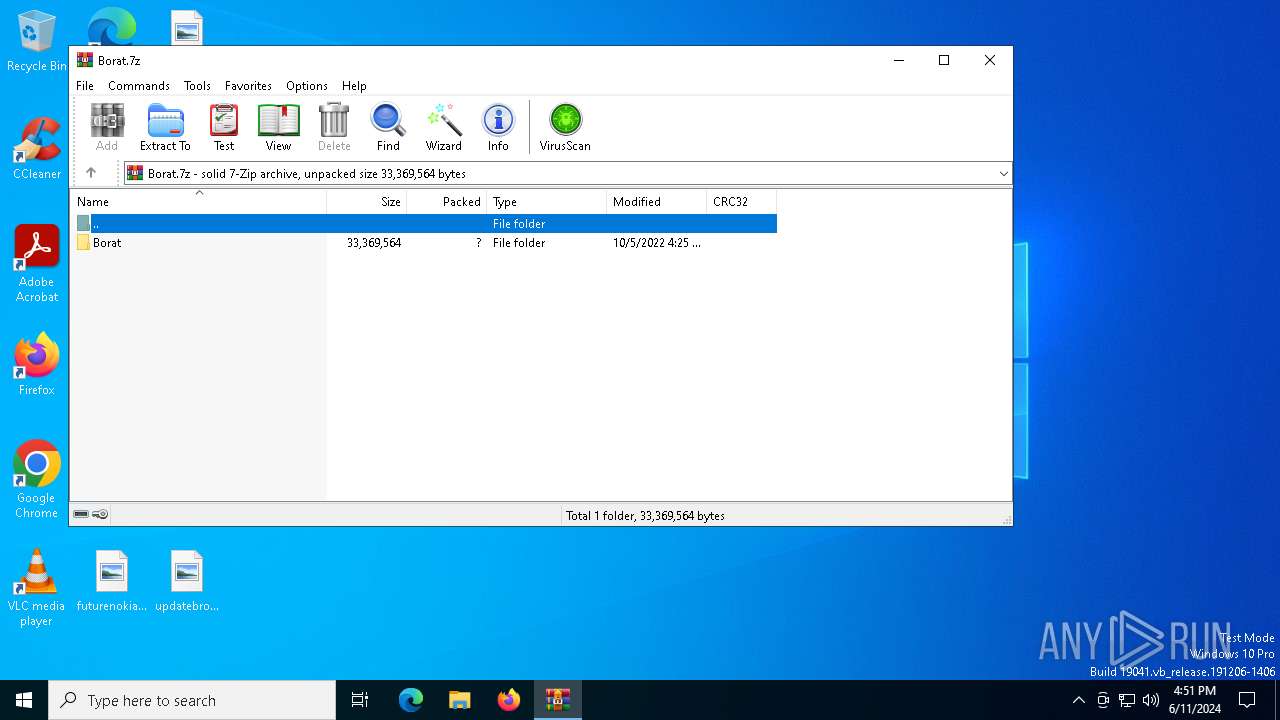
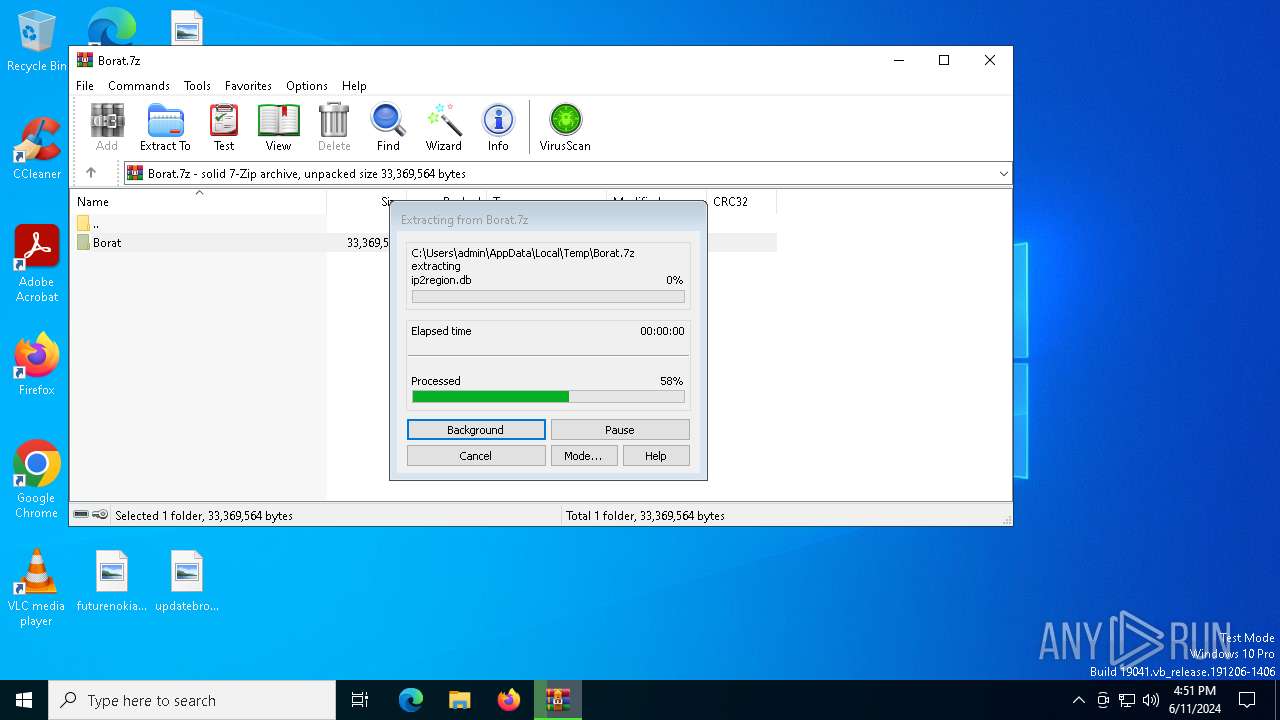
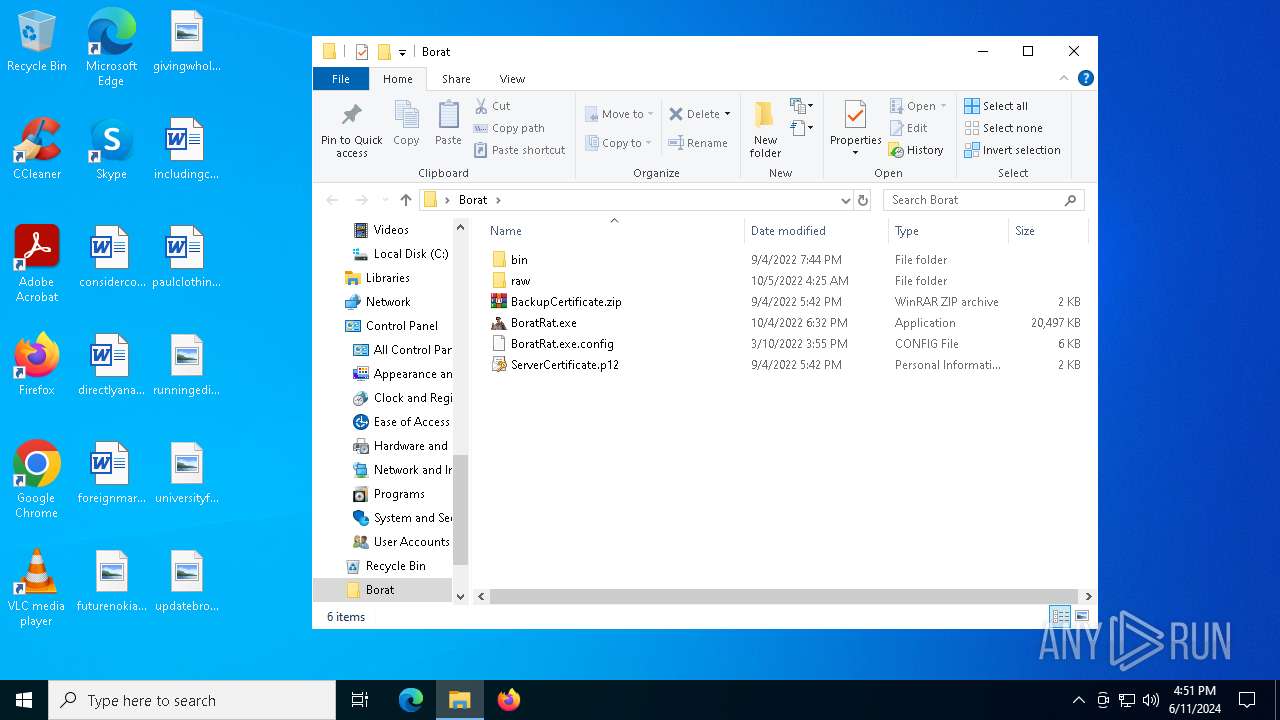
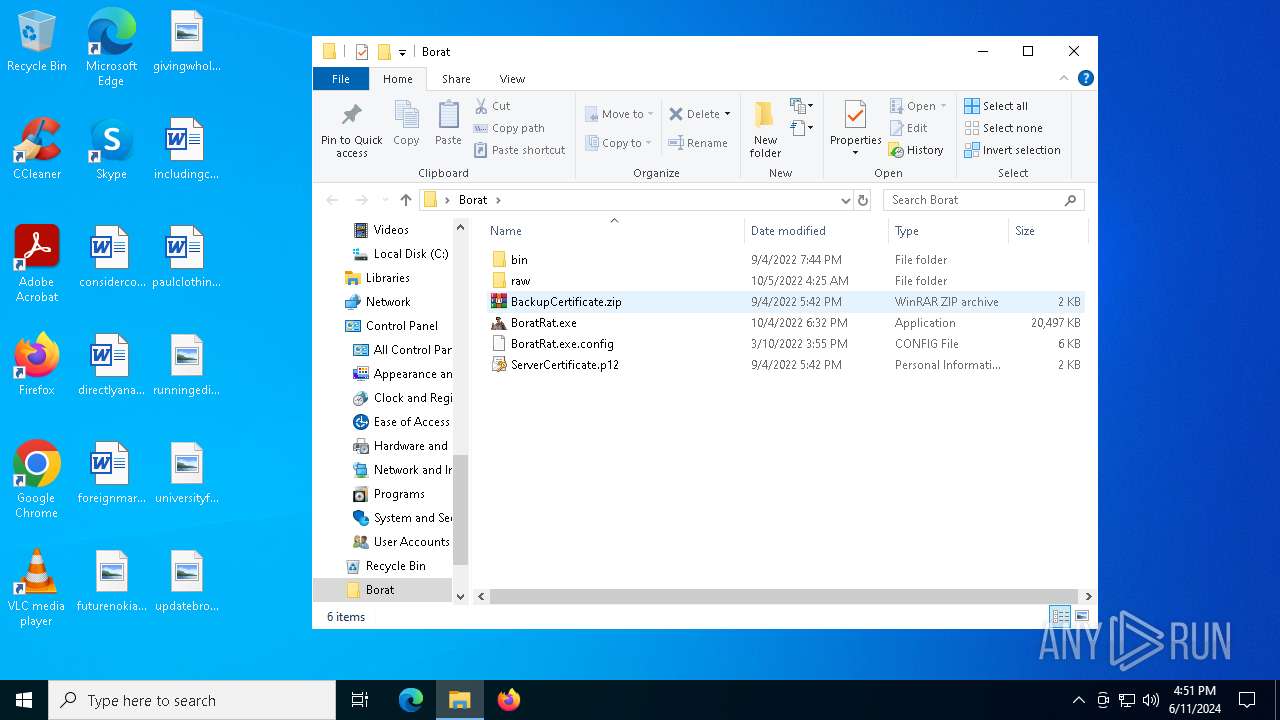
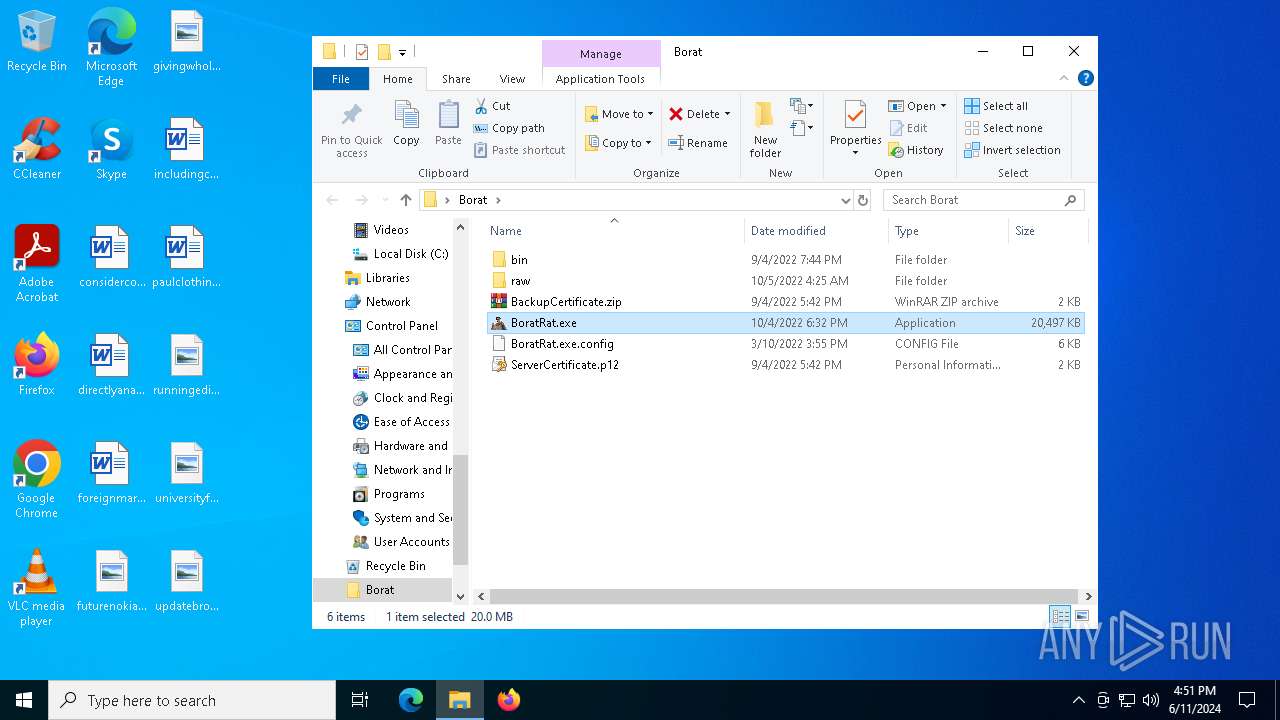
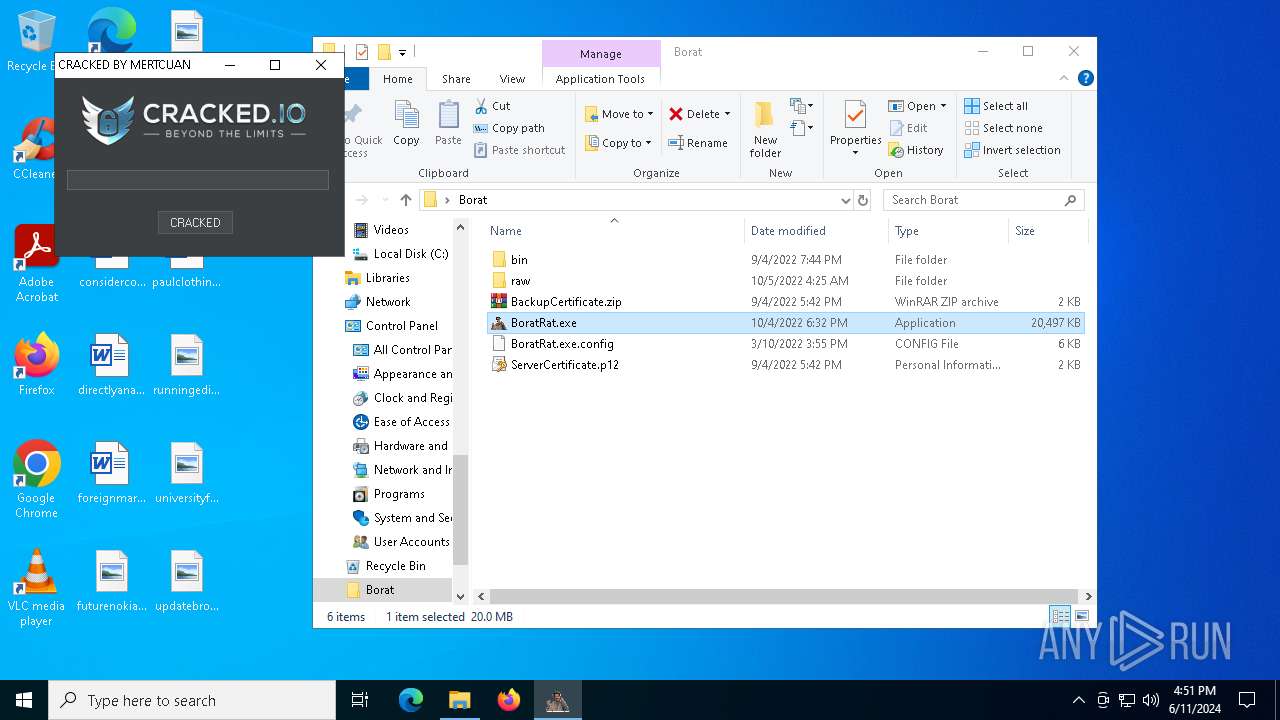
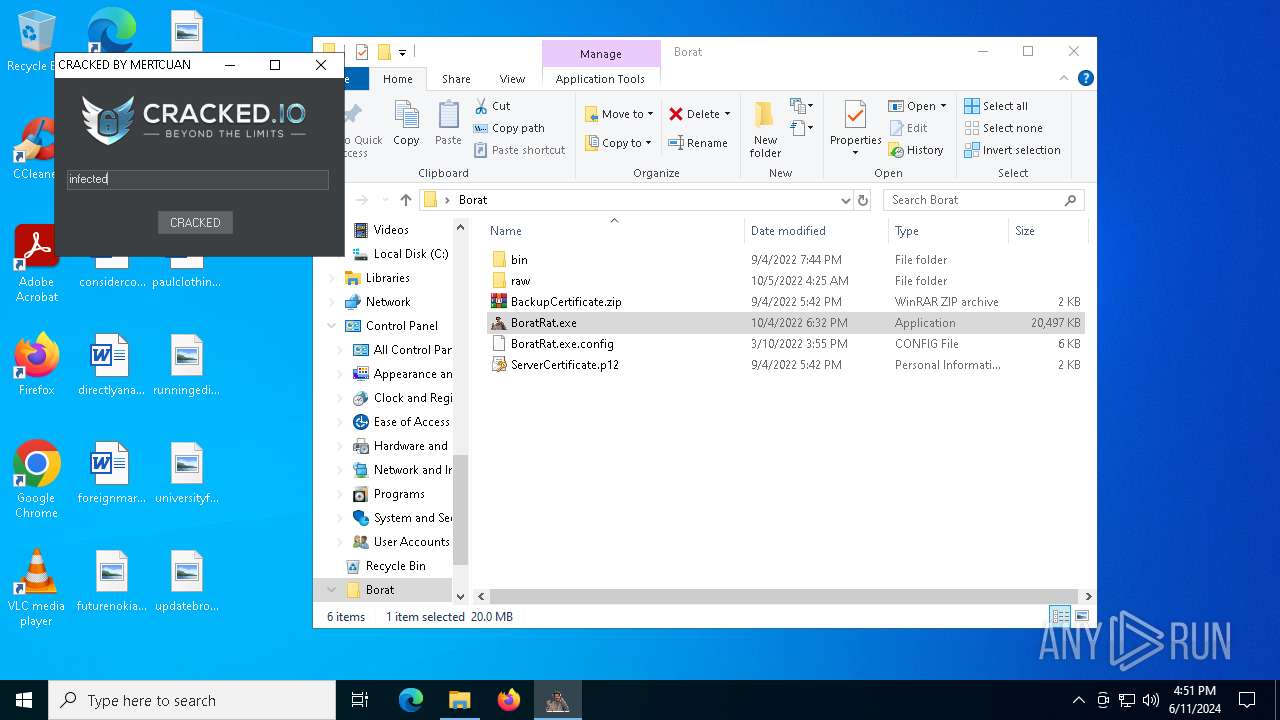
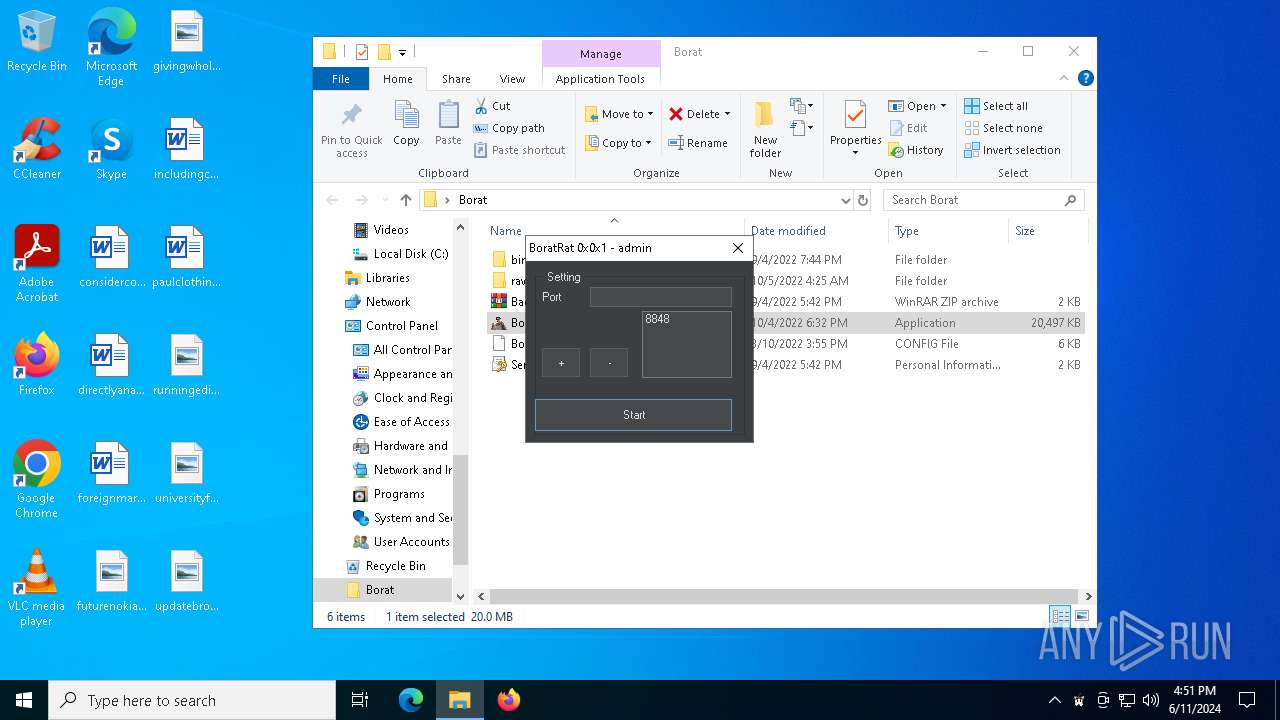
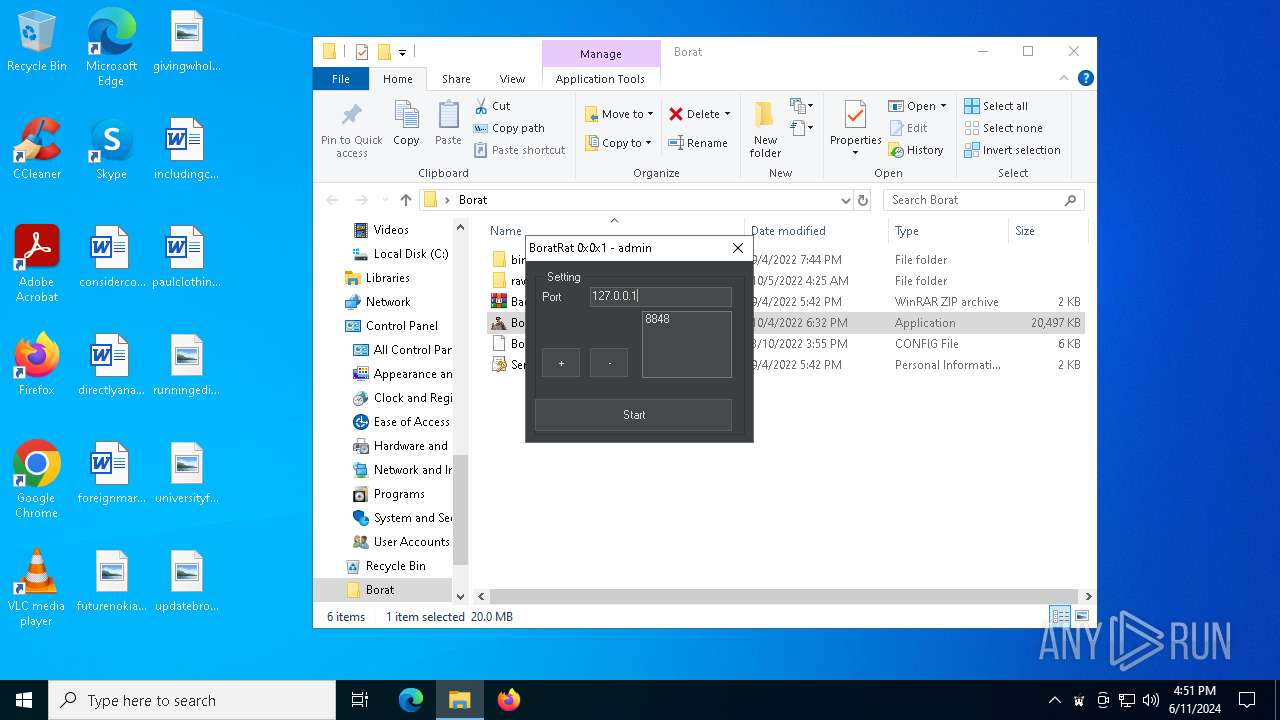
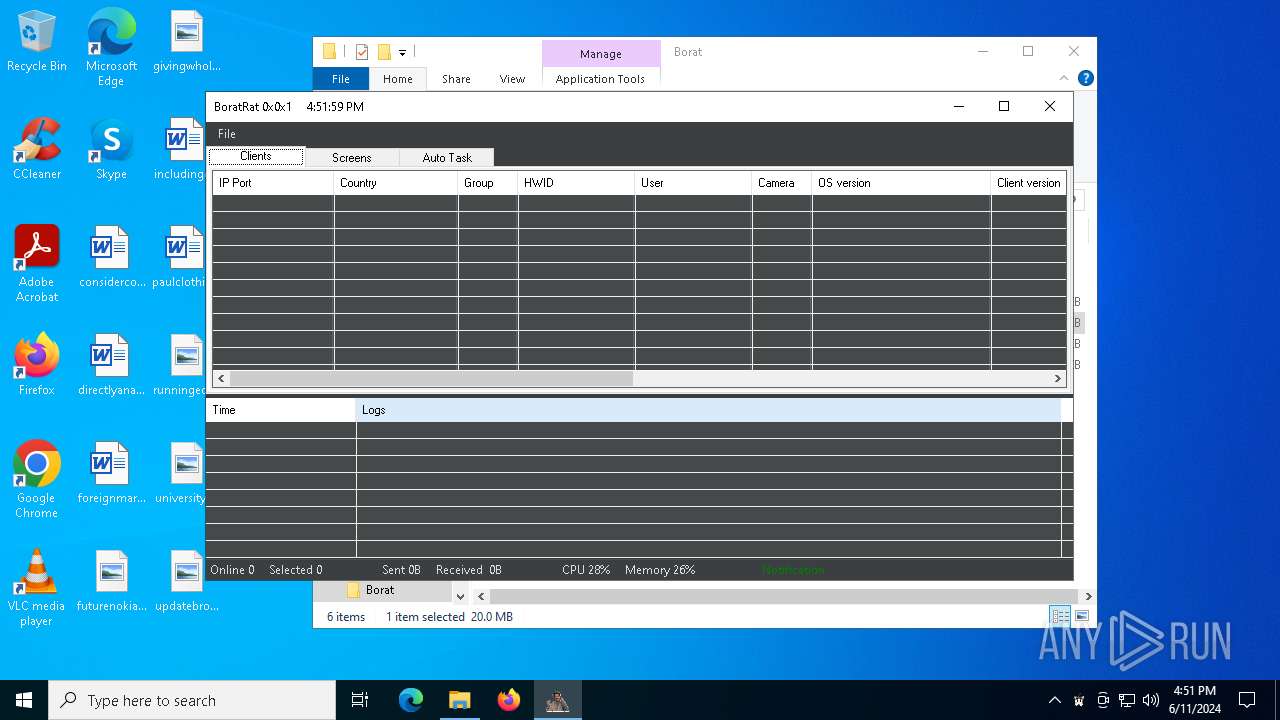
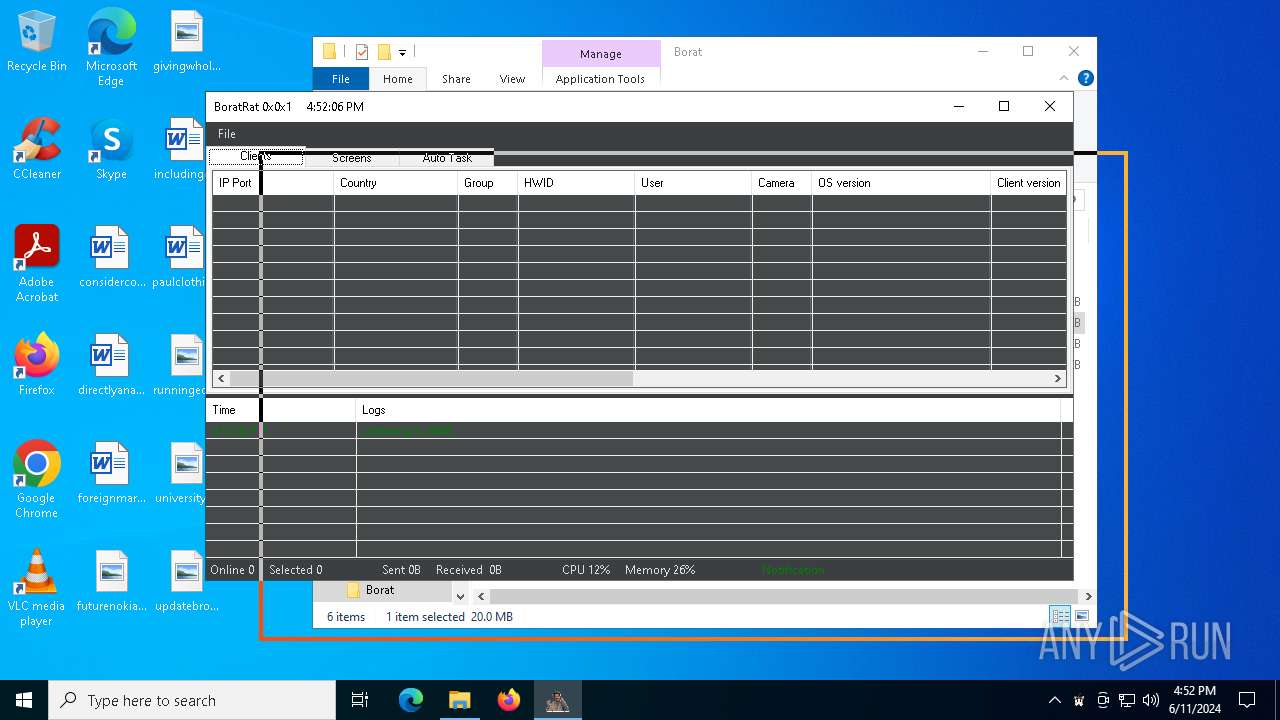
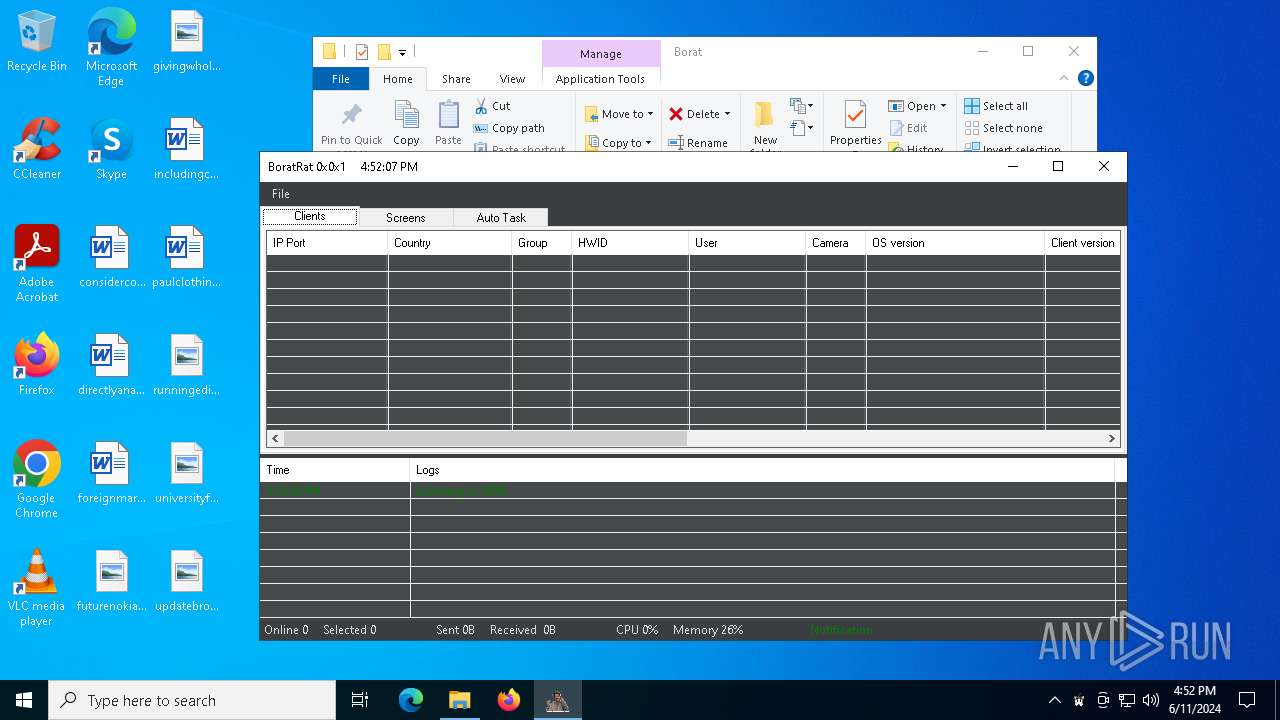
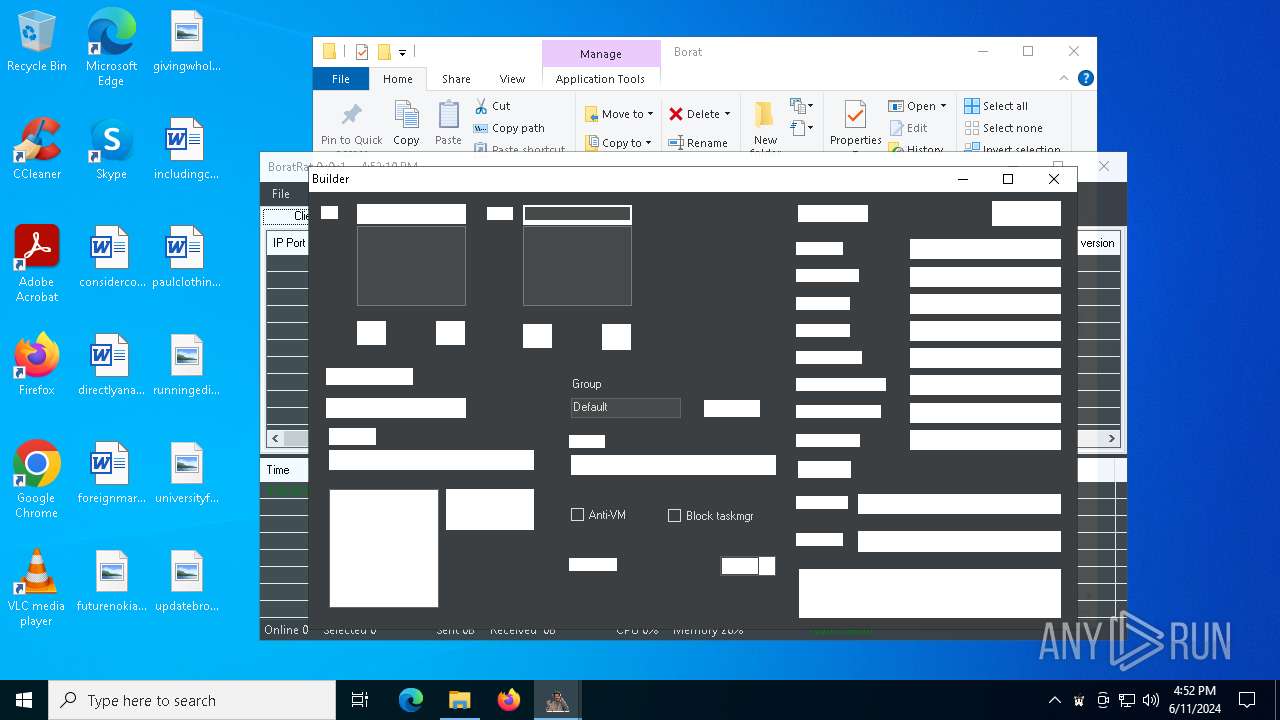
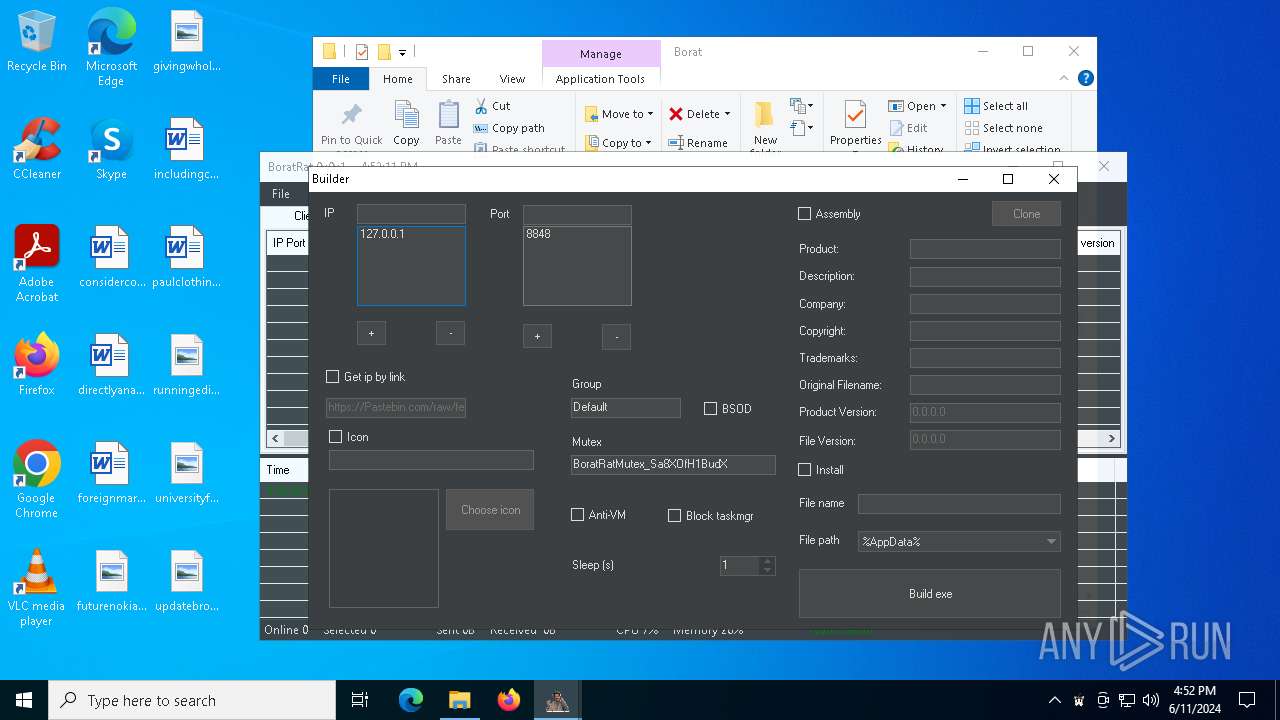
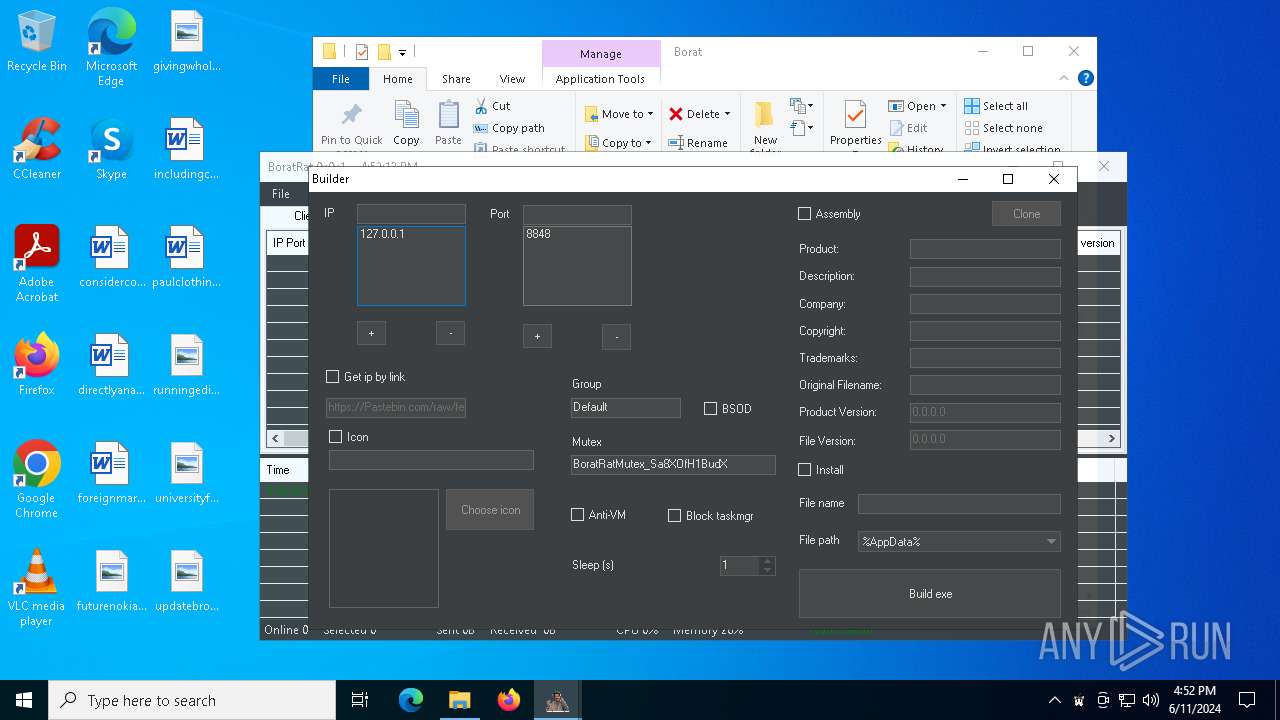
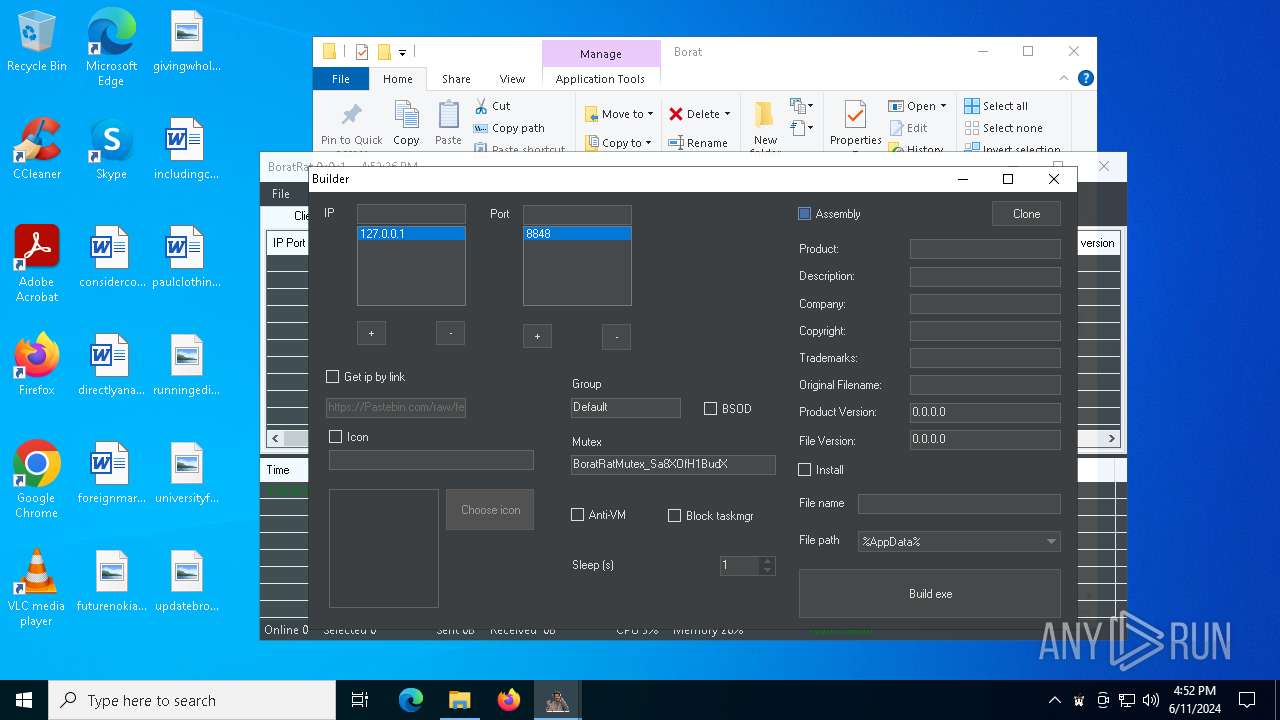
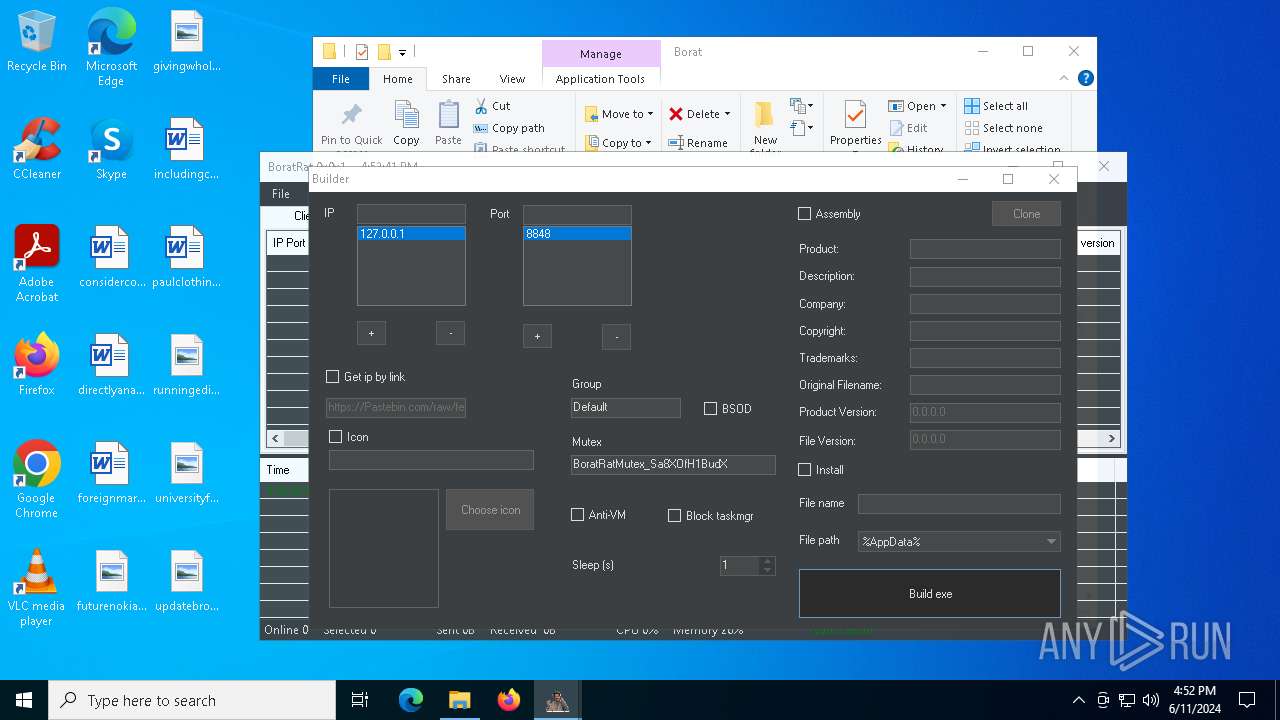
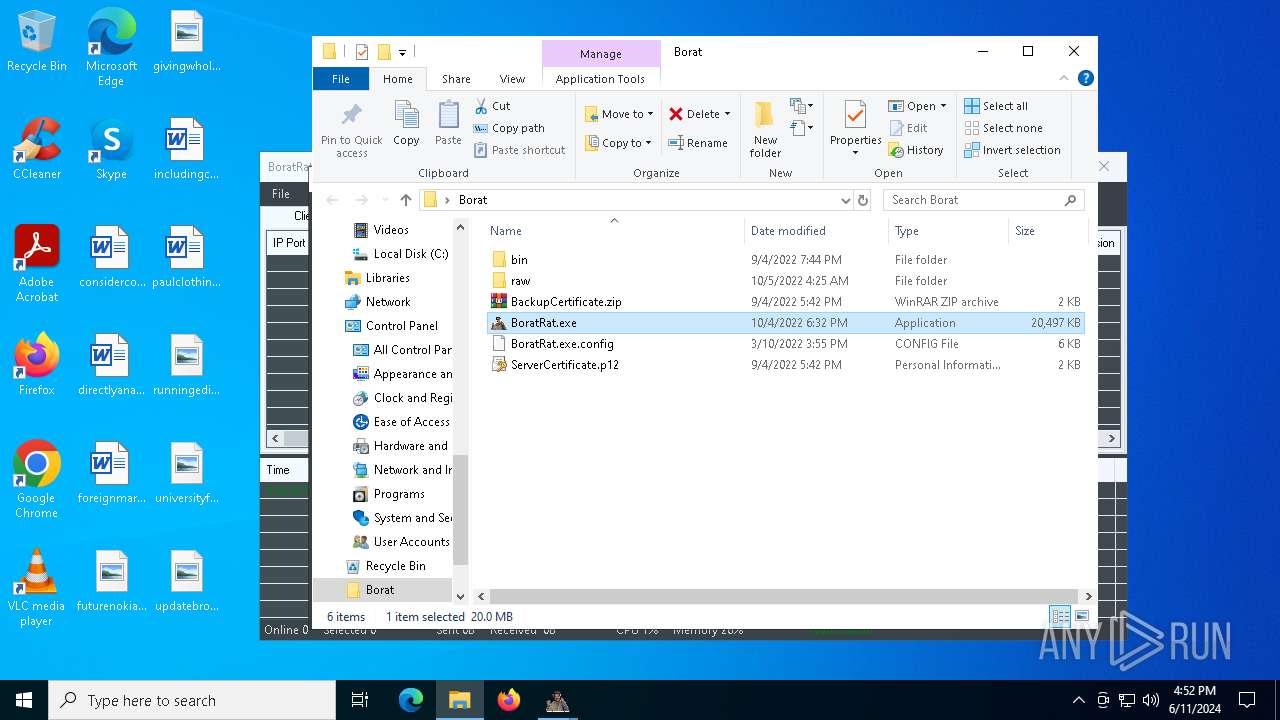
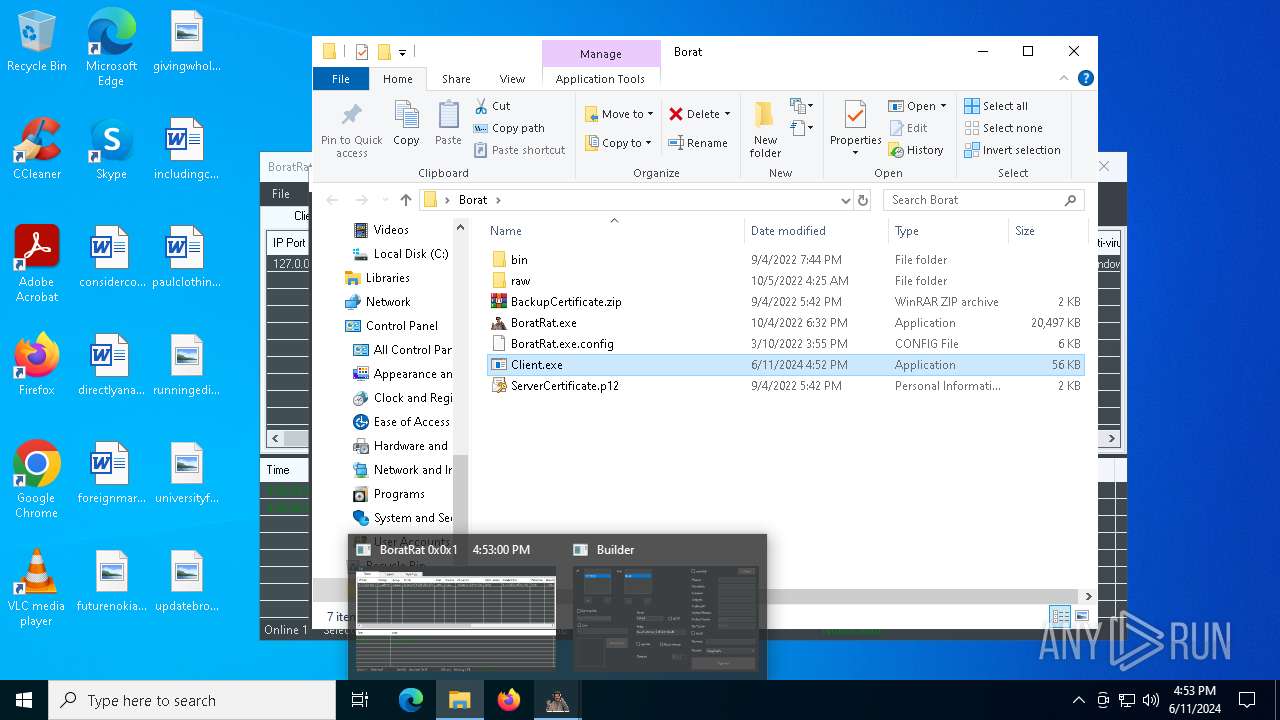
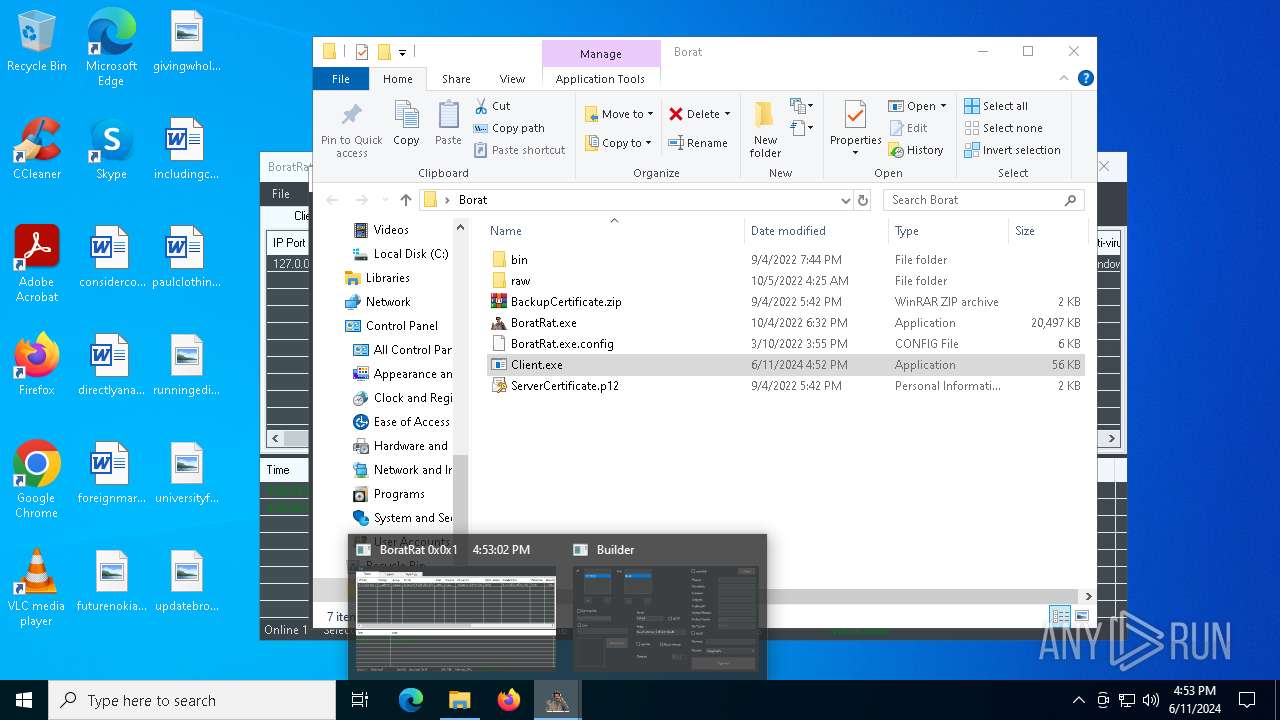
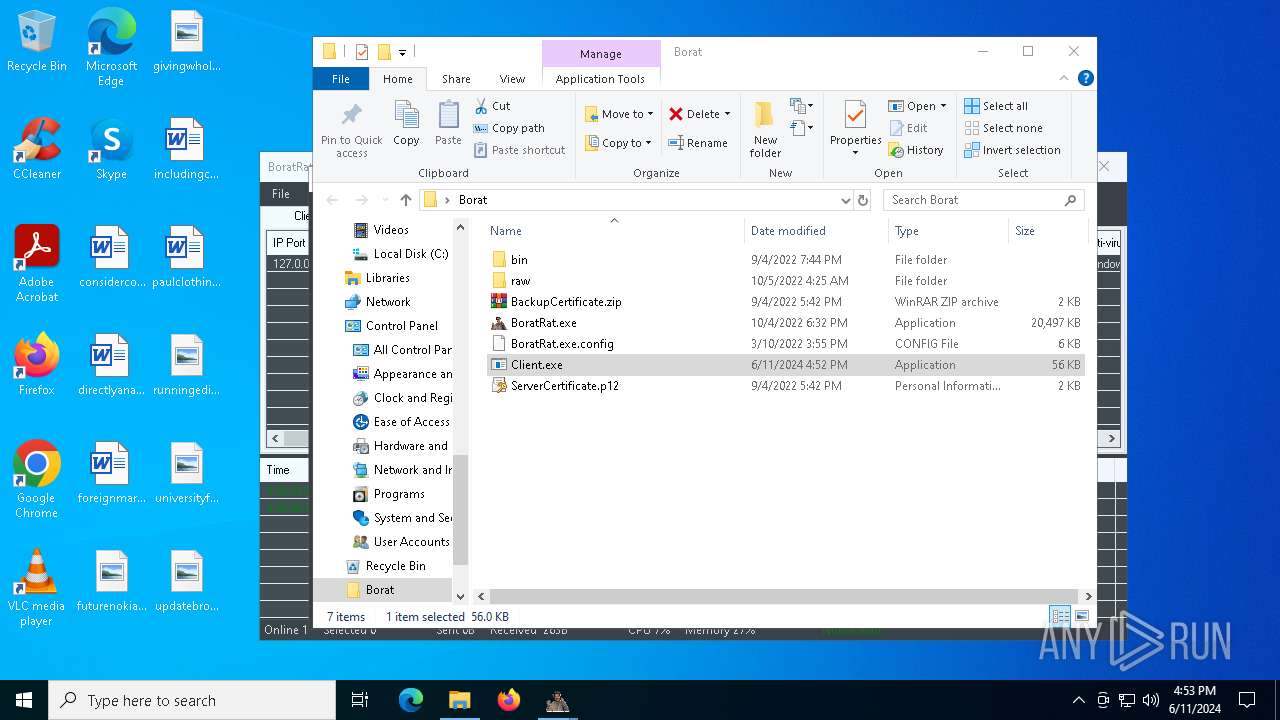
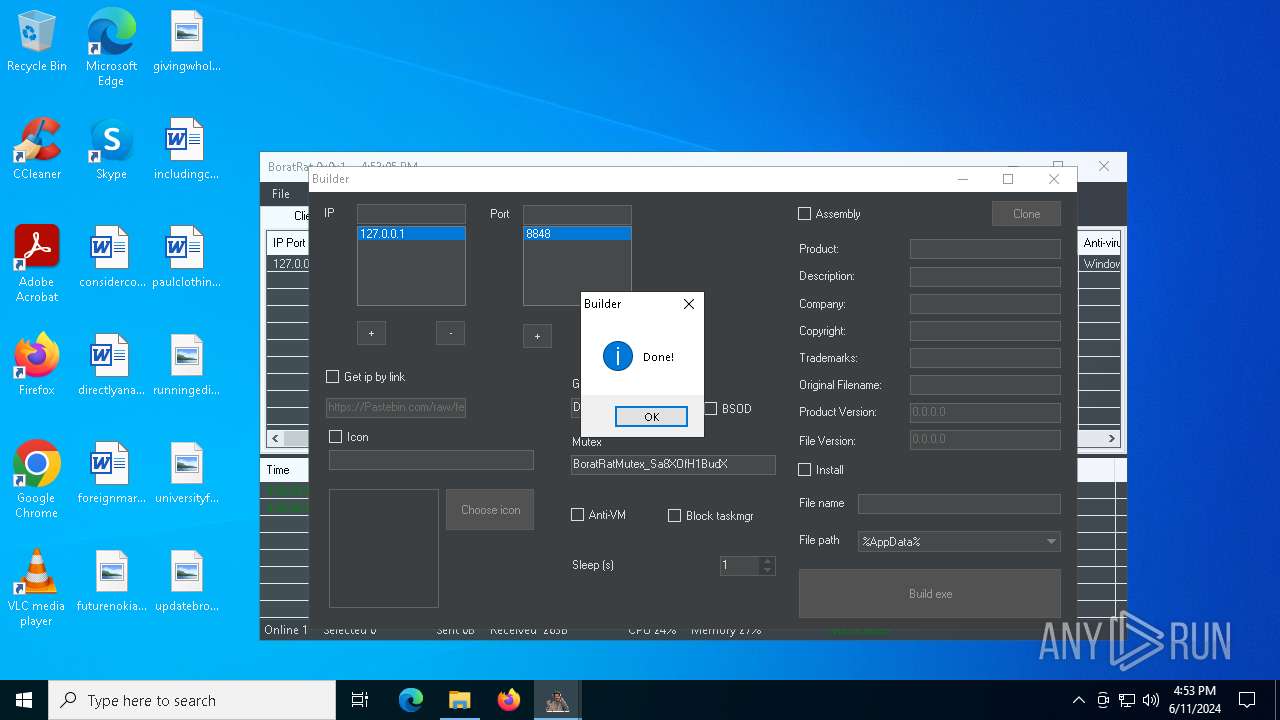
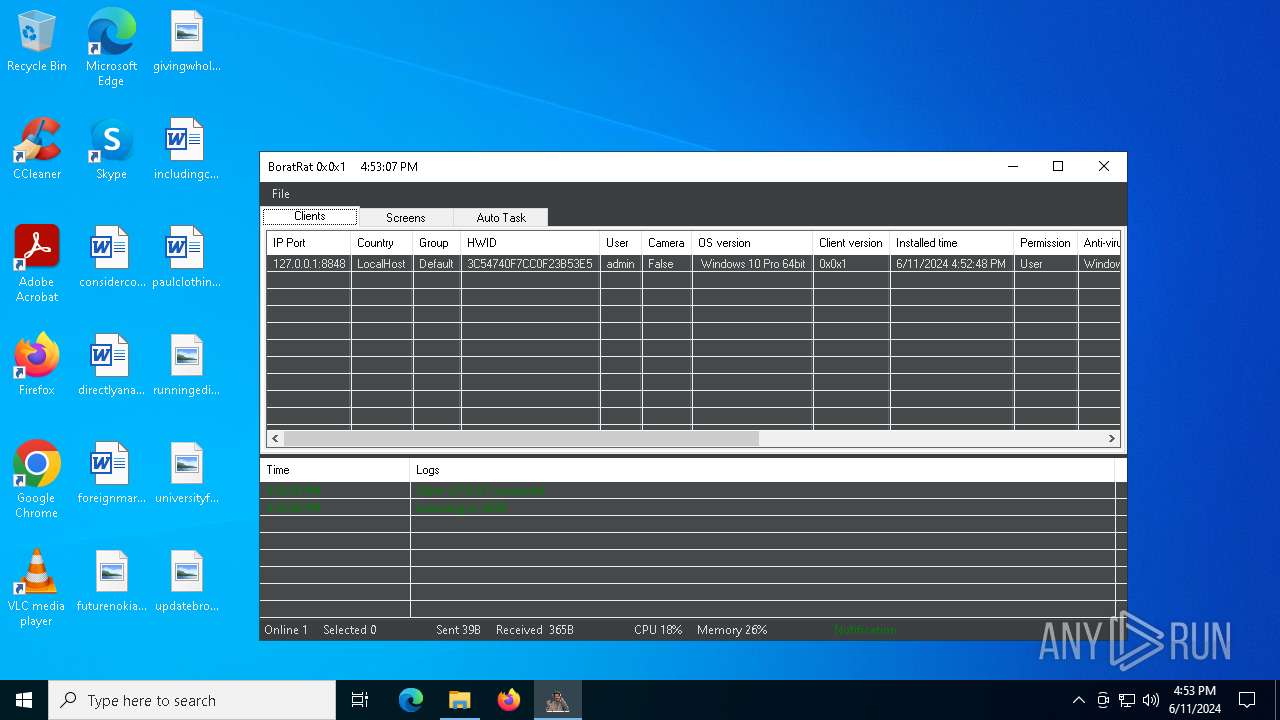
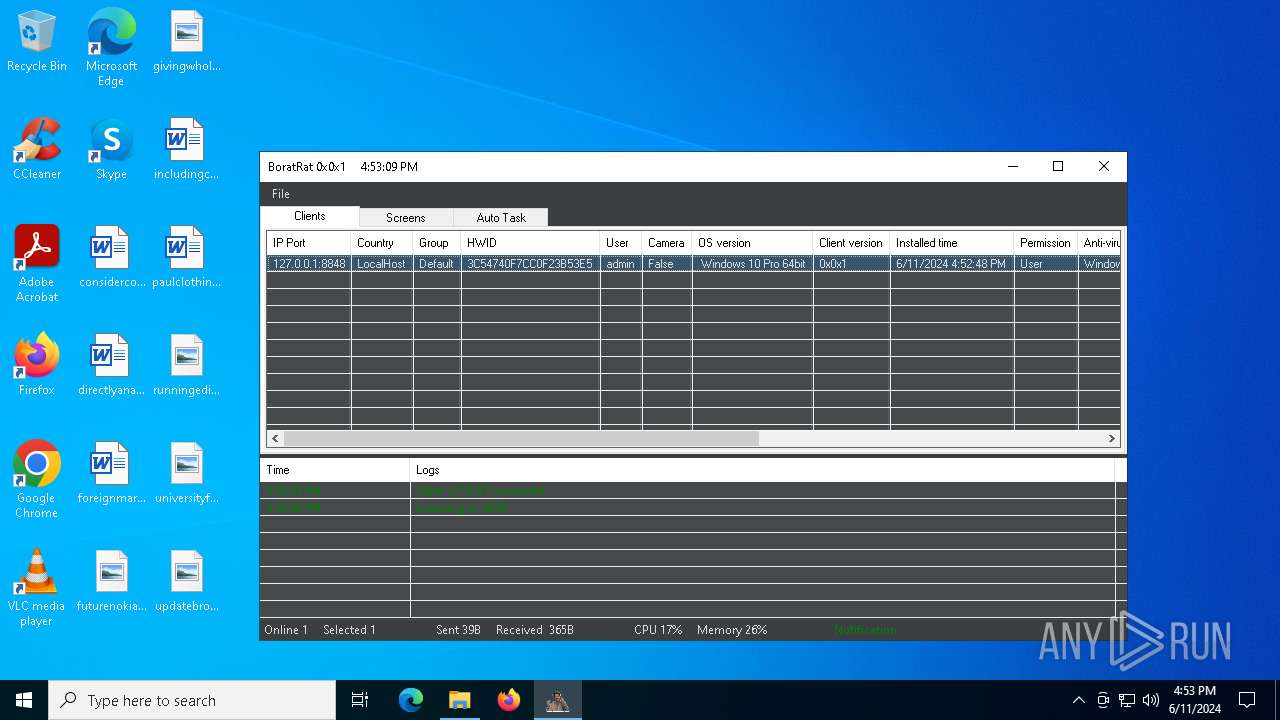
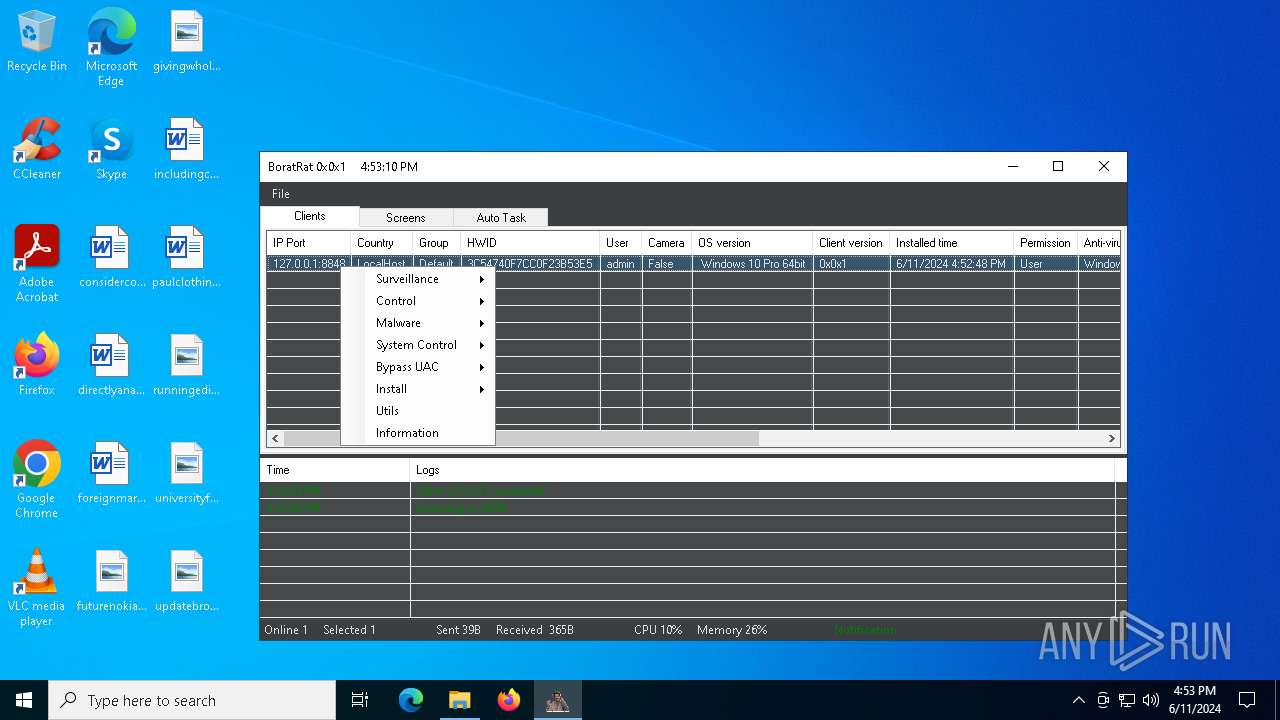
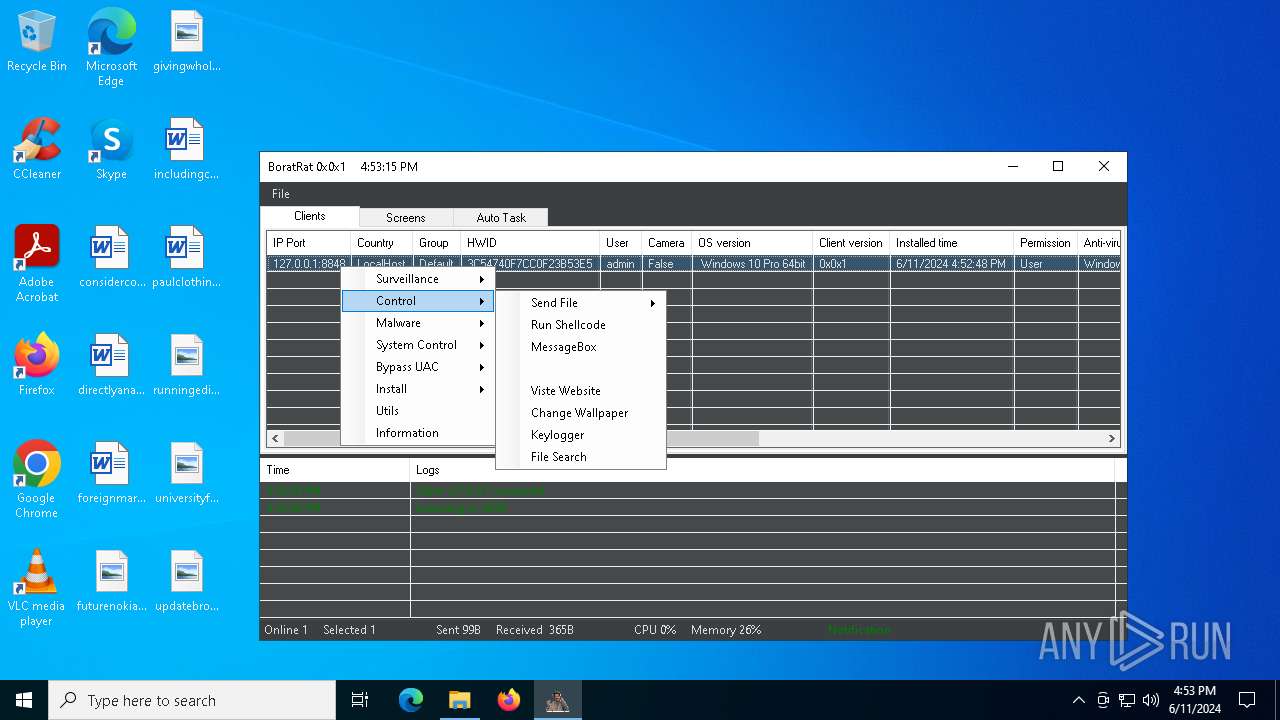
| File name: | Borat.7z |
| Full analysis: | https://app.any.run/tasks/bb932604-6819-4dfd-a3f3-96c583f7e96b |
| Verdict: | Malicious activity |
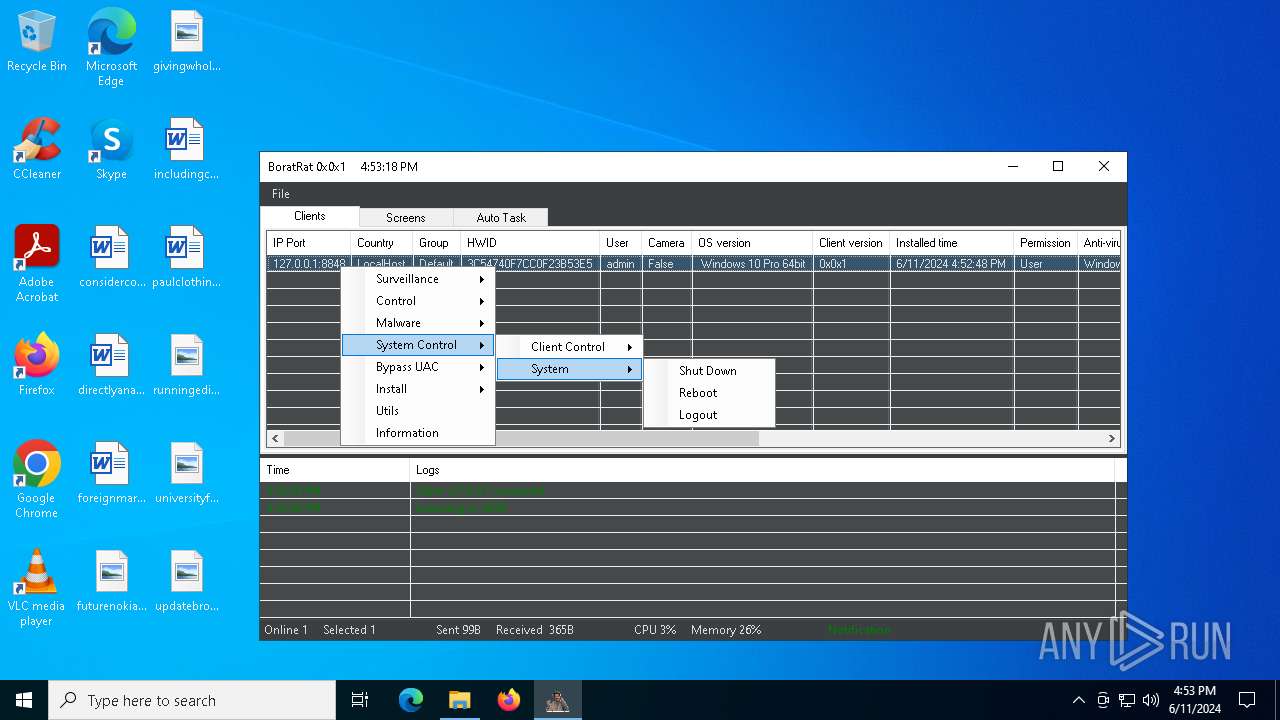
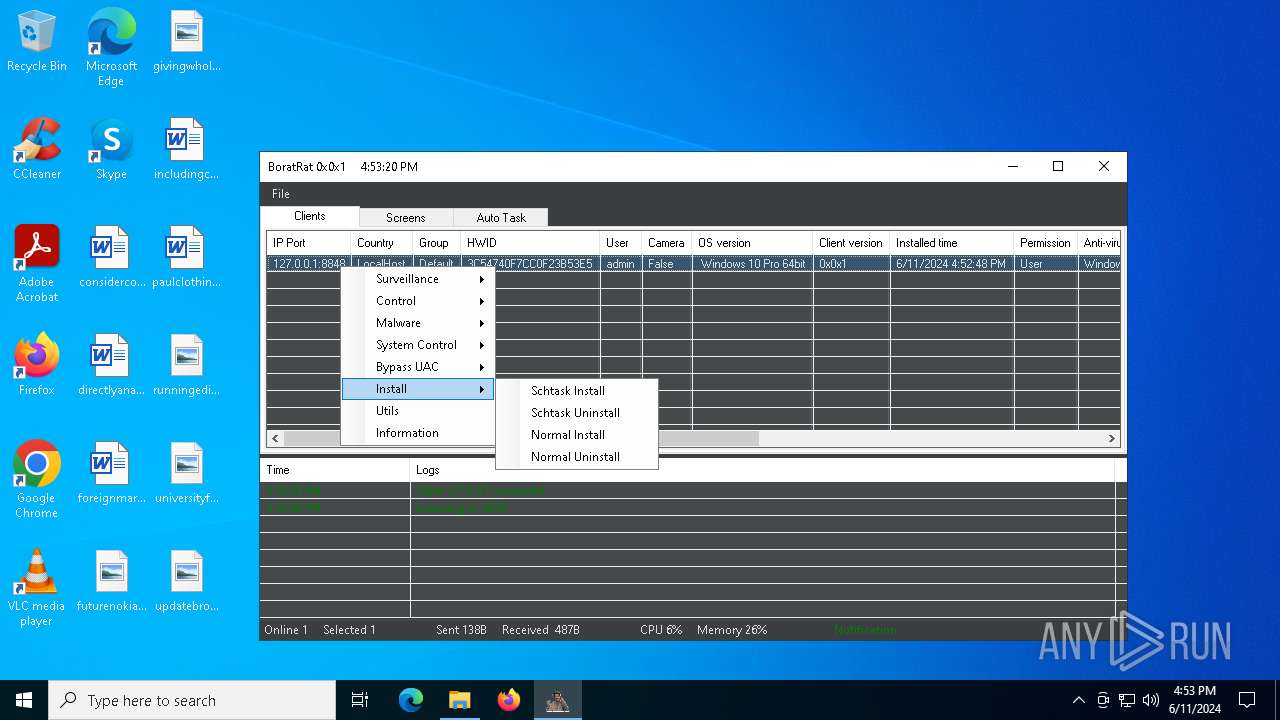
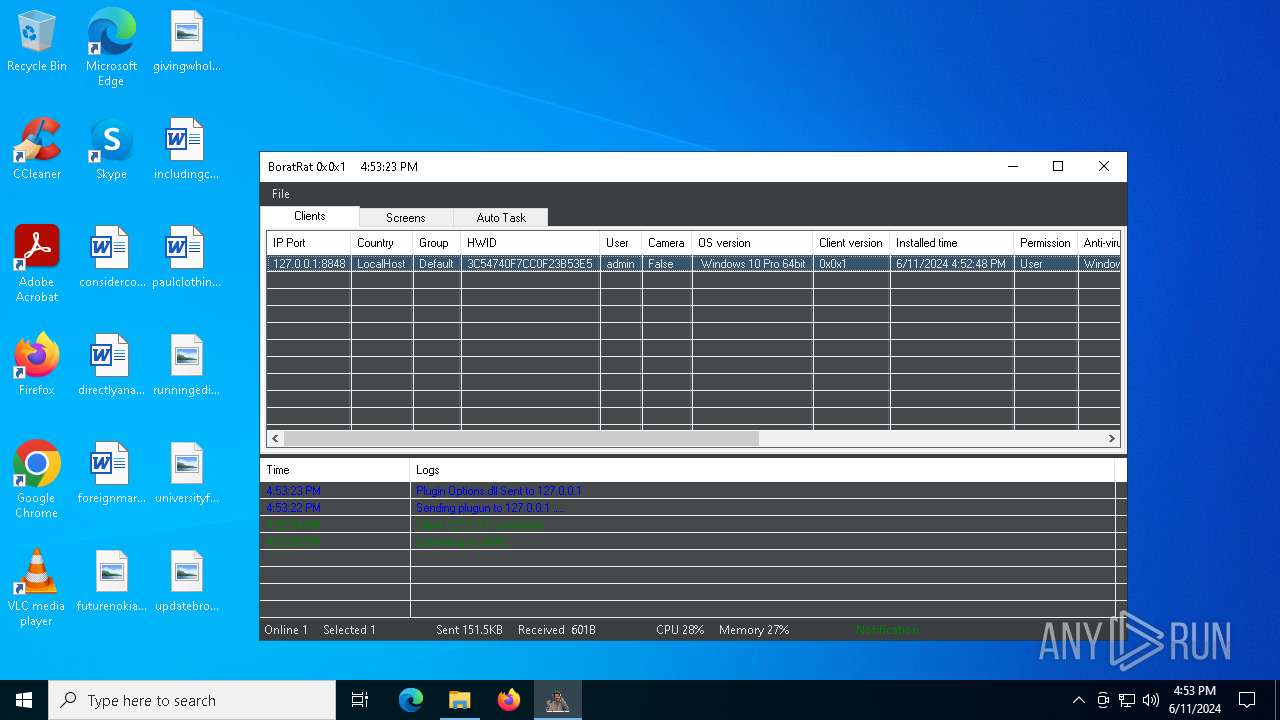
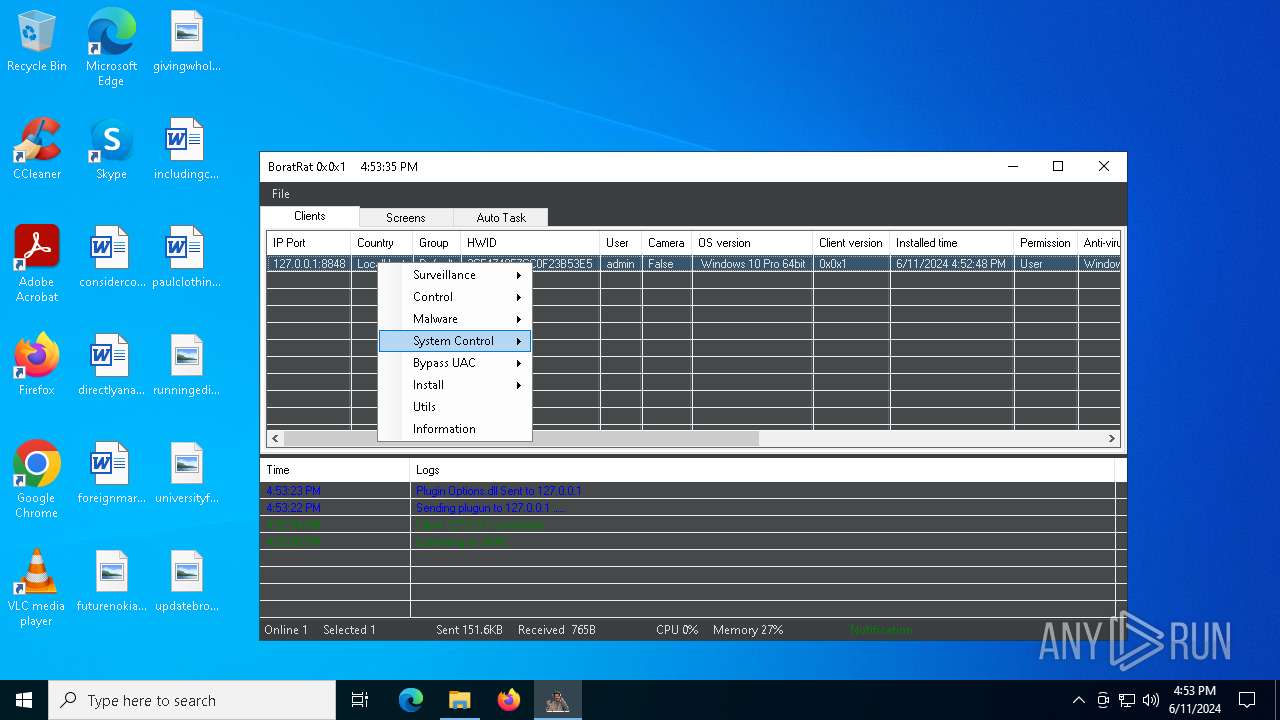
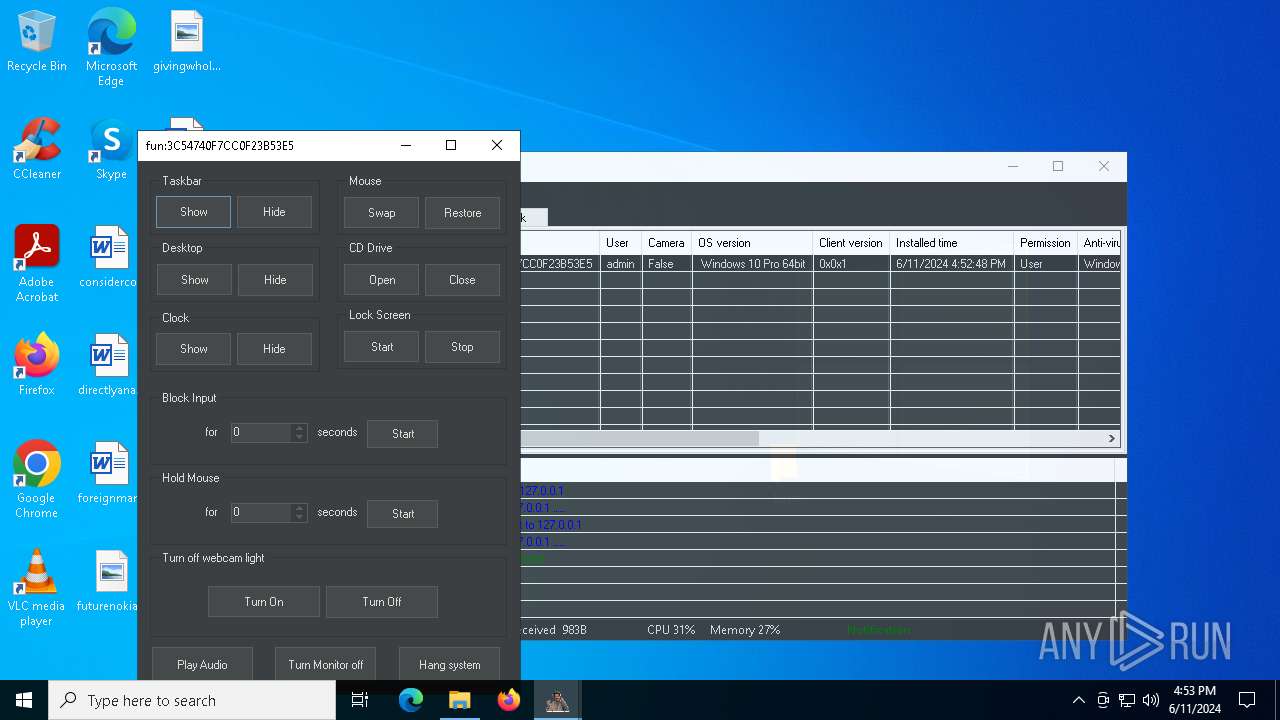
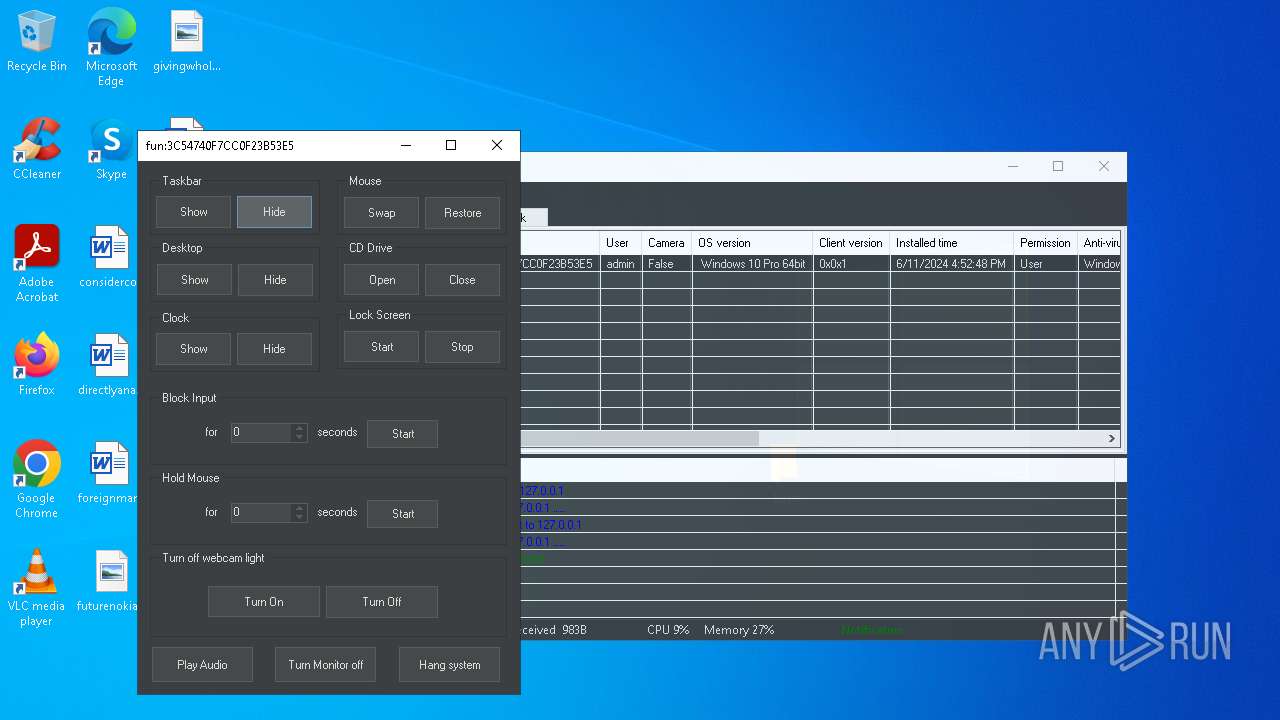
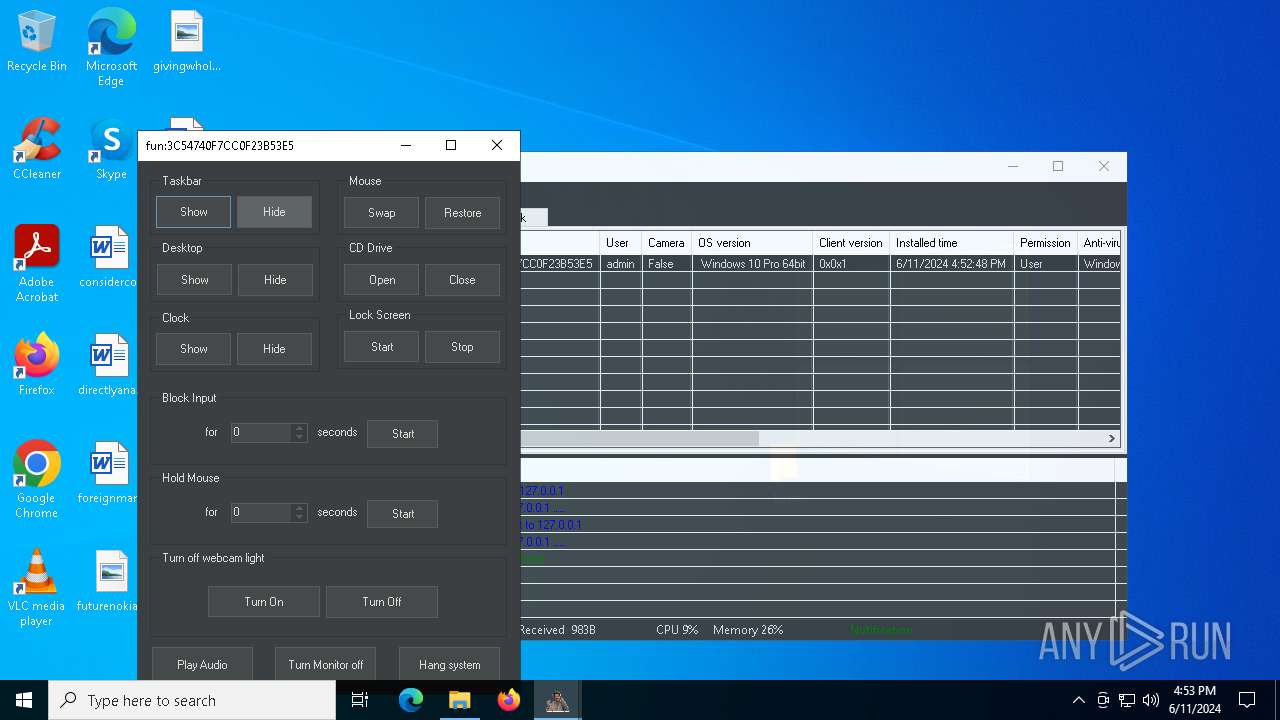
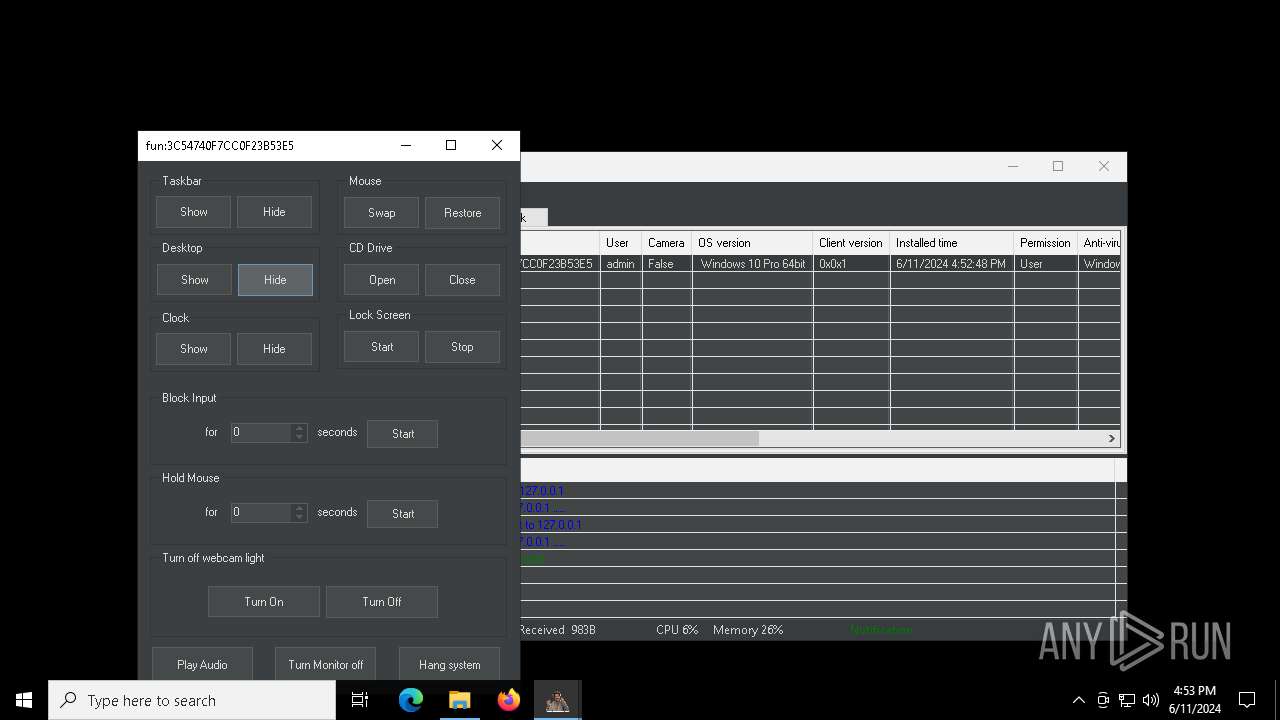
