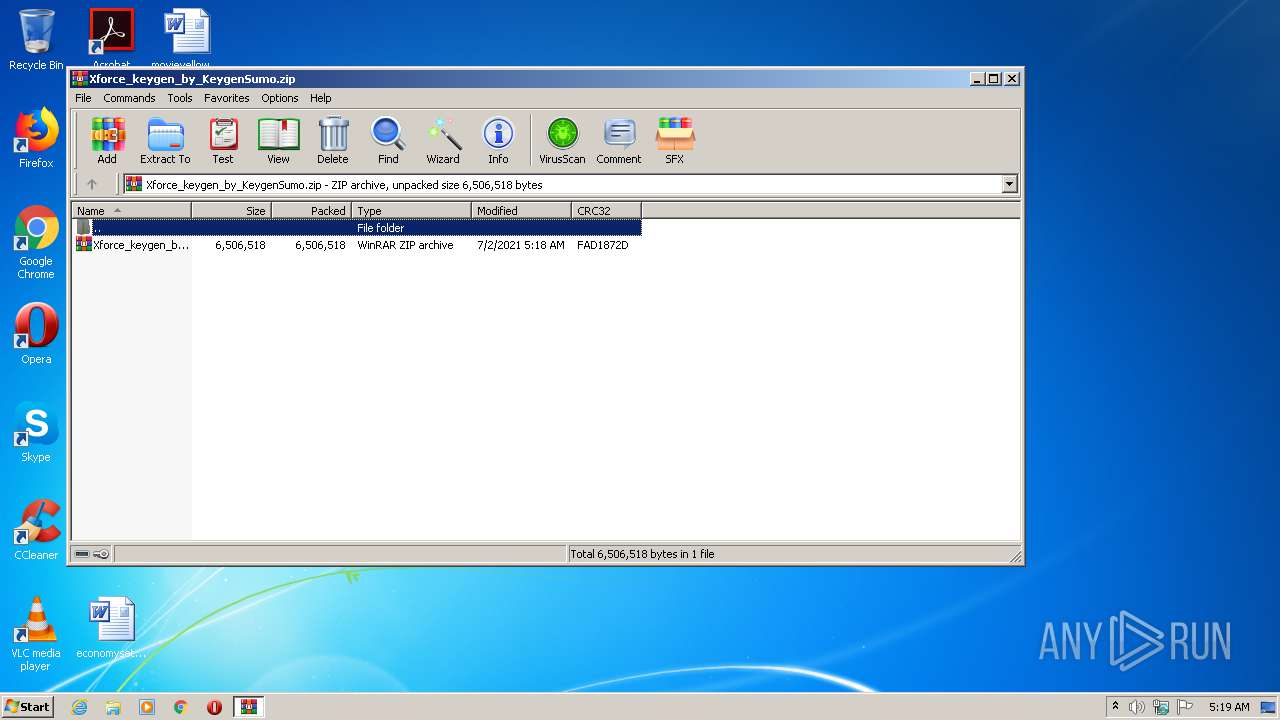
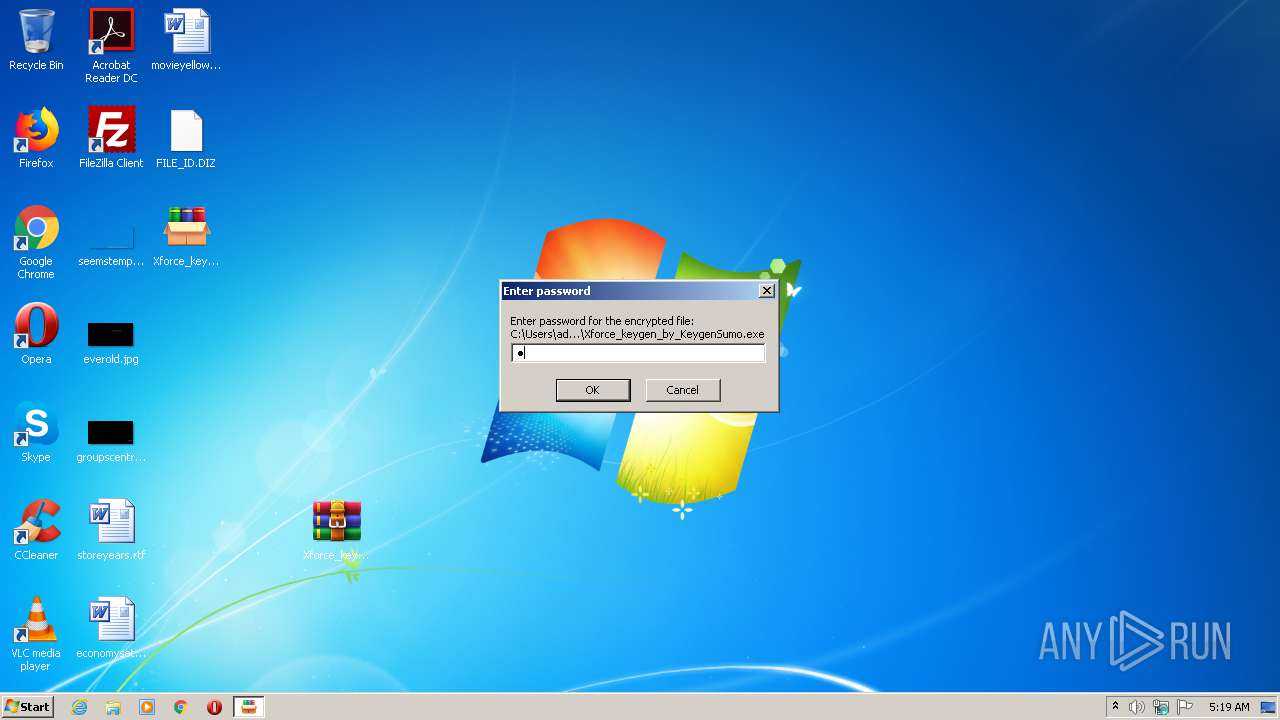
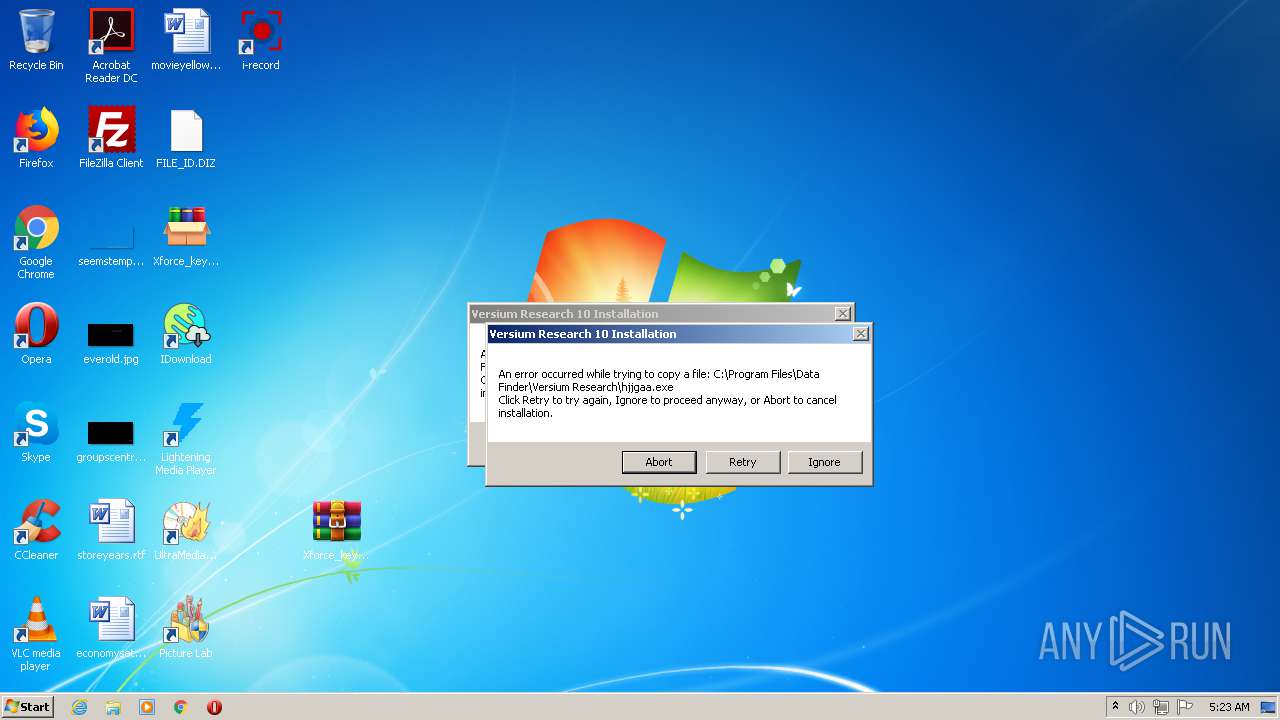
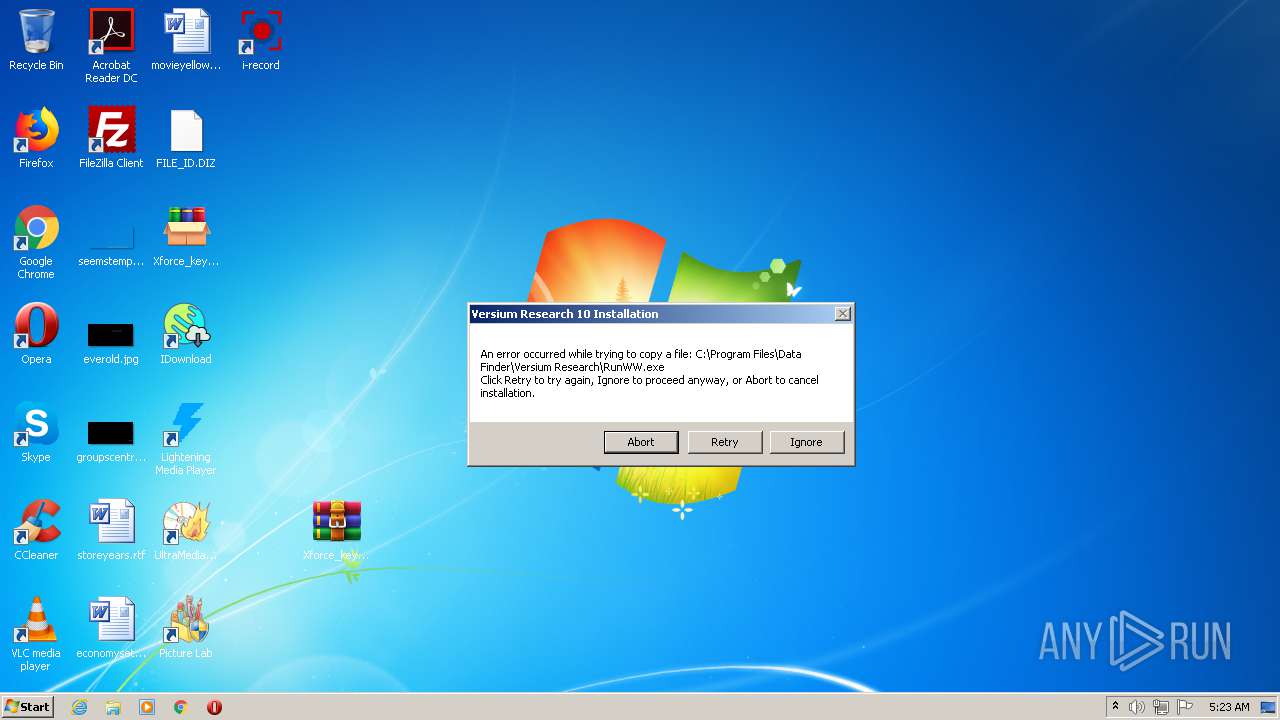
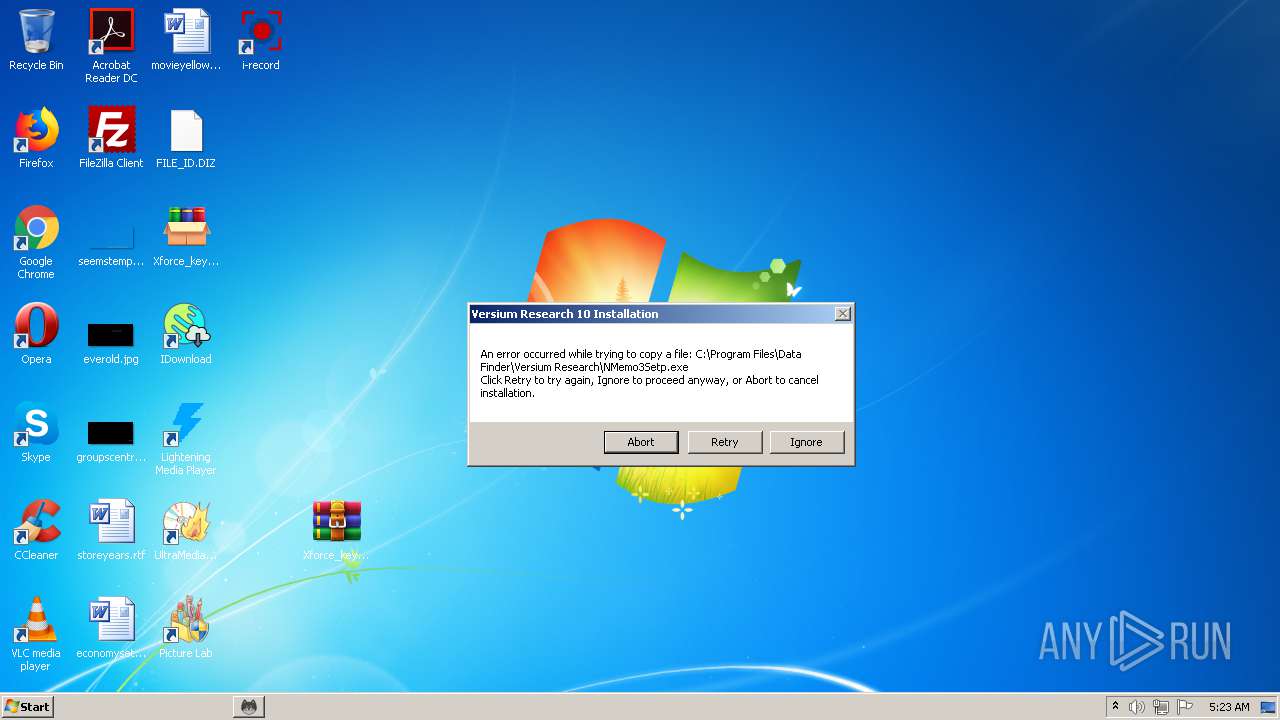
| File name: | Xforce_keygen_by_KeygenSumo.zip |
| Full analysis: | https://app.any.run/tasks/a662becf-b2c2-4b7b-aa68-48996347d4ed |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | July 02, 2021, 04:18:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | 12E971A3C2BA08EECF2554A7982BE128 |
| SHA1: | C32E1953EFBE09626B181C88CC76D34733E7291C |
| SHA256: | B6C5CEE94F3DCBA4570377CC032776DD5453291F7D36932AA50557C93E16C592 |
| SSDEEP: | 98304:W3Gj/vDBcShZQqeBI34nepmigVo5zpATCg/IOk3xqvRcdDgXQDrFrJMxSZn:WM/rOSiBI1nRpqCBsv2p0yJF |
MALICIOUS
Application was dropped or rewritten from another process
- Xforce_keygen_by_KeygenSumo.exe (PID: 2928)
- keygen-step-1.exe (PID: 2416)
- keygen-pr.exe (PID: 3996)
- keygen-step-6.exe (PID: 2152)
- JNCo2Vf2MC.EXE (PID: 2724)
- key.exe (PID: 4056)
- Crack.exe (PID: 2688)
- keygen-step-4.exe (PID: 3580)
- keygen-step-3.exe (PID: 2756)
- keygen-step-5.exe (PID: 1940)
- key.exe (PID: 2808)
- 43A1.tmp.exe (PID: 2172)
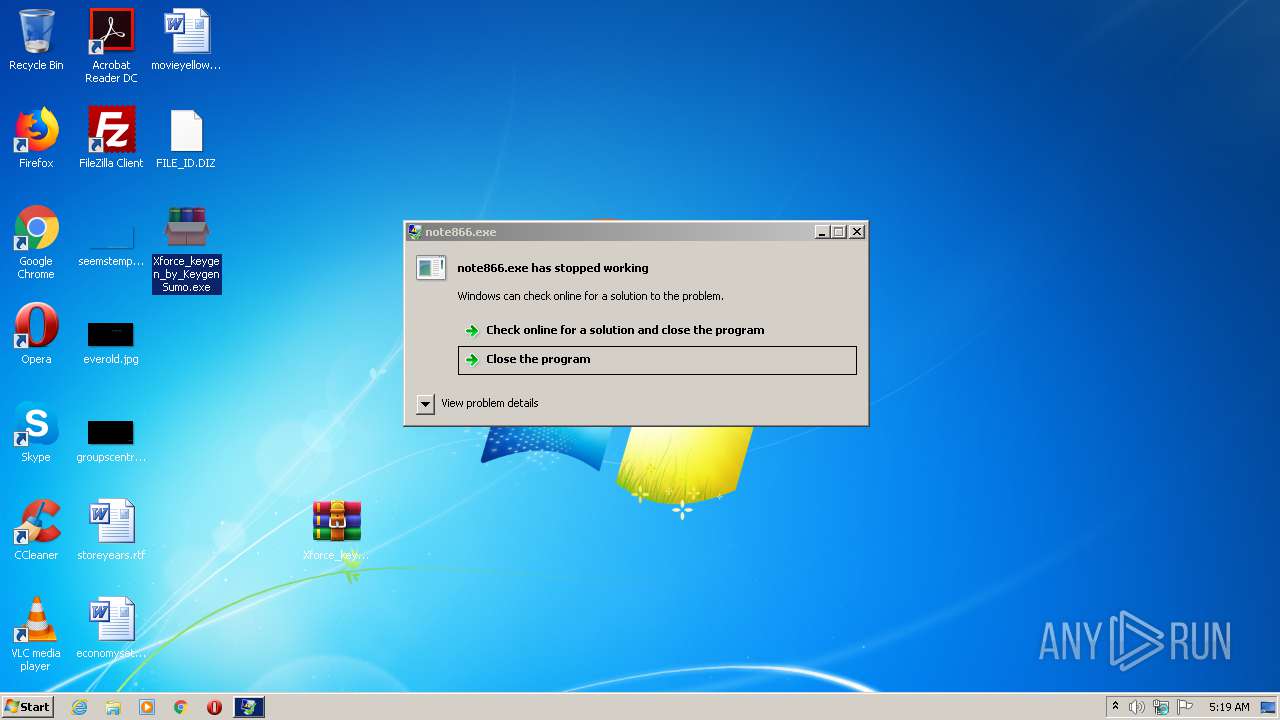
- note866.exe (PID: 4032)
- 5C0D.tmp.exe (PID: 4088)
- GloryWSetp.exe (PID: 3552)
- 1710767.exe (PID: 3404)
- 8602741.exe (PID: 2468)
- 6937479.exe (PID: 3548)
- IDWCH1.exe (PID: 2040)
- WinHoster.exe (PID: 1320)
- IDWCH1.exe (PID: 4072)
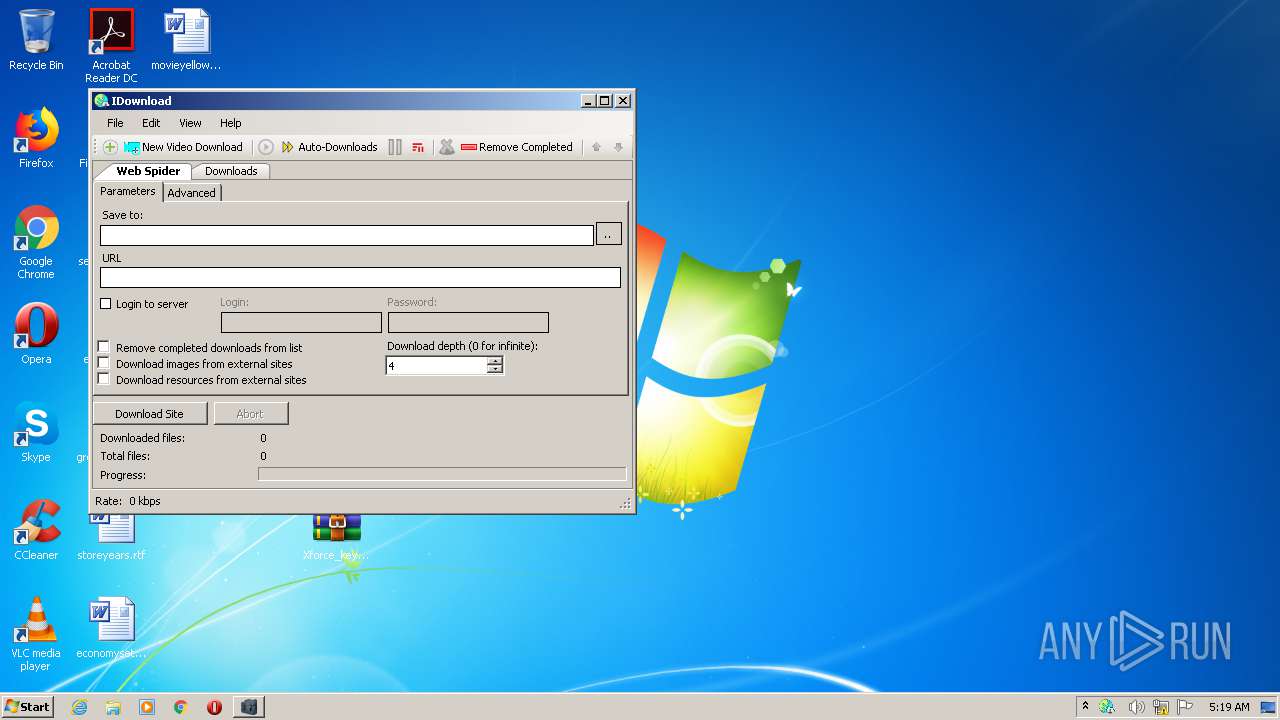
- IDownload.exe (PID: 3484)
- IDownload.App.exe (PID: 2476)
- Wudalakawi.exe (PID: 2540)
- SHigetinushae.exe (PID: 2960)
- hbggg.exe (PID: 5260)
- ifhwwyy.exe (PID: 13988)
- hbggg.exe (PID: 12256)
- jfiag3g_gg.exe (PID: 6504)
- jfiag3g_gg.exe (PID: 4548)
- Setup3310.exe (PID: 12972)
- jfiag3g_gg.exe (PID: 13172)
- jfiag3g_gg.exe (PID: 4336)
- google-game.exe (PID: 12044)
- SunLabsPlayer.exe (PID: 10548)
- guihuali-game.exe (PID: 13856)
- jfiag3g_gg.exe (PID: 6592)
- lighteningplayer-cache-gen.exe (PID: 11192)
- hjjgaa.exe (PID: 10188)
- NMemo3Setp.exe (PID: 9928)
- ns5A53.tmp (PID: 8364)
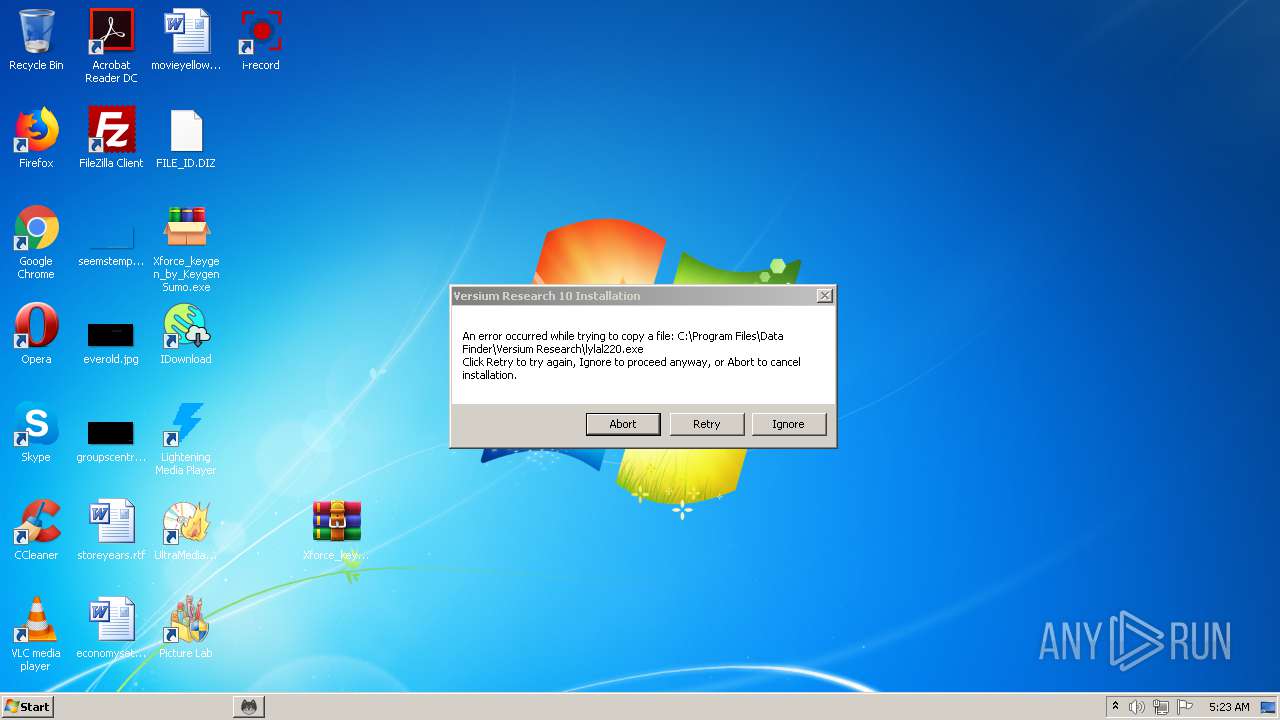
- lylal220.exe (PID: 2096)
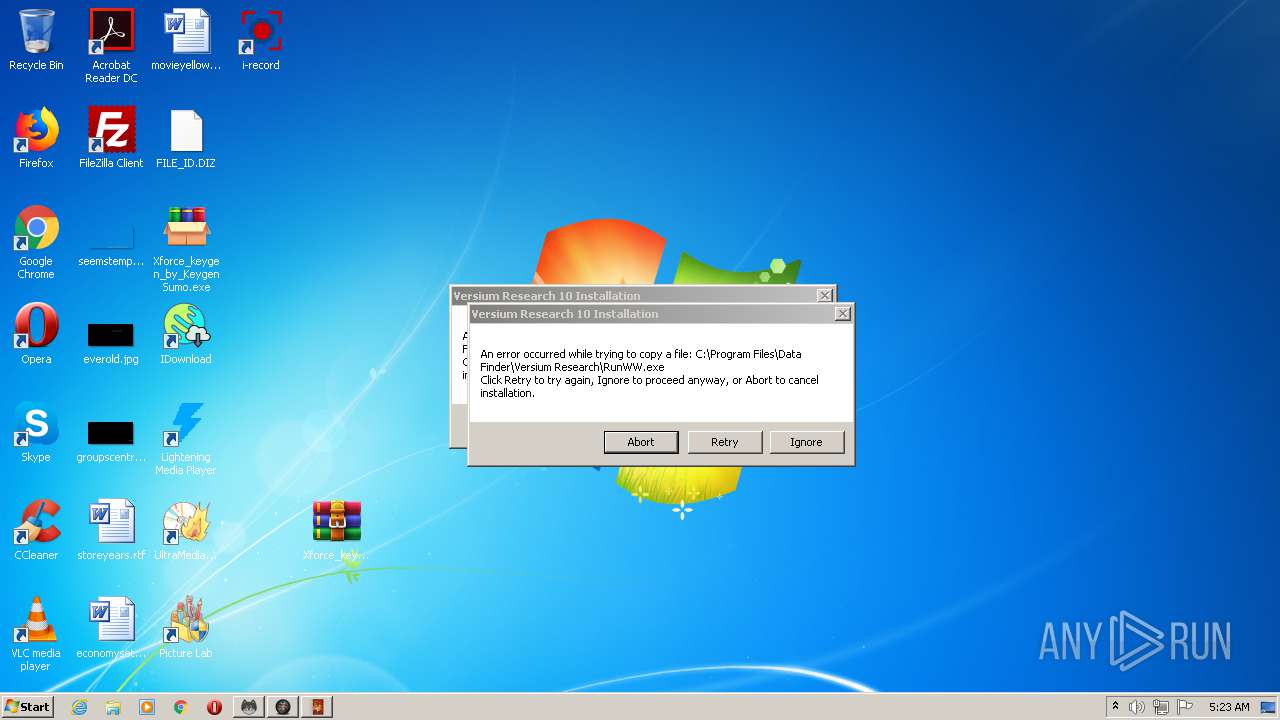
- RunWW.exe (PID: 11172)
- LabPicV3.exe (PID: 13008)
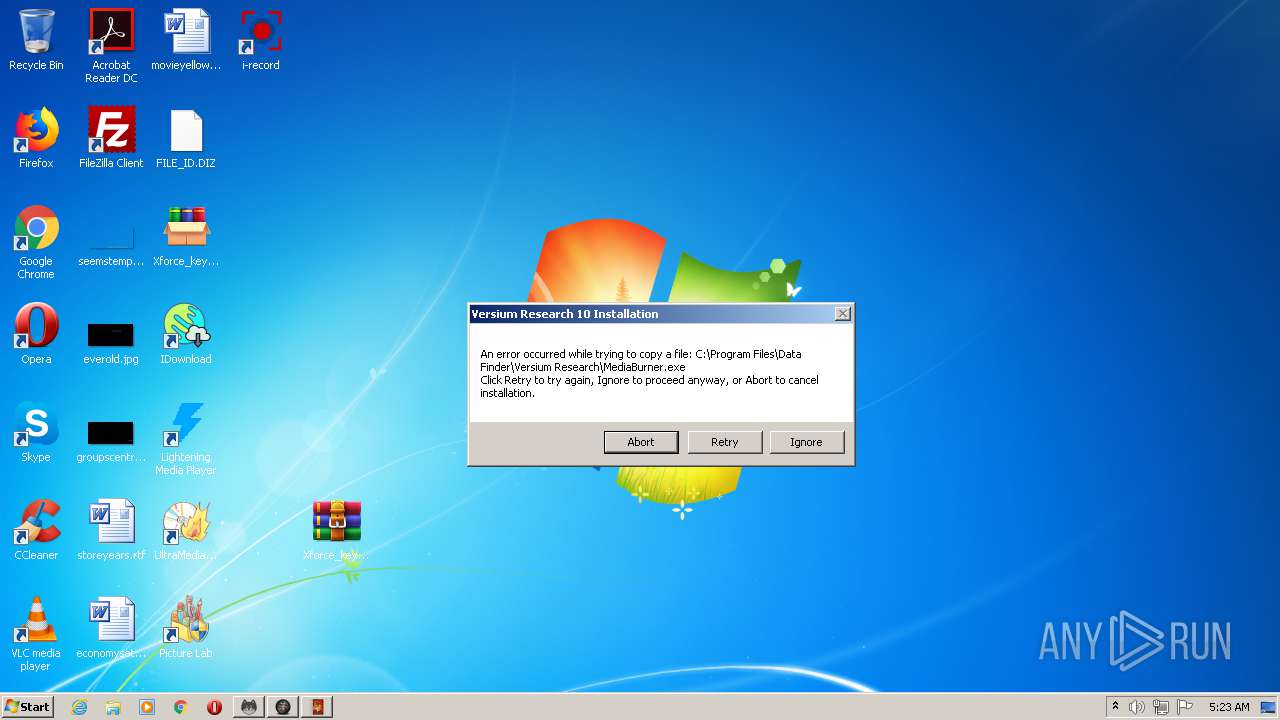
- MediaBurner.exe (PID: 8940)
- ns39F8.tmp (PID: 8572)
- jfiag3g_gg.exe (PID: 13956)
- 7625686.exe (PID: 4504)
- 7451165.exe (PID: 9444)
- ultramediaburner.exe (PID: 10248)
- 7233392.exe (PID: 11356)
- prolab.exe (PID: 6384)
- UltraMediaBurner.exe (PID: 1548)
- irecord.exe (PID: 12104)
- Sezhaetyhaezhae.exe (PID: 924)
- Cubaezhesihae.exe (PID: 13880)
- Qizhozhegaezha.exe (PID: 11624)
- ZHuxeshaewequ.exe (PID: 9728)
- I-Record.exe (PID: 4804)
- Fabikelaemu.exe (PID: 13604)
- Pytikaedaepo.exe (PID: 7964)
- ifhwwyy.exe (PID: 19700)
- ifhwwyy.exe (PID: 14616)
- ifhwwyy.exe (PID: 20136)
- jfiag3g_gg.exe (PID: 10236)
- jfiag3g_gg.exe (PID: 6728)
- Setup3310.exe (PID: 6376)
- jfiag3g_gg.exe (PID: 14548)
- Setup3310.exe (PID: 14180)
- Setup3310.exe (PID: 5000)
- google-game.exe (PID: 4868)
- google-game.exe (PID: 5940)
- jfiag3g_gg.exe (PID: 12716)
- jfiag3g_gg.exe (PID: 15836)
- google-game.exe (PID: 11148)
- jfiag3g_gg.exe (PID: 10300)
- SunLabsPlayer.exe (PID: 7516)
- SunLabsPlayer.exe (PID: 8580)
- SunLabsPlayer.exe (PID: 10752)
- nsEE21.tmp (PID: 10568)
- nsEE11.tmp (PID: 9580)
- nsF5B2.tmp (PID: 2768)
- ns40A7.tmp (PID: 17524)
- lighteningplayer-cache-gen.exe (PID: 2968)
- lighteningplayer-cache-gen.exe (PID: 11324)
- ns42BA.tmp (PID: 944)
- lighteningplayer-cache-gen.exe (PID: 3720)
- ns40A7.tmp (PID: 16276)
- hjjgaa.exe (PID: 13388)
- MediaBurner.exe (PID: 10756)
- RunWW.exe (PID: 5488)
- lylal220.exe (PID: 12416)
- NMemo3Setp.exe (PID: 17372)
- LabPicV3.exe (PID: 17736)
- jfiag3g_gg.exe (PID: 18260)
- guihuali-game.exe (PID: 12960)
- hjjgaa.exe (PID: 2608)
- RunWW.exe (PID: 3416)
- NMemo3Setp.exe (PID: 6680)
- MediaBurner.exe (PID: 5496)
- lylal220.exe (PID: 8152)
- LabPicV3.exe (PID: 4916)
- guihuali-game.exe (PID: 18532)
- jfiag3g_gg.exe (PID: 13500)
- hjjgaa.exe (PID: 16176)
- RunWW.exe (PID: 9916)
- NMemo3Setp.exe (PID: 7132)
- MediaBurner.exe (PID: 16980)
