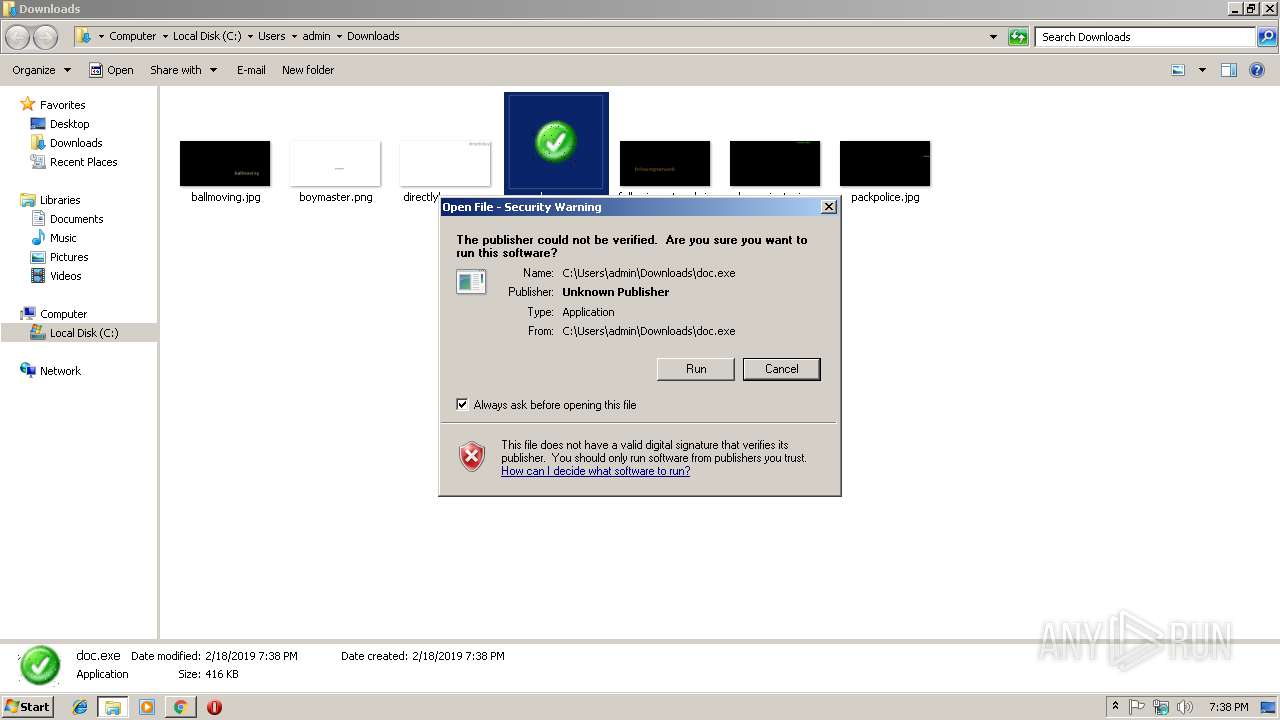
| URL: | https://109.169.89.4/doc/doc.exe |
| Full analysis: | https://app.any.run/tasks/eb9b4e2a-3c5d-4239-82f9-9f686a3826a5 |
| Verdict: | Malicious activity |
| Threats: | FormBook is a data stealer that is being distributed as a MaaS. FormBook differs from a lot of competing malware by its extreme ease of use that allows even the unexperienced threat actors to use FormBook virus. |
| Analysis date: | February 18, 2019, 19:37:58 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 8153FB3FDD2978002EF46F50FD4AFCF1 |
| SHA1: | F8387C20E6DCC49EE8ED922A8F46AD084D9E2BA9 |
| SHA256: | B668D8369CE0EA0CC51633837E7CC941C4AD0CFA3FBFAF630D34220E25E7232B |
| SSDEEP: | 3:N8+6KcpcQBK/n:2+6KcyUo |
MALICIOUS
Connects to CnC server
- explorer.exe (PID: 284)
- chrome.exe (PID: 3012)
Application was dropped or rewritten from another process
- doc.exe (PID: 3360)
Formbook was detected
- audiodg.exe (PID: 2604)
- Firefox.exe (PID: 2748)
Changes the autorun value in the registry
- audiodg.exe (PID: 2604)
FORMBOOK was detected
- explorer.exe (PID: 284)
- chrome.exe (PID: 3012)
Actions looks like stealing of personal data
- audiodg.exe (PID: 2604)
Stealing of credential data
- audiodg.exe (PID: 2604)
SUSPICIOUS
Reads Internet Cache Settings
- explorer.exe (PID: 284)
Executable content was dropped or overwritten
- chrome.exe (PID: 3012)
Creates files in the user directory
- explorer.exe (PID: 284)
- audiodg.exe (PID: 2604)
Starts CMD.EXE for commands execution
- audiodg.exe (PID: 2604)
Loads DLL from Mozilla Firefox
- audiodg.exe (PID: 2604)
INFO
Application launched itself
- chrome.exe (PID: 3012)
Reads Internet Cache Settings
- chrome.exe (PID: 3012)
Reads settings of System Certificates
- chrome.exe (PID: 3012)
Creates files in the user directory
- Firefox.exe (PID: 2748)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
49
Monitored processes
18
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 180 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=872,1327480604658831702,11706244389569366213,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=7B5A1FB9F795407E0F33BAF8D351B1BB --mojo-platform-channel-handle=940 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 284 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2336 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=872,1327480604658831702,11706244389569366213,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=82B850E60C024832ECEC2EE56EE1708B --mojo-platform-channel-handle=612 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2340 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=872,1327480604658831702,11706244389569366213,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=DC5FA8FF0C12210337EA6BCF02590ED2 --mojo-platform-channel-handle=512 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2356 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2420 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=872,1327480604658831702,11706244389569366213,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=958673DD3029EB97A84592E180A2FE2E --mojo-platform-channel-handle=4168 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2544 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=872,1327480604658831702,11706244389569366213,131072 --enable-features=PasswordImport --disable-gpu-sandbox --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=9BE1851EC617282BB5B4B870258A6CB6 --mojo-platform-channel-handle=3800 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2604 | "C:\Windows\System32\audiodg.exe" | C:\Windows\System32\audiodg.