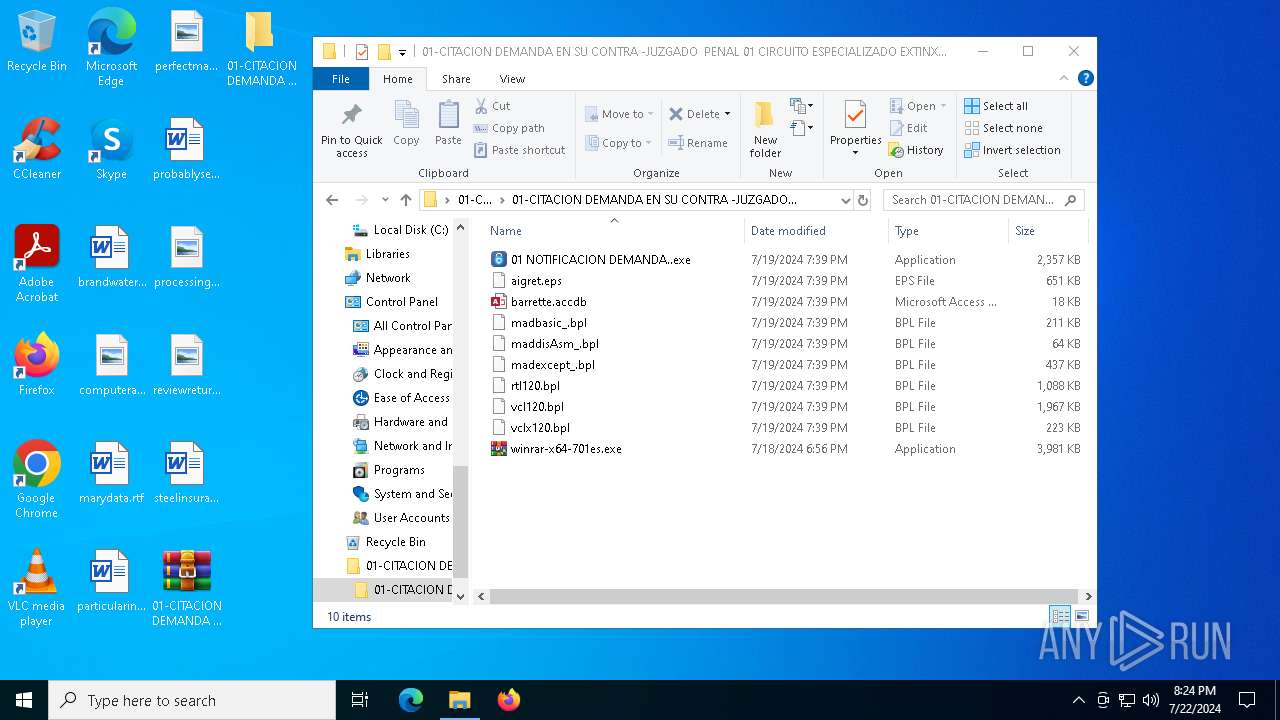
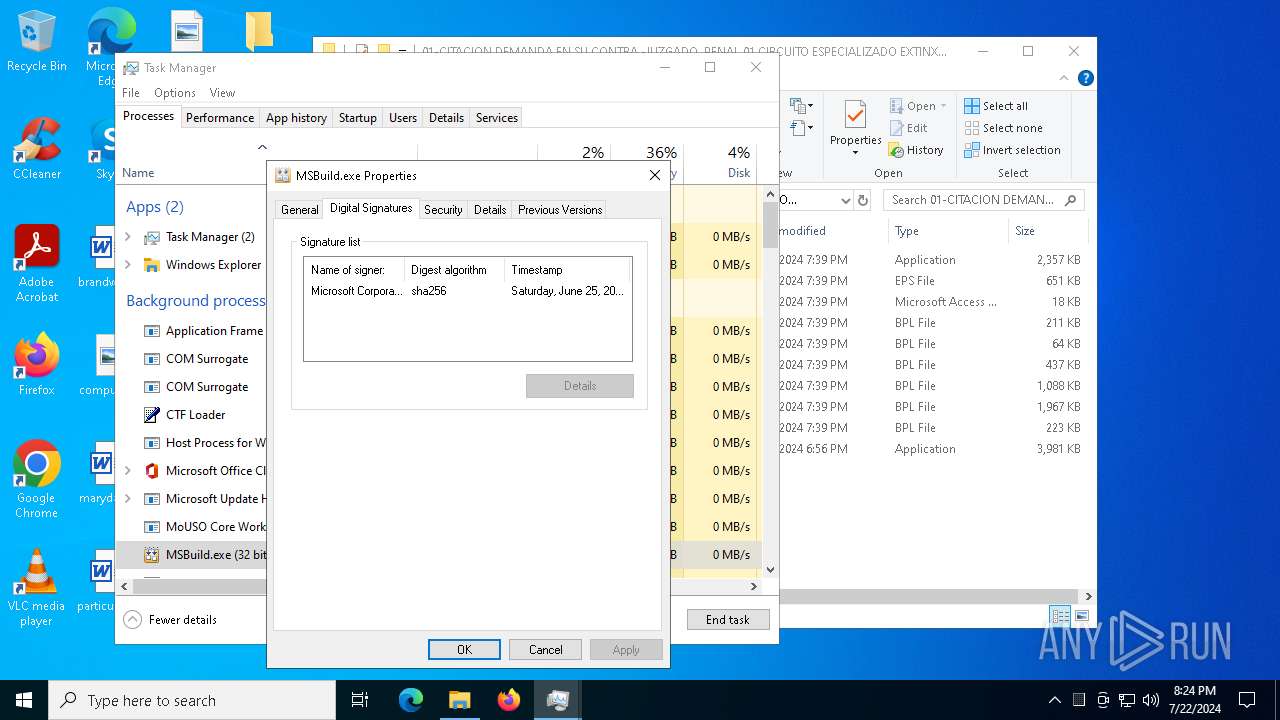
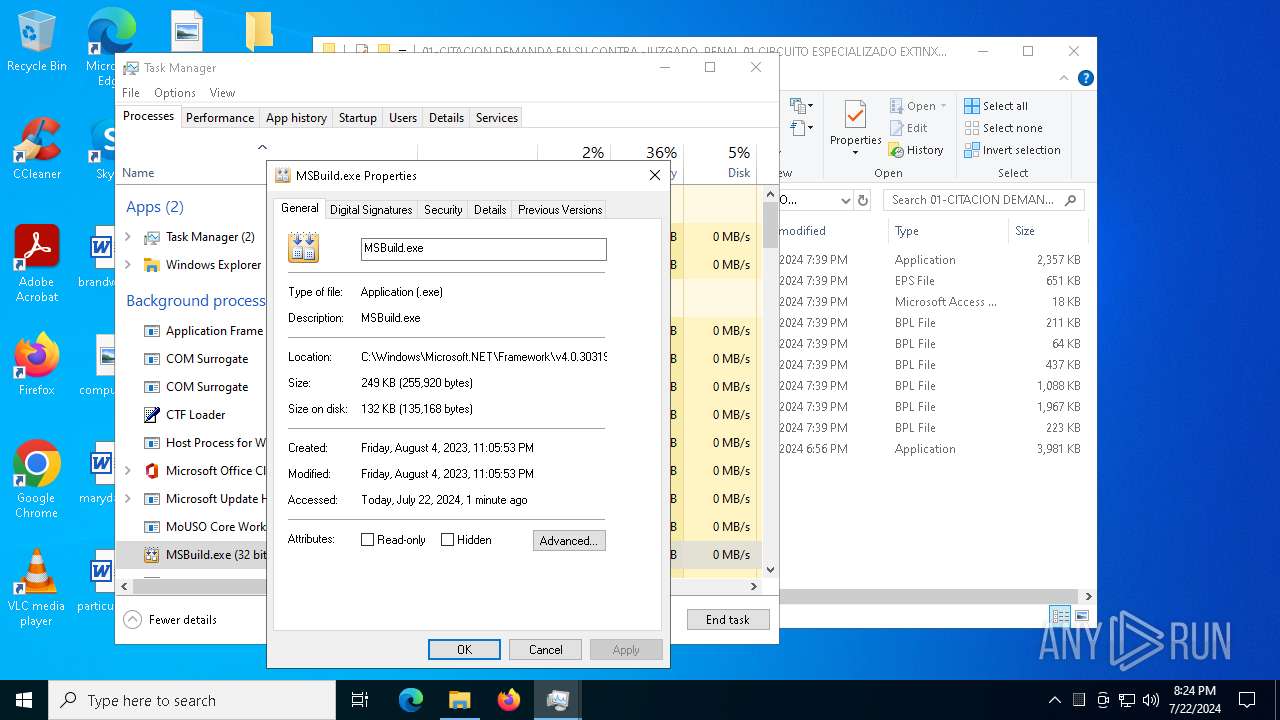
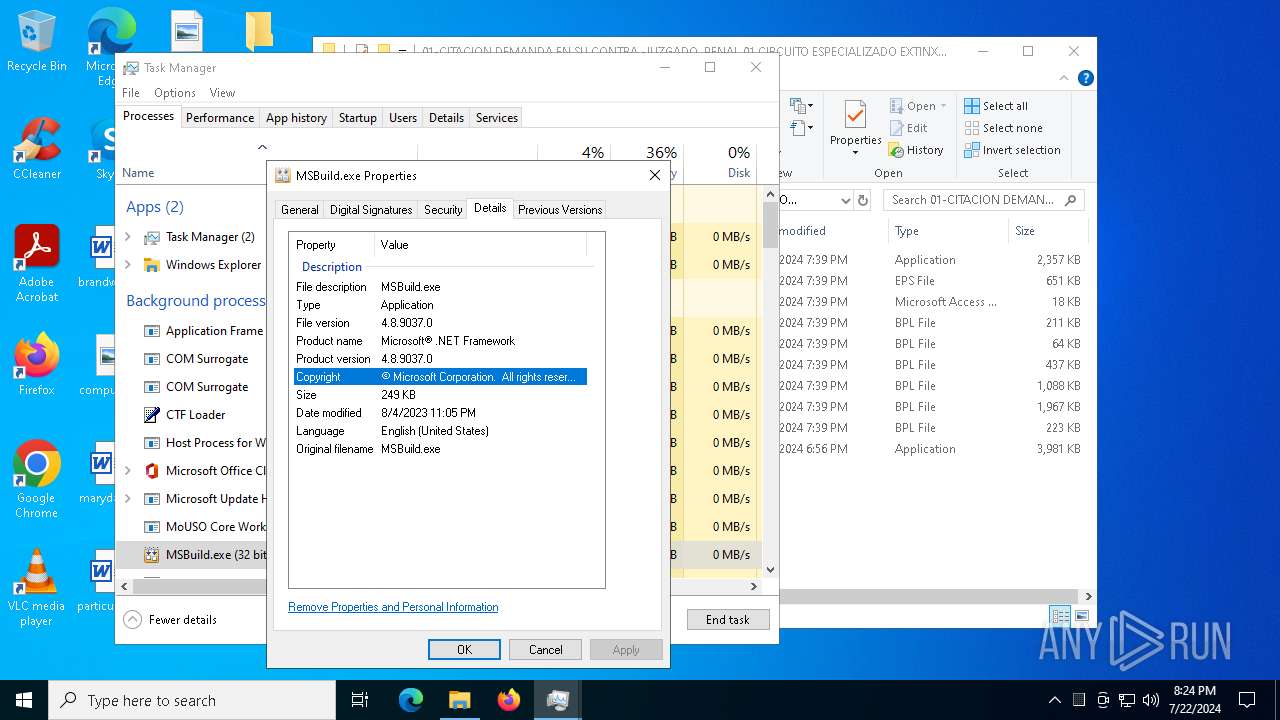
| File name: | aigret.eps |
| Full analysis: | https://app.any.run/tasks/70264f6e-e426-4c34-88e8-c2b8a7f9c39e |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | July 22, 2024, 20:21:33 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/octet-stream |
| File info: | data |
| MD5: | B16A26AEE27CDC91B7F545E03877F9C0 |
| SHA1: | 7EB68256AC0A97E4EE0DDC1DB648968987406910 |
| SHA256: | B3ABDC2B792CB4B0160BDCC291DCB13B31078D852BD20AE01AE0908A0B46B72F |
| SSDEEP: | 24576:mdDY9q8Uvwz4I87pTipZLDkRdp+ZIXTZcIqCPuwl:mtY9q8owz4I87pOpZLDk/p+ZIXTZ7qCh |