- jfiag3g_gg.exe (PID: 8600)
- guihuali-game.exe (PID: 9552)
- 7032118.exe (PID: 6808)
- jfiag3g_gg.exe (PID: 11416)
- lylal220.exe (PID: 8956)
- LabPicV3.exe (PID: 5132)
- 8936632.exe (PID: 18884)
- 4565871.exe (PID: 5976)
- prolab.exe (PID: 9644)
- jfiag3g_gg.exe (PID: 9148)
Drops executable file immediately after starts
- keygen-pr.exe (PID: 3996)
- cmd.exe (PID: 2864)
- Crack.exe (PID: 2688)
- cmd.exe (PID: 2920)
- IDWCH1.exe (PID: 2040)
- IDWCH1.exe (PID: 4072)
- IDownload.exe (PID: 3484)
- IDownload.tmp (PID: 2676)
- ifhwwyy.exe (PID: 13988)
- hbggg.exe (PID: 12256)
- Setup3310.exe (PID: 12972)
- google-game.exe (PID: 12044)
- Setup3310.tmp (PID: 4912)
- ultramediaburner.exe (PID: 10248)
- ultramediaburner.tmp (PID: 8752)
- prolab.exe (PID: 6384)
- prolab.tmp (PID: 5336)
- irecord.exe (PID: 12104)
- Setup3310.exe (PID: 5000)
- google-game.exe (PID: 5940)
- google-game.exe (PID: 4868)
- google-game.exe (PID: 11148)
- MediaBurner.exe (PID: 10756)
- lylal220.exe (PID: 8152)
- MediaBurner.exe (PID: 5496)
Stealing of credential data
- keygen-step-3.exe (PID: 2756)
- 43A1.tmp.exe (PID: 2172)
- RunWW.exe (PID: 11172)
Connects to CnC server
- keygen-step-1.exe (PID: 2416)
- keygen-step-3.exe (PID: 2756)
- 43A1.tmp.exe (PID: 2172)
- key.exe (PID: 4056)
- ifhwwyy.exe (PID: 13988)
- hbggg.exe (PID: 12256)
- hjjgaa.exe (PID: 10188)
- ifhwwyy.exe (PID: 14616)
- ifhwwyy.exe (PID: 20136)
- ifhwwyy.exe (PID: 19700)
- hjjgaa.exe (PID: 13388)
- hjjgaa.exe (PID: 2608)
AZORULT was detected
- keygen-step-1.exe (PID: 2416)
Runs PING.EXE for delay simulation
- cmd.exe (PID: 996)
Registers / Runs the DLL via REGSVR32.EXE
- cmd.exe (PID: 2920)
Loads dropped or rewritten executable
- rUNdlL32.eXe (PID: 2432)
- 43A1.tmp.exe (PID: 2172)
- 1710767.exe (PID: 3404)
- IDownload.App.exe (PID: 2476)
- rUNdlL32.eXe (PID: 5100)
- SunLabsPlayer.exe (PID: 10548)
- lighteningplayer-cache-gen.exe (PID: 11192)
- rUNdlL32.eXe (PID: 3888)
- RunWW.exe (PID: 11172)
- I-Record.exe (PID: 4804)
- 7451165.exe (PID: 9444)
- rUNdlL32.eXe (PID: 19604)
- rUNdlL32.eXe (PID: 17684)
- rUNdlL32.eXe (PID: 9424)
- SunLabsPlayer.exe (PID: 10752)
- SunLabsPlayer.exe (PID: 7516)
- SunLabsPlayer.exe (PID: 8580)
- lighteningplayer-cache-gen.exe (PID: 11324)
- lighteningplayer-cache-gen.exe (PID: 2968)
- lighteningplayer-cache-gen.exe (PID: 3720)
- rUNdlL32.eXe (PID: 8260)
Runs injected code in another process
- svchost.exe (PID: 876)
- rUNdlL32.eXe (PID: 2432)
Changes settings of System certificates
- 43A1.tmp.exe (PID: 2172)
- 1710767.exe (PID: 3404)
- Piiiiiiiipç87.exe (PID: 2964)
- SHigetinushae.exe (PID: 2960)
- ifhwwyy.exe (PID: 13988)
- Setup3310.tmp (PID: 4912)
Writes to a start menu file
- 5C0D.tmp.exe (PID: 4088)
RACCOON was detected
- 43A1.tmp.exe (PID: 2172)
Actions looks like stealing of personal data
- 43A1.tmp.exe (PID: 2172)
- key.exe (PID: 4056)
- svchost.exe (PID: 2252)
- 1710767.exe (PID: 3404)
- 6937479.exe (PID: 3548)
- Setup3310.tmp (PID: 4912)
- RunWW.exe (PID: 11172)
- 7451165.exe (PID: 9444)
- 7625686.exe (PID: 4504)
- Setup3310.tmp (PID: 17540)
- Setup3310.tmp (PID: 18992)
- Setup3310.tmp (PID: 7572)
Application was injected by another process
- svchost.exe (PID: 2252)
- svchost.exe (PID: 904)
- svchost.exe (PID: 876)
Changes the autorun value in the registry
- 8602741.exe (PID: 2468)
- Piiiiiiiipç87.exe (PID: 2964)
- ifhwwyy.exe (PID: 13988)
- 758____Dawn.exe (PID: 4188)
- ElZané_çé_.exe (PID: 13276)
- JFHGSFGSIUGFSUIG.exe (PID: 10016)
Steals credentials from Web Browsers
- key.exe (PID: 4056)
- 43A1.tmp.exe (PID: 2172)
- svchost.exe (PID: 2252)
- 1710767.exe (PID: 3404)
- 6937479.exe (PID: 3548)
- RunWW.exe (PID: 11172)
- 7451165.exe (PID: 9444)
- 7625686.exe (PID: 4504)
AGENTTESLA was detected
- svchost.exe (PID: 2252)
Detected Pony/Fareit Trojan
- key.exe (PID: 4056)
PONY was detected
- key.exe (PID: 4056)
REDLINE was detected
- 6937479.exe (PID: 3548)
- 7625686.exe (PID: 4504)
Starts Visual C# compiler
- IDownload.App.exe (PID: 2476)
VIDAR was detected
- RunWW.exe (PID: 11172)
SUSPICIOUS
Drops a file with a compile date too recent
- Xforce_keygen_by_KeygenSumo.exe (PID: 2928)
- keygen-step-4.exe (PID: 3580)
