| URL: | https://github.com/ohsoft/brtb/blob/master/brtsvc_setup_sign.exe |
| Full analysis: | https://app.any.run/tasks/90b38cff-7880-4073-b310-b013712e2c27 |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | May 12, 2025, 06:49:52 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | C612133C152DAFC540526A869AE80DEA |
| SHA1: | EF24CA3E1031E0E86D40D2024813DCCCF91E99DB |
| SHA256: | B5EA00F908A285408C3EA2A547FDDAD07C8024FDBEB1EBA20026605DA74ECDC1 |
| SSDEEP: | 3:N8tEd6NWYsRKSEHMXRl+L2AC:2usNWh+M+C |
MALICIOUS
MINER has been detected (SURICATA)
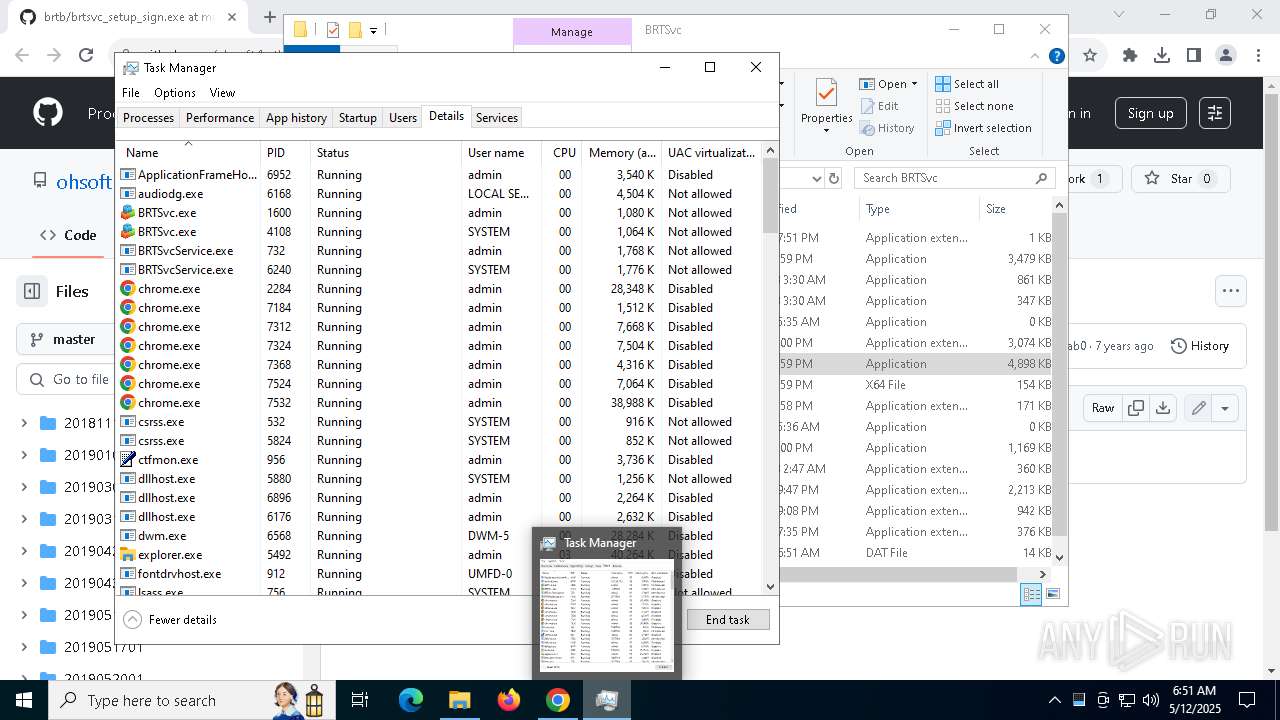
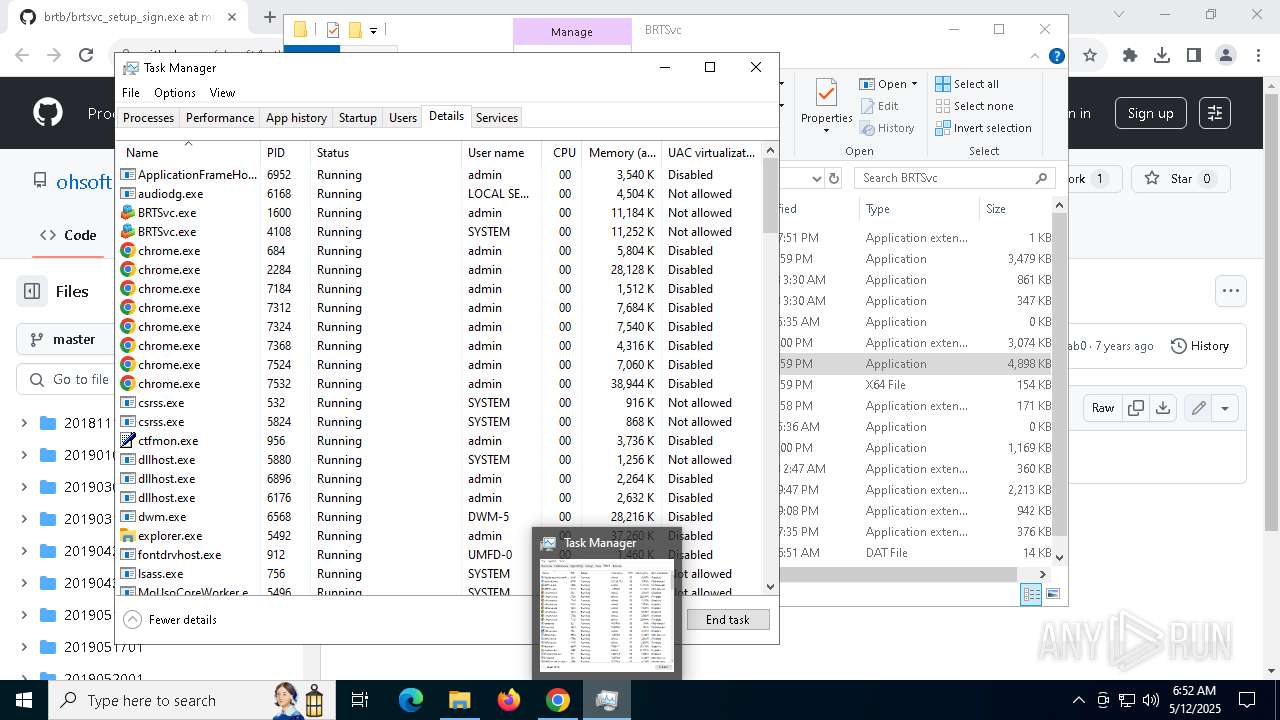
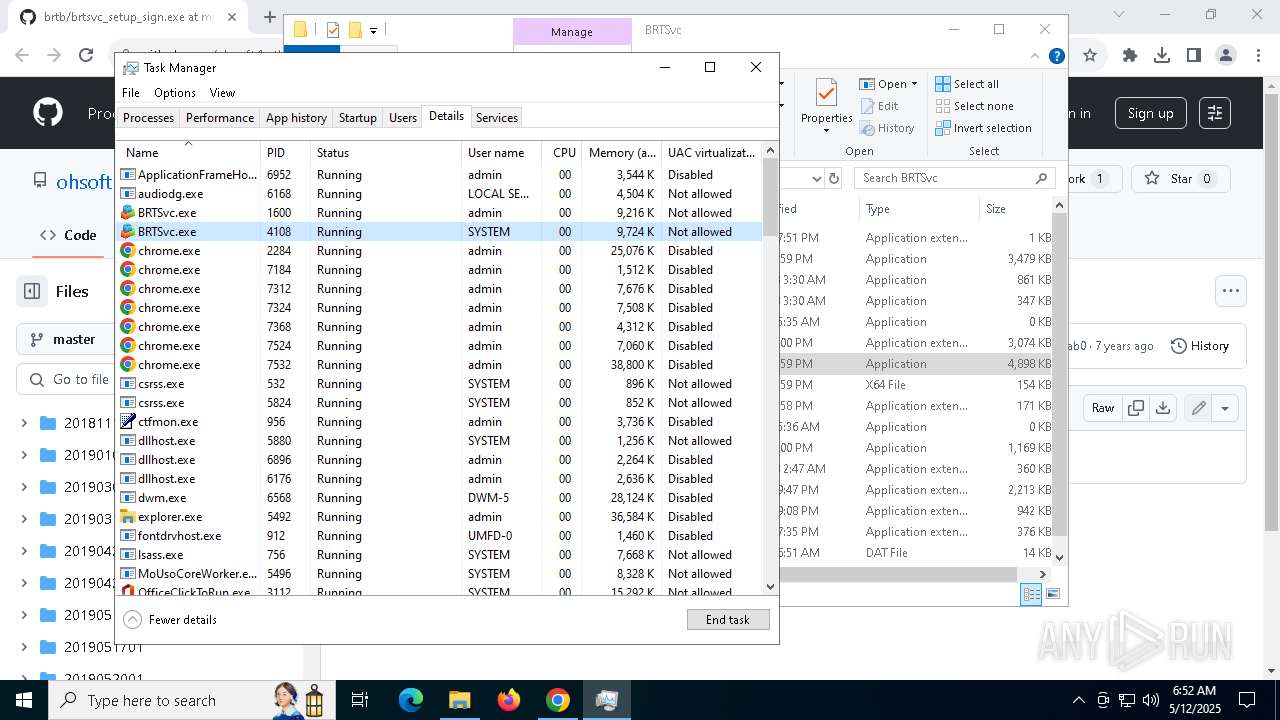
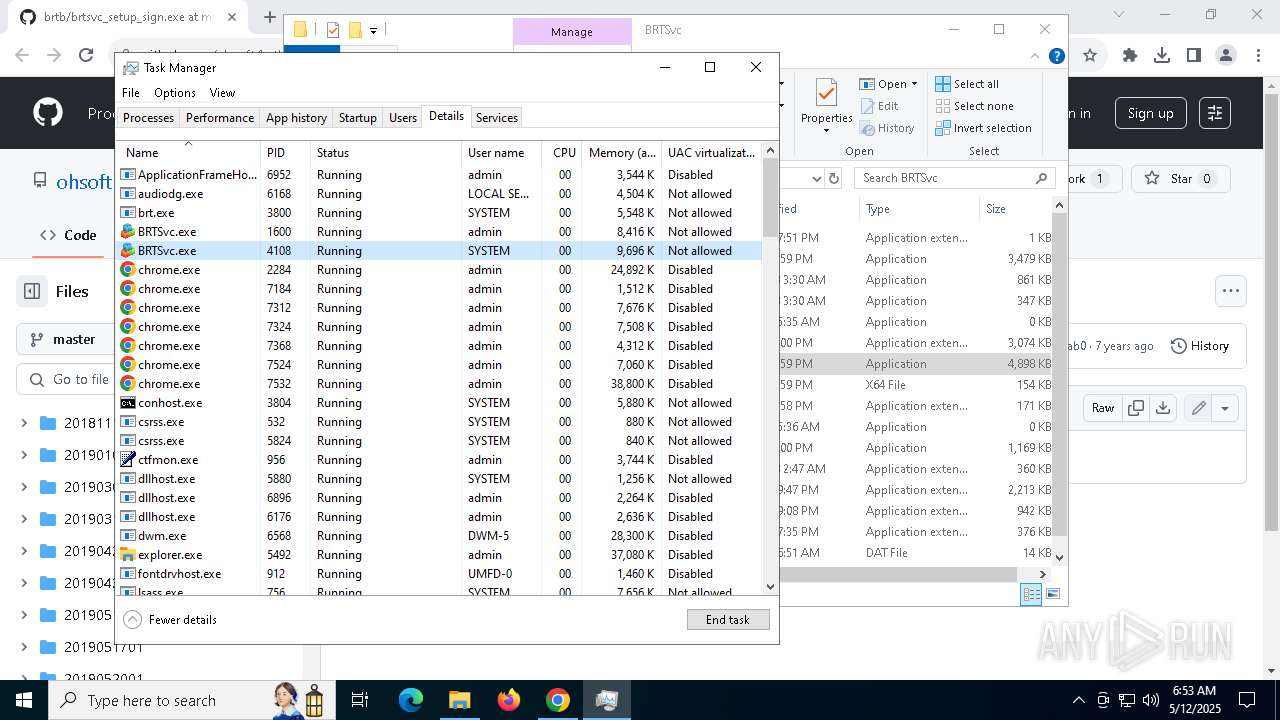
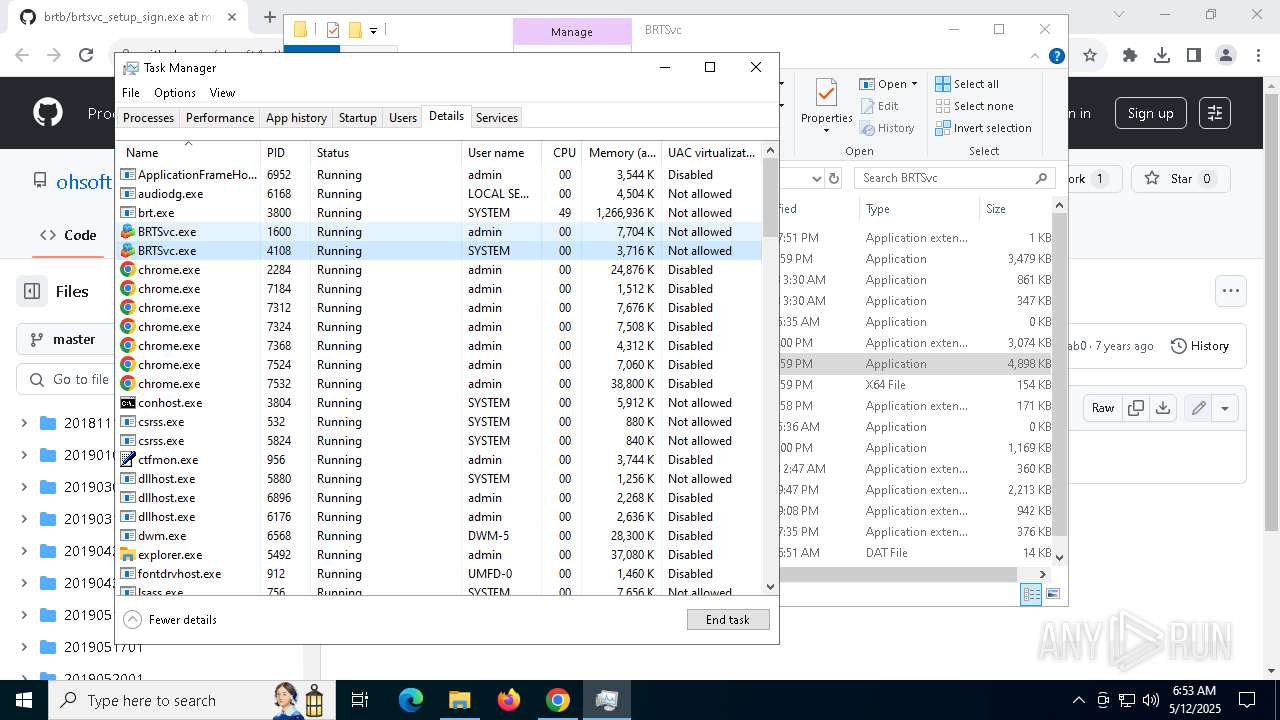
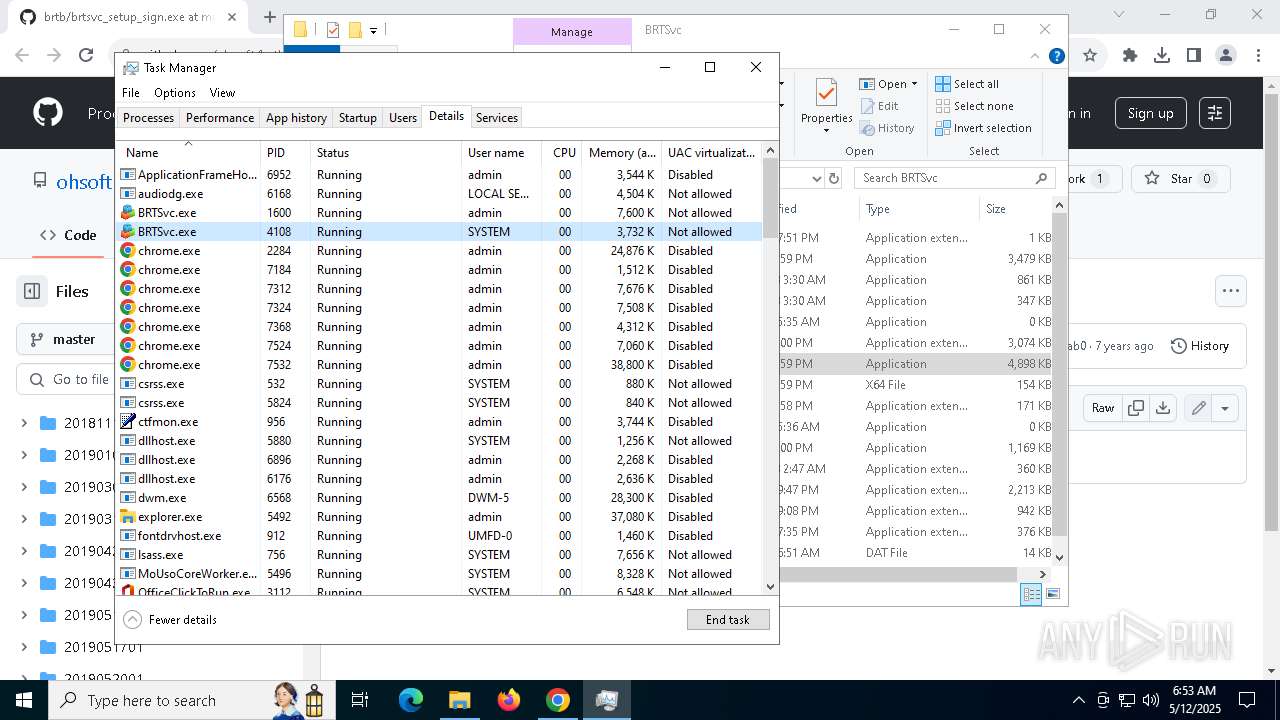
- brt.exe (PID: 6724)
- brt.exe (PID: 3800)
Connects to the CnC server
- brt.exe (PID: 6724)
- brt.exe (PID: 3800)
SUSPICIOUS
Executable content was dropped or overwritten
- brtsvc_setup_sign.exe (PID: 8064)
- brtsvc_setup_sign.tmp (PID: 8176)
- brtsvc_setup_sign.exe (PID: 4268)
- tmp3A81.tmp.tmp (PID: 7640)
- tmp3A81.tmp.exe (PID: 6208)
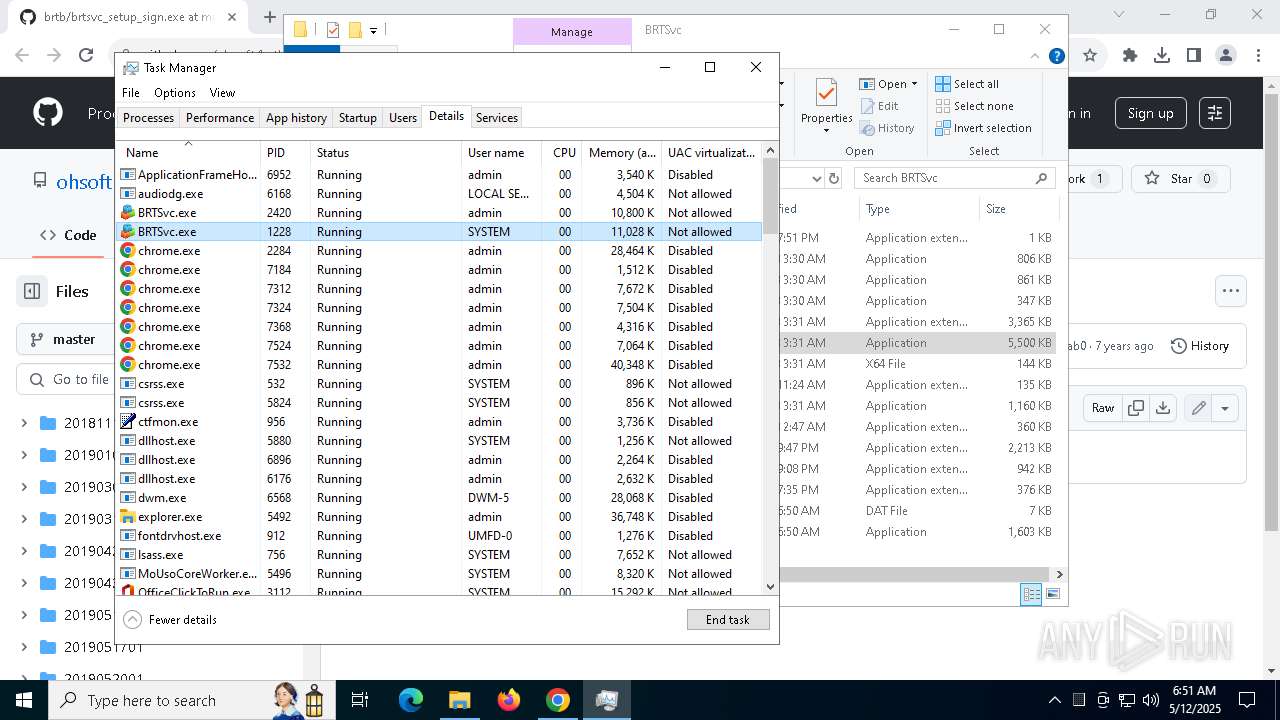
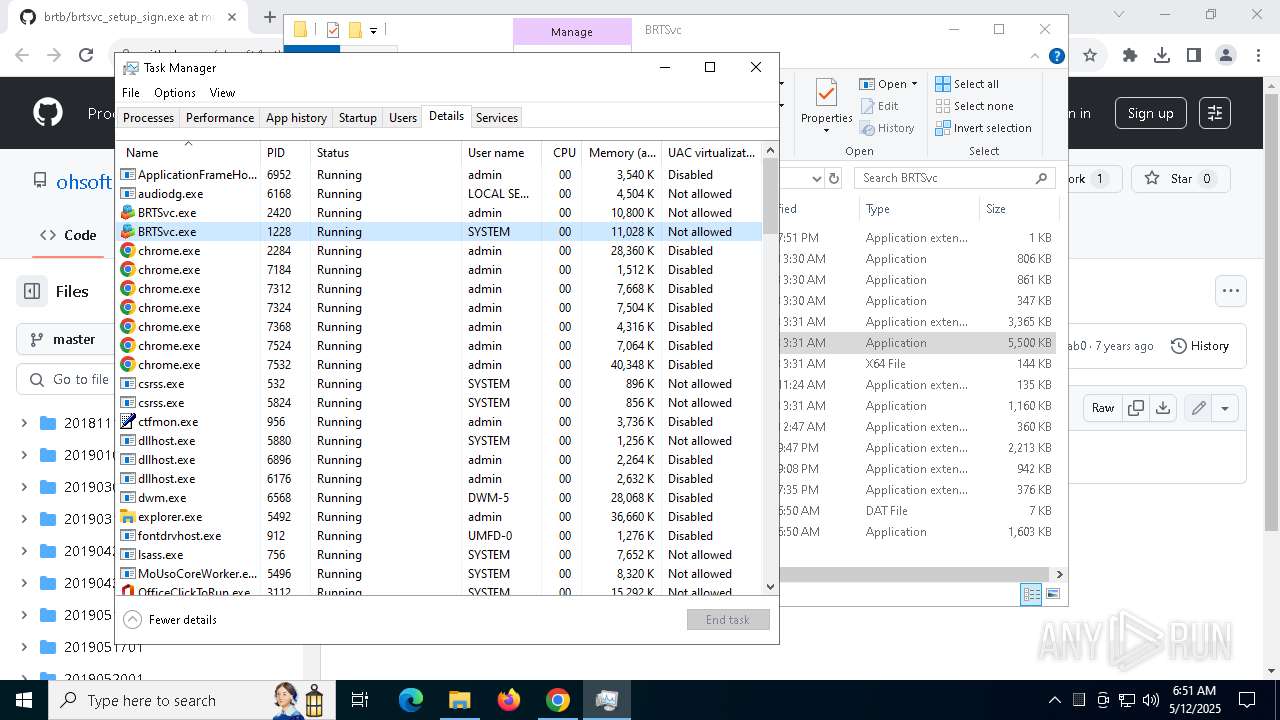
- BRTSvc.exe (PID: 1228)
Reads security settings of Internet Explorer
- brtsvc_setup_sign.tmp (PID: 8028)
Reads the Windows owner or organization settings
- brtsvc_setup_sign.tmp (PID: 8176)
Reads the BIOS version
- BRTSvc.exe (PID: 7264)
