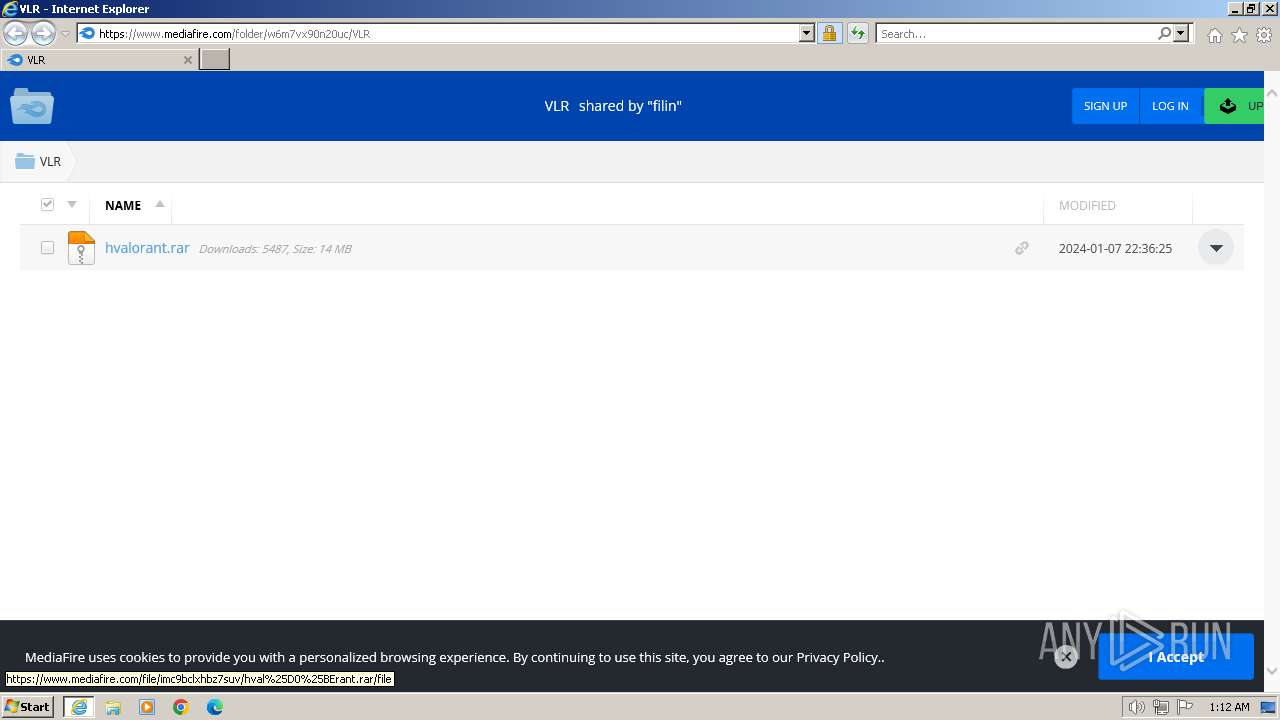
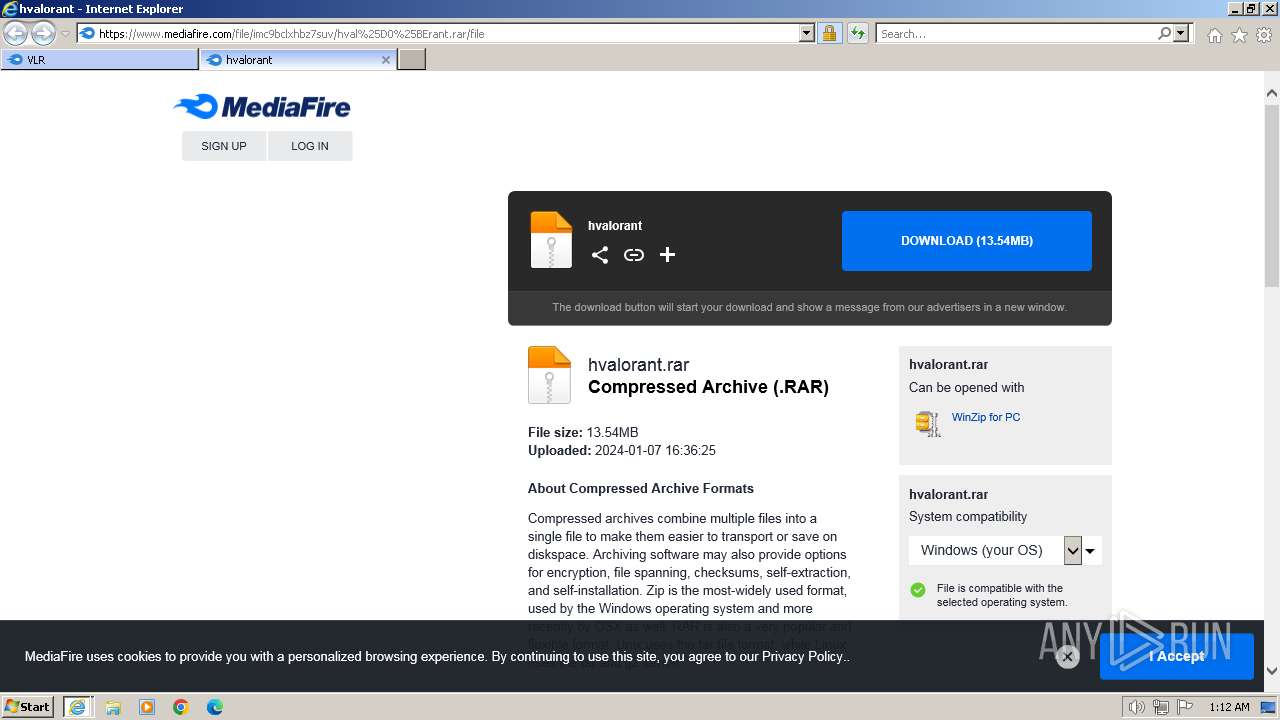
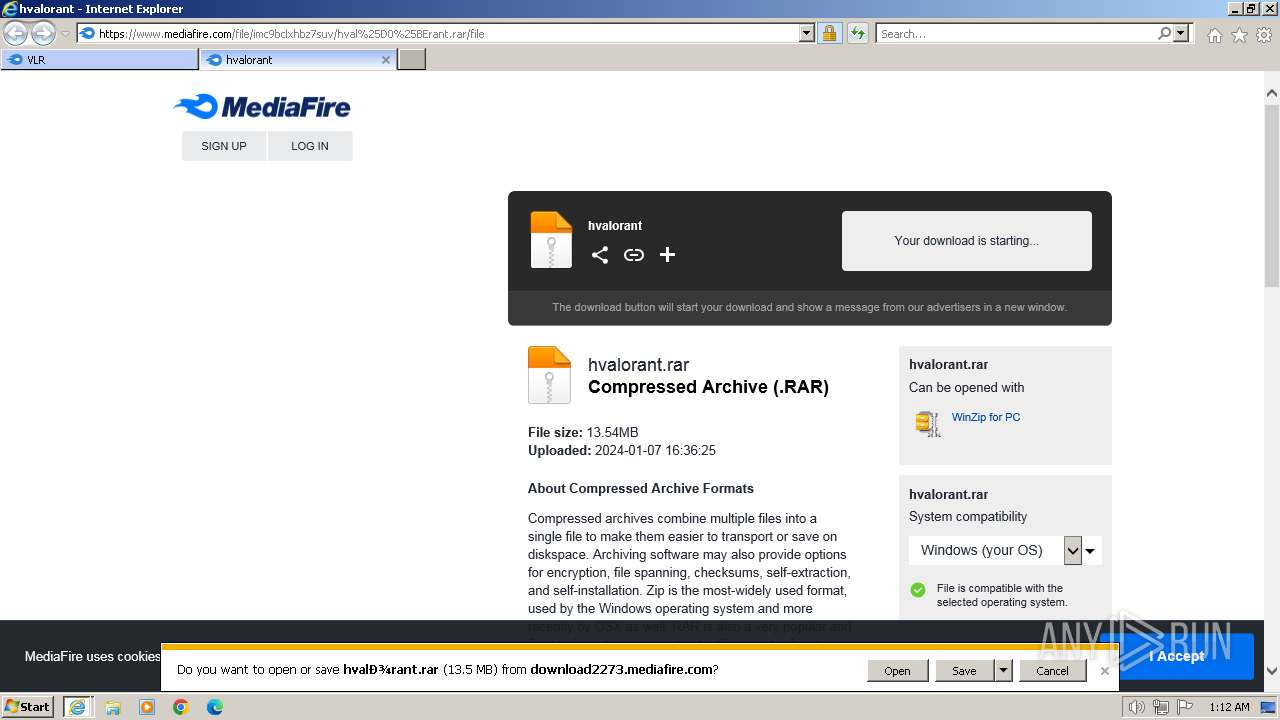
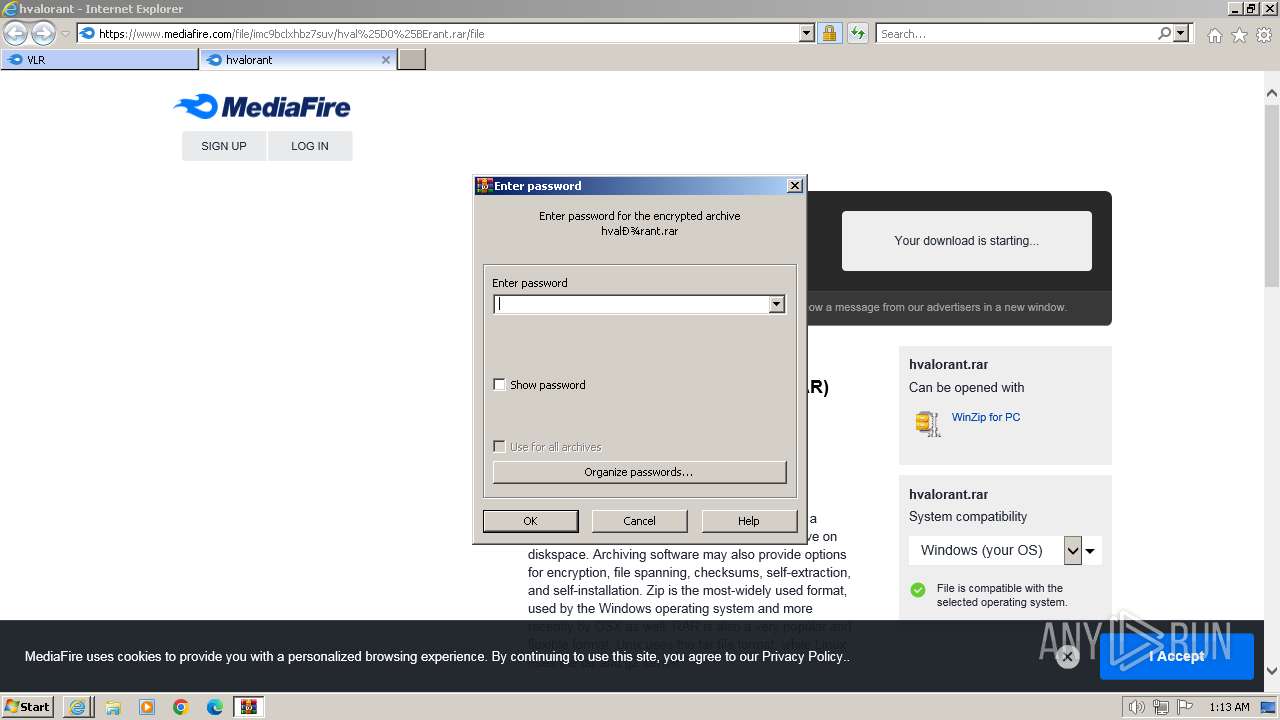
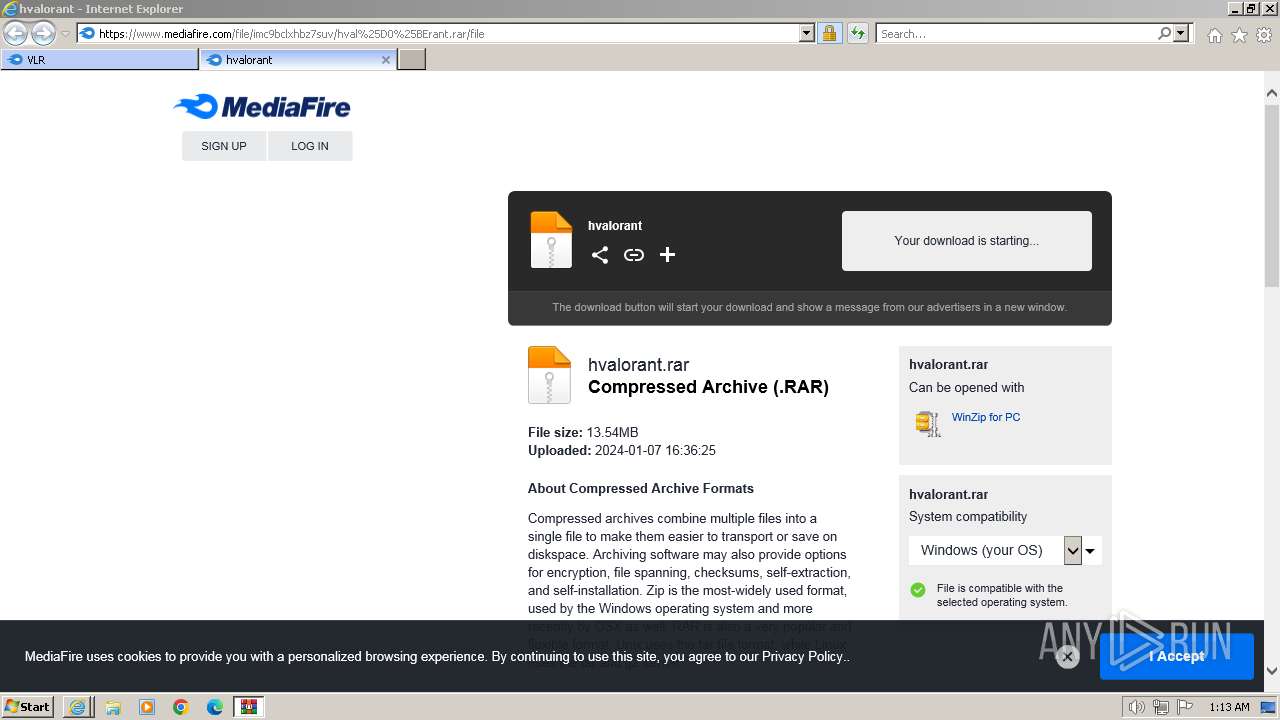
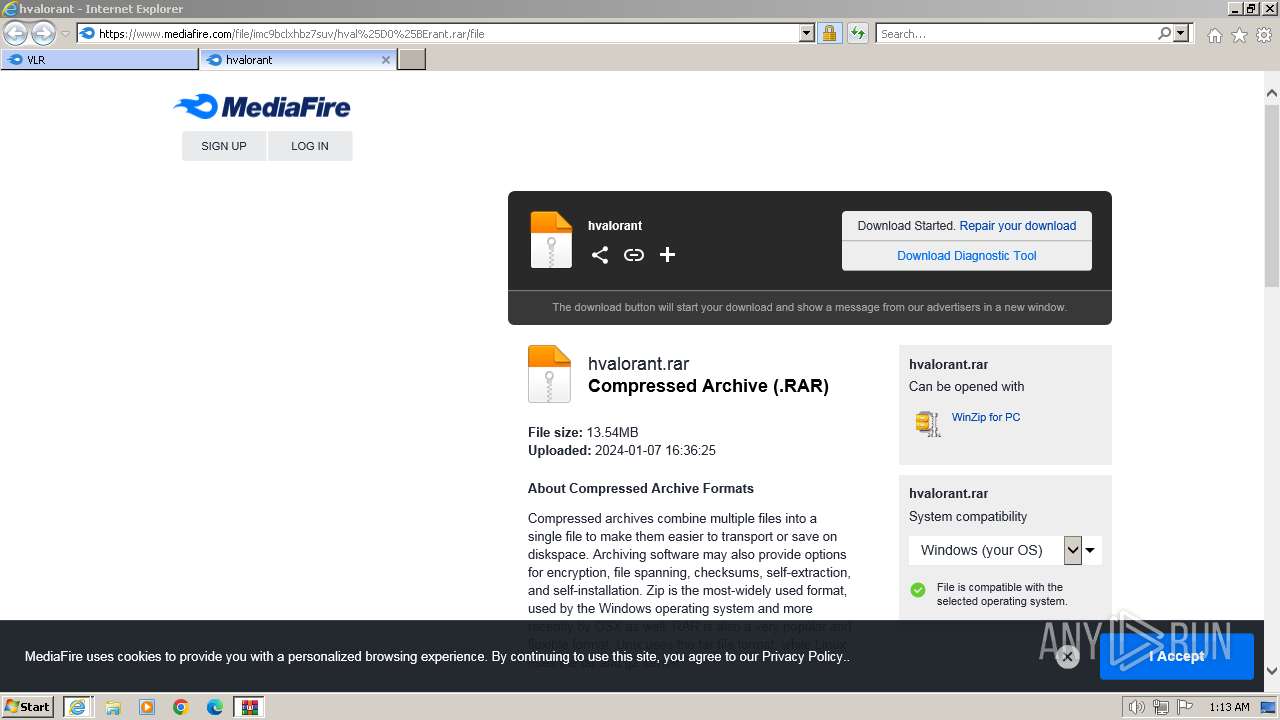
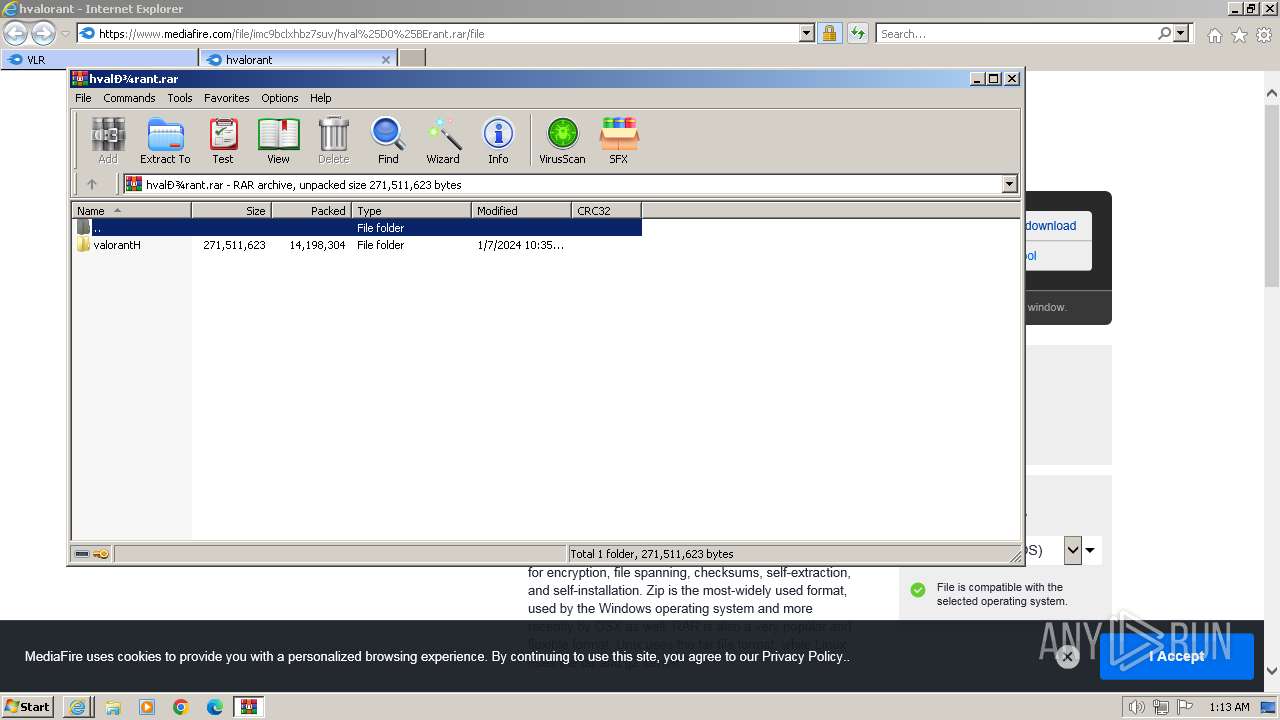
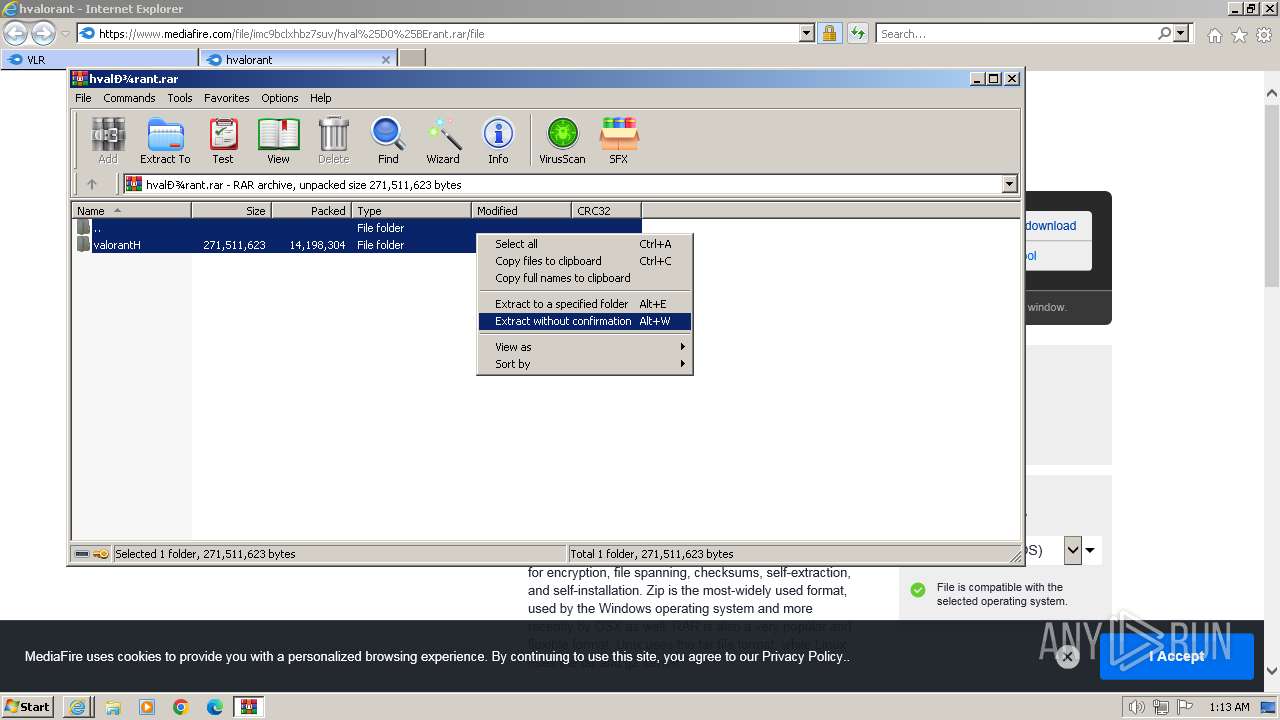
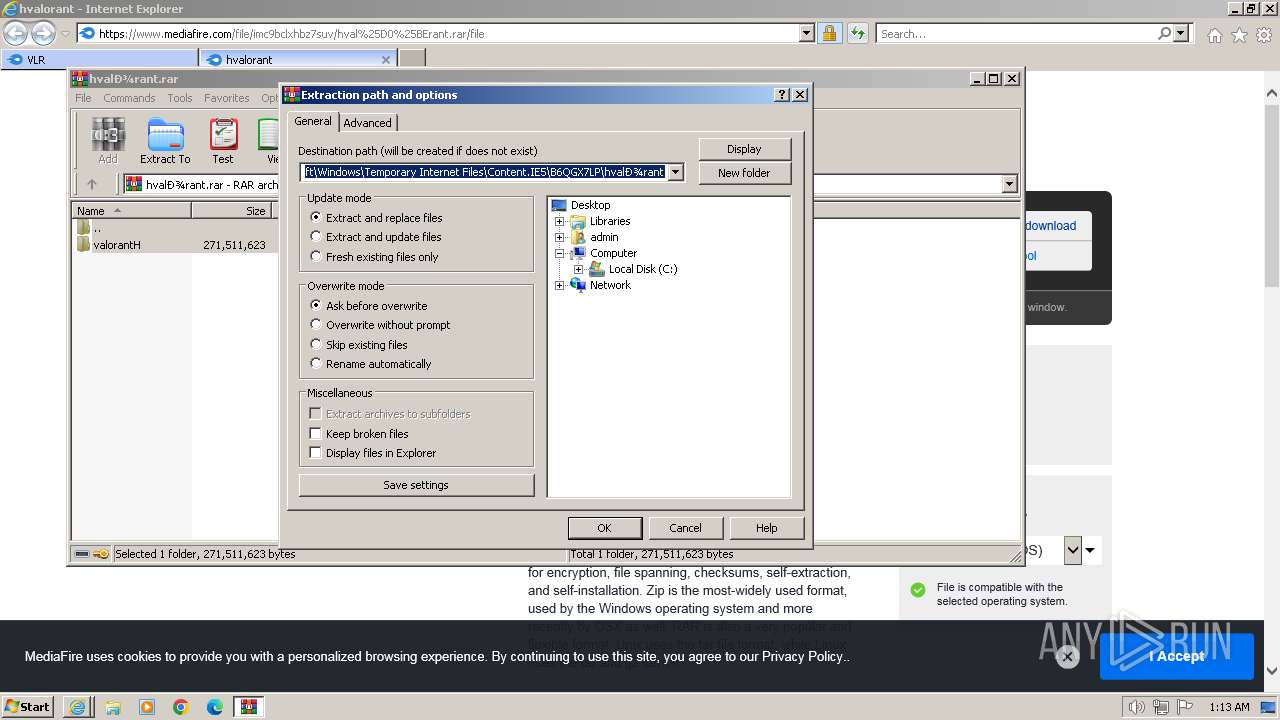
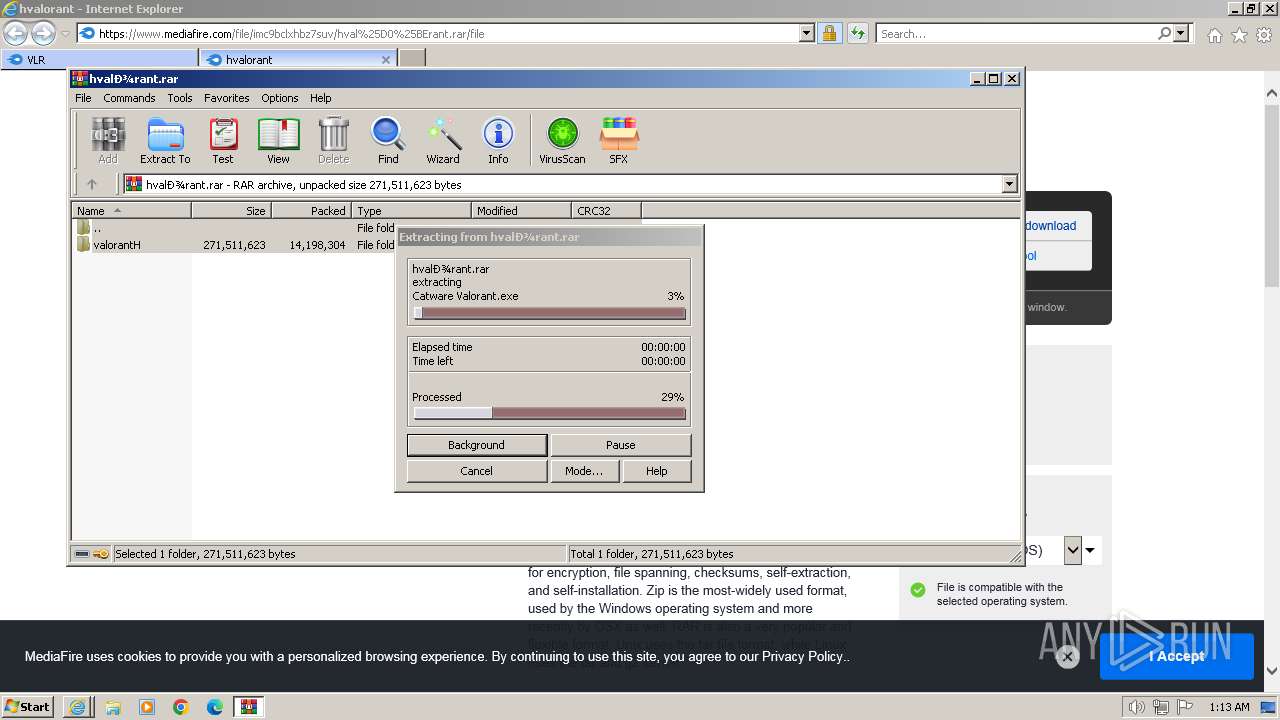
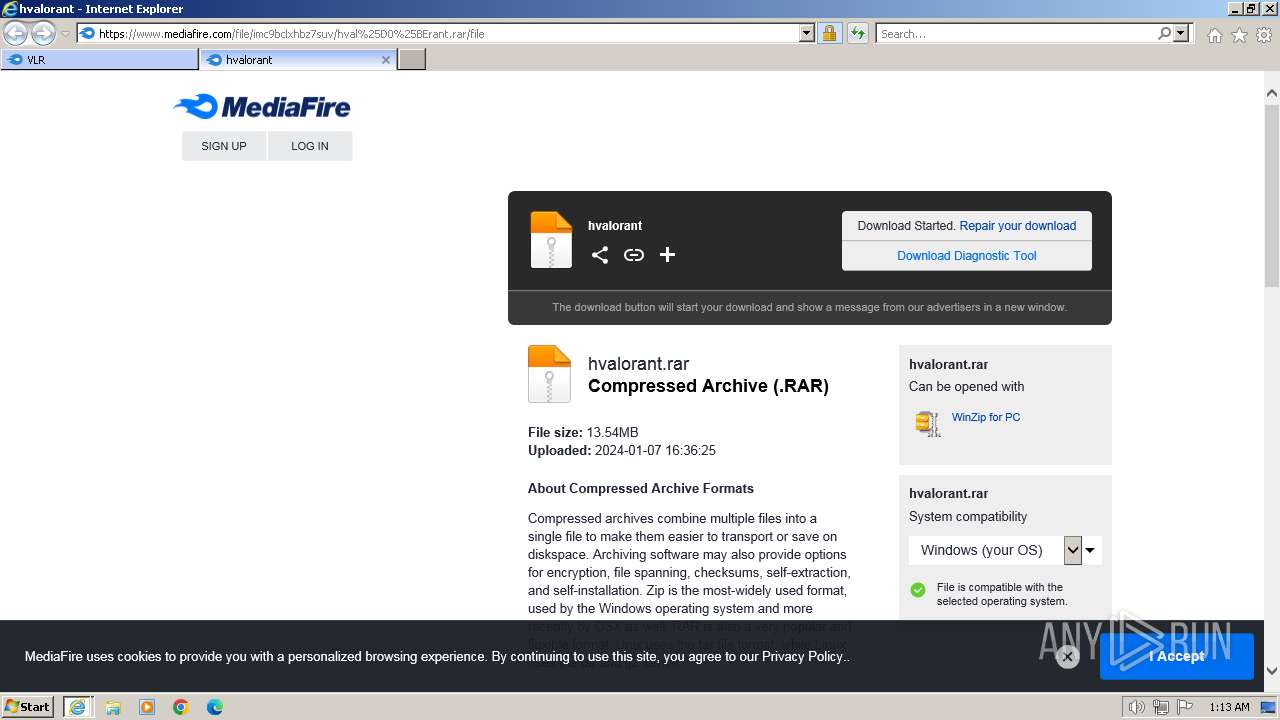
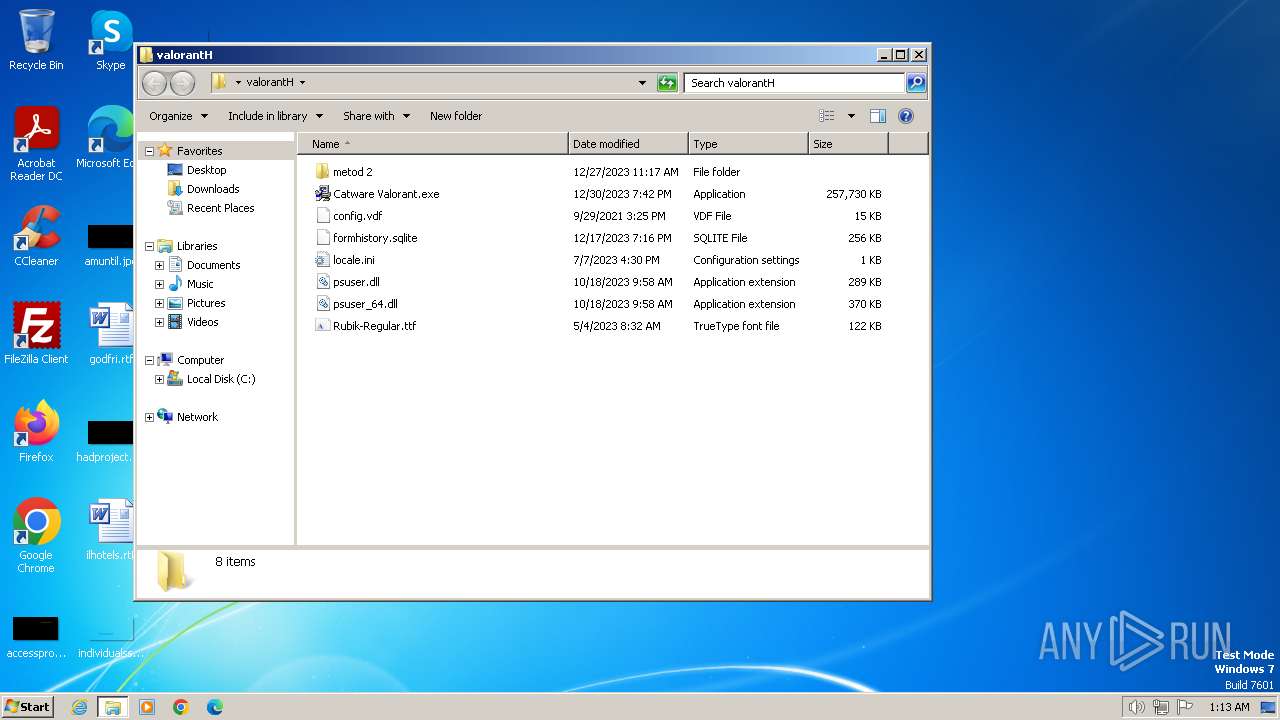
| URL: | https://www.mediafire.com/folder/w6m7vx90n20uc/VLR |
| Full analysis: | https://app.any.run/tasks/66b84d28-c25c-429d-987d-07f316275cef |
| Verdict: | Malicious activity |
| Threats: | RedLine Stealer is a malicious program that collects users’ confidential data from browsers, systems, and installed software. It also infects operating systems with other malware. |
| Analysis date: | January 13, 2024, 01:12:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 640183849E0311AC2A94BBDB4F62156B |
| SHA1: | 5921AB017EE6C633EDB2507ABEF4D489F78556DD |
| SHA256: | B36F01F2DF1A5BDFBADA26433DB91243B7A63081FB1BC5CFA7F7560281E5F60D |
| SSDEEP: | 3:N8DSLw3eGUbKgIgdkLozp3:2OLw3eG+dIHm3 |
MALICIOUS
REDLINE has been detected (SURICATA)
- vbc.exe (PID: 2852)
- vbc.exe (PID: 2656)
- vbc.exe (PID: 3312)
Steals credentials from Web Browsers
- vbc.exe (PID: 2852)
- vbc.exe (PID: 2656)
- vbc.exe (PID: 3312)
Create files in the Startup directory
- vbc.exe (PID: 2852)
Drops the executable file immediately after the start
