ05KXjm8vYA45jrFU7DoxTI.exe (PID: 3572)
- AFFC.tmp (PID: 6416)
Starts CMD.EXE for commands execution
- 7sUNl21hNDURJUs7KNZ0DZ3W.exe (PID: 832)
- explorer.exe (PID: 4428)
Executes application which crashes
- uLCMASuMhGcuMhXEKkvX7yWV.exe (PID: 2280)
- qtqjacwm.exe (PID: 3892)
- 7sUNl21hNDURJUs7KNZ0DZ3W.exe (PID: 832)
- Jz_6zt7_xunltvjRlbslBSjv.exe (PID: 1460)
Process drops SQLite DLL files
- _FG1Ws5eSolmsQKf_unB3Z1m.tmp (PID: 5372)
- AFFC.tmp (PID: 6600)
Drops 7-zip archiver for unpacking
- _FG1Ws5eSolmsQKf_unB3Z1m.tmp (PID: 5372)
- AFFC.tmp (PID: 6600)
Executes as Windows Service
- qtqjacwm.exe (PID: 3892)
Uses NETSH.EXE to add a firewall rule or allowed programs
- 7sUNl21hNDURJUs7KNZ0DZ3W.exe (PID: 832)
Detected use of alternative data streams (AltDS)
- svchost.exe (PID: 5448)
Connects to unusual port
- Jz_6zt7_xunltvjRlbslBSjv.exe (PID: 1460)
- svchost.exe (PID: 5220)
- svchost.exe (PID: 5448)
- 9E48.exe (PID: 7604)
- explorer.exe (PID: 6216)
- APhoneLIB.exe (PID: 8096)
- AppLaunch.exe (PID: 4108)
- AppLaunch.exe (PID: 7040)
Creates or modifies Windows services
- svchost.exe (PID: 5448)
Connects to SMTP port
- svchost.exe (PID: 5448)
Searches for installed software
- gJISphbSzATOOH2QAdr2T6sv.exe (PID: 7344)
- AFFC.tmp (PID: 6600)
- 9E48.exe (PID: 7604)
- 戶扄䕣瘷㘶㘷䘷 (PID: 7964)
- Jz_6zt7_xunltvjRlbslBSjv.exe (PID: 1460)
- AppLaunch.exe (PID: 4108)
- AppLaunch.exe (PID: 7040)
Application launched itself
- svchost.exe (PID: 5448)
- explorer.exe (PID: 4428)
Starts POWERSHELL.EXE for commands execution
- explorer.exe (PID: 4428)
- updater.exe (PID: 6016)
Script adds exclusion path to Windows Defender
- explorer.exe (PID: 4428)
Starts SC.EXE for service management
- cmd.exe (PID: 2380)
- cmd.exe (PID: 7764)
Uses powercfg.exe to modify the power settings
- cmd.exe (PID: 7040)
- cmd.exe (PID: 8120)
The process executes via Task Scheduler
- updater.exe (PID: 6016)
- tJ05KXjm8vYA45jrFU7DoxTI.exe (PID: 1540)
- tJ05KXjm8vYA45jrFU7DoxTI.exe (PID: 5956)
- dbcgshj (PID: 7284)
- tJ05KXjm8vYA45jrFU7DoxTI.exe (PID: 804)
- tJ05KXjm8vYA45jrFU7DoxTI.exe (PID: 6616)
- tJ05KXjm8vYA45jrFU7DoxTI.exe (PID: 1500)
- tJ05KXjm8vYA45jrFU7DoxTI.exe (PID: 7064)
- tJ05KXjm8vYA45jrFU7DoxTI.exe (PID: 7392)
- tJ05KXjm8vYA45jrFU7DoxTI.exe (PID: 7800)
Loads DLL from Mozilla Firefox
- explorer.exe (PID: 7160)
Starts application with an unusual extension
- B790.exe (PID: 7708)
Drops a system driver (possible attempt to evade defenses)
- updater.exe (PID: 6016)
The process creates files with name similar to system file names
- powershell.exe (PID: 6880)
INFO
Application launched itself
- msedge.exe (PID: 4956)
Reads the computer name
- identity_helper.exe (PID: 6328)
- sertup.exe (PID: 8188)
- OyPPF7mZkufMFu84JB0990bX.exe (PID: 3672)
- _FG1Ws5eSolmsQKf_unB3Z1m.tmp (PID: 5372)
- uLCMASuMhGcuMhXEKkvX7yWV.exe (PID: 2280)
- gJISphbSzATOOH2QAdr2T6sv.exe (PID: 7344)
- 7sUNl21hNDURJUs7KNZ0DZ3W.exe (PID: 832)
- dPptxYjvjE1mY9Vpid_m1HEK.exe (PID: 4052)
- APhoneLIB.exe (PID: 8096)
- APhoneLIB.exe (PID: 428)
- Jz_6zt7_xunltvjRlbslBSjv.exe (PID: 1460)
- qtqjacwm.exe (PID: 3892)
- tJ05KXjm8vYA45jrFU7DoxTI.exe (PID: 3572)
- 9E48.exe (PID: 7604)
- AFFC.tmp (PID: 6416)
- AFFC.tmp (PID: 6600)
- B230.exe (PID: 5692)
- B790.exe (PID: 7708)
- 戶扄䕣瘷㘶㘷䘷 (PID: 7964)
- AppLaunch.exe (PID: 4108)
- AppLaunch.exe (PID: 7040)
Checks supported languages
- identity_helper.exe (PID: 6328)
- sertup.exe (PID: 8188)
- uLCMASuMhGcuMhXEKkvX7yWV.exe (PID: 2280)
- _FG1Ws5eSolmsQKf_unB3Z1m.exe (PID: 6344)