- GloryWSetp.exe (PID: 3552)
- 8602741.exe (PID: 2468)
- 43A1.tmp.exe (PID: 2172)
- Piiiiiiiipç87.exe (PID: 2964)
- SHigetinushae.exe (PID: 2960)
- google-game.exe (PID: 12044)
- Setup.exe (PID: 6040)
- NMemo3Setp.exe (PID: 9928)
- JFHGSFGSIUGFSUIG.exe (PID: 10016)
- 758____Dawn.exe (PID: 4188)
- irecord.tmp (PID: 5460)
- ElZané_çé_.exe (PID: 13276)
- ZHuxeshaewequ.exe (PID: 9728)
- Pytikaedaepo.exe (PID: 7964)
- Cubaezhesihae.exe (PID: 13880)
- google-game.exe (PID: 5940)
- google-game.exe (PID: 11148)
- google-game.exe (PID: 4868)
- Setup.exe (PID: 18792)
- NMemo3Setp.exe (PID: 17372)
- Setup.exe (PID: 7248)
- Setup.exe (PID: 7332)
- NMemo3Setp.exe (PID: 6680)
- ElZané_çé_.exe (PID: 16672)
- JFHGSFGSIUGFSUIG.exe (PID: 15760)
- 758____Dawn.exe (PID: 5920)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2192)
- Xforce_keygen_by_KeygenSumo.exe (PID: 2928)
- keygen-pr.exe (PID: 3996)
- keygen-step-4.exe (PID: 3580)
- cmd.exe (PID: 2864)
- Crack.exe (PID: 2688)
- keygen-step-6.exe (PID: 2152)
- cmd.exe (PID: 2920)
- 5C0D.tmp.exe (PID: 4088)
- GloryWSetp.exe (PID: 3552)
- 43A1.tmp.exe (PID: 2172)
- 8602741.exe (PID: 2468)
- IDWCH1.exe (PID: 2040)
- 1710767.exe (PID: 3404)
- IDWCH1.tmp (PID: 2932)
- IDWCH1.exe (PID: 4072)
- Piiiiiiiipç87.exe (PID: 2964)
- IDownload.exe (PID: 3484)
- IDownload.tmp (PID: 2676)
- SHigetinushae.exe (PID: 2960)
- ifhwwyy.exe (PID: 13988)
- hbggg.exe (PID: 12256)
- Setup3310.exe (PID: 12972)
- Setup3310.tmp (PID: 4912)
- google-game.exe (PID: 12044)
- Setup.exe (PID: 6040)
- SunLabsPlayer.exe (PID: 10548)
- MediaBurner.exe (PID: 8940)
- lylal220.exe (PID: 2096)
- LabPicV3.exe (PID: 13008)
- hjjgaa.exe (PID: 10188)
- guihuali-game.exe (PID: 13856)
- MediaBurner.tmp (PID: 4160)
- LabPicV3.tmp (PID: 4108)
- NMemo3Setp.exe (PID: 9928)
- lylal220.tmp (PID: 6256)
- RunWW.exe (PID: 11172)
- JFHGSFGSIUGFSUIG.exe (PID: 10016)
- ultramediaburner.exe (PID: 10248)
- ultramediaburner.tmp (PID: 8752)
- 758____Dawn.exe (PID: 4188)
- 7451165.exe (PID: 9444)
- prolab.tmp (PID: 5336)
- prolab.exe (PID: 6384)
- ElZané_çé_.exe (PID: 13276)
- irecord.exe (PID: 12104)
- irecord.tmp (PID: 5460)
- Cubaezhesihae.exe (PID: 13880)
- ZHuxeshaewequ.exe (PID: 9728)
- Pytikaedaepo.exe (PID: 7964)
- Setup3310.exe (PID: 6376)
- ifhwwyy.exe (PID: 19700)
- Setup3310.exe (PID: 14180)
- Setup3310.exe (PID: 5000)
- Setup3310.tmp (PID: 18992)
- Setup3310.tmp (PID: 7572)
- google-game.exe (PID: 5940)
- google-game.exe (PID: 4868)
- Setup3310.tmp (PID: 17540)
- ifhwwyy.exe (PID: 20136)
- google-game.exe (PID: 11148)
- SunLabsPlayer.exe (PID: 7516)
- SunLabsPlayer.exe (PID: 10752)
- Setup.exe (PID: 18792)
- MediaBurner.exe (PID: 10756)
- SunLabsPlayer.exe (PID: 8580)
- lylal220.exe (PID: 12416)
- LabPicV3.exe (PID: 17736)
- hjjgaa.exe (PID: 13388)
- MediaBurner.tmp (PID: 19992)
- guihuali-game.exe (PID: 12960)
- lylal220.tmp (PID: 7012)
- LabPicV3.tmp (PID: 10080)
- NMemo3Setp.exe (PID: 17372)
- Setup.exe (PID: 7248)
- MediaBurner.exe (PID: 5496)
- lylal220.exe (PID: 8152)
- LabPicV3.exe (PID: 4916)
- MediaBurner.tmp (PID: 19644)
- Setup.exe (PID: 7332)
- hjjgaa.exe (PID: 2608)
- lylal220.tmp (PID: 5592)
- LabPicV3.tmp (PID: 16688)
- MediaBurner.exe (PID: 16980)
- guihuali-game.exe (PID: 18532)
- LabPicV3.exe (PID: 5132)
- MediaBurner.tmp (PID: 12516)
- lylal220.exe (PID: 8956)
- lylal220.tmp (PID: 2628)
- guihuali-game.exe (PID: 9552)
- LabPicV3.tmp (PID: 12652)
- NMemo3Setp.exe (PID: 6680)
- ElZané_çé_.exe (PID: 16672)
- prolab.exe (PID: 9644)
- JFHGSFGSIUGFSUIG.exe (PID: 15760)
- 758____Dawn.exe (PID: 5920)
- prolab.tmp (PID: 4844)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 2192)
- keygen-step-4.exe (PID: 3580)
- Xforce_keygen_by_KeygenSumo.exe (PID: 2928)
- cmd.exe (PID: 2864)
- Crack.exe (PID: 2688)
- keygen-step-6.exe (PID: 2152)
- 43A1.tmp.exe (PID: 2172)
- 1710767.exe (PID: 3404)
- IDWCH1.tmp (PID: 2932)
- IDownload.tmp (PID: 2676)
- SHigetinushae.exe (PID: 2960)
- ifhwwyy.exe (PID: 13988)
- SunLabsPlayer.exe (PID: 10548)
- Setup.exe (PID: 6040)
- guihuali-game.exe (PID: 13856)
- MediaBurner.tmp (PID: 4160)
- LabPicV3.tmp (PID: 4108)
- Setup3310.tmp (PID: 4912)
- lylal220.tmp (PID: 6256)