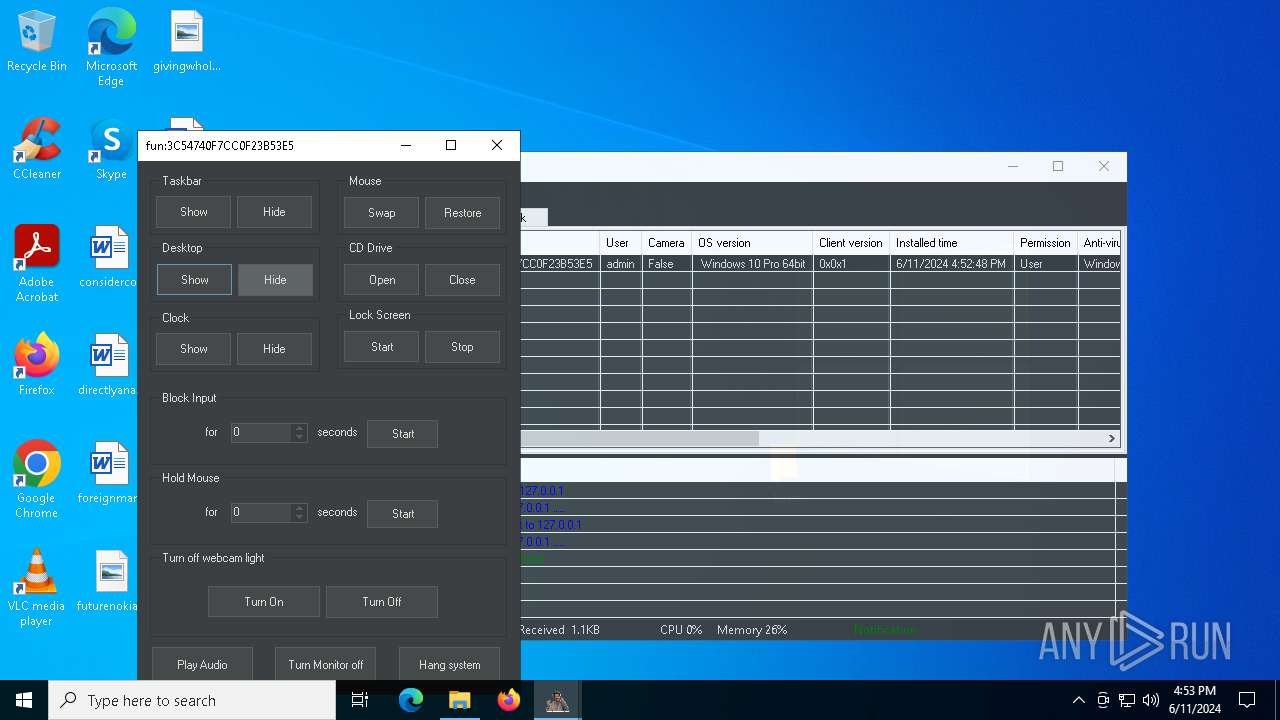
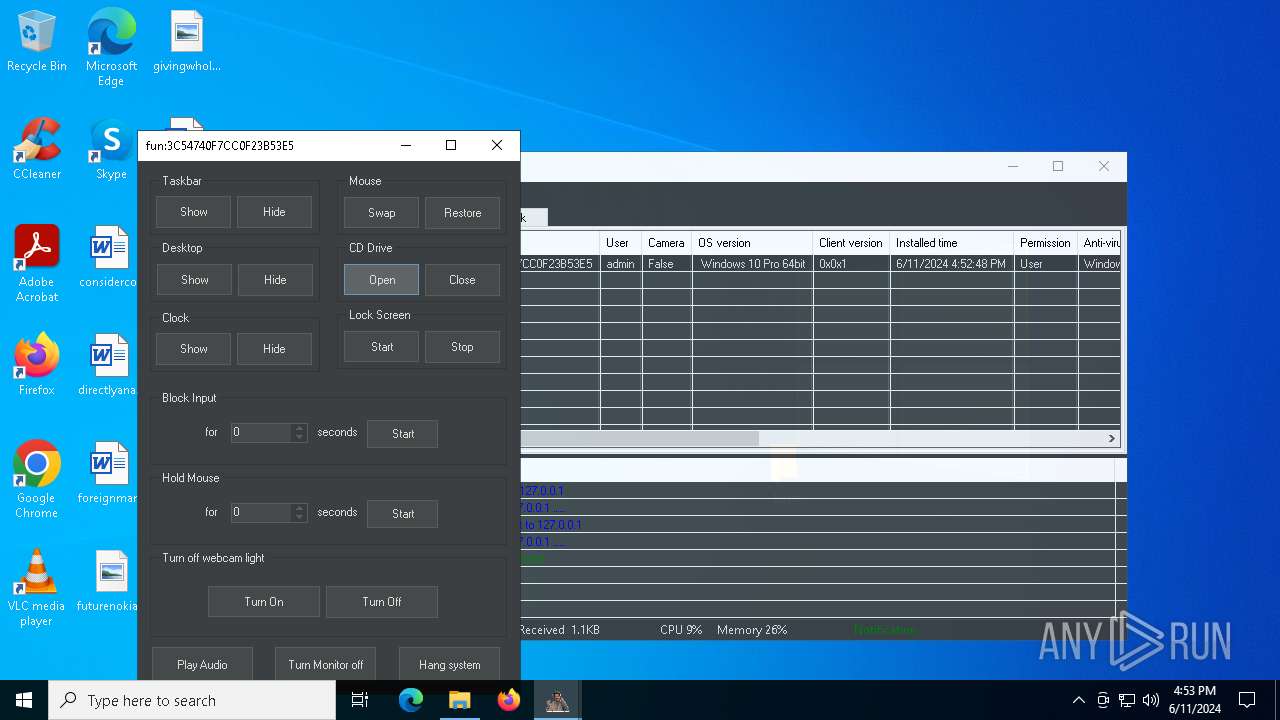
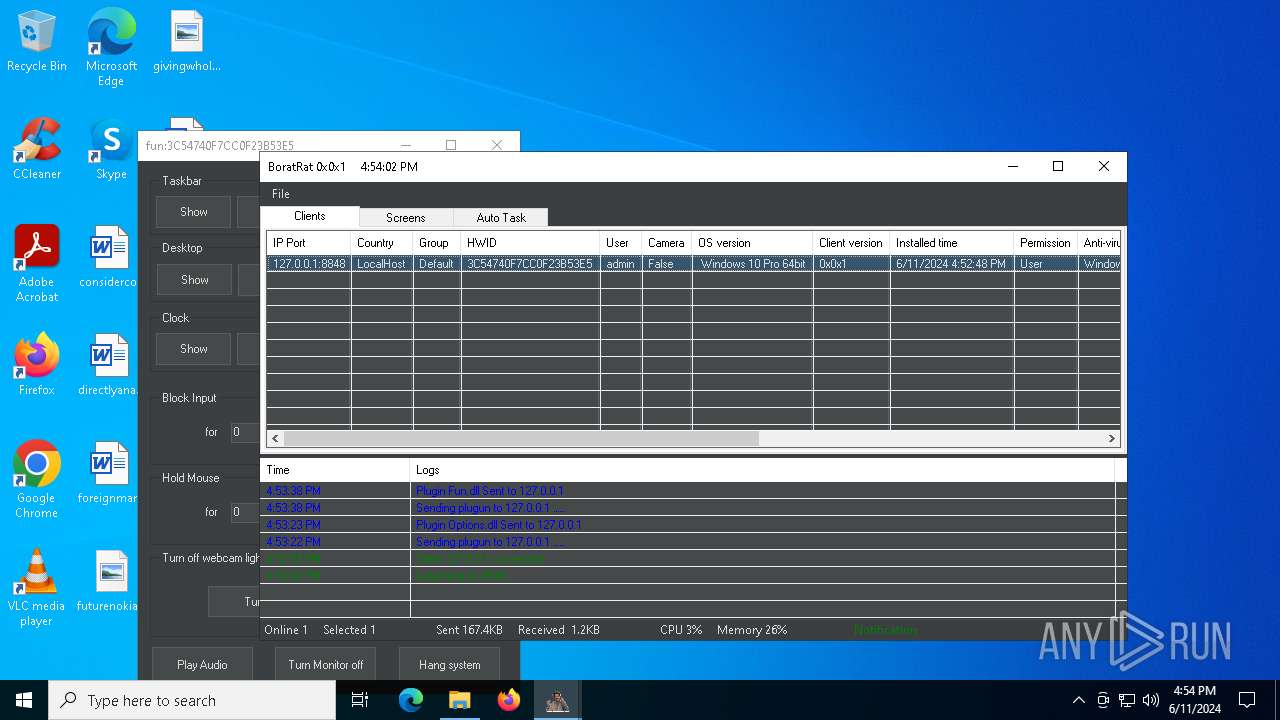
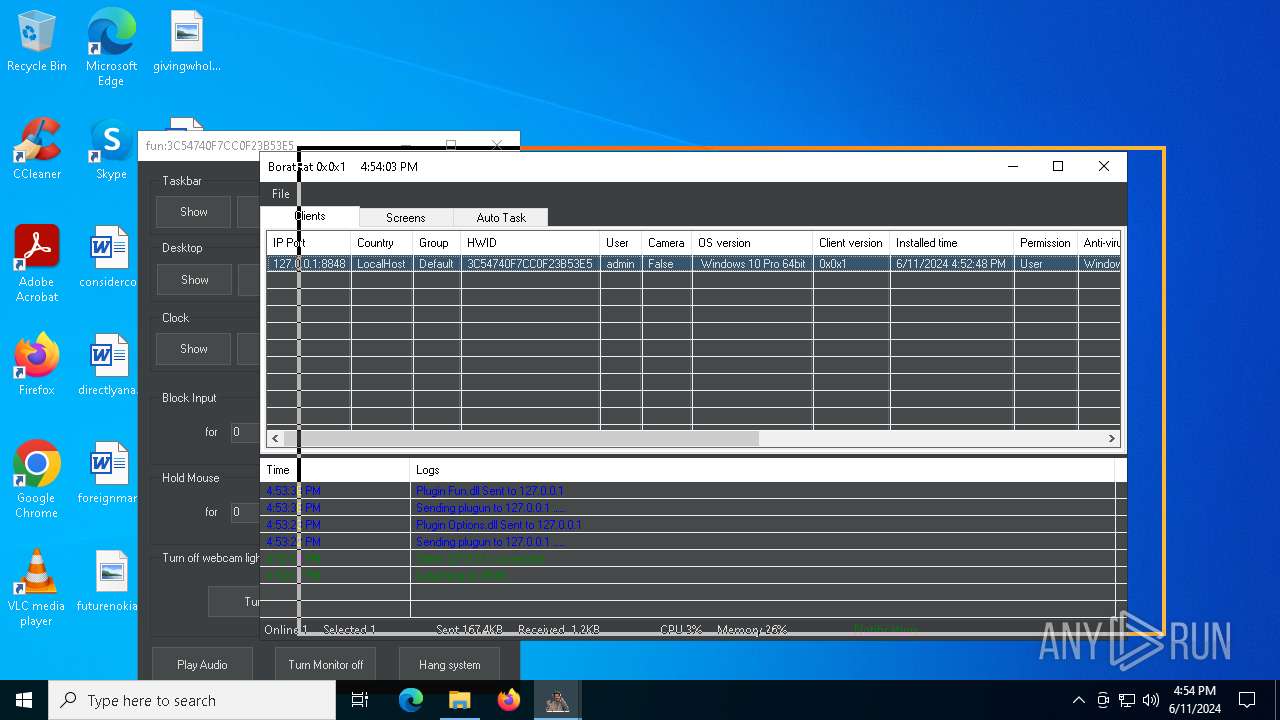
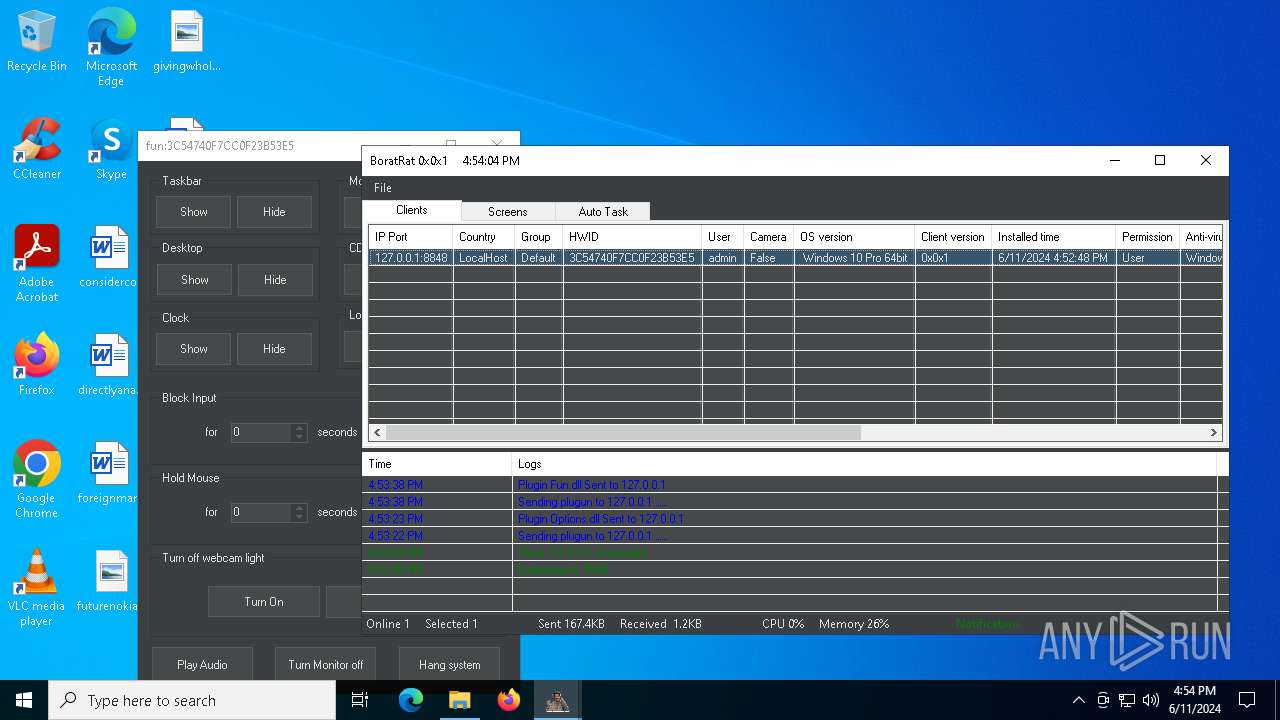
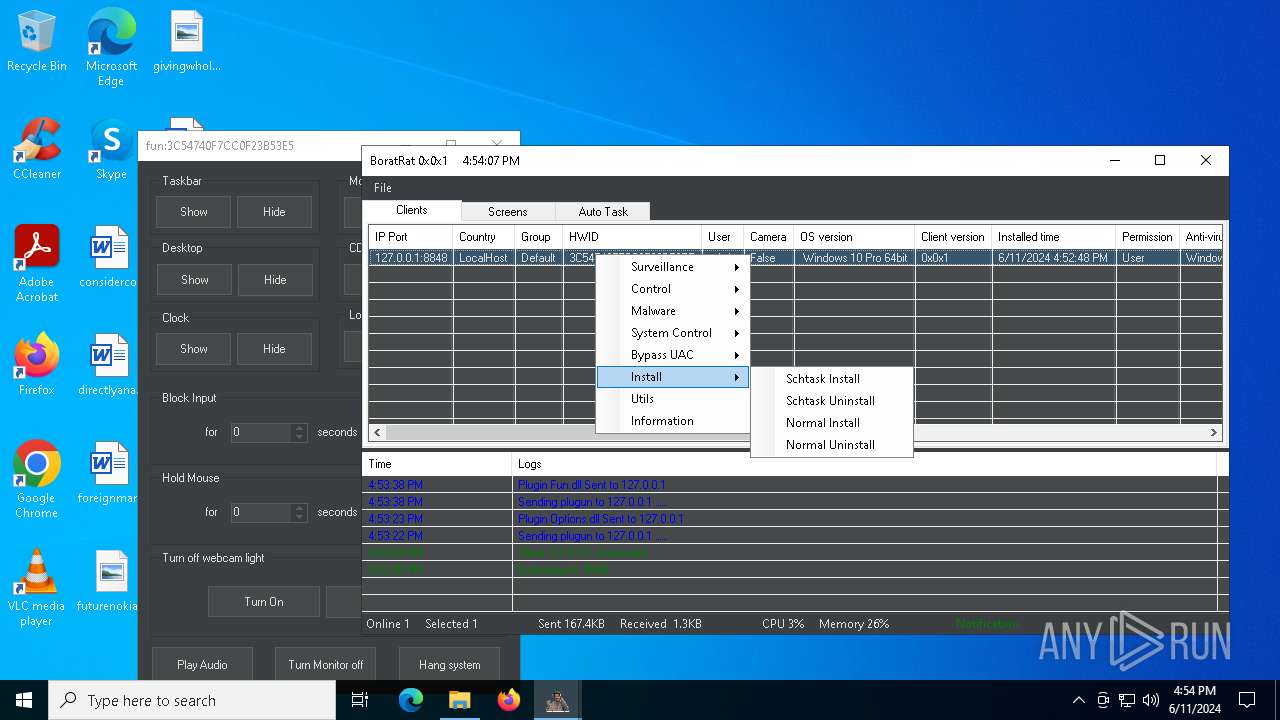
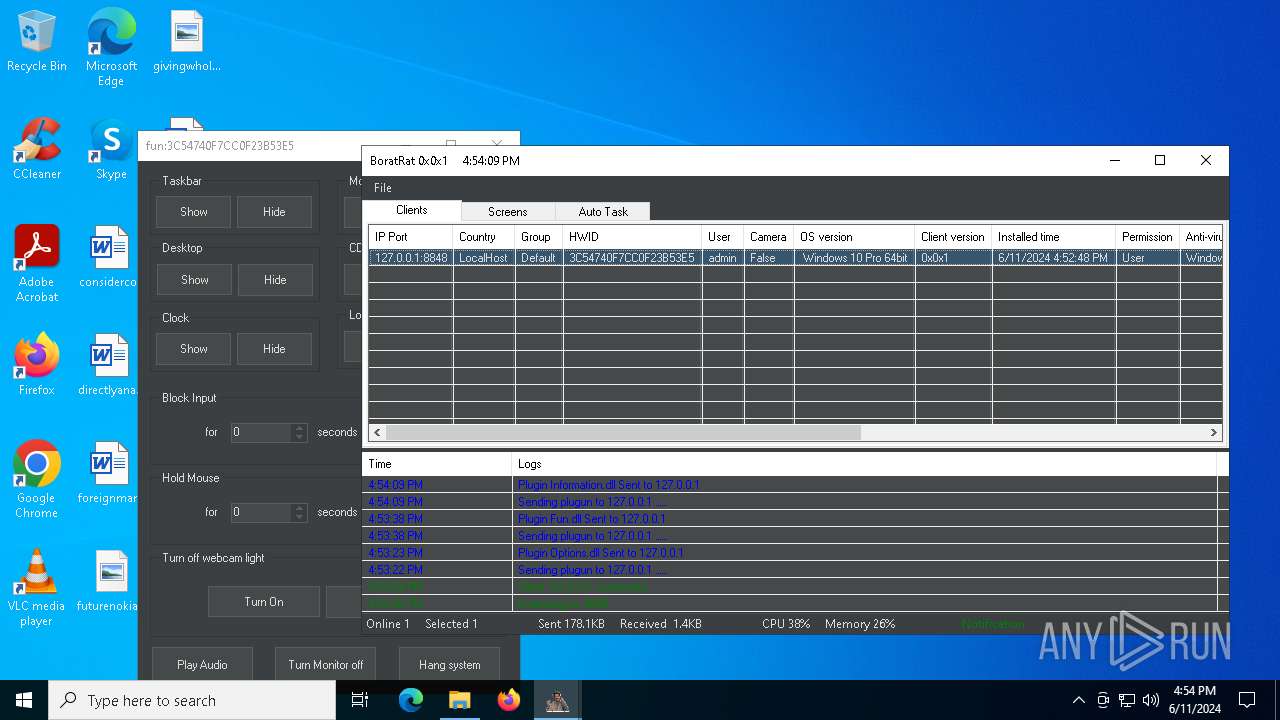
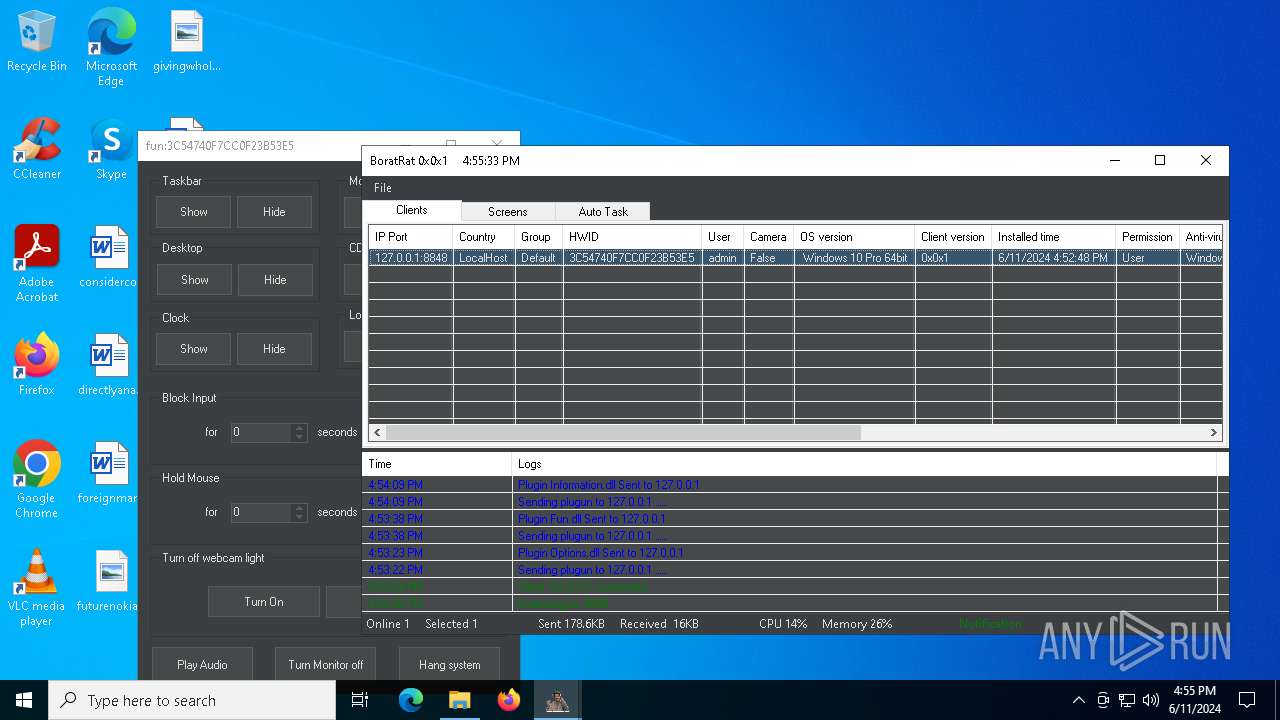
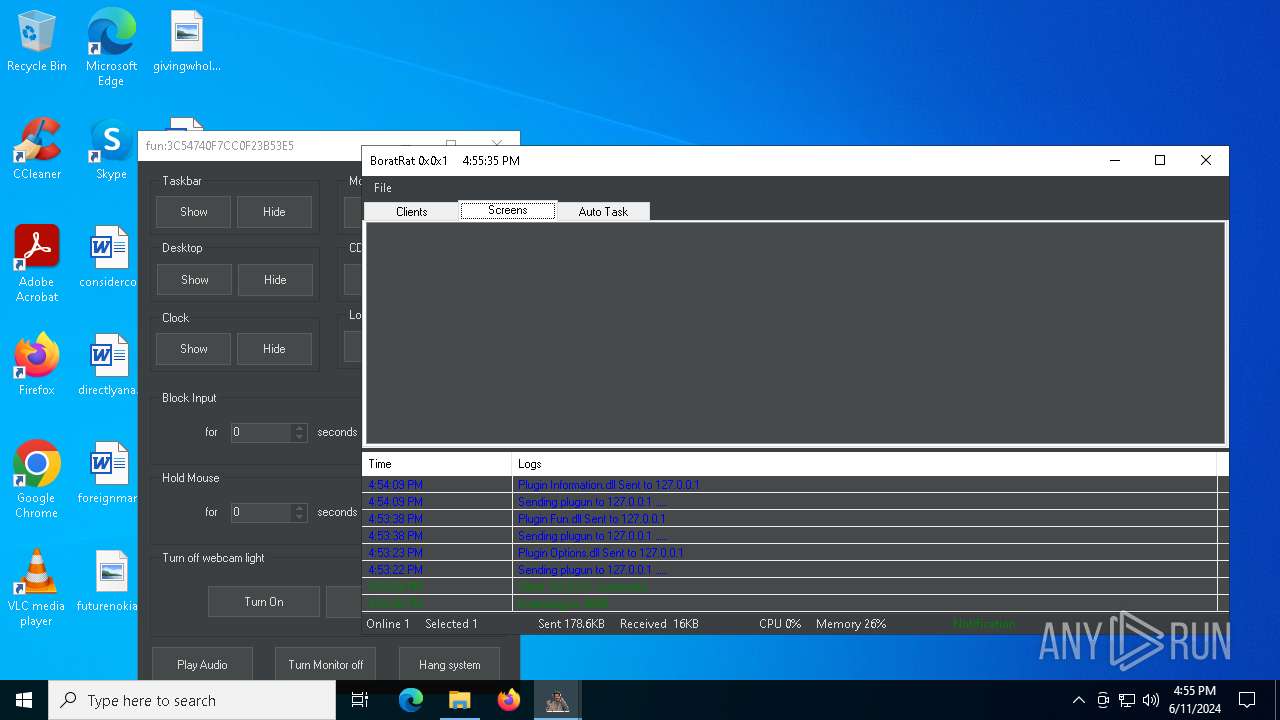
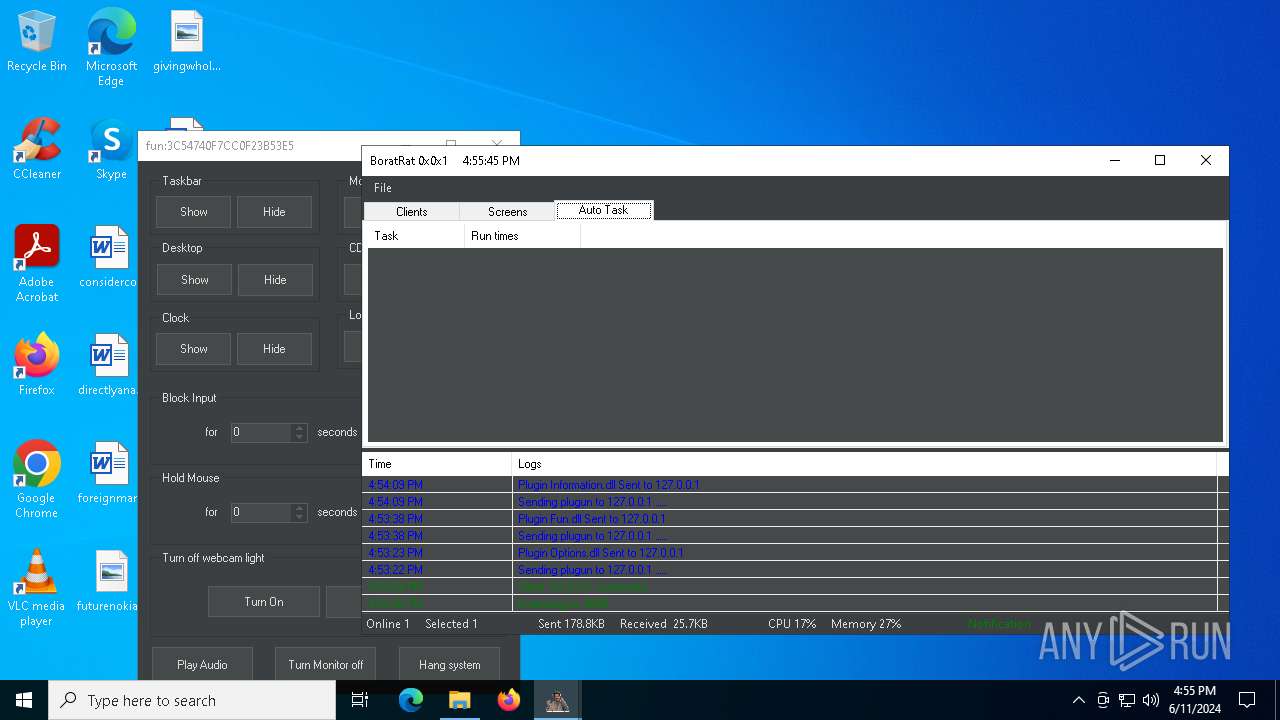
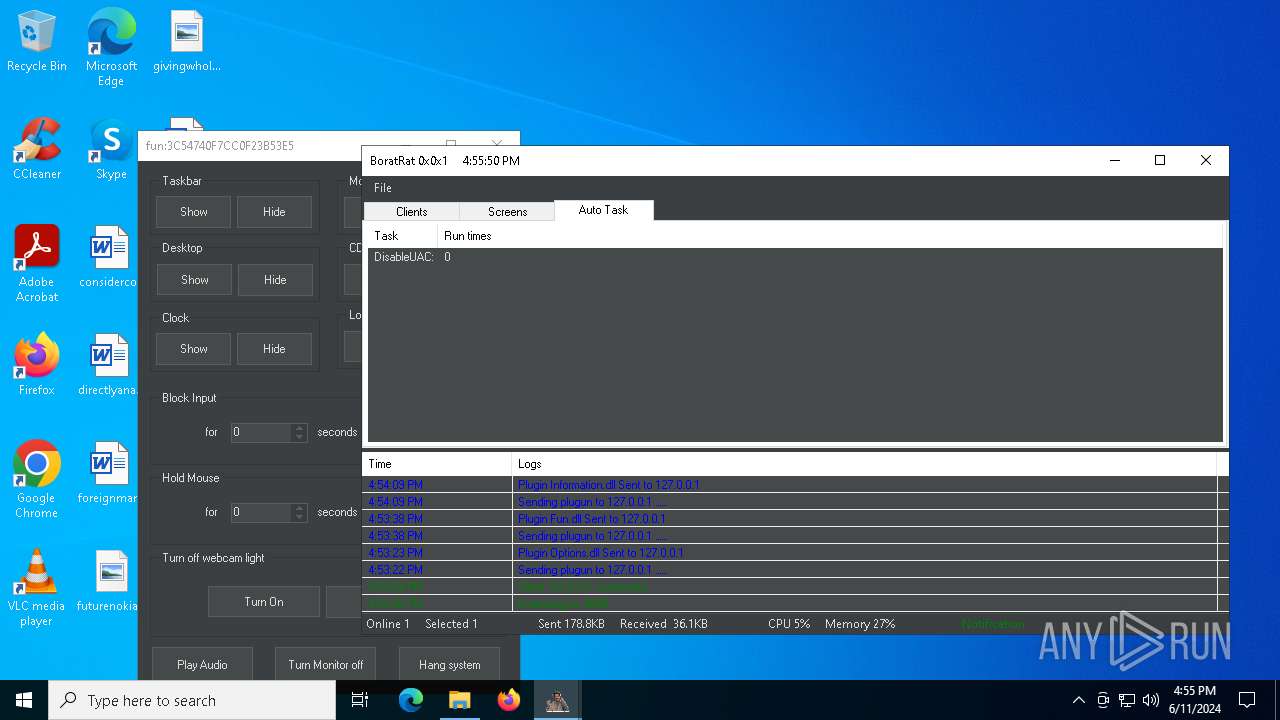
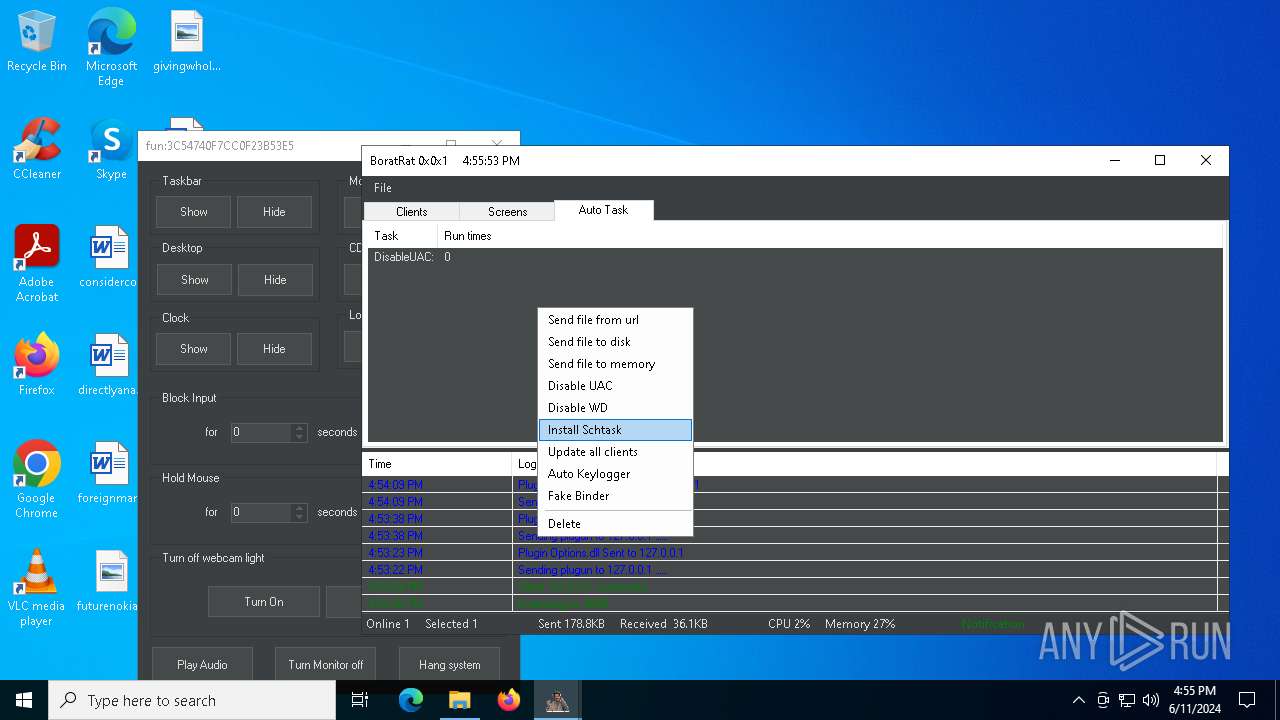
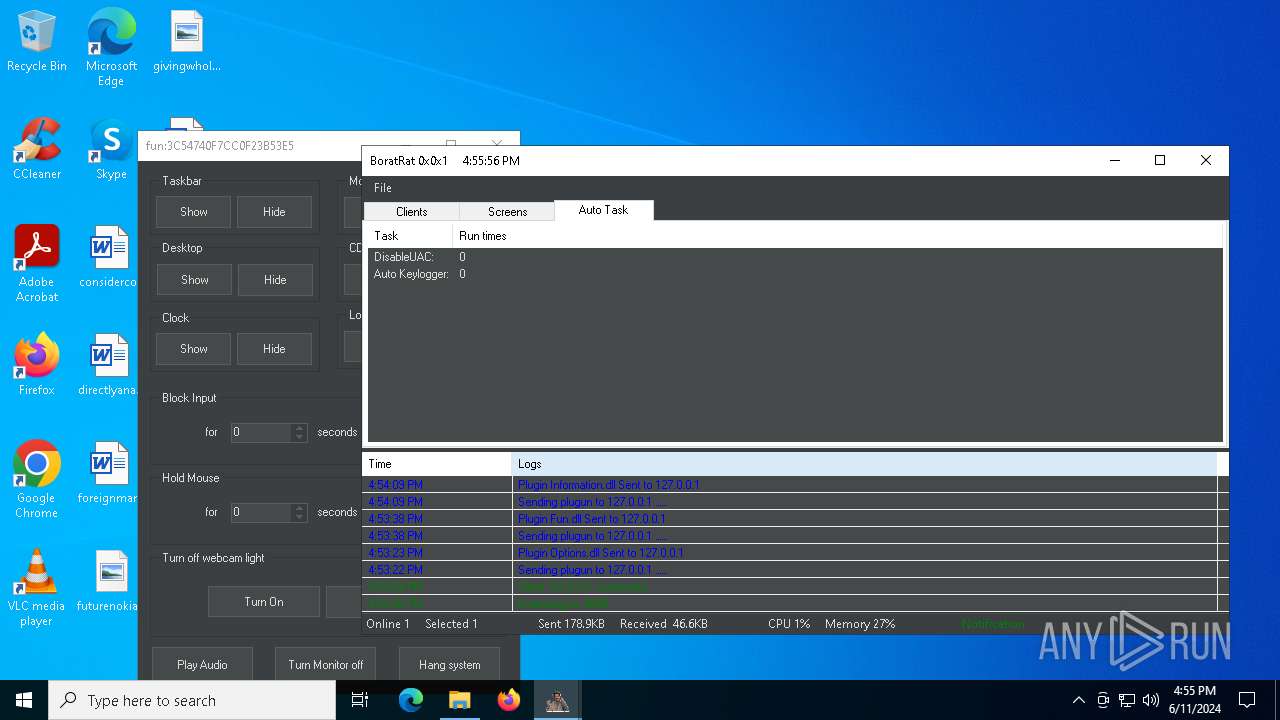
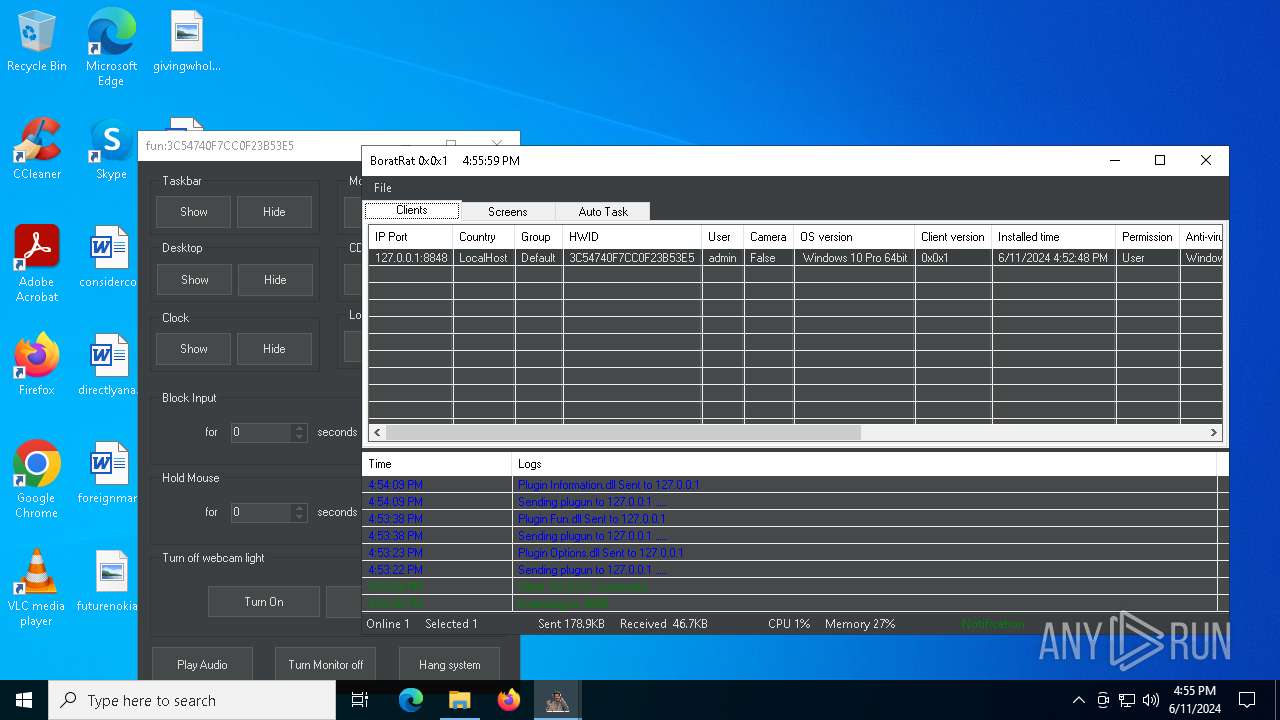
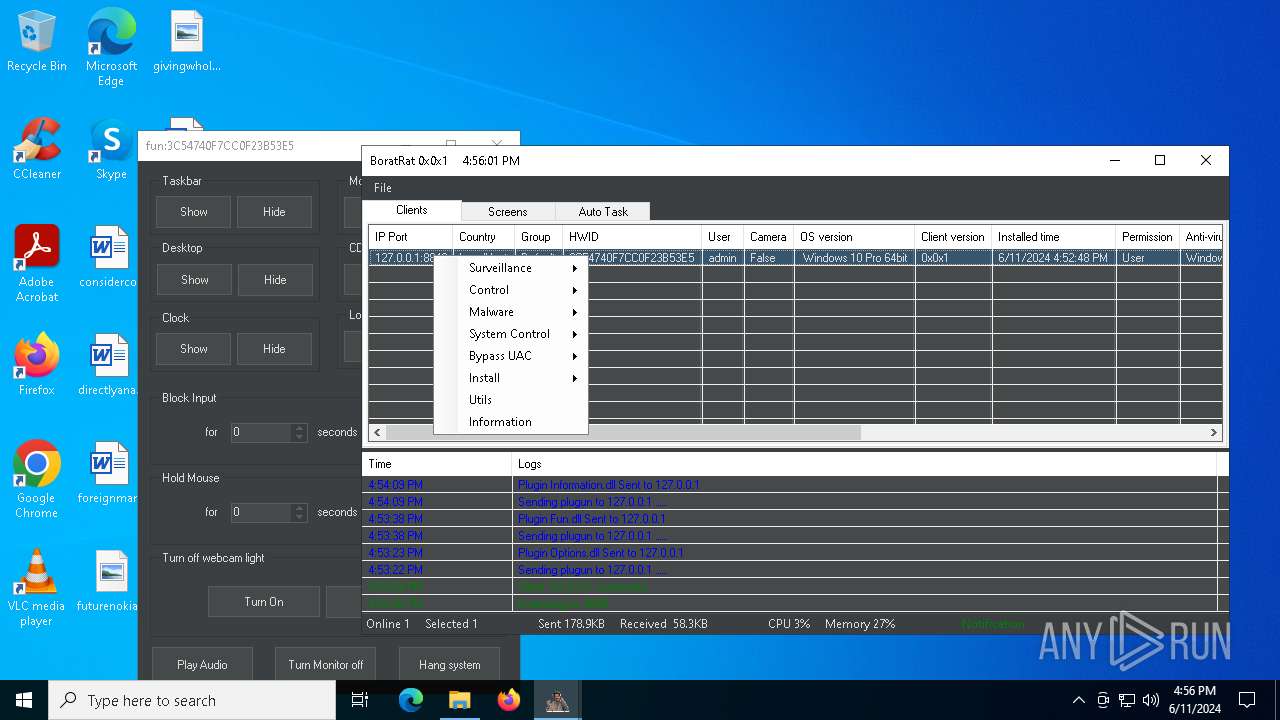
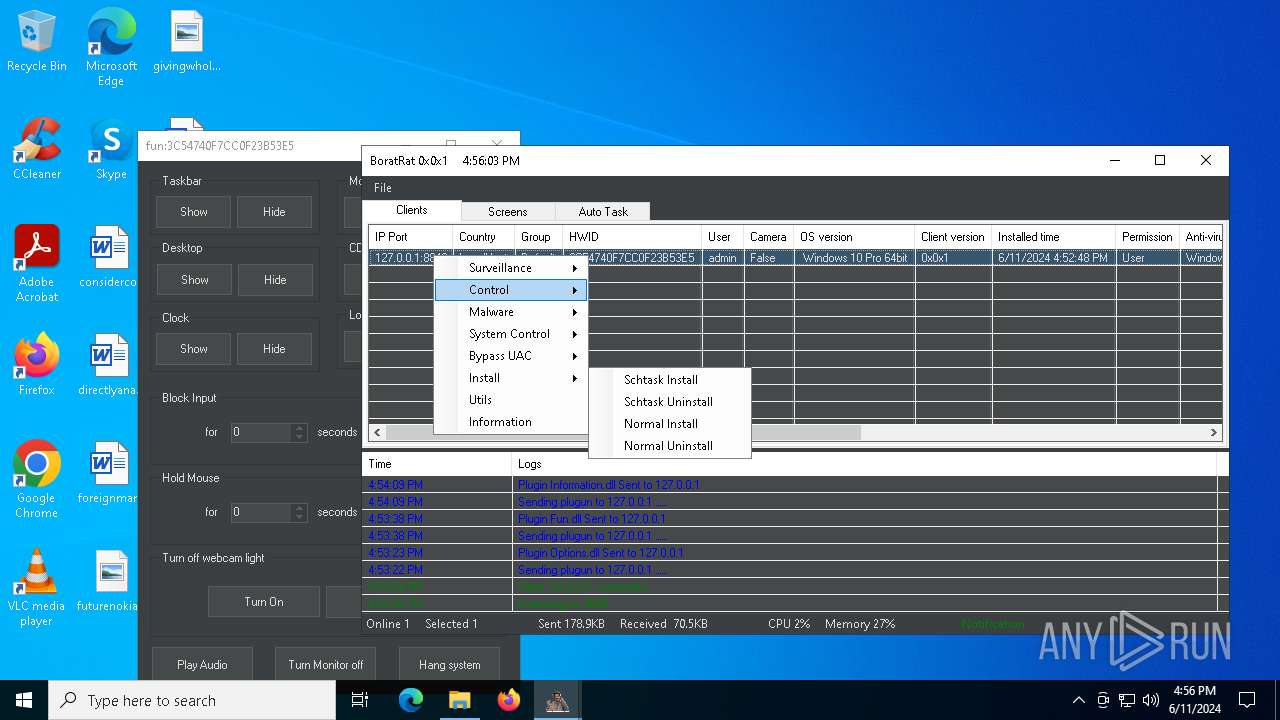
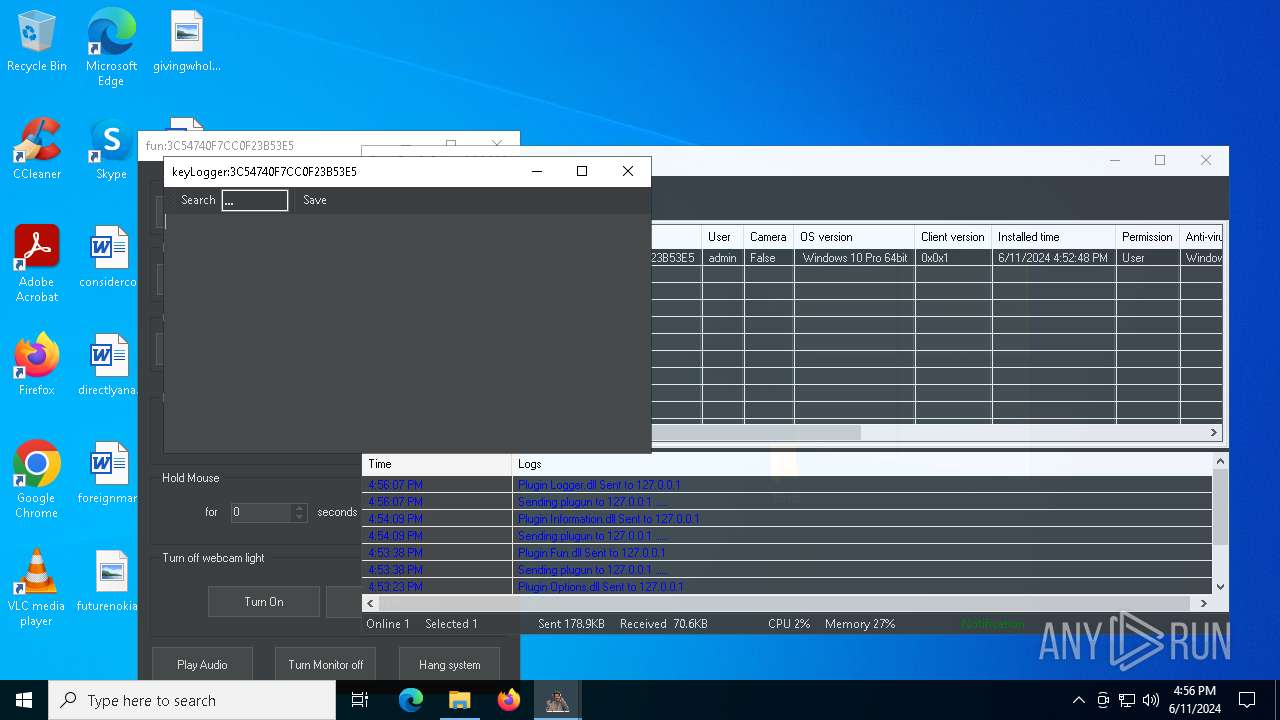
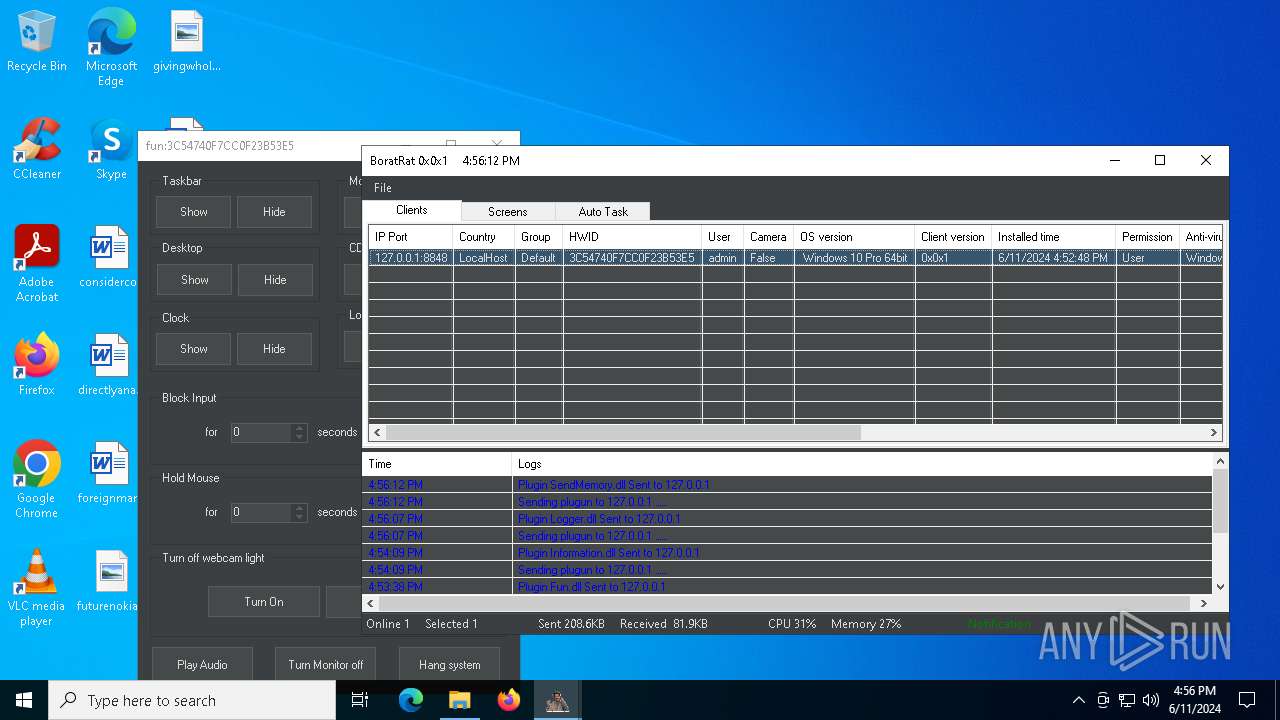
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | June 11, 2024, 16:50:50 |
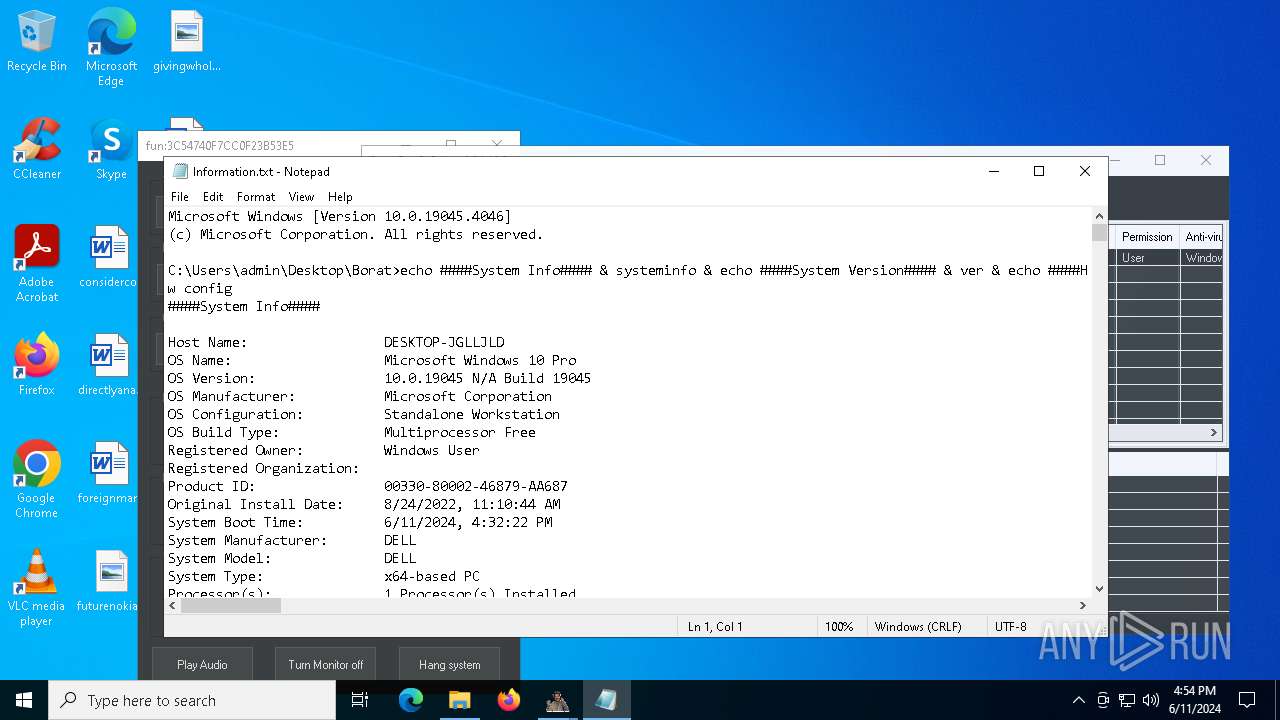
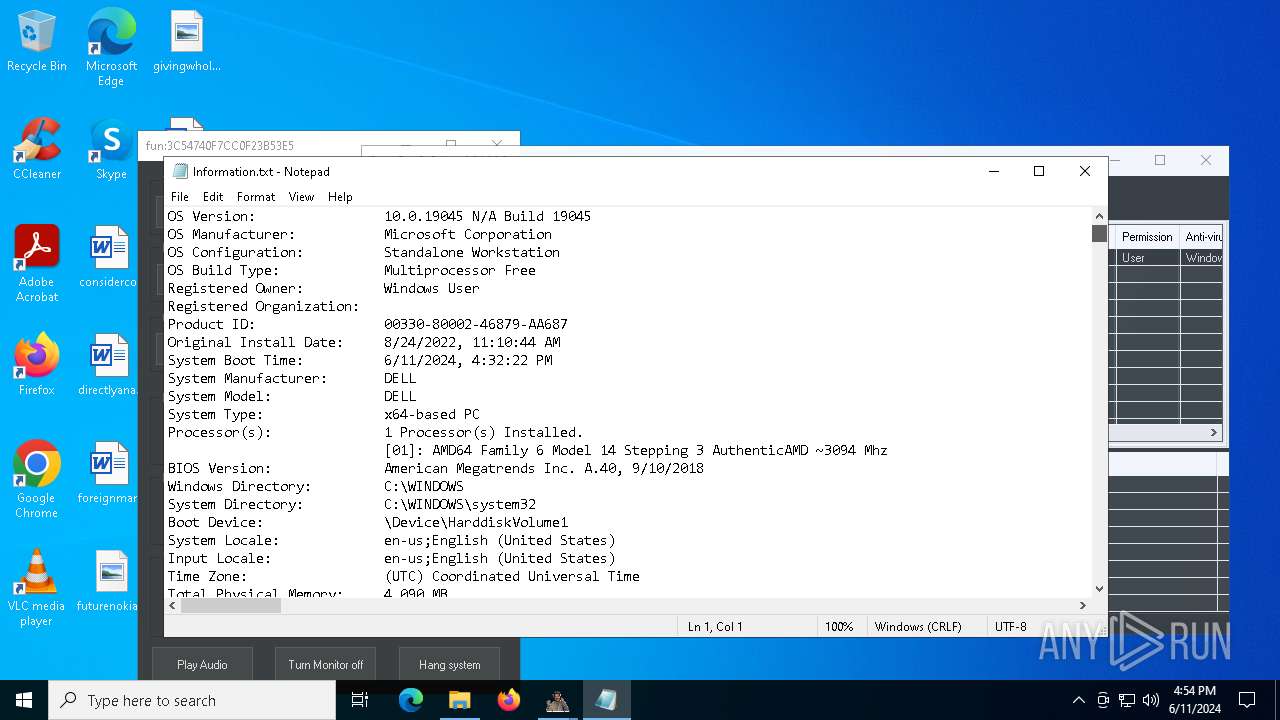
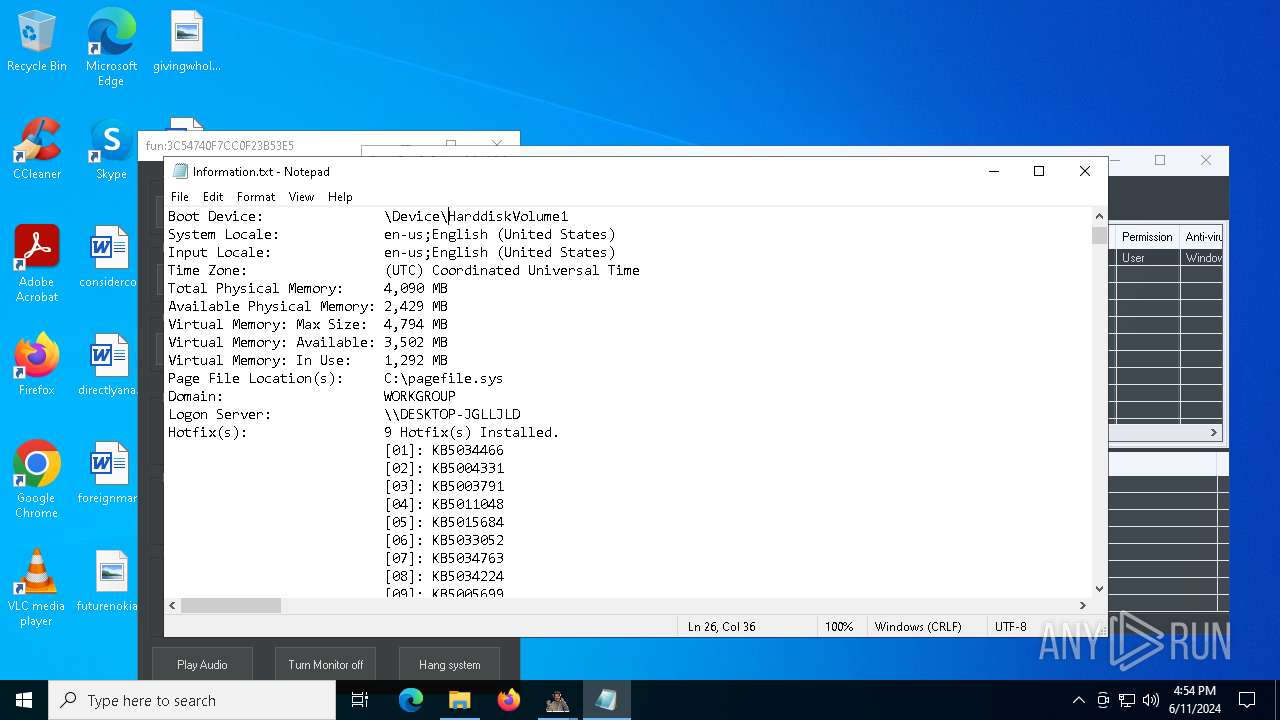
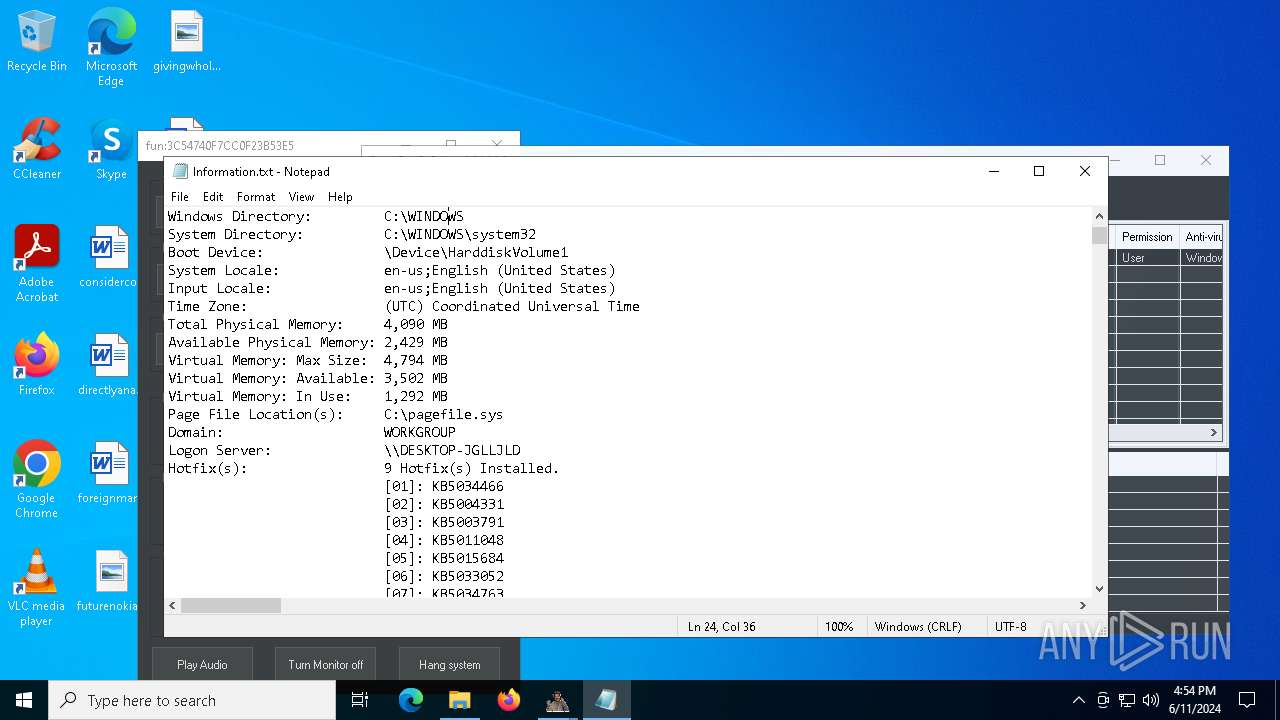
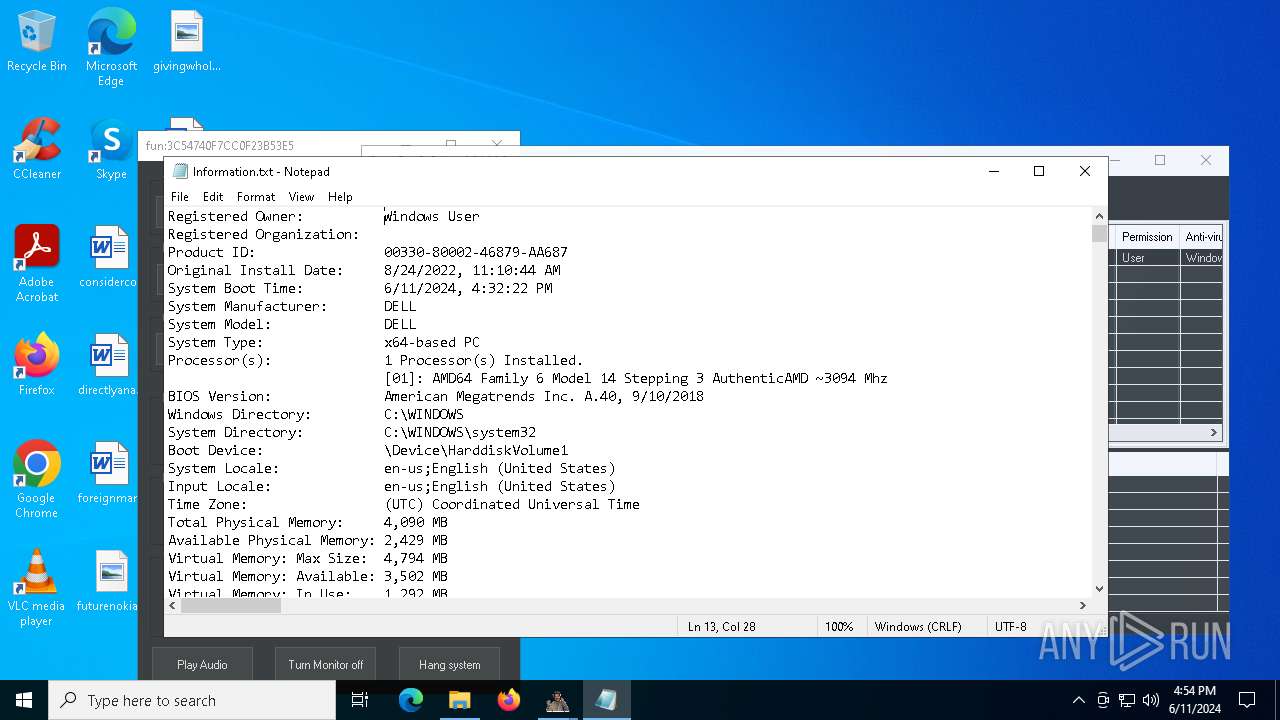
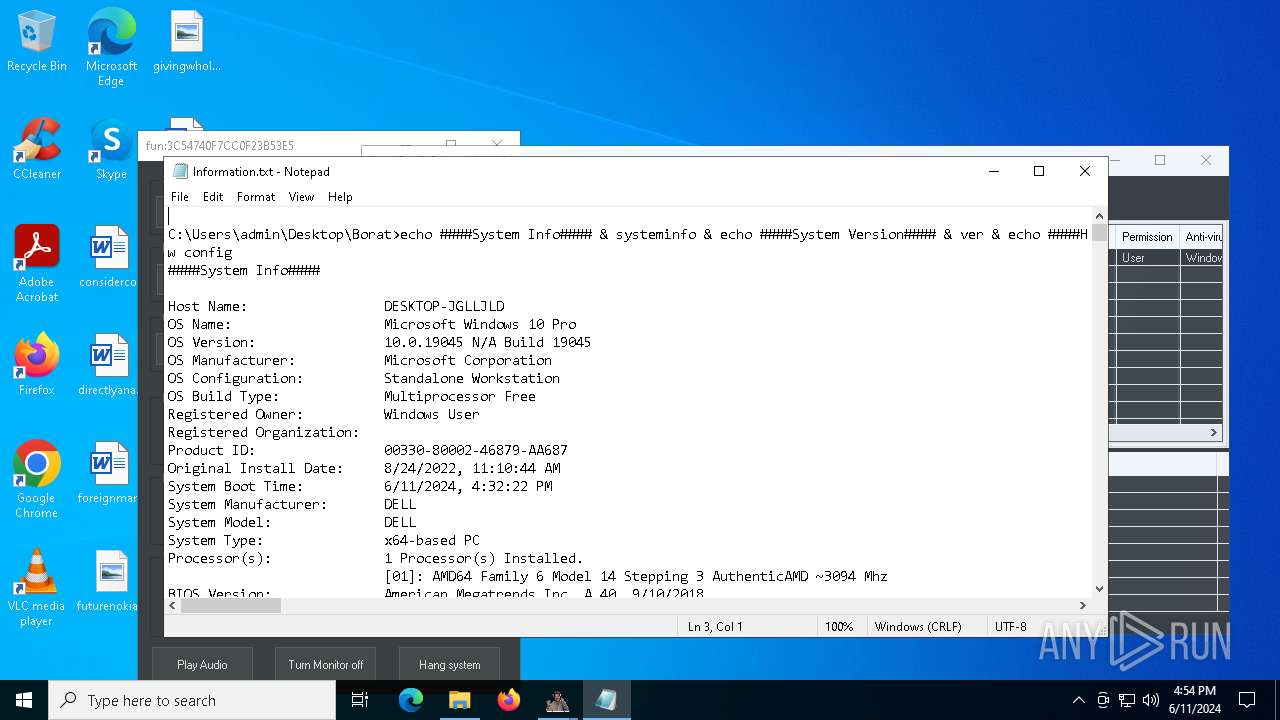
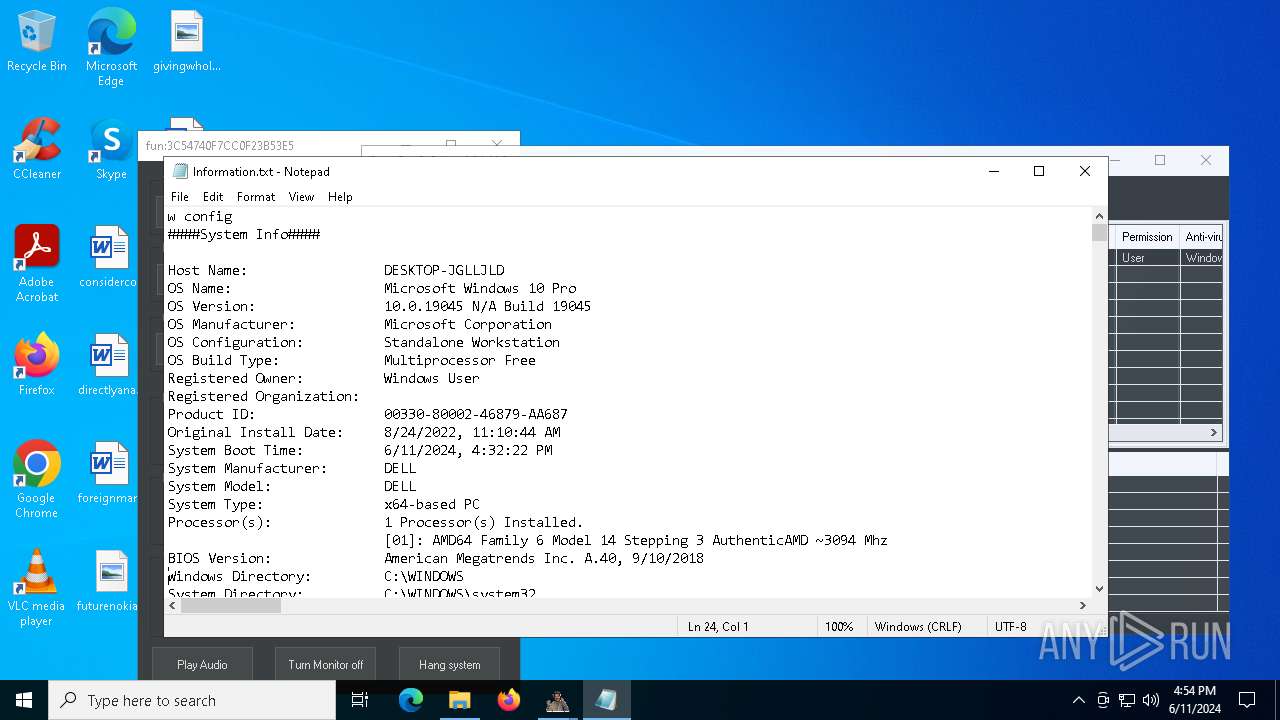
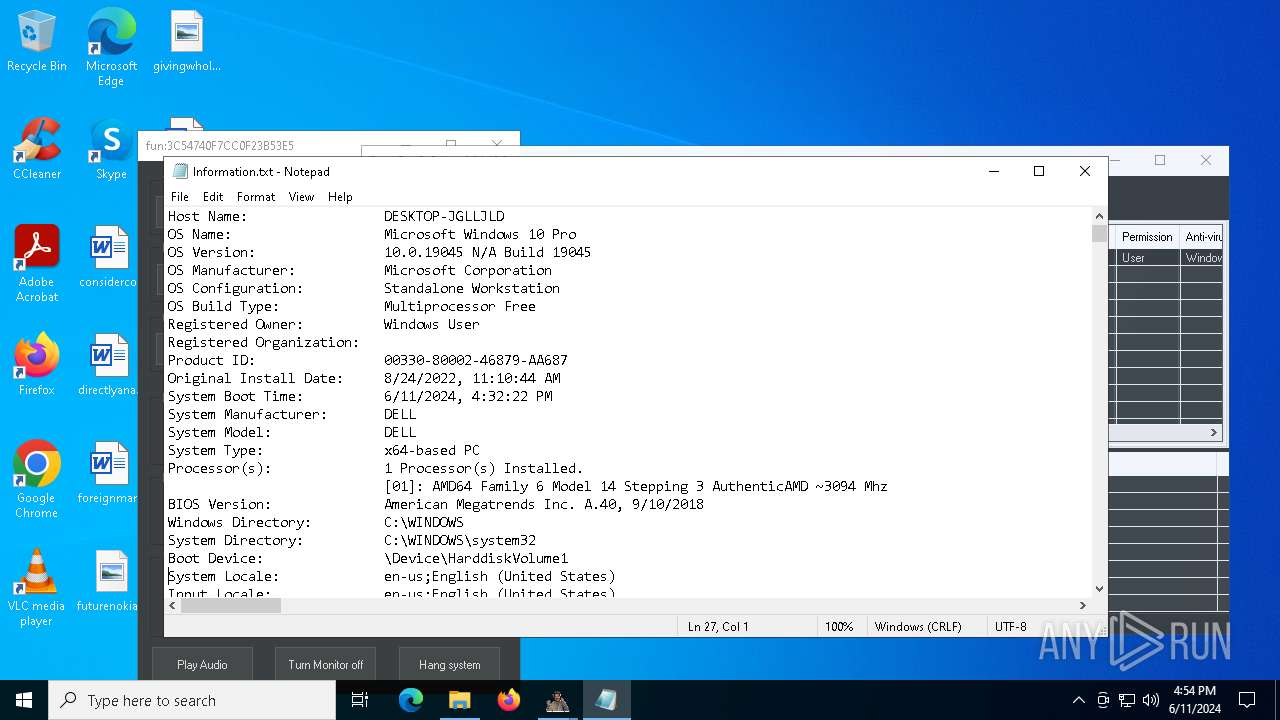
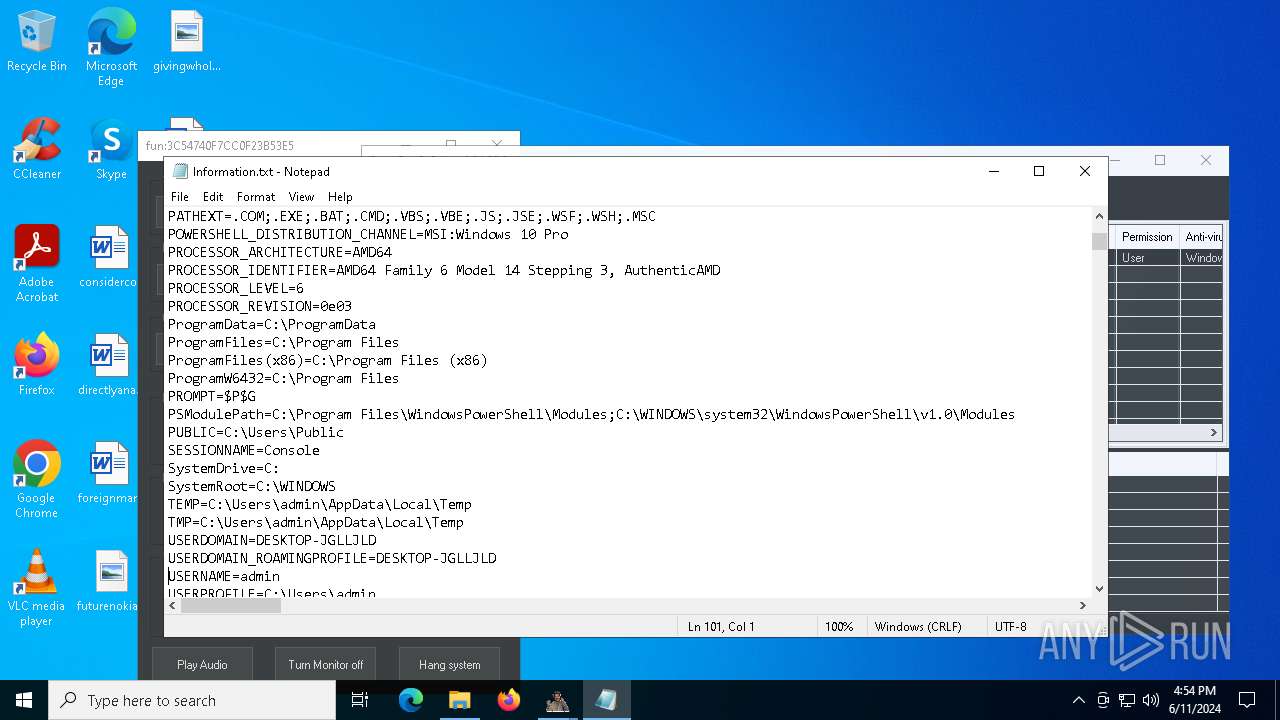
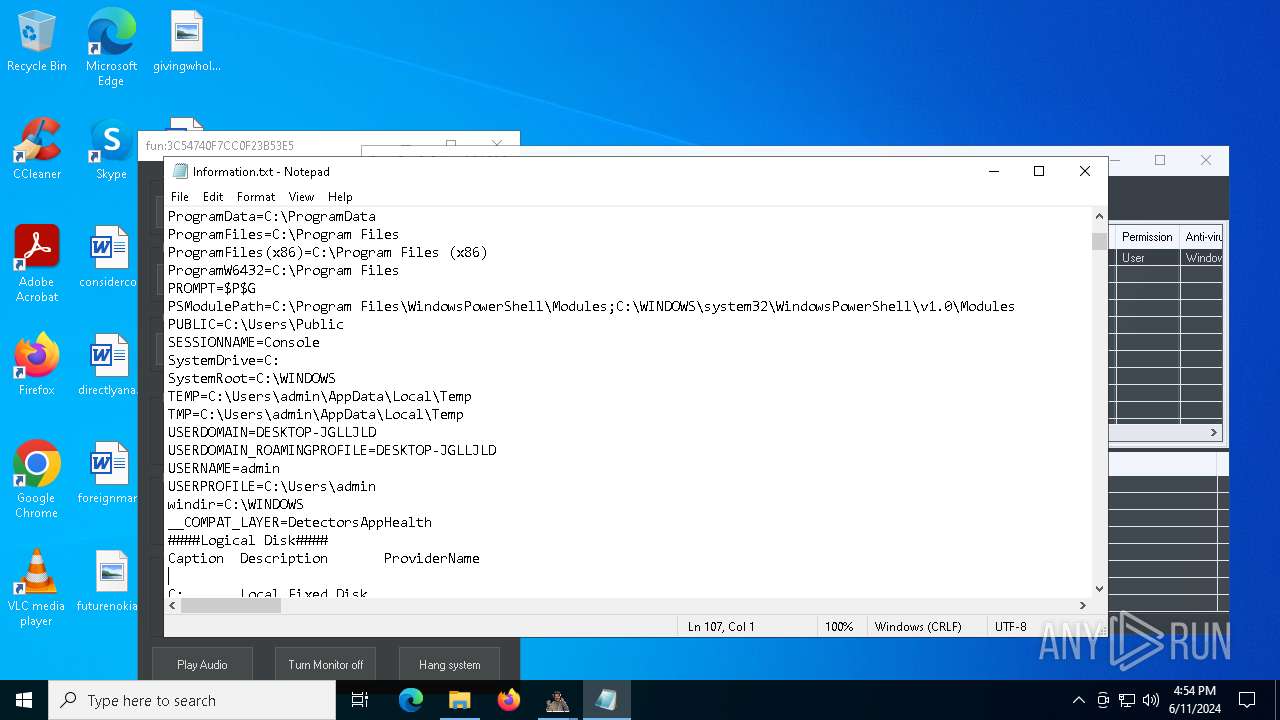
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 43C20E4EE2DD87C70DD0ED082DC74431 |
| SHA1: | 71051DEE5D0480B8AA30A599A95D0AD928F7BB9E |
| SHA256: | B2F4CC95E54ACC818410D79072CCD44A4DBB21AFAD82C2A4608B7B52F1502867 |
| SSDEEP: | 98304:4mnI+WmnzFhcWMOo/5ucNWw7tq3o280CB6oWprH0Vtcpot+FfRT5apCeiFqQgijQ:BtYHMwzJ4hoHQLs |