- _FG1Ws5eSolmsQKf_unB3Z1m.tmp (PID: 5372)
- 7sUNl21hNDURJUs7KNZ0DZ3W.exe (PID: 832)
- Uyal5Nnv9ND6NmWtJqSL9CPH.exe (PID: 2984)
- YEctALZbSKxWAvIJXZoUuOmp.exe (PID: 5320)
- OyPPF7mZkufMFu84JB0990bX.exe (PID: 3672)
- Jz_6zt7_xunltvjRlbslBSjv.exe (PID: 1460)
- dPptxYjvjE1mY9Vpid_m1HEK.exe (PID: 4052)
- n31xAIW0YAdwWWojVVP0vUfD.exe (PID: 7200)
- gJISphbSzATOOH2QAdr2T6sv.exe (PID: 7344)
- APhoneLIB.exe (PID: 428)
- APhoneLIB.exe (PID: 8096)
- qtqjacwm.exe (PID: 3892)
- tJ05KXjm8vYA45jrFU7DoxTI.exe (PID: 3572)
- d2a5TYKsBWxt3QBj0gdajIKB.exe (PID: 6268)
- 9E48.exe (PID: 7604)
- updater.exe (PID: 6016)
- AFFC.exe (PID: 5080)
- AFFC.tmp (PID: 6416)
- AFFC.exe (PID: 4632)
- AFFC.tmp (PID: 6600)
- B230.exe (PID: 5692)
- B790.exe (PID: 7708)
- 戶扄䕣瘷㘶㘷䘷 (PID: 7964)
- tJ05KXjm8vYA45jrFU7DoxTI.exe (PID: 1540)
- AppLaunch.exe (PID: 4108)
- tJ05KXjm8vYA45jrFU7DoxTI.exe (PID: 5956)
- AppLaunch.exe (PID: 7040)
- tJ05KXjm8vYA45jrFU7DoxTI.exe (PID: 1500)
- tJ05KXjm8vYA45jrFU7DoxTI.exe (PID: 6616)
- tJ05KXjm8vYA45jrFU7DoxTI.exe (PID: 804)
- dbcgshj (PID: 7284)
- tJ05KXjm8vYA45jrFU7DoxTI.exe (PID: 7064)
- tJ05KXjm8vYA45jrFU7DoxTI.exe (PID: 7392)
- tJ05KXjm8vYA45jrFU7DoxTI.exe (PID: 7800)
The process uses the downloaded file
- msedge.exe (PID: 7604)
- msedge.exe (PID: 4956)
- WinRAR.exe (PID: 7904)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 7904)
- explorer.exe (PID: 4428)
Process checks are UAC notifies on
- sertup.exe (PID: 8188)
- Jz_6zt7_xunltvjRlbslBSjv.exe (PID: 1460)
Reads the software policy settings
- sertup.exe (PID: 8188)
- dPptxYjvjE1mY9Vpid_m1HEK.exe (PID: 4052)
- WerFault.exe (PID: 7608)
- Jz_6zt7_xunltvjRlbslBSjv.exe (PID: 1460)
- WerFault.exe (PID: 6252)
Reads the machine GUID from the registry
- sertup.exe (PID: 8188)
- OyPPF7mZkufMFu84JB0990bX.exe (PID: 3672)
- Jz_6zt7_xunltvjRlbslBSjv.exe (PID: 1460)
- dPptxYjvjE1mY9Vpid_m1HEK.exe (PID: 4052)
- 9E48.exe (PID: 7604)
- B230.exe (PID: 5692)
- AppLaunch.exe (PID: 4108)
- AppLaunch.exe (PID: 7040)
Process checks computer location settings
- sertup.exe (PID: 8188)
- 7sUNl21hNDURJUs7KNZ0DZ3W.exe (PID: 832)
- dPptxYjvjE1mY9Vpid_m1HEK.exe (PID: 4052)
- tJ05KXjm8vYA45jrFU7DoxTI.exe (PID: 3572)
- AFFC.tmp (PID: 6416)
Creates files or folders in the user directory
- sertup.exe (PID: 8188)
- Jz_6zt7_xunltvjRlbslBSjv.exe (PID: 1460)
- WerFault.exe (PID: 7608)
- explorer.exe (PID: 4428)
- dPptxYjvjE1mY9Vpid_m1HEK.exe (PID: 4052)
- OyPPF7mZkufMFu84JB0990bX.exe (PID: 3672)
- B230.exe (PID: 5692)
- 9E48.exe (PID: 7604)
- WerFault.exe (PID: 6252)
- AppLaunch.exe (PID: 4108)
Create files in a temporary directory
- _FG1Ws5eSolmsQKf_unB3Z1m.exe (PID: 6344)
- _FG1Ws5eSolmsQKf_unB3Z1m.tmp (PID: 5372)
- 7sUNl21hNDURJUs7KNZ0DZ3W.exe (PID: 832)
- Jz_6zt7_xunltvjRlbslBSjv.exe (PID: 1460)
- explorer.exe (PID: 4428)
- AFFC.exe (PID: 5080)
- AFFC.exe (PID: 4632)
- AFFC.tmp (PID: 6600)
- explorer.exe (PID: 7720)
- B790.exe (PID: 7708)
Checks proxy server information
- sertup.exe (PID: 8188)
- uLCMASuMhGcuMhXEKkvX7yWV.exe (PID: 2280)
- WerFault.exe (PID: 7608)
- OyPPF7mZkufMFu84JB0990bX.exe (PID: 3672)
- dPptxYjvjE1mY9Vpid_m1HEK.exe (PID: 4052)
- explorer.exe (PID: 4428)
- tJ05KXjm8vYA45jrFU7DoxTI.exe (PID: 3572)
- B230.exe (PID: 5692)
- explorer.exe (PID: 7720)
- explorer.exe (PID: 7160)
- WerFault.exe (PID: 6252)
- APhoneLIB.exe (PID: 8096)
Creates files in the program directory
- _FG1Ws5eSolmsQKf_unB3Z1m.tmp (PID: 5372)
- APhoneLIB.exe (PID: 428)
- Jz_6zt7_xunltvjRlbslBSjv.exe (PID: 1460)
- d2a5TYKsBWxt3QBj0gdajIKB.exe (PID: 6268)
