| File name: | Sample1.zip |
| Full analysis: | https://app.any.run/tasks/ca32f04c-9d6b-4927-9056-2e836b0a7c1b |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | July 18, 2019, 14:39:20 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
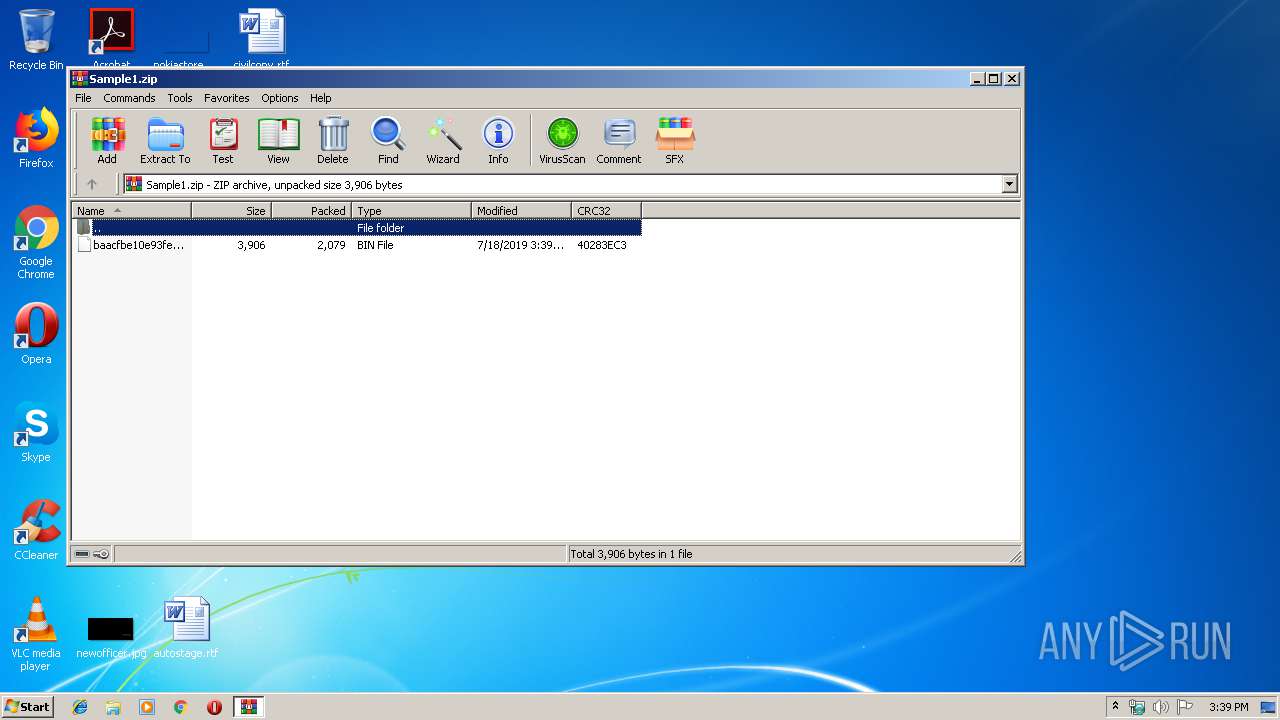
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 249A3CA445648A31AFD863DBB77268B2 |
| SHA1: | 7067ACD776956883CB6EBAE7613131DB001B99BA |
| SHA256: | B2E23269DCA9A5CF211A2B295E18BDD89ACAAF85776A1689DEE89164E92A5720 |
| SSDEEP: | 48:Zv3UIT3O5s9fzkwMrfBNmtsgfxwj6ggHaSCSGN4rWDau1aURvAPF:JBT3K6DmBNSsgejXg6pJaUBAPF |
MALICIOUS
Equation Editor starts application (CVE-2017-11882)
- EQNEDT32.EXE (PID: 2904)
Application was dropped or rewritten from another process
- rectorfile.exe (PID: 3420)
- rectorfile.exe (PID: 3524)
- rector.exe (PID: 3492)
- rector.exe (PID: 3988)
- rector.exe (PID: 2928)
- rector.exe (PID: 2936)
AGENTTESLA was detected
- rectorfile.exe (PID: 3420)
- rector.exe (PID: 3988)
- rector.exe (PID: 2928)
Actions looks like stealing of personal data
- rectorfile.exe (PID: 3420)
- rector.exe (PID: 3988)
- rector.exe (PID: 2928)
Downloads executable files from the Internet
- opera.exe (PID: 3940)
SUSPICIOUS
Application launched itself
- rectorfile.exe (PID: 3524)
- rector.exe (PID: 3492)
- rector.exe (PID: 2936)
Creates files in the user directory
- EQNEDT32.EXE (PID: 2904)
- rectorfile.exe (PID: 3420)
Executed via COM
- EQNEDT32.EXE (PID: 2904)
Executable content was dropped or overwritten