- vbc.exe (PID: 2852)
Unusual connection from system programs
- vbc.exe (PID: 2656)
- vbc.exe (PID: 3312)
- vbc.exe (PID: 2852)
Actions looks like stealing of personal data
- vbc.exe (PID: 2852)
- vbc.exe (PID: 2656)
- vbc.exe (PID: 3312)
SUSPICIOUS
The process executes VB scripts
- Catware Valorant.exe (PID: 2860)
- Catware Valorant.exe (PID: 3056)
- Catware Valorant.exe (PID: 3268)
Reads browser cookies
- vbc.exe (PID: 2852)
- vbc.exe (PID: 2656)
- vbc.exe (PID: 3312)
Executable content was dropped or overwritten
- vbc.exe (PID: 2852)
Searches for installed software
- vbc.exe (PID: 2852)
- vbc.exe (PID: 2656)
- vbc.exe (PID: 3312)
Reads the Internet Settings
- vbc.exe (PID: 2852)
Connects to unusual port
- vbc.exe (PID: 2656)
- vbc.exe (PID: 3312)
- vbc.exe (PID: 2852)
INFO
Application launched itself
- iexplore.exe (PID: 2040)
Manual execution by a user
- Catware Valorant.exe (PID: 2860)
- Catware Valorant.exe (PID: 3056)
- Catware Valorant.exe (PID: 3268)
Checks supported languages
- Catware Valorant.exe (PID: 2860)
- vbc.exe (PID: 2852)
- vbc.exe (PID: 2656)
- Catware Valorant.exe (PID: 3056)
- qemu-ga.exe (PID: 3016)
- Catware Valorant.exe (PID: 3268)
- vbc.exe (PID: 3312)
Reads the computer name
- Catware Valorant.exe (PID: 2860)
- vbc.exe (PID: 2852)
- Catware Valorant.exe (PID: 3056)
- qemu-ga.exe (PID: 3016)
- vbc.exe (PID: 2656)
- Catware Valorant.exe (PID: 3268)
- vbc.exe (PID: 3312)
The process uses the downloaded file
- iexplore.exe (PID: 2040)
