| URL: | https://mega.nz/file/KW5z3RxR#VK12T22AyB3Y1Y9-wZ9JkcuhR_KFjRR2yJg_SEdcW2E?uel=file.zip |
| Full analysis: | https://app.any.run/tasks/be7f3105-fa36-417c-b4cc-780412134489 |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | December 14, 2023, 07:49:03 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 007E2A08CB5CAEE709CE96064AF73426 |
| SHA1: | 2441E3B8F87D45E10F8CDFDE7F129C5AA543F747 |
| SHA256: | B58C2E5598A568D84C591D5EEA97E4DB21DE36246F85C10D4F0E026567F866C8 |
| SSDEEP: | 3:N8X/irg2CUXxEcQaS/RGQl6usH3fQAMYV:2ig2CUXYB36usvQ3YV |
MALICIOUS
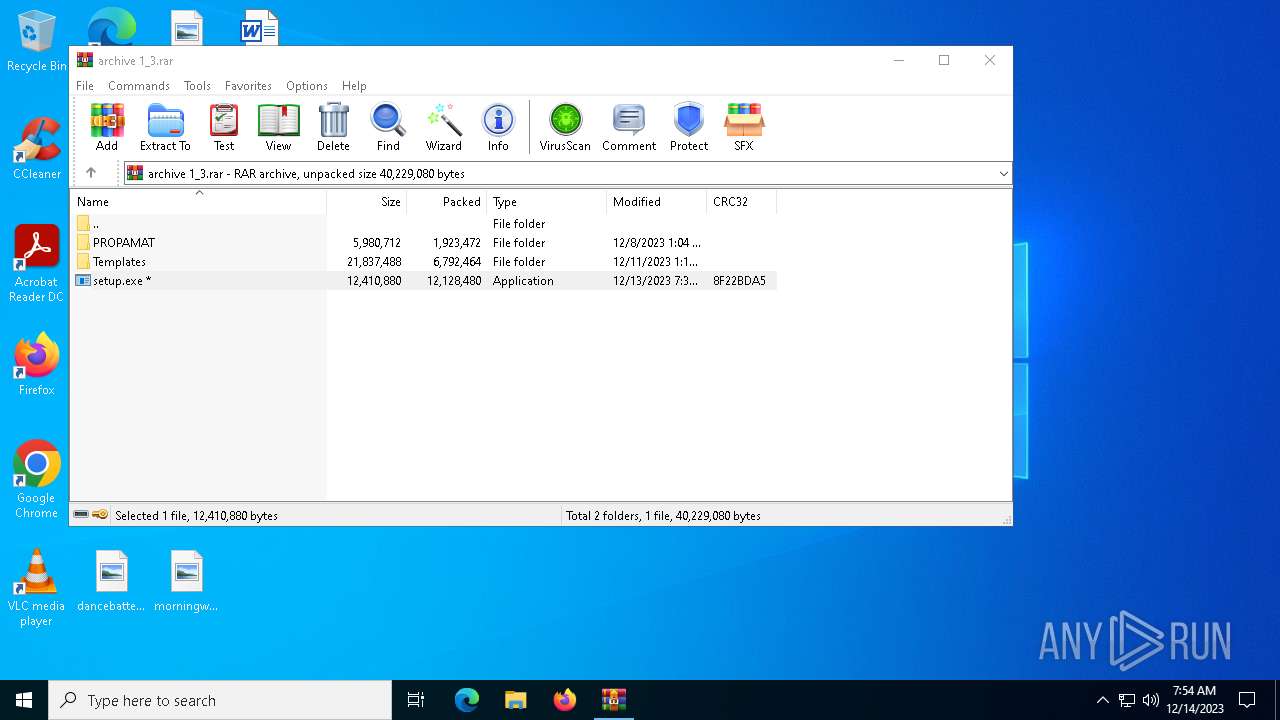
Drops the executable file immediately after the start
- setup.exe (PID: 7096)
- setup.exe (PID: 2116)
- WW13_64.exe (PID: 4508)
- R9xjSNTSHQc5MeswF4lWjJ5r.exe (PID: 6148)
- sHt80OJEDP7kj8X5QS49OXo9.exe (PID: 5964)
- uO3Nuz5ET3PKxtPnAXeI4Rex.exe (PID: 4320)
- sHt80OJEDP7kj8X5QS49OXo9.tmp (PID: 6360)
- DTPanelQT.exe (PID: 7368)
- mDhAmrjuJ0RbtfDpFce1HKra.exe (PID: 7912)
- zieHLA8NQI852wSb4lC7UHP2.exe (PID: 7836)
- 7nsBhSw3KD_7P95n7b_NuX9p.exe (PID: 7816)
- aGwqlXg4MsSR82Qts0Wn9hrw.exe (PID: 7376)
- IBAKBWA1bGabG21m0w3Vytqc.exe (PID: 7652)
- 5yJ27pEysT6fJzdq6LJ09com.exe (PID: 2856)
- LGm3L21BXa.exe (PID: 1452)
- DqT7nYPunqBMkuRLL7edn9lt.exe (PID: 1084)
- vQ6DLHi3GC4EYXblv6AP2N2V.exe (PID: 6044)
- updater.exe (PID: 2608)
- LGm3L21BXa.tmp (PID: 3860)
Connects to the CnC server
- WW13_64.exe (PID: 6504)
- WW13_64.exe (PID: 4508)
- ZzPTu52Dp3p6gXRktdO1e23F.exe (PID: 880)
- 㡮癄稵䔶坮确䑺捺㍢ (PID: 7216)
- jveESZmOmFEXAAXKAFgccWxe.exe (PID: 8168)
- IBAKBWA1bGabG21m0w3Vytqc.exe (PID: 7652)
- explorer.exe (PID: 4428)
- RegSvcs.exe (PID: 7896)
- explorer.exe (PID: 6432)
- explorer.exe (PID: 7784)
- Nrpb1aPFZTZwcMYNO3f044Q6.exe (PID: 7696)
- DTPanelQT.exe (PID: 7492)
PRIVATELOADER has been detected (SURICATA)
- WW13_64.exe (PID: 6504)
- WW13_64.exe (PID: 4508)
- IBAKBWA1bGabG21m0w3Vytqc.exe (PID: 7652)
- Nrpb1aPFZTZwcMYNO3f044Q6.exe (PID: 7696)
Actions looks like stealing of personal data
- WW13_64.exe (PID: 4508)
- jveESZmOmFEXAAXKAFgccWxe.exe (PID: 8168)
- 㡮癄稵䔶坮确䑺捺㍢ (PID: 7216)
- IBAKBWA1bGabG21m0w3Vytqc.exe (PID: 7652)
- RegSvcs.exe (PID: 7896)
- Nrpb1aPFZTZwcMYNO3f044Q6.exe (PID: 7696)
- explorer.exe (PID: 6432)
STEALC has been detected (SURICATA)
- ZzPTu52Dp3p6gXRktdO1e23F.exe (PID: 880)
Runs injected code in another process
- KiJ3hN2hayADiMWAVzxMucME.exe (PID: 1416)
Application was injected by another process
- explorer.exe (PID: 4428)
Create files in the Startup directory
- uO3Nuz5ET3PKxtPnAXeI4Rex.exe (PID: 4320)
- mDhAmrjuJ0RbtfDpFce1HKra.exe (PID: 7912)
- 7nsBhSw3KD_7P95n7b_NuX9p.exe (PID: 7816)
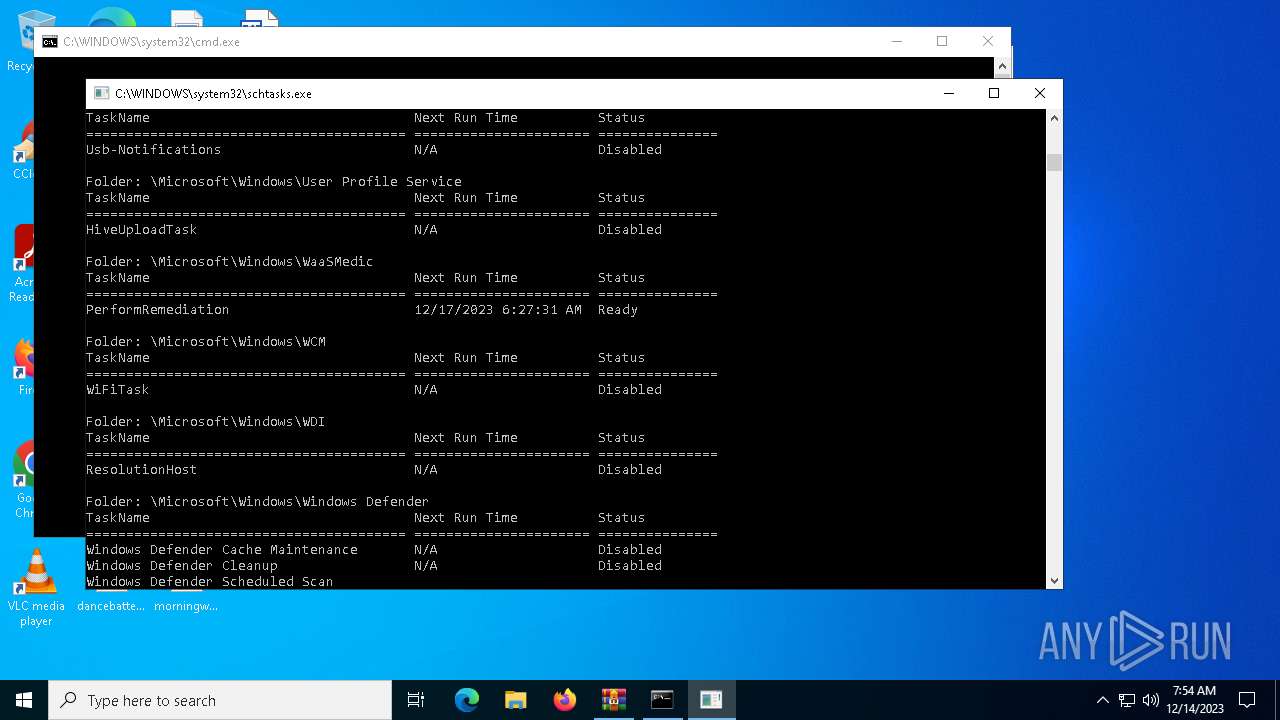
Uses Task Scheduler to run other applications
- uO3Nuz5ET3PKxtPnAXeI4Rex.exe (PID: 4320)
- sHt80OJEDP7kj8X5QS49OXo9.tmp (PID: 6360)
- mDhAmrjuJ0RbtfDpFce1HKra.exe (PID: 7912)
- 7nsBhSw3KD_7P95n7b_NuX9p.exe (PID: 7816)
- lV3SG2WiNRxQz1eD7GGPcp15.exe (PID: 3952)
- explorer.exe (PID: 4428)
Creates a writable file in the system directory
- uO3Nuz5ET3PKxtPnAXeI4Rex.exe (PID: 4320)
- powershell.exe (PID: 5796)
Uses Task Scheduler to autorun other applications
- uO3Nuz5ET3PKxtPnAXeI4Rex.exe (PID: 4320)
- mDhAmrjuJ0RbtfDpFce1HKra.exe (PID: 7912)
- 7nsBhSw3KD_7P95n7b_NuX9p.exe (PID: 7816)