- EQNEDT32.EXE (PID: 2904)
- opera.exe (PID: 3940)
Reads the cookies of Google Chrome
- rectorfile.exe (PID: 3420)
Checks for external IP
- rectorfile.exe (PID: 3420)
- rector.exe (PID: 3988)
- rector.exe (PID: 2928)
Reads the cookies of Mozilla Firefox
- rectorfile.exe (PID: 3420)
Reads Internet Cache Settings
- rector.exe (PID: 3988)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 1952)
Creates files in the user directory
- WINWORD.EXE (PID: 1952)
- opera.exe (PID: 3940)
Manual execution by user
- WINWORD.EXE (PID: 1952)
- opera.exe (PID: 3940)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 788 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:07:18 14:39:03 |
| ZipCRC: | 0x40283ec3 |
| ZipCompressedSize: | 2079 |
| ZipUncompressedSize: | 3906 |
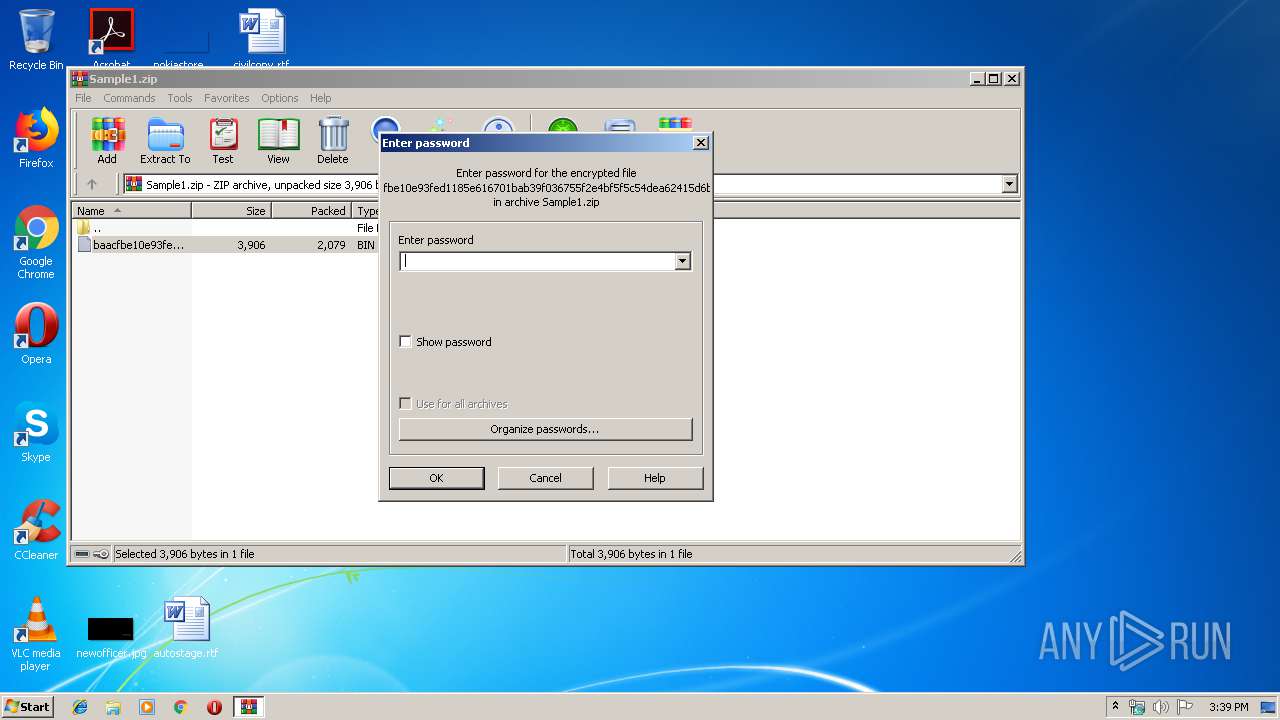
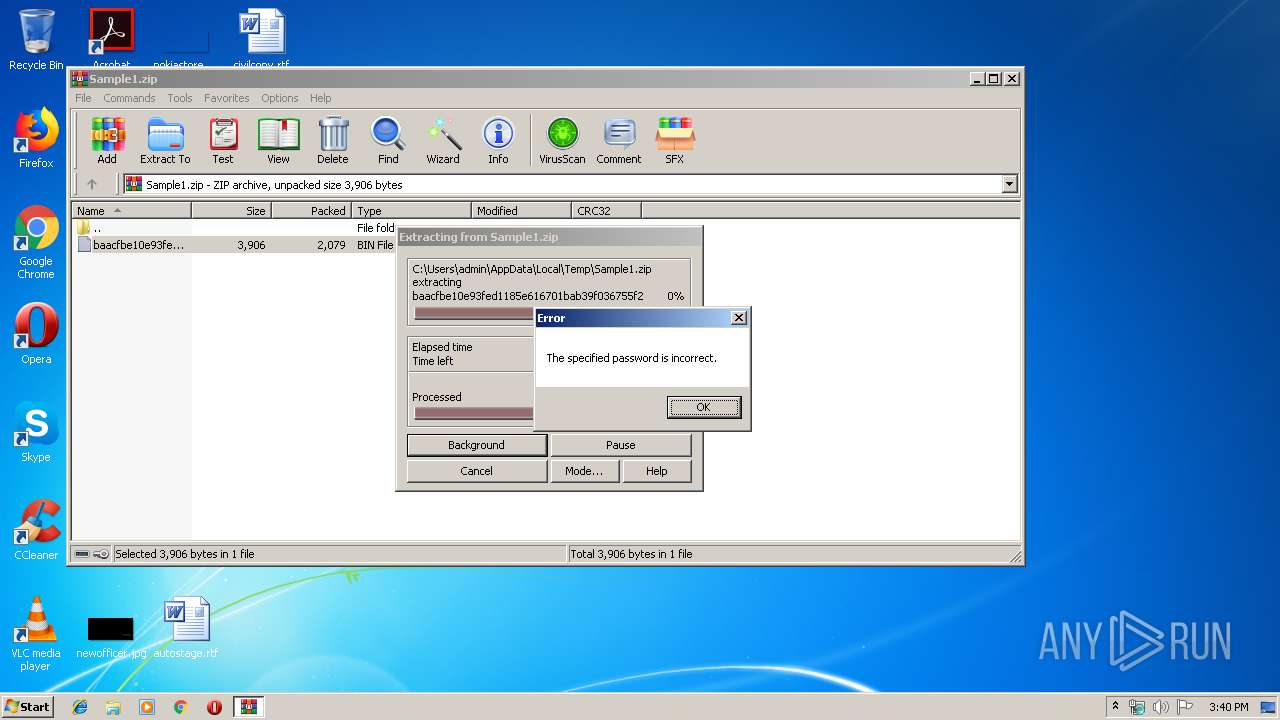
| ZipFileName: | baacfbe10e93fed1185e616701bab39f036755f2e4bf5f5c54dea62415d6b156.bin |
Total processes
45
Monitored processes
10
Malicious processes
8
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1952 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\ayyy.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2848 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Sample1.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2904 | "C:\Program Files\Common Files\Microsoft Shared\EQUATION\EQNEDT32.EXE" -Embedding | C:\Program Files\Common Files\Microsoft Shared\EQUATION\EQNEDT32.EXE | svchost.exe | ||||||||||||
