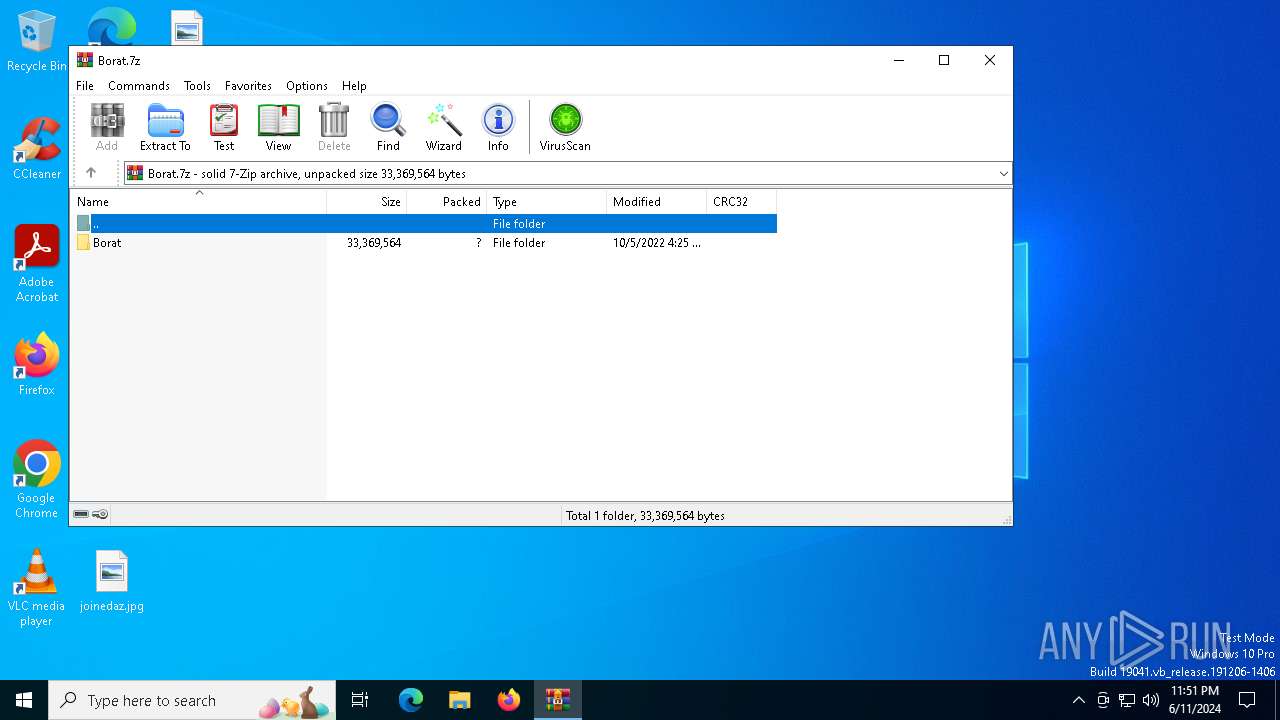
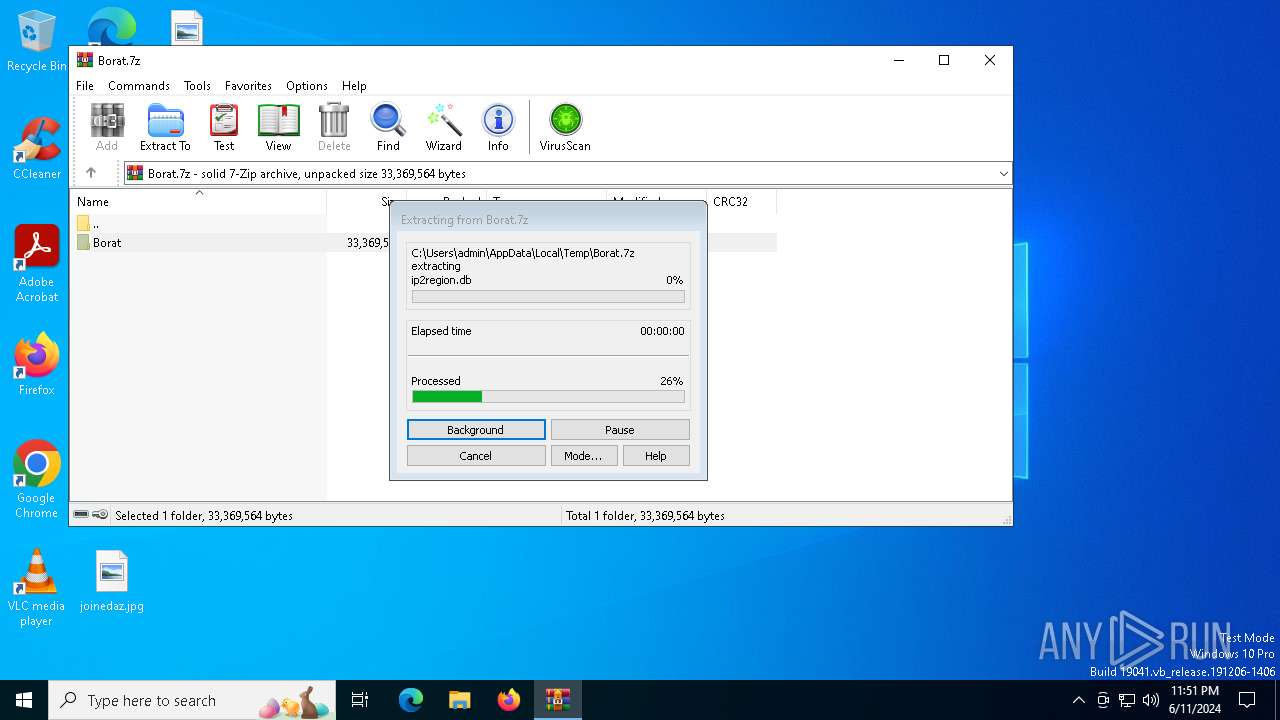
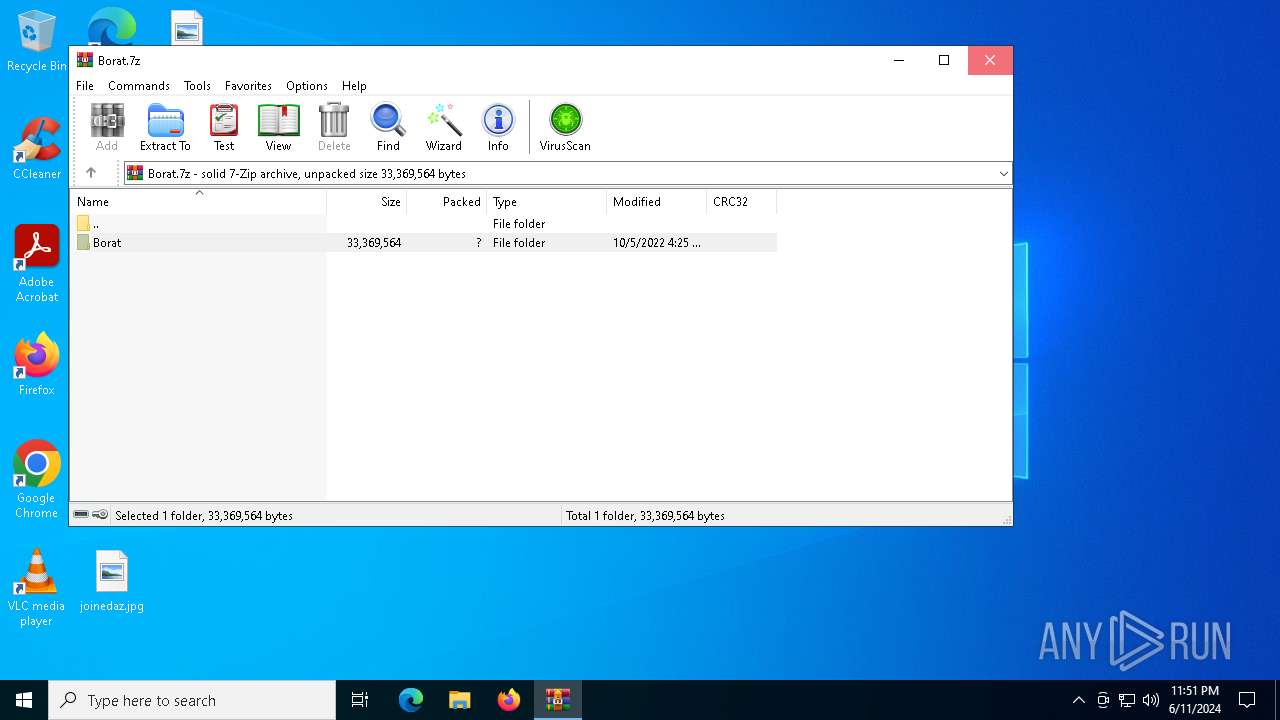
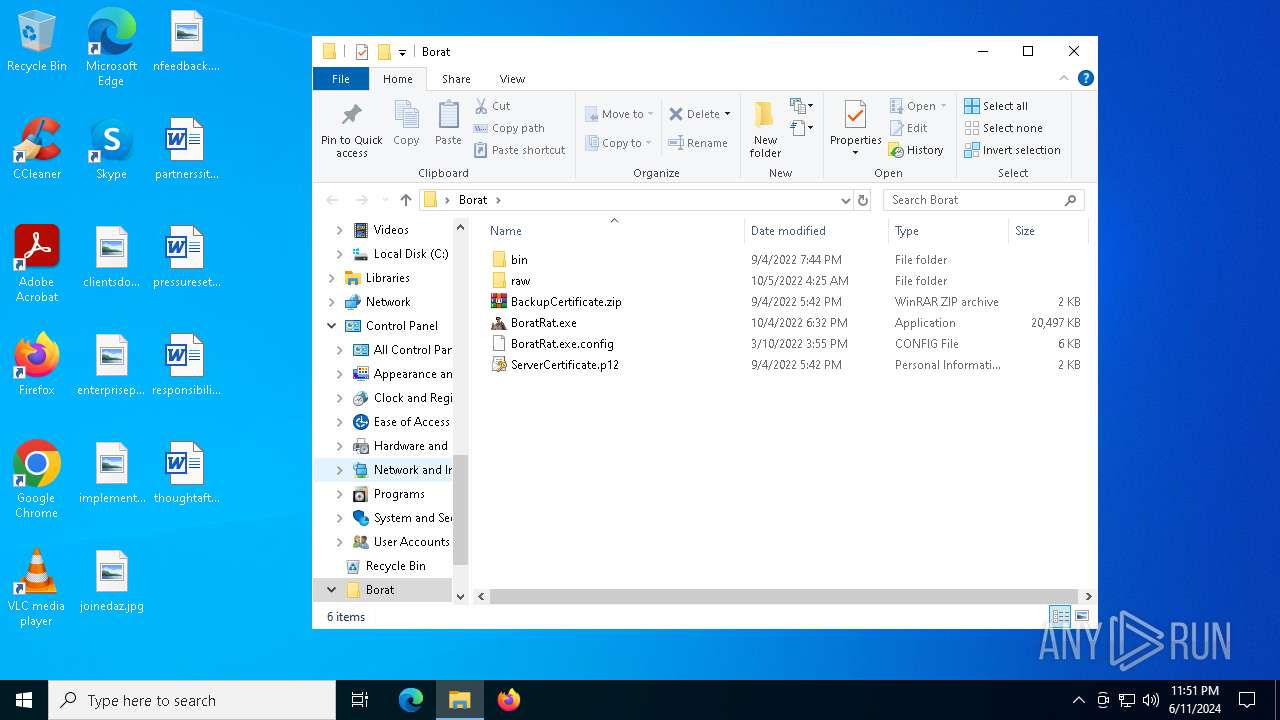
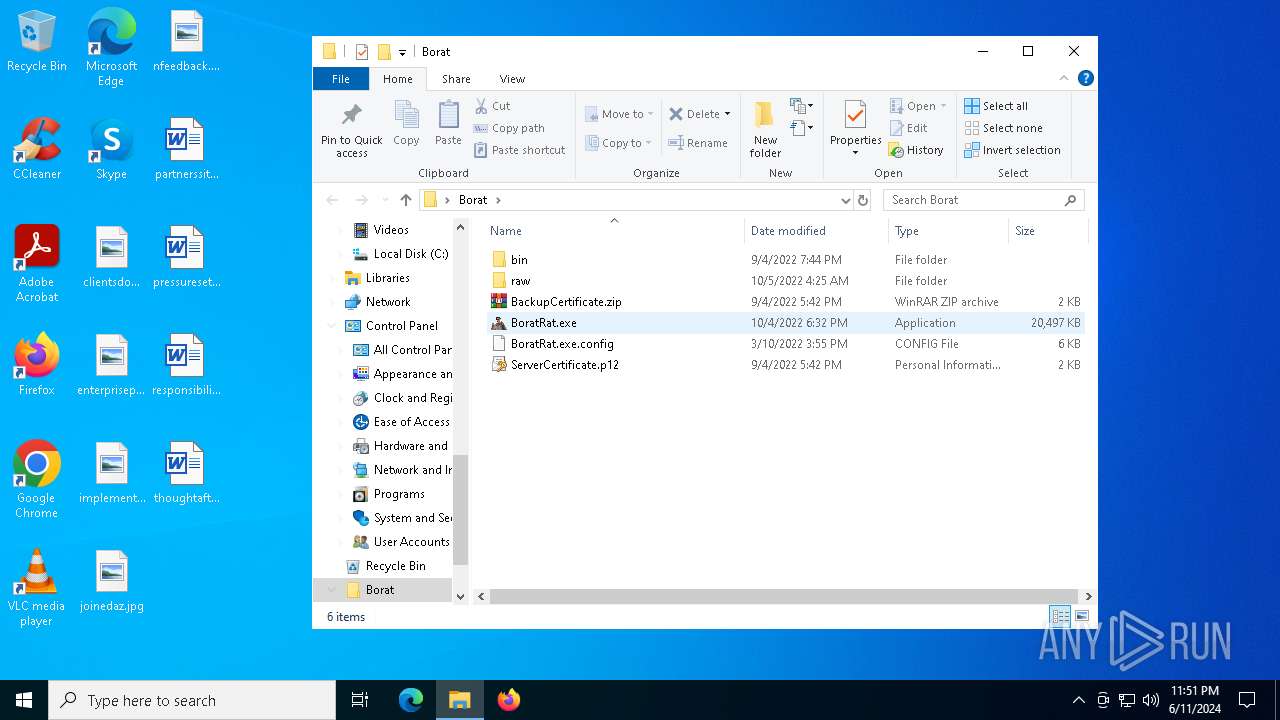
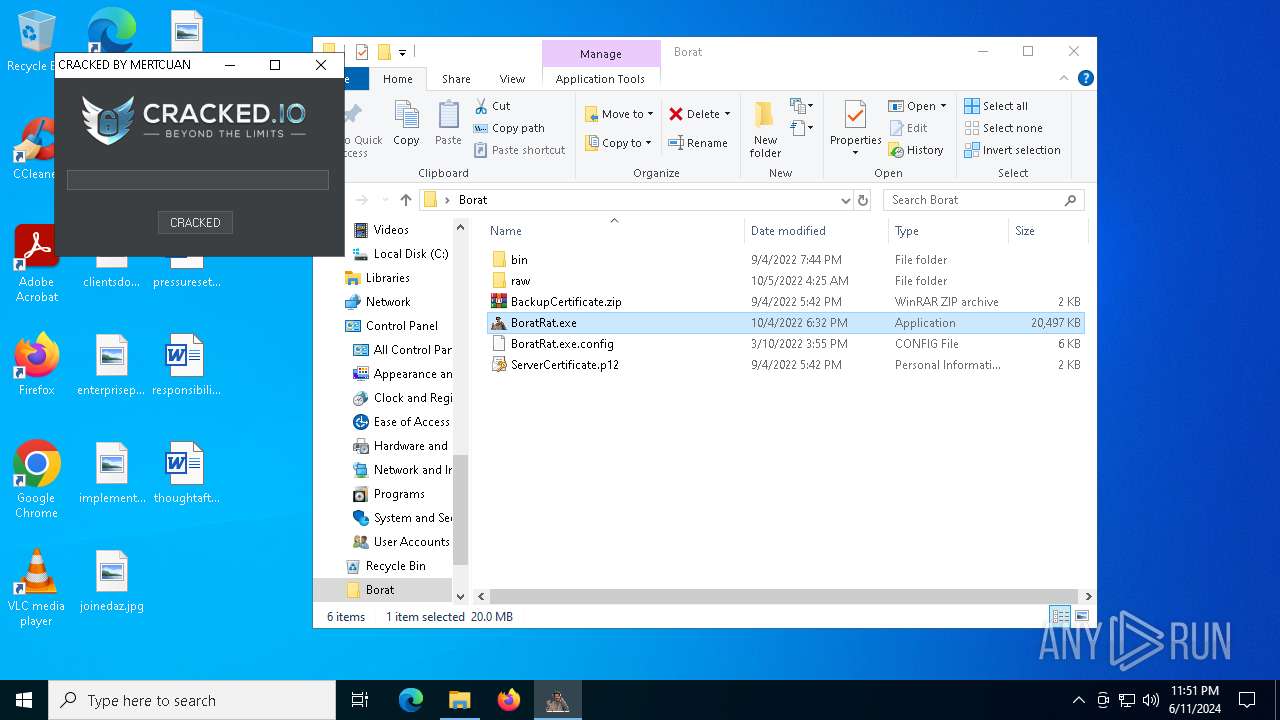
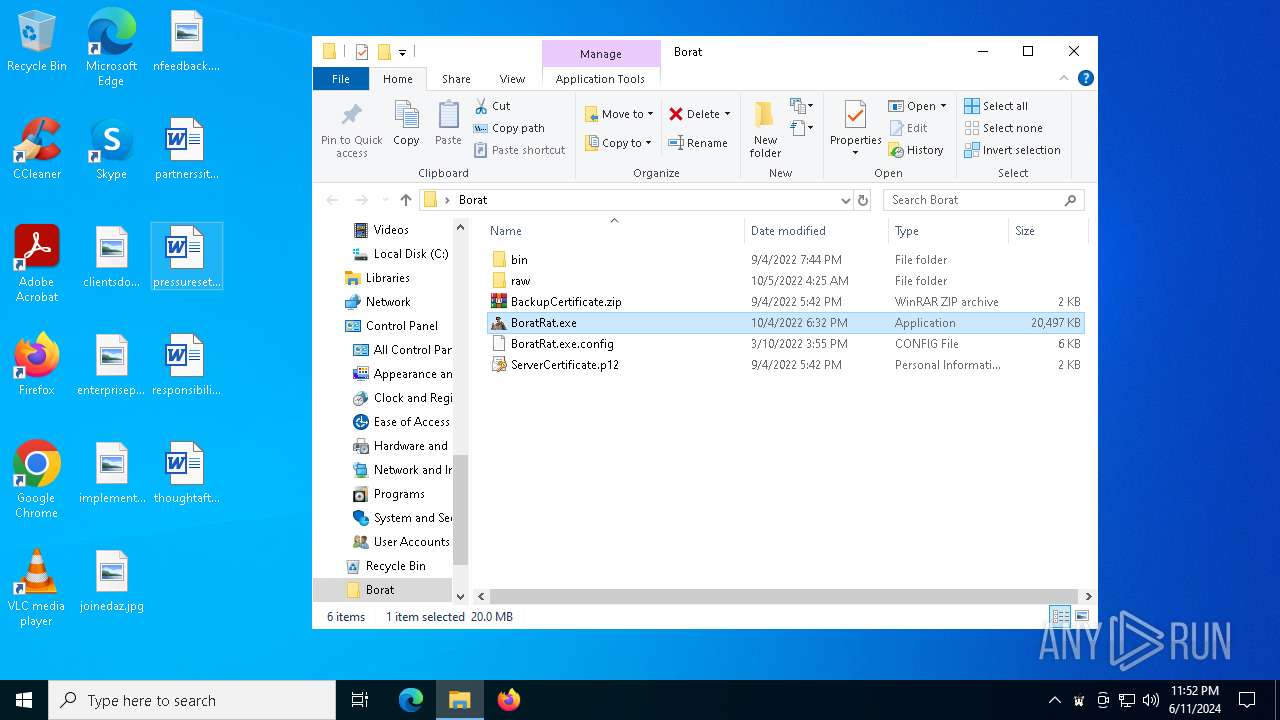
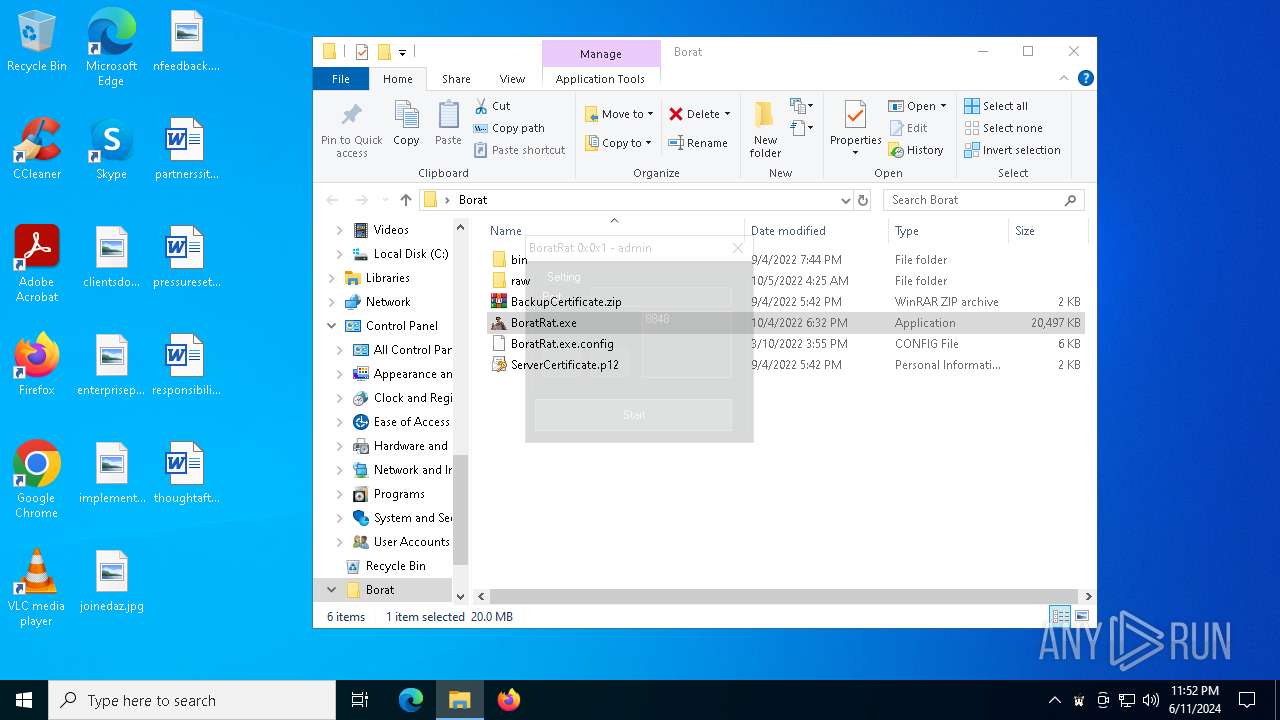
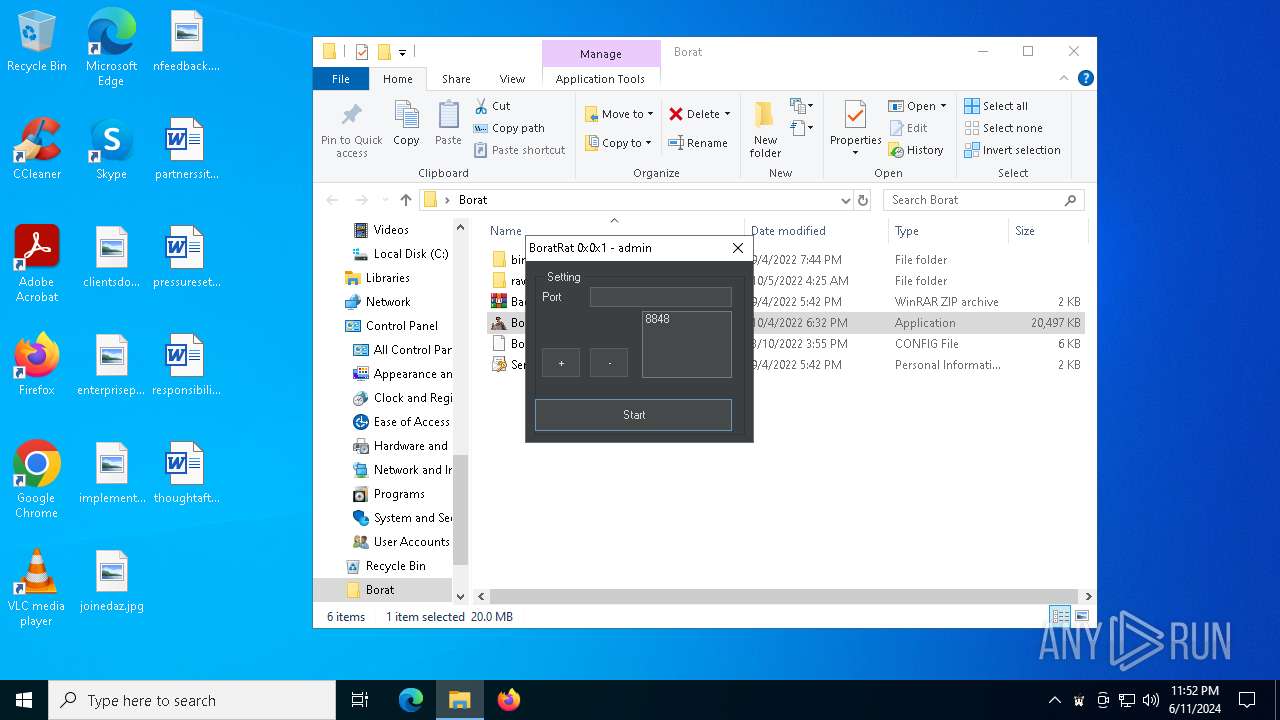
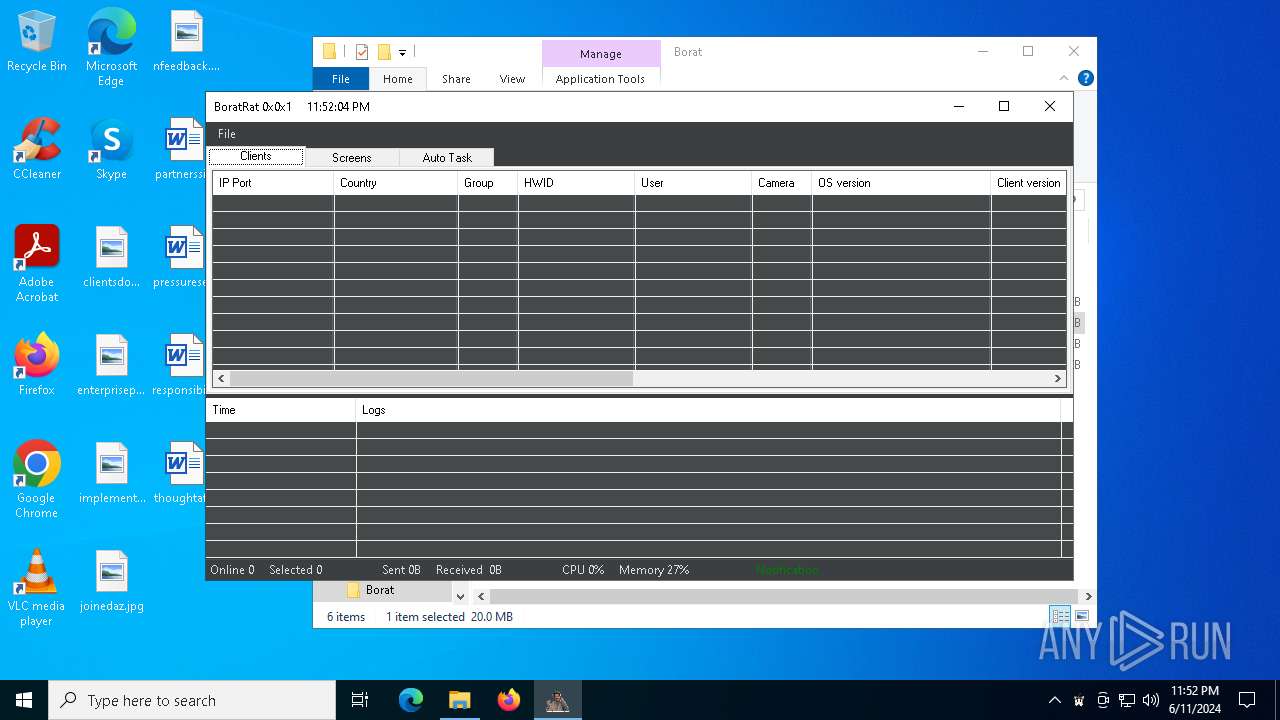
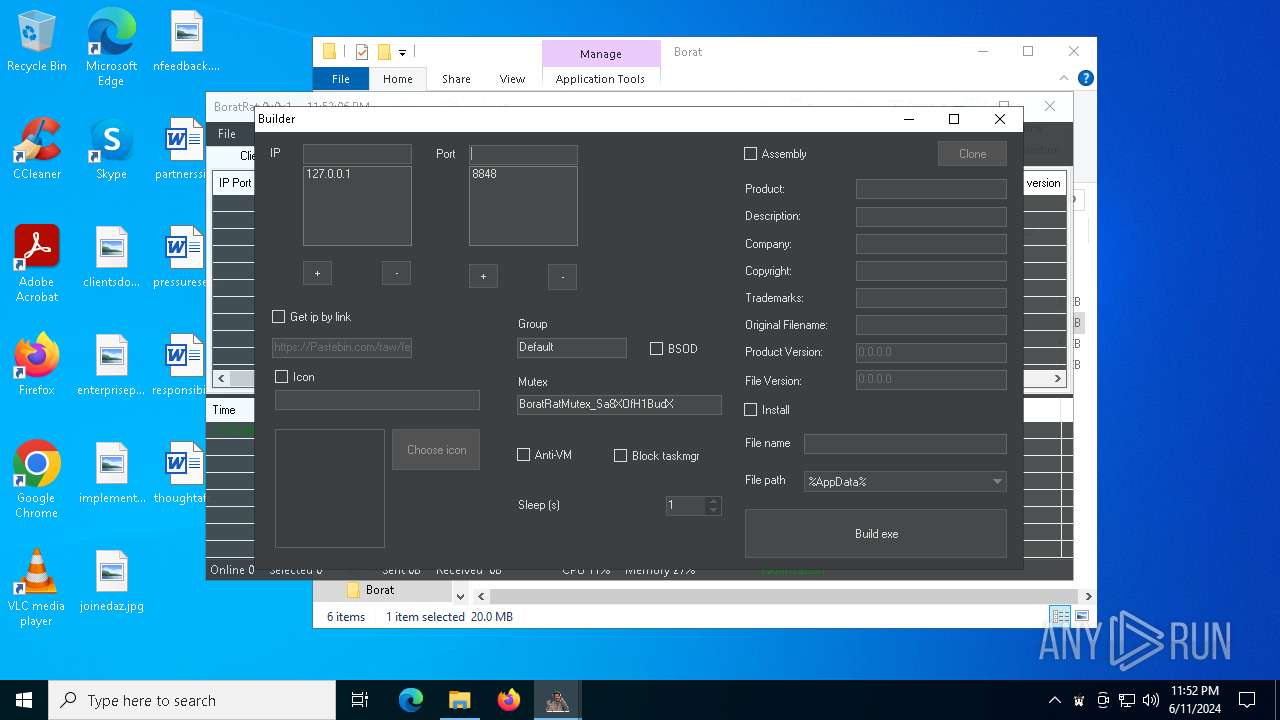
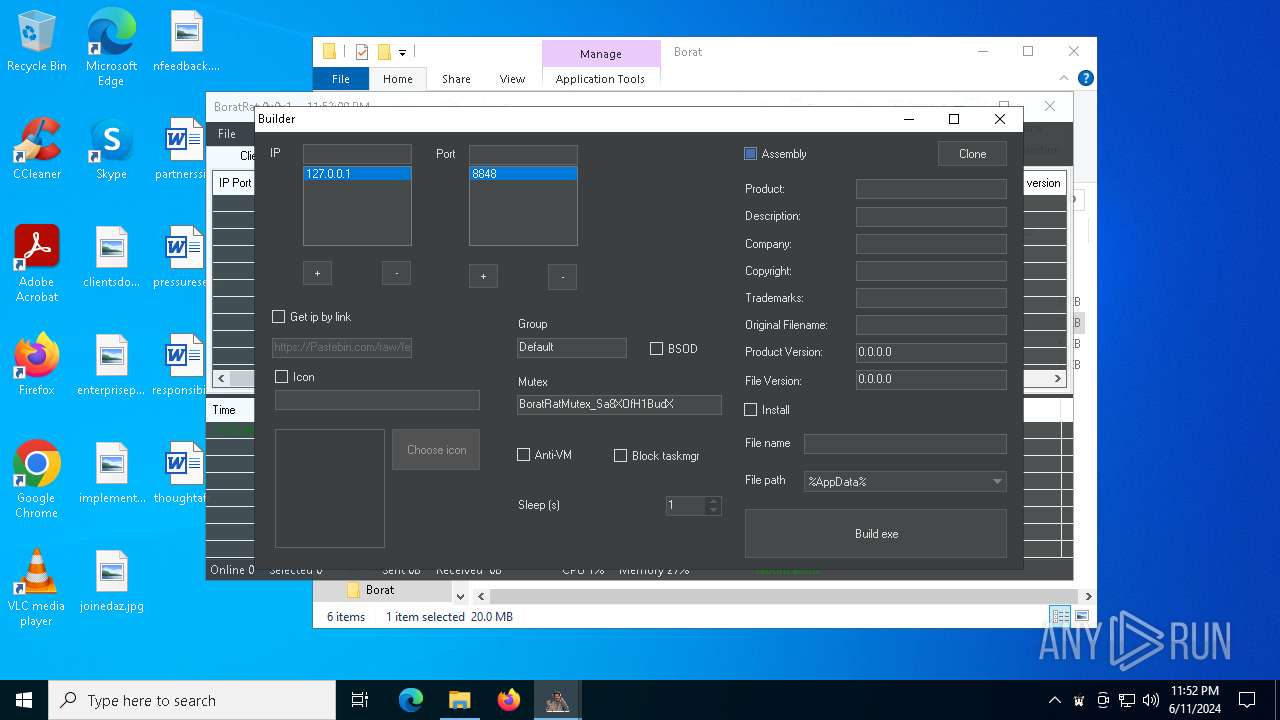
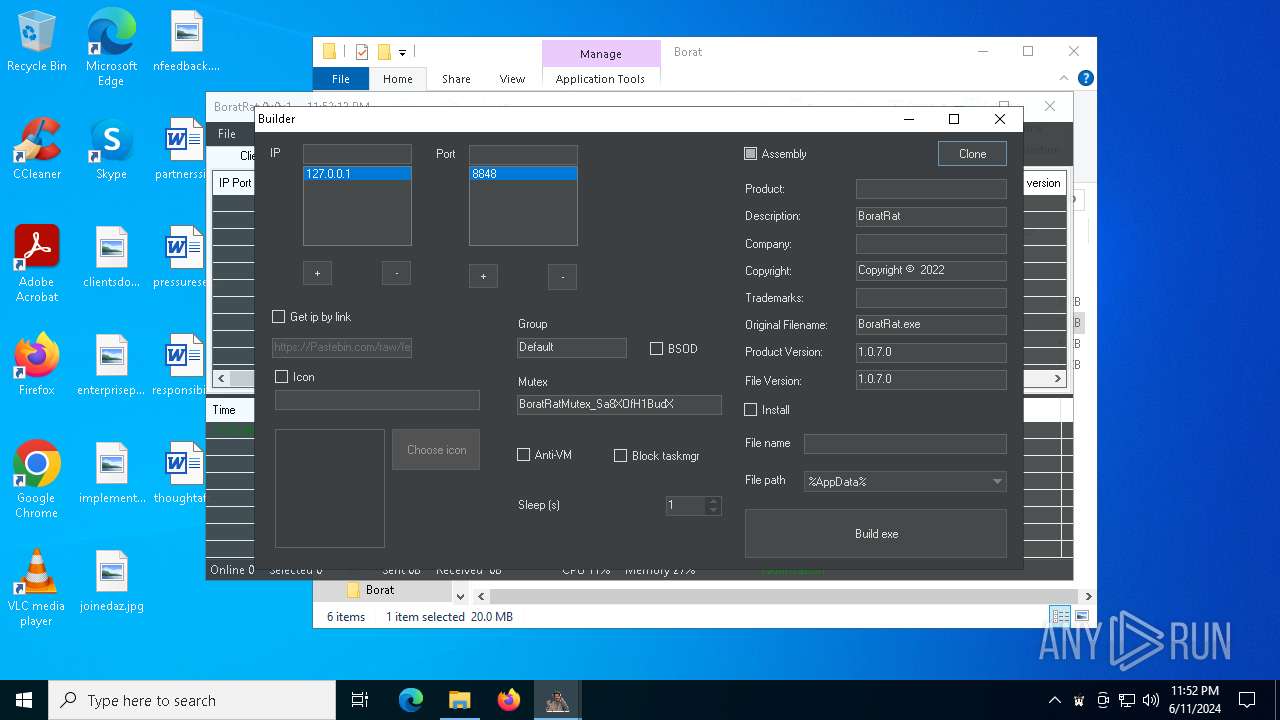
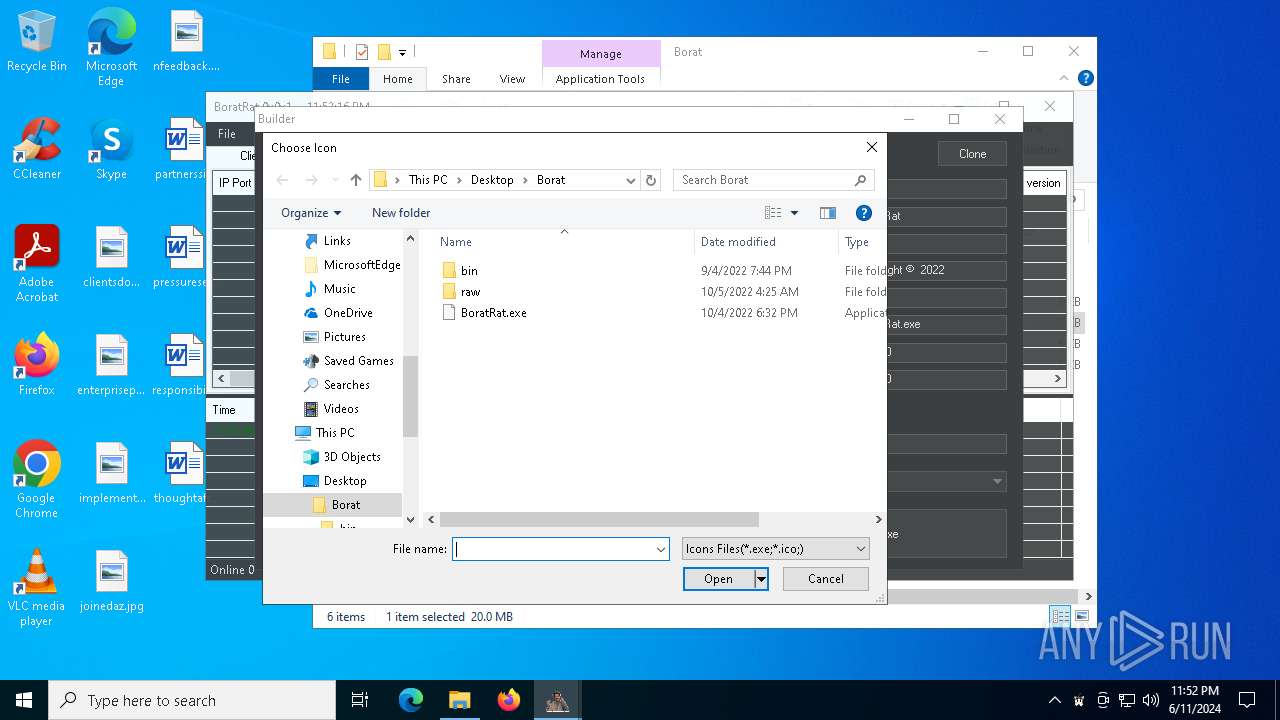
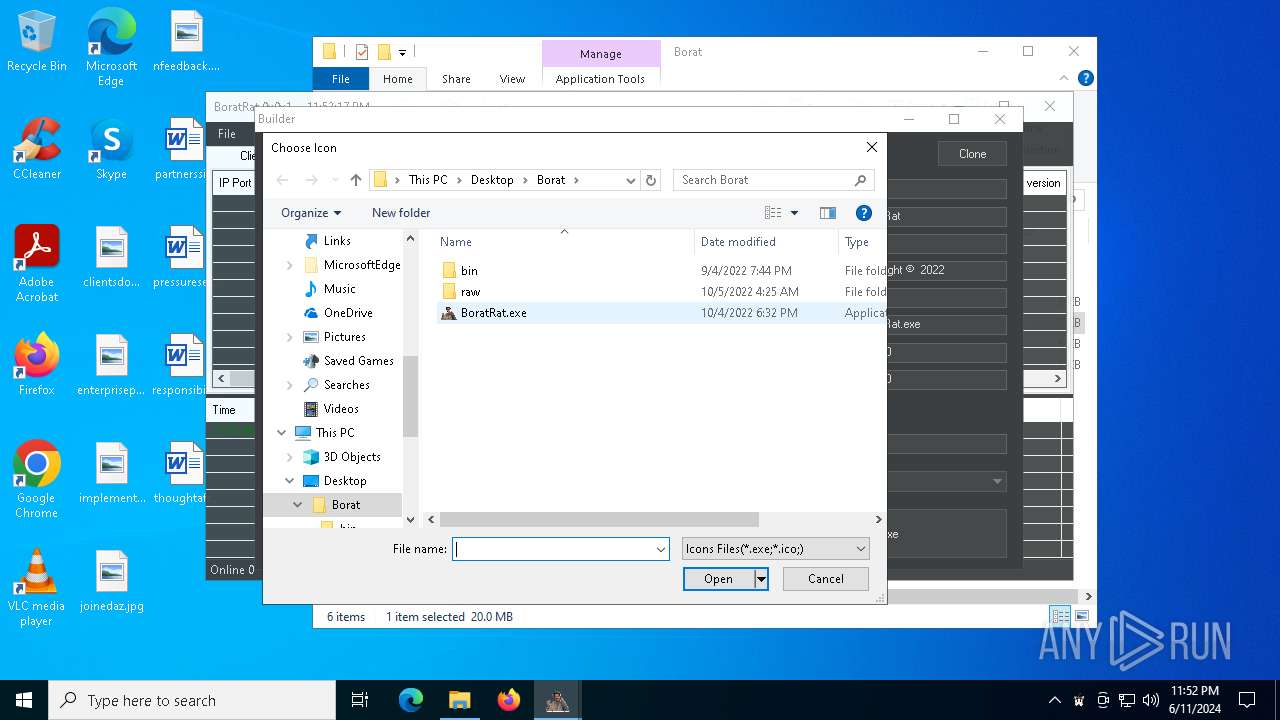
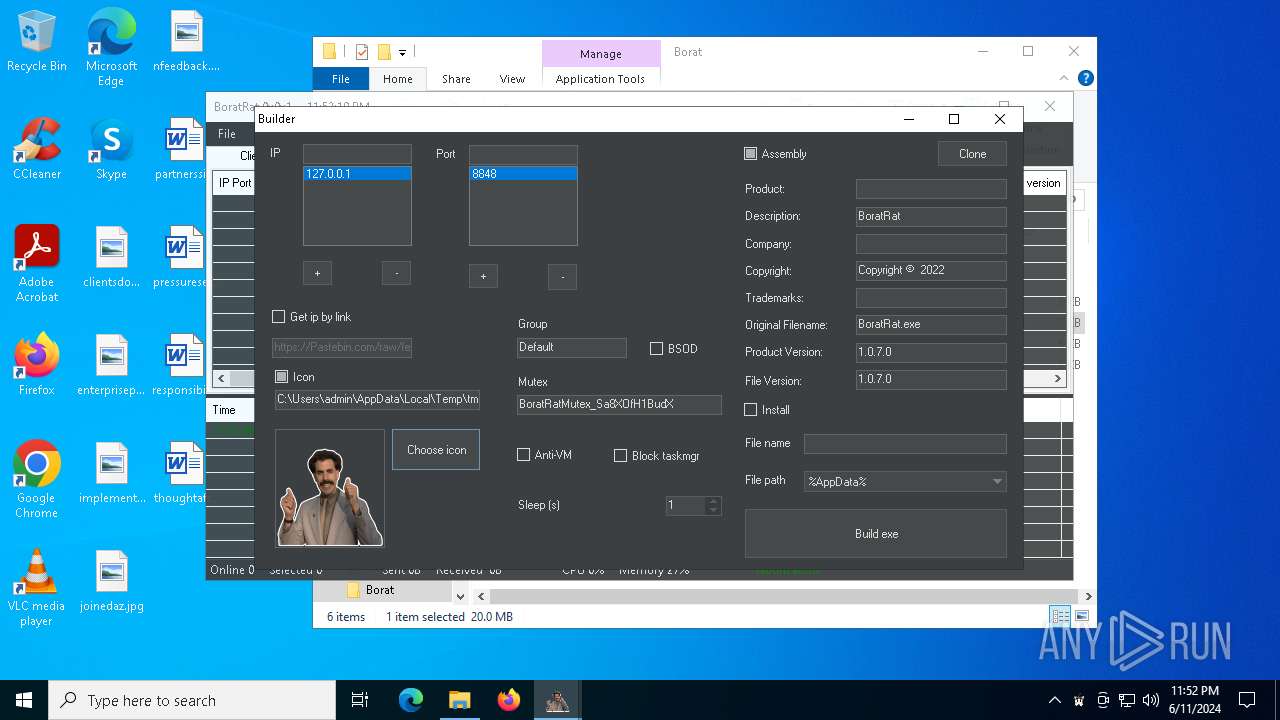
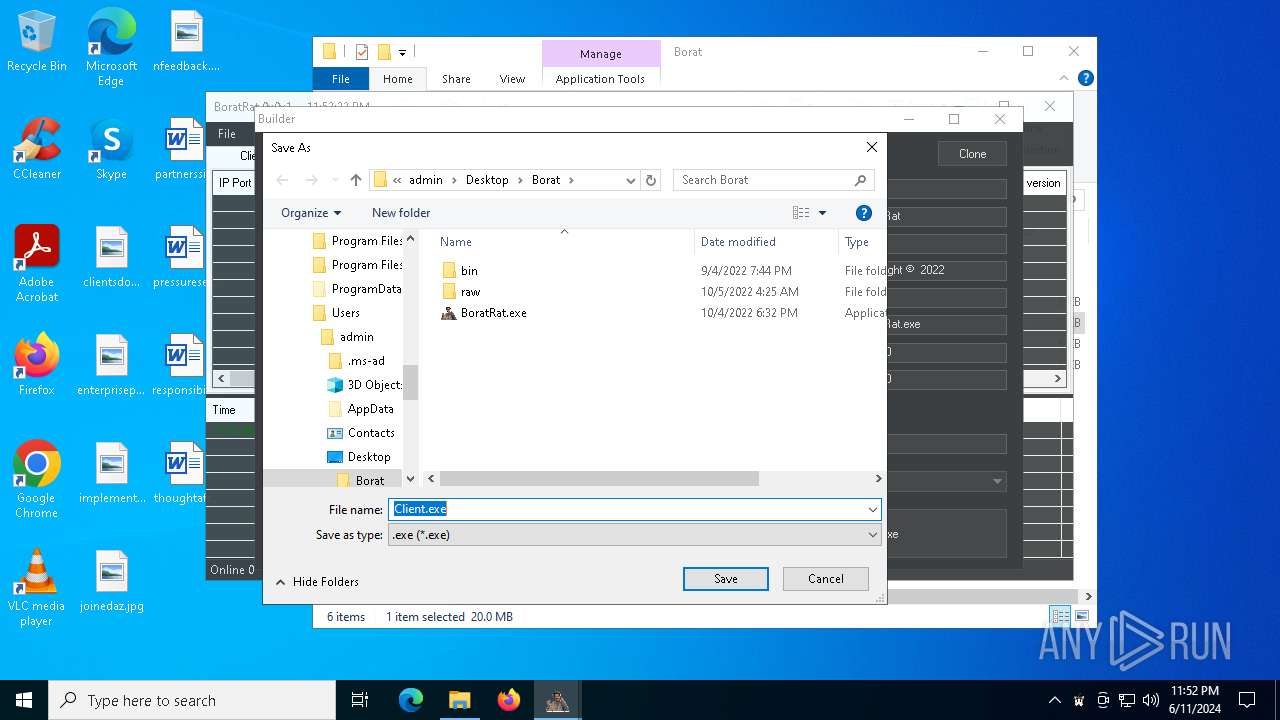
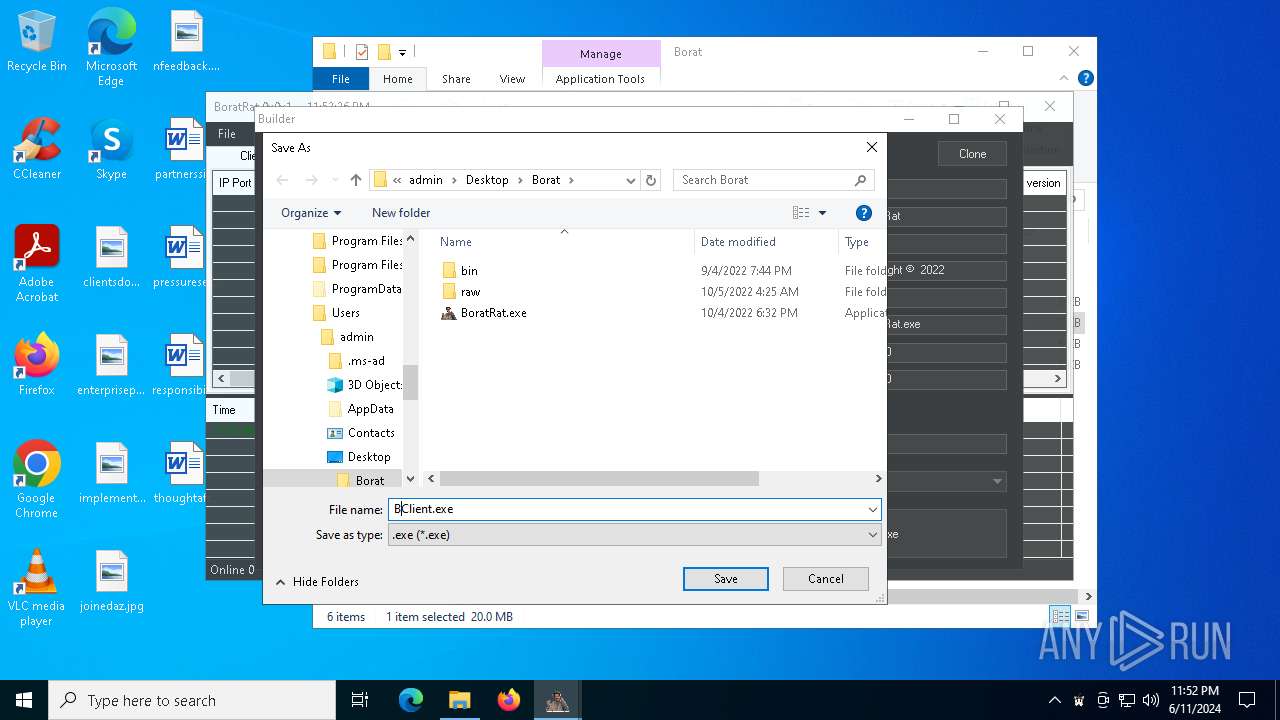
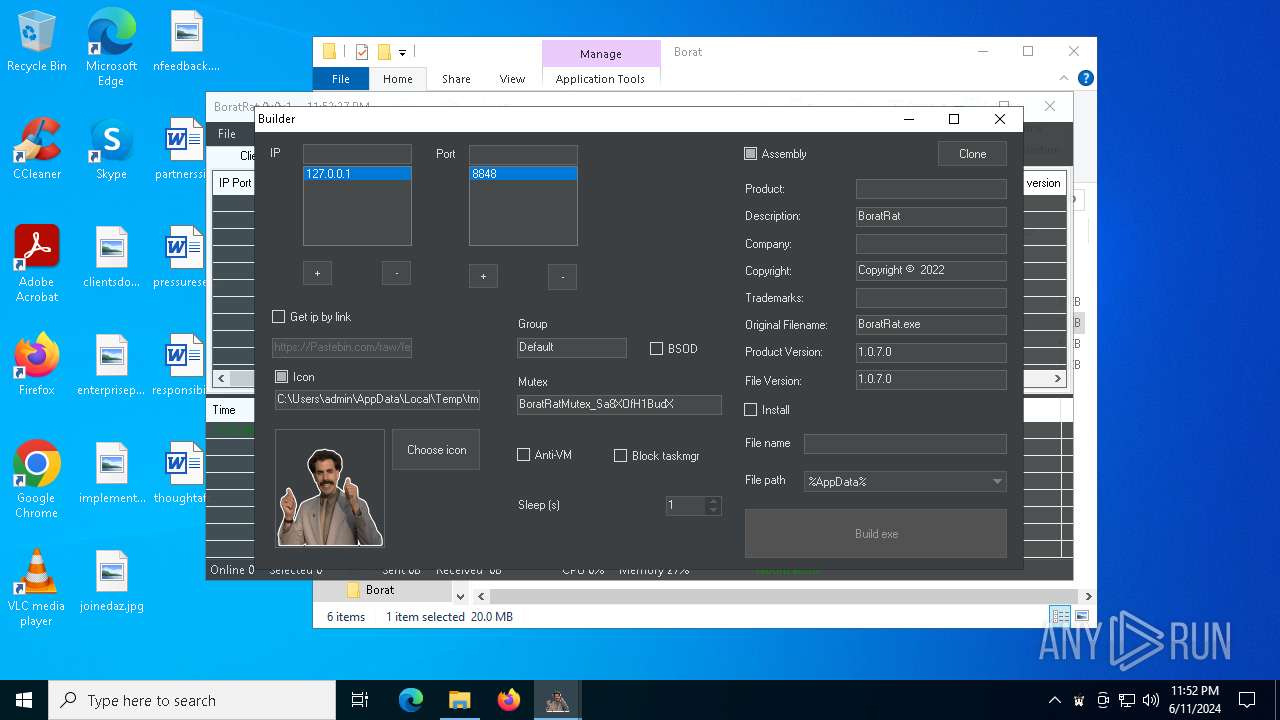
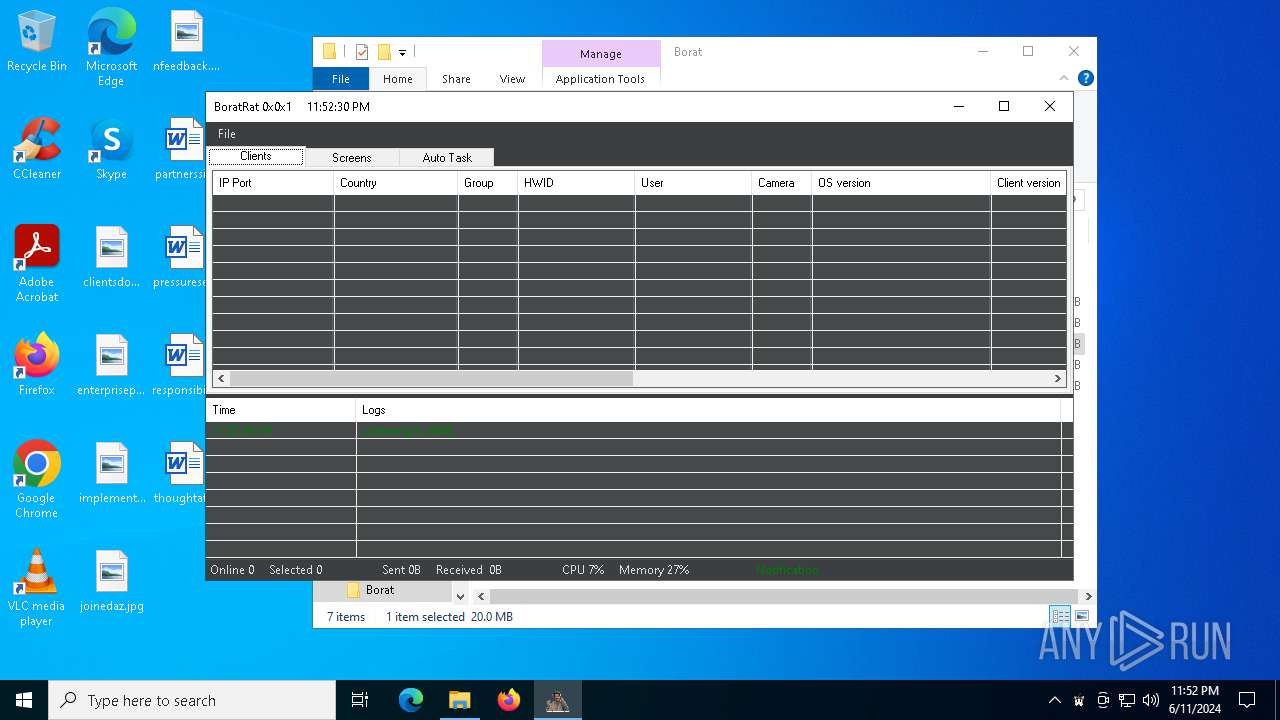
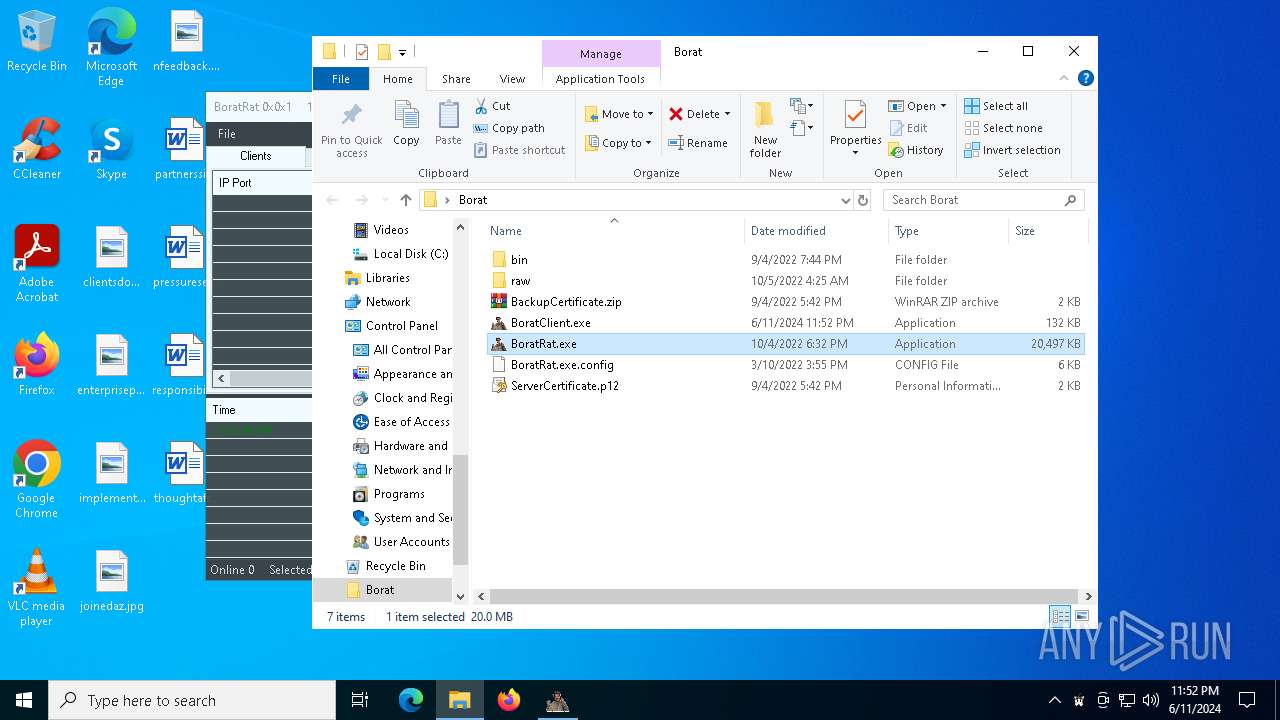
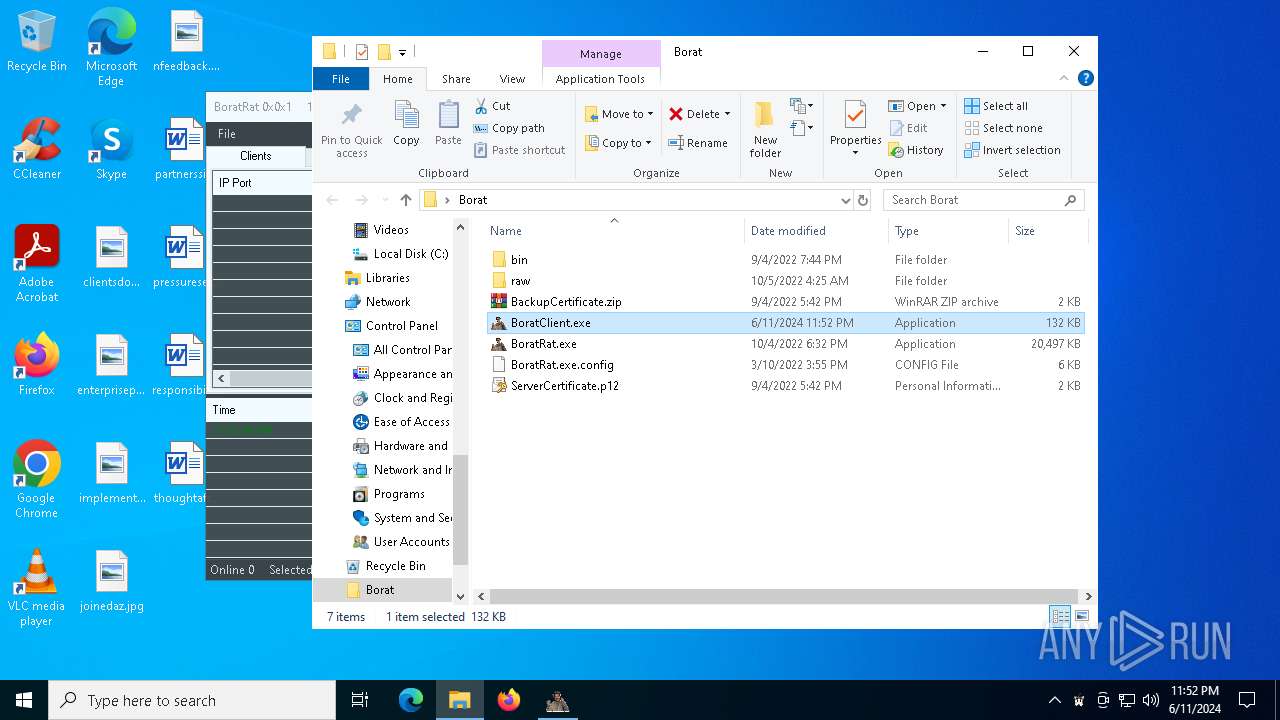
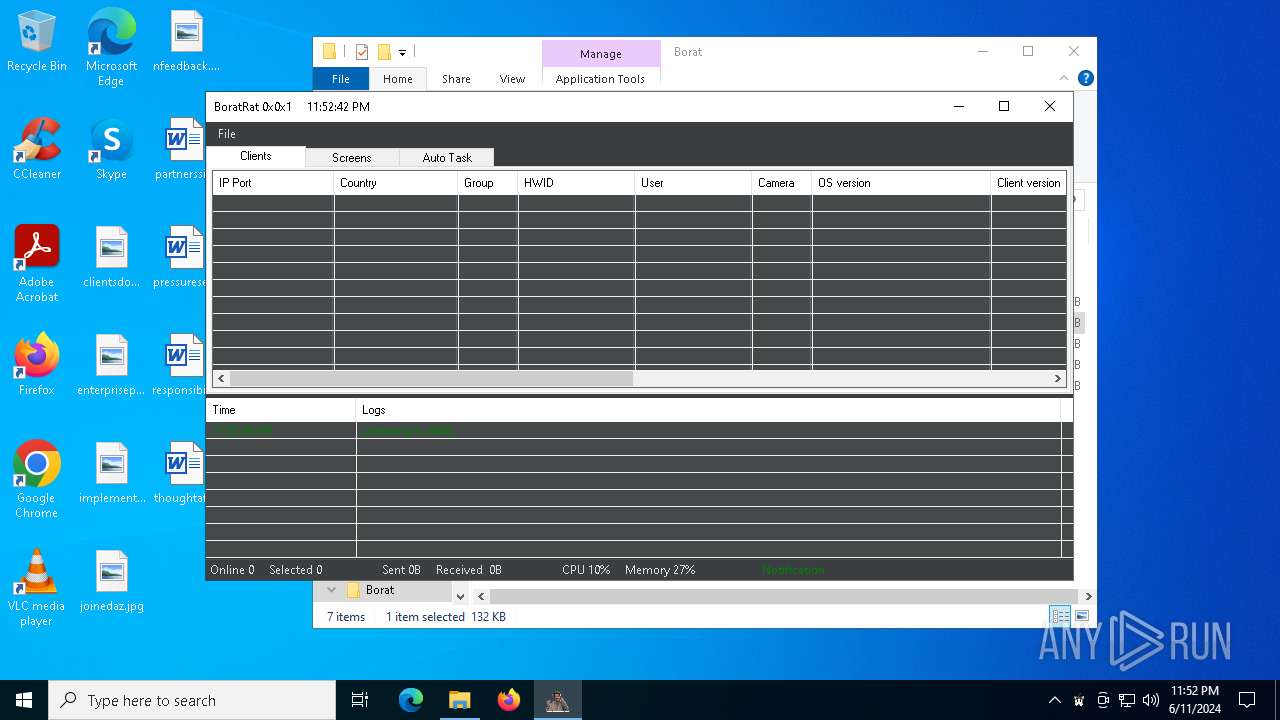
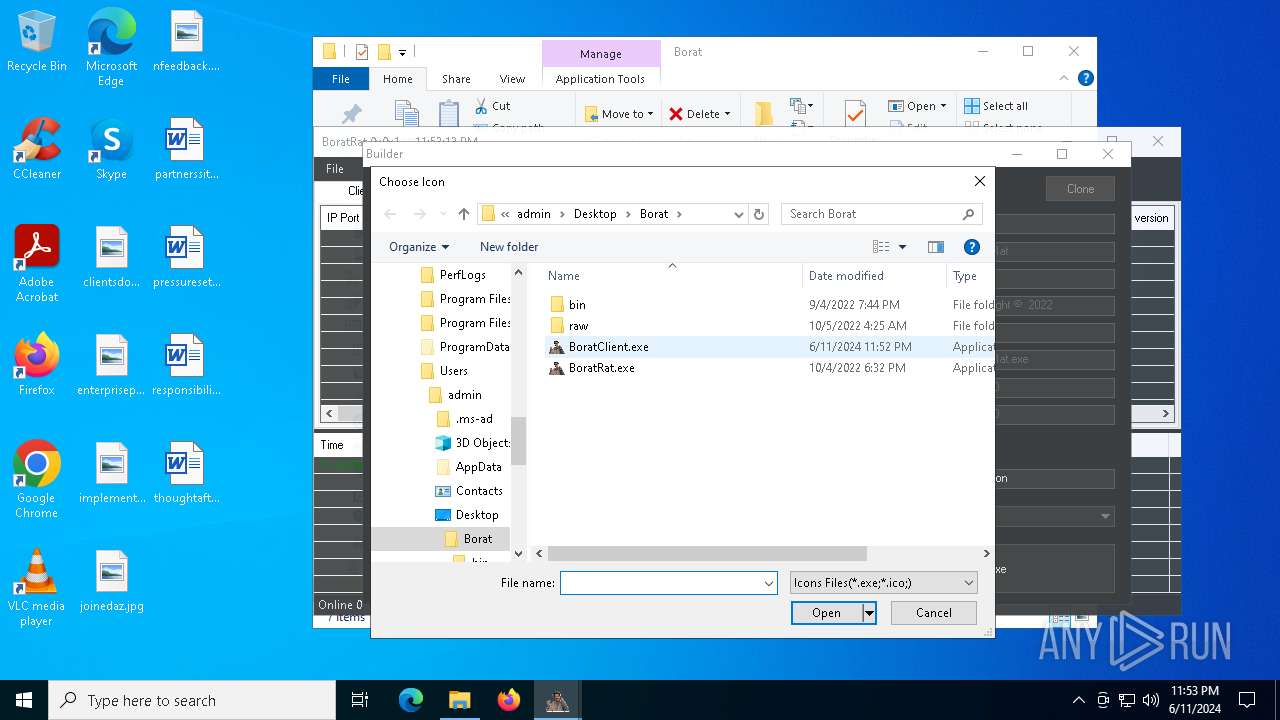
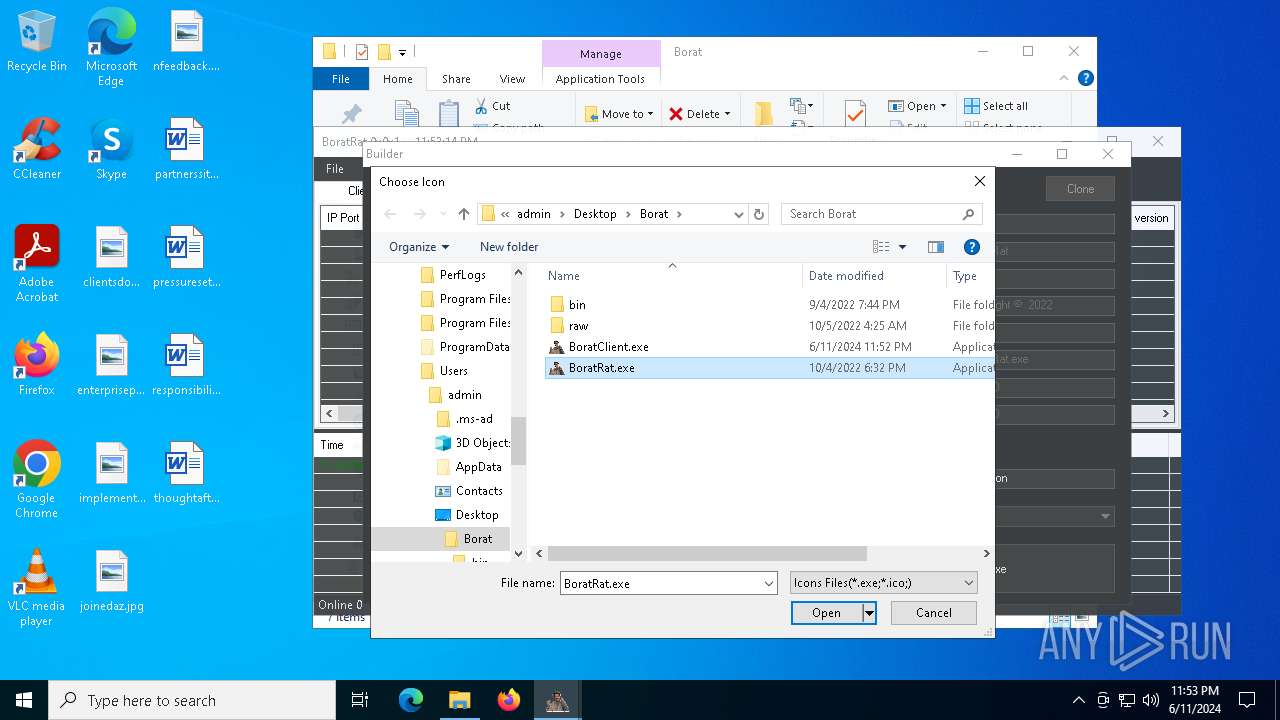
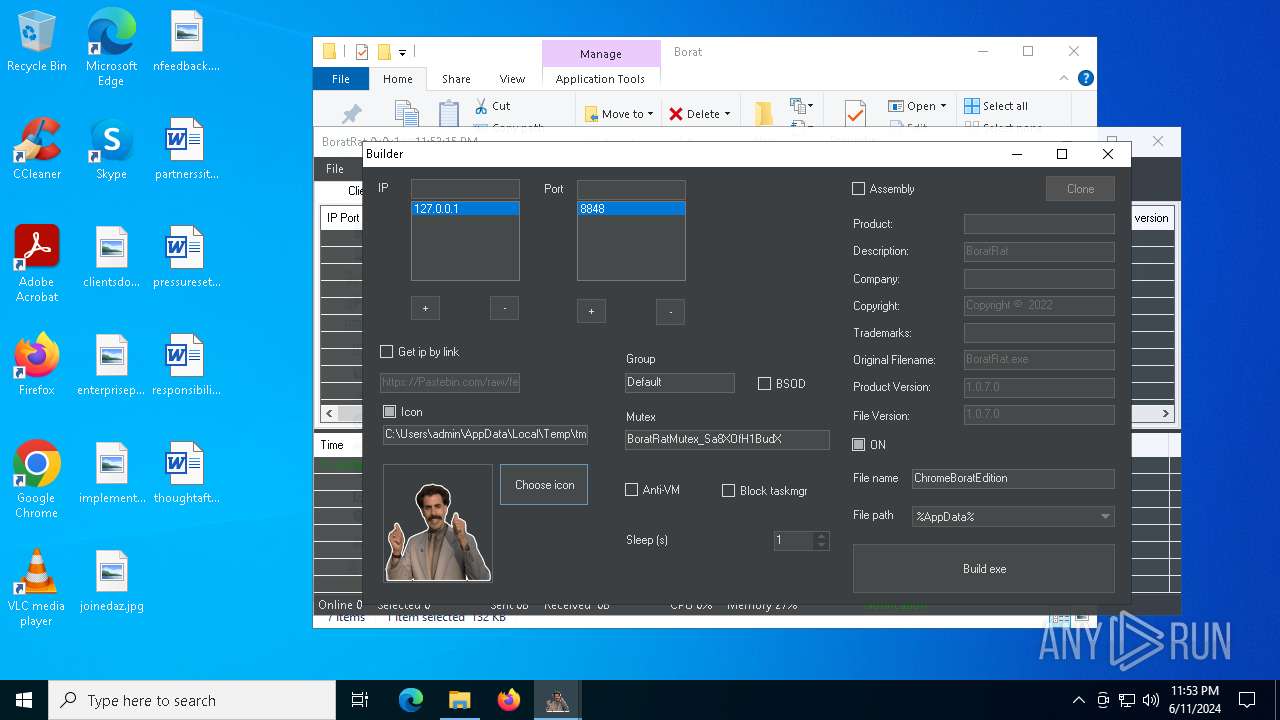
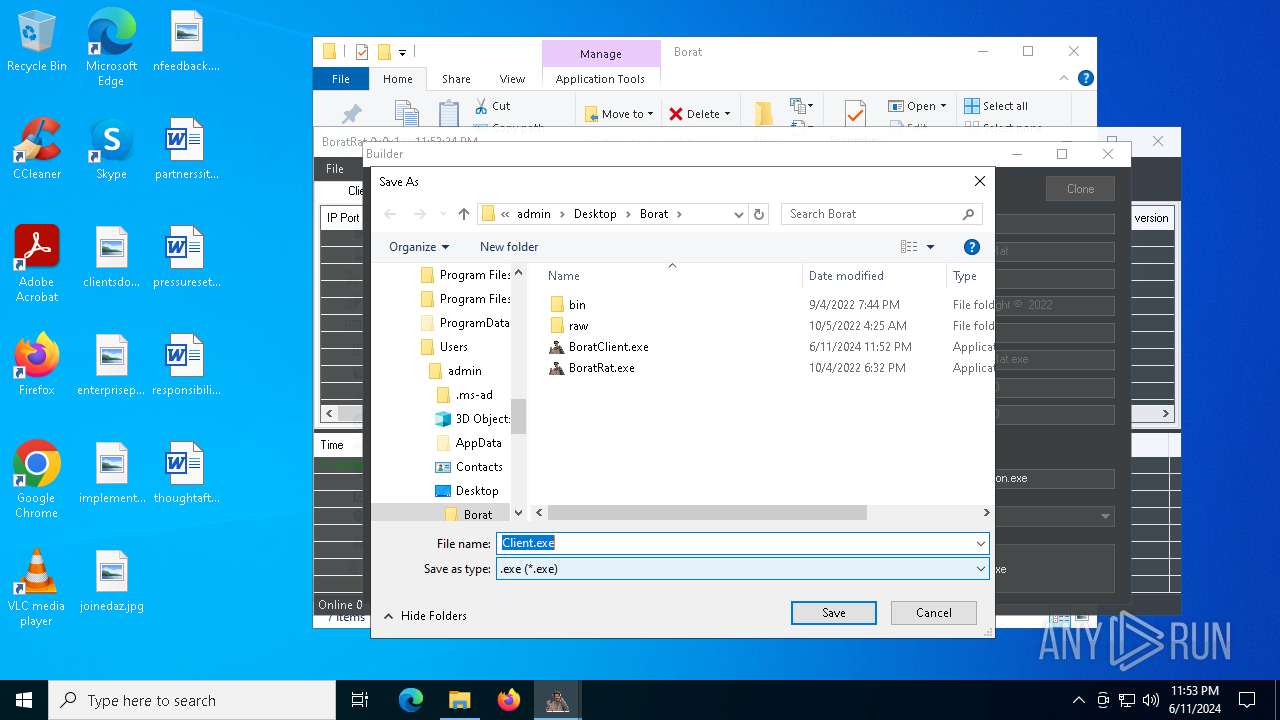
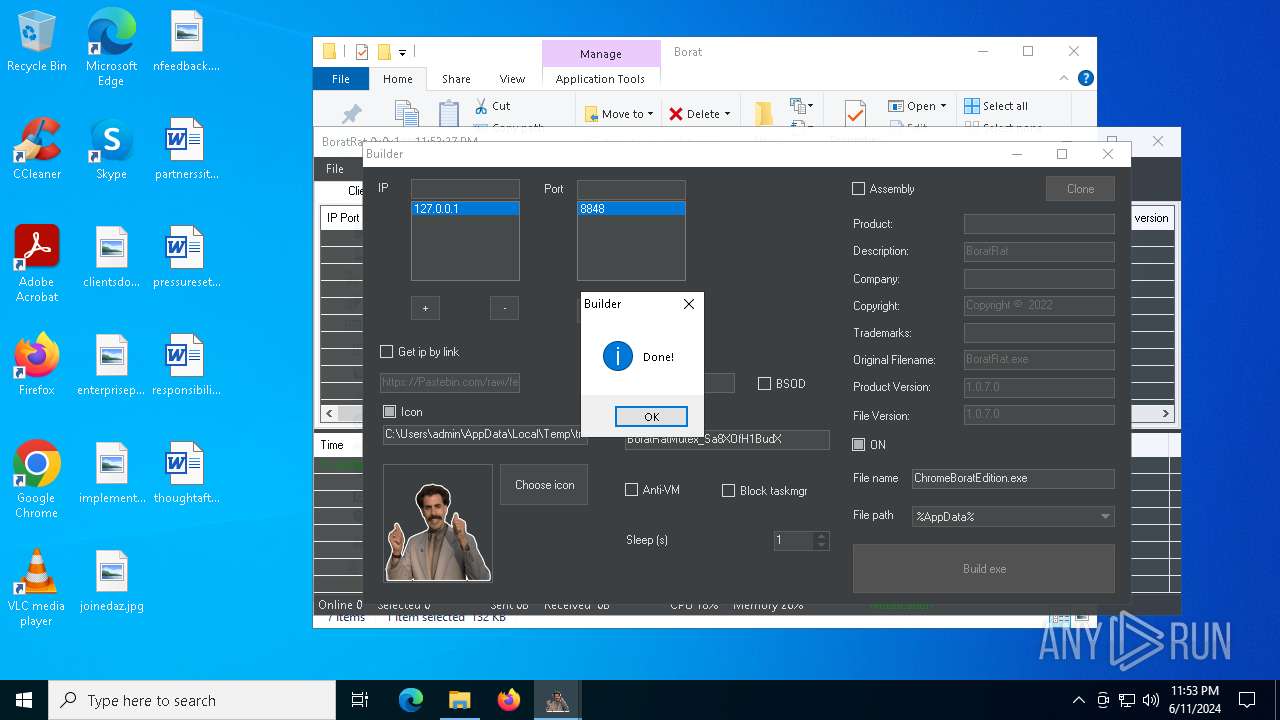
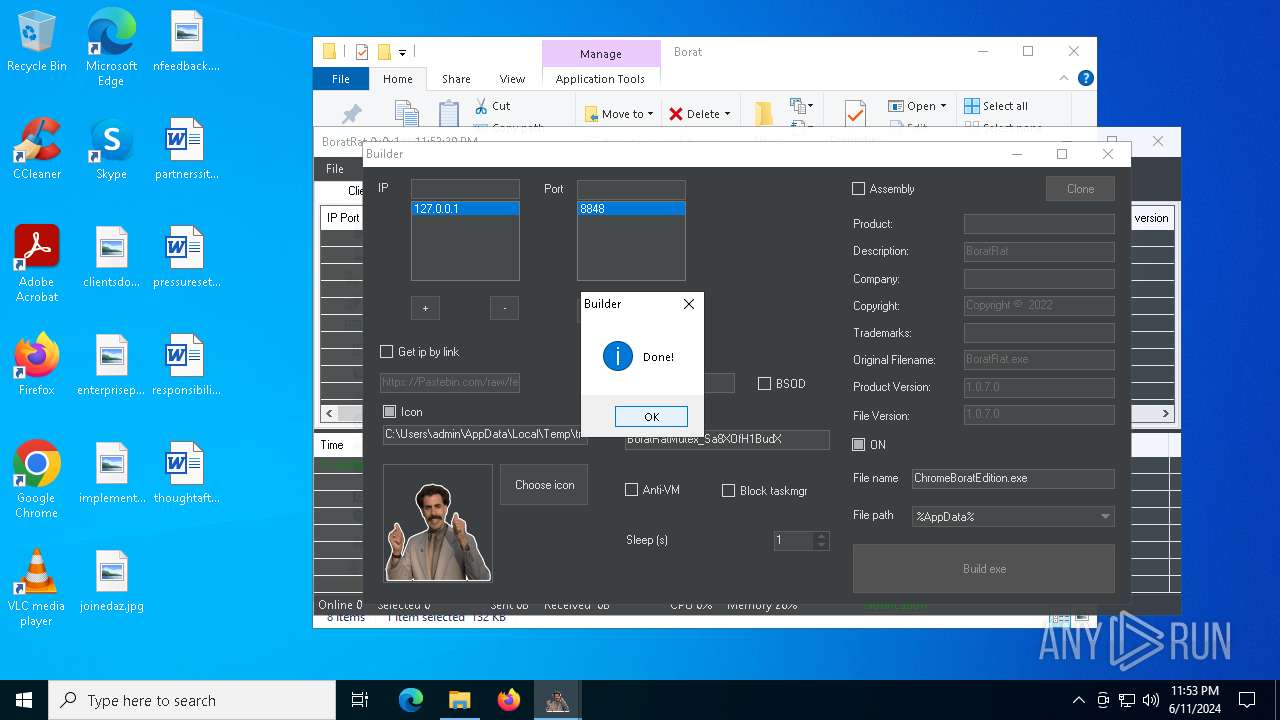
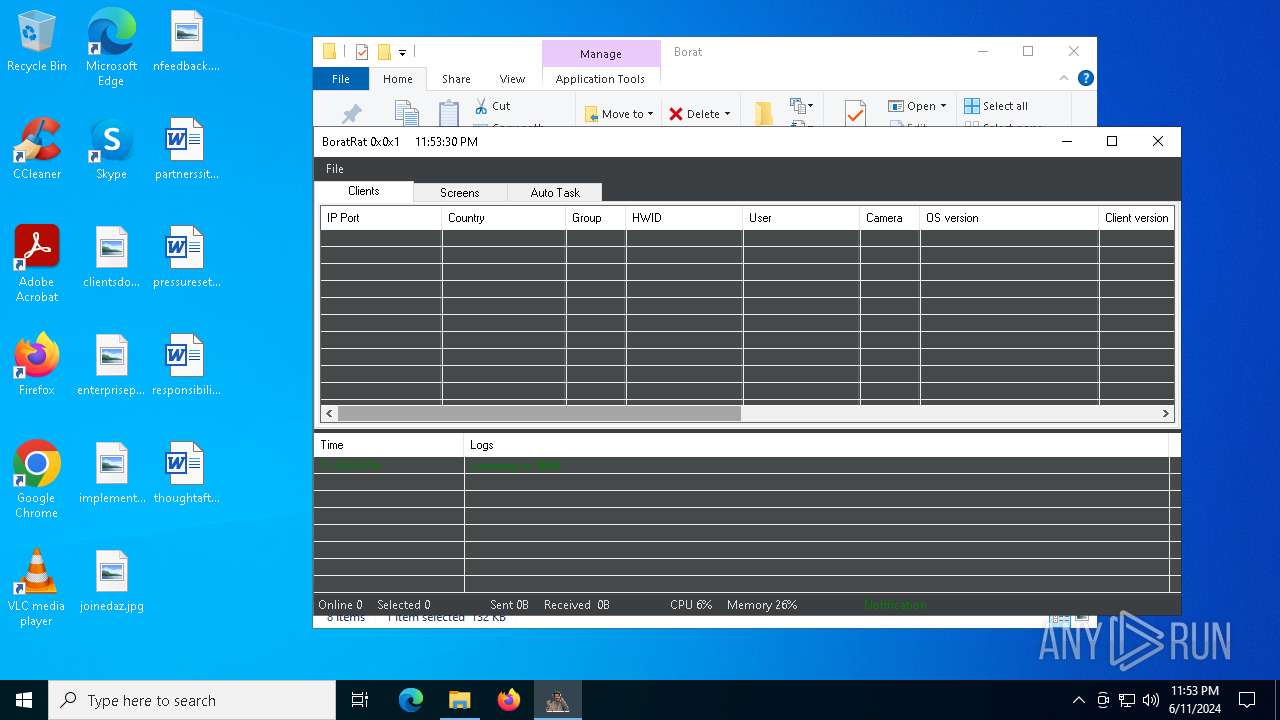
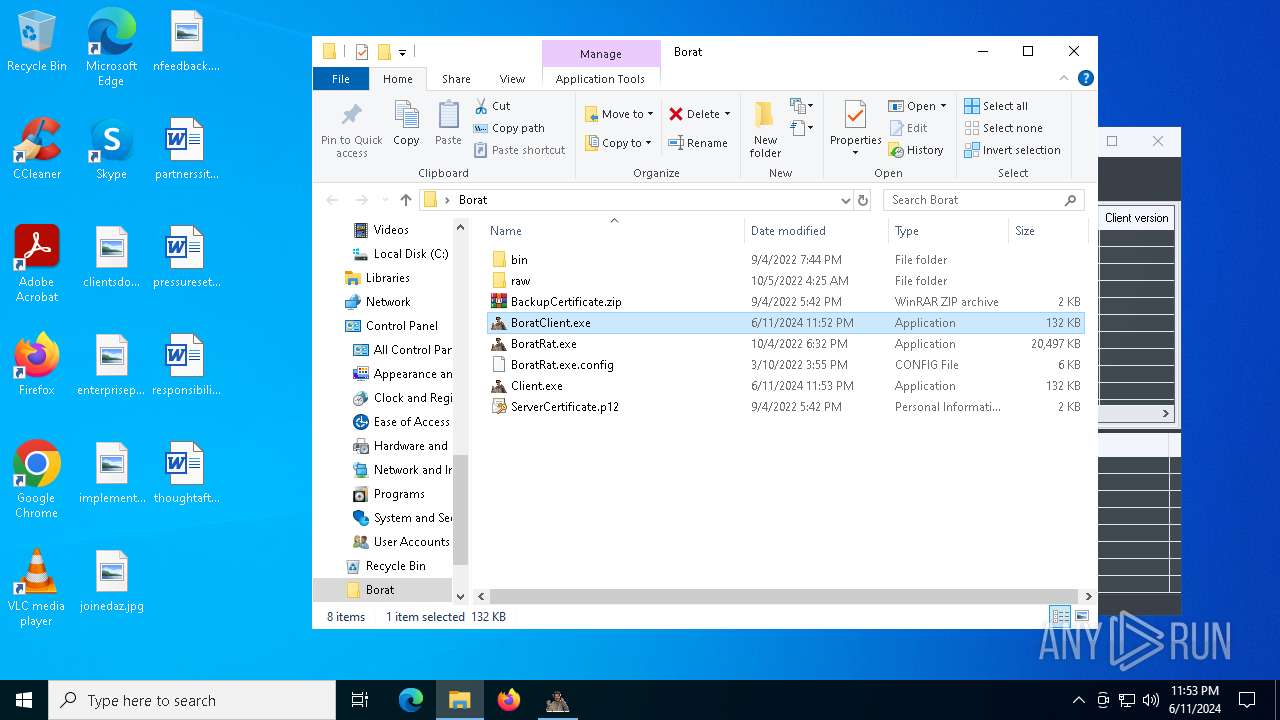
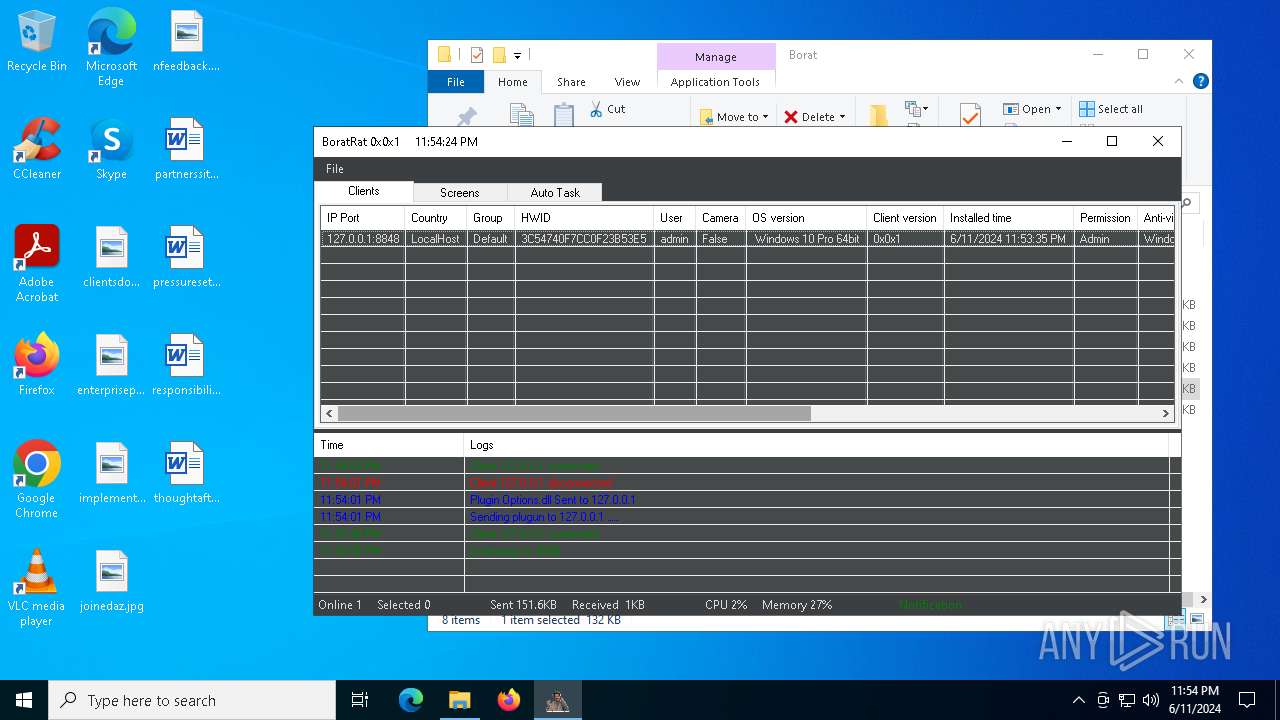
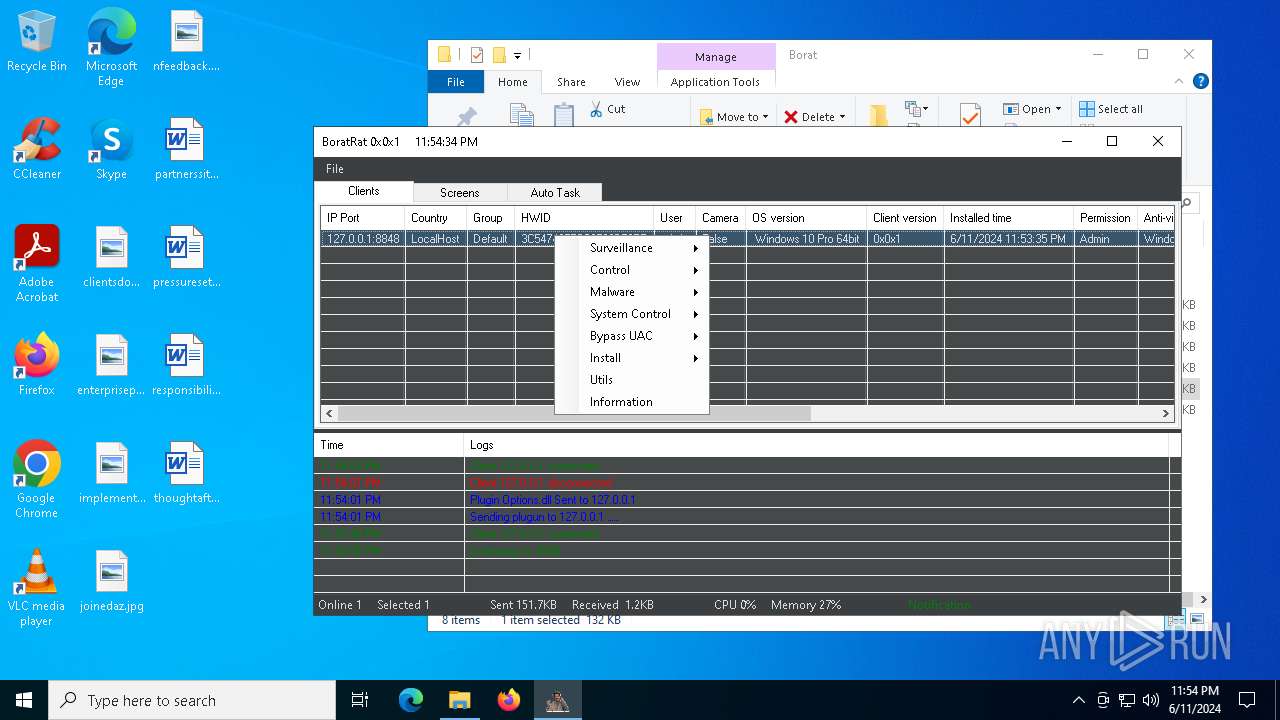
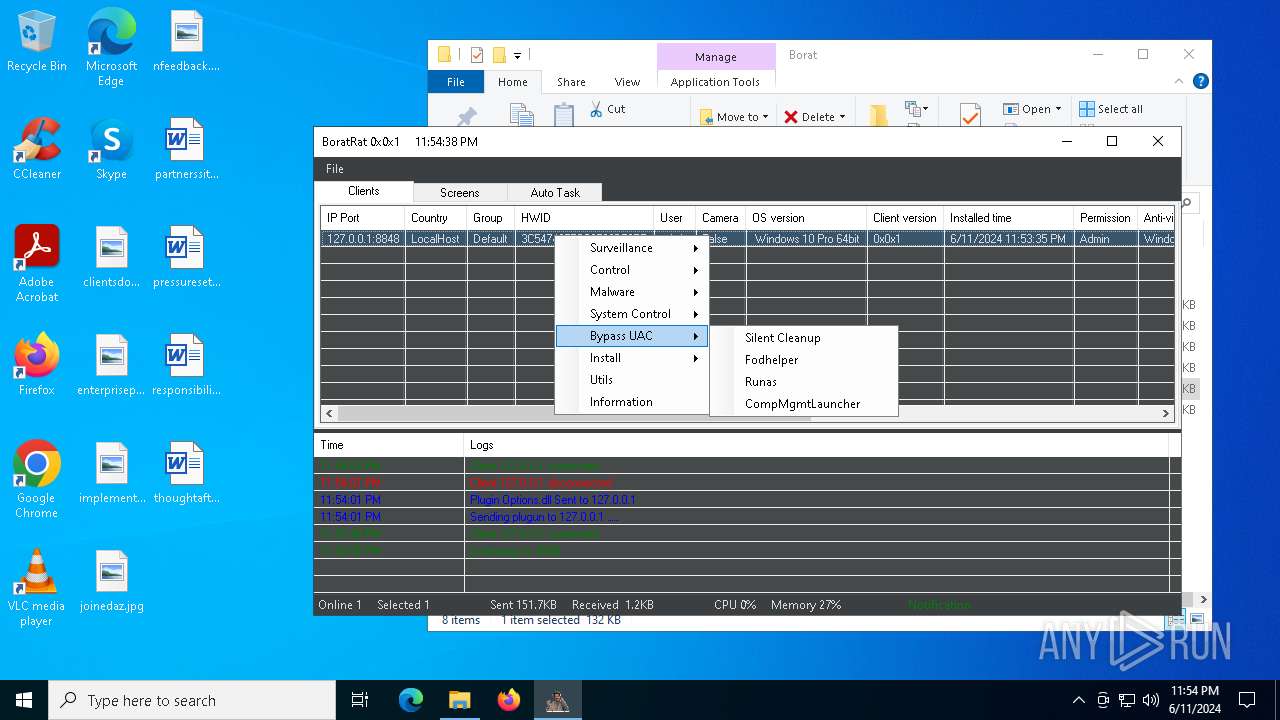
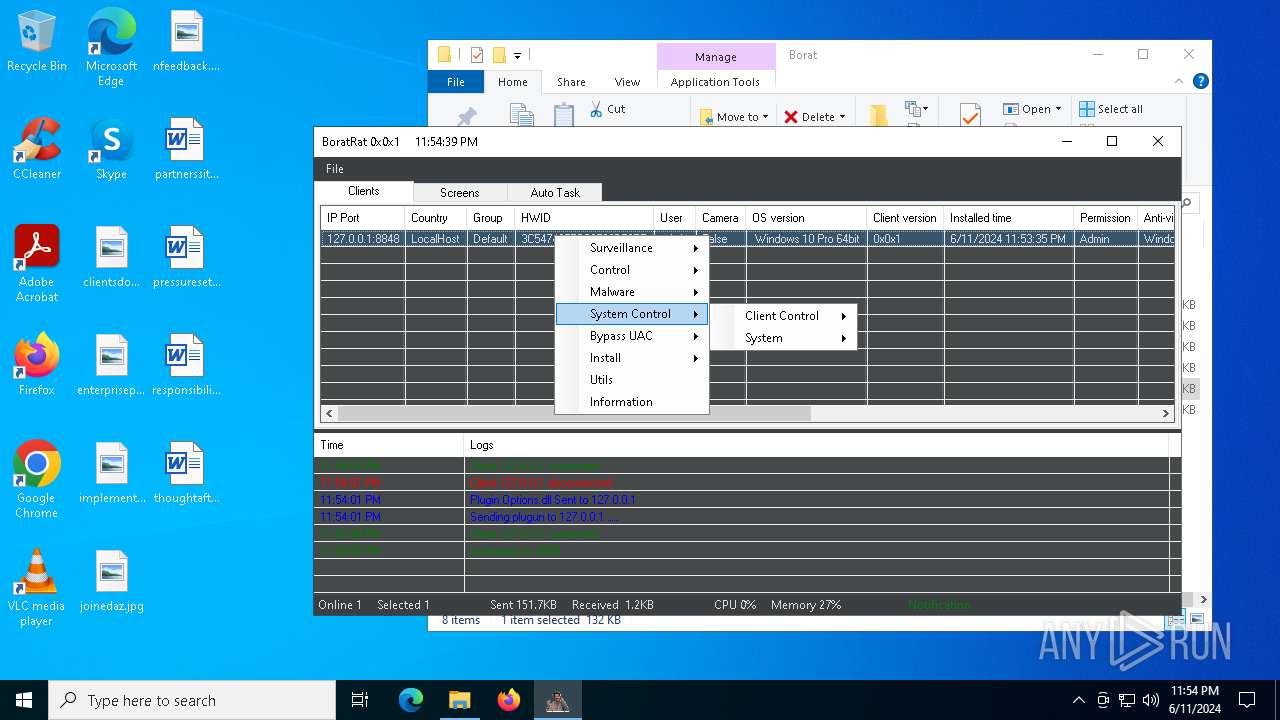
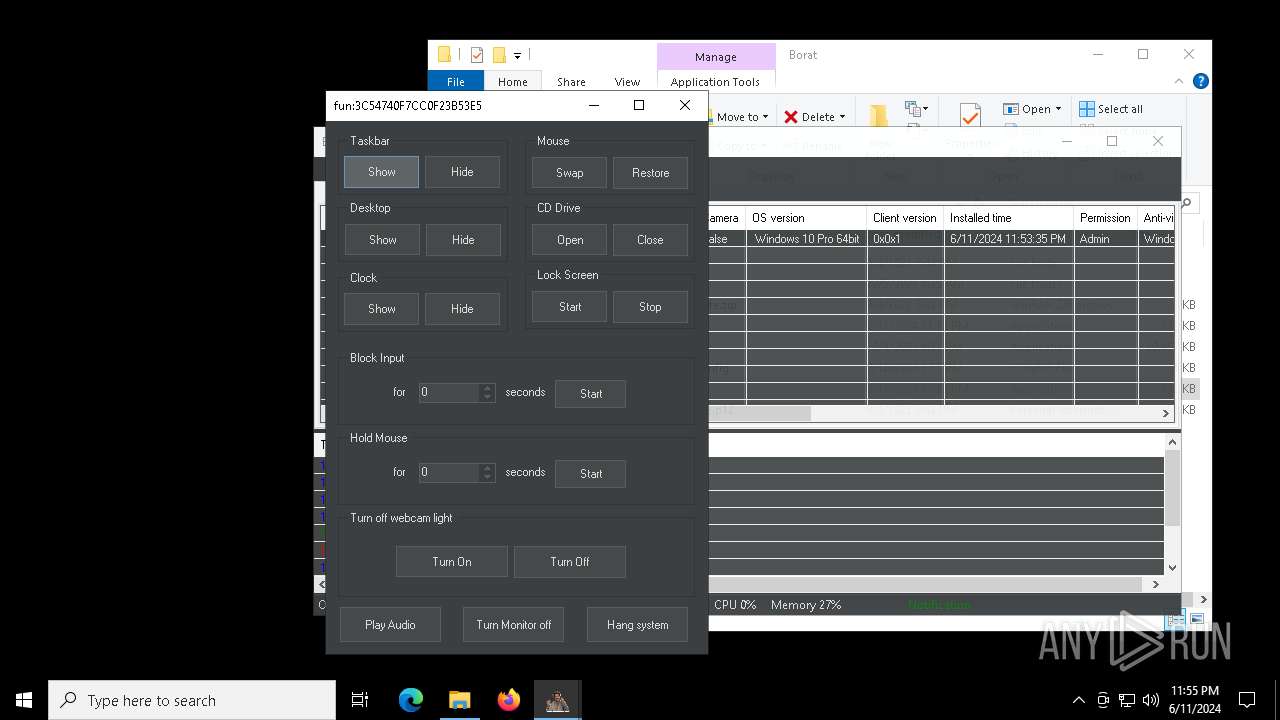
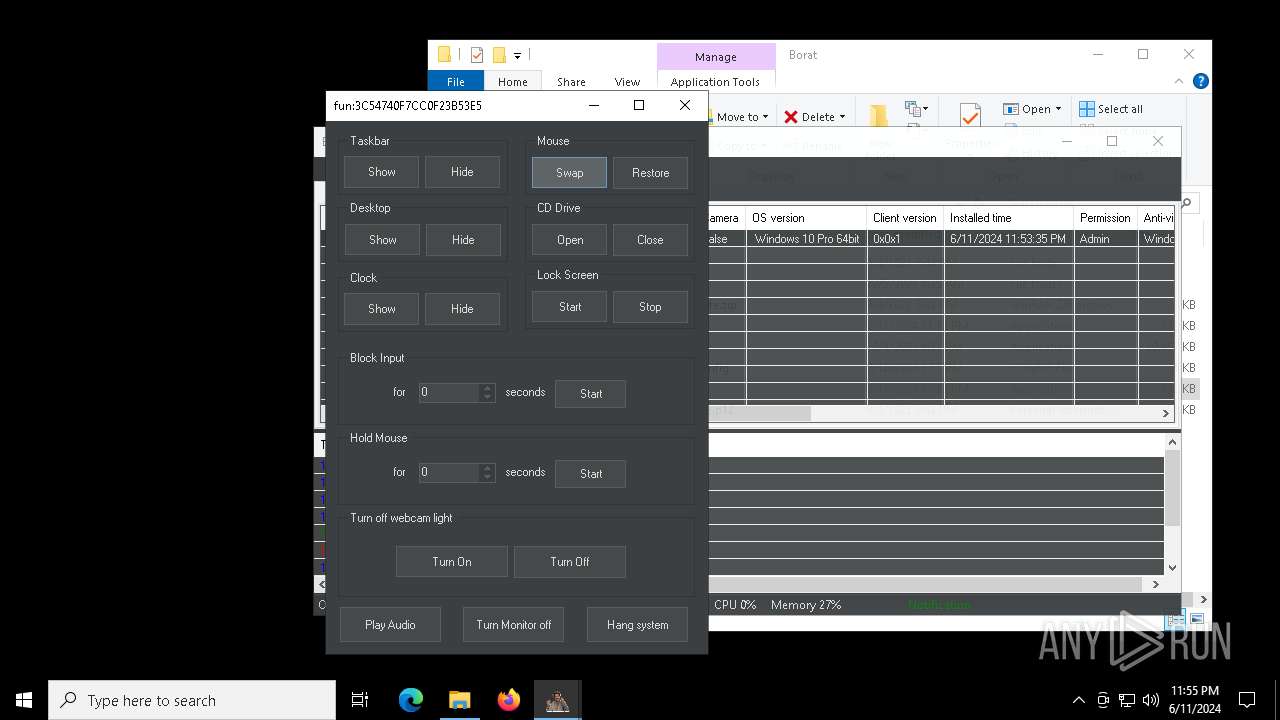
| File name: | Borat.7z |
| Full analysis: | https://app.any.run/tasks/7c5826c0-b1b0-4656-bb7f-182c374e6ade |
| Verdict: | Malicious activity |