- BRTSvc.exe (PID: 7932)
- BRTSvc.exe (PID: 2504)
- BRTSvc.exe (PID: 1228)
- BRTSvc.exe (PID: 2420)
Reads the date of Windows installation
- BRTSvc.exe (PID: 7932)
- BRTSvc.exe (PID: 7264)
- BRTSvc.exe (PID: 2504)
- BRTSvc.exe (PID: 2420)
- BRTSvc.exe (PID: 1228)
Process drops legitimate windows executable
- brtsvc_setup_sign.tmp (PID: 8176)
The process drops C-runtime libraries
- brtsvc_setup_sign.tmp (PID: 8176)
The process executes via Task Scheduler
- BRTSvc.exe (PID: 2420)
- BRTSvc.exe (PID: 1228)
- BRTSvc.exe (PID: 1600)
- BRTSvc.exe (PID: 4108)
The process checks if it is being run in the virtual environment
- BRTSvc.exe (PID: 2420)
- BRTSvc.exe (PID: 1228)
There is functionality for communication over UDP network (YARA)
- BRTSvc.exe (PID: 2420)
- BRTSvc.exe (PID: 1228)
There is functionality for taking screenshot (YARA)
- BRTSvc.exe (PID: 2420)
- BRTSvc.exe (PID: 1228)
- BRTSvc.exe (PID: 4108)
- BRTSvc.exe (PID: 1600)
Potential Corporate Privacy Violation
- brt.exe (PID: 6724)
- brt.exe (PID: 3800)
INFO
Manual execution by a user
- brtsvc_setup_sign.exe (PID: 8064)
- Taskmgr.exe (PID: 2772)
- BRTSvc.exe (PID: 7540)
- Taskmgr.exe (PID: 4448)
Executable content was dropped or overwritten
- chrome.exe (PID: 2284)
Create files in a temporary directory
- brtsvc_setup_sign.exe (PID: 8064)
- brtsvc_setup_sign.exe (PID: 4268)
- brtsvc_setup_sign.tmp (PID: 8176)
Checks supported languages
- brtsvc_setup_sign.exe (PID: 8064)
