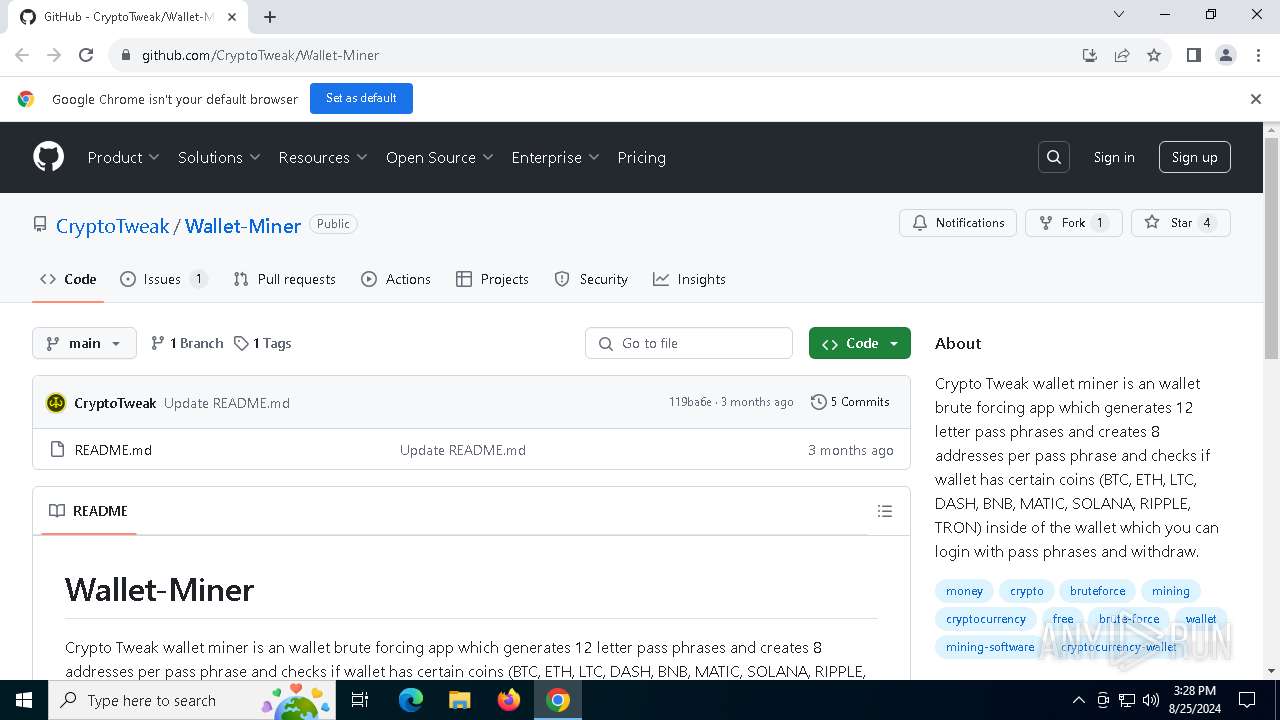
