| File name: | YBQOFHCX.msi |
| Full analysis: | https://app.any.run/tasks/dd730b05-c9a7-4e25-8402-1d8e4930e7d4 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | May 19, 2025, 20:07:46 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
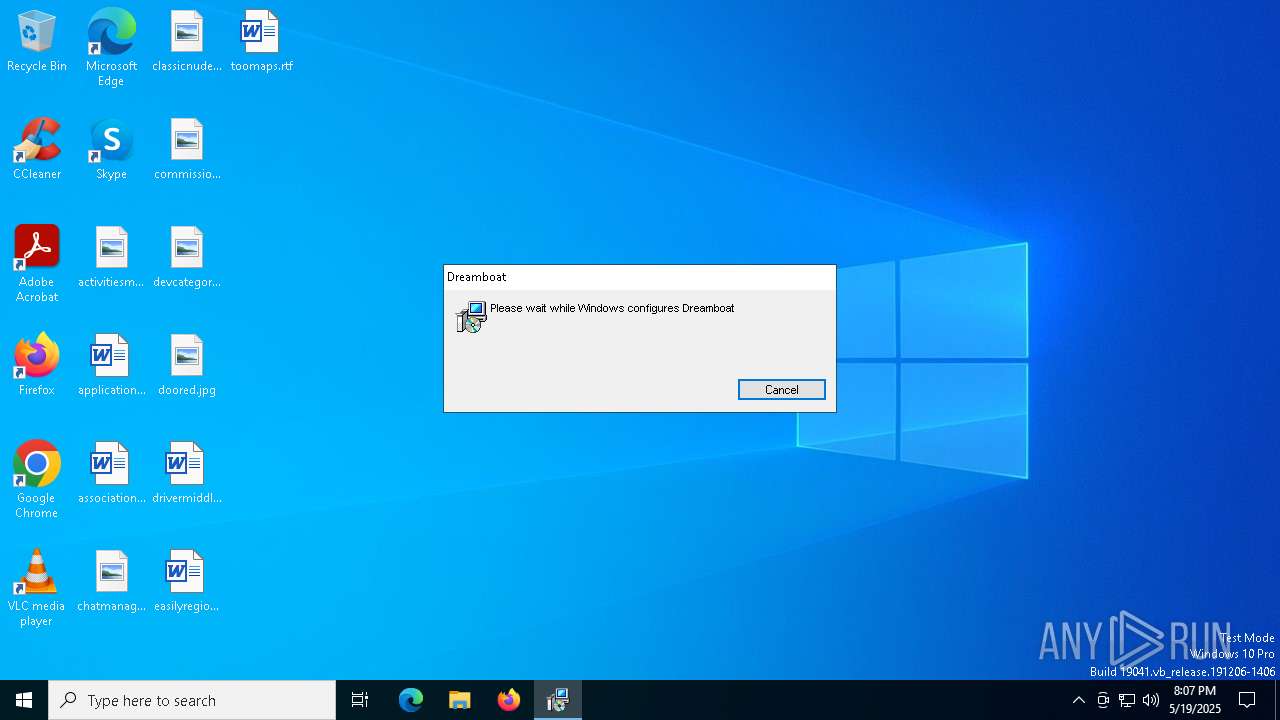
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, MSI Installer, Code page: 1252, Title: Installation Database, Subject: Dreamboat, Author: Salve Pupil, Keywords: Installer, Comments: This installer database contains the logic and data required to install Dreamboat., Template: Intel;1033, Revision Number: {D1A14993-475A-4072-88BE-E22241CC6BC1}, Create Time/Date: Sun May 18 15:25:28 2025, Last Saved Time/Date: Sun May 18 15:25:28 2025, Number of Pages: 500, Number of Words: 10, Name of Creating Application: WiX Toolset (4.0.0.0), Security: 2 |
| MD5: | B4D08697B7DE193A675E9F2AFF4A25F4 |
| SHA1: | 9157AE69B2BB045BAD06480AFBC6FD7886BEDA59 |
| SHA256: | B38F89519205F6183C4CE10141CBFD77AEB5406153A5440537A33A591D64E37D |
| SSDEEP: | 98304:fB8X+OyYDZeUGOOJ8URXZhfu0trfZOec/erjqIUKkzDhfKLI1e0baq8t+mORYUqj:i42eU |
MALICIOUS
GENERIC has been found (auto)
- msiexec.exe (PID: 5304)
- msiexec.exe (PID: 7216)
- LogicD.exe (PID: 6744)
ASYNCRAT has been detected (SURICATA)
- PlanExplorer.exe (PID: 6540)
SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 7268)
The process drops C-runtime libraries
- msiexec.exe (PID: 7216)
- LogicD.exe (PID: 6744)
Process drops legitimate windows executable
- msiexec.exe (PID: 7216)
- LogicD.exe (PID: 6744)
Executable content was dropped or overwritten
- LogicD.exe (PID: 6744)
- LogicD.exe (PID: 1324)
Starts itself from another location
- LogicD.exe (PID: 6744)
Uses WMIC.EXE to obtain computer system information
- PlanExplorer.exe (PID: 6540)
Contacting a server suspected of hosting an CnC
- PlanExplorer.exe (PID: 6540)
Connects to unusual port
- PlanExplorer.exe (PID: 6540)
INFO
The sample compiled with english language support
- msiexec.exe (PID: 5304)
- msiexec.exe (PID: 7216)
- LogicD.exe (PID: 6744)
- LogicD.exe (PID: 1324)
Checks supported languages
- msiexec.exe (PID: 7216)
Reads the computer name
- msiexec.exe (PID: 7216)
Manages system restore points
- SrTasks.exe (PID: 7228)
Executable content was dropped or overwritten
- msiexec.exe (PID: 7216)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Installer (100) |
|---|
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| Title: | Installation Database |
| Subject: | Dreamboat |
| Author: | Salve Pupil |
| Keywords: | Installer |
| Comments: | This installer database contains the logic and data required to install Dreamboat. |
| Template: | Intel;1033 |
| RevisionNumber: | {D1A14993-475A-4072-88BE-E22241CC6BC1} |
| CreateDate: | 2025:05:18 15:25:28 |
| ModifyDate: | 2025:05:18 15:25:28 |
| Pages: | 500 |
| Words: | 10 |
| Software: | WiX Toolset (4.0.0.0) |
| Security: | Read-only recommended |
Total processes
151
Monitored processes
14