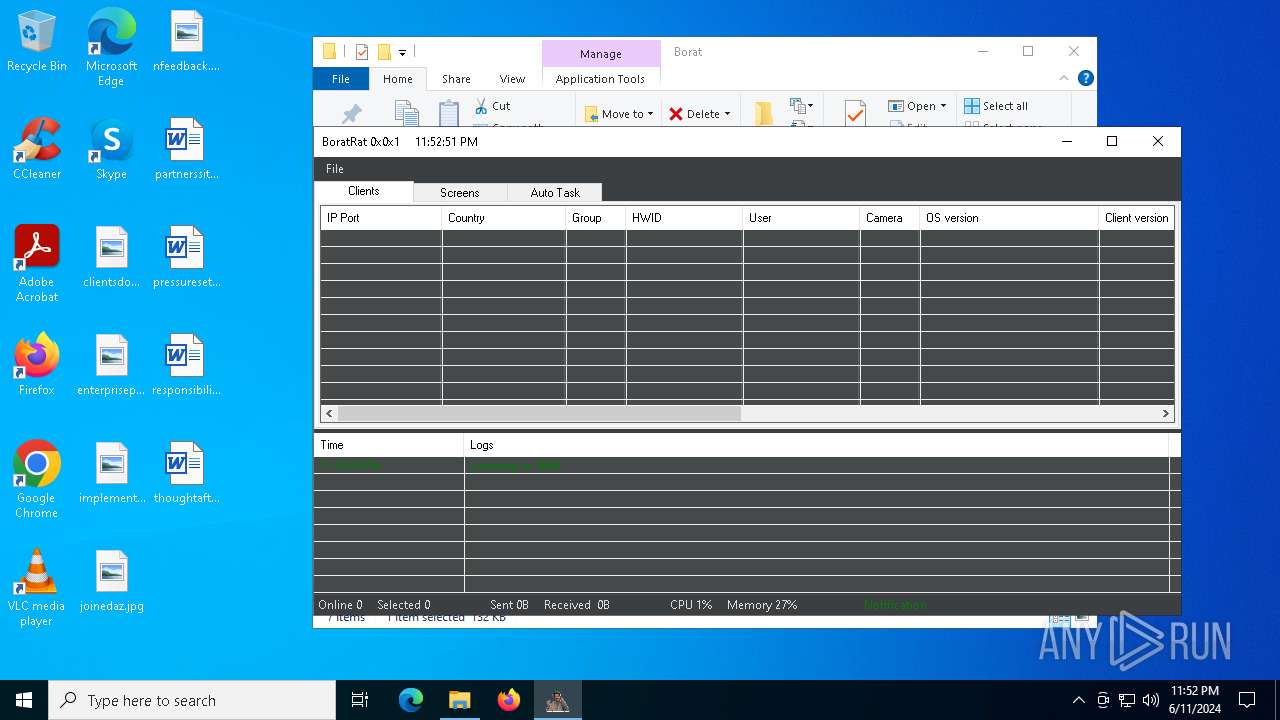
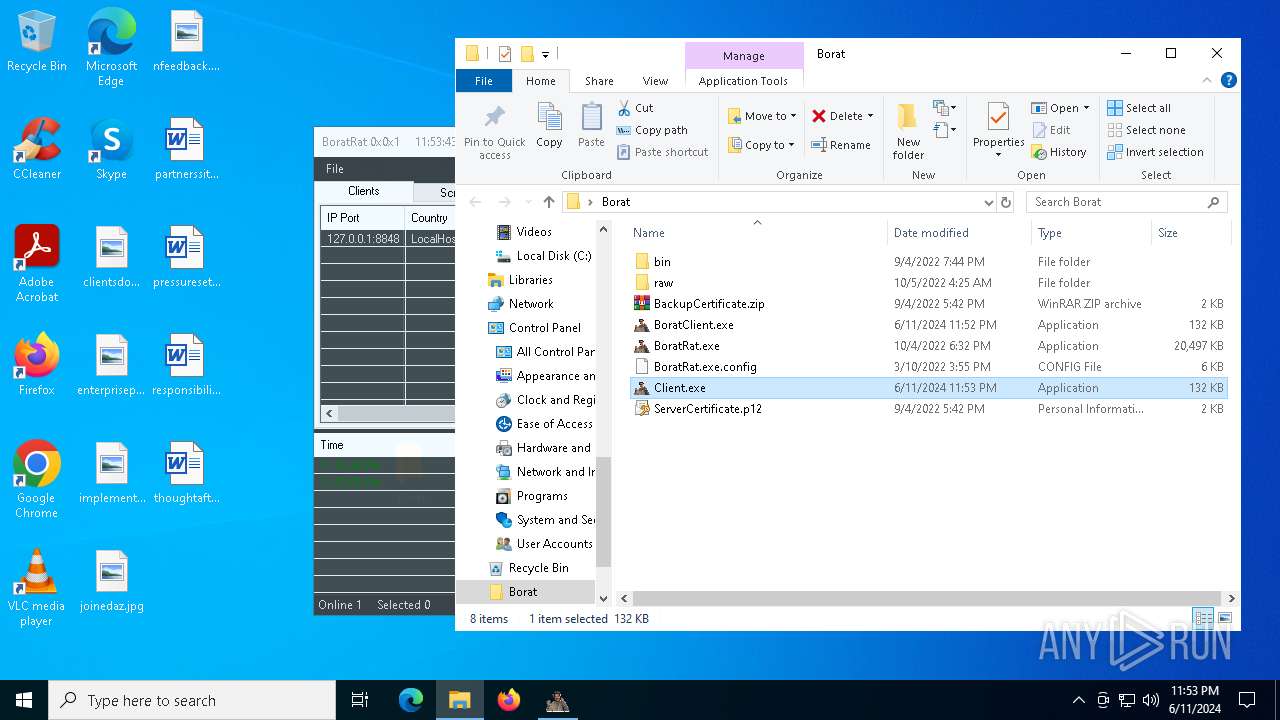
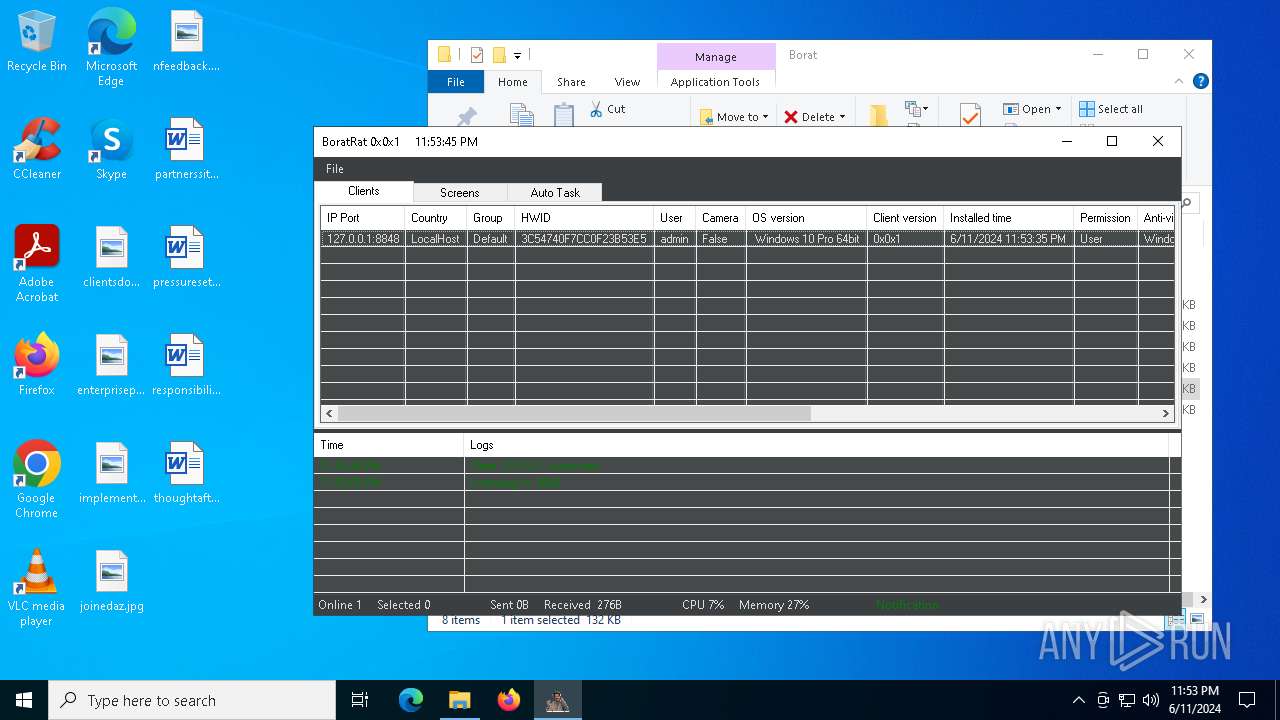
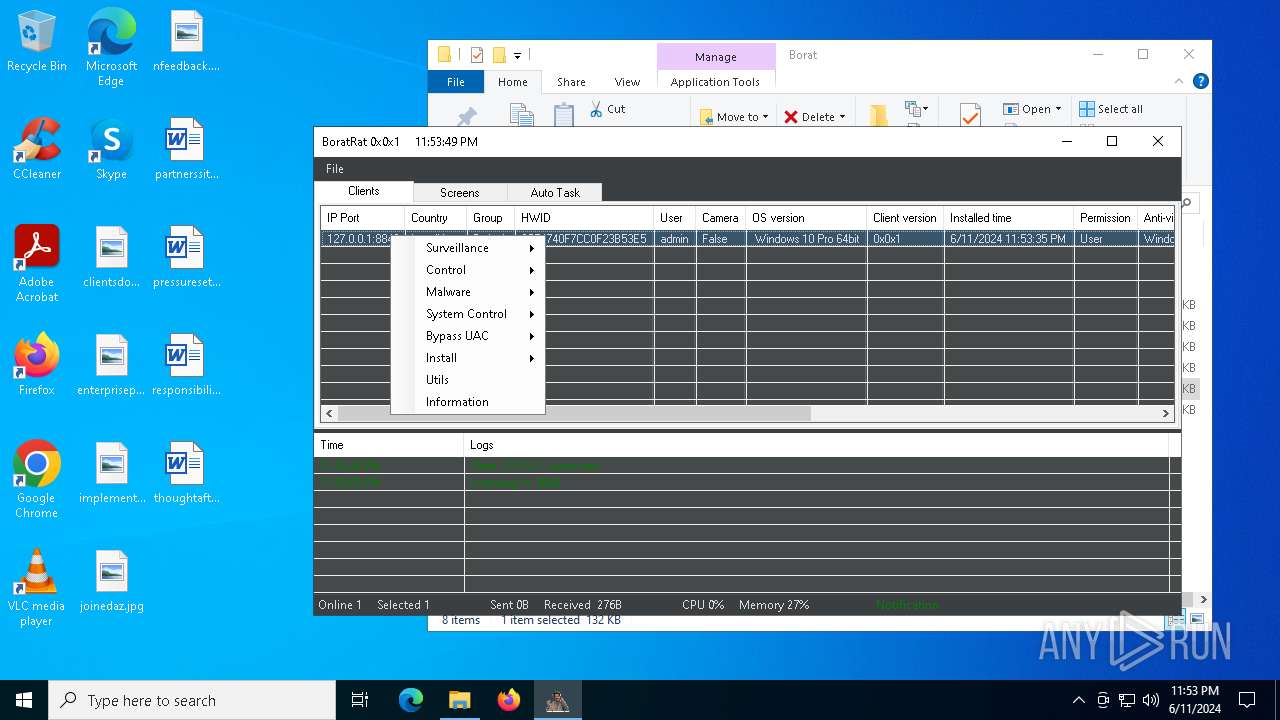
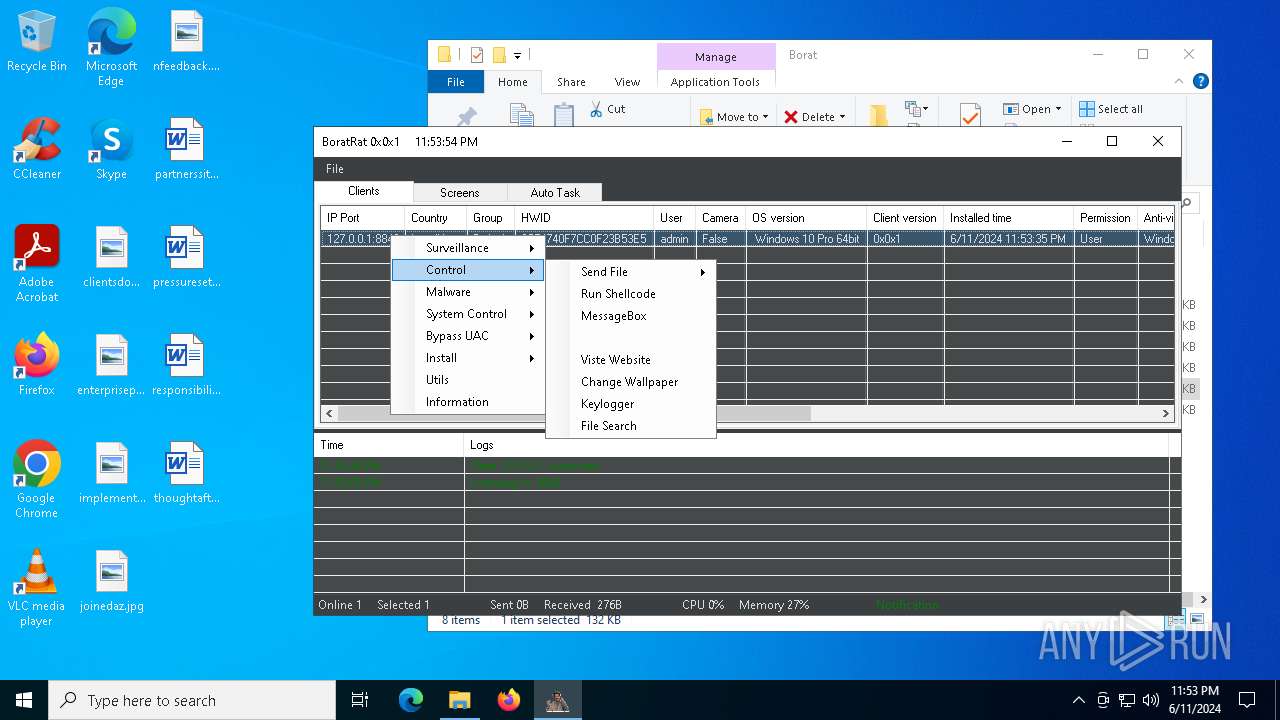
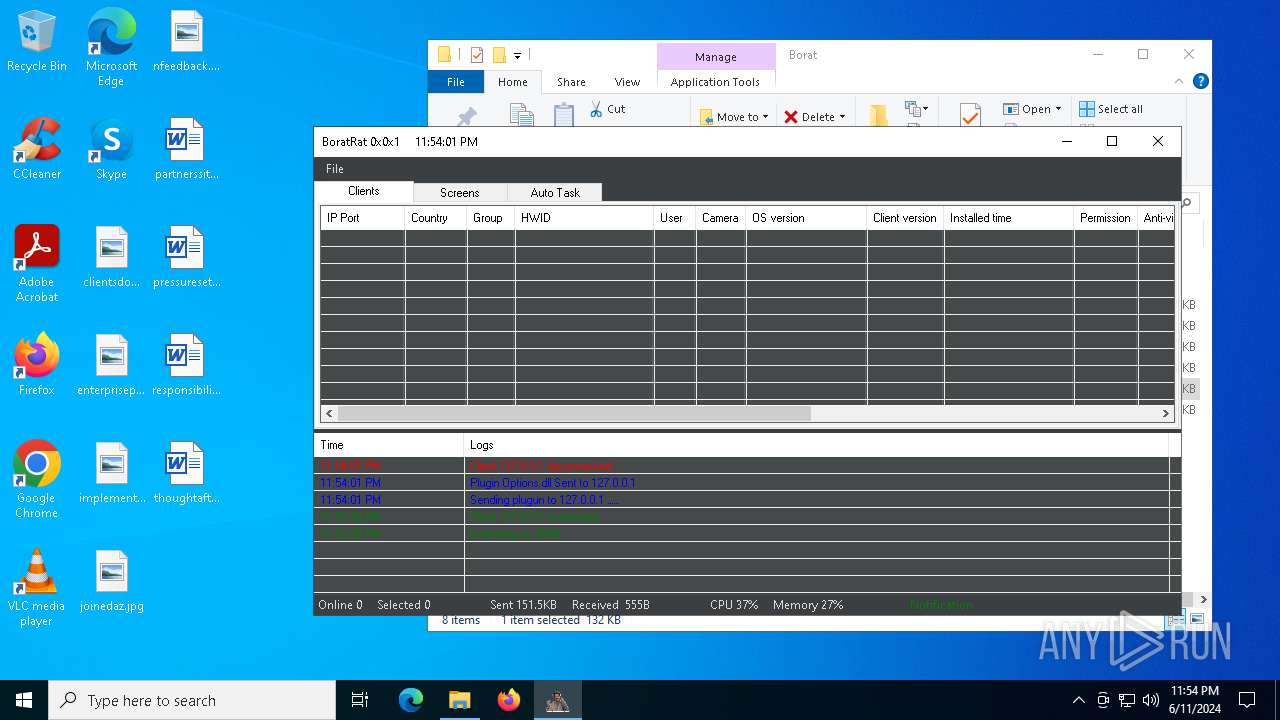
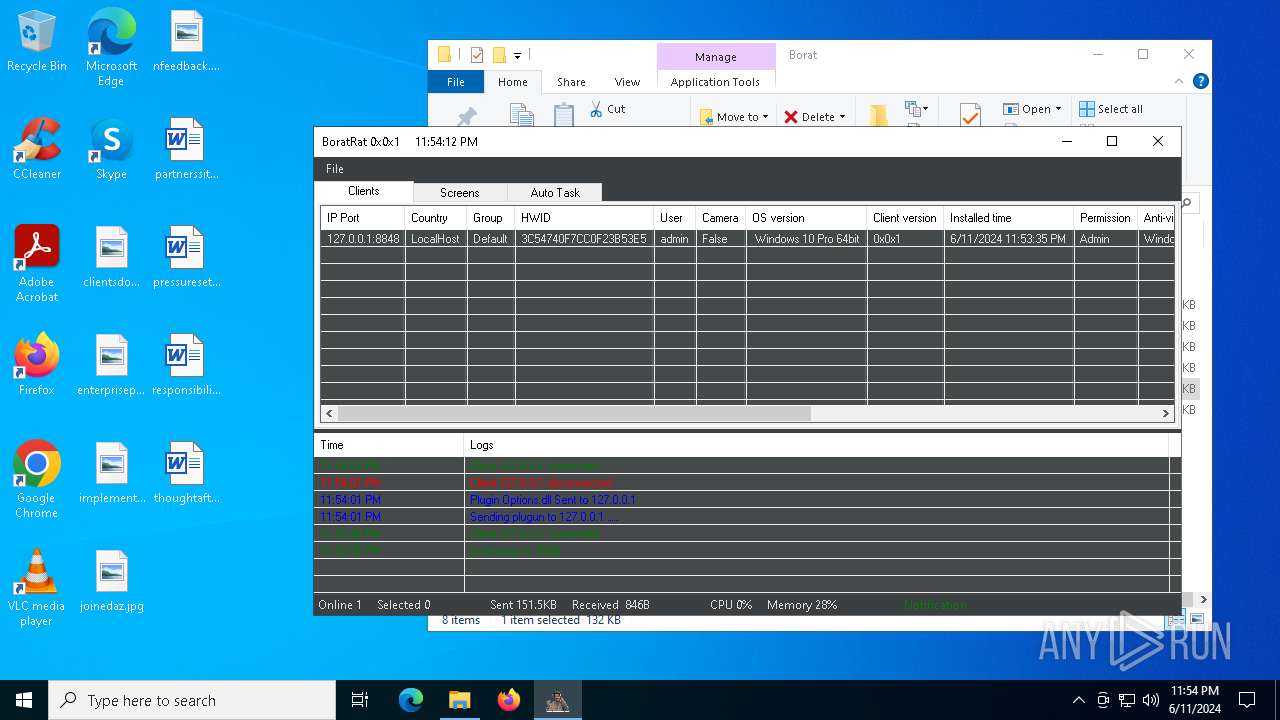
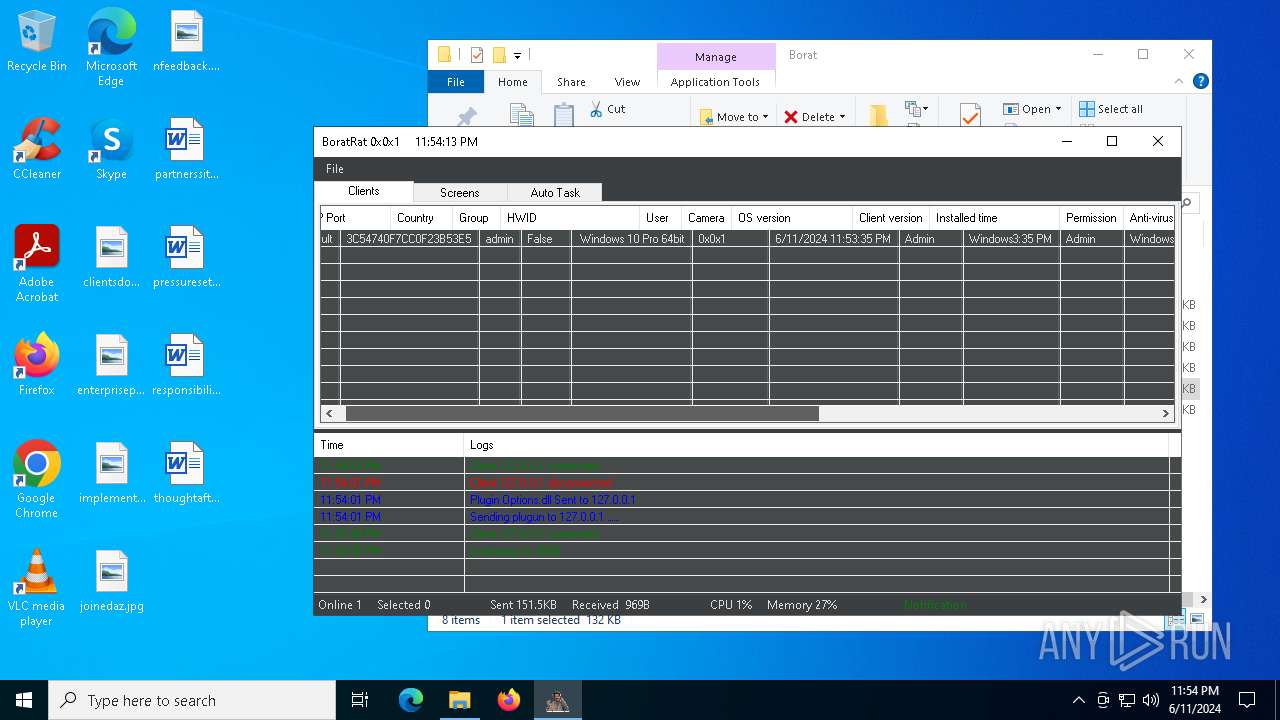
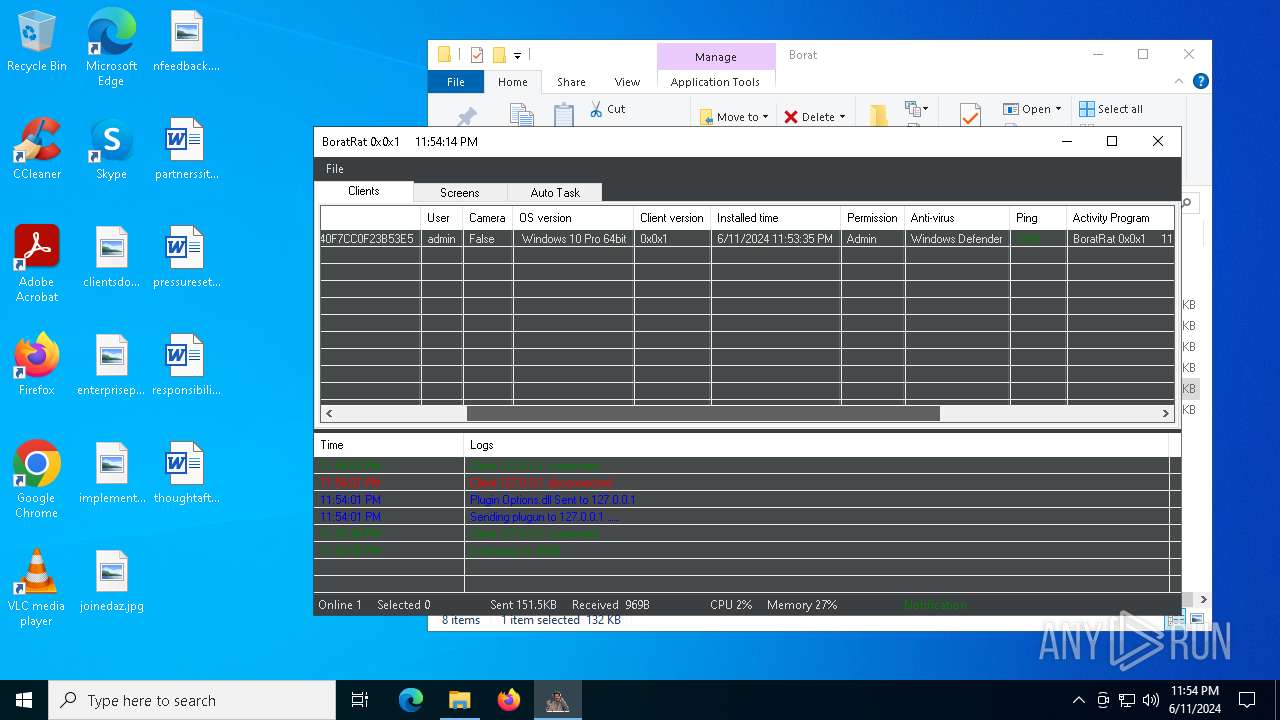
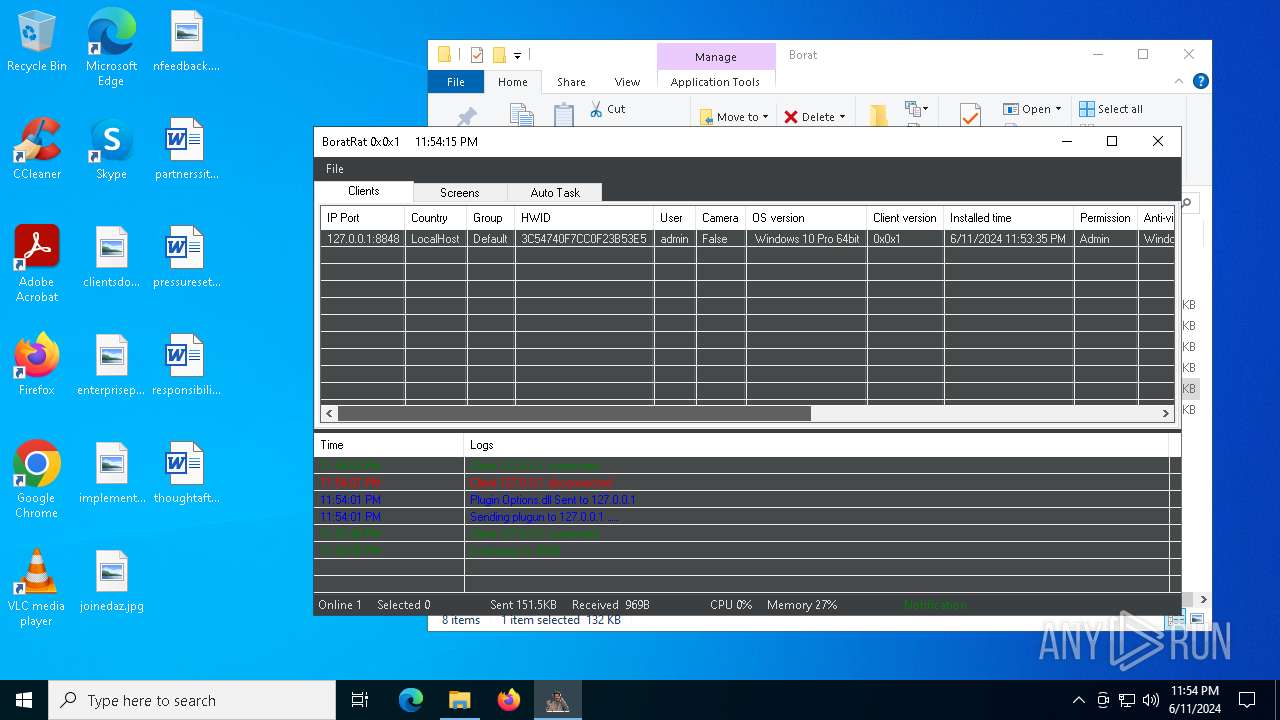
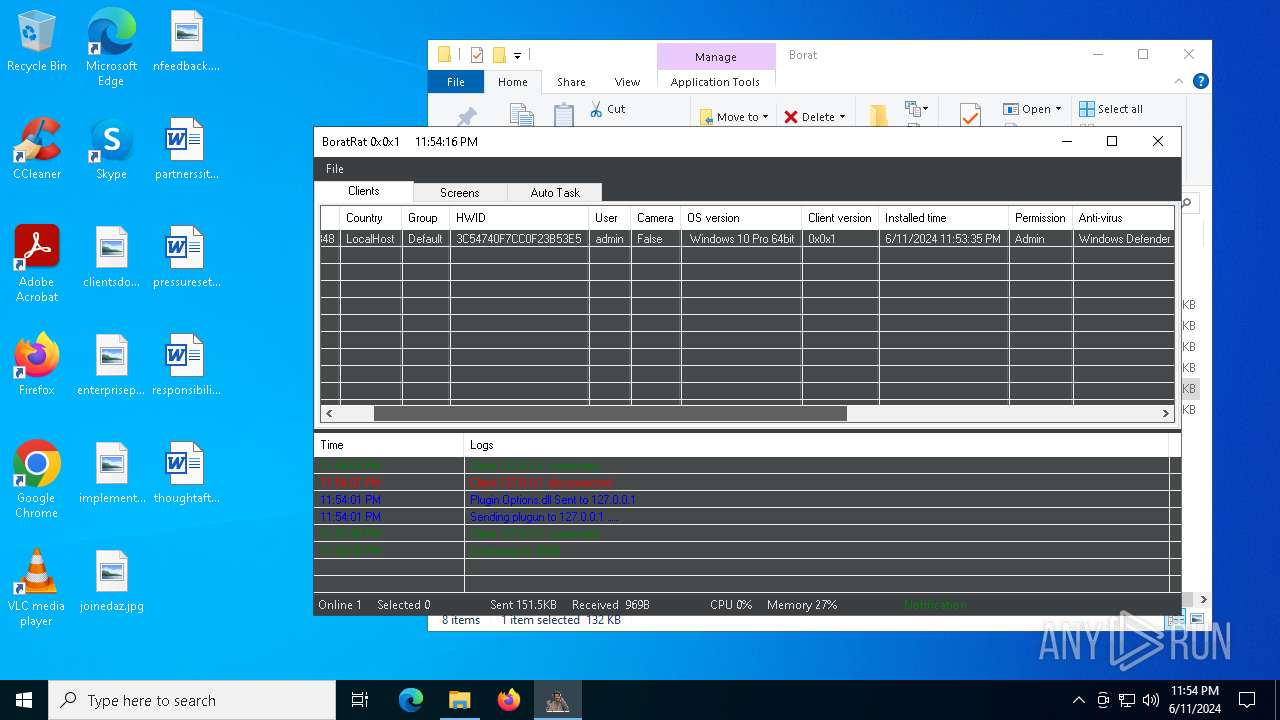
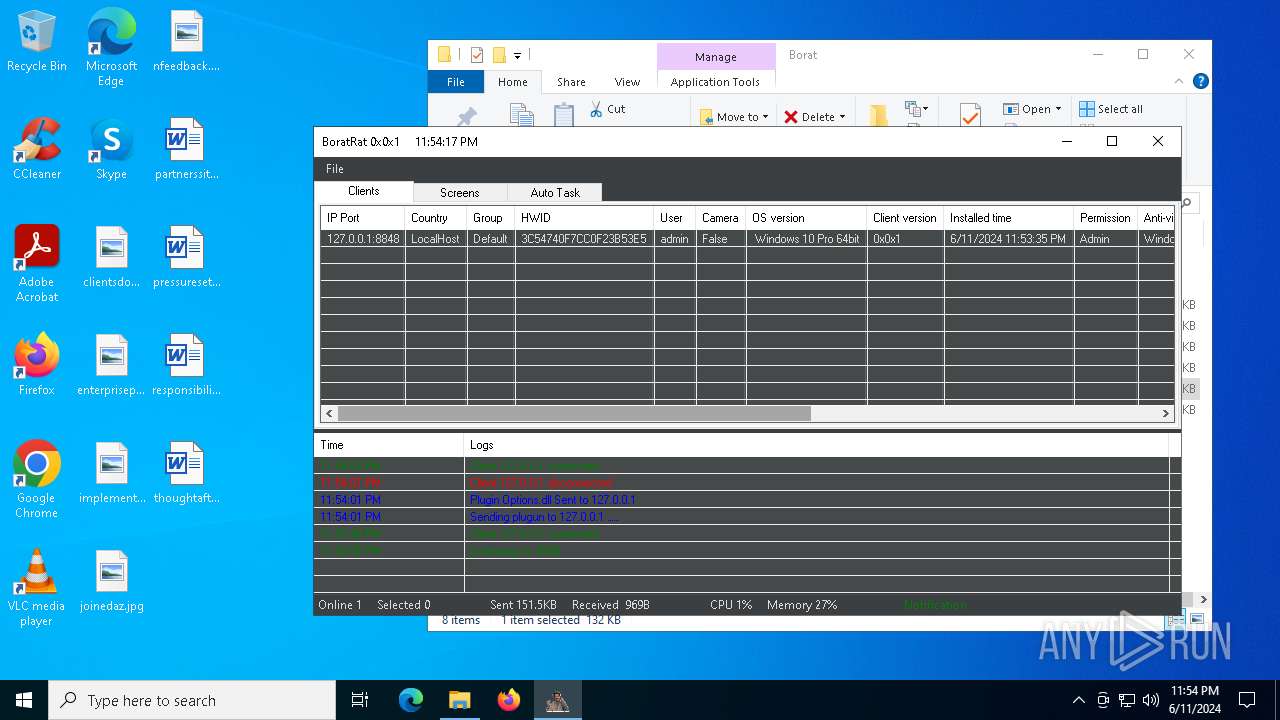
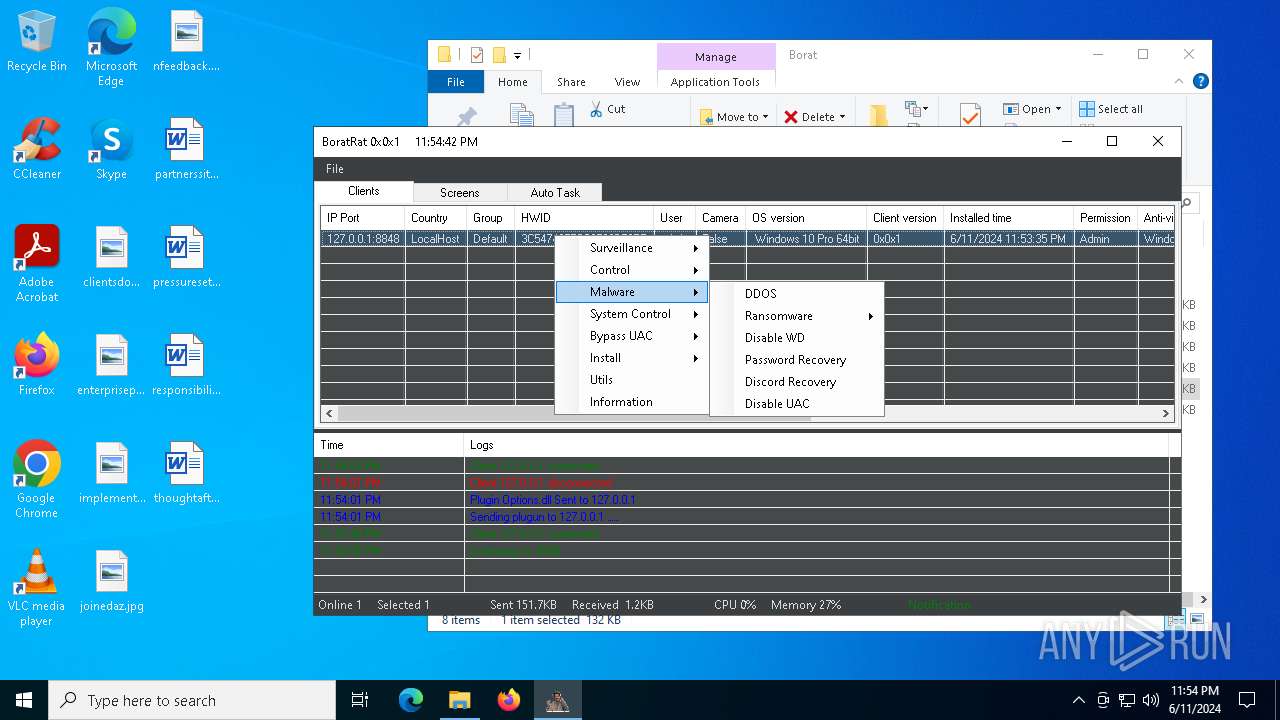
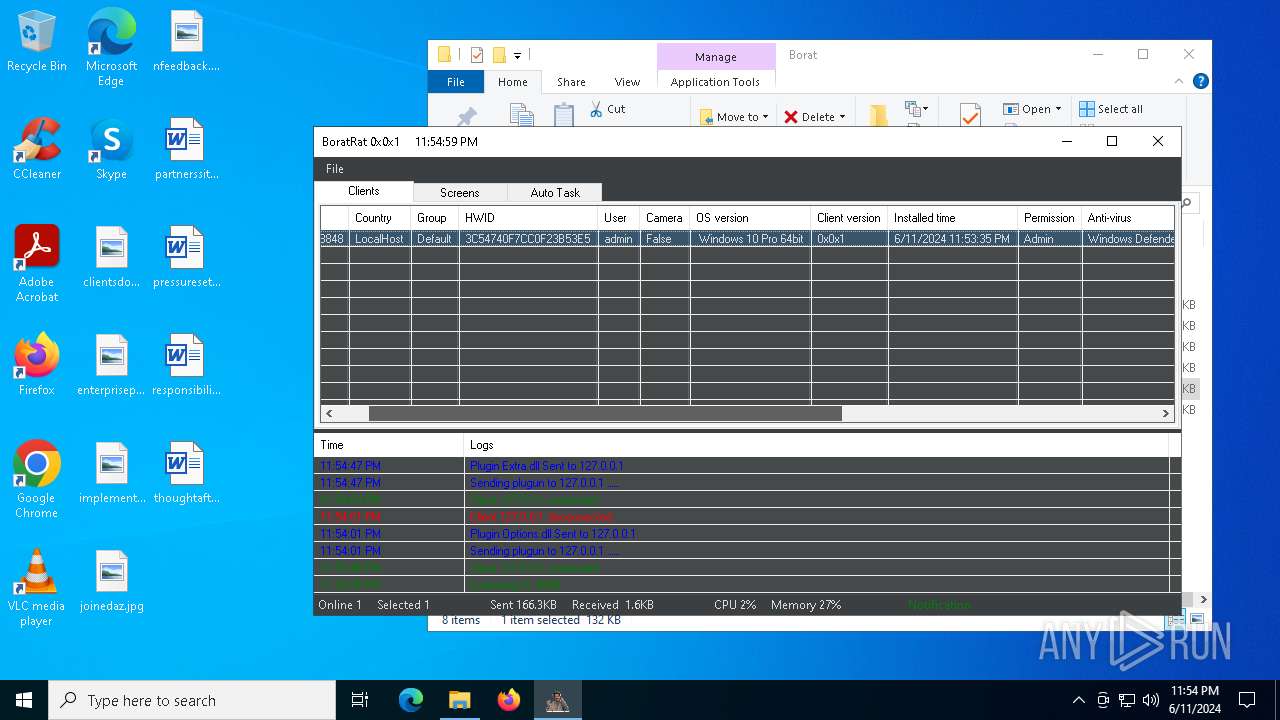
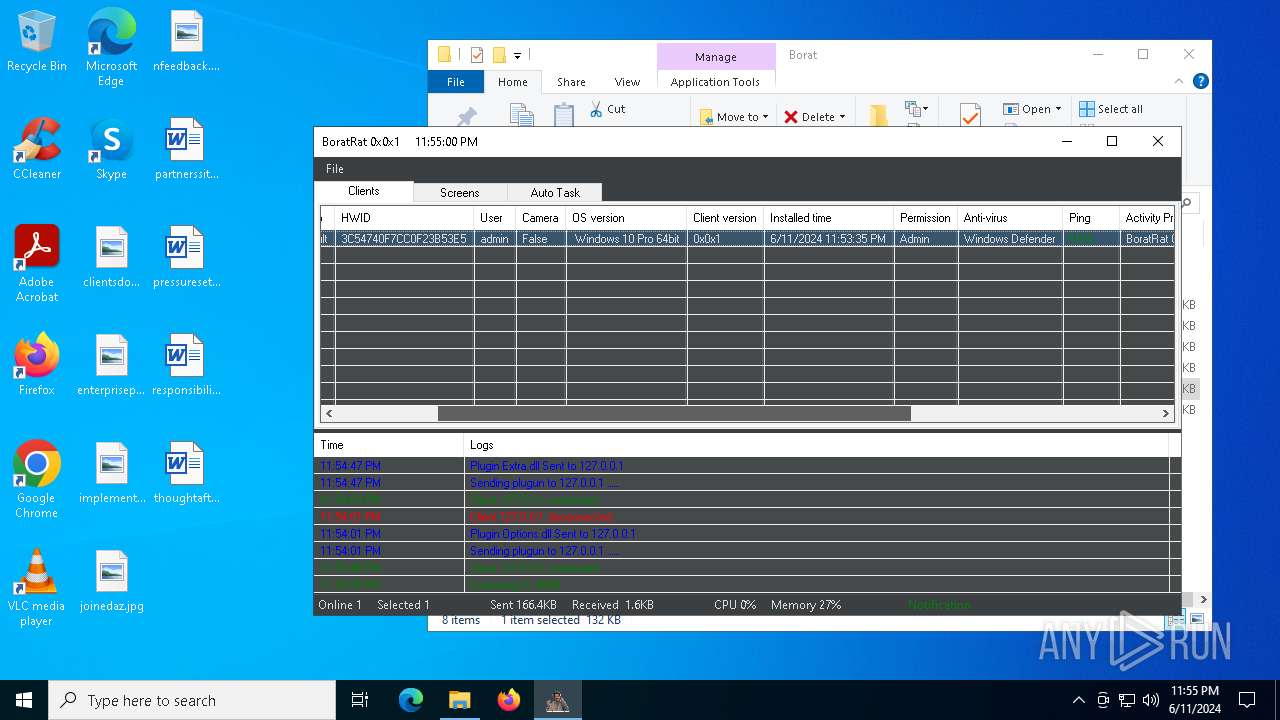
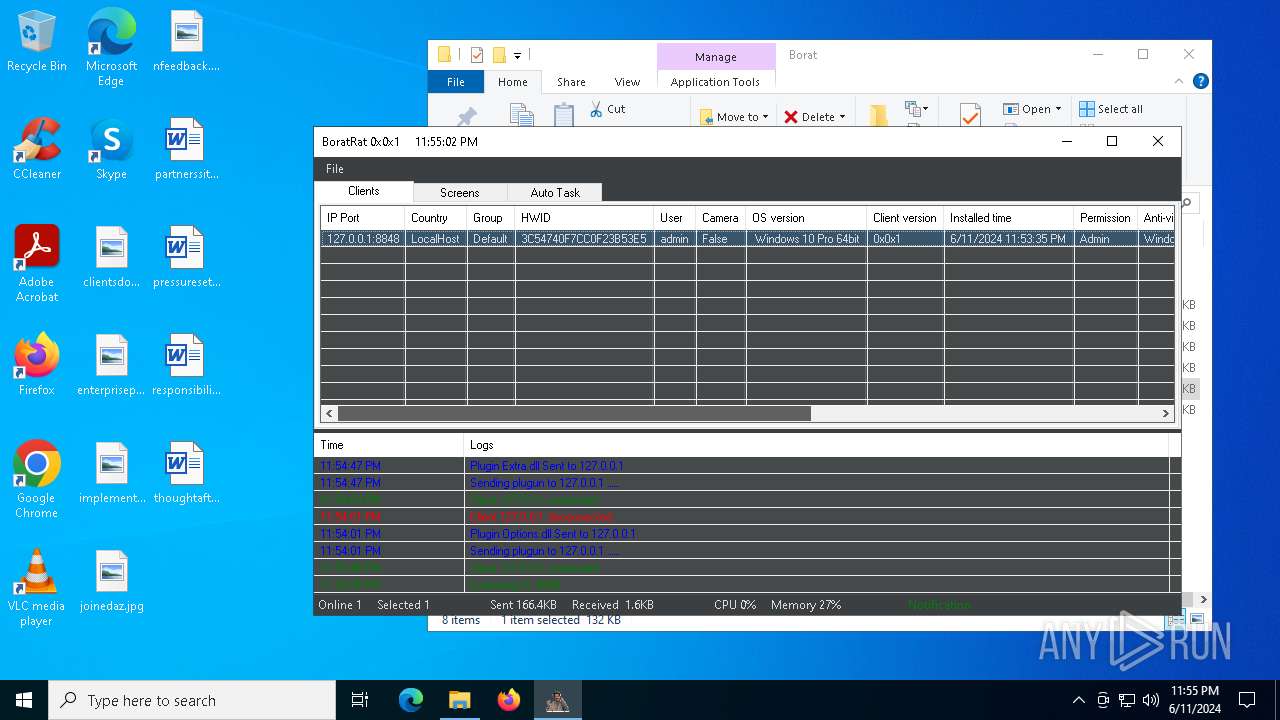
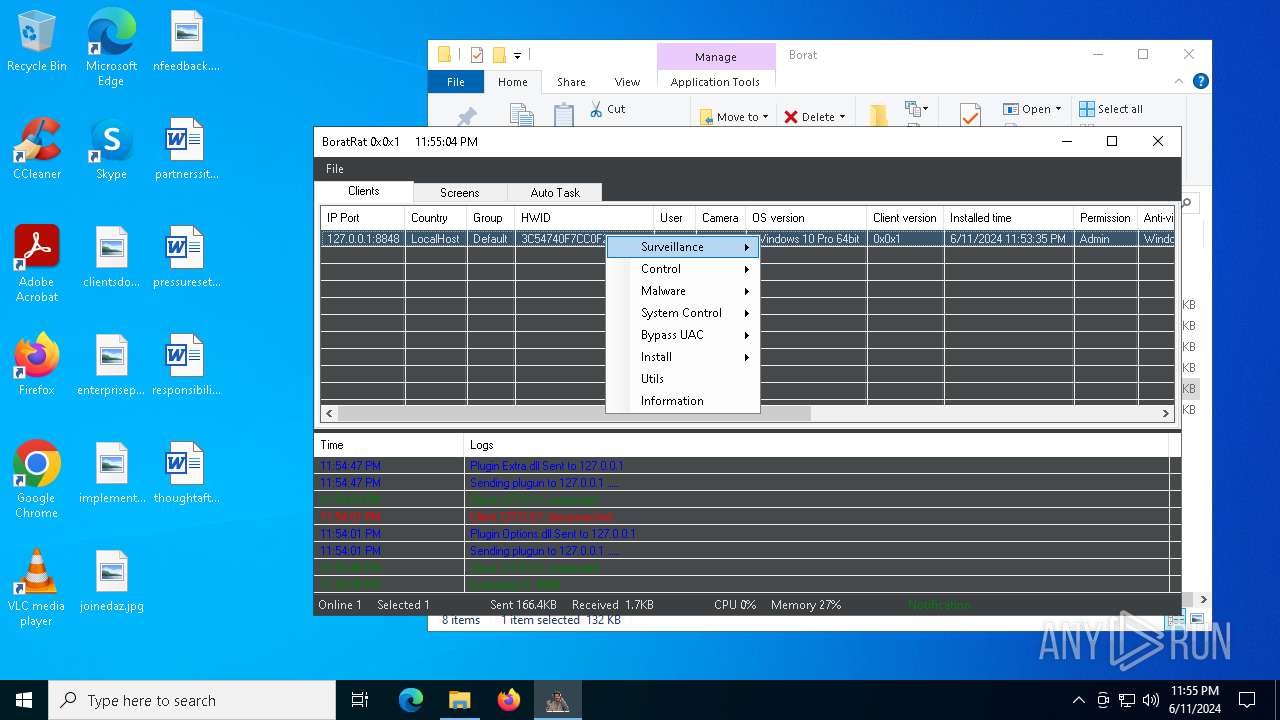
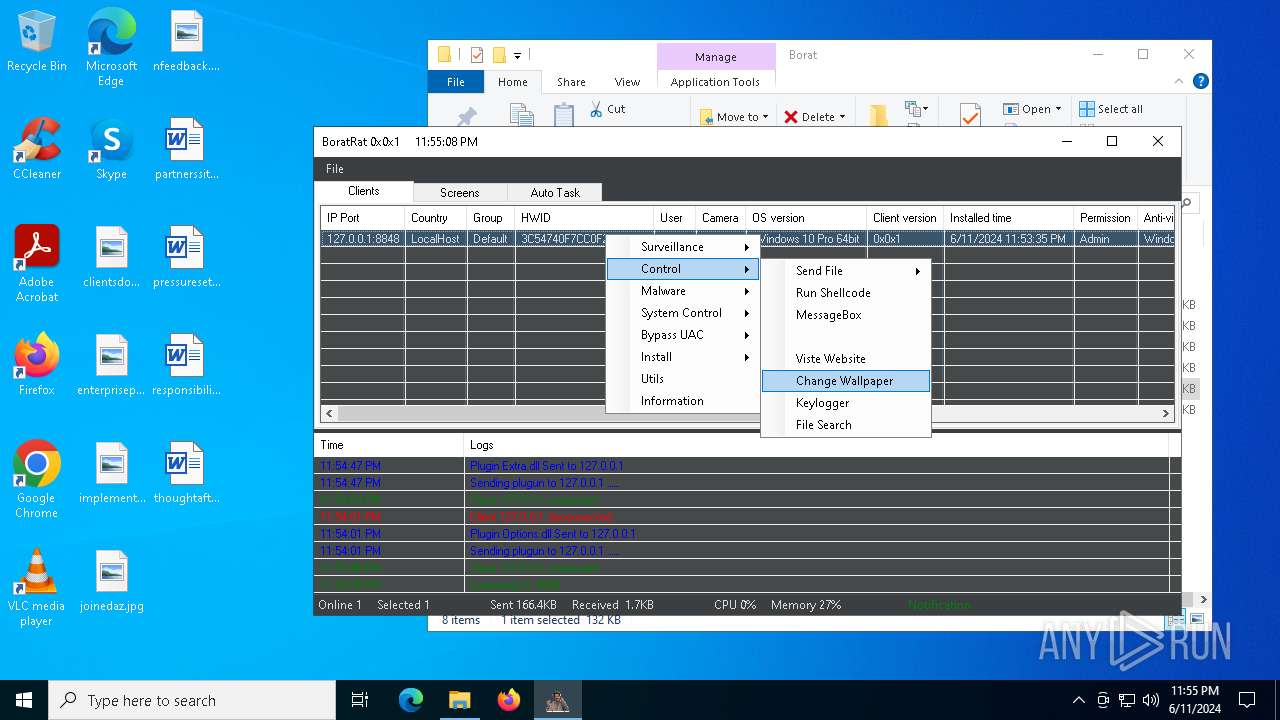
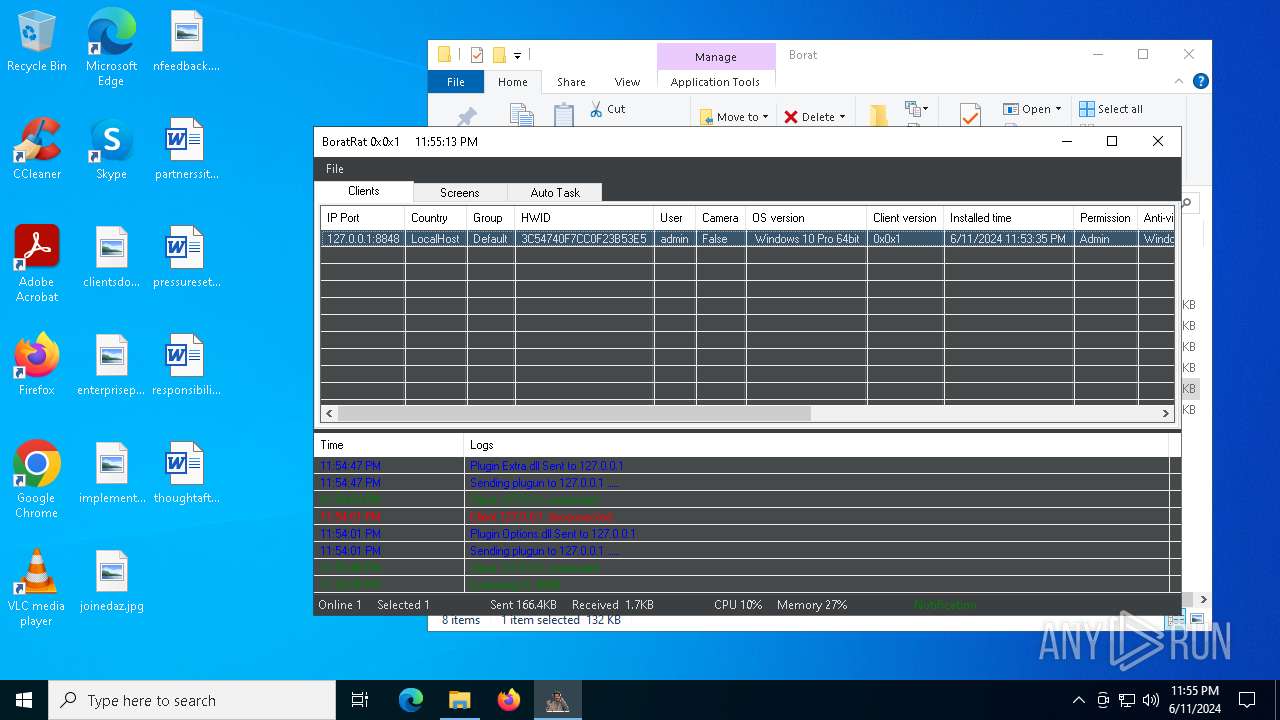
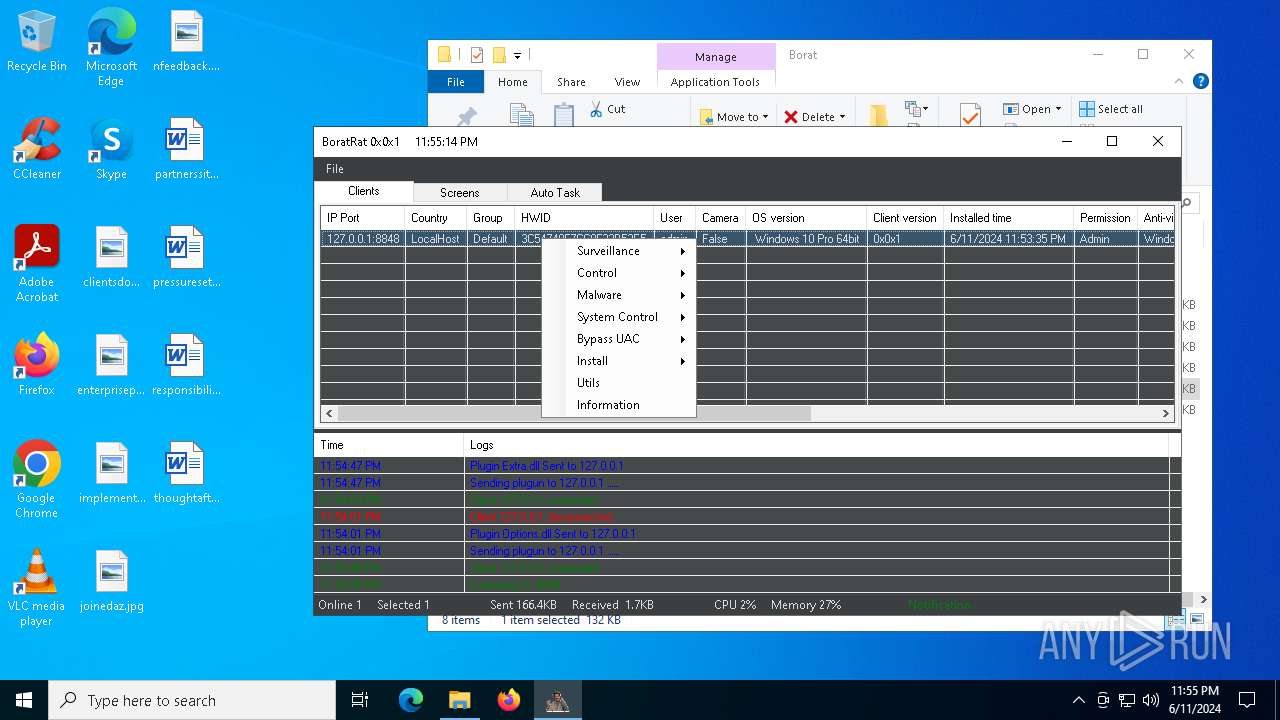
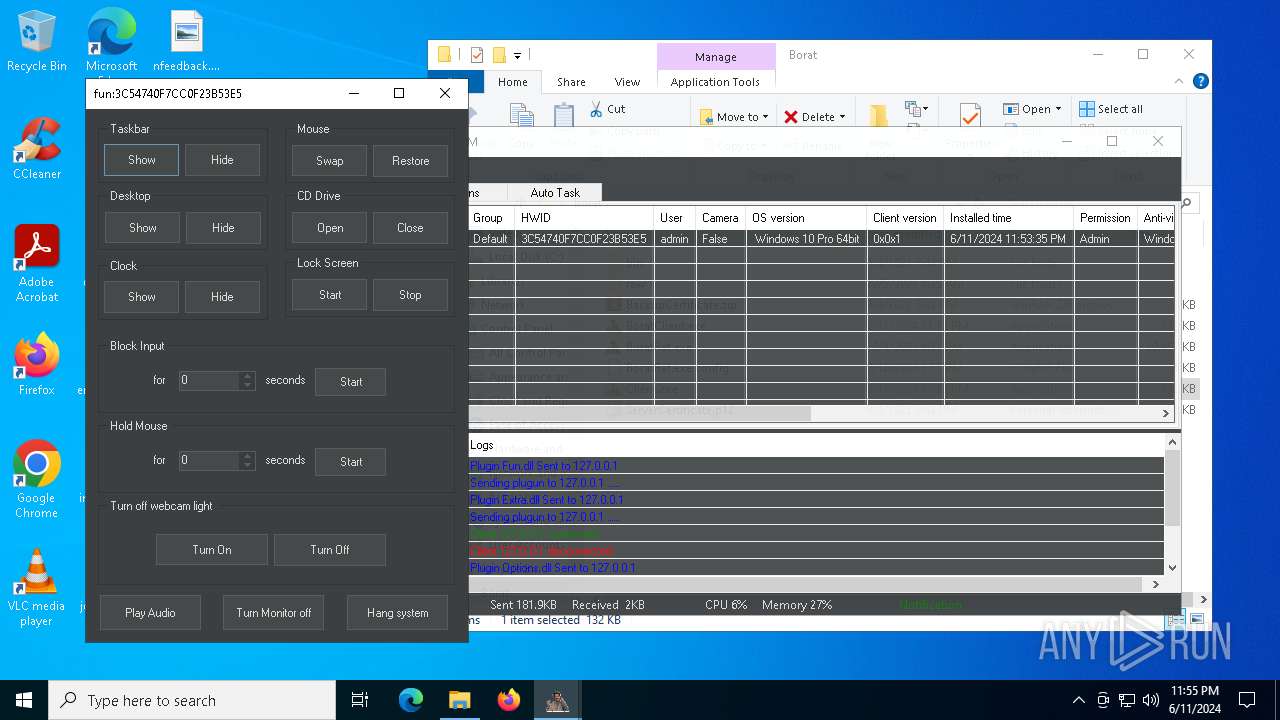
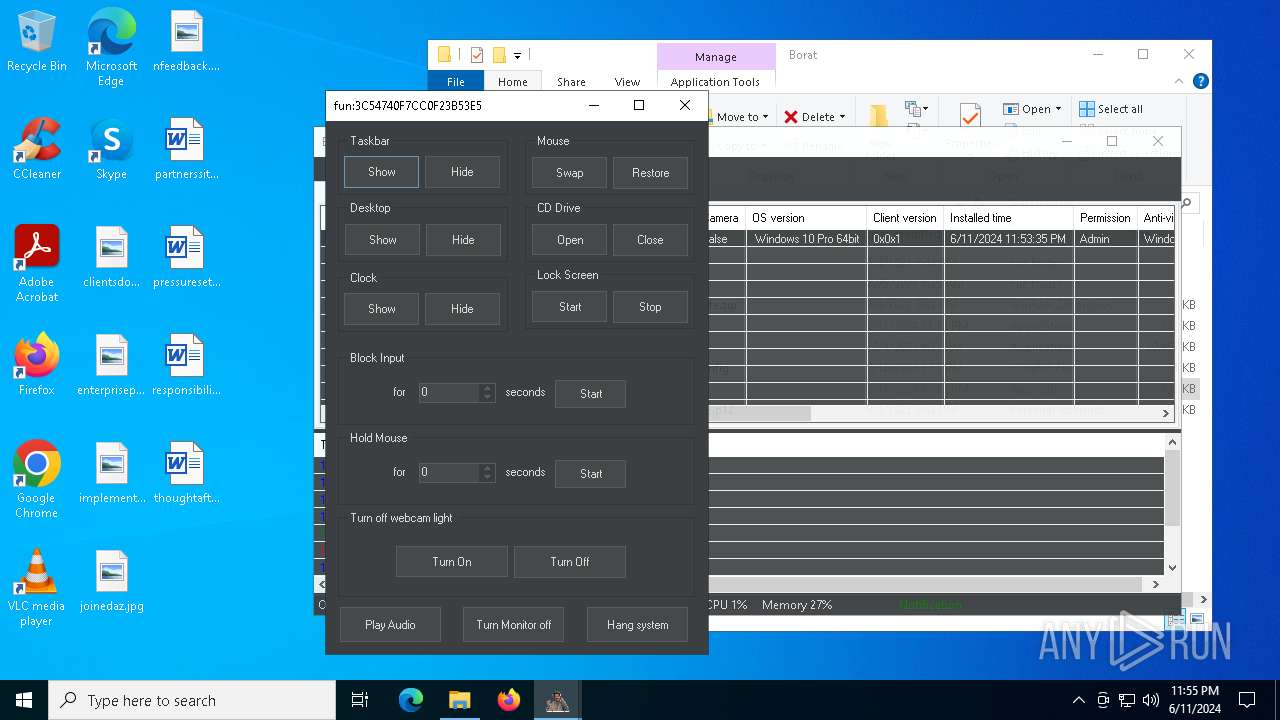
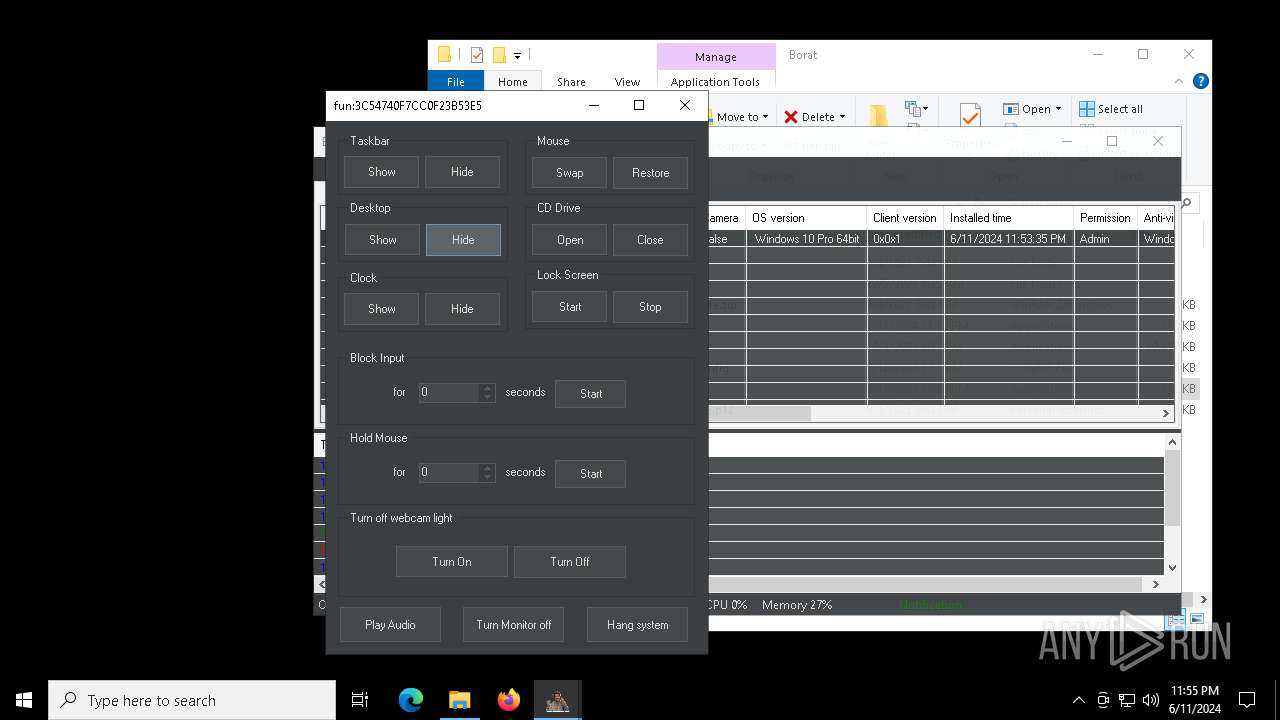
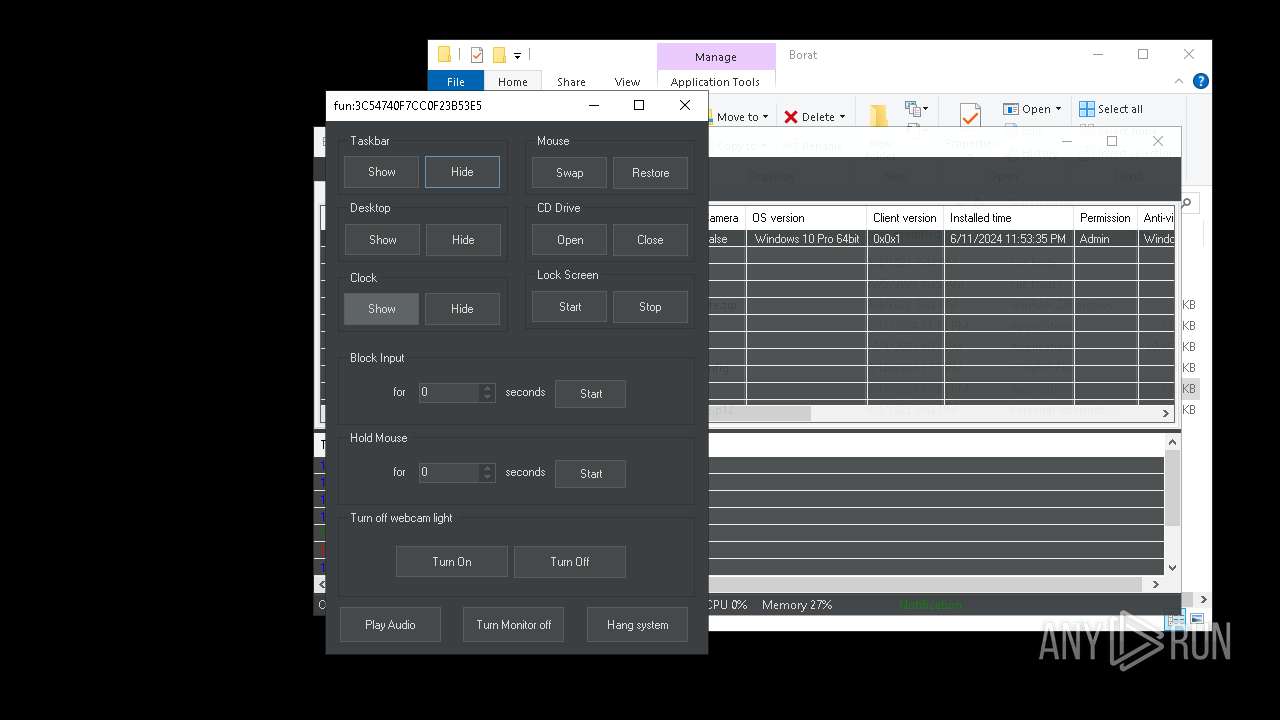
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | June 11, 2024, 23:51:19 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 43C20E4EE2DD87C70DD0ED082DC74431 |
| SHA1: | 71051DEE5D0480B8AA30A599A95D0AD928F7BB9E |
| SHA256: | B2F4CC95E54ACC818410D79072CCD44A4DBB21AFAD82C2A4608B7B52F1502867 |
| SSDEEP: | 98304:4mnI+WmnzFhcWMOo/5ucNWw7tq3o280CB6oWprH0Vtcpot+FfRT5apCeiFqQgijQ:BtYHMwzJ4hoHQLs |
MALICIOUS
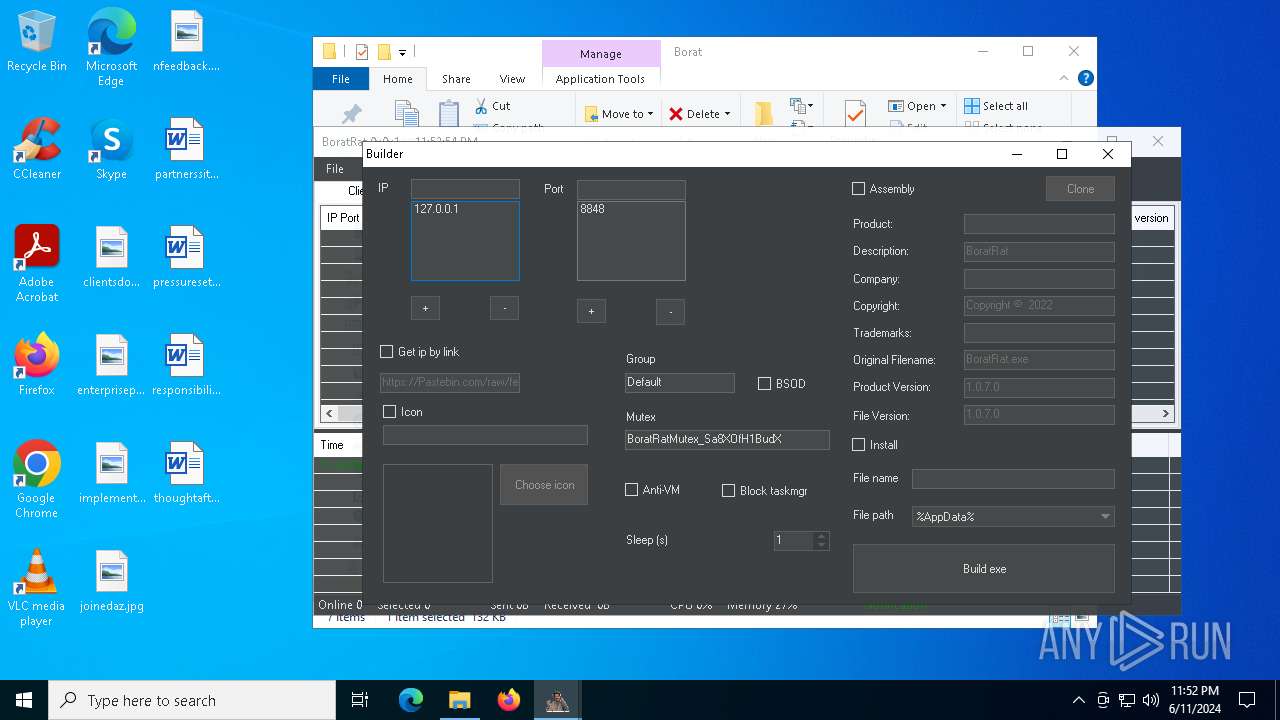
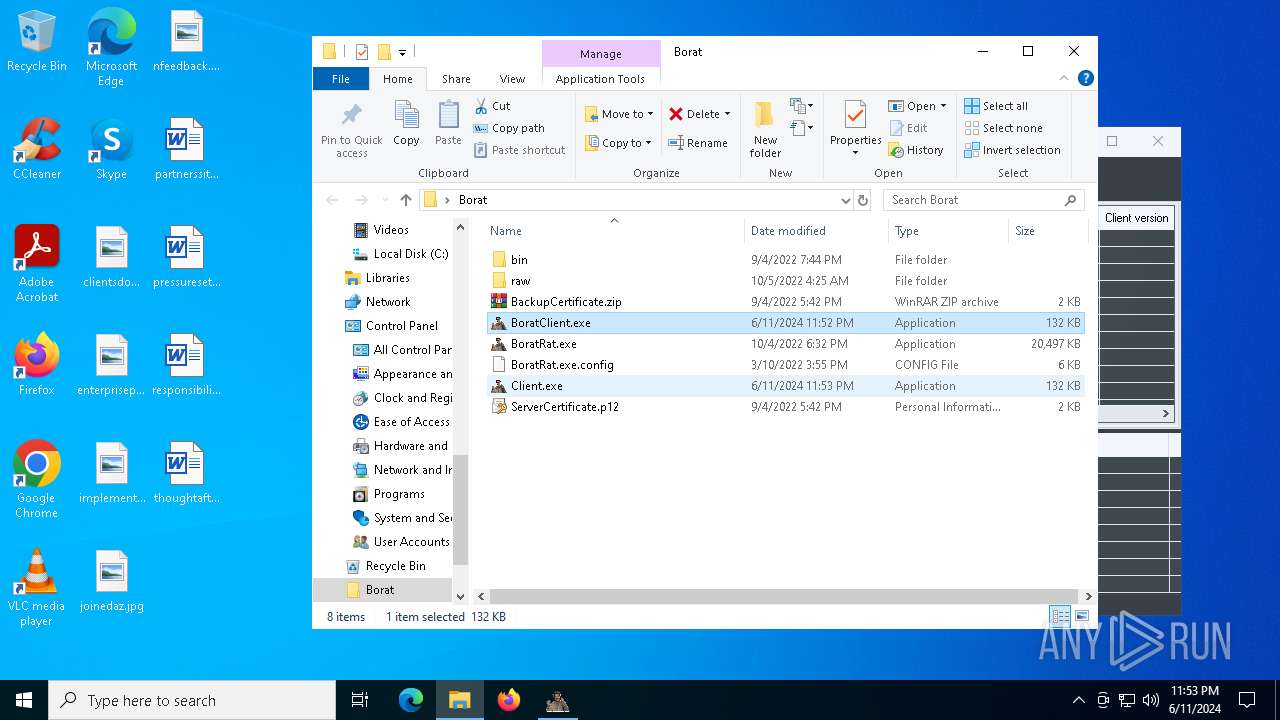
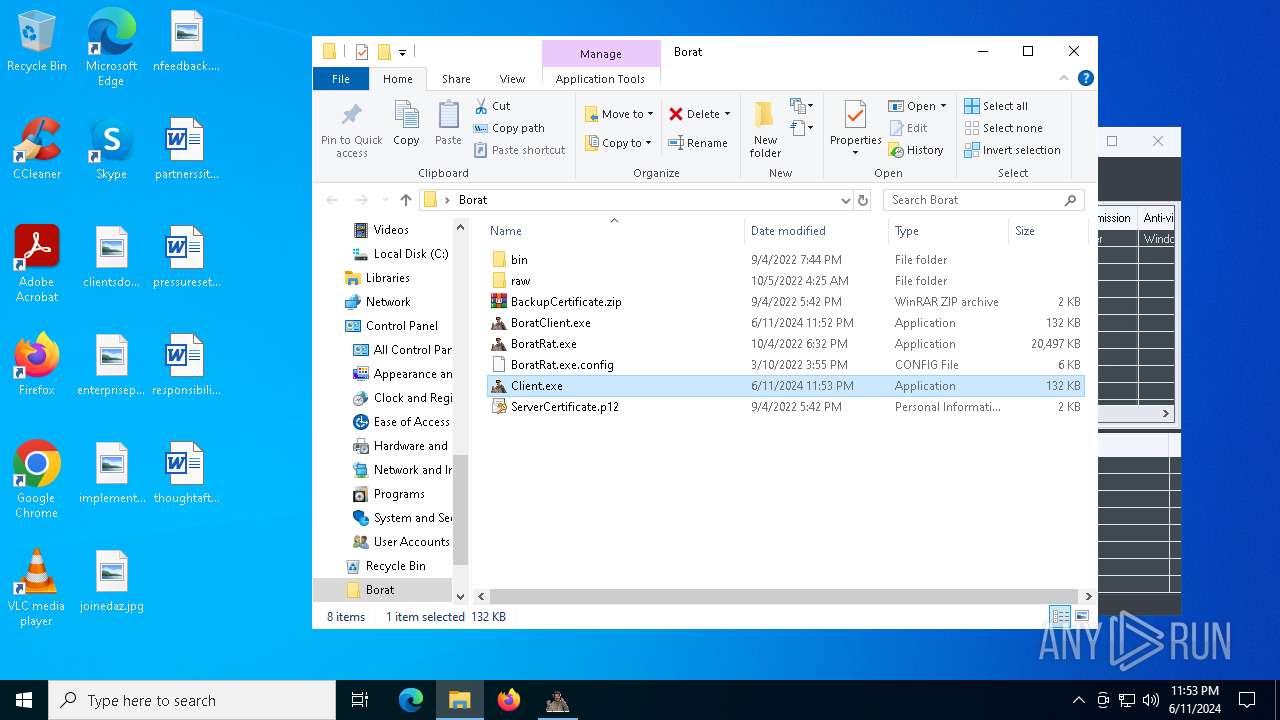
Drops the executable file immediately after the start
- WinRAR.exe (PID: 6492)
- BoratRat.exe (PID: 4700)
- Client.exe (PID: 5896)