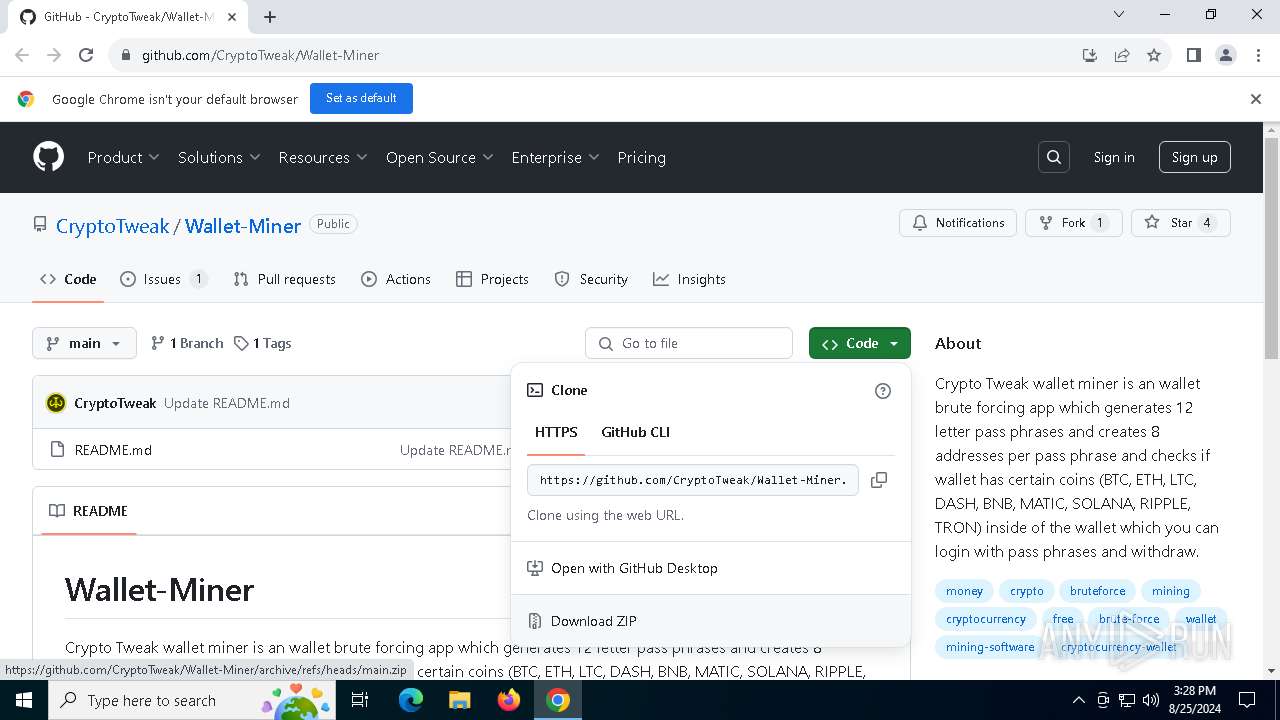
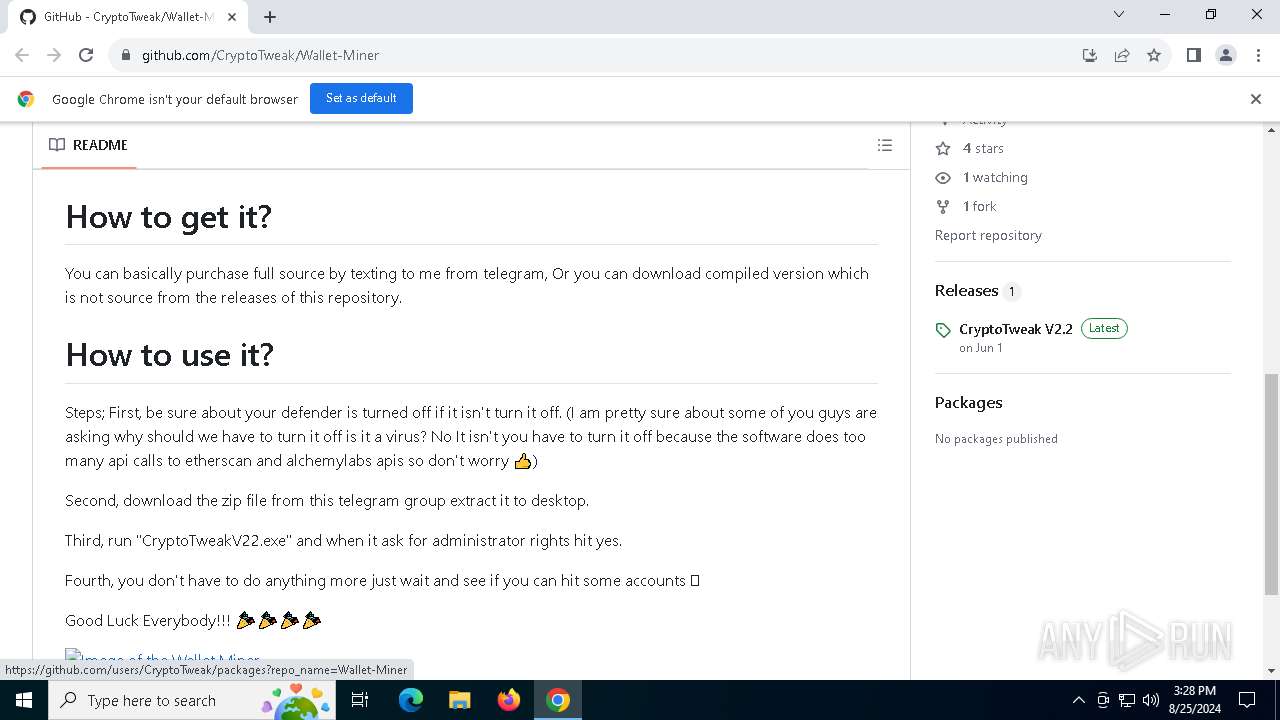