MALICIOUS
Drops the executable file immediately after the start
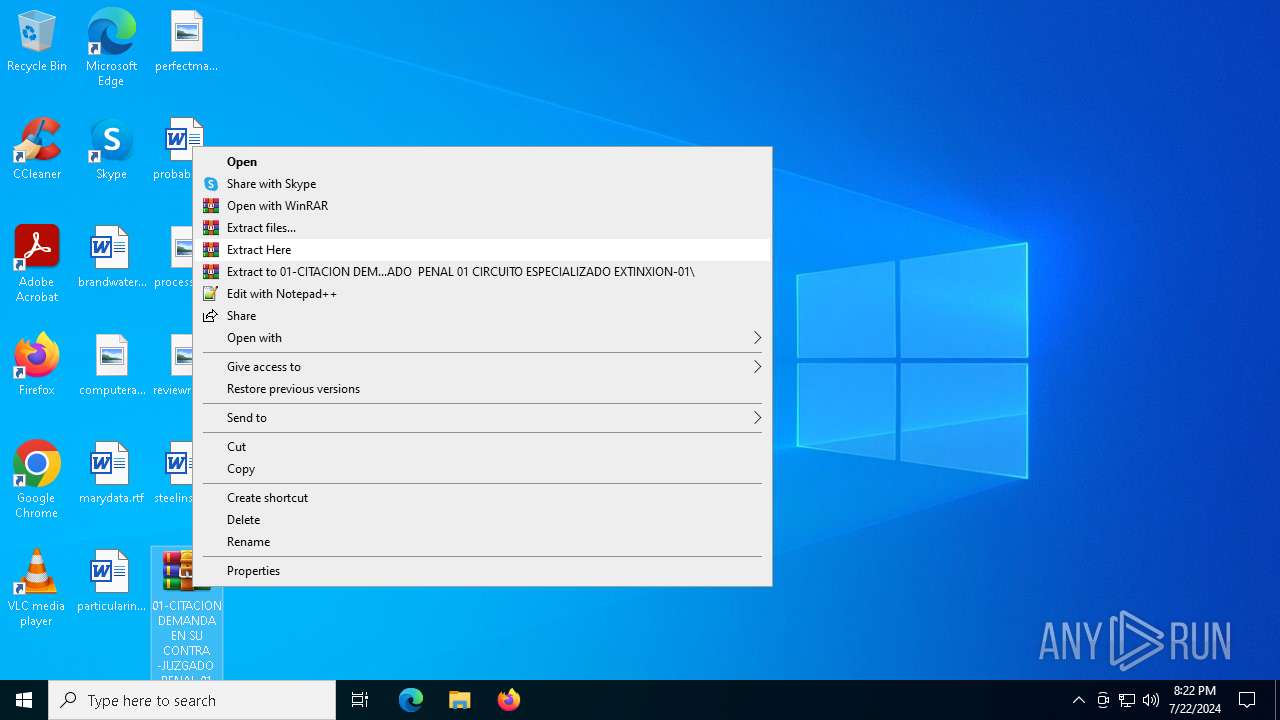
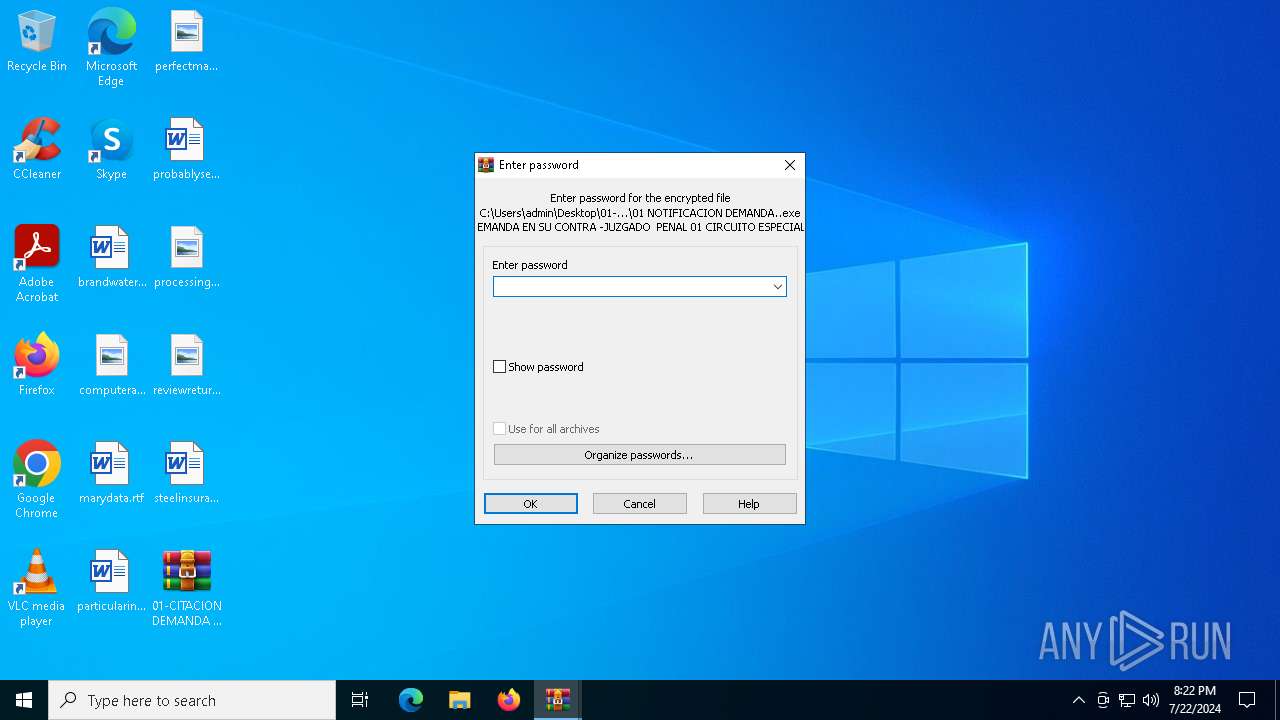
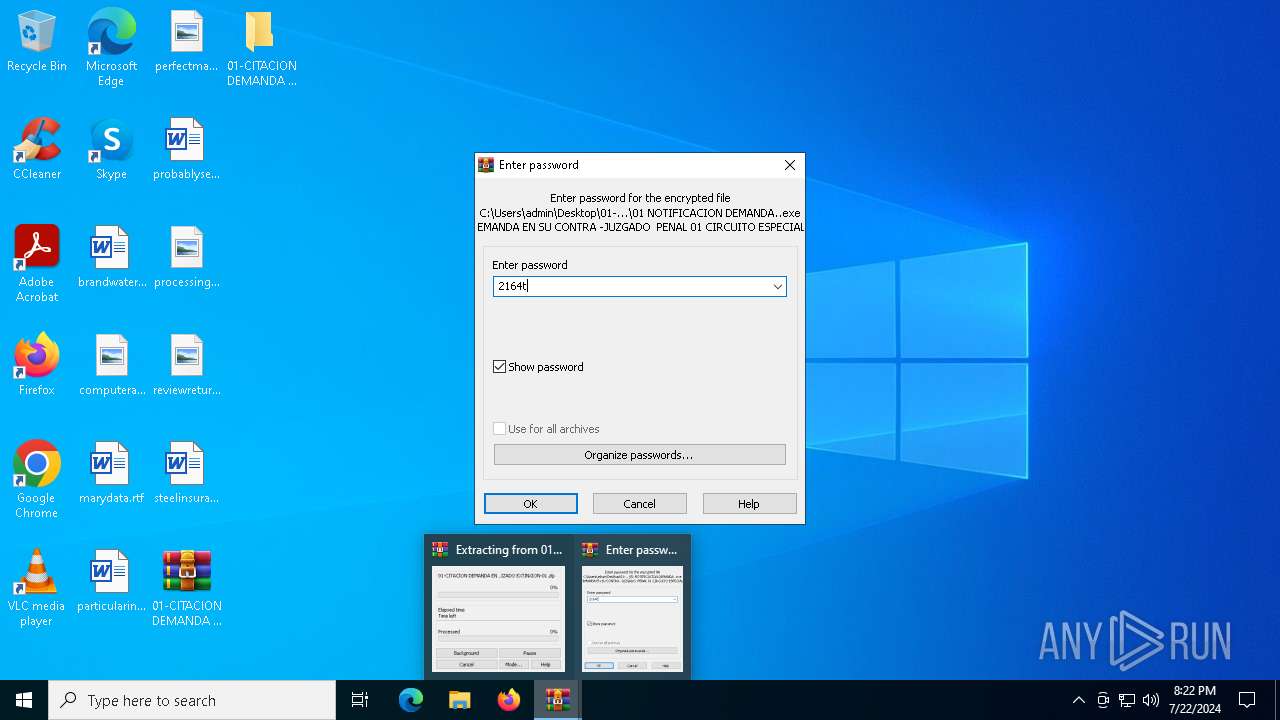
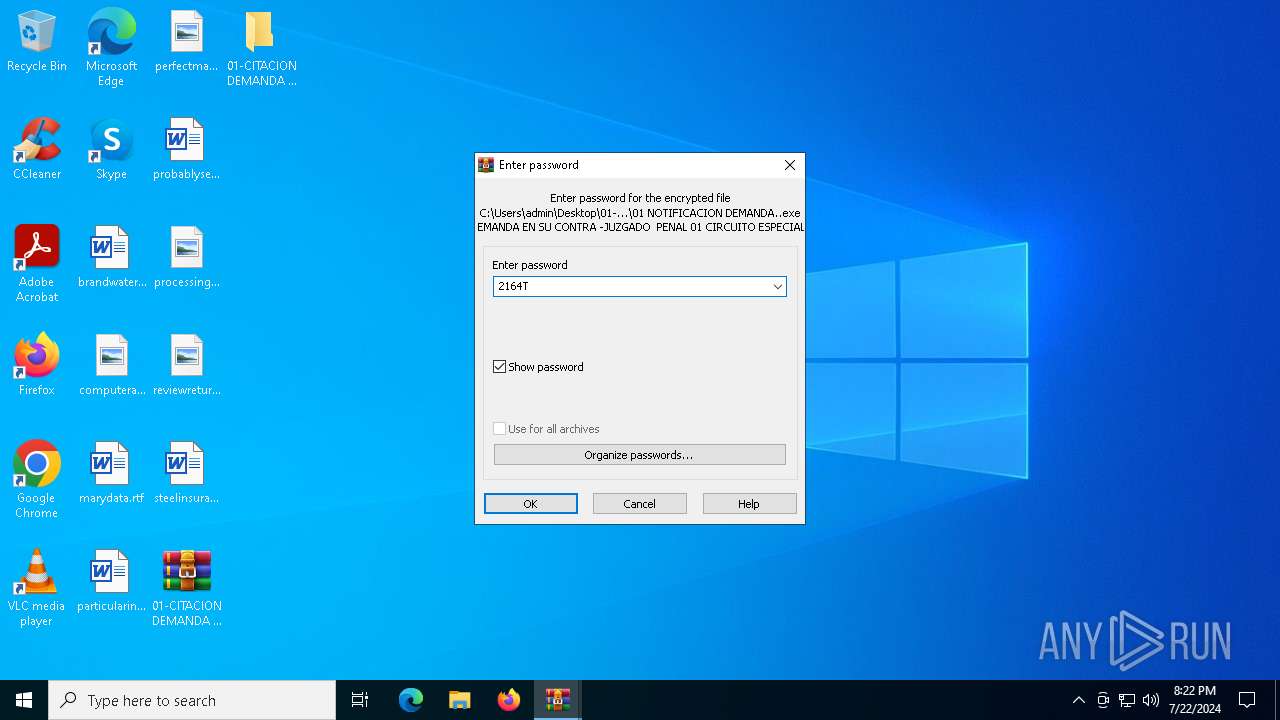
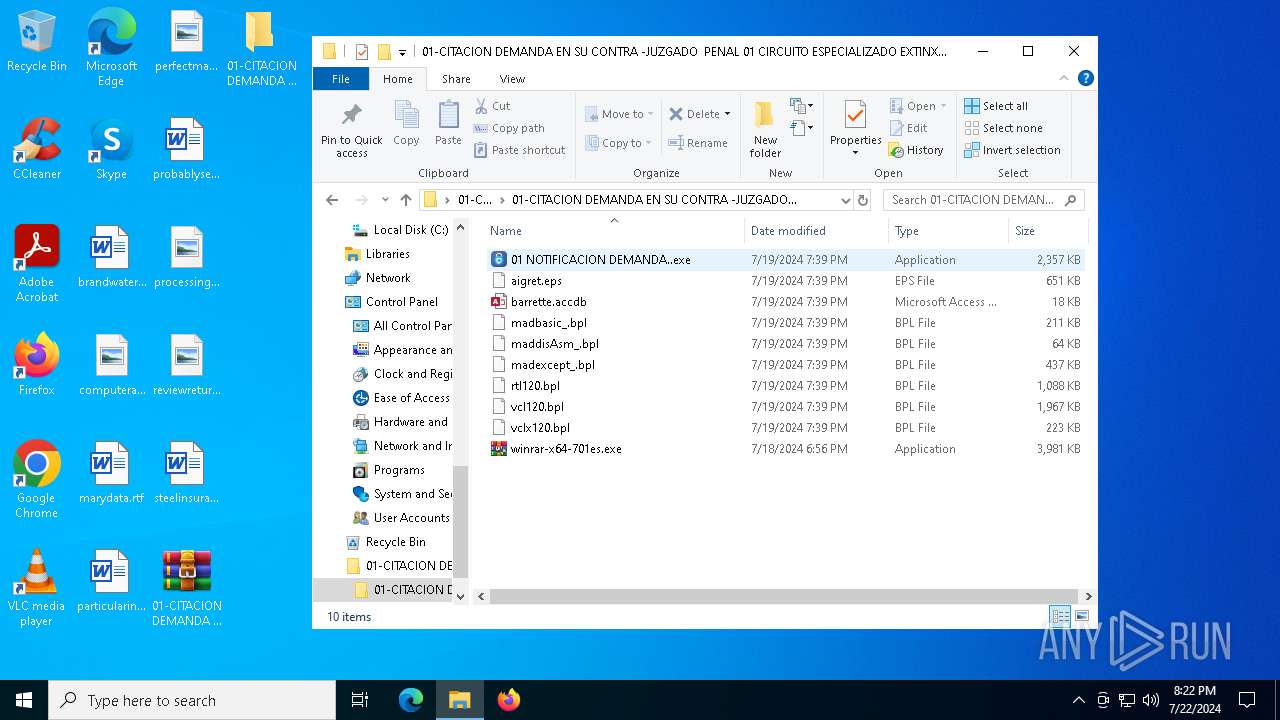
- 01 NOTIFICACION DEMANDA..exe (PID: 4788)
ASYNCRAT has been detected (YARA)
- MSBuild.exe (PID: 5672)
ASYNCRAT has been detected (MUTEX)
- MSBuild.exe (PID: 5672)
ASYNCRAT has been detected (SURICATA)
- MSBuild.exe (PID: 5672)
Actions looks like stealing of personal data
- MSBuild.exe (PID: 5672)
SUSPICIOUS
Starts CMD.EXE for commands execution
- 01 NOTIFICACION DEMANDA..exe (PID: 4788)
Connects to unusual port