LUMMA has been detected (SURICATA)
- 㡮癄稵䔶坮确䑺捺㍢ (PID: 7216)
- jveESZmOmFEXAAXKAFgccWxe.exe (PID: 8168)
- RegSvcs.exe (PID: 7896)
SMOKE has been detected (SURICATA)
- explorer.exe (PID: 4428)
- explorer.exe (PID: 6432)
- explorer.exe (PID: 7784)
Steals credentials from Web Browsers
- explorer.exe (PID: 6432)
Unusual connection from system programs
- explorer.exe (PID: 6432)
Changes the autorun value in the registry
- lV3SG2WiNRxQz1eD7GGPcp15.exe (PID: 3952)
AMADEY has been detected (SURICATA)
- lV3SG2WiNRxQz1eD7GGPcp15.exe (PID: 3952)
Modifies files in the Chrome extension folder
- Nrpb1aPFZTZwcMYNO3f044Q6.exe (PID: 7696)
Adds path to the Windows Defender exclusion list
- explorer.exe (PID: 4428)
Stop is detected
- 5yJ27pEysT6fJzdq6LJ09com.exe (PID: 4504)
Starts CMD.EXE for self-deleting
- DqT7nYPunqBMkuRLL7edn9lt.exe (PID: 1084)
RISEPRO has been detected (YARA)
- uO3Nuz5ET3PKxtPnAXeI4Rex.exe (PID: 4320)
- mDhAmrjuJ0RbtfDpFce1HKra.exe (PID: 7912)
REDLINE has been detected (YARA)
- AppLaunch.exe (PID: 3368)
SOCKS5SYSTEMZ has been detected (SURICATA)
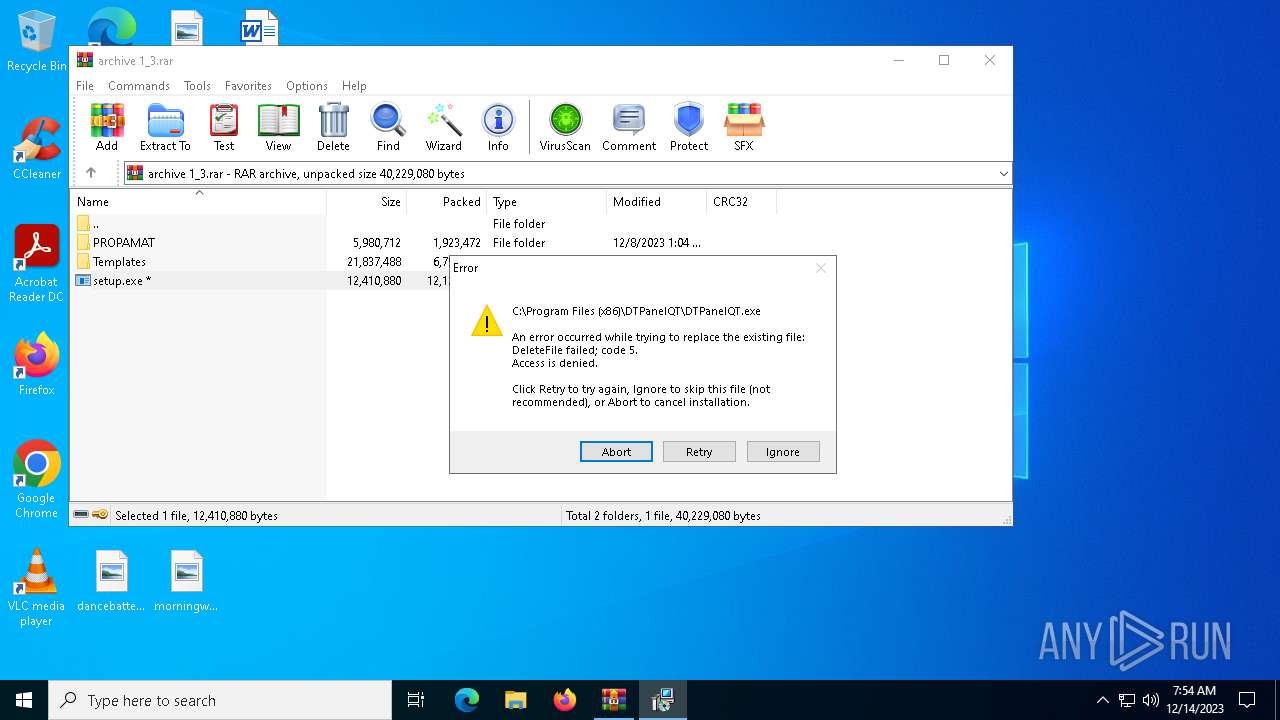
- DTPanelQT.exe (PID: 7492)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 4880)
- setup.exe (PID: 7096)
- setup.exe (PID: 2116)
- sHt80OJEDP7kj8X5QS49OXo9.tmp (PID: 6360)
- zieHLA8NQI852wSb4lC7UHP2.exe (PID: 7836)
- LGm3L21BXa.tmp (PID: 3860)
The process drops C-runtime libraries
- setup.exe (PID: 7096)
- setup.exe (PID: 2116)
Loads Python modules
- WW13_64.exe (PID: 6504)
- WW13_64.exe (PID: 4508)
Connects to the server without a host name
- WW13_64.exe (PID: 6504)
- WW13_64.exe (PID: 4508)
- ZzPTu52Dp3p6gXRktdO1e23F.exe (PID: 880)
- IBAKBWA1bGabG21m0w3Vytqc.exe (PID: 7652)
- Nrpb1aPFZTZwcMYNO3f044Q6.exe (PID: 7696)
- lV3SG2WiNRxQz1eD7GGPcp15.exe (PID: 3952)
- DqT7nYPunqBMkuRLL7edn9lt.exe (PID: 1084)
Checks for external IP
- WW13_64.exe (PID: 4508)
- IBAKBWA1bGabG21m0w3Vytqc.exe (PID: 7652)
- Nrpb1aPFZTZwcMYNO3f044Q6.exe (PID: 7696)
Process requests binary or script from the Internet
- WW13_64.exe (PID: 4508)
Starts CMD.EXE for commands execution
- WW13_64.exe (PID: 4508)
- R9xjSNTSHQc5MeswF4lWjJ5r.exe (PID: 6148)
- explorer.exe (PID: 4428)
- DqT7nYPunqBMkuRLL7edn9lt.exe (PID: 1084)
Executes application which crashes
- KKEb5KiRt4h8VfeXgS2GBXIS.exe (PID: 896)
- ZzPTu52Dp3p6gXRktdO1e23F.exe (PID: 880)
- DqT7nYPunqBMkuRLL7edn9lt.exe (PID: 1084)
Drops 7-zip archiver for unpacking
- WW13_64.exe (PID: 4508)
- sHt80OJEDP7kj8X5QS49OXo9.tmp (PID: 6360)
- LGm3L21BXa.tmp (PID: 3860)
Reads the date of Windows installation
- R9xjSNTSHQc5MeswF4lWjJ5r.exe (PID: 6148)
- lV3SG2WiNRxQz1eD7GGPcp15.exe (PID: 3952)
- Nrpb1aPFZTZwcMYNO3f044Q6.exe (PID: 7696)
- 5yJ27pEysT6fJzdq6LJ09com.exe (PID: 2856)
- DqT7nYPunqBMkuRLL7edn9lt.exe (PID: 1084)
Executing commands from a ".bat" file
- R9xjSNTSHQc5MeswF4lWjJ5r.exe (PID: 6148)
Application launched itself
- 5yJ27pEysT6fJzdq6LJ09com.exe (PID: 6696)
- jveESZmOmFEXAAXKAFgccWxe.exe (PID: 7692)
- explorer.exe (PID: 4428)
- 5yJ27pEysT6fJzdq6LJ09com.exe (PID: 2856)
- 5yJ27pEysT6fJzdq6LJ09com.exe (PID: 3112)
Reads the Windows owner or organization settings
- sHt80OJEDP7kj8X5QS49OXo9.tmp (PID: 6360)
- LGm3L21BXa.tmp (PID: 3860)
Checks Windows Trust Settings
- 5yJ27pEysT6fJzdq6LJ09com.exe (PID: 2856)