User: admin Company: Design Science, Inc. Integrity Level: MEDIUM Description: Microsoft Equation Editor Exit code: 0 Version: 00110900 Modules
| |||||||||||||||
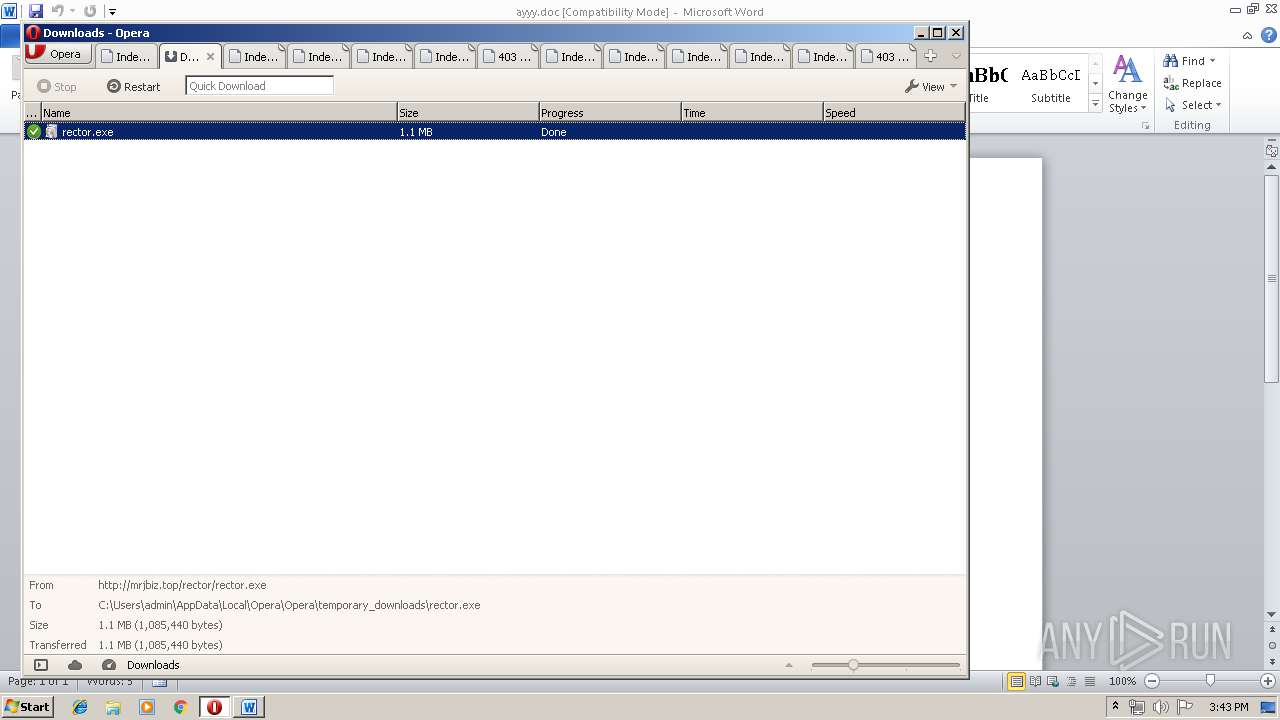
| 2928 | "C:\Users\admin\AppData\Local\Opera\Opera\temporary_downloads\rector.exe" | C:\Users\admin\AppData\Local\Opera\Opera\temporary_downloads\rector.exe | rector.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2936 | "C:\Users\admin\AppData\Local\Opera\Opera\temporary_downloads\rector.exe" | C:\Users\admin\AppData\Local\Opera\Opera\temporary_downloads\rector.exe | — | opera.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3420 | "C:\Users\admin\AppData\Roaming\rectorfile.exe" | C:\Users\admin\AppData\Roaming\rectorfile.exe | rectorfile.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3492 | "C:\Users\admin\AppData\Local\Opera\Opera\temporary_downloads\rector.exe" | C:\Users\admin\AppData\Local\Opera\Opera\temporary_downloads\rector.exe | — | opera.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3524 | "C:\Users\admin\AppData\Roaming\rectorfile.exe" | C:\Users\admin\AppData\Roaming\rectorfile.exe | — | EQNEDT32.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3940 | "C:\Program Files\Opera\opera.exe" | C:\Program Files\Opera\opera.exe | explorer.exe | ||||||||||||
User: admin Company: Opera Software Integrity Level: MEDIUM Description: Opera Internet Browser Exit code: 0 Version: 1748 Modules
| |||||||||||||||
