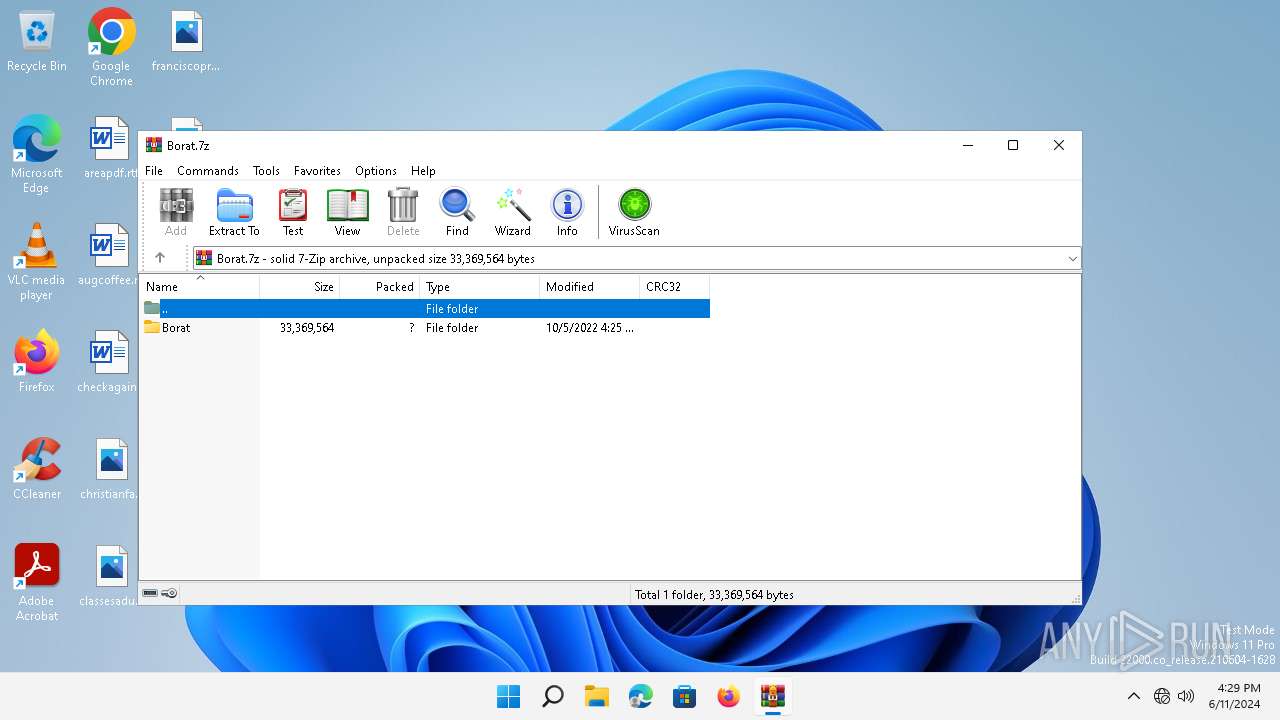
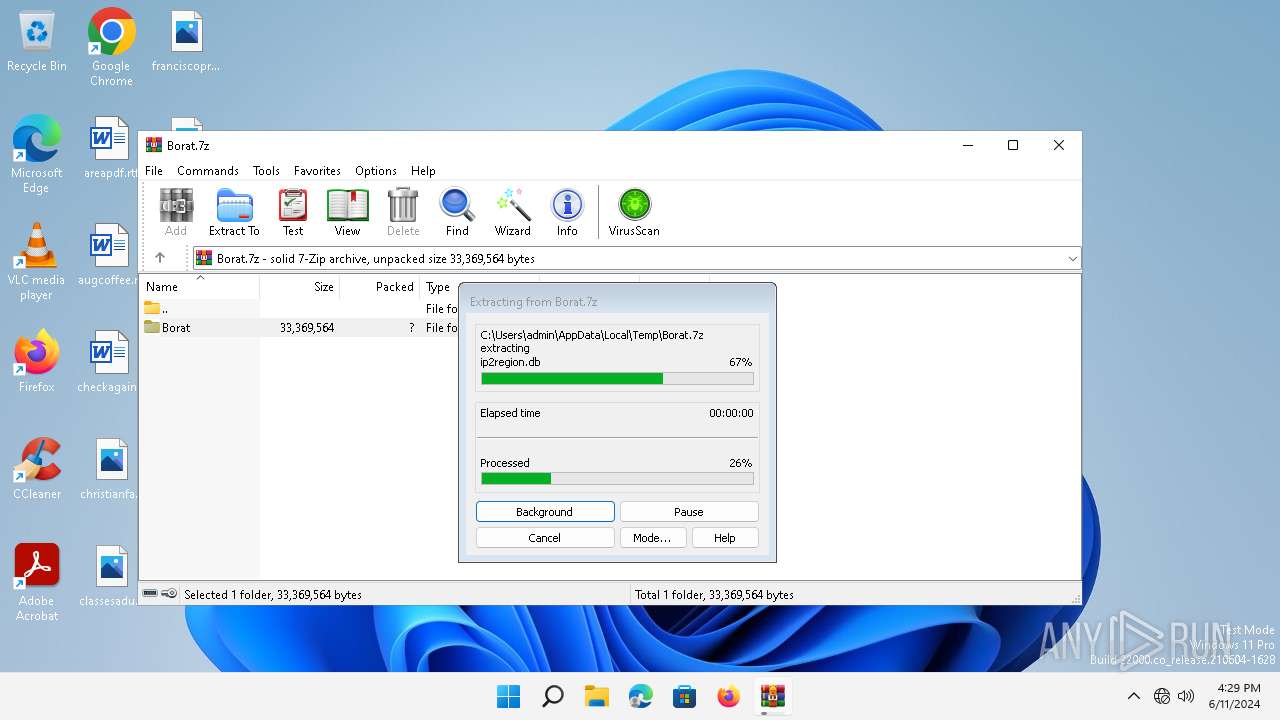
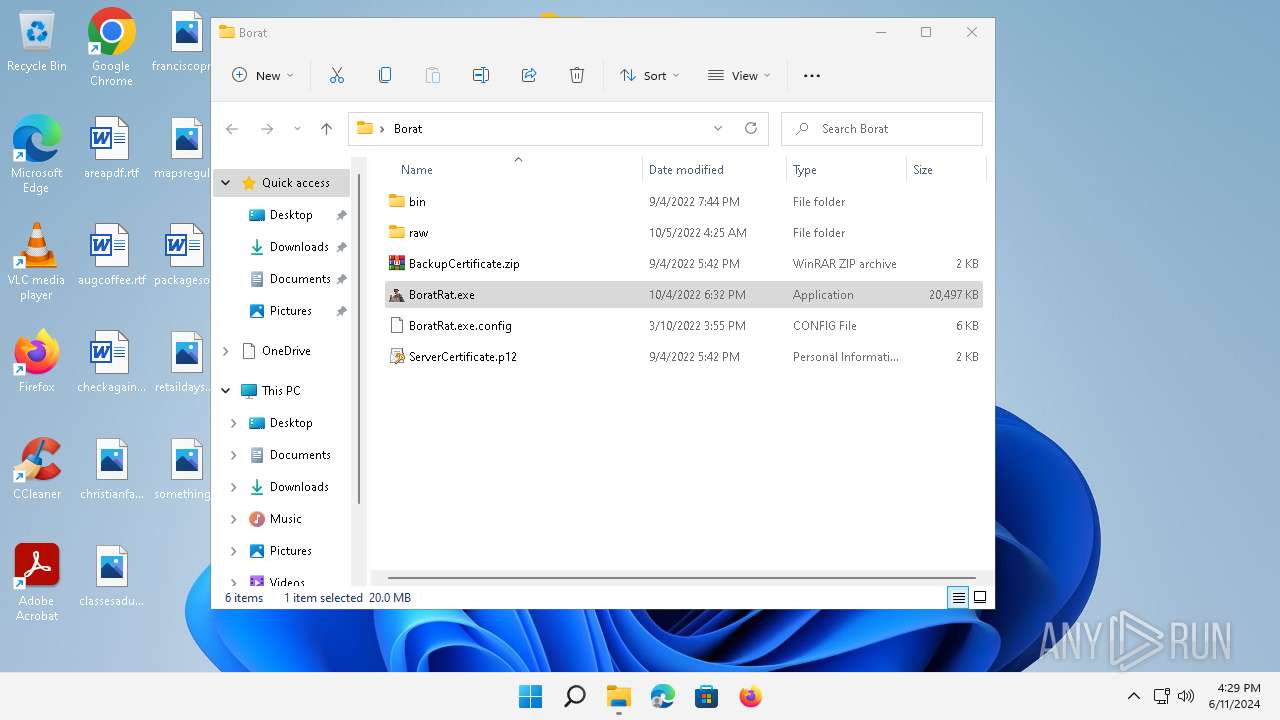
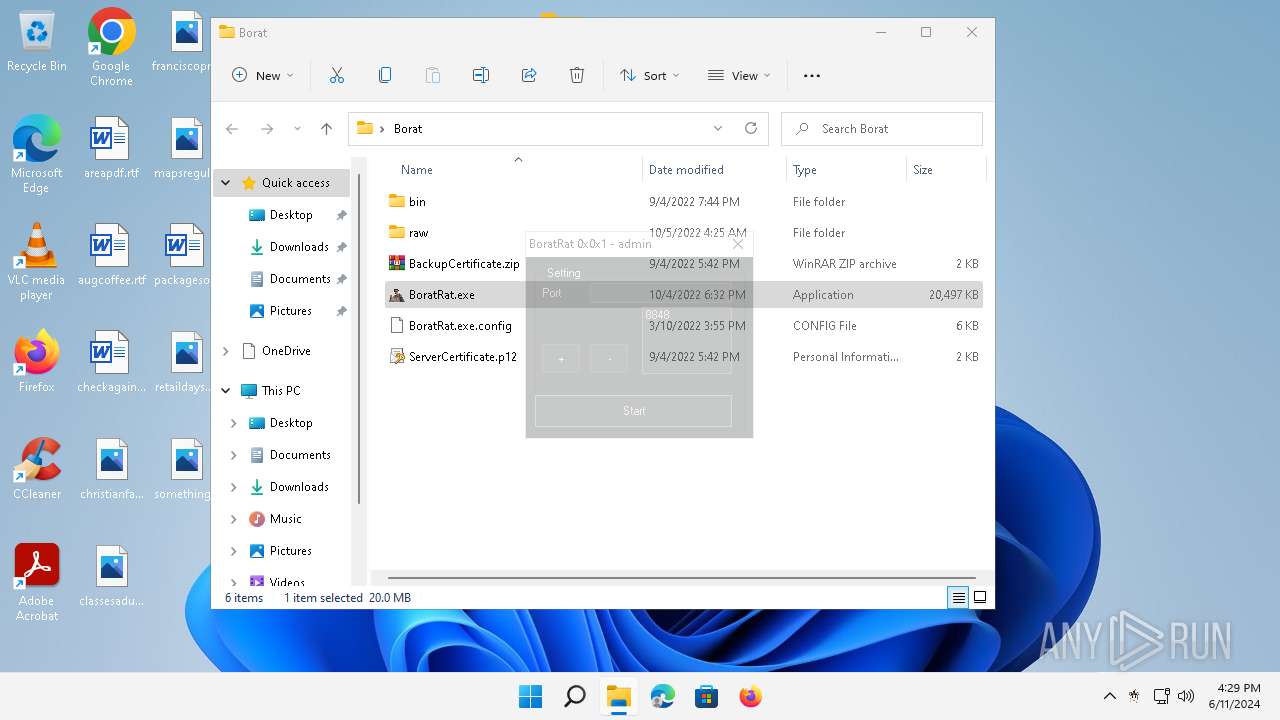
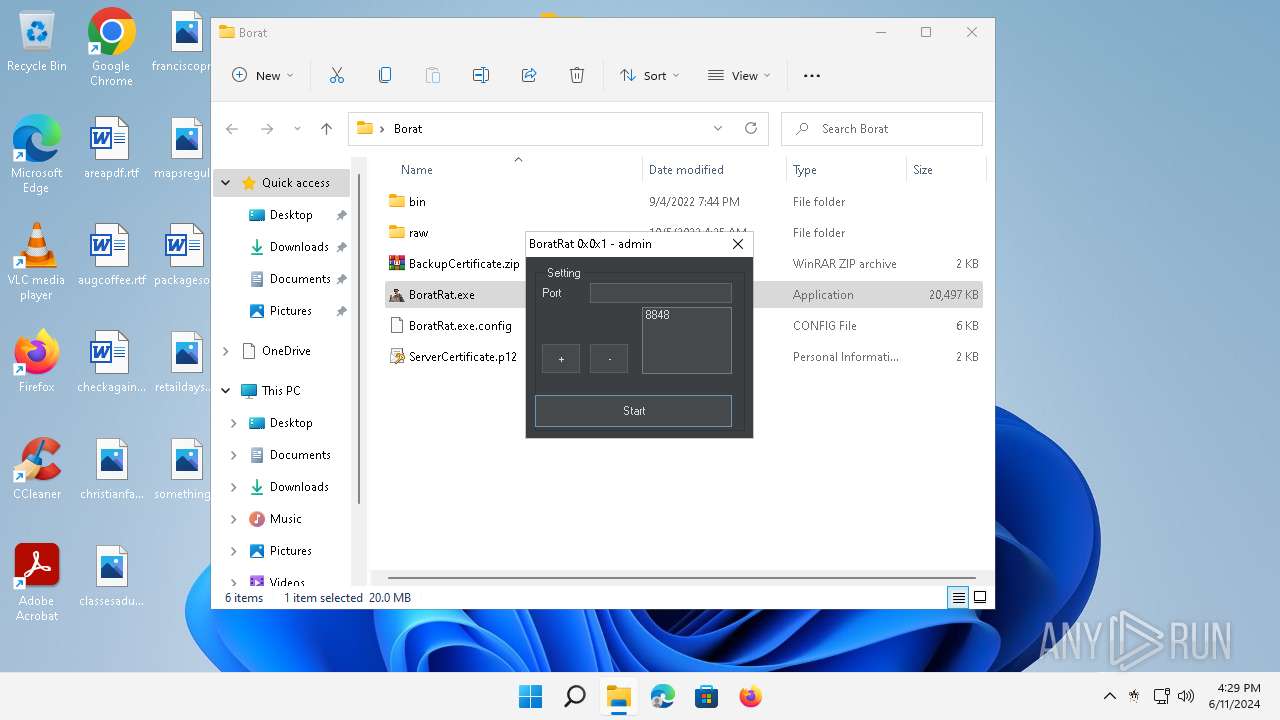
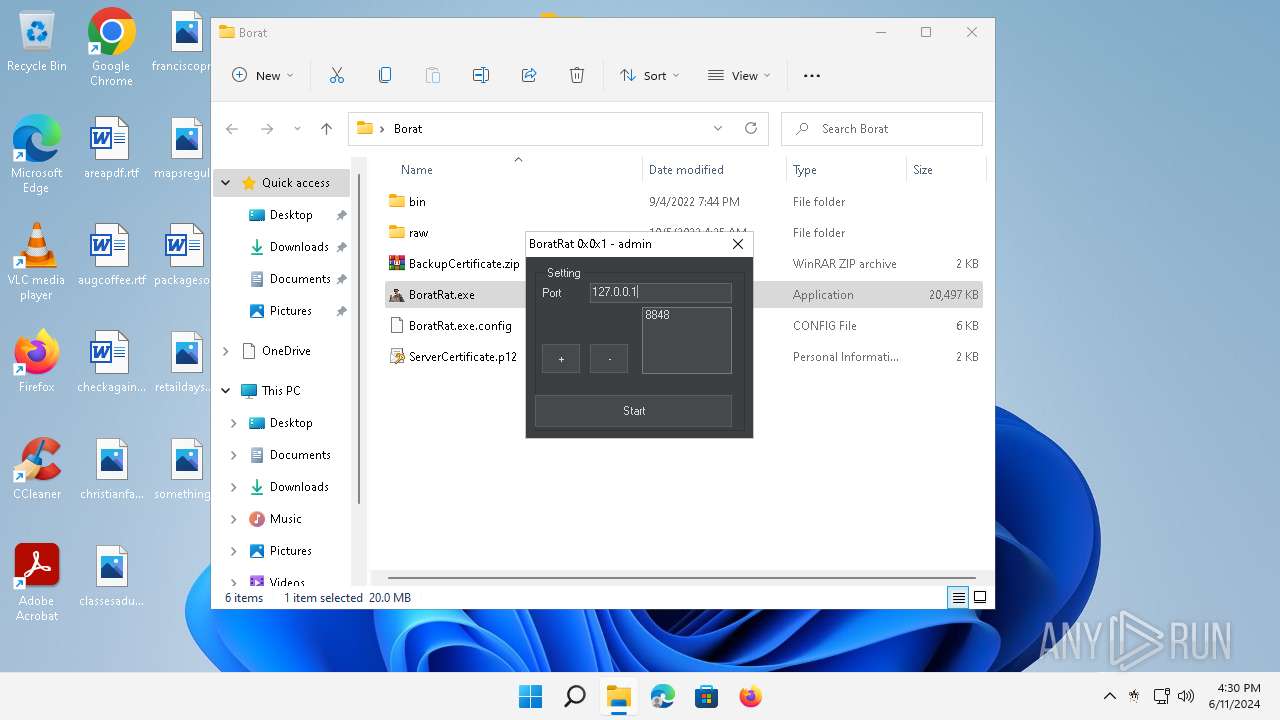
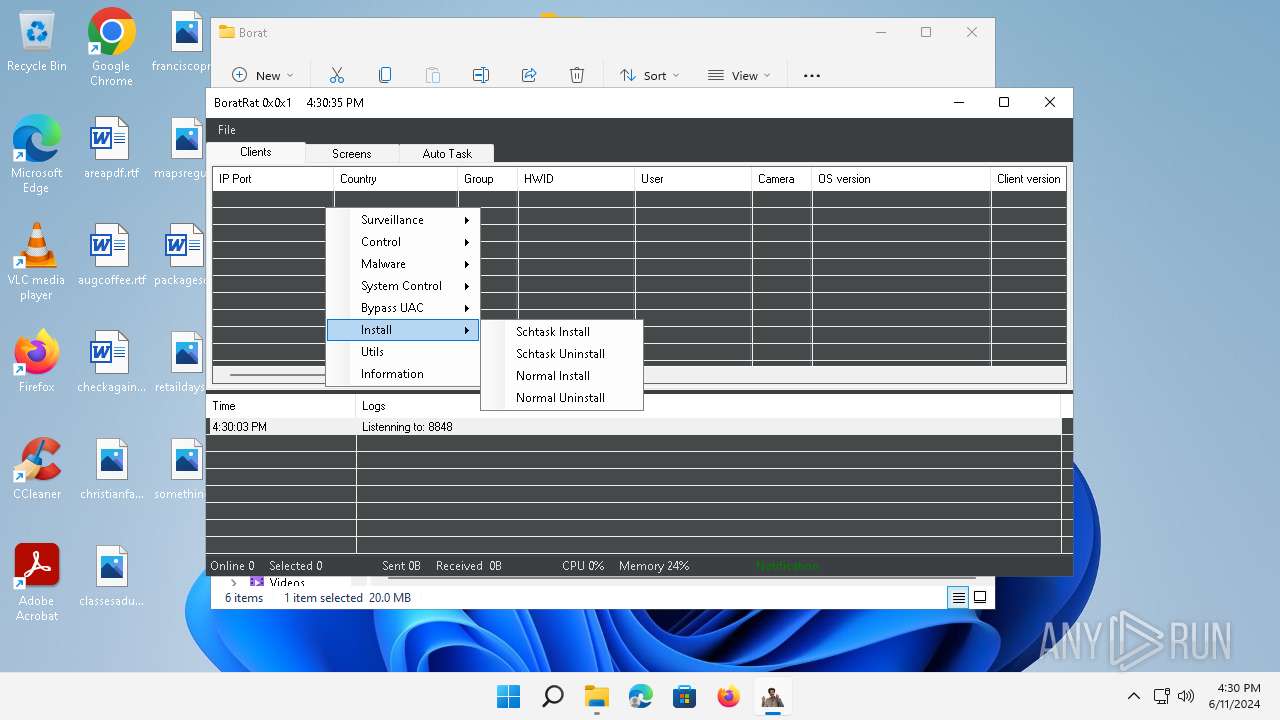
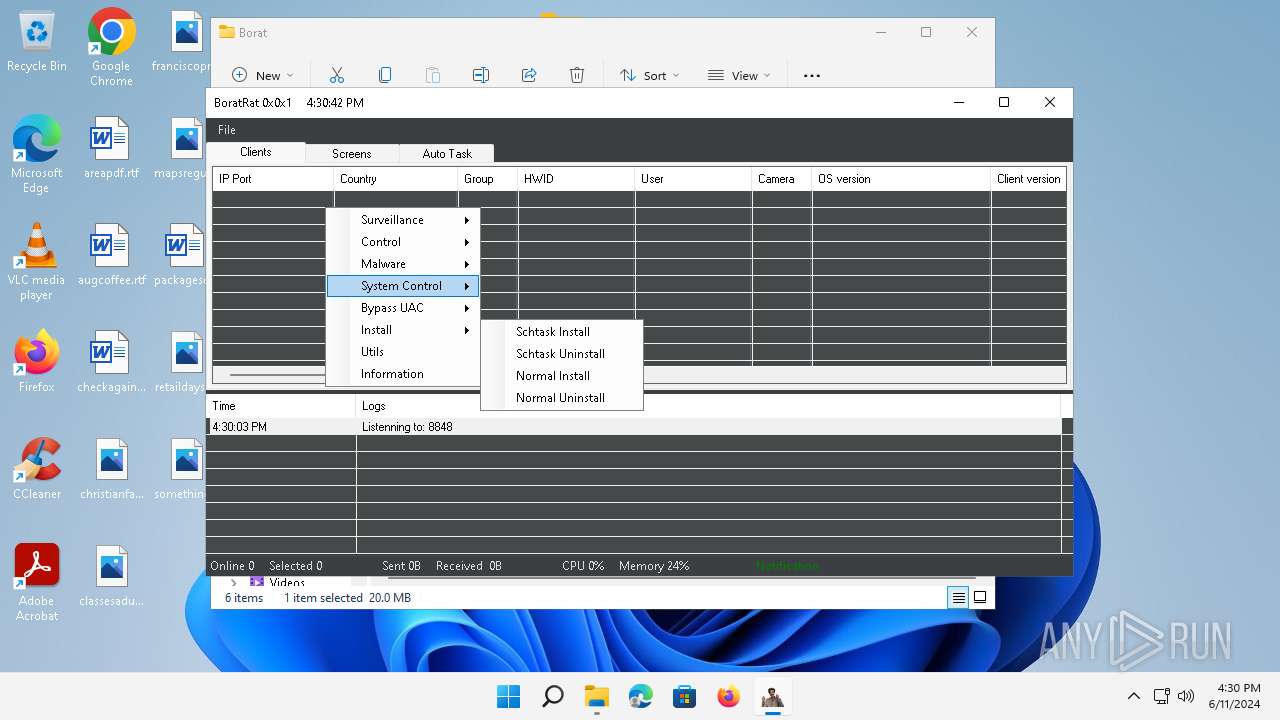
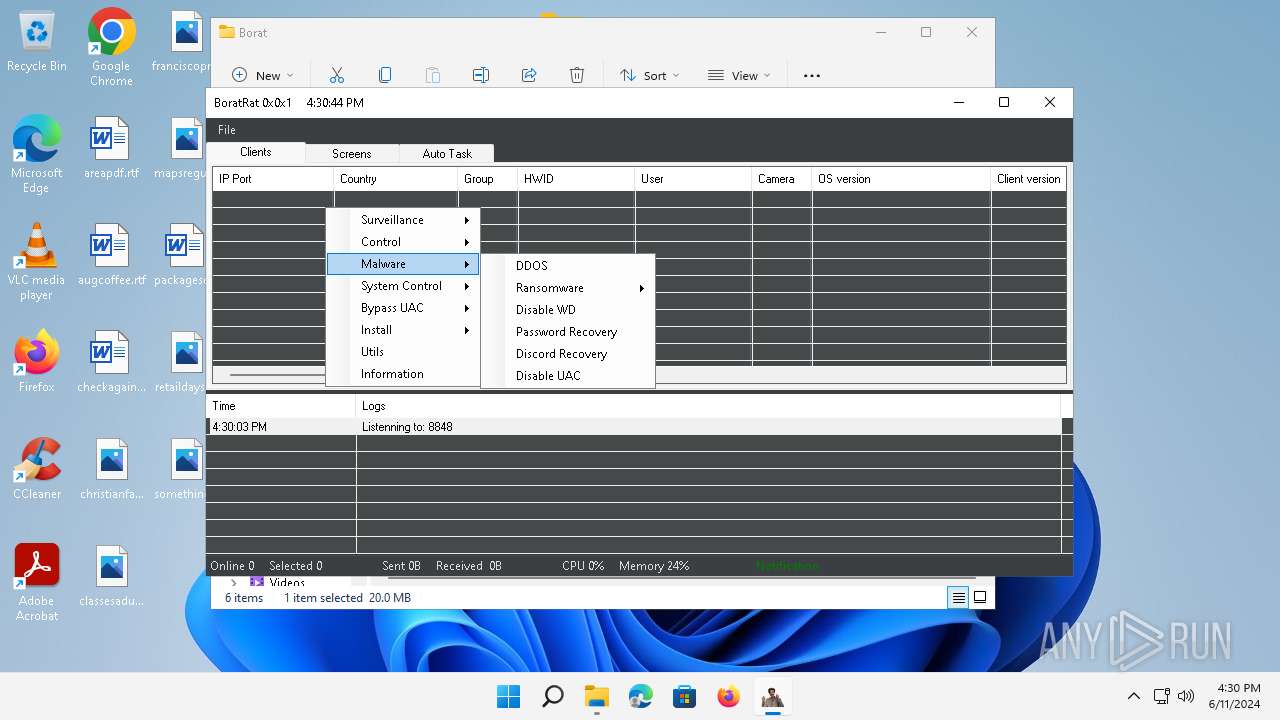
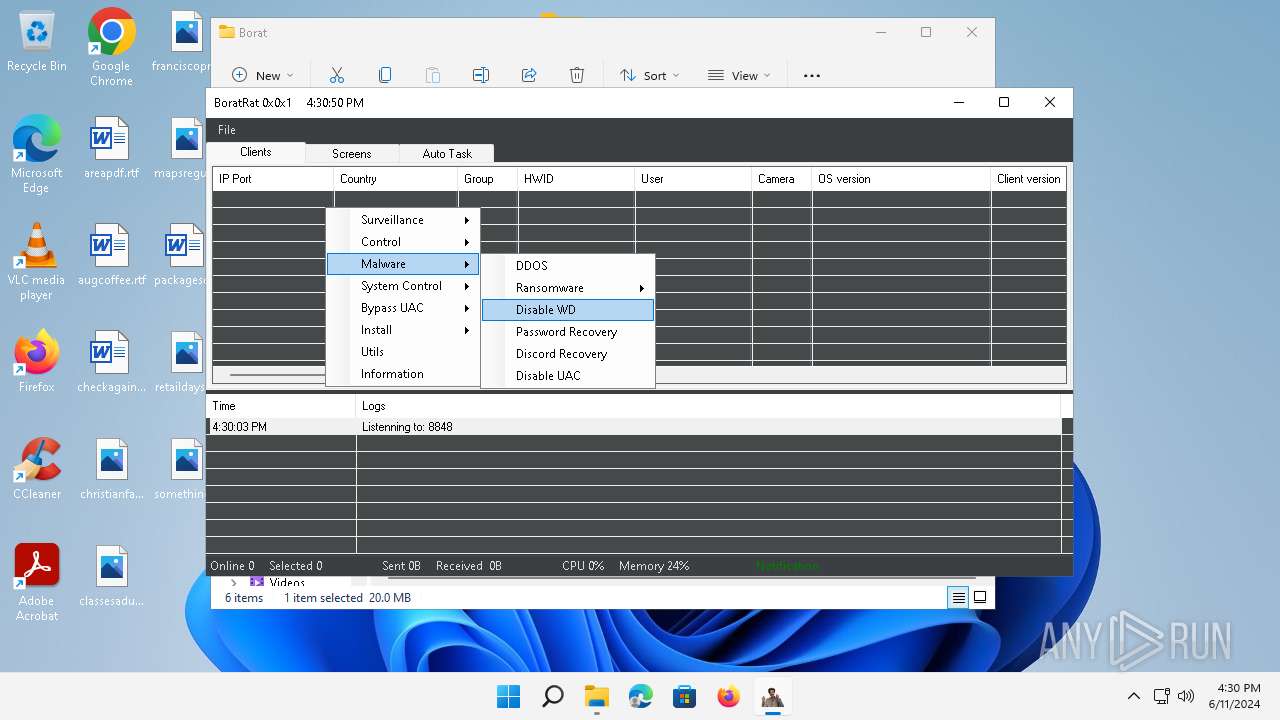
| File name: | Borat.7z |
| Full analysis: | https://app.any.run/tasks/c5933e52-a49f-4f7d-b137-bd8ca133e5c9 |
| Verdict: | Malicious activity |
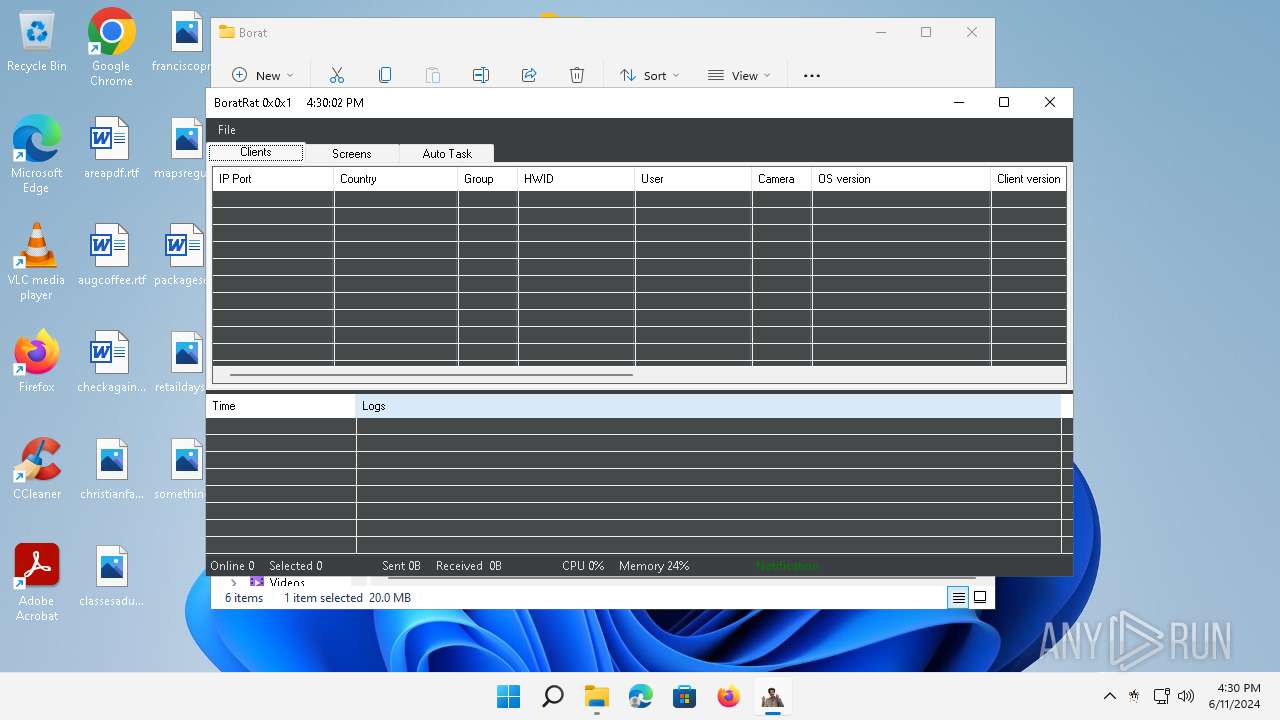
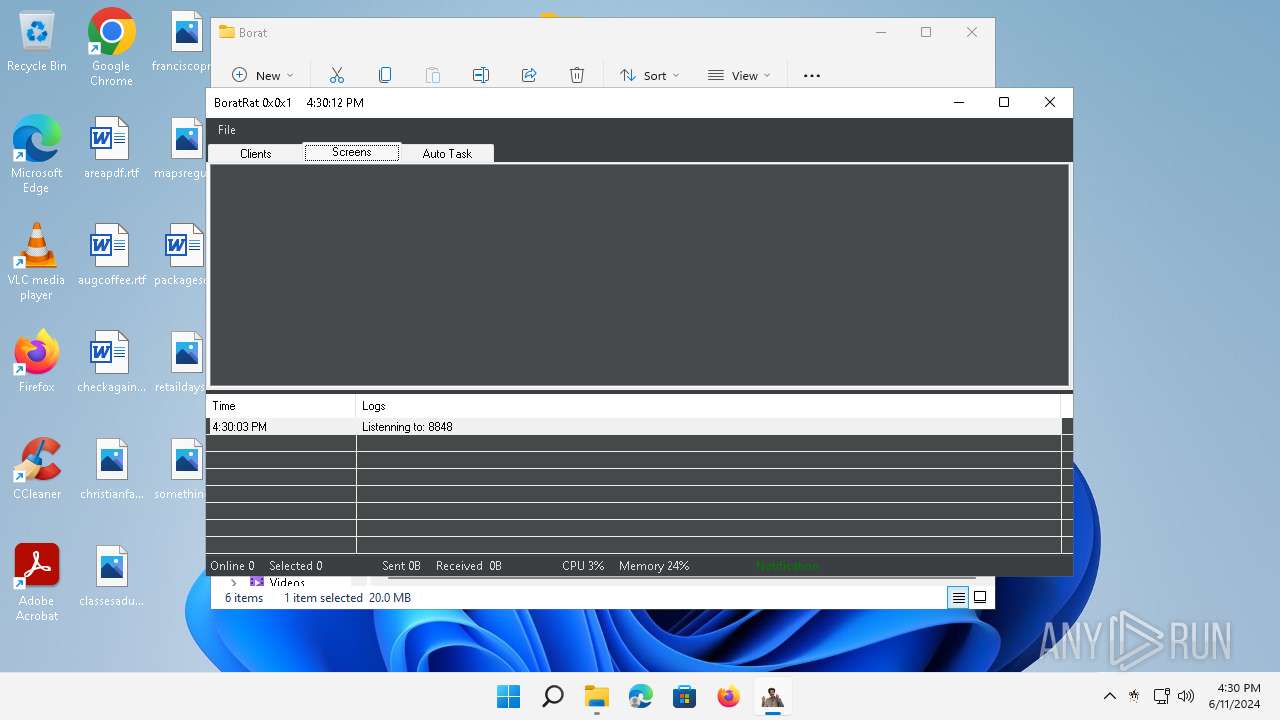
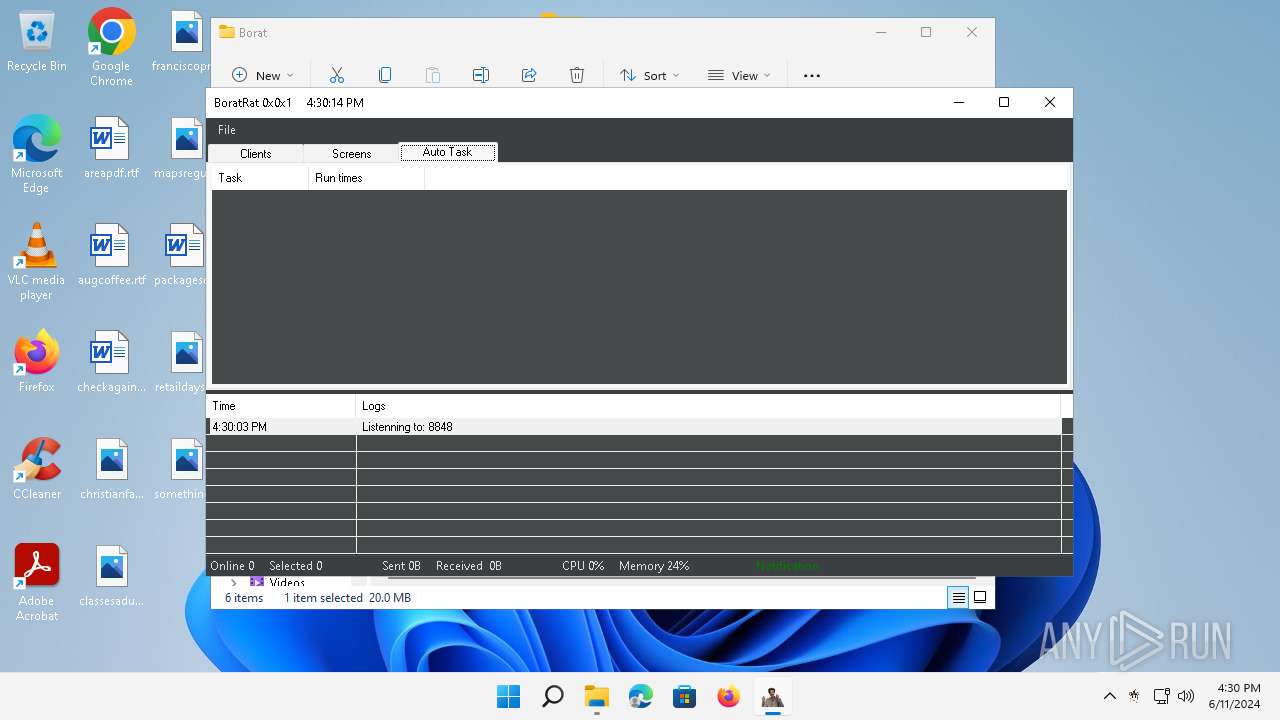
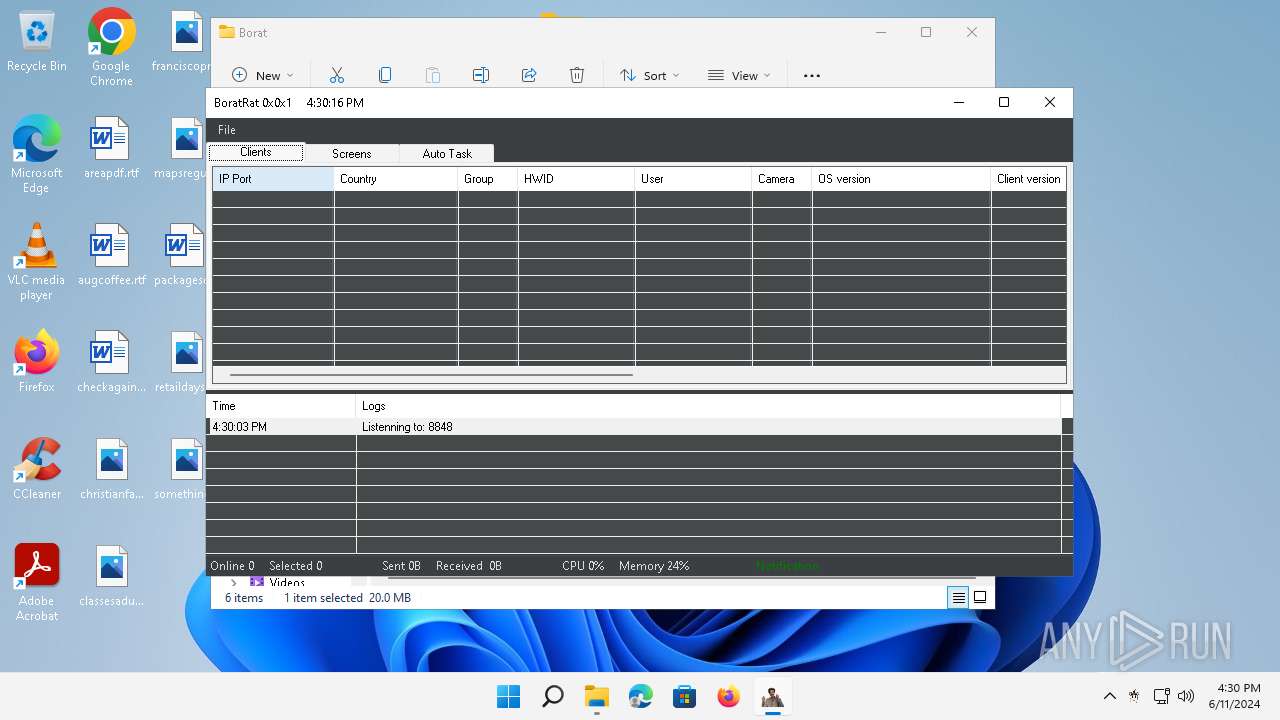
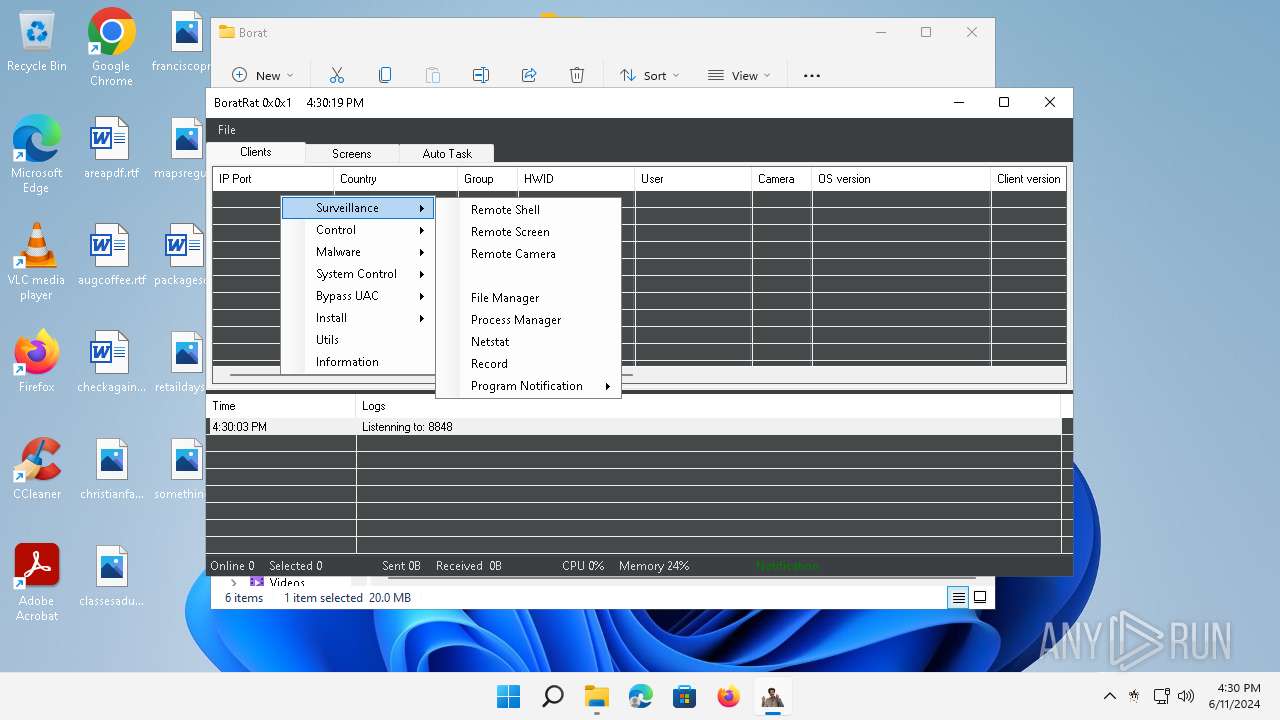
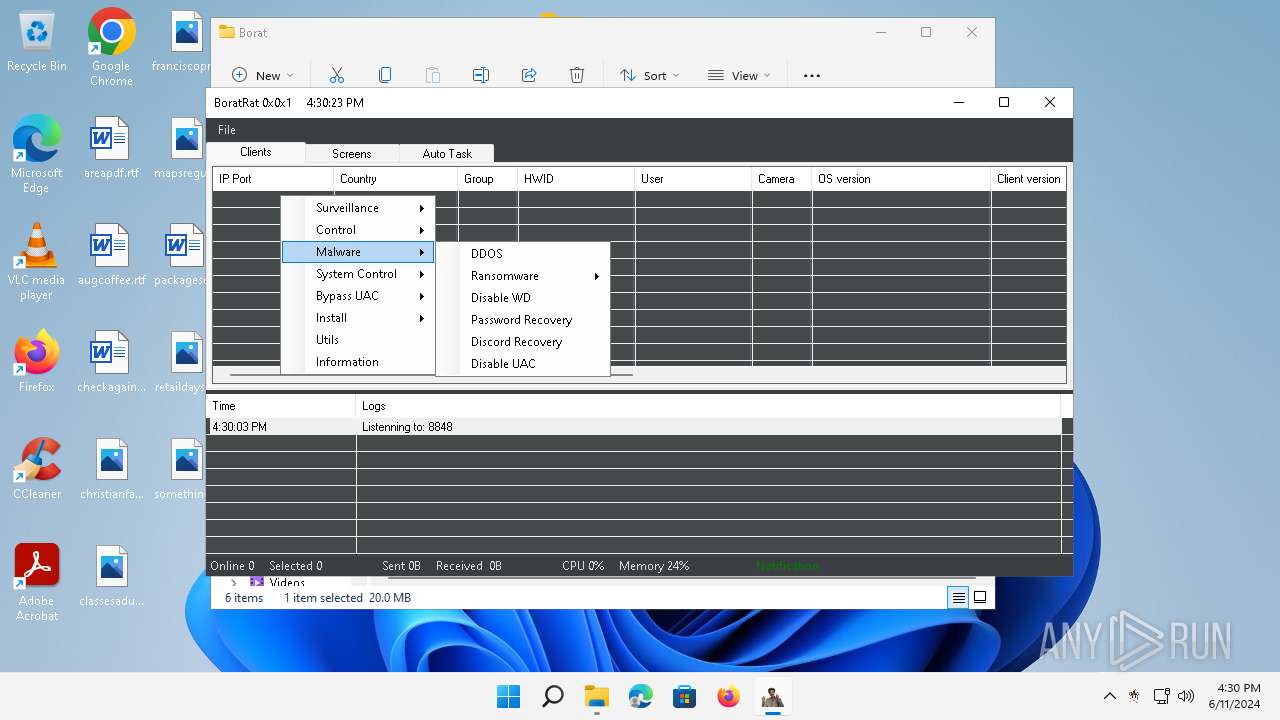
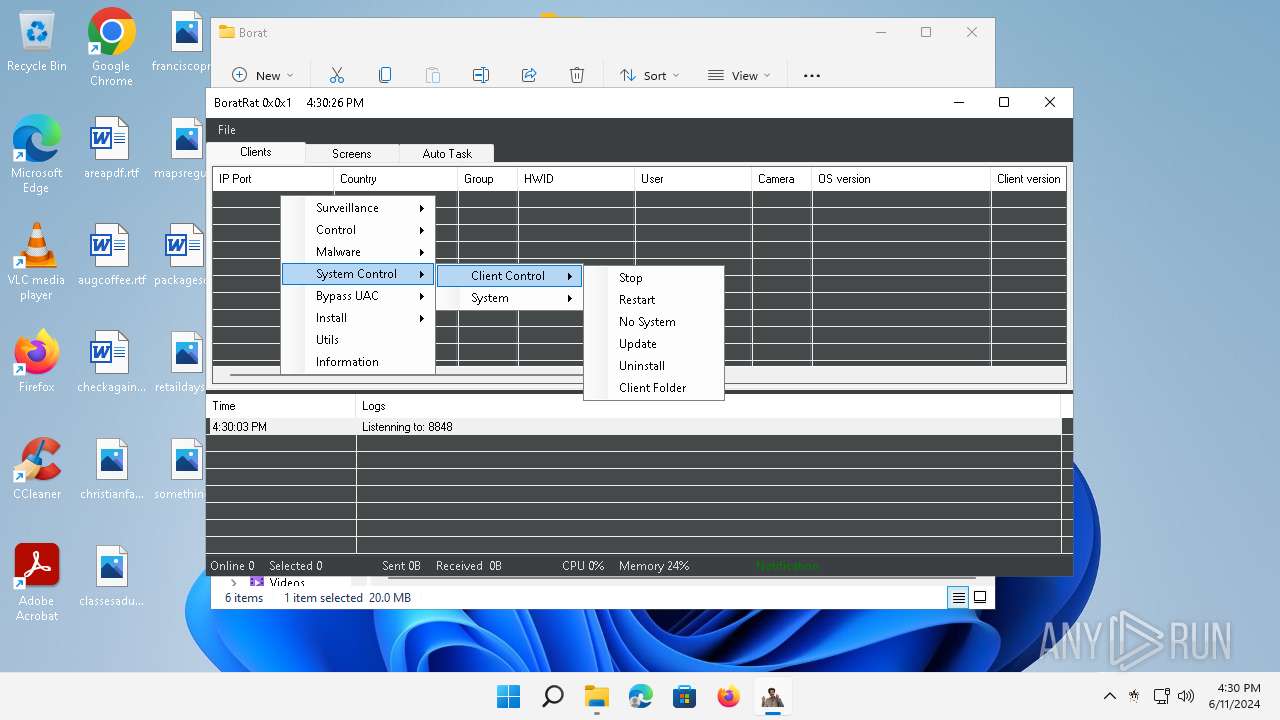
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | June 11, 2024, 16:29:02 |