- IBAKBWA1bGabG21m0w3Vytqc.exe (PID: 7652)
- 5yJ27pEysT6fJzdq6LJ09com.exe (PID: 4504)
- Nrpb1aPFZTZwcMYNO3f044Q6.exe (PID: 7696)
Reads security settings of Internet Explorer
- 5yJ27pEysT6fJzdq6LJ09com.exe (PID: 2856)
- IBAKBWA1bGabG21m0w3Vytqc.exe (PID: 7652)
- Nrpb1aPFZTZwcMYNO3f044Q6.exe (PID: 7696)
- 5yJ27pEysT6fJzdq6LJ09com.exe (PID: 4504)
Process drops SQLite DLL files
- sHt80OJEDP7kj8X5QS49OXo9.tmp (PID: 6360)
- LGm3L21BXa.tmp (PID: 3860)
The process checks if it is being run in the virtual environment
- rundll32.exe (PID: 5908)
- rundll32.exe (PID: 2764)
Connects to unusual port
- uO3Nuz5ET3PKxtPnAXeI4Rex.exe (PID: 4320)
- 1b87UN0D0yUAptLOc31oMQiH.exe (PID: 6712)
- Bn3Y5V0xUss2ym9T68bDhTaG.exe (PID: 6176)
- mDhAmrjuJ0RbtfDpFce1HKra.exe (PID: 7912)
- 7nsBhSw3KD_7P95n7b_NuX9p.exe (PID: 7816)
- explorer.exe (PID: 2404)
- AppLaunch.exe (PID: 3368)
- DTPanelQT.exe (PID: 7492)
Starts application with an unusual extension
- zieHLA8NQI852wSb4lC7UHP2.exe (PID: 7836)
Reads the BIOS version
- 7nsBhSw3KD_7P95n7b_NuX9p.exe (PID: 7816)
- Nrpb1aPFZTZwcMYNO3f044Q6.exe (PID: 7696)
Searches for installed software
- 㡮癄稵䔶坮确䑺捺㍢ (PID: 7216)
- jveESZmOmFEXAAXKAFgccWxe.exe (PID: 8168)
- RegSvcs.exe (PID: 7896)
- LGm3L21BXa.tmp (PID: 3860)
Loads DLL from Mozilla Firefox
- explorer.exe (PID: 7784)
Uses ICACLS.EXE to modify access control lists
- 5yJ27pEysT6fJzdq6LJ09com.exe (PID: 2856)
Starts POWERSHELL.EXE for commands execution
- explorer.exe (PID: 4428)
Script adds exclusion path to Windows Defender
- explorer.exe (PID: 4428)
Uses RUNDLL32.EXE to load library
- rundll32.exe (PID: 5908)
Uses powercfg.exe to modify the power settings
- cmd.exe (PID: 3056)
- cmd.exe (PID: 3708)
Starts SC.EXE for service management
- cmd.exe (PID: 5144)
- cmd.exe (PID: 5544)
The process executes via Task Scheduler
- updater.exe (PID: 2608)
- lV3SG2WiNRxQz1eD7GGPcp15.exe (PID: 6264)
- lV3SG2WiNRxQz1eD7GGPcp15.exe (PID: 488)
- lV3SG2WiNRxQz1eD7GGPcp15.exe (PID: 5148)
- lV3SG2WiNRxQz1eD7GGPcp15.exe (PID: 5100)
- dbcgshj (PID: 3180)
- lV3SG2WiNRxQz1eD7GGPcp15.exe (PID: 5400)
- lV3SG2WiNRxQz1eD7GGPcp15.exe (PID: 7484)
- lV3SG2WiNRxQz1eD7GGPcp15.exe (PID: 6752)
The process creates files with name similar to system file names
- powershell.exe (PID: 5796)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 6880)
Drops a system driver (possible attempt to evade defenses)
- updater.exe (PID: 2608)
INFO
Reads the computer name
- identity_helper.exe (PID: 1276)
- setup.exe (PID: 7096)
- WW13_64.exe (PID: 4508)
- ZzPTu52Dp3p6gXRktdO1e23F.exe (PID: 880)
- KKEb5KiRt4h8VfeXgS2GBXIS.exe (PID: 896)
- Bn3Y5V0xUss2ym9T68bDhTaG.exe (PID: 6176)
- 1b87UN0D0yUAptLOc31oMQiH.exe (PID: 6712)
- R9xjSNTSHQc5MeswF4lWjJ5r.exe (PID: 6148)
- DqT7nYPunqBMkuRLL7edn9lt.exe (PID: 1084)
- 5yJ27pEysT6fJzdq6LJ09com.exe (PID: 2856)
- sHt80OJEDP7kj8X5QS49OXo9.tmp (PID: 6360)
- uO3Nuz5ET3PKxtPnAXeI4Rex.exe (PID: 4320)
- zieHLA8NQI852wSb4lC7UHP2.exe (PID: 7836)
- DTPanelQT.exe (PID: 7368)
- mDhAmrjuJ0RbtfDpFce1HKra.exe (PID: 7912)
- 㡮癄稵䔶坮确䑺捺㍢ (PID: 7216)
- jveESZmOmFEXAAXKAFgccWxe.exe (PID: 8168)
- aGwqlXg4MsSR82Qts0Wn9hrw.exe (PID: 7376)
- 7nsBhSw3KD_7P95n7b_NuX9p.exe (PID: 7816)
- IBAKBWA1bGabG21m0w3Vytqc.exe (PID: 7652)
- setup.exe (PID: 2116)