| 3988 | "C:\Users\admin\AppData\Local\Opera\Opera\temporary_downloads\rector.exe" | C:\Users\admin\AppData\Local\Opera\Opera\temporary_downloads\rector.exe | rector.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 4294967295 Modules
| |||||||||||||||
Total events
2 030
Read events
1 550
Write events
473
Delete events
7
Modification events
| (PID) Process: | (2848) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2848) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2848) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\70\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2848) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Sample1.zip | |||
| (PID) Process: | (2848) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2848) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2848) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2848) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2848) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (2848) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
Executable files
5
Suspicious files
9
Text files
26
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2848 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2848.29998\baacfbe10e93fed1185e616701bab39f036755f2e4bf5f5c54dea62415d6b156.bin | — | |
MD5:— | SHA256:— | |||
| 1952 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR79D0.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3940 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opr17A.tmp | — | |
MD5:— | SHA256:— | |||
| 3940 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opr1AA.tmp | — | |
MD5:— | SHA256:— | |||
| 3940 | opera.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\4QHWN6TLFPF4YIFL75WU.temp | — | |
MD5:— | SHA256:— | |||
| 3940 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\sessions\opr9485.tmp | — | |
MD5:— | SHA256:— | |||
| 3940 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\sessions\oprA05D.tmp | — | |
MD5:— | SHA256:— | |||
| 2904 | EQNEDT32.EXE | C:\Users\admin\AppData\Roaming\rectorfile.exe | executable | |
MD5:— | SHA256:— | |||
| 1952 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\ayyy.doc.LNK | lnk | |
MD5:— | SHA256:— | |||
| 1952 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
25
TCP/UDP connections
18
DNS requests
9
Threats
23
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3940 | opera.exe | GET | — | 164.160.128.117:80 | http://mrjbiz.top/ugpounds/ | NG | — | — | malicious |
3940 | opera.exe | GET | 200 | 93.184.220.29:80 | http://crl4.digicert.com/DigiCertHighAssuranceEVRootCA.crl | US | der | 528 b | whitelisted |
3420 | rectorfile.exe | GET | 200 | 34.233.102.38:80 | http://checkip.amazonaws.com/ | US | text | 16 b | malicious |
3940 | opera.exe | GET | 200 | 172.217.16.142:80 | http://clients1.google.com/complete/search?q=mrj&client=opera-suggest-omnibox&hl=de | US | text | 96 b | whitelisted |
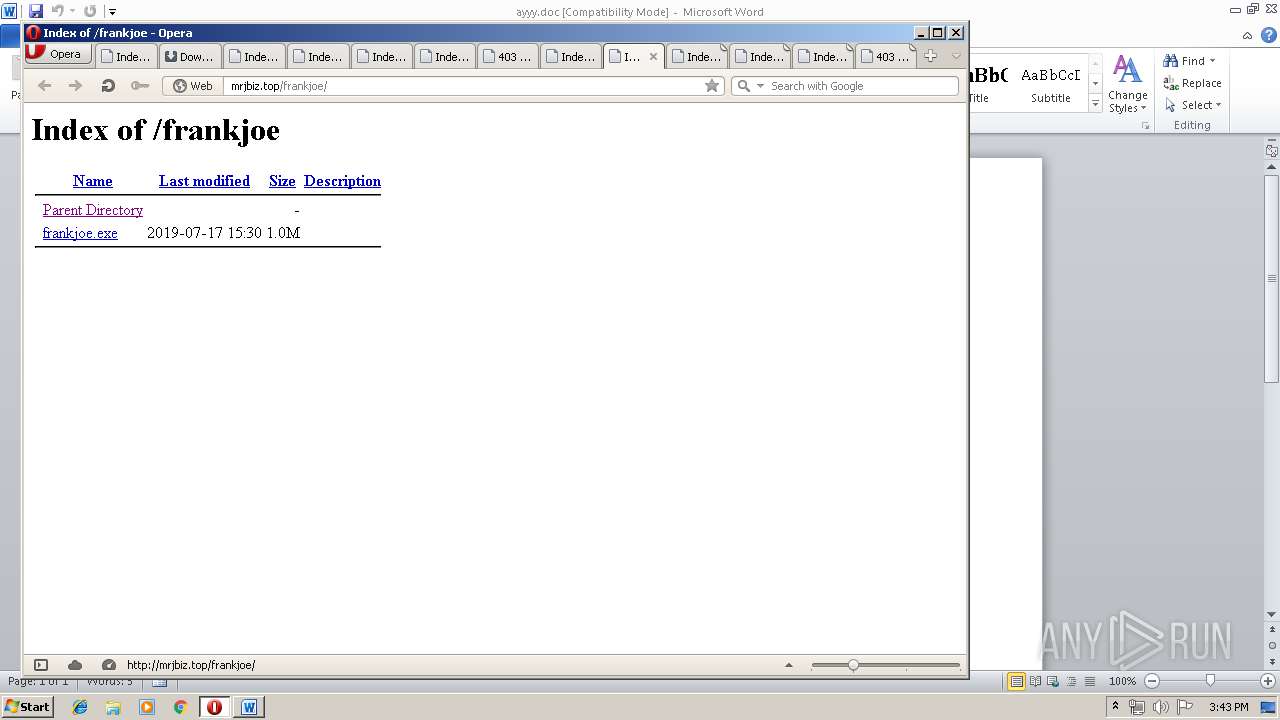