Actions looks like stealing of personal data
- WinRAR.exe (PID: 6492)
- BoratRat.exe (PID: 4700)
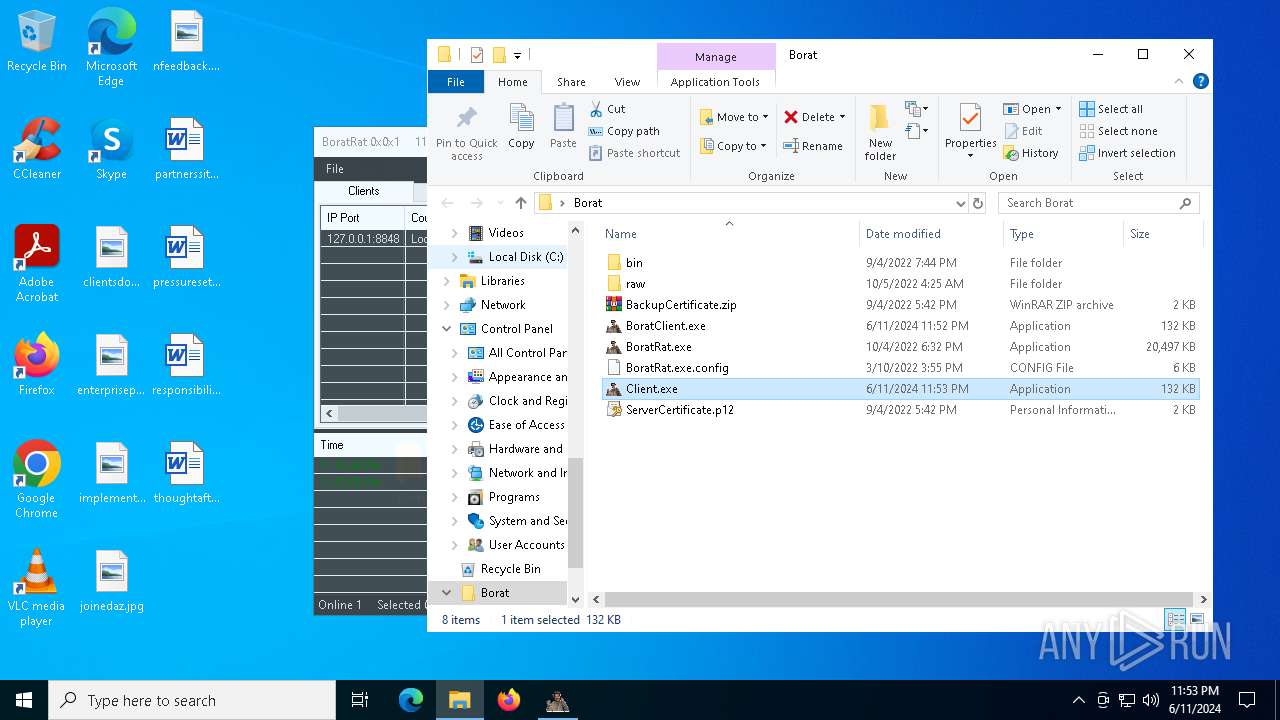
ASYNCRAT has been detected (YARA)
- BoratRat.exe (PID: 4700)
Changes the autorun value in the registry
- Client.exe (PID: 5896)
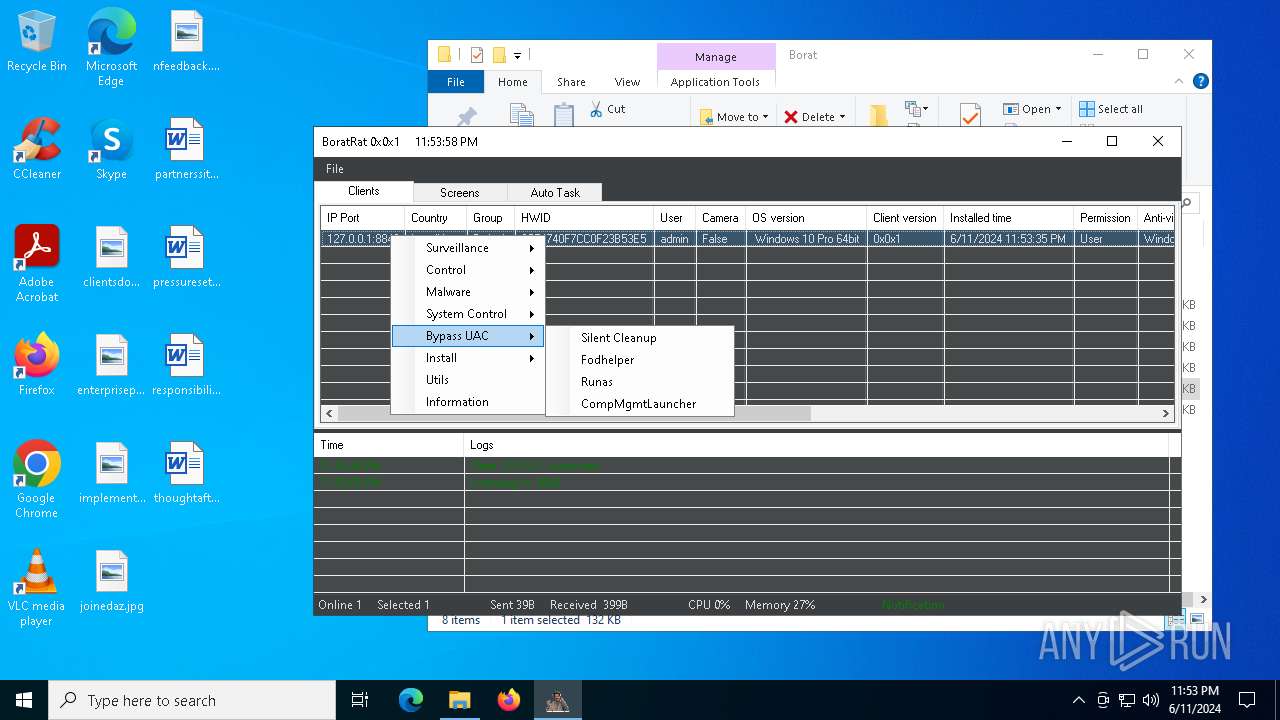
Bypass User Account Control (Modify registry)
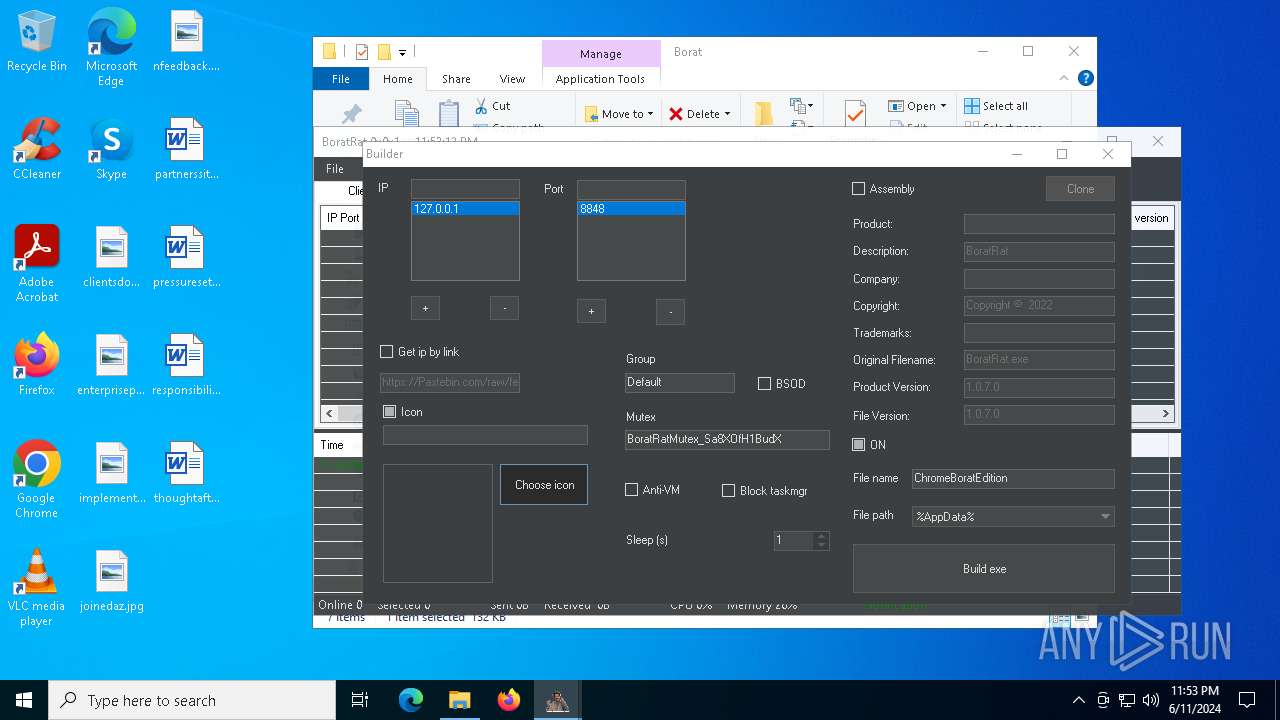
- ChromeBoratEdition.exe (PID: 4620)
Bypass User Account Control (fodhelper)
- fodhelper.exe (PID: 5404)
Antivirus name has been found in the command line (generic signature)
- cmd.exe (PID: 4060)
Starts NET.EXE for service management
- powershell.exe (PID: 6836)
SUSPICIOUS
The process creates files with name similar to system file names
- WinRAR.exe (PID: 6492)
The process checks if it is being run in the virtual environment
- BoratRat.exe (PID: 4700)
Reads security settings of Internet Explorer
- BoratRat.exe (PID: 4700)
- ChromeBoratEdition.exe (PID: 1180)
Creates file in the systems drive root
- BoratRat.exe (PID: 4700)
Executable content was dropped or overwritten
- BoratRat.exe (PID: 4700)
- Client.exe (PID: 5896)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 2764)
Starts CMD.EXE for commands execution
- Client.exe (PID: 5896)
- ChromeBoratEdition.exe (PID: 4620)
- powershell.exe (PID: 6836)
Executing commands from a ".bat" file
- Client.exe (PID: 5896)
The executable file from the user directory is run by the CMD process
- ChromeBoratEdition.exe (PID: 4620)
Changes default file association
- ChromeBoratEdition.exe (PID: 4620)
Reads the date of Windows installation
- ChromeBoratEdition.exe (PID: 1180)