| OS: | Windows 11 Professional (build: 22000, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 43C20E4EE2DD87C70DD0ED082DC74431 |
| SHA1: | 71051DEE5D0480B8AA30A599A95D0AD928F7BB9E |
| SHA256: | B2F4CC95E54ACC818410D79072CCD44A4DBB21AFAD82C2A4608B7B52F1502867 |
| SSDEEP: | 98304:4mnI+WmnzFhcWMOo/5ucNWw7tq3o280CB6oWprH0Vtcpot+FfRT5apCeiFqQgijQ:BtYHMwzJ4hoHQLs |
MALICIOUS
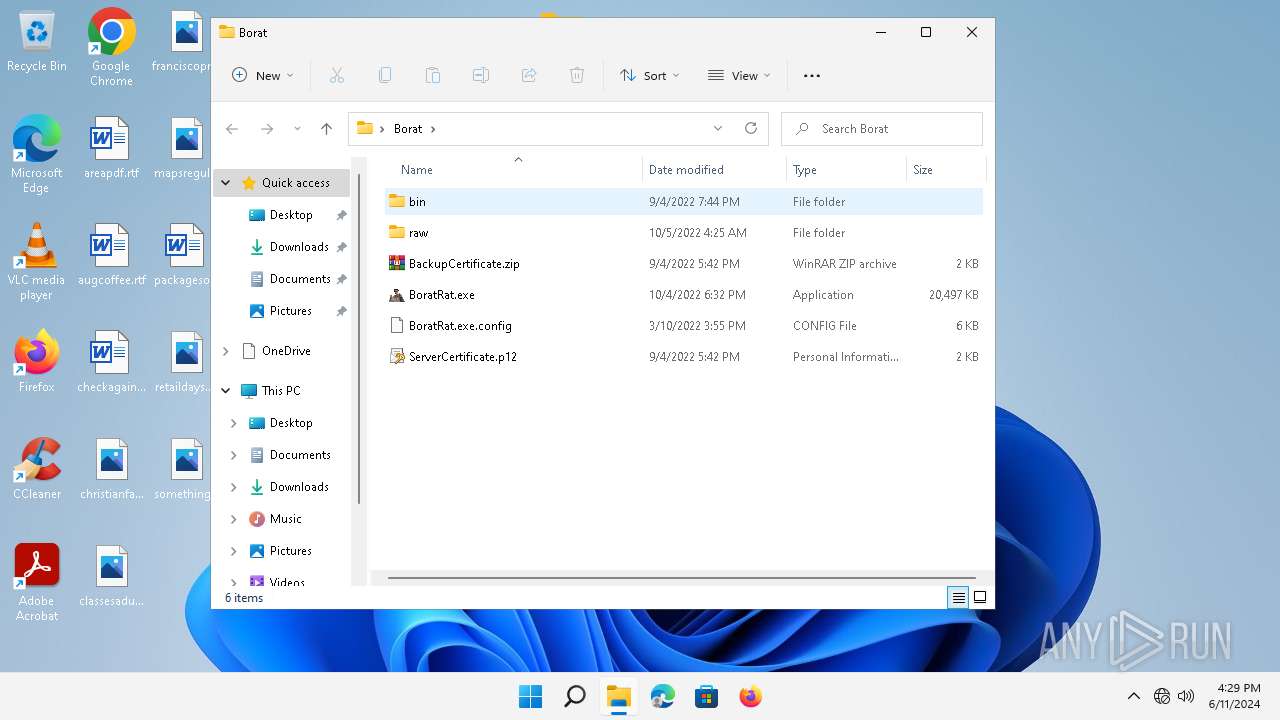
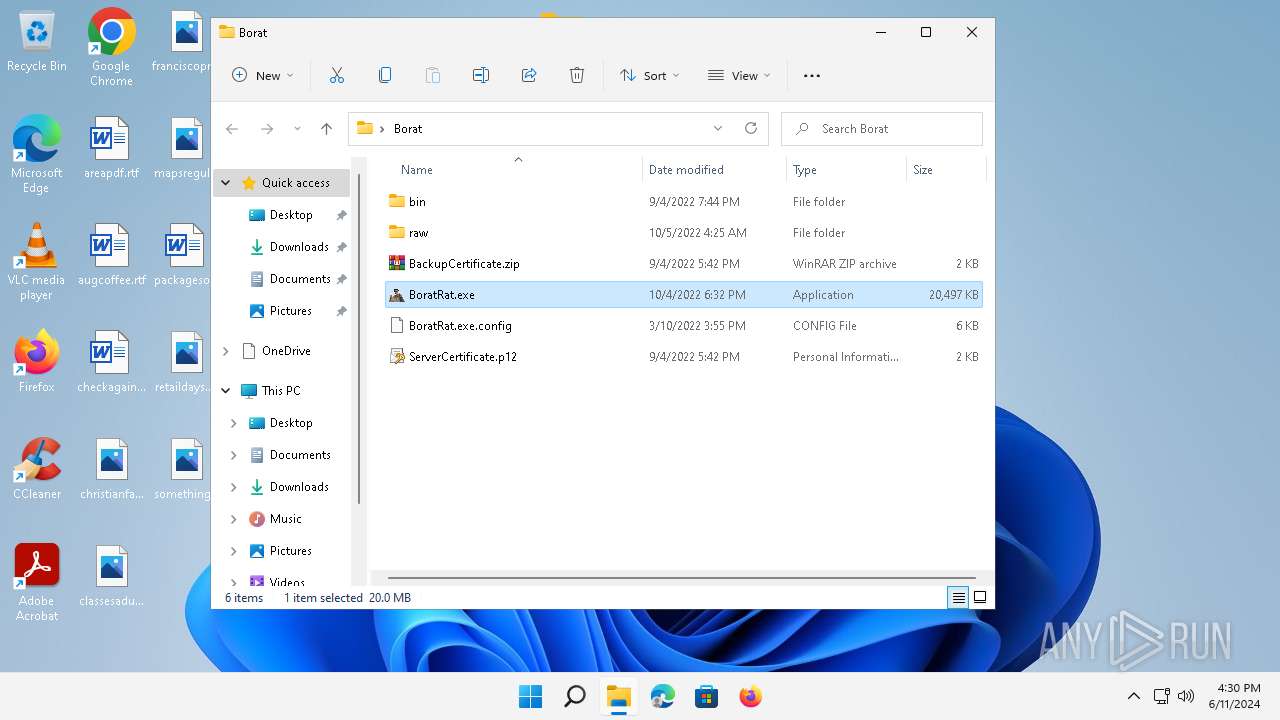
Drops the executable file immediately after the start
- WinRAR.exe (PID: 5992)
Actions looks like stealing of personal data
- WinRAR.exe (PID: 5992)
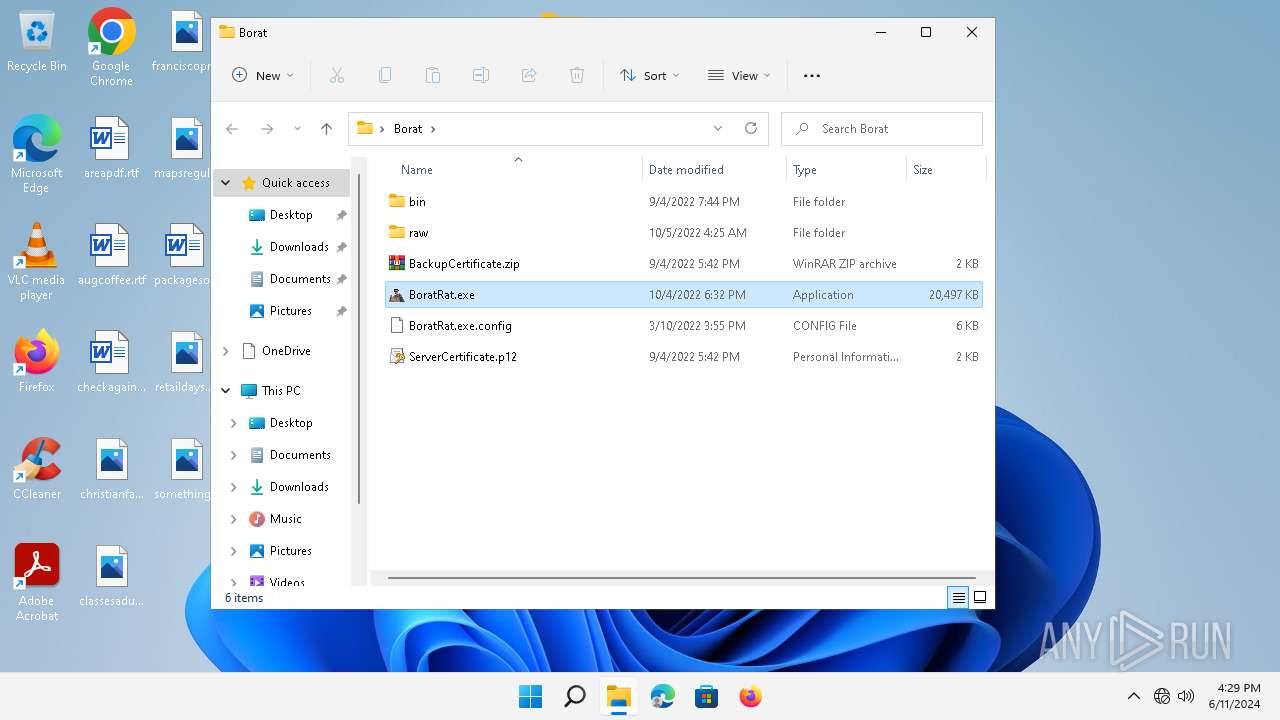
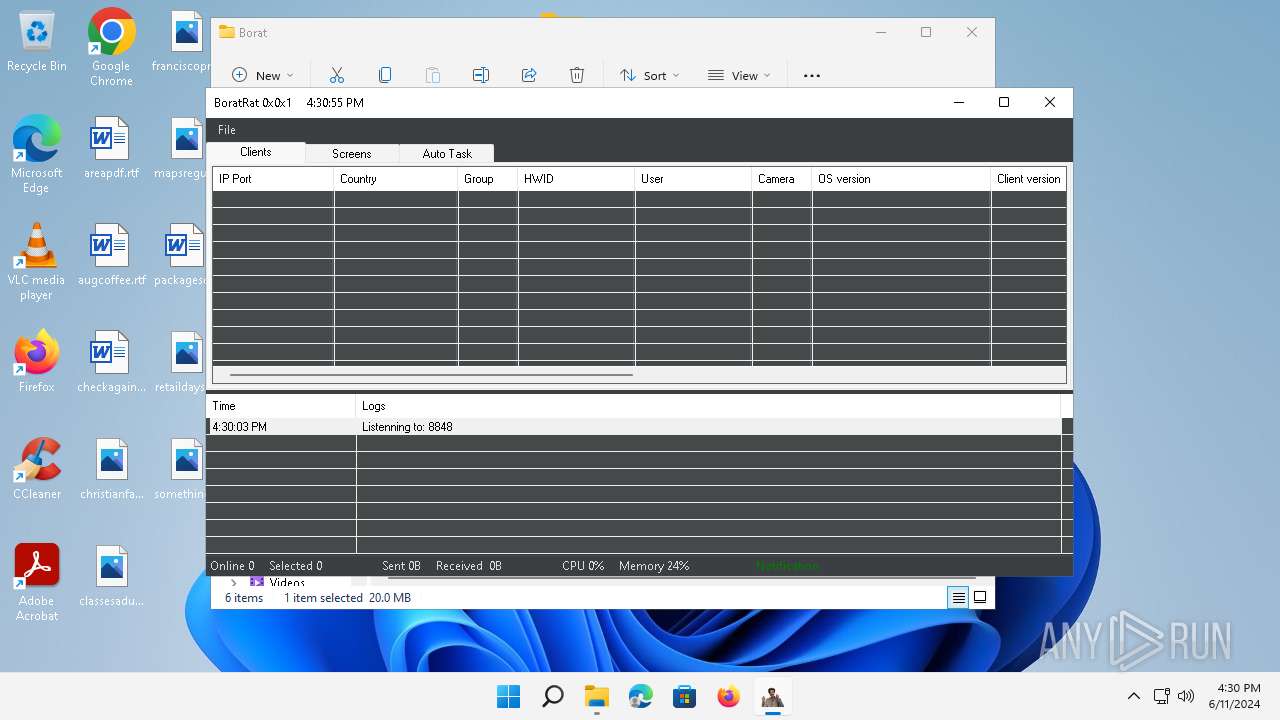
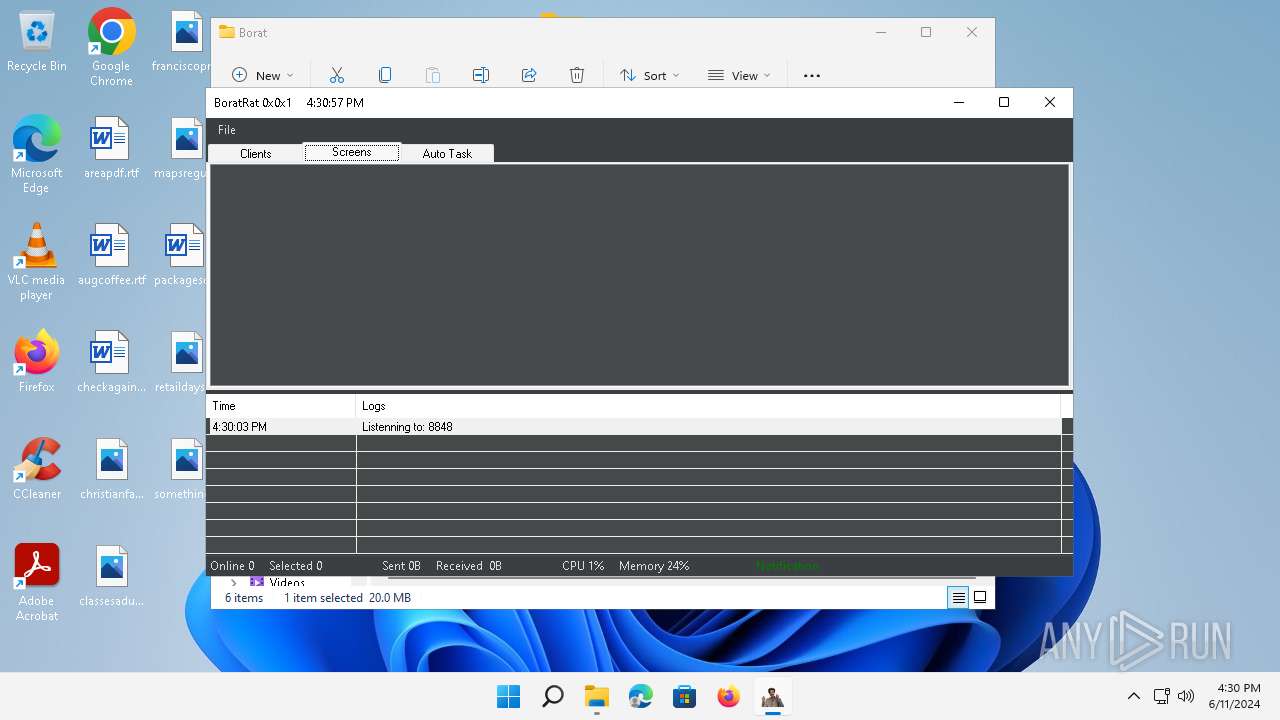
ASYNCRAT has been detected (YARA)
- BoratRat.exe (PID: 3632)
SUSPICIOUS
The process checks if it is being run in the virtual environment
- BoratRat.exe (PID: 3632)
The process creates files with name similar to system file names
- WinRAR.exe (PID: 5992)
Reads security settings of Internet Explorer