- brtsvc_setup_sign.tmp (PID: 8028)
- brtsvc_setup_sign.exe (PID: 4268)
- brtsvc_setup_sign.tmp (PID: 8176)
- BRTSvc.exe (PID: 7264)
- BRTSvcHelper.exe (PID: 8184)
- BRTSvc.exe (PID: 7932)
- BRTSvcHelper.exe (PID: 4996)
- BRTSvc.exe (PID: 2420)
- BRTSvc.exe (PID: 2504)
- BRTSvc.exe (PID: 1228)
- BRTSvcHelper.exe (PID: 3008)
- BRTSvcHelper.exe (PID: 5436)
- BRTSvcHelper.exe (PID: 6988)
Reads the computer name
- brtsvc_setup_sign.tmp (PID: 8028)
- brtsvc_setup_sign.tmp (PID: 8176)
- BRTSvc.exe (PID: 7264)
- BRTSvc.exe (PID: 2504)
- BRTSvc.exe (PID: 2420)
- BRTSvc.exe (PID: 1228)
- BRTSvc.exe (PID: 7932)
Application launched itself
- chrome.exe (PID: 2284)
Process checks computer location settings
- brtsvc_setup_sign.tmp (PID: 8028)
The sample compiled with english language support
- brtsvc_setup_sign.tmp (PID: 8176)
- tmp3A81.tmp.tmp (PID: 7640)
Reads Environment values
- BRTSvc.exe (PID: 7264)
- BRTSvc.exe (PID: 7932)
- BRTSvc.exe (PID: 2504)
- BRTSvc.exe (PID: 2420)
- BRTSvc.exe (PID: 1228)
Creates files in the program directory
- brtsvc_setup_sign.tmp (PID: 8176)
Reads product name
- BRTSvc.exe (PID: 7264)
- BRTSvc.exe (PID: 7932)
- BRTSvc.exe (PID: 2504)
- BRTSvc.exe (PID: 2420)
- BRTSvc.exe (PID: 1228)
Creates a software uninstall entry
- brtsvc_setup_sign.tmp (PID: 8176)
Compiled with Borland Delphi (YARA)
- BRTSvc.exe (PID: 2420)
- BRTSvc.exe (PID: 1228)
- BRTSvc.exe (PID: 4108)
- BRTSvc.exe (PID: 1600)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