- RunWW.exe (PID: 11172)
- ultramediaburner.tmp (PID: 8752)
- 7451165.exe (PID: 9444)
- prolab.tmp (PID: 5336)
- irecord.tmp (PID: 5460)
- Cubaezhesihae.exe (PID: 13880)
- ZHuxeshaewequ.exe (PID: 9728)
- Pytikaedaepo.exe (PID: 7964)
- Setup3310.tmp (PID: 18992)
- Setup3310.tmp (PID: 7572)
- Setup3310.tmp (PID: 17540)
- SunLabsPlayer.exe (PID: 10752)
- SunLabsPlayer.exe (PID: 7516)
- SunLabsPlayer.exe (PID: 8580)
- Setup.exe (PID: 18792)
- MediaBurner.tmp (PID: 19992)
- lylal220.tmp (PID: 7012)
- LabPicV3.tmp (PID: 10080)
- guihuali-game.exe (PID: 12960)
- MediaBurner.tmp (PID: 19644)
- guihuali-game.exe (PID: 18532)
- lylal220.tmp (PID: 5592)
- LabPicV3.tmp (PID: 16688)
- MediaBurner.tmp (PID: 12516)
- lylal220.tmp (PID: 2628)
- LabPicV3.tmp (PID: 12652)
- guihuali-game.exe (PID: 9552)
- prolab.tmp (PID: 4844)
Starts CMD.EXE for commands execution
- Xforce_keygen_by_KeygenSumo.exe (PID: 2928)
- keygen-step-5.exe (PID: 1940)
- keygen-step-3.exe (PID: 2756)
- JNCo2Vf2MC.EXE (PID: 2724)
- cmd.exe (PID: 2920)
- keygen-step-6.exe (PID: 2152)
- 43A1.tmp.exe (PID: 2172)
- SHigetinushae.exe (PID: 2960)
- RunWW.exe (PID: 11172)
- ZHuxeshaewequ.exe (PID: 9728)
- Cubaezhesihae.exe (PID: 13880)
- Pytikaedaepo.exe (PID: 7964)
Drops a file with too old compile date
- keygen-step-4.exe (PID: 3580)
- Xforce_keygen_by_KeygenSumo.exe (PID: 2928)
- Crack.exe (PID: 2688)
- cmd.exe (PID: 2920)
- IDWCH1.exe (PID: 2040)
- 43A1.tmp.exe (PID: 2172)
- IDWCH1.exe (PID: 4072)
- IDWCH1.tmp (PID: 2932)
- Piiiiiiiipç87.exe (PID: 2964)
- IDownload.exe (PID: 3484)
- IDownload.tmp (PID: 2676)
- SHigetinushae.exe (PID: 2960)
- Setup3310.exe (PID: 12972)
- Setup3310.tmp (PID: 4912)
- Setup.exe (PID: 6040)
- SunLabsPlayer.exe (PID: 10548)
- MediaBurner.exe (PID: 8940)
- lylal220.exe (PID: 2096)
- LabPicV3.exe (PID: 13008)
- guihuali-game.exe (PID: 13856)
- MediaBurner.tmp (PID: 4160)
- LabPicV3.tmp (PID: 4108)
- lylal220.tmp (PID: 6256)
- JFHGSFGSIUGFSUIG.exe (PID: 10016)
- ultramediaburner.exe (PID: 10248)
- ultramediaburner.tmp (PID: 8752)
- 758____Dawn.exe (PID: 4188)
- prolab.exe (PID: 6384)
- prolab.tmp (PID: 5336)
- irecord.exe (PID: 12104)
- irecord.tmp (PID: 5460)
- ElZané_çé_.exe (PID: 13276)
- ZHuxeshaewequ.exe (PID: 9728)
- Cubaezhesihae.exe (PID: 13880)
- Pytikaedaepo.exe (PID: 7964)
- Setup3310.exe (PID: 14180)
- Setup3310.exe (PID: 5000)
- Setup3310.tmp (PID: 18992)
- Setup3310.tmp (PID: 7572)
- Setup3310.exe (PID: 6376)
- Setup3310.tmp (PID: 17540)
- SunLabsPlayer.exe (PID: 8580)
- SunLabsPlayer.exe (PID: 10752)
- Setup.exe (PID: 18792)
- SunLabsPlayer.exe (PID: 7516)
- lylal220.exe (PID: 12416)
- LabPicV3.exe (PID: 17736)
- MediaBurner.tmp (PID: 19992)
- guihuali-game.exe (PID: 12960)
- MediaBurner.exe (PID: 10756)
- lylal220.tmp (PID: 7012)
- LabPicV3.tmp (PID: 10080)
- Setup.exe (PID: 7248)
- lylal220.exe (PID: 8152)
- MediaBurner.exe (PID: 5496)
- LabPicV3.exe (PID: 4916)
- Setup.exe (PID: 7332)
- MediaBurner.tmp (PID: 19644)
- guihuali-game.exe (PID: 18532)
- lylal220.tmp (PID: 5592)
- LabPicV3.tmp (PID: 16688)
- MediaBurner.exe (PID: 16980)
- lylal220.exe (PID: 8956)
- LabPicV3.exe (PID: 5132)
- MediaBurner.tmp (PID: 12516)
- lylal220.tmp (PID: 2628)
- LabPicV3.tmp (PID: 12652)
- guihuali-game.exe (PID: 9552)
- 758____Dawn.exe (PID: 5920)
- prolab.exe (PID: 9644)
- prolab.tmp (PID: 4844)
Reads the cookies of Google Chrome
- keygen-step-3.exe (PID: 2756)
- 43A1.tmp.exe (PID: 2172)
- svchost.exe (PID: 2252)
- 1710767.exe (PID: 3404)
- 6937479.exe (PID: 3548)
- jfiag3g_gg.exe (PID: 6504)
- jfiag3g_gg.exe (PID: 4548)
- jfiag3g_gg.exe (PID: 6592)
- RunWW.exe (PID: 11172)
- 7451165.exe (PID: 9444)
- 7625686.exe (PID: 4504)
- jfiag3g_gg.exe (PID: 14548)
- jfiag3g_gg.exe (PID: 10236)
- jfiag3g_gg.exe (PID: 6728)
- jfiag3g_gg.exe (PID: 18260)
- jfiag3g_gg.exe (PID: 13500)
Starts CMD.EXE for self-deleting
- keygen-step-3.exe (PID: 2756)
- keygen-step-6.exe (PID: 2152)
- 43A1.tmp.exe (PID: 2172)
- RunWW.exe (PID: 11172)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 2864)
- cmd.exe (PID: 12412)
Application launched itself
- key.exe (PID: 4056)
- cmd.exe (PID: 2920)
- hbggg.exe (PID: 5260)