- RegSvcs.exe (PID: 7896)
- Nrpb1aPFZTZwcMYNO3f044Q6.exe (PID: 7696)
- lV3SG2WiNRxQz1eD7GGPcp15.exe (PID: 3952)
- 5yJ27pEysT6fJzdq6LJ09com.exe (PID: 4504)
- LGm3L21BXa.tmp (PID: 3860)
- DTPanelQT.exe (PID: 7492)
- AppLaunch.exe (PID: 3368)
Checks supported languages
- identity_helper.exe (PID: 1276)
- setup.exe (PID: 7096)
- WW13_64.exe (PID: 6504)
- setup.exe (PID: 2116)
- WW13_64.exe (PID: 4508)
- KiJ3hN2hayADiMWAVzxMucME.exe (PID: 1416)
- R9xjSNTSHQc5MeswF4lWjJ5r.exe (PID: 6148)
- ZzPTu52Dp3p6gXRktdO1e23F.exe (PID: 880)
- KKEb5KiRt4h8VfeXgS2GBXIS.exe (PID: 896)
- Bn3Y5V0xUss2ym9T68bDhTaG.exe (PID: 6176)
- 1b87UN0D0yUAptLOc31oMQiH.exe (PID: 6712)
- 5yJ27pEysT6fJzdq6LJ09com.exe (PID: 6696)
- DqT7nYPunqBMkuRLL7edn9lt.exe (PID: 1084)
- h662quGI9oQwZm68YiQjblSe.exe (PID: 6344)
- 5yJ27pEysT6fJzdq6LJ09com.exe (PID: 2856)
- sHt80OJEDP7kj8X5QS49OXo9.tmp (PID: 6360)
- sHt80OJEDP7kj8X5QS49OXo9.exe (PID: 5964)
- uO3Nuz5ET3PKxtPnAXeI4Rex.exe (PID: 4320)
- jveESZmOmFEXAAXKAFgccWxe.exe (PID: 7692)
- zieHLA8NQI852wSb4lC7UHP2.exe (PID: 7836)
- DTPanelQT.exe (PID: 7368)
- DTPanelQT.exe (PID: 7492)
- mDhAmrjuJ0RbtfDpFce1HKra.exe (PID: 7912)
- 㡮癄稵䔶坮确䑺捺㍢ (PID: 7216)
- jveESZmOmFEXAAXKAFgccWxe.exe (PID: 8168)
- aGwqlXg4MsSR82Qts0Wn9hrw.exe (PID: 7376)
- 7nsBhSw3KD_7P95n7b_NuX9p.exe (PID: 7816)
- Nrpb1aPFZTZwcMYNO3f044Q6.exe (PID: 7696)
- IBAKBWA1bGabG21m0w3Vytqc.exe (PID: 7652)
- RegSvcs.exe (PID: 7896)
- lV3SG2WiNRxQz1eD7GGPcp15.exe (PID: 3952)
- vQ6DLHi3GC4EYXblv6AP2N2V.exe (PID: 6044)
- 5yJ27pEysT6fJzdq6LJ09com.exe (PID: 3112)
- 5yJ27pEysT6fJzdq6LJ09com.exe (PID: 4504)
- updater.exe (PID: 2608)
- LGm3L21BXa.exe (PID: 1452)
- LGm3L21BXa.tmp (PID: 3860)
- AppLaunch.exe (PID: 3368)
- lV3SG2WiNRxQz1eD7GGPcp15.exe (PID: 6264)
- lV3SG2WiNRxQz1eD7GGPcp15.exe (PID: 488)
- lV3SG2WiNRxQz1eD7GGPcp15.exe (PID: 6752)
- lV3SG2WiNRxQz1eD7GGPcp15.exe (PID: 5100)
- lV3SG2WiNRxQz1eD7GGPcp15.exe (PID: 5148)
- dbcgshj (PID: 3180)
- lV3SG2WiNRxQz1eD7GGPcp15.exe (PID: 5400)
- lV3SG2WiNRxQz1eD7GGPcp15.exe (PID: 7484)
The process uses the downloaded file
- msedge.exe (PID: 2816)
- msedge.exe (PID: 3752)
- WinRAR.exe (PID: 4880)
Create files in a temporary directory
- setup.exe (PID: 7096)
- setup.exe (PID: 2116)
- R9xjSNTSHQc5MeswF4lWjJ5r.exe (PID: 6148)
- sHt80OJEDP7kj8X5QS49OXo9.exe (PID: 5964)
- sHt80OJEDP7kj8X5QS49OXo9.tmp (PID: 6360)
- uO3Nuz5ET3PKxtPnAXeI4Rex.exe (PID: 4320)
- mDhAmrjuJ0RbtfDpFce1HKra.exe (PID: 7912)
- zieHLA8NQI852wSb4lC7UHP2.exe (PID: 7836)
- 7nsBhSw3KD_7P95n7b_NuX9p.exe (PID: 7816)
- aGwqlXg4MsSR82Qts0Wn9hrw.exe (PID: 7376)
- explorer.exe (PID: 6432)
- LGm3L21BXa.exe (PID: 1452)
- LGm3L21BXa.tmp (PID: 3860)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 4880)
- msedge.exe (PID: 6888)
- explorer.exe (PID: 4428)
Checks proxy server information
- WW13_64.exe (PID: 6504)
- WW13_64.exe (PID: 4508)
- ZzPTu52Dp3p6gXRktdO1e23F.exe (PID: 880)
- WerFault.exe (PID: 5152)
- WerFault.exe (PID: 2868)
- DqT7nYPunqBMkuRLL7edn9lt.exe (PID: 1084)
- 5yJ27pEysT6fJzdq6LJ09com.exe (PID: 2856)
- explorer.exe (PID: 4428)
- IBAKBWA1bGabG21m0w3Vytqc.exe (PID: 7652)
- explorer.exe (PID: 6432)
- explorer.exe (PID: 7784)
- lV3SG2WiNRxQz1eD7GGPcp15.exe (PID: 3952)
- Nrpb1aPFZTZwcMYNO3f044Q6.exe (PID: 7696)
- 5yJ27pEysT6fJzdq6LJ09com.exe (PID: 4504)