3940 | opera.exe | GET | 200 | 164.160.128.117:80 | http://mrjbiz.top/rector/rector.exe | NG | executable | 1.04 Mb | malicious |
3940 | opera.exe | GET | 200 | 164.160.128.117:80 | http://mrjbiz.top/rector/ | NG | html | 780 b | malicious |
3940 | opera.exe | GET | 200 | 172.217.16.142:80 | http://clients1.google.com/complete/search?q=mrjbiz&client=opera-suggest-omnibox&hl=de | US | text | 33 b | whitelisted |
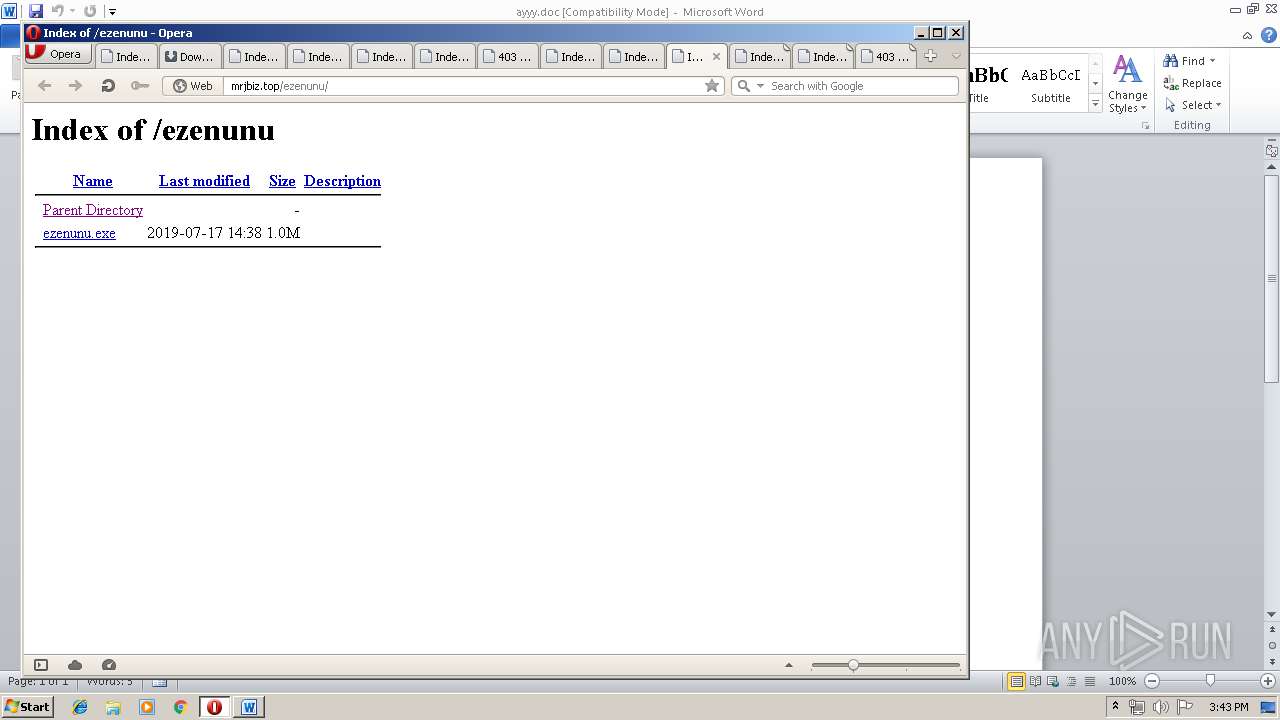
3940 | opera.exe | GET | 200 | 164.160.128.117:80 | http://mrjbiz.top/sunshine/ | NG | html | 786 b | malicious |
3940 | opera.exe | GET | 200 | 164.160.128.117:80 | http://mrjbiz.top/ugpounds/ | NG | html | 786 b | malicious |
3940 | opera.exe | GET | 200 | 164.160.128.117:80 | http://mrjbiz.top/peterz/ | NG | html | 780 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2904 | EQNEDT32.EXE | 164.160.128.117:80 | mrjbiz.top | Garanntor-Hosting-AS | NG | malicious |
3420 | rectorfile.exe | 34.233.102.38:80 | checkip.amazonaws.com | Amazon.com, Inc. | US | shared |
3940 | opera.exe | 185.26.182.93:443 | certs.opera.com | Opera Software AS | — | whitelisted |
3940 | opera.exe | 93.184.220.29:80 | crl4.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3940 | opera.exe | 172.217.16.142:80 | clients1.google.com | Google Inc. | US | whitelisted |
3420 | rectorfile.exe | 164.160.128.117:587 | mrjbiz.top | Garanntor-Hosting-AS | NG | malicious |
3940 | opera.exe | 164.160.128.117:80 | mrjbiz.top | Garanntor-Hosting-AS | NG | malicious |