Creates files in the user directory
- keygen-step-6.exe (PID: 2152)
- 5C0D.tmp.exe (PID: 4088)
- GloryWSetp.exe (PID: 3552)
- 8602741.exe (PID: 2468)
- key.exe (PID: 4056)
- svchost.exe (PID: 2252)
- SunLabsPlayer.exe (PID: 10548)
- powershell.exe (PID: 4492)
- NMemo3Setp.exe (PID: 9928)
- powershell.exe (PID: 14508)
- powershell.exe (PID: 5504)
- powershell.exe (PID: 6960)
- NMemo3Setp.exe (PID: 17372)
- NMemo3Setp.exe (PID: 6680)
Reads Environment values
- key.exe (PID: 2808)
- 6937479.exe (PID: 3548)
- 7625686.exe (PID: 4504)
Reads Windows Product ID
- key.exe (PID: 2808)
Reads the Windows organization settings
- key.exe (PID: 2808)
Reads Windows owner or organization settings
- key.exe (PID: 2808)
Adds / modifies Windows certificates
- 43A1.tmp.exe (PID: 2172)
- 1710767.exe (PID: 3404)
- SHigetinushae.exe (PID: 2960)
- ifhwwyy.exe (PID: 13988)
- Setup3310.tmp (PID: 4912)
Uses RUNDLL32.EXE to load library
- Crack.exe (PID: 2688)
- google-game.exe (PID: 12044)
- guihuali-game.exe (PID: 13856)
- google-game.exe (PID: 4868)
- google-game.exe (PID: 5940)
- google-game.exe (PID: 11148)
- guihuali-game.exe (PID: 12960)
Dropped object may contain URLs of mainers pools
- keygen-step-6.exe (PID: 2152)
Low-level read access rights to disk partition
- svchost.exe (PID: 904)
- svchost.exe (PID: 2252)
Searches for installed software
- key.exe (PID: 2808)
- 43A1.tmp.exe (PID: 2172)
- key.exe (PID: 4056)
- 1710767.exe (PID: 3404)
- 6937479.exe (PID: 3548)
- RunWW.exe (PID: 11172)
- 7451165.exe (PID: 9444)
- 7625686.exe (PID: 4504)
Loads DLL from Mozilla Firefox
- key.exe (PID: 4056)
Starts itself from another location
- 8602741.exe (PID: 2468)
Reads the cookies of Mozilla Firefox
- 43A1.tmp.exe (PID: 2172)
- svchost.exe (PID: 2252)
- 1710767.exe (PID: 3404)
- 6937479.exe (PID: 3548)
- RunWW.exe (PID: 11172)
- 7451165.exe (PID: 9444)
- 7625686.exe (PID: 4504)
Creates files in the program directory
- 1710767.exe (PID: 3404)
- SunLabsPlayer.exe (PID: 10548)
- lighteningplayer-cache-gen.exe (PID: 11192)
- RunWW.exe (PID: 11172)
- 7451165.exe (PID: 9444)
- lighteningplayer-cache-gen.exe (PID: 11324)
- lighteningplayer-cache-gen.exe (PID: 2968)
- lighteningplayer-cache-gen.exe (PID: 3720)
Checks for external IP
- svchost.exe (PID: 2252)
- ifhwwyy.exe (PID: 13988)
- hbggg.exe (PID: 12256)
- Setup3310.tmp (PID: 4912)
- hjjgaa.exe (PID: 10188)
- ifhwwyy.exe (PID: 19700)
- ifhwwyy.exe (PID: 14616)
- ifhwwyy.exe (PID: 20136)
- Setup3310.tmp (PID: 18992)
- Setup3310.tmp (PID: 7572)
- Setup3310.tmp (PID: 17540)
- hjjgaa.exe (PID: 13388)
- hjjgaa.exe (PID: 2608)
- hjjgaa.exe (PID: 16176)
Creates a directory in Program Files
- IDownload.tmp (PID: 2676)
- Piiiiiiiipç87.exe (PID: 2964)
- SunLabsPlayer.exe (PID: 10548)
- Setup.exe (PID: 6040)
- JFHGSFGSIUGFSUIG.exe (PID: 10016)
- 758____Dawn.exe (PID: 4188)
- ElZané_çé_.exe (PID: 13276)
- ultramediaburner.tmp (PID: 8752)
- prolab.tmp (PID: 5336)
- irecord.tmp (PID: 5460)
- 758____Dawn.exe (PID: 5920)
Executed via COM
- iexplore.exe (PID: 2412)
Starts Internet Explorer
- Wudalakawi.exe (PID: 2540)
- Qizhozhegaezha.exe (PID: 11624)
- Sezhaetyhaezhae.exe (PID: 924)
- Fabikelaemu.exe (PID: 13604)
Creates a software uninstall entry
- SunLabsPlayer.exe (PID: 10548)
- SunLabsPlayer.exe (PID: 7516)
- SunLabsPlayer.exe (PID: 10752)
- SunLabsPlayer.exe (PID: 8580)
Executes application which crashes
- cmd.exe (PID: 4288)
- cmd.exe (PID: 2284)
- cmd.exe (PID: 10092)
- cmd.exe (PID: 17508)
Starts application with an unusual extension
- SunLabsPlayer.exe (PID: 10548)
- SunLabsPlayer.exe (PID: 10752)
- SunLabsPlayer.exe (PID: 8580)
- SunLabsPlayer.exe (PID: 7516)
Executes PowerShell scripts
- ns39F8.tmp (PID: 8572)
- nsEE11.tmp (PID: 9580)
- nsEE21.tmp (PID: 10568)
- nsF5B2.tmp (PID: 2768)
INFO
Manual execution by user
- WinRAR.exe (PID: 2192)
- Xforce_keygen_by_KeygenSumo.exe (PID: 2928)
Reads Microsoft Office registry keys
- key.exe (PID: 2808)
Application was dropped or rewritten from another process
- IDWCH1.tmp (PID: 2908)
- IDWCH1.tmp (PID: 2932)
- Piiiiiiiipç87.exe (PID: 2964)
- IDownload.tmp (PID: 2676)
- Setup3310.tmp (PID: 4912)
- Setup.exe (PID: 6040)
- lylal220.tmp (PID: 6256)