- MSBuild.exe (PID: 5672)
Executable content was dropped or overwritten
- 01 NOTIFICACION DEMANDA..exe (PID: 4788)
Contacting a server suspected of hosting an CnC
- MSBuild.exe (PID: 5672)
INFO
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 2668)
Creates files or folders in the user directory
- 01 NOTIFICACION DEMANDA..exe (PID: 4788)
Checks proxy server information
- slui.exe (PID: 4816)
Reads the computer name
- 01 NOTIFICACION DEMANDA..exe (PID: 4788)
- MSBuild.exe (PID: 5672)
Create files in a temporary directory
- 01 NOTIFICACION DEMANDA..exe (PID: 4788)
Manual execution by a user
- WinRAR.exe (PID: 7008)
- 01 NOTIFICACION DEMANDA..exe (PID: 4788)
- Taskmgr.exe (PID: 6468)
- Taskmgr.exe (PID: 7012)
Reads the software policy settings
- slui.exe (PID: 4816)
- MSBuild.exe (PID: 5672)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 7008)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7008)
Checks supported languages
- MSBuild.exe (PID: 5672)
- 01 NOTIFICACION DEMANDA..exe (PID: 4788)
Reads the machine GUID from the registry
- MSBuild.exe (PID: 5672)
Reads Environment values
- MSBuild.exe (PID: 5672)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 7012)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AsyncRat
(PID) Process(5672) MSBuild.exe
C2 (1)melo2024.kozow.com
Ports (1)8000
Version| CRACKED BY https://t.me/xworm_v2
Options
AutoRunfalse