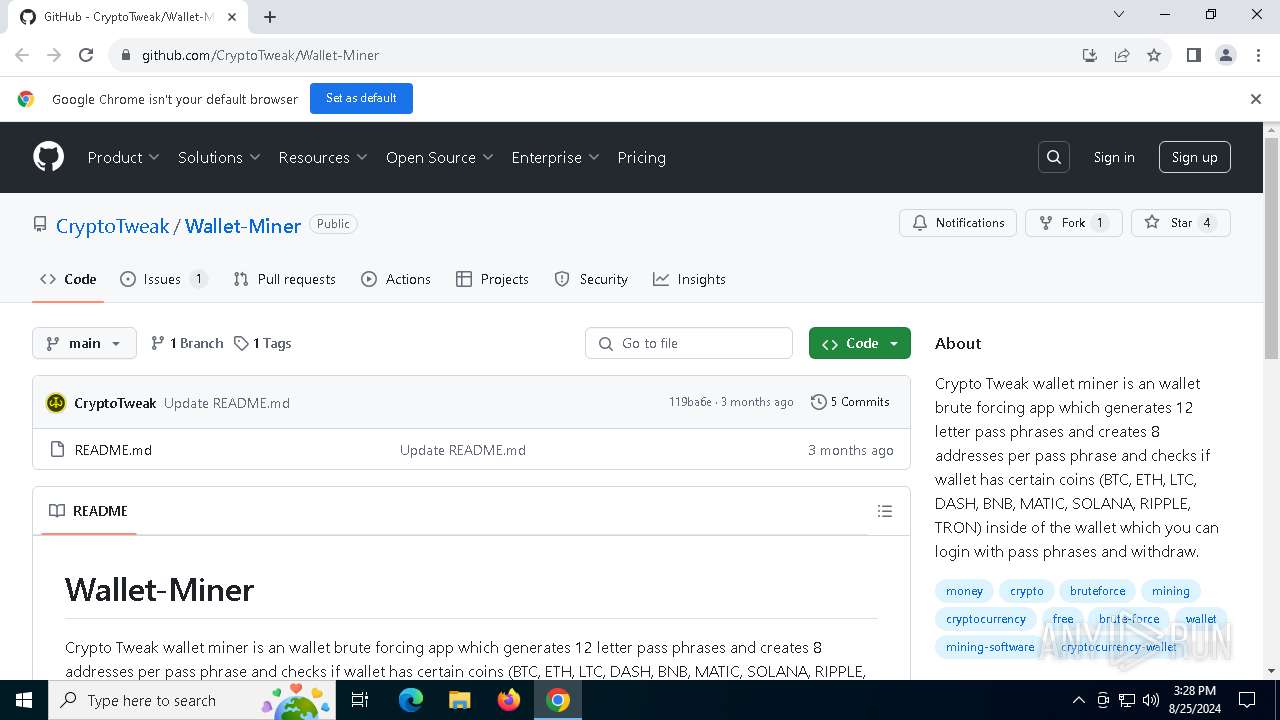