Starts POWERSHELL.EXE for commands execution
- ChromeBoratEdition.exe (PID: 1180)
Base64-obfuscated command line is found
- ChromeBoratEdition.exe (PID: 1180)
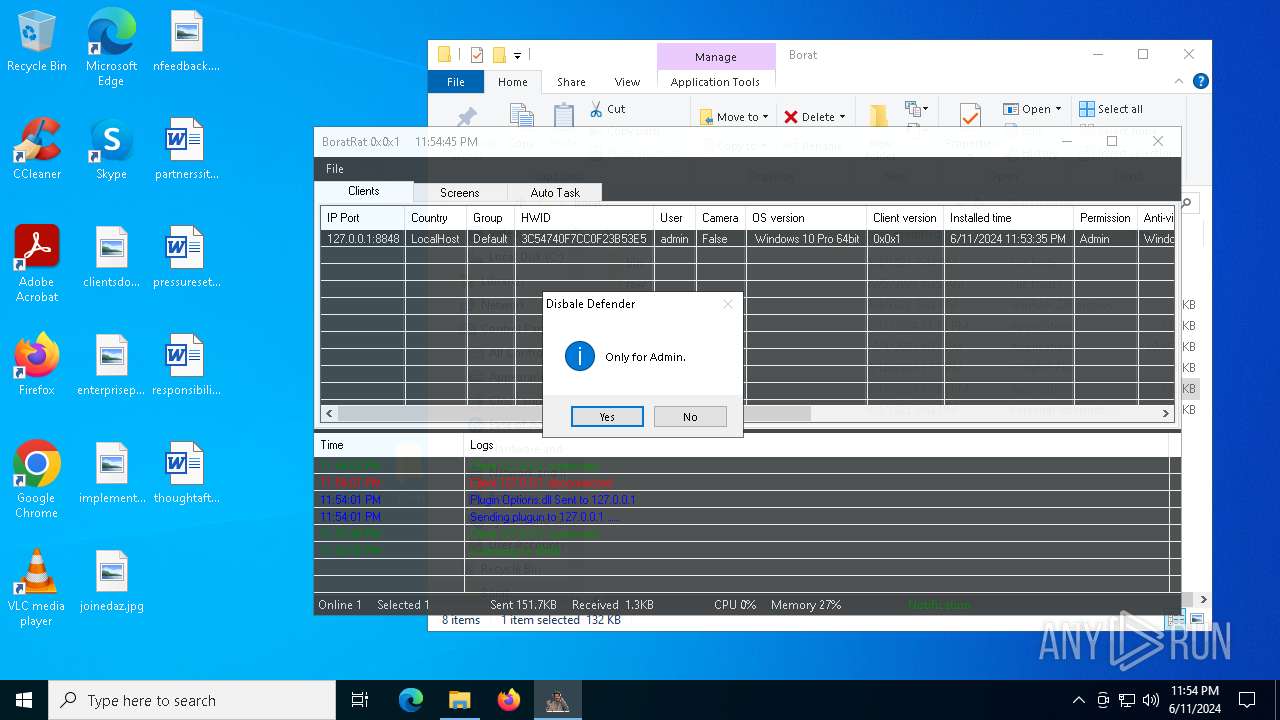
Found strings related to reading or modifying Windows Defender settings
- powershell.exe (PID: 6836)
Identifying current user with WHOAMI command
- powershell.exe (PID: 6836)
BASE64 encoded PowerShell command has been detected
- ChromeBoratEdition.exe (PID: 1180)
Uses sleep to delay execution (POWERSHELL)
- powershell.exe (PID: 6836)
Starts SC.EXE for service management
- powershell.exe (PID: 6836)
INFO
Checks supported languages
- BoratRat.exe (PID: 4700)
- BoratClient.exe (PID: 5076)
- Client.exe (PID: 5896)
- ChromeBoratEdition.exe (PID: 4620)
- ChromeBoratEdition.exe (PID: 1180)
Manual execution by a user
- BoratRat.exe (PID: 4700)
- BoratClient.exe (PID: 5076)
- Client.exe (PID: 5896)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6492)
Reads the computer name
- BoratRat.exe (PID: 4700)
- BoratClient.exe (PID: 5076)
- Client.exe (PID: 5896)
- ChromeBoratEdition.exe (PID: 4620)
- ChromeBoratEdition.exe (PID: 1180)
Reads the machine GUID from the registry
- BoratRat.exe (PID: 4700)
- Client.exe (PID: 5896)
- ChromeBoratEdition.exe (PID: 4620)
- ChromeBoratEdition.exe (PID: 1180)
Create files in a temporary directory
- BoratRat.exe (PID: 4700)
- Client.exe (PID: 5896)
Creates files or folders in the user directory
- BoratRat.exe (PID: 4700)
- Client.exe (PID: 5896)
Reads the software policy settings
- slui.exe (PID: 5960)
- ChromeBoratEdition.exe (PID: 4620)
- ChromeBoratEdition.exe (PID: 1180)
- slui.exe (PID: 4952)
Reads Environment values