MutexAsyncMutex_6SI8OkPnk
InstallFolder%AppData%
Certificates
Cert1MIIE8jCCAtqgAwIBAgIQAOQb7nA/hP/L1XXxqdDJNzANBgkqhkiG9w0BAQ0FADAaMRgwFgYDVQQDDA9Bc3luY1JBVCBTZXJ2ZXIwIBcNMjMwNTI1MDUyMTIyWhgPOTk5OTEyMzEyMzU5NTlaMBoxGDAWBgNVBAMMD0FzeW5jUkFUIFNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAIykAVxs0s6rZ/dwP6ujJtpnj6RSsCsZN6Cfj1InZxSIswX+zNiKJys8xyLlyexoya3ebLp5gOSz...
Server_SignatureVDW90fot0UJzaNczUi0kDNApIr64dBioK/nQB9y7Rd4q0FrktdyhSFDErXPfi/Zv4rPByVXnBqci278oG8gV3+4cXIVpfkR/2UTL/5fU1P9Dfack2HTVz6T+MHXHn+RCdX7vIhK/tXRasVMoWCJKUsNlzrsXtHtu22EHiLSv+c51ch5zBK9anp3vPjKcb6Mz6K5lQGqrGxAlLvwx5/jjKJkCnUE7Bj8nGXsa8zrIBQYot50U8L7ZrMy4zOdruFDGUjQkuJNTIAkb7oh4zs5OWgA30M9thKnaCPS0MaLsvQ66...