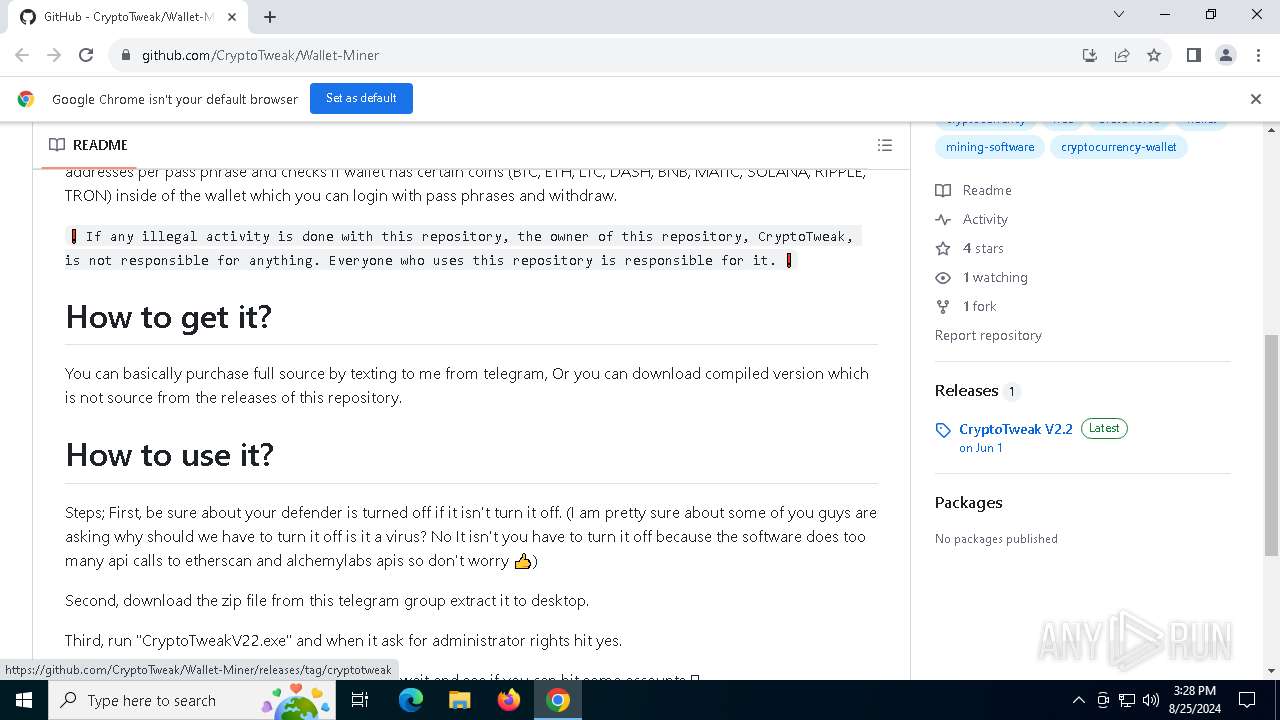