199
Monitored processes
54
Malicious processes
10
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 684 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --disable-gpu-sandbox --use-gl=disabled --gpu-vendor-id=5140 --gpu-device-id=140 --gpu-sub-system-id=0 --gpu-revision=0 --gpu-driver-version=10.0.19041.3636 --no-appcompat-clear --gpu-preferences=WAAAAAAAAADoABAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAABEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=4676 --field-trial-handle=1916,i,6063272698836028771,8460223169374365998,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 732 | "C:\Program Files (x86)\BRTSvc\BRTSvcService.exe" /run:ia 1600 | C:\Program Files (x86)\BRTSvc\BRTSvcService.exe | — | BRTSvc.exe | |||||||||||
User: admin Company: oort - ASProtect 64 (License for a firm or a company) Integrity Level: HIGH Description: User Interface Application Exit code: 0 Version: 5.70.025.110 Modules
| |||||||||||||||
| 976 | "C:\Windows\Temp\is-THQ5J.tmp\BRTSvcService.exe" /run:ia 2416 | C:\Windows\Temp\is-THQ5J.tmp\BRTSvcService.exe | — | BRTSvc.exe | |||||||||||
User: SYSTEM Company: oort - ASProtect 64 (License for a firm or a company) Integrity Level: SYSTEM Description: User Interface Application Exit code: 0 Version: 5.70.025.110 Modules
| |||||||||||||||