- BoratRat.exe (PID: 3632)
Reads the Internet Settings
- BoratRat.exe (PID: 3632)
INFO
Checks supported languages
- BoratRat.exe (PID: 3632)
Reads the computer name
- BoratRat.exe (PID: 3632)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5992)
Manual execution by a user
- BoratRat.exe (PID: 3632)
Reads the machine GUID from the registry
- BoratRat.exe (PID: 3632)
Creates files or folders in the user directory
- BoratRat.exe (PID: 3632)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
94
Monitored processes
2
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3632 | "C:\Users\admin\Desktop\Borat\BoratRat.exe" | C:\Users\admin\Desktop\Borat\BoratRat.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: BoratRat Exit code: 0 Version: 1.0.7.0 Modules
| |||||||||||||||
| 5992 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Borat.7z | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
8 965
Read events
8 938
Write events
27
Delete events
0
Modification events
| (PID) Process: | (5992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | VerInfo |
Value: 005B050074844A861CBCDA01 | |||
| (PID) Process: | (5992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (5992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (5992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Borat.7z | |||
| (PID) Process: | (5992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF82000000820000004204000065020000 | |||
| (PID) Process: | (5992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\AppData\Local\Temp | |||
Executable files
24
Suspicious files
4
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5992.18009\Borat\bin\ip2region.db | — | |
MD5:— | SHA256:— | |||
| 5992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5992.18009\Borat\bin\Audio.dll | executable | |
MD5:9726D7FE49C8BA43845AD8E5E2802BB8 | SHA256:DF31A70CEB0C481646EEAF94189242200FAFD3DF92F8B3EC97C0D0670F0E2259 | |||
| 5992 | WinRAR.exe | C:\USERS\ADMIN\APPDATA\ROAMING\WINRAR\VERSION.DAT | binary | |