- AFFC.tmp (PID: 6600)
- updater.exe (PID: 6016)
- APhoneLIB.exe (PID: 8096)
Reads Environment values
- OyPPF7mZkufMFu84JB0990bX.exe (PID: 3672)
- tJ05KXjm8vYA45jrFU7DoxTI.exe (PID: 3572)
- B230.exe (PID: 5692)
- 9E48.exe (PID: 7604)
- Jz_6zt7_xunltvjRlbslBSjv.exe (PID: 1460)
- AppLaunch.exe (PID: 7040)
- AppLaunch.exe (PID: 4108)
Reads CPU info
- Jz_6zt7_xunltvjRlbslBSjv.exe (PID: 1460)
Reads product name
- Jz_6zt7_xunltvjRlbslBSjv.exe (PID: 1460)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
RisePro
(PID) Process(1460) Jz_6zt7_xunltvjRlbslBSjv.exe
C2193.42.33.14
Tofsee
(PID) Process(5448) svchost.exe
C2 (2)vanaheim.cn
jotunheim.name
Encrypted Strings (59)c:\Windows
\system32\
ImagePath
.exe
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
MSConfig
/r
.exe
cmd /C move /Y "%s" %s
sc config %s binPath= "%s%s /d\"%s\""
sc start %s
svchost.exe
SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System
ConsentPromptBehaviorAdmin
PromptOnSecureDesktop
MSConfig
:.repos
USERPROFILE
\Local Settings:.repos
USERPROFILE
\Local Settings\Application Data\Microsoft\Windows\UsrClass.dat.repos
USERPROFILE
\wincookie.repos
TMP
Config
Control Panel\Buses
Config
SOFTWARE\Microsoft\Buses
Config
Control Panel\Buses
Config
SOFTWARE\Microsoft\Buses
SYSTEM\CurrentControlSet\services
ImagePath
SYSTEM\CurrentControlSet\services
SYSTEM\CurrentControlSet\services
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
SOFTWARE\Microsoft\Windows Defender\Exclusions\Paths
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
.exe
qazwsxed
%s%i%i%i%i.bat
@echo off
:next_try
del "%s">nul
if exist "%s" (
ping 127.0.0.1 >nul
goto next_try
)
del %%0
svchost.exe
.exe
/u
USERPROFILE
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
/d
/e
/d
/e
.exe
"%s" /u"%s"
USERPROFILE
.exe
USERPROFILE
USERPROFILE
ver=%d lid=%d
win=%X/%d sid=%s
rep=%s
RedLine
(PID) Process(7040) AppLaunch.exe
C2 (1)45.15.156.187:23929
BotnetLogsDiller Cloud (Telegram: @logsdillabot)
Options
ErrorMessage
Keys
XorScuffs
Total processes
290
Monitored processes
142
Malicious processes
33
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 364 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=5520 --field-trial-handle=2108,i,474765032815162970,10990450434591992098,131072 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 111.0.1661.62 Modules
| |||||||||||||||
| 428 | "C:\Program Files (x86)\APhoneLIB\APhoneLIB.exe" -i | C:\Program Files (x86)\APhoneLIB\APhoneLIB.exe | — | _FG1Ws5eSolmsQKf_unB3Z1m.tmp | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 0.8.2.402 Modules
| |||||||||||||||
| 528 | powercfg /x -standby-timeout-dc 0 | C:\Windows\System32\powercfg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Power Settings Command-Line Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 708 | schtasks /create /f /RU "admin" /tr "C:\ProgramData\OfficeTrackerNMP1\OfficeTrackerNMP1.exe" /tn "OfficeTrackerNMP1 LG" /sc ONLOGON /rl HIGHEST | C:\Windows\SysWOW64\schtasks.exe | — | Jz_6zt7_xunltvjRlbslBSjv.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 804 | "C:\Users\admin\Pictures\Minor Policy\tJ05KXjm8vYA45jrFU7DoxTI.exe" | C:\Users\admin\Pictures\Minor Policy\tJ05KXjm8vYA45jrFU7DoxTI.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 832 | "C:\Users\admin\Pictures\Minor Policy\7sUNl21hNDURJUs7KNZ0DZ3W.exe" | C:\Users\admin\Pictures\Minor Policy\7sUNl21hNDURJUs7KNZ0DZ3W.exe | sertup.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225477 Modules
| |||||||||||||||
| 952 | powercfg /x -standby-timeout-ac 0 | C:\Windows\System32\powercfg.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Power Settings Command-Line Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 956 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --first-renderer-process --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=3416 --field-trial-handle=2108,i,474765032815162970,10990450434591992098,131072 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 111.0.1661.62 Modules
| |||||||||||||||
| 1164 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | — | B230.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Exit code: 4294967295 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 1188 | sc stop UsoSvc | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
60 731
Read events
60 380
Write events
250
Delete events
101
Modification events
| (PID) Process: | (4956) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (4956) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (4956) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (4956) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (4956) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate\ClientState\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (4956) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (4956) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge |
| Operation: | write | Name: | UsageStatsInSample |
Value: 1 | |||
| (PID) Process: | (4956) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (4956) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | urlstats |
Value: 0 | |||
| (PID) Process: | (4956) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: BC8CC635B5602F00 | |||
Executable files
263
Suspicious files
217
Text files
127
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4956 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF14d02f.TMP | — | |
MD5:— | SHA256:— | |||
| 4956 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4956 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF14d05e.TMP | — | |
MD5:— | SHA256:— | |||
| 4956 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4956 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF14d05e.TMP | — | |
MD5:— | SHA256:— | |||
| 4956 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4956 | msedge.exe | C:\USERS\ADMIN\APPDATA\LOCAL\MICROSOFT\EDGE\USER DATA\VARIATIONS | binary | |
MD5:CDDDC745A8C954DC438C931889999BDB | SHA256:3DC9043838386F5363AC96A01477CF3163B5118B80191576A11B32CE9894314C | |||
| 4956 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Local State | binary | |
MD5:2C03702042B7978489B141D5B435FF78 | SHA256:1D4C24A76B5A44D1209BBBA5F207A4D671676E16C7BB1C8FA5790252E0F58EA9 | |||
| 4956 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Site Characteristics Database\LOG.old~RF14d02f.TMP | text | |
MD5:D480C74EE54A756F9A0AE4C42DC88EE1 | SHA256:61F10687C404E33B9D61AB49E0B9FCD809F3DA06E7471164BF8DA209A05DFF78 | |||
| 4956 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgeCoupons\coupons_data.db\LOG.old~RF14d03f.TMP | text | |
MD5:808538C5690E3D0F21CE81C36A71A5EA | SHA256:8FB89B3277E41E7BA44CF553EB7987C19804DD7162293BF68292699E690BA6AD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
188
TCP/UDP connections
482
DNS requests
133
Threats
274
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3908 | svchost.exe | GET | 206 | 23.32.238.99:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/4643befd-79b8-4e0c-a2fb-c0e3ee78dcd5?P1=1703220168&P2=404&P3=2&P4=ZD7nFhPZSU3C965TUBLMl7lPedEexASqlHDzyuSCvQvOCz0BzsumBwPI39wX5VkcWSwGML%2fOTqcYBAQurxPjZw%3d%3d | unknown | binary | 1.09 Kb | unknown |