- 758____Dawn.exe (PID: 4188)
- LabPicV3.tmp (PID: 4108)
- MediaBurner.tmp (PID: 4160)
- JFHGSFGSIUGFSUIG.exe (PID: 10016)
- ElZané_çé_.exe (PID: 13276)
- ultramediaburner.tmp (PID: 8752)
- prolab.tmp (PID: 5336)
- irecord.tmp (PID: 5460)
- Setup3310.tmp (PID: 18992)
- Setup3310.tmp (PID: 7572)
- Setup3310.tmp (PID: 17540)
- Setup.exe (PID: 18792)
- Setup.exe (PID: 7332)
- Setup.exe (PID: 7248)
- MediaBurner.tmp (PID: 19992)
- lylal220.tmp (PID: 7012)
- LabPicV3.tmp (PID: 10080)
- JFHGSFGSIUGFSUIG.exe (PID: 15760)
- 758____Dawn.exe (PID: 5920)
- ElZané_çé_.exe (PID: 16672)
- MediaBurner.tmp (PID: 19644)
- LabPicV3.tmp (PID: 16688)
- lylal220.tmp (PID: 5592)
- MediaBurner.tmp (PID: 12516)
- lylal220.tmp (PID: 2628)
- LabPicV3.tmp (PID: 12652)
- JFHGSFGSIUGFSUIG.exe (PID: 14928)
- ElZané_çé_.exe (PID: 17484)
- 758____Dawn.exe (PID: 10268)
- prolab.tmp (PID: 4844)
- JFHGSFGSIUGFSUIG.exe (PID: 16560)
- ElZané_çé_.exe (PID: 15944)
- 758____Dawn.exe (PID: 17144)
Loads dropped or rewritten executable
- IDWCH1.tmp (PID: 2932)
- IDownload.tmp (PID: 2676)
- Setup3310.tmp (PID: 4912)
- MediaBurner.tmp (PID: 4160)
- lylal220.tmp (PID: 6256)
- LabPicV3.tmp (PID: 4108)
- ultramediaburner.tmp (PID: 8752)
- prolab.tmp (PID: 5336)
- irecord.tmp (PID: 5460)
- Setup3310.tmp (PID: 7572)
- Setup3310.tmp (PID: 18992)
- Setup3310.tmp (PID: 17540)
- LabPicV3.tmp (PID: 10080)
- MediaBurner.tmp (PID: 19992)
- lylal220.tmp (PID: 7012)
- MediaBurner.tmp (PID: 19644)
- lylal220.tmp (PID: 5592)
- LabPicV3.tmp (PID: 16688)
- MediaBurner.tmp (PID: 12516)
- lylal220.tmp (PID: 2628)
- LabPicV3.tmp (PID: 12652)
Creates files in the program directory
- Piiiiiiiipç87.exe (PID: 2964)
- IDownload.tmp (PID: 2676)
- Setup.exe (PID: 6040)
- JFHGSFGSIUGFSUIG.exe (PID: 10016)
- 758____Dawn.exe (PID: 4188)
- ultramediaburner.tmp (PID: 8752)
- prolab.tmp (PID: 5336)
- ElZané_çé_.exe (PID: 13276)
- irecord.tmp (PID: 5460)
- Setup.exe (PID: 18792)
- Setup.exe (PID: 7248)
- Setup.exe (PID: 7332)
- 758____Dawn.exe (PID: 5920)
Creates a software uninstall entry
- IDownload.tmp (PID: 2676)
- Setup.exe (PID: 6040)
- ultramediaburner.tmp (PID: 8752)
- prolab.tmp (PID: 5336)
- irecord.tmp (PID: 5460)
- Setup.exe (PID: 18792)
- Setup.exe (PID: 7248)
- Setup.exe (PID: 7332)
Reads settings of System Certificates
- Wudalakawi.exe (PID: 2540)
- SHigetinushae.exe (PID: 2960)
- iexplore.exe (PID: 2760)
- iexplore.exe (PID: 308)
- iexplore.exe (PID: 2580)
- iexplore.exe (PID: 2412)
- Cubaezhesihae.exe (PID: 13880)
- ZHuxeshaewequ.exe (PID: 9728)
- Fabikelaemu.exe (PID: 13604)
- Pytikaedaepo.exe (PID: 7964)
- Sezhaetyhaezhae.exe (PID: 924)
- 758____Dawn.exe (PID: 5920)
Application launched itself
- iexplore.exe (PID: 2412)
- iexplore.exe (PID: 2580)
- iexplore.exe (PID: 11448)
- iexplore.exe (PID: 4544)
- iexplore.exe (PID: 12944)
Changes internet zones settings
- iexplore.exe (PID: 2412)
- iexplore.exe (PID: 2580)
- iexplore.exe (PID: 11448)
- iexplore.exe (PID: 12944)
- iexplore.exe (PID: 4544)
Changes settings of System certificates
- iexplore.exe (PID: 308)
- iexplore.exe (PID: 2580)
Adds / modifies Windows certificates
- iexplore.exe (PID: 308)
- iexplore.exe (PID: 2580)
Creates files in the user directory
- iexplore.exe (PID: 2760)
- iexplore.exe (PID: 308)
Reads internet explorer settings
- iexplore.exe (PID: 2760)
- iexplore.exe (PID: 308)
- iexplore.exe (PID: 6456)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | Xforce_keygen_by_KeygenSumo.zip |
|---|---|
| ZipUncompressedSize: | 6506518 |
| ZipCompressedSize: | 6506518 |
| ZipCRC: | 0xfad1872d |
| ZipModifyDate: | 2021:07:02 07:18:08 |
| ZipCompression: | None |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 10 |
Total processes
337
Monitored processes
230
Malicious processes
56
Suspicious processes
57