Keys
AESef3a6e00a19a29644d1a0e1b56039abc50b3764a83e580ef7441c861f069fe20
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
Total processes
149
Monitored processes
11
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 528 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 944 | C:\WINDOWS\SysWOW64\cmd.exe | C:\Windows\SysWOW64\cmd.exe | — | 01 NOTIFICACION DEMANDA..exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
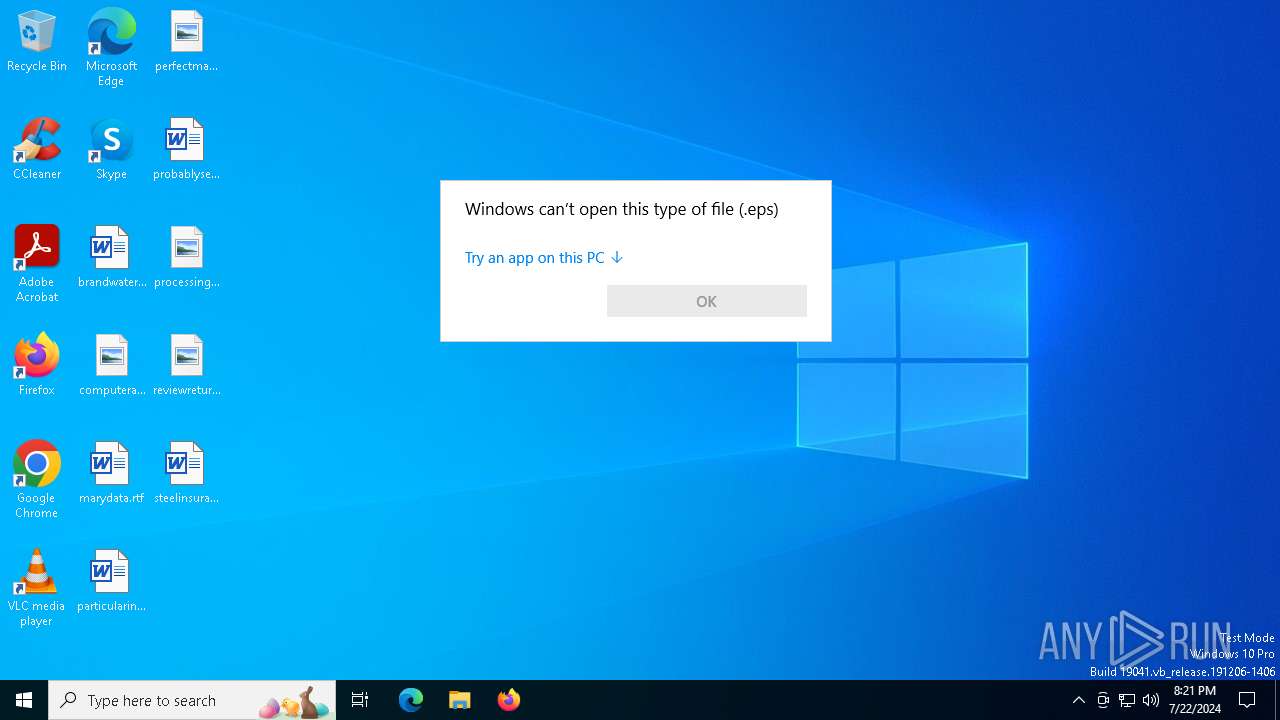
| 2668 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\AppData\Local\Temp\aigret.eps | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
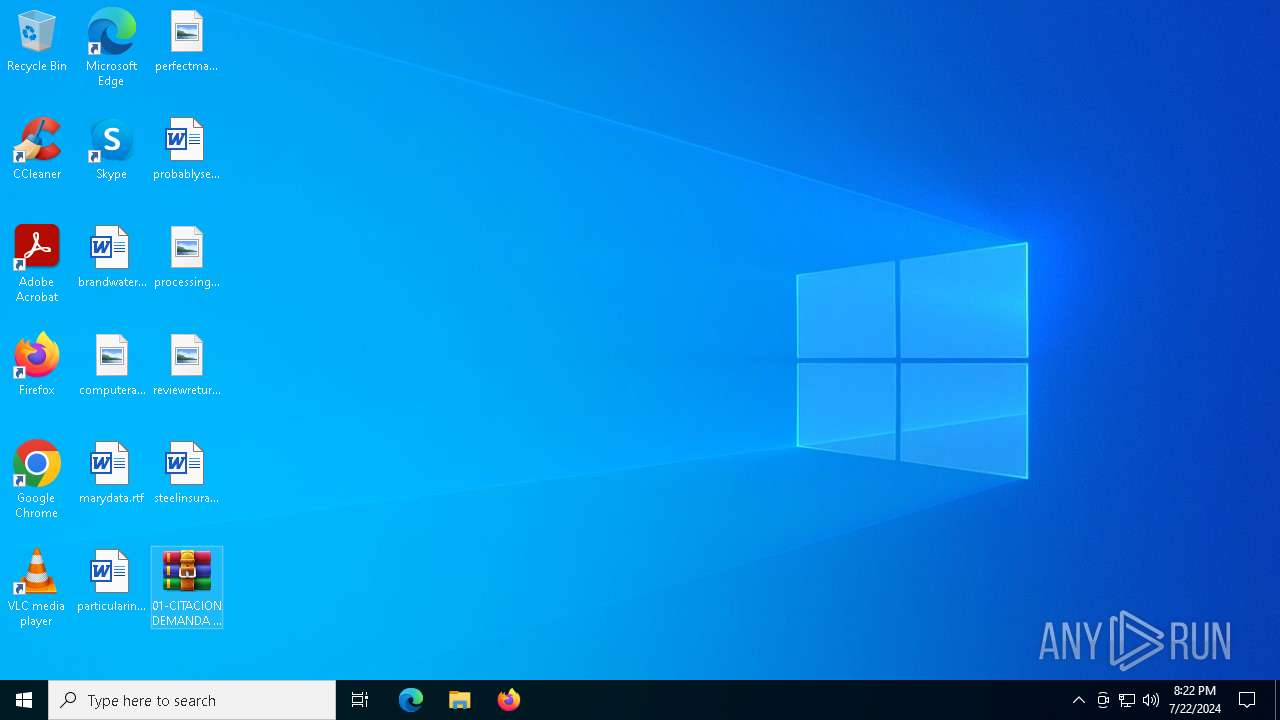
| 4788 | "C:\Users\admin\Desktop\01-CITACION DEMANDA EN SU CONTRA -JUZGADO PENAL 01 CIRCUITO ESPECIALIZADO EXTINXION-01\01-CITACION DEMANDA EN SU CONTRA -JUZGADO PENAL 01 CIRCUITO ESPECIALIZADO EXTINXION-01\01 NOTIFICACION DEMANDA..exe" | C:\Users\admin\Desktop\01-CITACION DEMANDA EN SU CONTRA -JUZGADO PENAL 01 CIRCUITO ESPECIALIZADO EXTINXION-01\01-CITACION DEMANDA EN SU CONTRA -JUZGADO PENAL 01 CIRCUITO ESPECIALIZADO EXTINXION-01\01 NOTIFICACION DEMANDA..exe | explorer.exe | ||||||||||||
User: admin Company: iTop Inc. Integrity Level: MEDIUM Description: DualSafe Password Manager Exit code: 1 Version: 1.4.0.3 Modules
| |||||||||||||||
| 4816 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4992 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5672 | C:\WINDOWS\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Version: 4.8.9037.0 built by: NET481REL1 Modules
AsyncRat(PID) Process(5672) MSBuild.exe C2 (1)melo2024.kozow.com Ports (1)8000 Version| CRACKED BY https://t.me/xworm_v2 Options AutoRunfalse MutexAsyncMutex_6SI8OkPnk InstallFolder%AppData% Certificates Cert1MIIE8jCCAtqgAwIBAgIQAOQb7nA/hP/L1XXxqdDJNzANBgkqhkiG9w0BAQ0FADAaMRgwFgYDVQQDDA9Bc3luY1JBVCBTZXJ2ZXIwIBcNMjMwNTI1MDUyMTIyWhgPOTk5OTEyMzEyMzU5NTlaMBoxGDAWBgNVBAMMD0FzeW5jUkFUIFNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAIykAVxs0s6rZ/dwP6ujJtpnj6RSsCsZN6Cfj1InZxSIswX+zNiKJys8xyLlyexoya3ebLp5gOSz... Server_SignatureVDW90fot0UJzaNczUi0kDNApIr64dBioK/nQB9y7Rd4q0FrktdyhSFDErXPfi/Zv4rPByVXnBqci278oG8gV3+4cXIVpfkR/2UTL/5fU1P9Dfack2HTVz6T+MHXHn+RCdX7vIhK/tXRasVMoWCJKUsNlzrsXtHtu22EHiLSv+c51ch5zBK9anp3vPjKcb6Mz6K5lQGqrGxAlLvwx5/jjKJkCnUE7Bj8nGXsa8zrIBQYot50U8L7ZrMy4zOdruFDGUjQkuJNTIAkb7oh4zs5OWgA30M9thKnaCPS0MaLsvQ66... Keys AESef3a6e00a19a29644d1a0e1b56039abc50b3764a83e580ef7441c861f069fe20 Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941 | |||||||||||||||
| 6328 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6468 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Manager Exit code: 3221226540 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
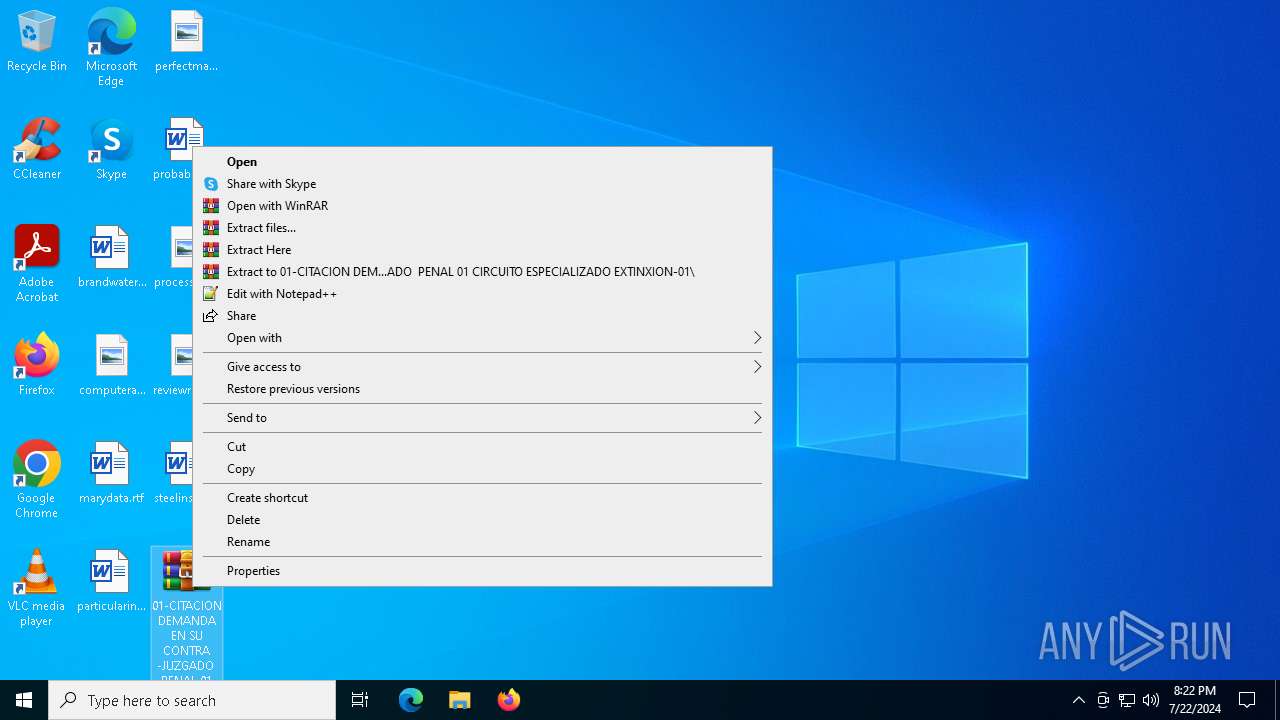
| 7008 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\01-CITACION DEMANDA EN SU CONTRA -JUZGADO PENAL 01 CIRCUITO ESPECIALIZADO EXTINXION-01.zip" "C:\Users\admin\Desktop\01-CITACION DEMANDA EN SU CONTRA -JUZGADO PENAL 01 CIRCUITO ESPECIALIZADO EXTINXION-01\" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
