| File name: | Valorant Bypass Cheat.rar |
| Full analysis: | https://app.any.run/tasks/d2c454cd-78c3-4f48-886a-654b836d6615 |
| Verdict: | Malicious activity |
| Threats: | Quasar is a very popular RAT in the world thanks to its code being available in open-source. This malware can be used to control the victim’s computer remotely. |
| Analysis date: | April 20, 2020, 15:06:28 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | A650E102F4C798AF75AAEB1FBFA480E4 |
| SHA1: | 9ADE8A3E80A1154E58F92A221F0BB7FBA4B54CB8 |
| SHA256: | B3150C91823FD478EBFA4A2A66A09EEB63FDE1334DA98915D9C5C85782780150 |
| SSDEEP: | 3072:DWt4k9r2e+6V19fEEffdP8IPaiTEJcBXn2338zlHSWCM3W:qC22ShfEE3XvwJsXu38hPBW |
MALICIOUS
Application was dropped or rewritten from another process
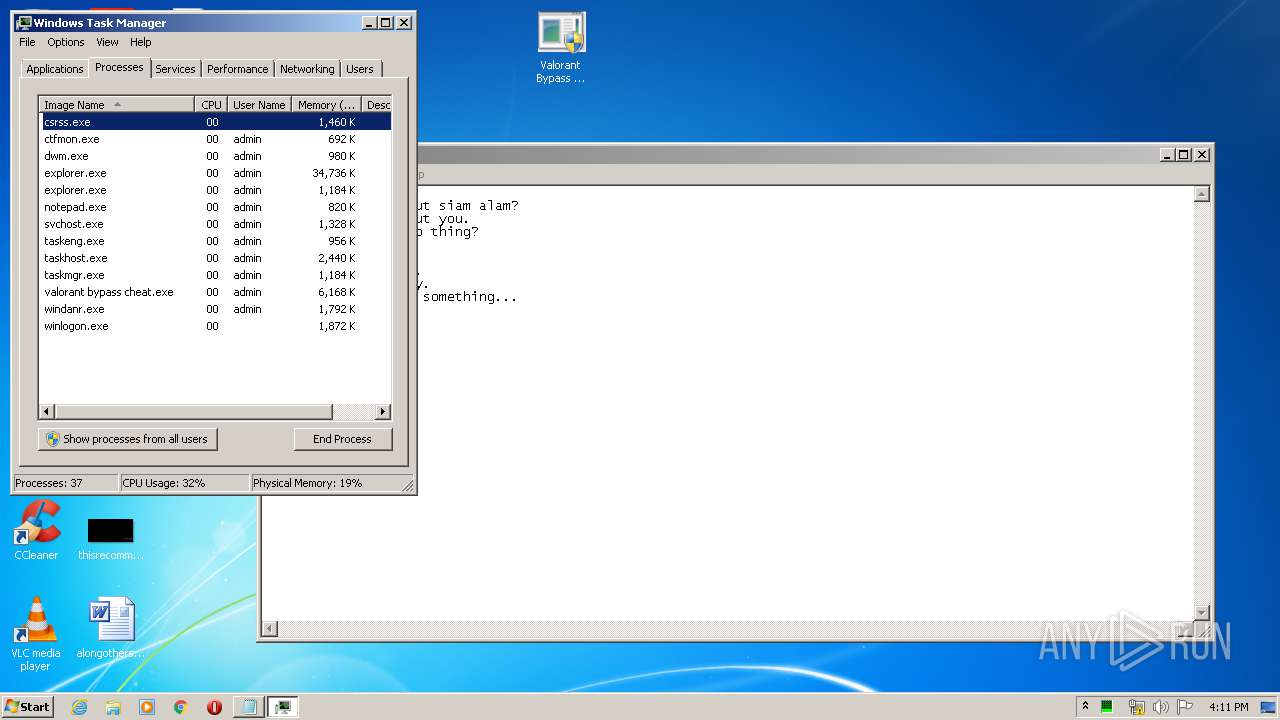
- Valorant Bypass Cheat.exe (PID: 2952)
- Valorant Bypass Cheat.exe (PID: 3900)
- Valorant Bypass Cheat.exe (PID: 3260)
- Valorant Bypass Cheat.exe (PID: 3640)
- valorant bypass cheat.exe (PID: 2756)
- icsys.icn.exe (PID: 2896)
- explorer.exe (PID: 4072)
- spoolsv.exe (PID: 2916)
- svchost.exe (PID: 940)
- spoolsv.exe (PID: 2064)
Drops/Copies Quasar RAT executable
- Valorant Bypass Cheat.exe (PID: 2952)
Changes the autorun value in the registry
- explorer.exe (PID: 4072)
- svchost.exe (PID: 940)
Uses Task Scheduler to autorun other applications
- valorant bypass cheat.exe (PID: 2756)
Uses Task Scheduler to run other applications
- svchost.exe (PID: 940)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 4052)
- schtasks.exe (PID: 2420)
- schtasks.exe (PID: 3728)