- WinRAR.exe (PID: 1924)
Reads the machine GUID from the registry
- Catware Valorant.exe (PID: 2860)
- vbc.exe (PID: 2852)
- Catware Valorant.exe (PID: 3056)
- vbc.exe (PID: 2656)
- Catware Valorant.exe (PID: 3268)
- vbc.exe (PID: 3312)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1924)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 1924)
Reads Environment values
- vbc.exe (PID: 2852)
- vbc.exe (PID: 2656)
- vbc.exe (PID: 3312)
Reads product name
- vbc.exe (PID: 2852)
- vbc.exe (PID: 2656)
- vbc.exe (PID: 3312)
Creates files or folders in the user directory
- vbc.exe (PID: 2852)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
52
Monitored processes
10
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 864 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2040 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1924 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\hvalоrant.rar" | C:\Program Files\WinRAR\WinRAR.exe | iexplore.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2040 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://www.mediafire.com/folder/w6m7vx90n20uc/VLR" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2656 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\vbc.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\vbc.exe | Catware Valorant.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual Basic Command Line Compiler Exit code: 0 Version: 14.8.3761.0 Modules
| |||||||||||||||
| 2852 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\vbc.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\vbc.exe | Catware Valorant.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual Basic Command Line Compiler Exit code: 0 Version: 14.8.3761.0 Modules
| |||||||||||||||
| 2860 | "C:\Users\admin\Desktop\valоrantH\Catware Valorant.exe" | C:\Users\admin\Desktop\valоrantH\Catware Valorant.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3016 | "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\qemu-ga.exe" | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\qemu-ga.exe | — | vbc.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: qemu-ga Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3056 | "C:\Users\admin\Desktop\valоrantH\Catware Valorant.exe" | C:\Users\admin\Desktop\valоrantH\Catware Valorant.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3268 | "C:\Users\admin\Desktop\valоrantH\Catware Valorant.exe" | C:\Users\admin\Desktop\valоrantH\Catware Valorant.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3312 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\vbc.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\vbc.exe | Catware Valorant.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Visual Basic Command Line Compiler Exit code: 0 Version: 14.8.3761.0 Modules
| |||||||||||||||
Total events
32 727
Read events
32 591
Write events
129
Delete events
7
Modification events