MD5:7556A1CE824DED33C579B142E518A0C4 | SHA256:3C78686009986D23F484A789889C64429798D875D56EC71BA866673DAA0BF38B | |||
| 5992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5992.18009\Borat\bin\Extra.dll | executable | |
MD5:62C231BAFA469AB04F090FCB4475D360 | SHA256:6A4F32B0228092CE68E8448C6F4B74B4C654F40FB2D462C1D6BBD4B4EF09053D | |||
| 5992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5992.18009\Borat\BackupCertificate.zip | compressed | |
MD5:9322F71EDD95192E1F4D275BFD6D87F3 | SHA256:F13033134C386E85A1E9009E863A3E6380438F83E3336B76A33E701A88F64946 | |||
| 5992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5992.18009\Borat\bin\Discord.dll | executable | |
MD5:7EE673594BBB20F65448AAB05F1361D0 | SHA256:8FA7634B7DCA1A451CF8940429BE6AD2440821ED04D5D70B6E727E5968E0B5F6 | |||
| 5992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5992.18009\Borat\ServerCertificate.p12 | der | |
MD5:478EE44A47895E687296B9AB34DF04C4 | SHA256:4B0612B2CD5E7ECC456D5C29C89917B8EC881C5F4FD94AFE157098CA96308781 | |||
| 5992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5992.18009\Borat\BoratRat.exe | executable | |
MD5:65B694D69D327EFE28FCBCE125401E96 | SHA256:DE60ECBBFEF30C93FE8875EF69B358B20076D1F969FC3D21AB44D59DC9EF7CAB | |||
| 5992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5992.18009\Borat\bin\FileSearcher.dll | executable | |
MD5:0B7C33C5739903BA4F4B78C446773528 | SHA256:2D9625F41793F62BFE32C10B2D5E05668E321BCAF8B73414B3C31EF677B9BFF4 | |||
| 5992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5992.18009\Borat\bin\Netstat.dll | executable | |
MD5:12911F5654D6346FE99EF91E90849C13 | SHA256:7EED1B90946A6DB1FE978D177A80542B5DB0BF3156C979DC8A8869A94811BF4B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
24
DNS requests
9
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1332 | svchost.exe | GET | 200 | 2.16.164.35:80 | http://www.msftconnecttest.com/connecttest.txt | unknown | — | — | unknown |