- BoratRat.exe (PID: 4700)
- ChromeBoratEdition.exe (PID: 1180)
- ChromeBoratEdition.exe (PID: 4620)
Checks proxy server information
- slui.exe (PID: 4952)
Reads security settings of Internet Explorer
- fodhelper.exe (PID: 5404)
Reads Microsoft Office registry keys
- fodhelper.exe (PID: 5404)
Process checks computer location settings
- ChromeBoratEdition.exe (PID: 1180)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6836)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 6836)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
155
Monitored processes
26
Malicious processes
7
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1120 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1180 | "C:\Users\admin\AppData\Roaming\ChromeBoratEdition.exe" | C:\Users\admin\AppData\Roaming\ChromeBoratEdition.exe | — | fodhelper.exe | |||||||||||
User: admin Integrity Level: HIGH Version: 1.0.7.0 Modules
| |||||||||||||||
| 1256 | "C:\WINDOWS\system32\whoami.exe" /groups | C:\Windows\System32\whoami.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: whoami - displays logged on user information Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1708 | "C:\WINDOWS\system32\net1.exe" start TrustedInstaller | C:\Windows\System32\net1.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1788 | timeout 3 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2764 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\tmpE18E.tmp.bat"" | C:\Windows\System32\cmd.exe | — | Client.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3100 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3672 | SecurityHealthSystray | C:\Windows\System32\SecurityHealthSystray.