- DTPanelQT.exe (PID: 7492)
Application launched itself
- msedge.exe (PID: 3752)
The executable file from the user directory is run by the CMD process
- ZzPTu52Dp3p6gXRktdO1e23F.exe (PID: 880)
- KKEb5KiRt4h8VfeXgS2GBXIS.exe (PID: 896)
- KiJ3hN2hayADiMWAVzxMucME.exe (PID: 1416)
- R9xjSNTSHQc5MeswF4lWjJ5r.exe (PID: 6148)
- Bn3Y5V0xUss2ym9T68bDhTaG.exe (PID: 6176)
- 1b87UN0D0yUAptLOc31oMQiH.exe (PID: 6712)
- 5yJ27pEysT6fJzdq6LJ09com.exe (PID: 6696)
- DqT7nYPunqBMkuRLL7edn9lt.exe (PID: 1084)
- h662quGI9oQwZm68YiQjblSe.exe (PID: 6344)
- sHt80OJEDP7kj8X5QS49OXo9.exe (PID: 5964)
- uO3Nuz5ET3PKxtPnAXeI4Rex.exe (PID: 4320)
- jveESZmOmFEXAAXKAFgccWxe.exe (PID: 7692)
- zieHLA8NQI852wSb4lC7UHP2.exe (PID: 7836)
- mDhAmrjuJ0RbtfDpFce1HKra.exe (PID: 7912)
- aGwqlXg4MsSR82Qts0Wn9hrw.exe (PID: 7376)
- 7nsBhSw3KD_7P95n7b_NuX9p.exe (PID: 7816)
- Nrpb1aPFZTZwcMYNO3f044Q6.exe (PID: 7696)
- IBAKBWA1bGabG21m0w3Vytqc.exe (PID: 7652)
Reads the machine GUID from the registry
- Bn3Y5V0xUss2ym9T68bDhTaG.exe (PID: 6176)
- 1b87UN0D0yUAptLOc31oMQiH.exe (PID: 6712)
- 5yJ27pEysT6fJzdq6LJ09com.exe (PID: 2856)
- uO3Nuz5ET3PKxtPnAXeI4Rex.exe (PID: 4320)
- mDhAmrjuJ0RbtfDpFce1HKra.exe (PID: 7912)
- aGwqlXg4MsSR82Qts0Wn9hrw.exe (PID: 7376)
- IBAKBWA1bGabG21m0w3Vytqc.exe (PID: 7652)
- Nrpb1aPFZTZwcMYNO3f044Q6.exe (PID: 7696)
- 5yJ27pEysT6fJzdq6LJ09com.exe (PID: 4504)
- AppLaunch.exe (PID: 3368)
Process checks computer location settings
- R9xjSNTSHQc5MeswF4lWjJ5r.exe (PID: 6148)
- IBAKBWA1bGabG21m0w3Vytqc.exe (PID: 7652)
- Nrpb1aPFZTZwcMYNO3f044Q6.exe (PID: 7696)
- lV3SG2WiNRxQz1eD7GGPcp15.exe (PID: 3952)
- 5yJ27pEysT6fJzdq6LJ09com.exe (PID: 2856)
- DqT7nYPunqBMkuRLL7edn9lt.exe (PID: 1084)
Creates files or folders in the user directory
- WerFault.exe (PID: 6312)
- WerFault.exe (PID: 5152)
- WerFault.exe (PID: 5504)
- WerFault.exe (PID: 6936)
- WerFault.exe (PID: 7136)
- WerFault.exe (PID: 2728)
- WerFault.exe (PID: 2868)
- WerFault.exe (PID: 5036)
- DqT7nYPunqBMkuRLL7edn9lt.exe (PID: 1084)
- uO3Nuz5ET3PKxtPnAXeI4Rex.exe (PID: 4320)
- explorer.exe (PID: 4428)
- 5yJ27pEysT6fJzdq6LJ09com.exe (PID: 2856)
- 7nsBhSw3KD_7P95n7b_NuX9p.exe (PID: 7816)
- mDhAmrjuJ0RbtfDpFce1HKra.exe (PID: 7912)
- aGwqlXg4MsSR82Qts0Wn9hrw.exe (PID: 7376)
- IBAKBWA1bGabG21m0w3Vytqc.exe (PID: 7652)
- Nrpb1aPFZTZwcMYNO3f044Q6.exe (PID: 7696)
- 5yJ27pEysT6fJzdq6LJ09com.exe (PID: 4504)
- WerFault.exe (PID: 3116)
- WerFault.exe (PID: 4944)
- WerFault.exe (PID: 5372)
Reads the software policy settings
- WerFault.exe (PID: 2868)
- WerFault.exe (PID: 5152)
- 5yJ27pEysT6fJzdq6LJ09com.exe (PID: 2856)
- IBAKBWA1bGabG21m0w3Vytqc.exe (PID: 7652)
- Nrpb1aPFZTZwcMYNO3f044Q6.exe (PID: 7696)
Creates files in the program directory
- sHt80OJEDP7kj8X5QS49OXo9.tmp (PID: 6360)
- uO3Nuz5ET3PKxtPnAXeI4Rex.exe (PID: 4320)
- DTPanelQT.exe (PID: 7368)
- mDhAmrjuJ0RbtfDpFce1HKra.exe (PID: 7912)
- 7nsBhSw3KD_7P95n7b_NuX9p.exe (PID: 7816)
- vQ6DLHi3GC4EYXblv6AP2N2V.exe (PID: 6044)
- LGm3L21BXa.tmp (PID: 3860)
- updater.exe (PID: 2608)
- DTPanelQT.exe (PID: 7492)
Process checks are UAC notifies on
- 7nsBhSw3KD_7P95n7b_NuX9p.exe (PID: 7816)
- Nrpb1aPFZTZwcMYNO3f044Q6.exe (PID: 7696)
Reads Environment values
- lV3SG2WiNRxQz1eD7GGPcp15.exe (PID: 3952)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