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1324 | C:\ProgramData\ctDocker\LogicD.exe | C:\ProgramData\ctDocker\LogicD.exe | LogicD.exe | ||||||||||||
User: admin Company: AOMEI International Network Limited Integrity Level: MEDIUM Description: Splash Window Version: 4.0.0.0 Modules
| |||||||||||||||
| 2240 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | WMIC.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2420 | "wmic" computersystem get domain | C:\Windows\SysWOW64\wbem\WMIC.exe | — | PlanExplorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5304 | "C:\Windows\System32\msiexec.exe" /i C:\Users\admin\AppData\Local\Temp\YBQOFHCX.msi | C:\Windows\System32\msiexec.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6540 | C:\Users\admin\PlanExplorer.exe | C:\Users\admin\PlanExplorer.exe | LogicD.exe | ||||||||||||
User: admin Company: iTop Inc. Integrity Level: MEDIUM Description: Check Language Version: 1.0.0.20 Modules
| |||||||||||||||
| 6744 | "C:\Users\admin\AppData\Roaming\Inflictor\LogicD.exe" | C:\Users\admin\AppData\Roaming\Inflictor\LogicD.exe | msiexec.exe | ||||||||||||
User: admin Company: AOMEI International Network Limited Integrity Level: MEDIUM Description: Splash Window Exit code: 0 Version: 4.0.0.0 Modules
| |||||||||||||||
| 7152 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7216 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7228 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7268 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
6 845
Read events
6 580
Write events
247
Delete events
18
Modification events
| (PID) Process: | (7268) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000C91835B6F9C8DB01641C0000141D0000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7268) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000C91835B6F9C8DB01641C0000081D0000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7268) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000C91835B6F9C8DB01641C0000801C0000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7268) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000C91835B6F9C8DB01641C0000841C0000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7268) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 4800000000000000E6E039B6F9C8DB01641C0000801C0000E80300000000000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7268) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\11000001 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7268) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\11000001 |
| Operation: | write | Name: | Element |
Value: 0000000000000000000000000000000006000000000000004800000000000000715E5C2FA985EB1190A89A9B763584210000000000000000745E5C2FA985EB1190A89A9B7635842100000000000000000000000000000000 | |||
| (PID) Process: | (7268) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\12000002 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7268) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\12000002 |