11 573
Read events
11 560
Write events
12
Delete events
1
Modification events
| (PID) Process: | (2668) OpenWith.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\Office16\oregres.dll,-205 |
Value: Word | |||
| (PID) Process: | (2668) OpenWith.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @wmploc.dll,-102 |
Value: Windows Media Player | |||
| (PID) Process: | (7008) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (7008) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (7008) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 1 | |||
| (PID) Process: | (7008) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7008) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7008) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7008) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7012) Taskmgr.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\TaskManager |
| Operation: | delete value | Name: | Preferences |
Value: | |||
Executable files
12
Suspicious files
8
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7008 | WinRAR.exe | C:\Users\admin\Desktop\01-CITACION DEMANDA EN SU CONTRA -JUZGADO PENAL 01 CIRCUITO ESPECIALIZADO EXTINXION-01\01-CITACION DEMANDA EN SU CONTRA -JUZGADO PENAL 01 CIRCUITO ESPECIALIZADO EXTINXION-01\barrette.accdb | binary | |
MD5:3DE728173727B206FE14724BA05A28C2 | SHA256:F923B85549CF4D2F87C11F4CDEB5ABB408974AEA8235AA68ACC849736EBDDE28 | |||
| 944 | cmd.exe | C:\Users\admin\AppData\Local\Temp\jcqlfwedwbge | — | |
MD5:— | SHA256:— | |||
| 7008 | WinRAR.exe | C:\Users\admin\Desktop\01-CITACION DEMANDA EN SU CONTRA -JUZGADO PENAL 01 CIRCUITO ESPECIALIZADO EXTINXION-01\01-CITACION DEMANDA EN SU CONTRA -JUZGADO PENAL 01 CIRCUITO ESPECIALIZADO EXTINXION-01\01 NOTIFICACION DEMANDA..exe | executable | |
MD5:5D52EF45B6E5BF144307A84C2AF1581B | SHA256:26A24D3B0206C6808615C7049859C2FE62C4DCD87E7858BE40AE8112B0482616 | |||
| 7008 | WinRAR.exe | C:\Users\admin\Desktop\01-CITACION DEMANDA EN SU CONTRA -JUZGADO PENAL 01 CIRCUITO ESPECIALIZADO EXTINXION-01\01-CITACION DEMANDA EN SU CONTRA -JUZGADO PENAL 01 CIRCUITO ESPECIALIZADO EXTINXION-01\aigret.eps | binary | |
MD5:B16A26AEE27CDC91B7F545E03877F9C0 | SHA256:B3ABDC2B792CB4B0160BDCC291DCB13B31078D852BD20AE01AE0908A0B46B72F | |||
| 7008 | WinRAR.exe | C:\Users\admin\Desktop\01-CITACION DEMANDA EN SU CONTRA -JUZGADO PENAL 01 CIRCUITO ESPECIALIZADO EXTINXION-01\01-CITACION DEMANDA EN SU CONTRA -JUZGADO PENAL 01 CIRCUITO ESPECIALIZADO EXTINXION-01\madexcept_.bpl | executable | |
MD5:98E59596EDD9B888D906C5409E515803 | SHA256:A6CA13AF74A64E4AB5EBB2D12B757CECF1A683CB9CD0AE7906DB1B4B2C8A90C0 | |||
| 7008 | WinRAR.exe | C:\Users\admin\Desktop\01-CITACION DEMANDA EN SU CONTRA -JUZGADO PENAL 01 CIRCUITO ESPECIALIZADO EXTINXION-01\01-CITACION DEMANDA EN SU CONTRA -JUZGADO PENAL 01 CIRCUITO ESPECIALIZADO EXTINXION-01\madbasic_.bpl | executable | |