| 1228 | "C:\Program Files (x86)\BRTSvc\BRTSvc.exe" /Run | C:\Program Files (x86)\BRTSvc\BRTSvc.exe | svchost.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1600 | "C:\Program Files (x86)\BRTSvc\BRTSvc.exe" /Run | C:\Program Files (x86)\BRTSvc\BRTSvc.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: HIGH Version: 1.0.0.0 Modules
| |||||||||||||||
| 1912 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2088 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=4452 --field-trial-handle=1916,i,6063272698836028771,8460223169374365998,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2284 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --disk-cache-dir=null --disk-cache-size=1 --media-cache-size=1 --disable-gpu-shader-disk-cache --disable-background-networking --disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints "https://github.com/ohsoft/brtb/blob/master/brtsvc_setup_sign.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2416 | "C:\WINDOWS\TEMP\is-THQ5J.tmp\BRTSvc.exe" "/ExitApp:C:\Program Files (x86)\BRTSvc" | C:\Windows\Temp\is-THQ5J.tmp\BRTSvc.exe | — | tmp3A81.tmp.tmp | |||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2420 | "C:\Program Files (x86)\BRTSvc\BRTSvc.exe" /Run | C:\Program Files (x86)\BRTSvc\BRTSvc.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
54 869
Read events
54 792
Write events
68
Delete events
9
Modification events