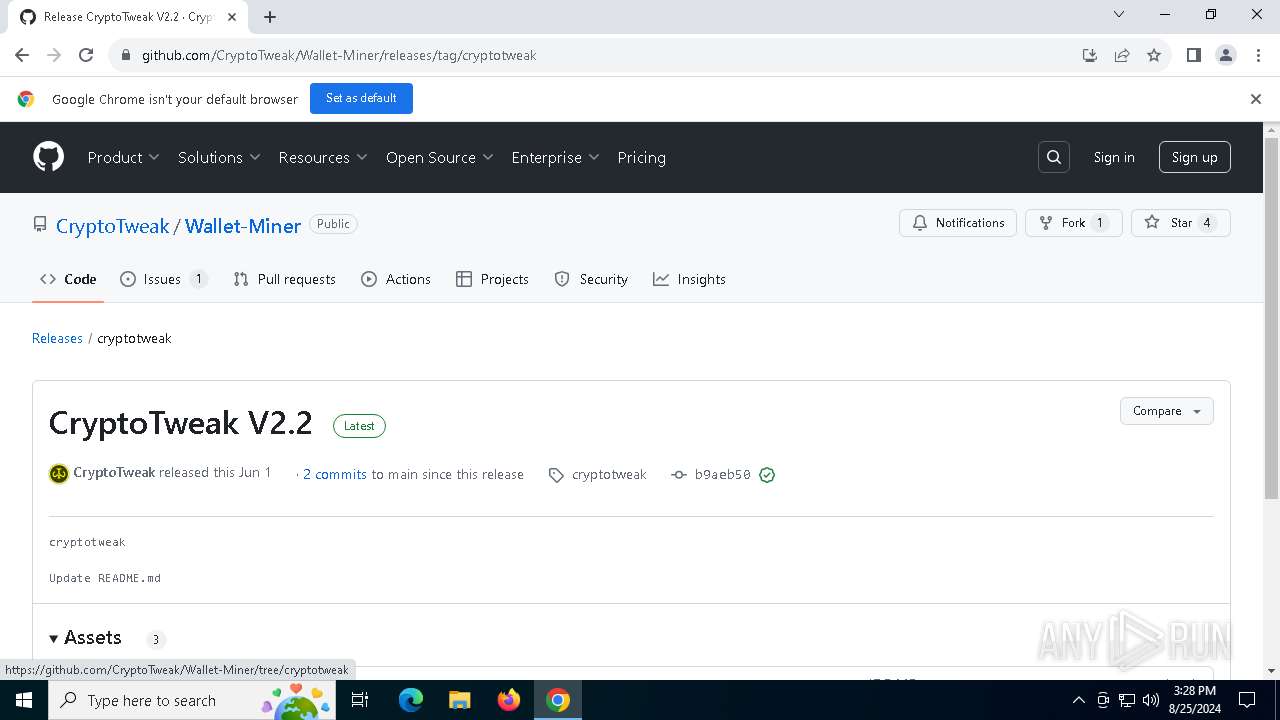
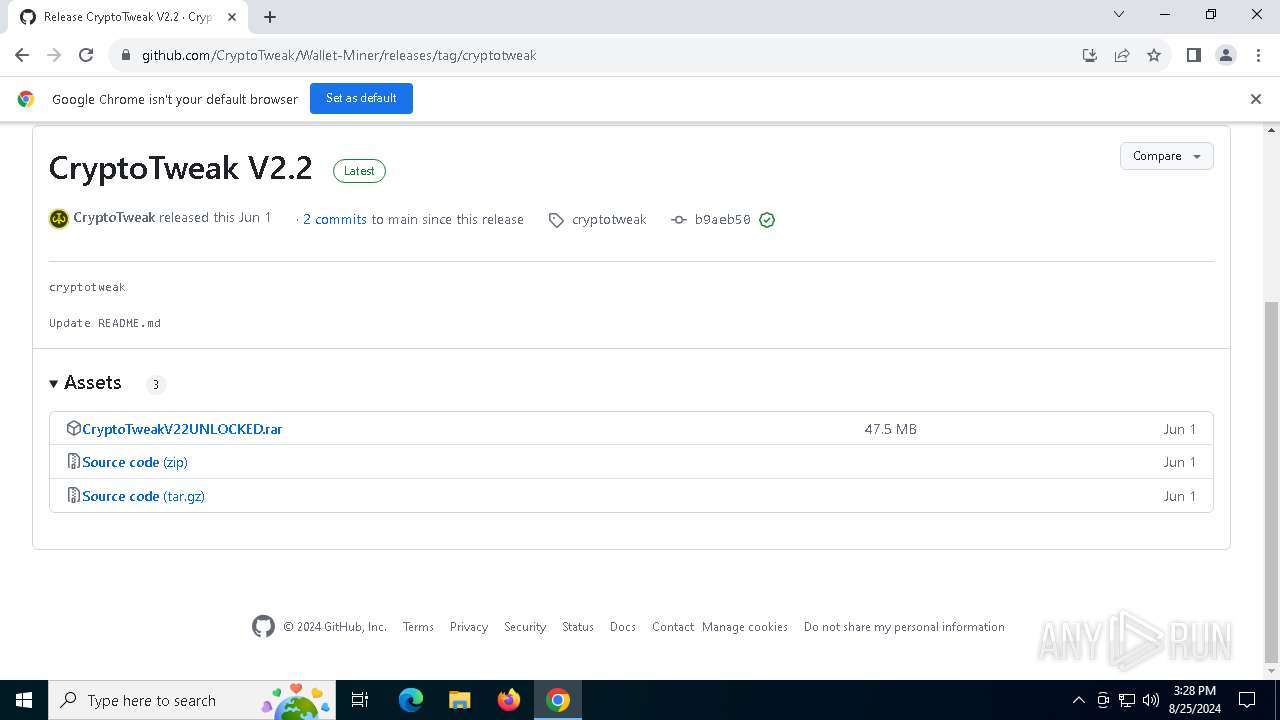