| Operation: | write | Name: | Element |
Value: \EFI\Microsoft\Boot\bootmgfw.efi | |||
| (PID) Process: | (7268) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{5b970157-8568-11eb-b45c-806e6f6e6963}\Elements\11000001 |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
12
Suspicious files
25
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7216 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 7216 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:65E658FAF6C963CDCDC519C0BA4FC69C | SHA256:F4C9304BB503E4C23B279FD4C35713768CF1FF10D507BF0347CCA56076666851 | |||
| 7216 | msiexec.exe | C:\Windows\Installer\inprogressinstallinfo.ipi | binary | |
MD5:4FE48BF5806BB85358A82D1CD24ACD06 | SHA256:2BE1E3E5FEABB7C04F718A2C62A88DD89F9B5A652831C45D466CEE8FC101ED28 | |||
| 7216 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{66eed979-6ae8-46f3-91b1-83459ab8728a}_OnDiskSnapshotProp | binary | |
MD5:65E658FAF6C963CDCDC519C0BA4FC69C | SHA256:F4C9304BB503E4C23B279FD4C35713768CF1FF10D507BF0347CCA56076666851 | |||
| 7216 | msiexec.exe | C:\Windows\Temp\~DF4BE8505CC5D64EB4.TMP | binary | |
MD5:4FE48BF5806BB85358A82D1CD24ACD06 | SHA256:2BE1E3E5FEABB7C04F718A2C62A88DD89F9B5A652831C45D466CEE8FC101ED28 | |||
| 7216 | msiexec.exe | C:\Windows\Installer\MSIF4F.tmp | binary | |
MD5:F729CF3B41B230DDED83D503309152CF | SHA256:68B592347B4F86D49E2A4EB42C5E2447228F72F4336D4E8438F250B254C3F4B1 | |||
| 7216 | msiexec.exe | C:\Users\admin\AppData\Roaming\Inflictor\Cleagfe.qwy | binary | |
MD5:DCC51402C54E2444E1408F27A4B5CC2A | SHA256:35666471C7C18504FB67BB2DA3B5E31A2CE7215F376EABF597CDB8F9A793B7D7 | |||
| 7216 | msiexec.exe | C:\Windows\Temp\~DF86E646D0777C998F.TMP | binary | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
| 7216 | msiexec.exe | C:\Users\admin\AppData\Roaming\Inflictor\msvcp140.dll | executable | |
MD5:E9F00DD8746712610706CBEFFD8DF0BD | SHA256:4CB882621A3D1C6283570447F842801B396DB1B3DCD2E01C2F7002EFD66A0A97 | |||
| 7216 | msiexec.exe | C:\Users\admin\AppData\Roaming\Inflictor\Cled.ipus | binary | |
MD5:7EEF45F7162AC35D99202CB81151362F | SHA256:21CBF41C30E1A043C820AFBADA90277A57AD6F970F1F7D84421A18DB11A2C48E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
28
DNS requests
16
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.193:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2088 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2088 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5024 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.193:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.3:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
8020 | svchost.exe | 23.35.238.131:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6540 | PlanExplorer.exe | Domain Observed Used for C2 Detected | REMOTE [ANY.RUN] AsyncRAT SSL certificate |
6540 | PlanExplorer.exe | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] AsyncRAT Successful Connection |