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 272 | ping 1.1.1.1 -n 1 -w 3000 | C:\Windows\system32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 308 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2580 CREDAT:275457 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 348 | "C:\Windows\system32\cmd.exe" /c ping 127.0.0.1 && del "C:\Users\admin\AppData\Local\Temp\RarSFX0\keygen-step-6.exe" >> NUL | C:\Windows\system32\cmd.exe | — | keygen-step-6.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 876 | C:\Windows\system32\svchost.exe -k netsvcs | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 904 | C:\Windows\system32\svchost.exe -k SystemNetworkService | C:\Windows\system32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 924 | "C:\Users\admin\AppData\Local\Temp\79-2c5b7-6a9-7569d-5204d928ba9d4\Sezhaetyhaezhae.exe" | C:\Users\admin\AppData\Local\Temp\79-2c5b7-6a9-7569d-5204d928ba9d4\Sezhaetyhaezhae.exe | JFHGSFGSIUGFSUIG.exe | ||||||||||||
User: admin Company: Soft_Cpm_ID__wcz9g62k6fav6864eh3z Integrity Level: HIGH Description: Soft_Cpm_ID__wcz9g62k6fav6864eh3z Exit code: 0 Version: 3.3.3.3 Modules
| |||||||||||||||
| 944 | "C:\Users\admin\AppData\Local\Temp\nscE16E.tmp\ns42BA.tmp" "C:\Program Files\lighteningplayer\lighteningplayer-cache-gen.exe" C:\Program Files\lighteningplayer\plugins\ /SILENT | C:\Users\admin\AppData\Local\Temp\nscE16E.tmp\ns42BA.tmp | — | SunLabsPlayer.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 996 | cmd.exe /C ping 1.1.1.1 -n 1 -w 3000 > Nul & Del /f /q "C:\Users\admin\AppData\Local\Temp\RarSFX0\keygen-step-3.exe" | C:\Windows\system32\cmd.exe | — | keygen-step-3.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1320 | "C:\Users\admin\AppData\Roaming\WinHost\WinHoster.exe" | C:\Users\admin\AppData\Roaming\WinHost\WinHoster.exe | — | 8602741.exe | |||||||||||
User: admin Company: WinHost Integrity Level: MEDIUM Description: WinHost Exit code: 0 Version: 1.0.0.12 Modules
| |||||||||||||||
| 1460 | "C:\Windows\System32\cmd.exe" /q /C TypE "C:\Users\admin\AppData\Local\Temp\JNCo2Vf2MC.EXE" > JNCo2Vf2MC.EXE &&stArt JNCo2VF2MC.eXe -PaZ3cHdzoOBUwugzFH & iF "-PaZ3cHdzoOBUwugzFH " == "" for %h In ( "C:\Users\admin\AppData\Local\Temp\JNCo2Vf2MC.EXE" ) do taskkill /f /iM "%~NXh" > NuL | C:\Windows\System32\cmd.exe | — | JNCo2Vf2MC.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
25 420
Read events
22 151
Write events
3 208
Delete events
61
Modification events
| (PID) Process: | (2136) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2136) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2136) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2136) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13D\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (2136) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\Xforce_keygen_by_KeygenSumo.zip | |||
| (PID) Process: | (2136) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2136) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2136) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2136) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2136) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
Executable files
836
Suspicious files
111
Text files
340
Unknown types
218
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2136 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2136.38554\Xforce_keygen_by_KeygenSumo.zip | — | |
MD5:— | SHA256:— | |||
| 2192 | WinRAR.exe | C:\Users\admin\Desktop\Xforce_keygen_by_KeygenSumo.exe | executable | |
MD5:— | SHA256:— | |||
| 2928 | Xforce_keygen_by_KeygenSumo.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\keygen-step-6.exe | executable | |
MD5:— | SHA256:— | |||
| 2928 | Xforce_keygen_by_KeygenSumo.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\keygen-step-4.exe | executable | |
MD5:— | SHA256:— | |||
| 2928 | Xforce_keygen_by_KeygenSumo.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\keygen-step-3.exe | executable | |
MD5:— | SHA256:— | |||
| 3580 | keygen-step-4.exe | C:\Users\admin\AppData\Local\Temp\RarSFX2\hbggg.exe | executable | |
MD5:— | SHA256:— | |||
| 2928 | Xforce_keygen_by_KeygenSumo.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\keygen.bat | text | |
MD5:96969F73AB2C8E4BE632CDBD0EAD0760 | SHA256:04C2002DE2CB5022E9C3B9325216CE74847F74166AA702EFF6DF01067930B49E | |||
| 2928 | Xforce_keygen_by_KeygenSumo.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\keygen-step-5.exe | executable | |
MD5:— | SHA256:— | |||
| 2864 | cmd.exe | C:\Users\admin\AppData\Local\Temp\JNCo2Vf2MC.EXE | executable | |