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Security notification icon Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4020 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4060 | "C:\WINDOWS\system32\cmd.exe" /d/r SecurityHealthSystray & "%ProgramFiles%\Windows Defender\MSASCuiL.exe" | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
43 373
Read events
43 067
Write events
274
Delete events
32
Modification events
| (PID) Process: | (6492) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6492) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6492) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6492) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Borat.7z | |||
| (PID) Process: | (6492) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6492) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6492) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6492) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6492) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (6492) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\AppData\Local\Temp | |||
Executable files
33
Suspicious files
6
Text files
12
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6492 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6492.21656\Borat\bin\ip2region.db | — | |
MD5:— | SHA256:— | |||
| 6492 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6492.21656\Borat\bin\Discord.dll | executable | |
MD5:7EE673594BBB20F65448AAB05F1361D0 | SHA256:8FA7634B7DCA1A451CF8940429BE6AD2440821ED04D5D70B6E727E5968E0B5F6 | |||
| 6492 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6492.21656\Borat\BoratRat.exe | executable | |
MD5:65B694D69D327EFE28FCBCE125401E96 | SHA256:DE60ECBBFEF30C93FE8875EF69B358B20076D1F969FC3D21AB44D59DC9EF7CAB | |||
| 6492 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6492.21656\Borat\BackupCertificate.zip | compressed | |
MD5:9322F71EDD95192E1F4D275BFD6D87F3 | SHA256:F13033134C386E85A1E9009E863A3E6380438F83E3336B76A33E701A88F64946 | |||
| 6492 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6492.21656\Borat\bin\Extra.dll | executable | |
MD5:62C231BAFA469AB04F090FCB4475D360 | SHA256:6A4F32B0228092CE68E8448C6F4B74B4C654F40FB2D462C1D6BBD4B4EF09053D | |||
| 6492 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6492.21656\Borat\BoratRat.exe.config | xml | |
MD5:3E645CCCA1C44A00210924A3B0780955 | SHA256:F29E697EFD7C5ECB928C0310EA832325BF6518786C8E1585E1B85CDC8701602F | |||
| 6492 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6492.21656\Borat\bin\FileSearcher.dll | executable | |
MD5:0B7C33C5739903BA4F4B78C446773528 | SHA256:2D9625F41793F62BFE32C10B2D5E05668E321BCAF8B73414B3C31EF677B9BFF4 | |||
| 6492 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6492.21656\Borat\bin\Fun.dll | executable | |
MD5:499FC6AC30B3B342833C79523BE4A60C | SHA256:DCAC599B1BAB37E1A388AC469E6CC5DE1F35EB02BEAA6778F07A1C090CE3EA04 | |||
| 6492 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6492.21656\Borat\bin\Keylogger.exe | executable | |
MD5:A45679BDCF30F068032BD37A194FA175 | SHA256:16BEB1AE2DE2974CCC2371D9F619F492295E590ABB65D3102E362C8EC27F2BBB | |||
| 6492 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6492.21656\Borat\bin\Information.dll | executable | |
MD5:87651B12453131DAFD3E91F60D8AEF5A | SHA256:A15D72D990686D06D89D7E11DF2B16BCD5719A40298C19D046FA22C40D56AF44 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
60
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2384 | svchost.exe | GET | 200 | 23.45.13.35:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
2384 | svchost.exe | GET | 200 | 2.17.0.227:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
3904 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
4680 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | — | — | unknown |
6792 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | unknown |
2908 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | unknown |
6436 | SIHClient.exe | GET | 200 | 2.17.0.227:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
6436 | SIHClient.exe | GET | 200 | 2.17.0.227:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2384 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5076 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5140 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4364 | svchost.exe | 239.255.255.250:1900 | — | — | — | unknown |
2384 | svchost.exe | 23.45.13.35:80 | crl.microsoft.com | Akamai International B.V. | US | unknown |
4680 | SearchApp.exe | 23.194.131.160:443 | www.bing.com | Akamai International B.V. | US | unknown |
4680 | SearchApp.exe | 23.194.131.145:443 | www.bing.com | Akamai International B.V. | US | unknown |
2384 | svchost.exe | 2.17.0.227:80 | www.microsoft.com | AKAMAI-AS | DK | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
r.bing.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
arc.msn.com |
| whitelisted |