MALICIOUS
Actions looks like stealing of personal data
- WinRAR.exe (PID: 2620)
- BoratRat.exe (PID: 6376)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2620)
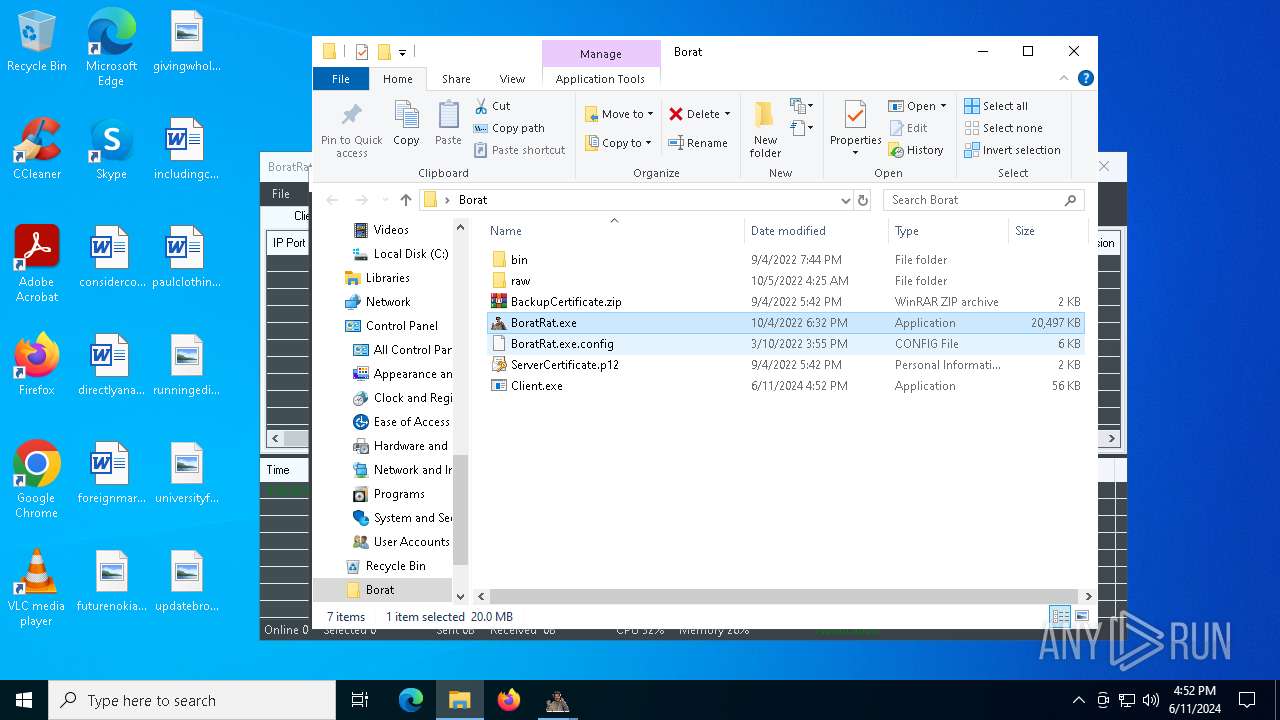
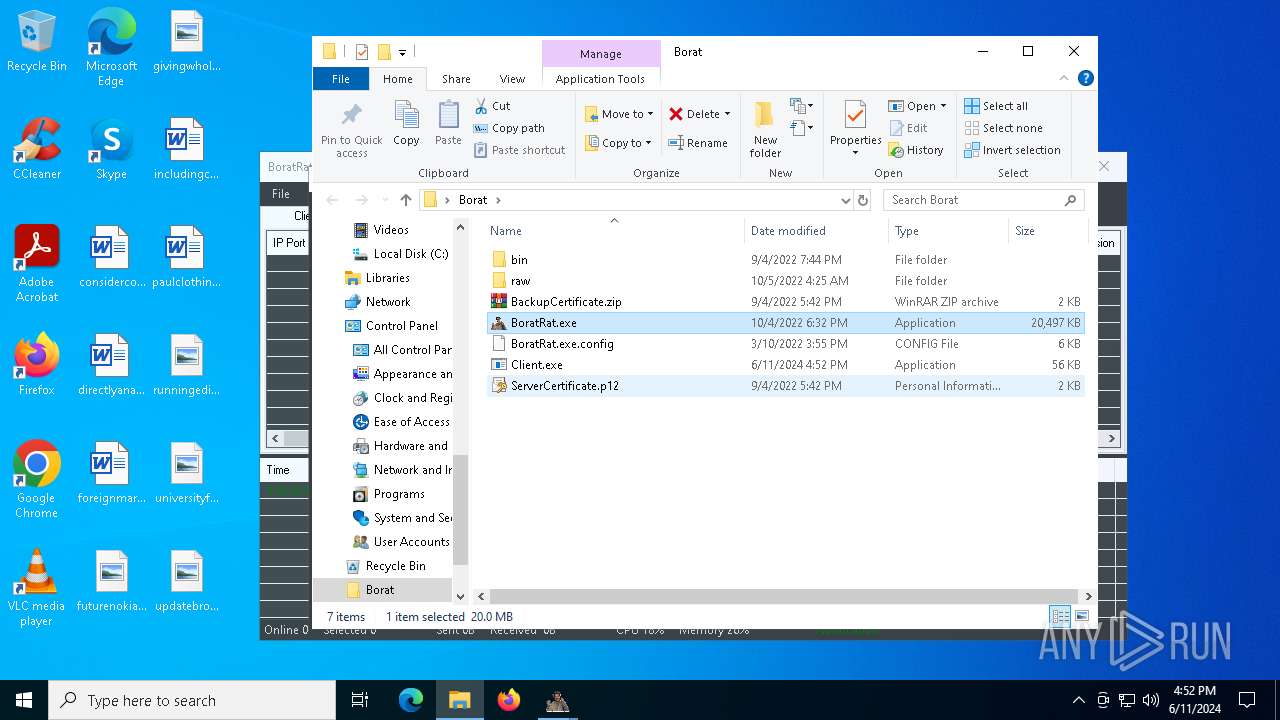
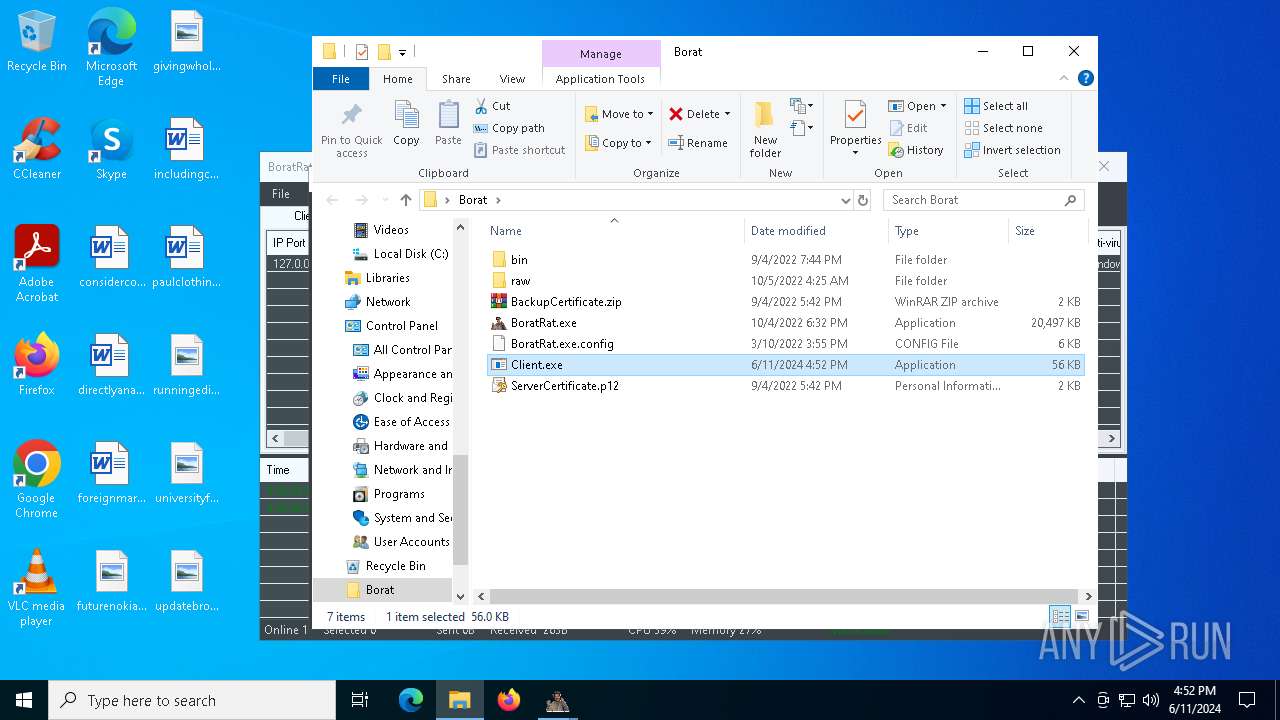
- BoratRat.exe (PID: 6376)
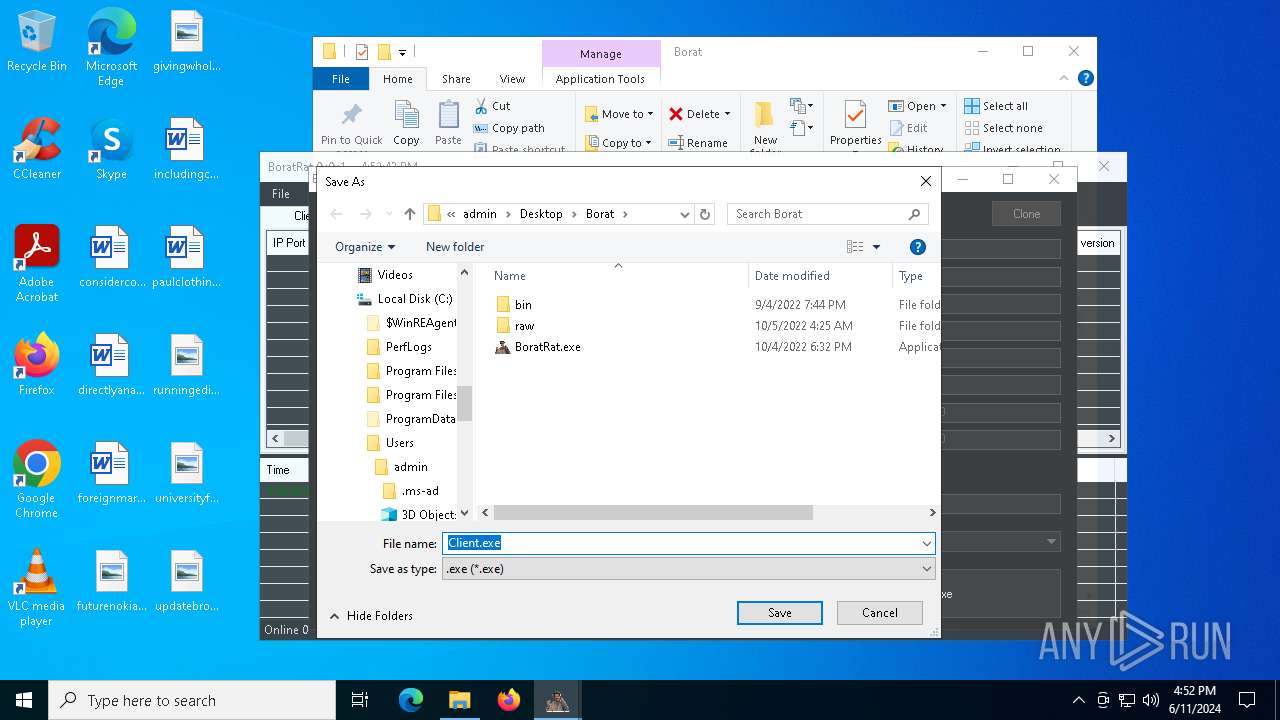
- Client.exe (PID: 6296)
ASYNCRAT has been detected (YARA)
- BoratRat.exe (PID: 6376)
- Client.exe (PID: 6296)
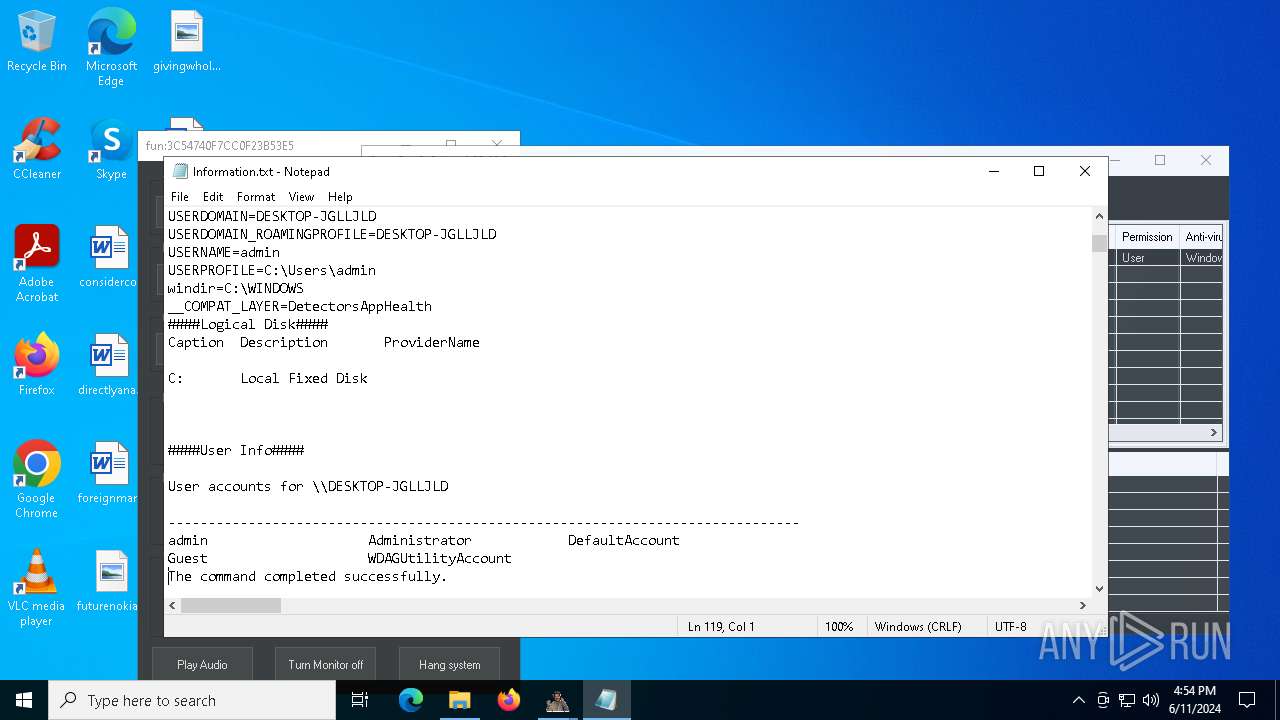
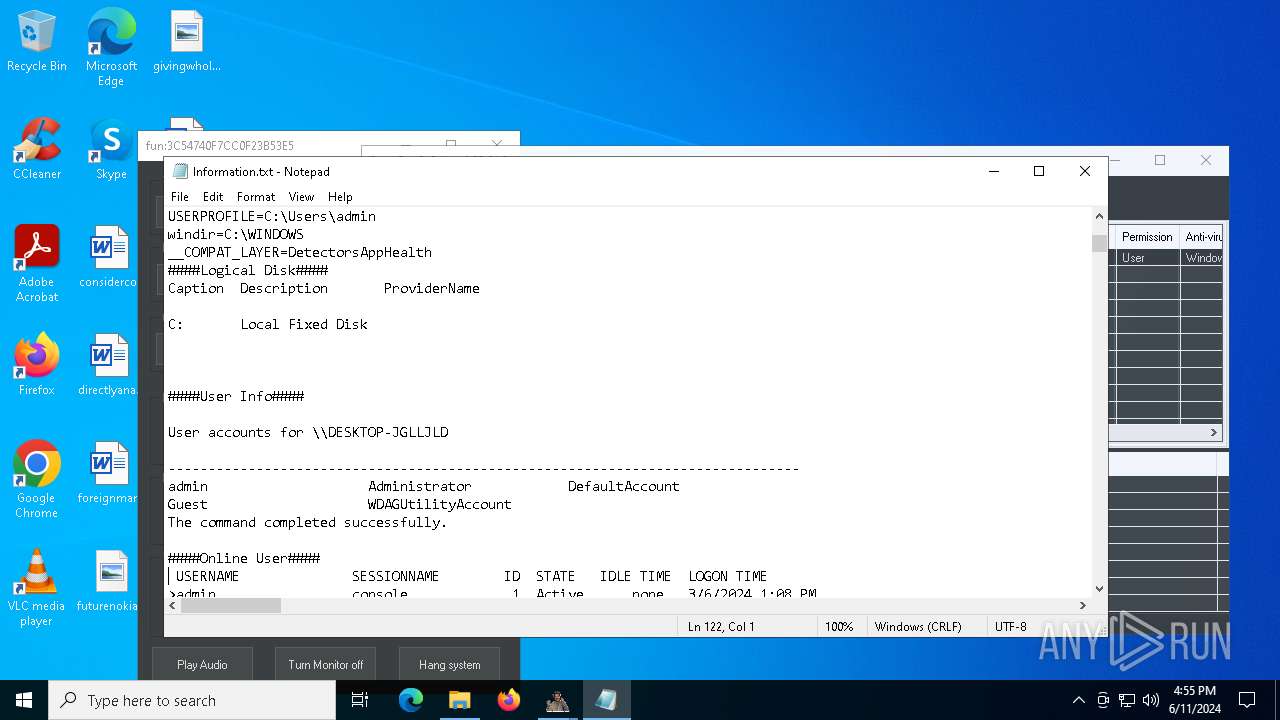
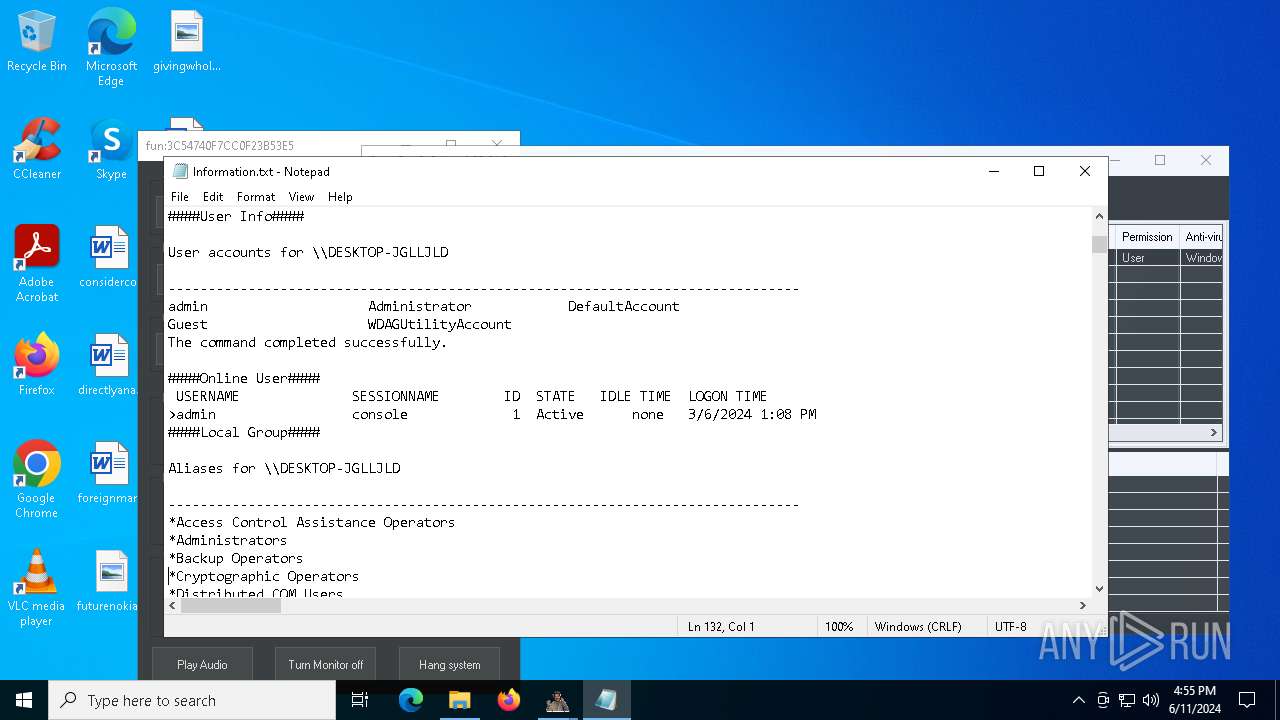
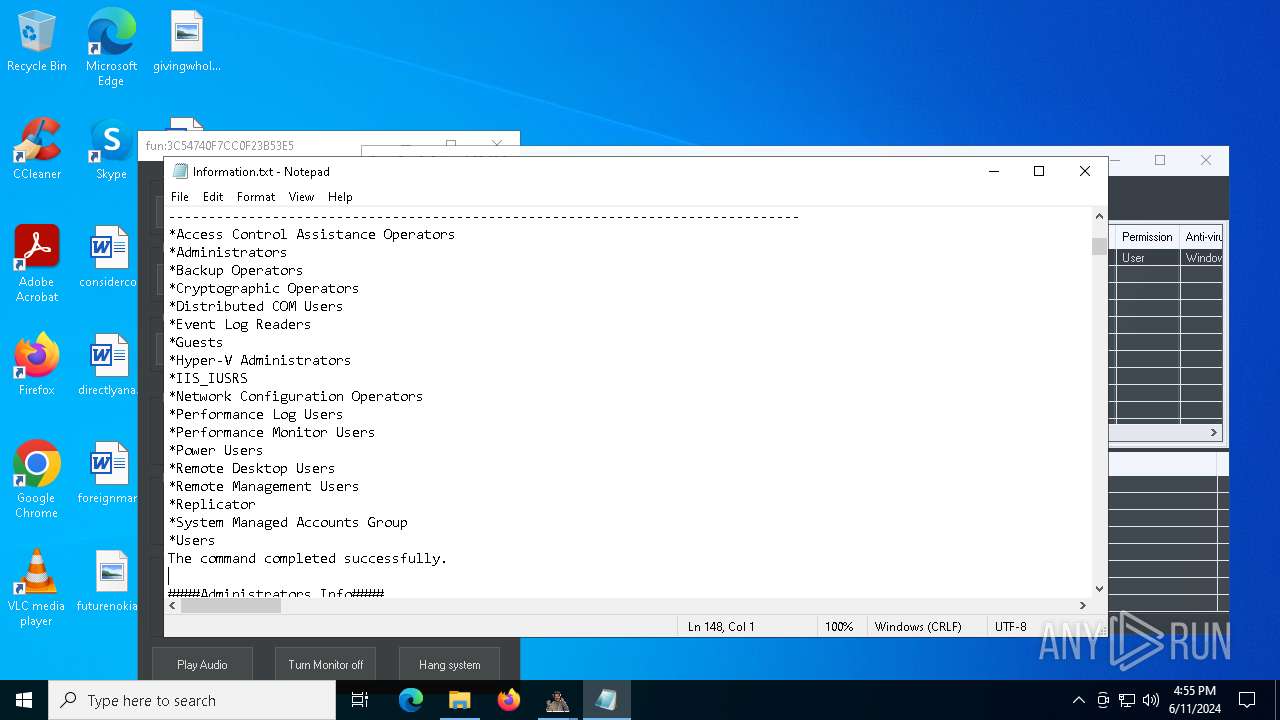
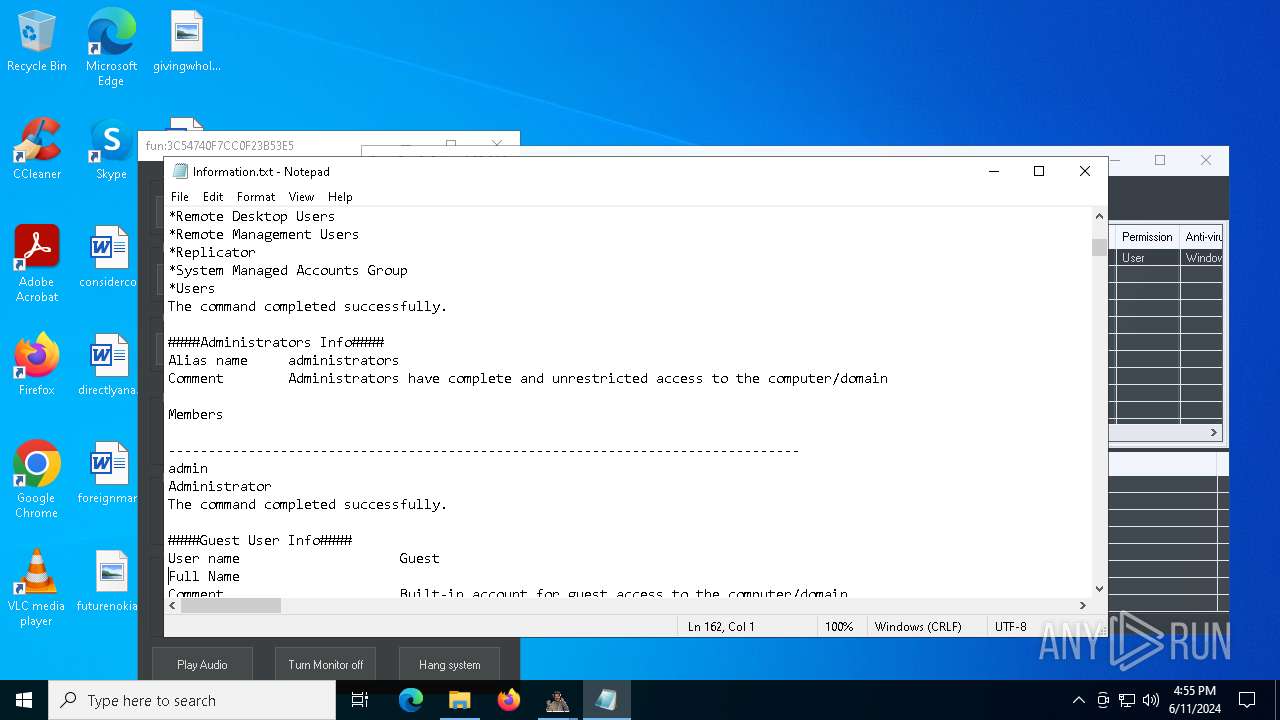
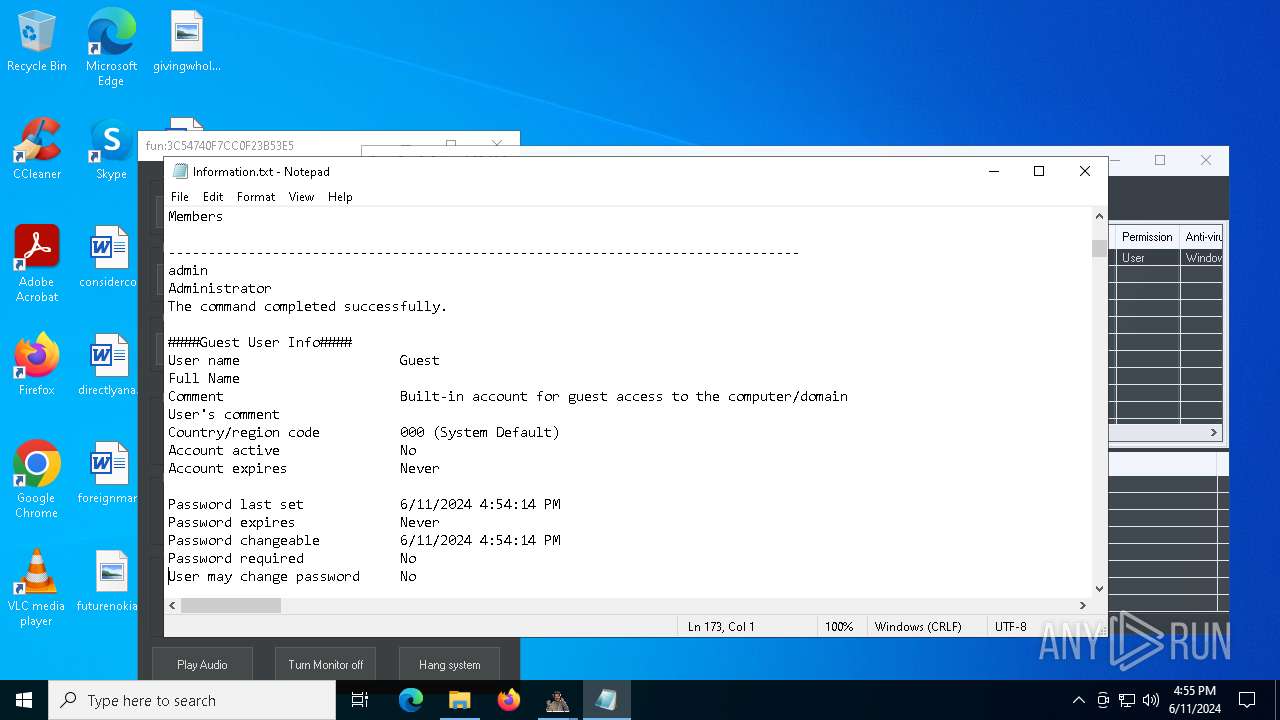
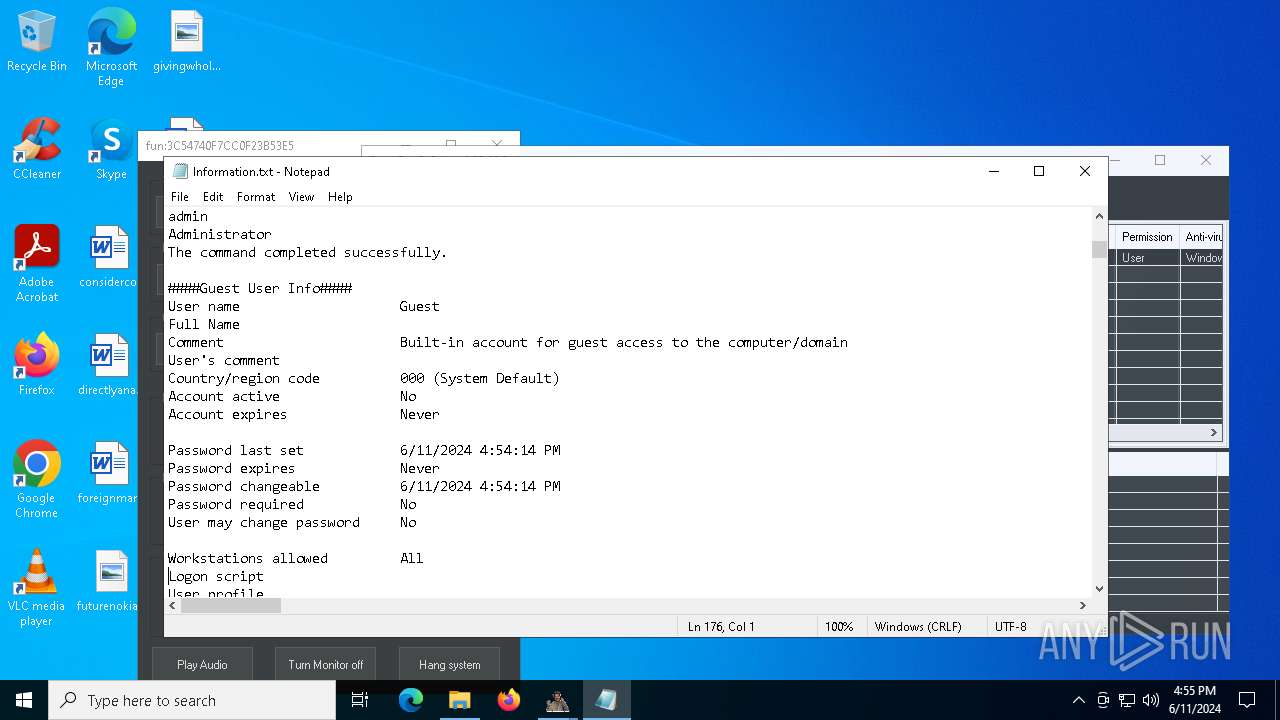
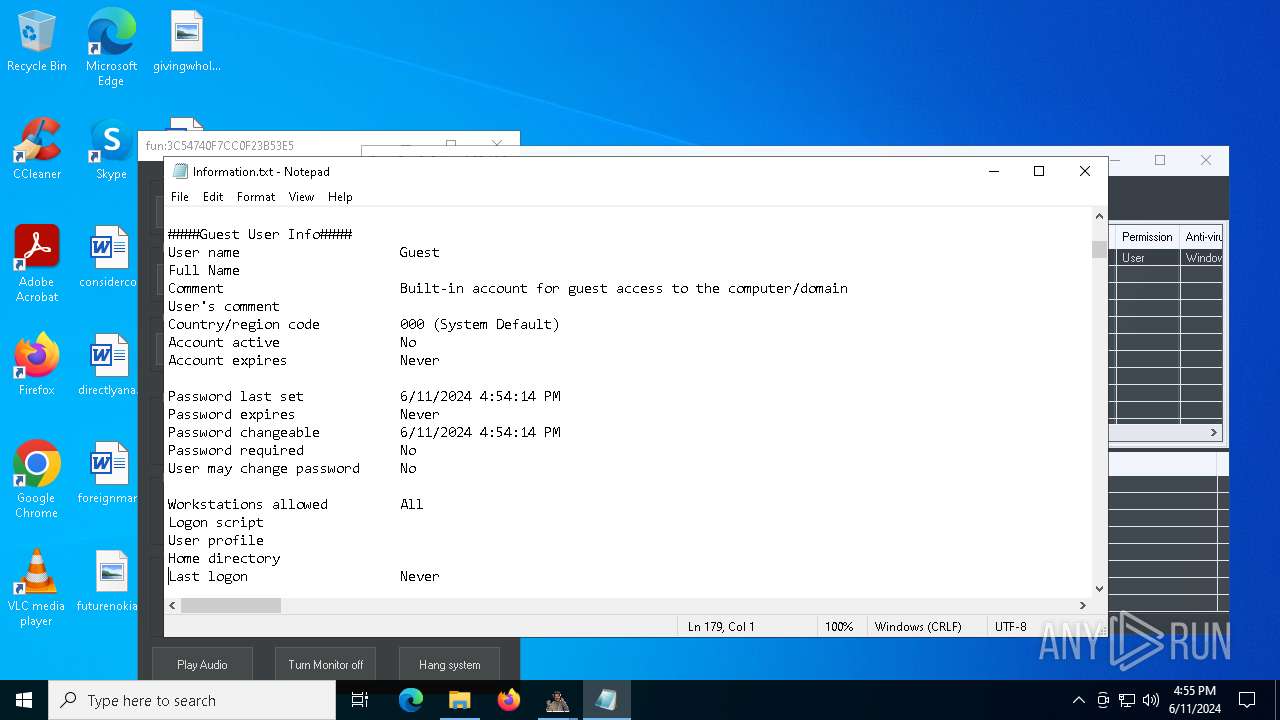
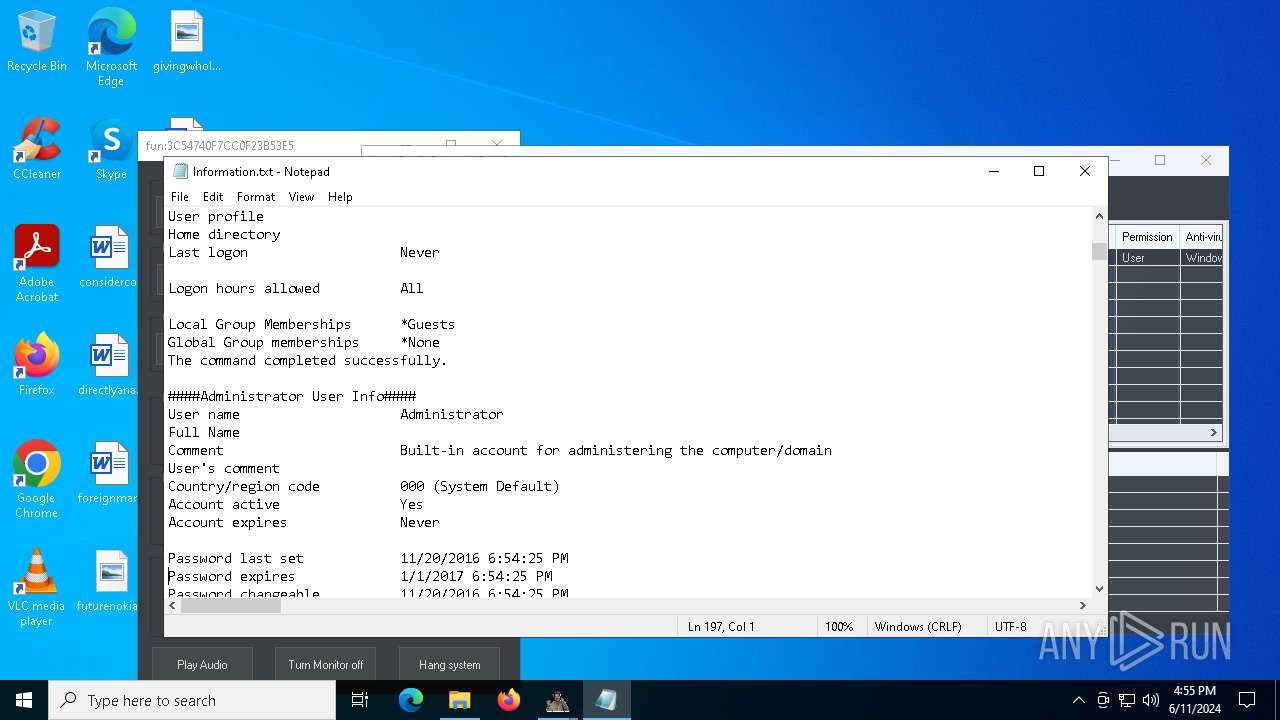
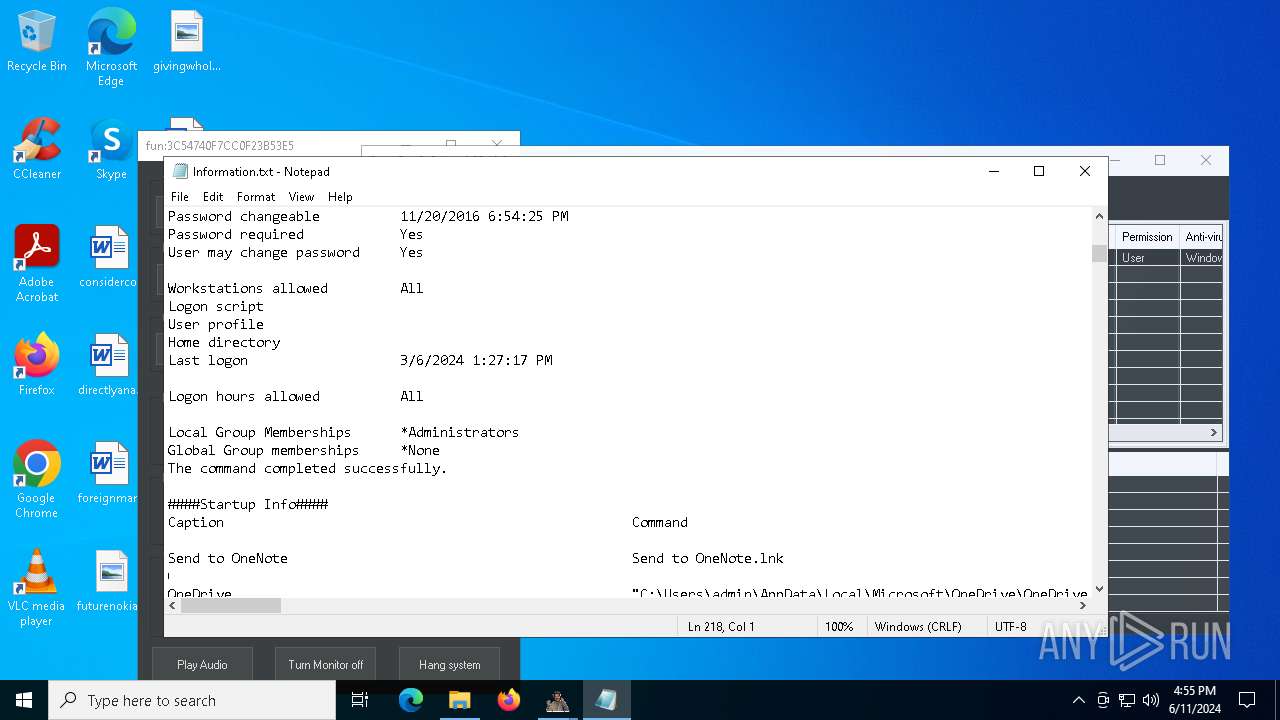
Starts NET.EXE to view/change users localgroup
- cmd.exe (PID: 7036)
- net.exe (PID: 4060)
- net.exe (PID: 864)
Starts NET.EXE to view/add/change user profiles
- cmd.exe (PID: 7036)
- net.exe (PID: 7016)
- net.exe (PID: 1460)
- net.exe (PID: 1924)
SUSPICIOUS
The process creates files with name similar to system file names
- WinRAR.exe (PID: 2620)
Creates file in the systems drive root
- BoratRat.exe (PID: 6376)
The process checks if it is being run in the virtual environment
- BoratRat.exe (PID: 6376)
Reads security settings of Internet Explorer
- BoratRat.exe (PID: 6376)
- TextInputHost.exe (PID: 736)