RisePro
(PID) Process(4320) uO3Nuz5ET3PKxtPnAXeI4Rex.exe
C2193.233.132.51
(PID) Process(7912) mDhAmrjuJ0RbtfDpFce1HKra.exe
C2195.20.16.45
RedLine
(PID) Process(3368) AppLaunch.exe
C2 (1)45.15.156.187:23929
BotnetLogsDiller Cloud (Telegram: @logsdillabot)
Options
ErrorMessage
Keys
XorScuffs
Total processes
366
Monitored processes
205
Malicious processes
58
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=audio.mojom.AudioService --lang=en-US --service-sandbox-type=audio --mojo-platform-channel-handle=1668 --field-trial-handle=1964,i,16138432378268198214,11264646325332633625,131072 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 111.0.1661.62 Modules
| |||||||||||||||
| 128 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 488 | "C:\Users\admin\Pictures\Minor Policy\lV3SG2WiNRxQz1eD7GGPcp15.exe" | C:\Users\admin\Pictures\Minor Policy\lV3SG2WiNRxQz1eD7GGPcp15.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 528 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=2084 --field-trial-handle=1964,i,16138432378268198214,11264646325332633625,131072 /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 111.0.1661.62 Modules
| |||||||||||||||
| 596 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=2464 --field-trial-handle=1964,i,16138432378268198214,11264646325332633625,131072 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 111.0.1661.62 Modules
| |||||||||||||||
| 872 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=5536 --field-trial-handle=1964,i,16138432378268198214,11264646325332633625,131072 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 111.0.1661.62 Modules
| |||||||||||||||
| 880 | "C:\Users\admin/Documents\Minor Policy\ZzPTu52Dp3p6gXRktdO1e23F.exe" "" | C:\Users\admin\Documents\Minor Policy\ZzPTu52Dp3p6gXRktdO1e23F.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225477 Modules
| |||||||||||||||
| 896 | "C:\Users\admin/Documents\Minor Policy\KKEb5KiRt4h8VfeXgS2GBXIS.exe" "" | C:\Users\admin\Documents\Minor Policy\KKEb5KiRt4h8VfeXgS2GBXIS.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3762504530 Modules
| |||||||||||||||
| 896 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1084 | "C:\Users\admin/Documents\Minor Policy\DqT7nYPunqBMkuRLL7edn9lt.exe" "" | C:\Users\admin\Documents\Minor Policy\DqT7nYPunqBMkuRLL7edn9lt.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 1998805824 Modules
| |||||||||||||||
Total events
75 449
Read events
75 018
Write events
309
Delete events
122
Modification events
| (PID) Process: | (3752) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3752) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3752) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3752) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3752) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate\ClientState\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3752) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (3752) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge |
| Operation: | write | Name: | UsageStatsInSample |
Value: 1 | |||
| (PID) Process: | (3752) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: BC8CC635B5602F00 | |||