MD5:— | SHA256:— | |||
| 2928 | Xforce_keygen_by_KeygenSumo.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\keygen-step-1.exe | executable | |
MD5:C615D0BFA727F494FEE9ECB3F0ACF563 | SHA256:95D91FEBC45D03C1EE477C127BCBD332CD6FBCE1E91105004AF723594E6F0199 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
85
TCP/UDP connections
108
DNS requests
83
Threats
312
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2152 | keygen-step-6.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | US | der | 727 b | whitelisted |
2152 | keygen-step-6.exe | GET | 200 | 23.45.105.185:80 | http://x1.c.lencr.org/ | NL | der | 717 b | whitelisted |
2152 | keygen-step-6.exe | GET | 200 | 85.214.154.106:80 | http://www.almanhost.com/components/fw4.exe | DE | executable | 101 Kb | suspicious |
2152 | keygen-step-6.exe | GET | 200 | 85.214.154.106:80 | http://www.almanhost.com/components/fw3.exe | DE | executable | 118 Kb | suspicious |
2152 | keygen-step-6.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECEGmjTouN%2FW5s3CDseaiw7qE%3D | US | der | 471 b | whitelisted |
2172 | 43A1.tmp.exe | GET | — | 35.205.249.65:80 | http://35.205.249.65//l/f/7UoemHkBuI_ccNKojRXh/104bf05a22da2d07b24c600ab6b3f27e8da008f3 | US | — | — | malicious |
2152 | keygen-step-6.exe | GET | 301 | 85.214.154.106:80 | http://www.almanhost.com/components/fw6.exe | DE | executable | 101 Kb | suspicious |
2152 | keygen-step-6.exe | GET | 301 | 85.214.154.106:80 | http://www.almanhost.com/components/fw5.exe | DE | executable | 101 Kb | suspicious |
2152 | keygen-step-6.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | US | der | 471 b | whitelisted |
2152 | keygen-step-6.exe | GET | 301 | 85.214.154.106:80 | http://www.almanhost.com/components/fw2.php | DE | executable | 515 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2416 | keygen-step-1.exe | 185.173.37.179:80 | kvaka.li | M-Telecom, LLC | RU | malicious |
2756 | keygen-step-3.exe | 107.191.60.39:80 | www.w7dslkipoja.com | Choopa, LLC | JP | malicious |
2152 | keygen-step-6.exe | 151.139.128.14:80 | ocsp.comodoca.com | Highwinds Network Group, Inc. | US | suspicious |
2152 | keygen-step-6.exe | 85.214.154.106:443 | www.almanhost.com | Strato AG | DE | suspicious |
2152 | keygen-step-6.exe | 195.138.255.11:80 | crl.identrust.com | AS33891 Netzbetrieb GmbH | DE | whitelisted |
2152 | keygen-step-6.exe | 85.214.154.106:80 | www.almanhost.com | Strato AG | DE | suspicious |
2152 | keygen-step-6.exe | 195.138.255.18:80 | r3.o.lencr.org | AS33891 Netzbetrieb GmbH | DE | unknown |
3552 | GloryWSetp.exe | 104.21.42.63:443 | videoconvert-download38.xyz | Cloudflare Inc | US | suspicious |
2152 | keygen-step-6.exe | 23.45.105.185:80 | x1.c.lencr.org | Akamai International B.V. | NL | unknown |
2172 | 43A1.tmp.exe | 35.205.249.65:80 | — | Google Inc. | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.w7dslkipoja.com |
| suspicious |
kvaka.li |
| malicious |
iplogger.org |
| shared |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
ocsp.sectigo.com |
| whitelisted |
www.almanhost.com |
| suspicious |
crl.identrust.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2416 | keygen-step-1.exe | A Network Trojan was detected | ET TROJAN Win32/AZORult V3.3 Client Checkin M2 |
2416 | keygen-step-1.exe | A Network Trojan was detected | AV TROJAN Azorult CnC Beacon |
2152 | keygen-step-6.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2152 | keygen-step-6.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
2152 | keygen-step-6.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
2152 | keygen-step-6.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
2152 | keygen-step-6.exe | Potentially Bad Traffic | ET CURRENT_EVENTS Terse alphanumeric executable downloader high likelihood of being hostile |
2152 | keygen-step-6.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
2152 | keygen-step-6.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
2152 | keygen-step-6.exe | Potentially Bad Traffic | ET CURRENT_EVENTS Terse alphanumeric executable downloader high likelihood of being hostile |
103 ETPRO signatures available at the full report