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Audio Device Graph Isolation Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2748 | "C:\Program Files\Mozilla Firefox\Firefox.exe" | C:\Program Files\Mozilla Firefox\Firefox.exe | audiodg.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 61.0.2 Modules
| |||||||||||||||
| 2772 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=872,1327480604658831702,11706244389569366213,131072 --enable-features=PasswordImport --service-pipe-token=9A0EAD4AFD8AFA7516EDF6E549A9802B --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=9A0EAD4AFD8AFA7516EDF6E549A9802B --renderer-client-id=4 --mojo-platform-channel-handle=1904 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
Total events
1 590
Read events
1 362
Write events
222
Delete events
6
Modification events
| (PID) Process: | (3012) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3012) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3012) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3012) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3012) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (3012) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3516-13180984670829101 |
Value: 0 | |||
| (PID) Process: | (3012) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (3012) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3012-13194992294422750 |
Value: 259 | |||
| (PID) Process: | (3012) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
| (PID) Process: | (3012) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete key | Name: | |
Value: | |||
Executable files
3
Suspicious files
102
Text files
67
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3012 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\74896489-90a2-4533-a088-639934155ff9.tmp | — | |
MD5:— | SHA256:— | |||
| 3012 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Download Service\EntryDB\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3012 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3012 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Download Service\EntryDB\CURRENT | — | |
MD5:— | SHA256:— | |||
| 3012 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\CURRENT | — | |
MD5:— | SHA256:— | |||
| 3012 | chrome.exe | C:\Users\admin\AppData\Local\Temp\TarEC0B.tmp | — | |
MD5:— | SHA256:— | |||
| 3012 | chrome.exe | C:\Users\admin\AppData\Local\Temp\CabEC3B.tmp | — | |
MD5:— | SHA256:— | |||
| 3012 | chrome.exe | C:\Users\admin\AppData\Local\Temp\TarEC3C.tmp | — | |
MD5:— | SHA256:— | |||
| 3012 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\25e72ec4-7ad8-4dc8-9716-d9d842daa8fe.tmp | — | |
MD5:— | SHA256:— | |||