Executable content was dropped or overwritten
- BoratRat.exe (PID: 6376)
- Client.exe (PID: 6296)
Starts CMD.EXE for commands execution
- Client.exe (PID: 6296)
Uses WMIC.EXE to obtain local storage devices information
- cmd.exe (PID: 7036)
Uses WMIC.EXE to obtain commands that are run when users log in
- cmd.exe (PID: 7036)
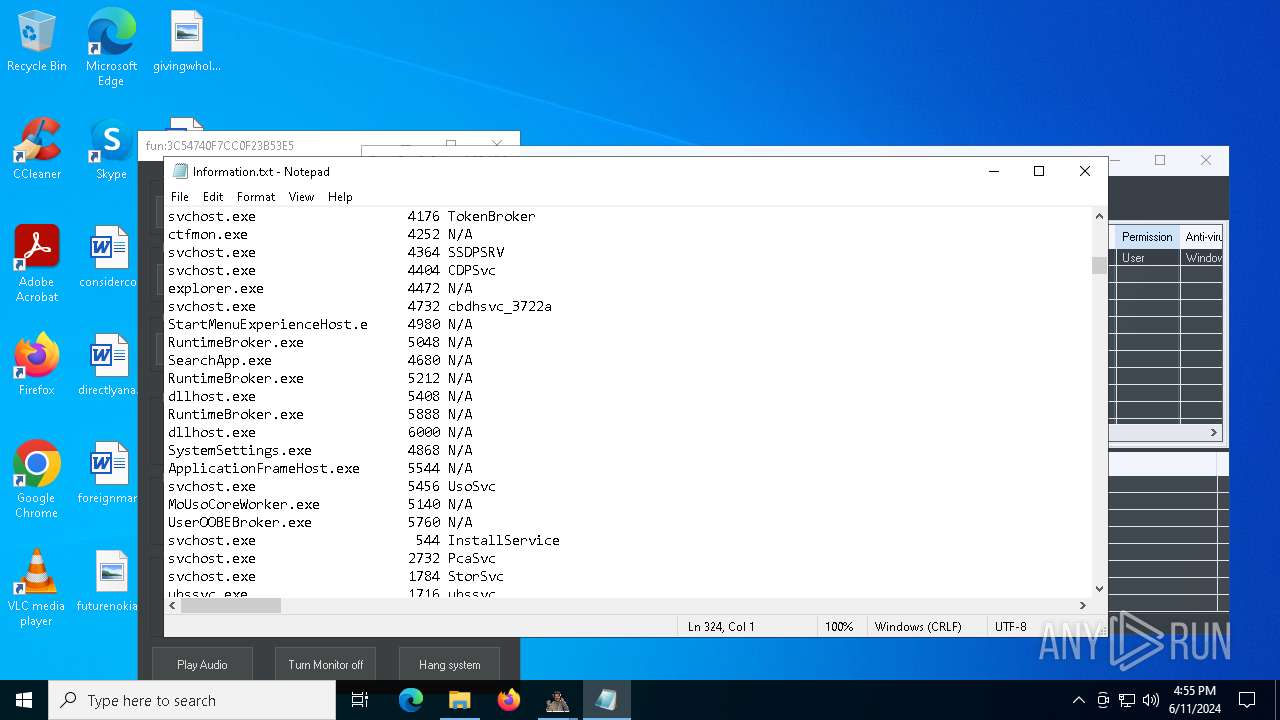
Get information on the list of running processes
- cmd.exe (PID: 7036)
Process uses IPCONFIG to discover network configuration
- cmd.exe (PID: 7036)
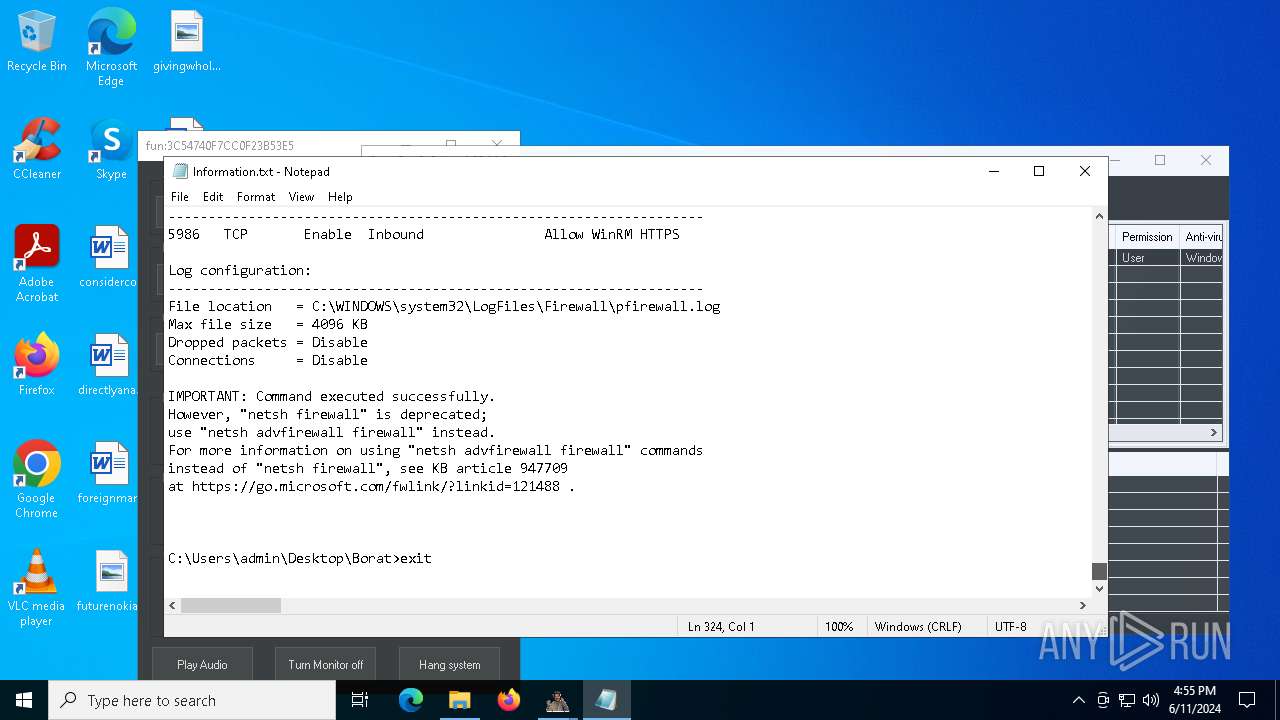
Suspicious use of NETSH.EXE
- cmd.exe (PID: 7036)
Uses ROUTE.EXE to obtain the routing table information
- cmd.exe (PID: 7036)
Starts SC.EXE for service management
- cmd.exe (PID: 7036)
Process uses ARP to discover network configuration
- cmd.exe (PID: 7036)
Reads the date of Windows installation
- BoratRat.exe (PID: 6376)
The process executes via Task Scheduler
- Client.exe (PID: 5912)
INFO
Manual execution by a user
- BoratRat.exe (PID: 6376)
- Client.exe (PID: 6296)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2620)
Reads the computer name
- BoratRat.exe (PID: 6376)
- Client.exe (PID: 6296)
- Client.exe (PID: 5912)
- TextInputHost.exe (PID: 736)
Checks supported languages
- BoratRat.exe (PID: 6376)
- Client.exe (PID: 6296)
- Client.exe (PID: 5912)
- TextInputHost.exe (PID: 736)
Reads the machine GUID from the registry
- BoratRat.exe (PID: 6376)
- Client.exe (PID: 5912)
- Client.exe (PID: 6296)
Creates files or folders in the user directory