| (PID) Process: | (3752) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (3752) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | urlstats |
Value: 0 | |||
Executable files
321
Suspicious files
259
Text files
197
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3752 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF14e444.TMP | — | |
MD5:— | SHA256:— | |||
| 3752 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3752 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF14e444.TMP | — | |
MD5:— | SHA256:— | |||
| 3752 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3752 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF14e405.TMP | — | |
MD5:— | SHA256:— | |||
| 3752 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3752 | msedge.exe | C:\USERS\ADMIN\APPDATA\LOCAL\MICROSOFT\EDGE\USER DATA\VARIATIONS | binary | |
MD5:CDDDC745A8C954DC438C931889999BDB | SHA256:3DC9043838386F5363AC96A01477CF3163B5118B80191576A11B32CE9894314C | |||
| 3752 | msedge.exe | C:\USERS\ADMIN\APPDATA\LOCAL\MICROSOFT\EDGE\USER DATA\CRASHPAD\SETTINGS.DAT | binary | |
MD5:AE78610F57A24ED740046B2A7CBE0272 | SHA256:7155BB73DA7368FB1A65E29E58B36988C7DEA30362619803908D7CFD955C22E9 | |||
| 3752 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Last Version | text | |
MD5:D6DB6EA02FE506F2DA98F1C137243587 | SHA256:126173A7D7D0F54A9FCE5465180BC49DB023E723A41BB55A0F9497BE76FBAA28 | |||
| 3752 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Sync Data\LevelDB\LOG.old~RF14e415.TMP | text | |
MD5:BAC7C6FC0247F868CFF8018E24CFB4EC | SHA256:A5C5BBAB942880AB4139B5E762F73AE053C3D7D49116A48ABB92A99D9BF4DA8C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
298
TCP/UDP connections
6 570
DNS requests
173
Threats
6 560
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2556 | svchost.exe | HEAD | 200 | 87.248.205.0:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/26b10680-9c99-4cf8-93c0-fca56709a250?P1=1703084393&P2=404&P3=2&P4=jW0H8LoGs3n2lTnS%2f9sPkkTTj4wiXHOUgKaRbkrTWnJ4Fa1lajrpm6JkkTki57PjJCbvsDuy2Gj4eZi%2bocM2Ow%3d%3d | unknown | — | — | unknown |
6504 | WW13_64.exe | GET | — | 195.20.16.45:80 | http://195.20.16.45/api/tracemap.php | unknown | — | — | unknown |
2556 | svchost.exe | GET | 206 | 87.248.205.0:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/26b10680-9c99-4cf8-93c0-fca56709a250?P1=1703084393&P2=404&P3=2&P4=jW0H8LoGs3n2lTnS%2f9sPkkTTj4wiXHOUgKaRbkrTWnJ4Fa1lajrpm6JkkTki57PjJCbvsDuy2Gj4eZi%2bocM2Ow%3d%3d | unknown | binary | 1.09 Kb | unknown |
2556 | svchost.exe | GET | 206 | 87.248.205.0:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/26b10680-9c99-4cf8-93c0-fca56709a250?P1=1703084393&P2=404&P3=2&P4=jW0H8LoGs3n2lTnS%2f9sPkkTTj4wiXHOUgKaRbkrTWnJ4Fa1lajrpm6JkkTki57PjJCbvsDuy2Gj4eZi%2bocM2Ow%3d%3d | unknown | binary | 236 b | unknown |
2556 | svchost.exe | GET | 206 | 87.248.205.0:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/26b10680-9c99-4cf8-93c0-fca56709a250?P1=1703084393&P2=404&P3=2&P4=jW0H8LoGs3n2lTnS%2f9sPkkTTj4wiXHOUgKaRbkrTWnJ4Fa1lajrpm6JkkTki57PjJCbvsDuy2Gj4eZi%2bocM2Ow%3d%3d | unknown | binary | 3.30 Kb | unknown |
6504 | WW13_64.exe | GET | — | 77.105.147.130:80 | http://77.105.147.130/api/tracemap.php | unknown | — | — | unknown |