3984 | svchost.exe | GET | 304 | 2.19.11.178:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?594e198d9cbfa5a7 | unknown | — | — | unknown |
3984 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
1088 | svchost.exe | POST | 403 | 2.18.110.57:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
1088 | svchost.exe | POST | 403 | 2.18.110.57:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
1088 | svchost.exe | POST | 403 | 2.18.110.57:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
1088 | svchost.exe | POST | 403 | 2.18.110.57:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
2828 | svchost.exe | GET | 200 | 2.19.126.163:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/pinrulesstl.cab?6bd83704331f154b | unknown | — | — | unknown |
1088 | svchost.exe | POST | 403 | 2.18.110.57:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
1088 | svchost.exe | POST | 403 | 2.18.110.57:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4552 | svchost.exe | 239.255.255.250:1900 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1332 | svchost.exe | 2.16.164.42:80 | — | Akamai International B.V. | NL | unknown |
5748 | svchost.exe | 2.18.109.164:443 | fs.microsoft.com | Akamai International B.V. | FR | unknown |
1332 | svchost.exe | 2.16.164.35:80 | — | Akamai International B.V. | NL | unknown |
3984 | svchost.exe | 20.190.160.22:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3984 | svchost.exe | 2.19.11.178:80 | ctldl.windowsupdate.com | Elisa Oyj | NL | unknown |
3984 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2844 | svchost.exe | 51.104.15.252:443 | v10.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | unknown |
2844 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
fs.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
v10.events.data.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1332 | svchost.exe | Misc activity | ET INFO Microsoft Connection Test |