3848 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
7036 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | unknown | binary | 471 b | unknown |
7776 | SIHClient.exe | GET | 200 | 104.119.109.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | binary | 418 b | unknown |
7776 | SIHClient.exe | GET | 200 | 104.119.109.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | binary | 409 b | unknown |
8188 | sertup.exe | GET | 200 | 195.20.16.45:80 | http://195.20.16.45/api/tracemap.php | unknown | text | 15 b | unknown |
8188 | sertup.exe | POST | 200 | 195.20.16.45:80 | http://195.20.16.45/api/firegate.php | unknown | text | 108 b | unknown |
2344 | svchost.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | binary | 1.11 Kb | unknown |
2344 | svchost.exe | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Time-Stamp%20PCA%202010(1).crl | unknown | binary | 814 b | unknown |
8188 | sertup.exe | HEAD | 200 | 188.114.97.3:80 | http://zen.topteamlife.com/order/adobe.exe | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3764 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6512 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4956 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3772 | msedge.exe | 31.216.145.5:443 | mega.nz | Datacenter Luxembourg S.A. | LU | unknown |
3772 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3772 | msedge.exe | 51.104.176.40:443 | nav-edge.smartscreen.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3772 | msedge.exe | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
3772 | msedge.exe | 89.44.169.134:443 | eu.static.mega.co.nz | Datacenter Luxembourg S.A. | LU | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
mega.nz |
| whitelisted |
config.edge.skype.com |
| whitelisted |
nav-edge.smartscreen.microsoft.com |
| whitelisted |
data-edge.smartscreen.microsoft.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
eu.static.mega.co.nz |
| shared |
www.bing.com |
| whitelisted |
g.api.mega.co.nz |
| shared |
edgeassetservice.azureedge.net |
| whitelisted |
postnav-edge.smartscreen.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3772 | msedge.exe | Misc activity | ET INFO File Sharing Related Domain in DNS Lookup (mega .nz) |
3772 | msedge.exe | Misc activity | ET INFO File Sharing Related Domain in DNS Lookup (mega .nz) |
3772 | msedge.exe | Misc activity | ET INFO File Sharing Domain Observed in TLS SNI (mega .nz) |
3772 | msedge.exe | Misc activity | ET INFO Observed DNS Query to Filesharing Service (mega .co .nz) |
3772 | msedge.exe | Misc activity | ET INFO Observed DNS Query to Filesharing Service (mega .co .nz) |
3772 | msedge.exe | Misc activity | ET INFO File Sharing Domain Observed in TLS SNI (mega .nz) |
3772 | msedge.exe | Misc activity | ET INFO Observed DNS Query to Filesharing Service (mega .co .nz) |
3772 | msedge.exe | Misc activity | ET INFO Observed DNS Query to Filesharing Service (mega .co .nz) |
3772 | msedge.exe | Misc activity | ET INFO Observed DNS Query to Filesharing Service (mega .co .nz) |
3772 | msedge.exe | Misc activity | ET INFO Observed DNS Query to Filesharing Service (mega .co .nz) |
32 ETPRO signatures available at the full report
Process | Message |
|---|---|
Jz_6zt7_xunltvjRlbslBSjv.exe | 5445dfg |
Jz_6zt7_xunltvjRlbslBSjv.exe | 5yh45 |
Jz_6zt7_xunltvjRlbslBSjv.exe | th1y5atj8 |