6504 | WW13_64.exe | GET | 200 | 46.35.111.154:80 | http://46.35.111.154/UserCheck/PortalMain?IID=4ABE1015-5037-4E91-63A5-13E80B548392&origUrl=aHR0cDovLzE5NS4yMC4xNi40NS9hcGkvdHJhY2VtYXAucGhw | unknown | html | 106 Kb | unknown |
2556 | svchost.exe | GET | 206 | 87.248.205.0:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/26b10680-9c99-4cf8-93c0-fca56709a250?P1=1703084393&P2=404&P3=2&P4=jW0H8LoGs3n2lTnS%2f9sPkkTTj4wiXHOUgKaRbkrTWnJ4Fa1lajrpm6JkkTki57PjJCbvsDuy2Gj4eZi%2bocM2Ow%3d%3d | unknown | binary | 9.81 Kb | unknown |
6504 | WW13_64.exe | GET | 200 | 46.35.111.154:80 | http://46.35.111.154/UserCheck/PortalMain?IID=DE5C2409-4C10-75E6-B8CA-F22DF6071B93&origUrl=aHR0cDovLzc3LjEwNS4xNDcuMTMwL2FwaS90cmFjZW1hcC5waHA | unknown | html | 106 Kb | unknown |
2556 | svchost.exe | GET | 206 | 87.248.205.0:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/26b10680-9c99-4cf8-93c0-fca56709a250?P1=1703084393&P2=404&P3=2&P4=jW0H8LoGs3n2lTnS%2f9sPkkTTj4wiXHOUgKaRbkrTWnJ4Fa1lajrpm6JkkTki57PjJCbvsDuy2Gj4eZi%2bocM2Ow%3d%3d | unknown | binary | 15.2 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3240 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3752 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
528 | msedge.exe | 31.216.144.5:443 | mega.nz | Datacenter Luxembourg S.A. | LU | unknown |
528 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
528 | msedge.exe | 20.105.95.163:443 | nav-edge.smartscreen.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
528 | msedge.exe | 51.104.176.40:443 | data-edge.smartscreen.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3764 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
528 | msedge.exe | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
528 | msedge.exe | 89.44.169.134:443 | eu.static.mega.co.nz | Datacenter Luxembourg S.A. | LU | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
mega.nz |
| whitelisted |
config.edge.skype.com |
| whitelisted |
nav-edge.smartscreen.microsoft.com |
| whitelisted |
data-edge.smartscreen.microsoft.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
eu.static.mega.co.nz |
| shared |
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
g.api.mega.co.nz |
| shared |
edgeassetservice.azureedge.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
528 | msedge.exe | Misc activity | ET INFO File Sharing Related Domain in DNS Lookup (mega .nz) |
528 | msedge.exe | Misc activity | ET INFO File Sharing Related Domain in DNS Lookup (mega .nz) |
528 | msedge.exe | Misc activity | ET INFO File Sharing Domain Observed in TLS SNI (mega .nz) |
528 | msedge.exe | Misc activity | ET INFO Observed DNS Query to Filesharing Service (mega .co .nz) |
528 | msedge.exe | Misc activity | ET INFO Observed DNS Query to Filesharing Service (mega .co .nz) |
528 | msedge.exe | Misc activity | ET INFO File Sharing Domain Observed in TLS SNI (mega .nz) |
528 | msedge.exe | Misc activity | ET INFO Observed DNS Query to Filesharing Service (mega .co .nz) |
528 | msedge.exe | Misc activity | ET INFO Observed DNS Query to Filesharing Service (mega .co .nz) |
528 | msedge.exe | Misc activity | ET INFO File Sharing Related Domain in DNS Lookup (mega .nz) |
528 | msedge.exe | Misc activity | ET INFO File Sharing Domain Observed in TLS SNI (mega .nz) |
36 ETPRO signatures available at the full report