| (PID) Process: | (2284) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2284) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2284) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2284) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (2284) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (2088) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 010000000000000063A0ED1C0AC3DB01 | |||
| (PID) Process: | (8176) brtsvc_setup_sign.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\BRTSvc_is1 |
| Operation: | write | Name: | NoModify |
Value: 1 | |||
| (PID) Process: | (8176) brtsvc_setup_sign.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\BRTSvc_is1 |
| Operation: | write | Name: | NoRepair |
Value: 1 | |||
| (PID) Process: | (8176) brtsvc_setup_sign.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\BRTSvc_is1 |
| Operation: | write | Name: | InstallDate |
Value: 20250512 | |||
| (PID) Process: | (8176) brtsvc_setup_sign.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\BRTSvc_is1 |
| Operation: | write | Name: | MajorVersion |
Value: 1 | |||
Executable files
67
Suspicious files
134
Text files
33
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2284 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF10c536.TMP | — | |
MD5:— | SHA256:— | |||
| 2284 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2284 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RF10c536.TMP | — | |
MD5:— | SHA256:— | |||
| 2284 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2284 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF10c546.TMP | — | |
MD5:— | SHA256:— | |||
| 2284 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2284 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF10c546.TMP | — | |
MD5:— | SHA256:— | |||
| 2284 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2284 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF10c546.TMP | — | |
MD5:— | SHA256:— | |||
| 2284 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
74
DNS requests
62
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.164.106:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
8108 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
8108 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7144 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYjhkYWYwZDctOTExOS00MGQ5LTgyNjAtN2FlY2ZjMDg0NmNj/1.0.0.17_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | unknown | — | — | whitelisted |
7144 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYjhkYWYwZDctOTExOS00MGQ5LTgyNjAtN2FlY2ZjMDg0NmNj/1.0.0.17_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.164.106:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7324 | chrome.exe | 140.82.121.3:443 | github.com | GITHUB | US | whitelisted |
2284 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
7324 | chrome.exe | 173.194.76.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
7324 | chrome.exe | 185.199.111.154:443 | github.githubassets.com | FASTLY | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
github.com |
| whitelisted |