| 3012 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
23
DNS requests
29
Threats
11
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
284 | explorer.exe | POST | — | 104.18.43.198:80 | http://www.elnaya.com/cu/ | US | — | — | malicious |
284 | explorer.exe | GET | 404 | 199.192.26.225:80 | http://www.ajexin.com/cu/?pPx=K2KdTxYP8t70tPH0&kfJH54=gIfzxdGTZmj5swk40qgcav/+Iepvt6J9UDmlsy/FwuYUMSVQW4jYvUpfC7kxB/y2bo2YoA== | US | html | 326 b | malicious |
284 | explorer.exe | POST | — | 104.18.43.198:80 | http://www.elnaya.com/cu/ | US | — | — | malicious |
3012 | chrome.exe | GET | 463 | 69.172.201.153:80 | http://www.lead.ltd/cu/?GFF=6lcL_rMXcny4&GV=SPEzm+gB9vVA5ZnYuksQVgaObP64hcqRwYjQenpcjBxbFbRzEaeuVnpg5FWw38KBWTB1zA==&sql=1 | US | html | 8.64 Kb | malicious |
3012 | chrome.exe | GET | 204 | 172.217.22.99:80 | http://www.gstatic.com/generate_204 | US | — | — | whitelisted |
284 | explorer.exe | GET | 301 | 104.18.43.198:80 | http://www.elnaya.com/cu/?kfJH54=LKtrWeOLNGwUoSd8q9Azw08Ci+jHYdG973oFZVYvpuPyHL66uLBQAzOdq9vgS9LMt1U/EQ==&pPx=K2KdTxYP8t70tPH0&sql=1 | US | html | 185 b | malicious |
284 | explorer.exe | POST | — | 104.18.43.198:80 | http://www.elnaya.com/cu/ | US | — | — | malicious |
3012 | chrome.exe | GET | 200 | 2.16.186.56:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | unknown | compressed | 55.2 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3012 | chrome.exe | 109.169.89.4:443 | — | iomart Cloud Services Limited. | GB | suspicious |
3012 | chrome.exe | 172.217.22.99:443 | www.gstatic.com | Google Inc. | US | whitelisted |
3012 | chrome.exe | 172.217.22.67:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
284 | explorer.exe | 104.18.43.198:80 | www.elnaya.com | Cloudflare Inc | US | shared |
284 | explorer.exe | 199.192.26.225:80 | www.ajexin.com | — | US | malicious |
3012 | chrome.exe | 172.217.22.10:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
3012 | chrome.exe | 69.172.201.153:80 | www.lead.ltd | Dosarrest Internet Security LTD | US | malicious |
3012 | chrome.exe | 216.58.210.14:443 | clients2.google.com | Google Inc. | US | whitelisted |
3012 | chrome.exe | 172.217.23.174:443 | safebrowsing.google.com | Google Inc. | US | whitelisted |
3012 | chrome.exe | 172.217.16.131:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
accounts.google.com |
| shared |
www.download.windowsupdate.com |
| whitelisted |
sb-ssl.google.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
safebrowsing.google.com |
| whitelisted |
clients2.google.com |
| whitelisted |
clients1.google.com |
| whitelisted |
www.ajexin.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
284 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (GET) |
284 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (GET) |
284 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] TrojanSpy:FormBook CnC Checkin (POST) |
284 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] TrojanSpy:FormBook CnC Checkin (POST) |
284 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (POST) |
3012 | chrome.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (GET) |
5 ETPRO signatures available at the full report