| (PID) Process: | (2040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (2040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (2040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (2040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
4
Suspicious files
95
Text files
154
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 864 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\ID4ERY6K.txt | text | |
MD5:84BB503CF2CE3A57D662C1F7E06C00FD | SHA256:91405AB683BBA1F2E104F3F5A754C9FB046F4A8A1A166454DEBE8879965F756D | |||
| 864 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 864 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\XV9KCFAY.txt | text | |
MD5:77CC58D35CD53A701D01F9A359F84D47 | SHA256:A4BDAC7E307554514251E48458789F2B943587C3DA12CE2A37DB6347F096AF44 | |||
| 864 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B2FAF7692FD9FFBD64EDE317E42334BA_D7393C8F62BDE4D4CB606228BC7A711E | binary | |
MD5:6CFBDC30F8FA4B813C6FAC8DFE74AABB | SHA256:B4020DC65FB348C74B242520D63C9389BCBD62E79FC570E785E3113893E56BA7 | |||
| 864 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\07CEF2F654E3ED6050FFC9B6EB844250_BACC6CD2B29F18349081C9FD2343833B | binary | |
MD5:5D5C86E349E7072C1B15BF8E25A77DAC | SHA256:4EBDC98DA02DC63E9273A2911C3218403F309B1431E48AA1A1A5AC87CD57BDB8 | |||
| 864 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\mf_logo_u1_full_color[1].svg | image | |
MD5:E09B5AF507BD602AD839B261FD897170 | SHA256:BFCC5BC8242D357752657942690541BB3E4B907384AF1C56586F6466D7116DB2 | |||