accounts.google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
github.githubassets.com |
| whitelisted |
avatars.githubusercontent.com |
| whitelisted |
user-images.githubusercontent.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7324 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
7324 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
6724 | brt.exe | Potential Corporate Privacy Violation | ET INFO Cryptocurrency Miner Checkin M2 |
3800 | brt.exe | Potential Corporate Privacy Violation | ET INFO Cryptocurrency Miner Checkin M2 |
Process | Message |
|---|---|
BRTSvc.exe | [5/12/2025 6:50:32 AM][PID:1228][SessionID:0]Session 0 start |
BRTSvc.exe | [5/12/2025 6:50:32 AM][PID:1228][SessionID:0]Start app |
BRTSvc.exe | [5/12/2025 6:50:32 AM][PID:1228][SessionID:0]ActiveSession state: WTSActive |
BRTSvc.exe | [5/12/2025 6:50:33 AM][PID:1228][SessionID:0]ActiveSession state: WTSActive |
BRTSvc.exe | [5/12/2025 6:50:34 AM][PID:1228][SessionID:0]ActiveSession state: WTSActive |
BRTSvc.exe | [5/12/2025 6:50:35 AM][PID:1228][SessionID:0]ActiveSession state: WTSActive |
BRTSvc.exe | [5/12/2025 6:50:36 AM][PID:1228][SessionID:0]ActiveSession state: WTSActive |
BRTSvc.exe | [5/12/2025 6:50:37 AM][PID:1228][SessionID:0]ActiveSession state: WTSActive |
BRTSvc.exe | [5/12/2025 6:50:38 AM][PID:1228][SessionID:0]ActiveSession state: WTSActive |
BRTSvc.exe | [5/12/2025 6:50:39 AM][PID:1228][SessionID:0]ActiveSession state: WTSActive |