MD5:E03A0056E75D3A5707BA199BC2EA701F | SHA256:7826395127E791A883359EA81308174700DA0AF8052CC9853B19FD29C2E4BADB | |||
| 7008 | WinRAR.exe | C:\Users\admin\Desktop\01-CITACION DEMANDA EN SU CONTRA -JUZGADO PENAL 01 CIRCUITO ESPECIALIZADO EXTINXION-01\01-CITACION DEMANDA EN SU CONTRA -JUZGADO PENAL 01 CIRCUITO ESPECIALIZADO EXTINXION-01\winrar-x64-701es.exe | executable | |
MD5:6FD5D917D1AFCA88894BF84C93E31AA3 | SHA256:F5A13BB8F154DB80FD9EBF38381F320DBC9741596EB6B910A18FE538DCF3A87F | |||
| 7008 | WinRAR.exe | C:\Users\admin\Desktop\01-CITACION DEMANDA EN SU CONTRA -JUZGADO PENAL 01 CIRCUITO ESPECIALIZADO EXTINXION-01\01-CITACION DEMANDA EN SU CONTRA -JUZGADO PENAL 01 CIRCUITO ESPECIALIZADO EXTINXION-01\vclx120.bpl | executable | |
MD5:3CB8F7606940C9B51C45EBAEB84AF728 | SHA256:2FEEC33D1E3F3D69C717F4528B8F7F5C030CAAE6FB37C2100CB0B5341367D053 | |||
| 7008 | WinRAR.exe | C:\Users\admin\Desktop\01-CITACION DEMANDA EN SU CONTRA -JUZGADO PENAL 01 CIRCUITO ESPECIALIZADO EXTINXION-01\01-CITACION DEMANDA EN SU CONTRA -JUZGADO PENAL 01 CIRCUITO ESPECIALIZADO EXTINXION-01\maddisAsm_.bpl | executable | |
MD5:EF3B47B2EA3884914C13C778FF29EB5B | SHA256:475F7CDFFD8ED4D6F52BD98AE2BB684F1C923A1BE2A692757A9AF788A39B1D87 | |||
| 7008 | WinRAR.exe | C:\Users\admin\Desktop\01-CITACION DEMANDA EN SU CONTRA -JUZGADO PENAL 01 CIRCUITO ESPECIALIZADO EXTINXION-01\01-CITACION DEMANDA EN SU CONTRA -JUZGADO PENAL 01 CIRCUITO ESPECIALIZADO EXTINXION-01\rtl120.bpl | executable | |
MD5:1681F93E11A7ED23612A55BCEF7F1023 | SHA256:7ED5369FCF0283EA18974C43DBFF80E6006B155B76DA7C72FA9619EB03F54CEF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
48
DNS requests
23
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3148 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2792 | RUXIMICS.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3108 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6012 | MoUsoCoreWorker.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4204 | svchost.exe | 4.209.32.67:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
6184 | slui.exe | 20.83.72.98:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4816 | slui.exe | 20.83.72.98:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5368 | SearchApp.exe | 2.20.142.129:443 | www.bing.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2284 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.kozow .com Domain |
5672 | MSBuild.exe | Domain Observed Used for C2 Detected | REMOTE [ANY.RUN] AsyncRAT SSL certificate |
5672 | MSBuild.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Malicious SSL Cert (AsyncRAT Server) |
5672 | MSBuild.exe | Domain Observed Used for C2 Detected | ET MALWARE Generic AsyncRAT Style SSL Cert |
5672 | MSBuild.exe | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] AsyncRAT Successful Connection |
1 ETPRO signatures available at the full report