- BoratRat.exe (PID: 6376)
- Client.exe (PID: 6296)
Reads Environment values
- Client.exe (PID: 6296)
- BoratRat.exe (PID: 6376)
Reads the software policy settings
- Client.exe (PID: 6296)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 2304)
- WMIC.exe (PID: 2044)
- explorer.exe (PID: 8)
- notepad.exe (PID: 7112)
Reads the time zone
- net1.exe (PID: 1792)
- net1.exe (PID: 1496)
Process checks computer location settings
- BoratRat.exe (PID: 6376)
Reads Microsoft Office registry keys
- explorer.exe (PID: 8)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
162
Monitored processes
36
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 8 | C:\WINDOWS\explorer.exe /factory,{75dff2b7-6936-4c06-a8bb-676a7b00b24b} -Embedding | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | "C:\WINDOWS\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe" -ServerName:InputApp.AppXjd5de1g66v206tj52m9d0dtpppx4cgpn.mca | C:\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Version: 123.26505.0.0 Modules
| |||||||||||||||
| 864 | net localgroup administrators | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1092 | query user | C:\Windows\System32\query.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MultiUser Query Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1460 | net user guest | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1492 | hostname | C:\Windows\System32\HOSTNAME.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Hostname APP Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1496 | C:\WINDOWS\system32\net1 user guest | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1744 | "C:\WINDOWS\system32\quser.exe" | C:\Windows\System32\quser.exe | — | query.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Query User Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1792 | C:\WINDOWS\system32\net1 user administrator | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1924 | net user administrator | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
32 168
Read events
32 062
Write events
100
Delete events
6
Modification events
| (PID) Process: | (2620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (2620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Borat.7z | |||
| (PID) Process: | (2620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (2620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\AppData\Local\Temp | |||
Executable files
26
Suspicious files
3
Text files
7
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2620 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2620.48931\Borat\bin\ip2region.db | — | |
MD5:— | SHA256:— | |||
| 2620 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2620.48931\Borat\BackupCertificate.zip | compressed | |
MD5:9322F71EDD95192E1F4D275BFD6D87F3 | SHA256:F13033134C386E85A1E9009E863A3E6380438F83E3336B76A33E701A88F64946 | |||
| 2620 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2620.48931\Borat\BoratRat.exe.config | xml | |
MD5:3E645CCCA1C44A00210924A3B0780955 | SHA256:F29E697EFD7C5ECB928C0310EA832325BF6518786C8E1585E1B85CDC8701602F | |||