- schtasks.exe (PID: 3776)
- schtasks.exe (PID: 2356)
- schtasks.exe (PID: 2764)
QUASAR was detected
- valorant bypass cheat.exe (PID: 2756)
SUSPICIOUS
Creates files in the Windows directory
- Valorant Bypass Cheat.exe (PID: 2952)
- icsys.icn.exe (PID: 2896)
- explorer.exe (PID: 4072)
- spoolsv.exe (PID: 2916)
Executable content was dropped or overwritten
- Valorant Bypass Cheat.exe (PID: 2952)
- icsys.icn.exe (PID: 2896)
- explorer.exe (PID: 4072)
- spoolsv.exe (PID: 2916)
Starts application with an unusual extension
- Valorant Bypass Cheat.exe (PID: 2952)
Starts itself from another location
- Valorant Bypass Cheat.exe (PID: 2952)
- icsys.icn.exe (PID: 2896)
- spoolsv.exe (PID: 2916)
- svchost.exe (PID: 940)
Removes files from Windows directory
- icsys.icn.exe (PID: 2896)
- explorer.exe (PID: 4072)
- spoolsv.exe (PID: 2916)
Creates executable files which already exist in Windows
- icsys.icn.exe (PID: 2896)
- spoolsv.exe (PID: 2916)
Creates or modifies windows services
- svchost.exe (PID: 940)
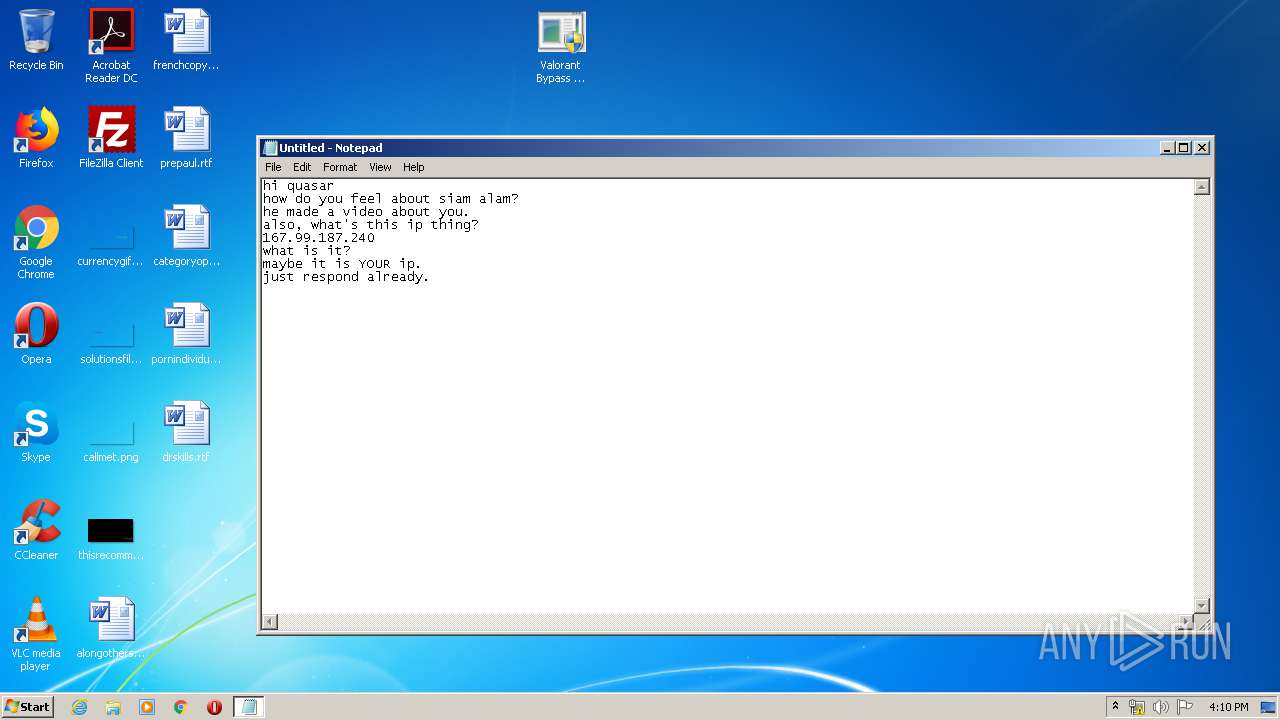
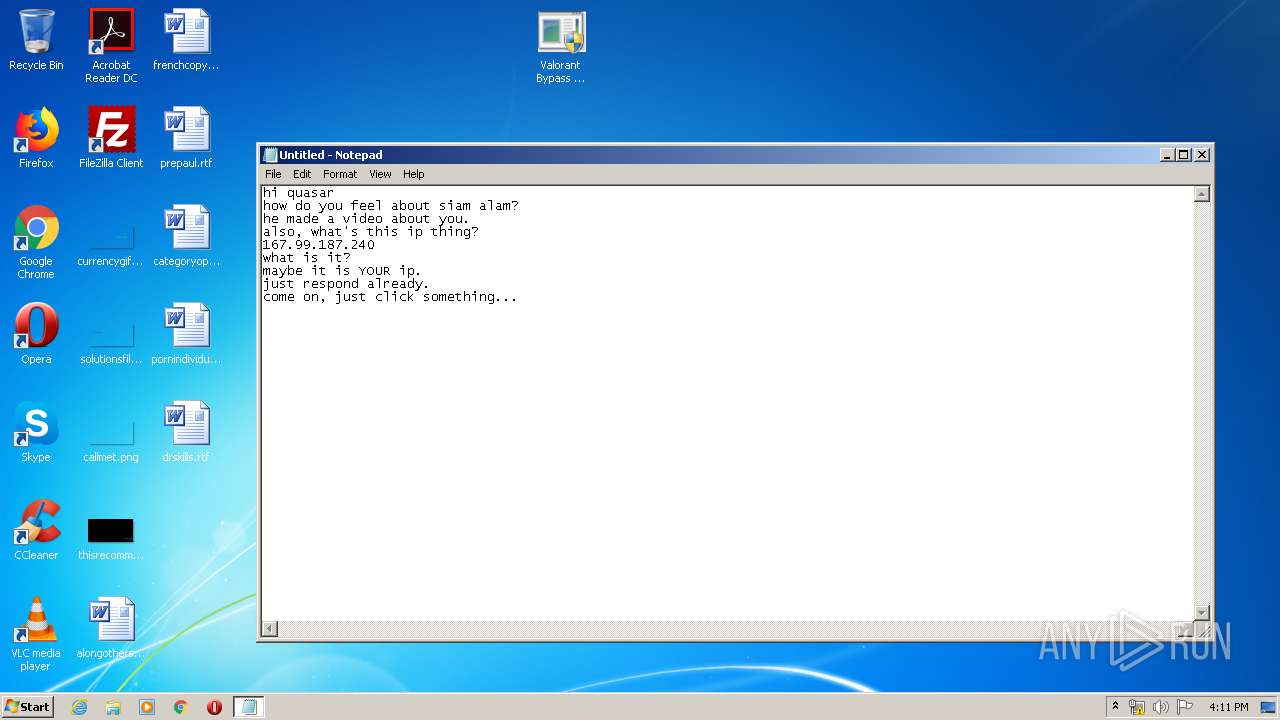
Checks for external IP
- valorant bypass cheat.exe (PID: 2756)
Connects to unusual port
- valorant bypass cheat.exe (PID: 2756)
INFO
Manual execution by user
- Valorant Bypass Cheat.exe (PID: 3900)
- Valorant Bypass Cheat.exe (PID: 2952)
- Valorant Bypass Cheat.exe (PID: 3640)
- Valorant Bypass Cheat.exe (PID: 3260)
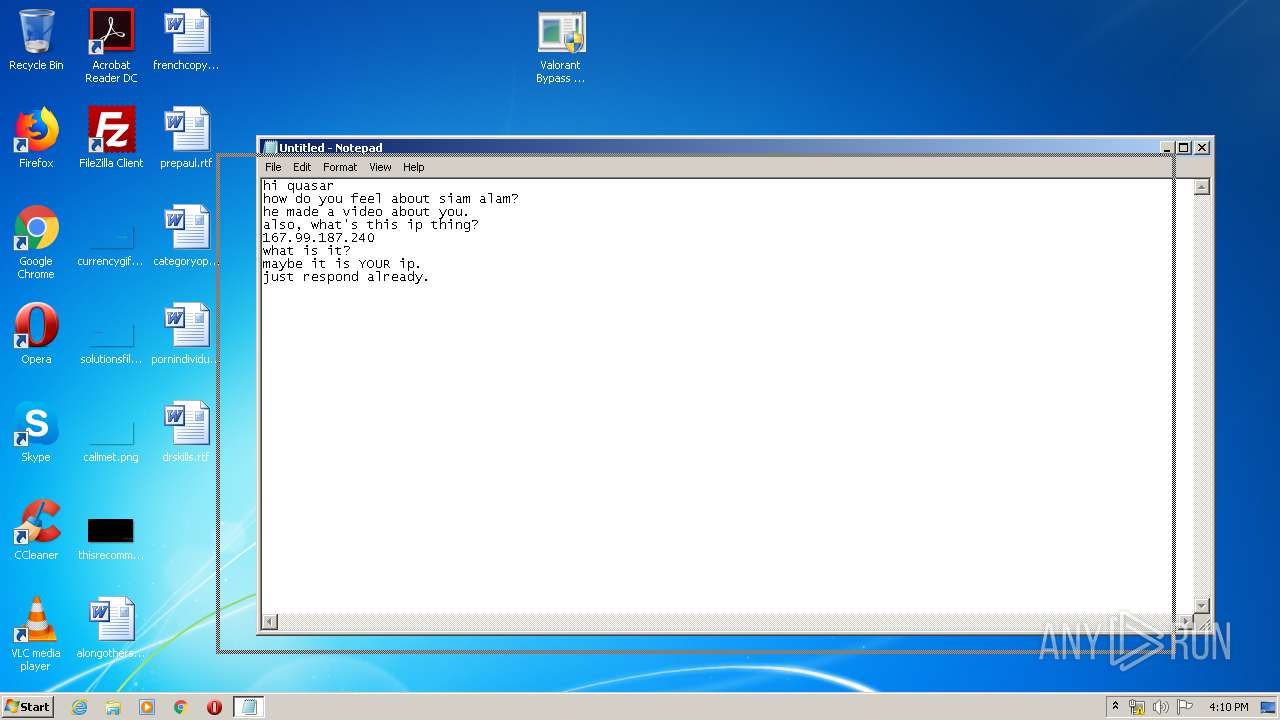
- notepad.exe (PID: 2564)
- taskmgr.exe (PID: 3616)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
64
Monitored processes
19
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 940 | c:\windows\resources\svchost.exe | c:\windows\resources\svchost.exe | spoolsv.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 2064 | c:\windows\resources\spoolsv.exe PR | c:\windows\resources\spoolsv.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 2356 | "schtasks" /create /tn "nitro" /sc ONLOGON /tr "c:\users\admin\desktop\valorant bypass cheat.exe " /rl HIGHEST /f | C:\Windows\system32\schtasks.exe | — | valorant bypass cheat.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2420 | schtasks /create /tn "svchost" /tr "c:\windows\resources\svchost.exe" /sc daily /st 16:10 /f | C:\Windows\system32\schtasks.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2564 | "C:\Windows\system32\notepad.exe" | C:\Windows\system32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2756 | "c:\users\admin\desktop\valorant bypass cheat.exe " | c:\users\admin\desktop\valorant bypass cheat.exe | Valorant Bypass Cheat.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Version: 1.3.0.0 Modules
| |||||||||||||||
| 2764 | schtasks /create /tn "svchost" /tr "c:\windows\resources\svchost.exe" /sc daily /st 16:13 /f | C:\Windows\system32\schtasks.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2896 | C:\Windows\Resources\Themes\icsys.icn.exe | C:\Windows\Resources\Themes\icsys.icn.exe | Valorant Bypass Cheat.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 2916 | c:\windows\resources\spoolsv.exe SE | c:\windows\resources\spoolsv.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 2952 | "C:\Users\admin\Desktop\Valorant Bypass Cheat.exe" | C:\Users\admin\Desktop\Valorant Bypass Cheat.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
Total events
569
Read events
480
Write events
89
Delete events
0
Modification events
| (PID) Process: | (3824) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3824) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3824) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3824) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Valorant Bypass Cheat.rar | |||
| (PID) Process: | (3824) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3824) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3824) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3824) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3824) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (3824) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\AppData\Local\Temp | |||
Executable files
5
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3824 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3824.5042\Valorant Bypass Cheat.exe | — | |
MD5:— | SHA256:— | |||
| 3640 | Valorant Bypass Cheat.exe | C:\Users\admin\AppData\Local\Temp\~DF77405A5F5B359676.TMP | — | |
MD5:— | SHA256:— | |||
| 2064 | spoolsv.exe | C:\Users\admin\AppData\Local\Temp\~DF5BA219F8AF4CDB63.TMP | — | |
MD5:— | SHA256:— | |||
| 2916 | spoolsv.exe | C:\Users\admin\AppData\Local\Temp\~DF63B48733E2D9B3D1.TMP | — | |
MD5:— | SHA256:— | |||
| 2896 | icsys.icn.exe | C:\Users\admin\AppData\Local\Temp\~DF2B29BF4FAE84A7EC.TMP | — | |
MD5:— | SHA256:— | |||
| 2952 | Valorant Bypass Cheat.exe | C:\Users\admin\AppData\Local\Temp\~DFC073350FDC6DC3CE.TMP | — | |
MD5:— | SHA256:— | |||
| 4072 | explorer.exe | C:\windows\resources\spoolsv.exe | executable | |
MD5:— | SHA256:— | |||
| 2896 | icsys.icn.exe | C:\windows\resources\themes\explorer.exe | executable | |
MD5:— | SHA256:— | |||
| 2916 | spoolsv.exe | C:\windows\resources\svchost.exe | executable | |
MD5:— | SHA256:— | |||
| 2952 | Valorant Bypass Cheat.exe | C:\Windows\Resources\Themes\icsys.icn.exe | executable | |
MD5:5D14B4D32E275FAD22FA91165034A421 | SHA256:395043C4F852574591735828A8616C088D2FA752B7C941055AC0BCA82A62EBD3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
12
DNS requests
3
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2756 | valorant bypass cheat.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/ | unknown | text | 347 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2756 | valorant bypass cheat.exe | 208.95.112.1:80 | ip-api.com | IBURST | — | malicious |
2756 | valorant bypass cheat.exe | 167.99.187.240:1111 | — | — | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ip-api.com |
| malicious |
dns.msftncsi.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2756 | valorant bypass cheat.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup ip-api.com |
2756 | valorant bypass cheat.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
2756 | valorant bypass cheat.exe | A Network Trojan was detected | REMOTE [PTsecurity] Quasar.RAT IP Lookup |
1 ETPRO signatures available at the full report