| 864 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\VLR[1].htm | html | |
MD5:E5BEA4E0A784906EE915AA4644139549 | SHA256:9BE68CE0548B4C010F578D48B61E01D0E9850EA8CC795A64E2D232CF452C5753 | |||
| 864 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\mf_logo_u1_full_color_reversed[1].svg | image | |
MD5:BCD95CFB6B9474DBA955AAB2CFE0432B | SHA256:1A0EC73A3CA7F354865D6B95401C50627FDF5A9B0DA763A6F75FA818FD775B55 | |||
| 864 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\myfiles.css_121918[1].css | text | |
MD5:6DD7BBF6331BE11194A0DD9CFB19AC6B | SHA256:B4714676C161538A3B43173D17E0958A43F7CCABB65E6061A1A117CA7F54BAAB | |||
| 864 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B2FAF7692FD9FFBD64EDE317E42334BA_D7393C8F62BDE4D4CB606228BC7A711E | binary | |
MD5:6DF4B06A2B6A15932B5C7868FEC2B4E3 | SHA256:1BC4686BEAA67FF6E2A285CA18BEC0E7DEE6E82D156E634C658A832FE8BDAD39 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
37
TCP/UDP connections
105
DNS requests
49
Threats
13
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
864 | iexplore.exe | GET | 200 | 216.58.212.131:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
864 | iexplore.exe | GET | 200 | 216.58.212.131:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQD7vSzSbK8Z0QnHSrEZ7mPf | unknown | binary | 472 b | unknown |
864 | iexplore.exe | GET | 200 | 216.58.212.131:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCECO0Y37WzHRLPzhV9vNju | unknown | binary | 472 b | unknown |
864 | iexplore.exe | GET | 200 | 216.58.212.131:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
864 | iexplore.exe | GET | 200 | 18.245.39.64:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | unknown | binary | 1.49 Kb | unknown |
864 | iexplore.exe | GET | 200 | 216.58.212.131:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCECbzjAowsPTyEMLulIc7EGw%3D | unknown | binary | 471 b | unknown |
864 | iexplore.exe | GET | 200 | 216.58.212.131:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCAPCRpfvazdAnzYNtm9aj3 | unknown | binary | 472 b | unknown |
864 | iexplore.exe | GET | 200 | 18.245.39.64:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEkpLy9ROx7U76vGUhC06D6E%3D | unknown | binary | 1.37 Kb | unknown |
864 | iexplore.exe | GET | 200 | 216.58.212.131:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCc21SZGmxMgAqM79mihzX3 | unknown | binary | 472 b | unknown |
864 | iexplore.exe | GET | 200 | 143.204.178.12:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | unknown | binary | 2.02 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
864 | iexplore.exe | 104.16.113.74:443 | www.mediafire.com | CLOUDFLARENET | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
864 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
864 | iexplore.exe | 104.18.38.233:80 | ocsp.comodoca.com | CLOUDFLARENET | — | shared |
864 | iexplore.exe | 172.64.149.23:80 | ocsp.comodoca.com | CLOUDFLARENET | US | unknown |
864 | iexplore.exe | 104.16.114.74:443 | www.mediafire.com | CLOUDFLARENET | — | unknown |
864 | iexplore.exe | 216.58.212.131:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
864 | iexplore.exe | 172.217.16.202:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.mediafire.com |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
static.mediafire.com |
| shared |
fonts.googleapis.com |
| whitelisted |
www.google.com |
| whitelisted |
ajax.googleapis.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
1080 | svchost.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain in DNS Lookup (download .mediafire .com) |
2852 | vbc.exe | Potentially Bad Traffic | ET INFO Microsoft net.tcp Connection Initialization Activity |
2852 | vbc.exe | A Network Trojan was detected | ET MALWARE [ANY.RUN] RedLine Stealer/MetaStealer Family Related (MC-NMF Authorization) |
2852 | vbc.exe | A Network Trojan was detected | ET MALWARE Redline Stealer/MetaStealer Family Activity (Response) |
2852 | vbc.exe | Successful Credential Theft Detected | SUSPICIOUS [ANY.RUN] Clear Text Password Exfiltration Atempt |
2852 | vbc.exe | Successful Credential Theft Detected | SUSPICIOUS [ANY.RUN] Clear Text Password Exfiltration Atempt |
2656 | vbc.exe | Potentially Bad Traffic | ET INFO Microsoft net.tcp Connection Initialization Activity |
2656 | vbc.exe | A Network Trojan was detected | ET MALWARE [ANY.RUN] RedLine Stealer/MetaStealer Family Related (MC-NMF Authorization) |
2656 | vbc.exe | A Network Trojan was detected | ET MALWARE Redline Stealer/MetaStealer Family Activity (Response) |