| 2620 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2620.48931\Borat\bin\FileSearcher.dll | executable | |
MD5:0B7C33C5739903BA4F4B78C446773528 | SHA256:2D9625F41793F62BFE32C10B2D5E05668E321BCAF8B73414B3C31EF677B9BFF4 | |||
| 2620 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2620.48931\Borat\bin\Extra.dll | executable | |
MD5:62C231BAFA469AB04F090FCB4475D360 | SHA256:6A4F32B0228092CE68E8448C6F4B74B4C654F40FB2D462C1D6BBD4B4EF09053D | |||
| 2620 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2620.48931\Borat\BoratRat.exe | executable | |
MD5:65B694D69D327EFE28FCBCE125401E96 | SHA256:DE60ECBBFEF30C93FE8875EF69B358B20076D1F969FC3D21AB44D59DC9EF7CAB | |||
| 2620 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2620.48931\Borat\bin\Audio.dll | executable | |
MD5:9726D7FE49C8BA43845AD8E5E2802BB8 | SHA256:DF31A70CEB0C481646EEAF94189242200FAFD3DF92F8B3EC97C0D0670F0E2259 | |||
| 2620 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2620.48931\Borat\bin\Discord.dll | executable | |
MD5:7EE673594BBB20F65448AAB05F1361D0 | SHA256:8FA7634B7DCA1A451CF8940429BE6AD2440821ED04D5D70B6E727E5968E0B5F6 | |||
| 2620 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2620.48931\Borat\ServerCertificate.p12 | der | |
MD5:478EE44A47895E687296B9AB34DF04C4 | SHA256:4B0612B2CD5E7ECC456D5C29C89917B8EC881C5F4FD94AFE157098CA96308781 | |||
| 2620 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2620.48931\Borat\bin\Miscellaneous.dll | executable | |
MD5:509D41DA4A688A2E50FC8E3AFCA074C7 | SHA256:F91973113FD01465999CE317F3E7A89DF8C91A5EFADCFA61E5CCCE687BF3580A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
65
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4384 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
4680 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | — | — | unknown |
3976 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | unknown |
5140 | MoUsoCoreWorker.exe | GET | 200 | 23.200.189.225:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
6408 | SIHClient.exe | GET | 200 | 23.200.189.225:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
6408 | SIHClient.exe | GET | 200 | 23.200.189.225:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
5140 | MoUsoCoreWorker.exe | GET | 200 | 92.123.180.147:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
2908 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4364 | svchost.exe | 239.255.255.250:1900 | — | — | — | unknown |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3708 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5140 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4680 | SearchApp.exe | 2.18.29.224:443 | — | Akamai International B.V. | PL | unknown |
4680 | SearchApp.exe | 2.18.29.218:443 | — | Akamai International B.V. | PL | unknown |
4680 | SearchApp.exe | 2.18.29.209:443 | — | Akamai International B.V. | PL | unknown |
4384 | svchost.exe | 20.190.159.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4384 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |