| File name: | dadb34bc38c683a7a0c4e54c884c037642a467cf |
| Full analysis: | https://app.any.run/tasks/bf69cf10-961b-4f61-9896-0f7c0beb826c |
| Verdict: | Malicious activity |
| Threats: | RedLine Stealer is a malicious program that collects users’ confidential data from browsers, systems, and installed software. It also infects operating systems with other malware. |
| Analysis date: | November 04, 2024, 14:50:24 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386, for MS Windows, 4 sections |
| MD5: | C66D251CC852604DCF9D8AC220DCB62E |
| SHA1: | DADB34BC38C683A7A0C4E54C884C037642A467CF |
| SHA256: | B64E617C9303D7B51BE90125D1DCEB5F0E2F00B058B662946DE1B1092130723F |
| SSDEEP: | 6144:snz/VT9u7VeAV5sUj67l90z/gJt3ze0lasT8MP04PgJHk51AzJR2k4/zYPBfly6a:snHufz4Jt9lasYMNIJHK1AzJ+YPTW |
MALICIOUS
REDLINE has been detected (YARA)
- vbc.exe (PID: 6676)
SUSPICIOUS
The process executes VB scripts
- dadb34bc38c683a7a0c4e54c884c037642a467cf.exe (PID: 1732)
Executes application which crashes
- dadb34bc38c683a7a0c4e54c884c037642a467cf.exe (PID: 1732)
Connects to unusual port
- vbc.exe (PID: 6676)
INFO
Checks supported languages
- vbc.exe (PID: 6676)
- dadb34bc38c683a7a0c4e54c884c037642a467cf.exe (PID: 1732)
Reads the machine GUID from the registry
- vbc.exe (PID: 6676)
Reads the computer name
- vbc.exe (PID: 6676)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
RedLine
(PID) Process(6676) vbc.exe
C2 (1)167.235.71.14:20469
BotnetGoogle2
Options
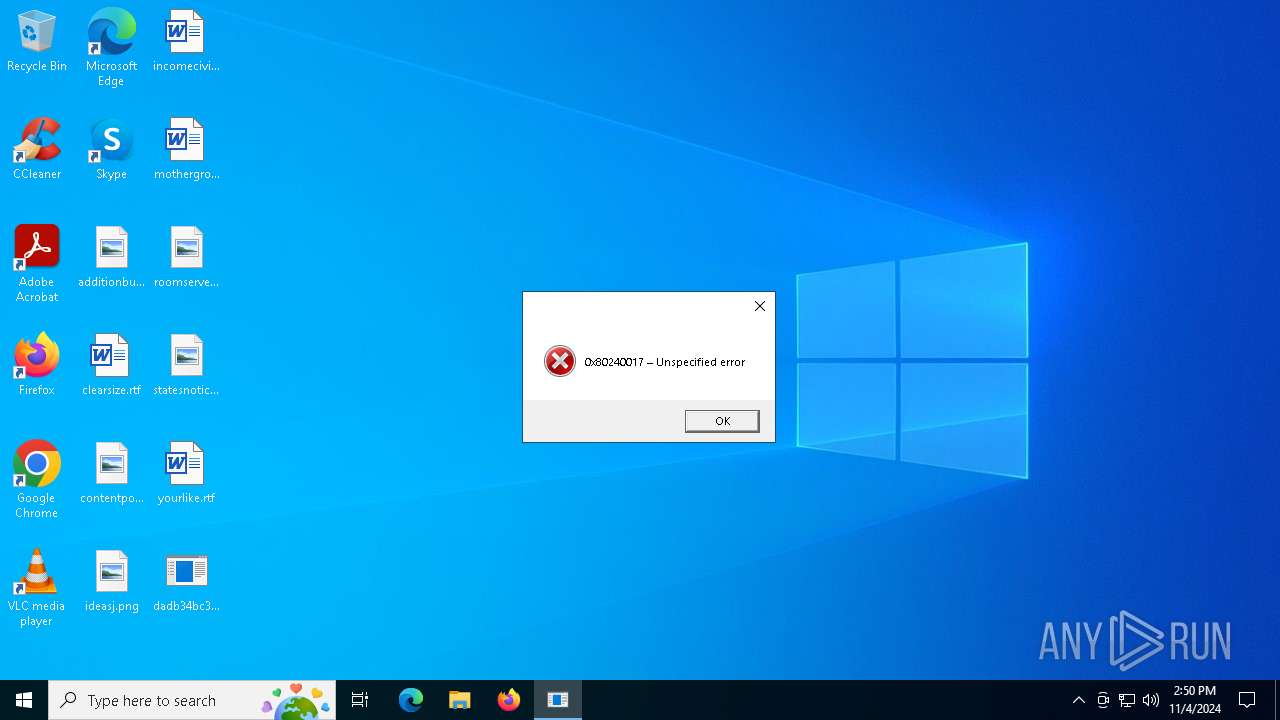
ErrorMessage0x80240017 – Unspecified error
Keys
XorDetents
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:11:10 04:00:11+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.32 |
| CodeSize: | 266240 |
| InitializedDataSize: | 198656 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1895 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
129
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1732 | "C:\Users\admin\Desktop\dadb34bc38c683a7a0c4e54c884c037642a467cf.exe" | C:\Users\admin\Desktop\dadb34bc38c683a7a0c4e54c884c037642a467cf.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225477 Modules
| |||||||||||||||
| 6132 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | dadb34bc38c683a7a0c4e54c884c037642a467cf.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6596 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 1732 -s 328 | C:\Windows\SysWOW64\WerFault.exe | dadb34bc38c683a7a0c4e54c884c037642a467cf.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6676 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\vbc.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\vbc.exe | dadb34bc38c683a7a0c4e54c884c037642a467cf.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual Basic Command Line Compiler Version: 14.8.9037.0 Modules
RedLine(PID) Process(6676) vbc.exe C2 (1)167.235.71.14:20469 BotnetGoogle2 Options ErrorMessage0x80240017 – Unspecified error Keys XorDetents | |||||||||||||||
Total events
8 126
Read events
8 126
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
2
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6596 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_dadb34bc38c683a7_cb1c1374a7641389a2d5595fbdbfe3b610394bc3_e86b5d2b_ac37ab10-49cf-4ba8-a26f-7eb2a99a3496\Report.wer | — | |
MD5:— | SHA256:— | |||
| 6596 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERC6A4.tmp.dmp | binary | |
MD5:34C0E5B6BD4288B6634D3D323D77F452 | SHA256:A613C0C0378E17C90979C5088864EDF2D65907E8A913321469E9230C60C4CACF | |||
| 6596 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERC713.tmp.WERInternalMetadata.xml | xml | |
MD5:19BC60945F6CC2B483EAE535ACD9BC67 | SHA256:B16F12CF673962D0E41513CFDA14E253A7C2CFFDC20C52E5A90E5B6586D3AA79 | |||
| 6596 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERC762.tmp.xml | xml | |
MD5:95D900917B800A5A8F9C5FFDC8E4A167 | SHA256:C5F3850342270719C4A3066B06B583018E92E9EDE26B2549B1AFCE8F80CC572E | |||
| 6596 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\dadb34bc38c683a7a0c4e54c884c037642a467cf.exe.1732.dmp | binary | |
MD5:1284E55AA1031F7A9F46703F4C2D8416 | SHA256:27801D32D5ED6C5BB21A3FD00FD88E80D61384F67AA96B5D6205C9375AC5F354 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
22
DNS requests
8
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6944 | svchost.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3396 | RUXIMICS.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 23.32.185.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3396 | RUXIMICS.exe | GET | 200 | 23.32.185.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3396 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6944 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6944 | svchost.exe | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
3396 | RUXIMICS.exe | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6596 | WerFault.exe | 20.42.73.29:443 | watson.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6944 | svchost.exe | 23.32.185.131:80 | www.microsoft.com | AKAMAI-AS | BR | whitelisted |
3396 | RUXIMICS.exe | 23.32.185.131:80 | www.microsoft.com | AKAMAI-AS | BR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
watson.events.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6676 | vbc.exe | Potentially Bad Traffic | ET INFO Microsoft net.tcp Connection Initialization Activity |
6676 | vbc.exe | Potentially Bad Traffic | ET INFO Microsoft net.tcp Connection Initialization Activity |