3940 | opera.exe | 185.26.182.93:80 | certs.opera.com | Opera Software AS | — | whitelisted |
3988 | rector.exe | 164.160.128.117:587 | mrjbiz.top | Garanntor-Hosting-AS | NG | malicious |
3988 | rector.exe | 52.6.79.229:80 | checkip.amazonaws.com | Amazon.com, Inc. | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
mrjbiz.top |
| malicious |
checkip.amazonaws.com |
| malicious |
certs.opera.com |
| whitelisted |
crl4.digicert.com |
| whitelisted |
gh-ws-rhl01.garanntor.net |
| malicious |
clients1.google.com |
| whitelisted |
sitecheck2.opera.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1044 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
2904 | EQNEDT32.EXE | A Network Trojan was detected | ET CURRENT_EVENTS SUSPICIOUS Firesale gTLD EXE DL with no Referer June 13 2016 |
2904 | EQNEDT32.EXE | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
2904 | EQNEDT32.EXE | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2904 | EQNEDT32.EXE | Misc activity | ET INFO Possible EXE Download From Suspicious TLD |
3420 | rectorfile.exe | A Network Trojan was detected | MALWARE [PTsecurity] AgentTesla IP Check |
3420 | rectorfile.exe | Generic Protocol Command Decode | SURICATA Applayer Detect protocol only one direction |
3940 | opera.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
3940 | opera.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3940 | opera.exe | Misc activity | ET INFO Possible EXE Download From Suspicious TLD |
6 ETPRO signatures available at the full report