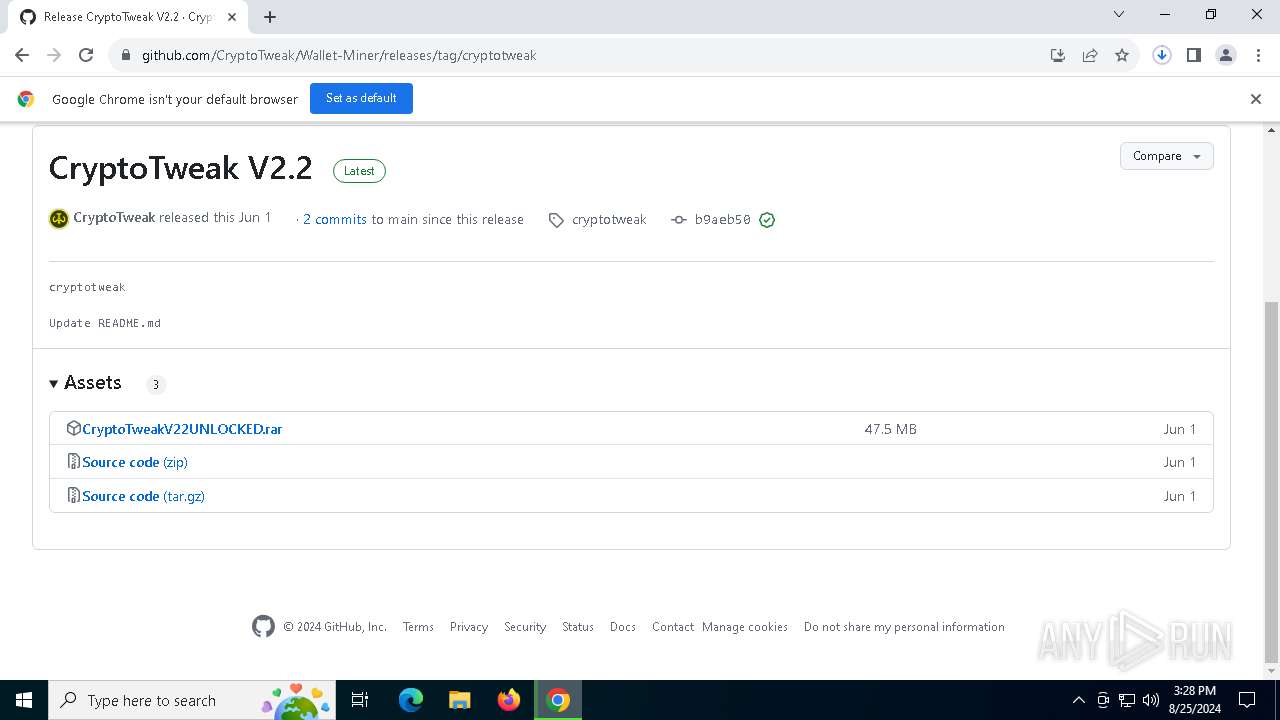
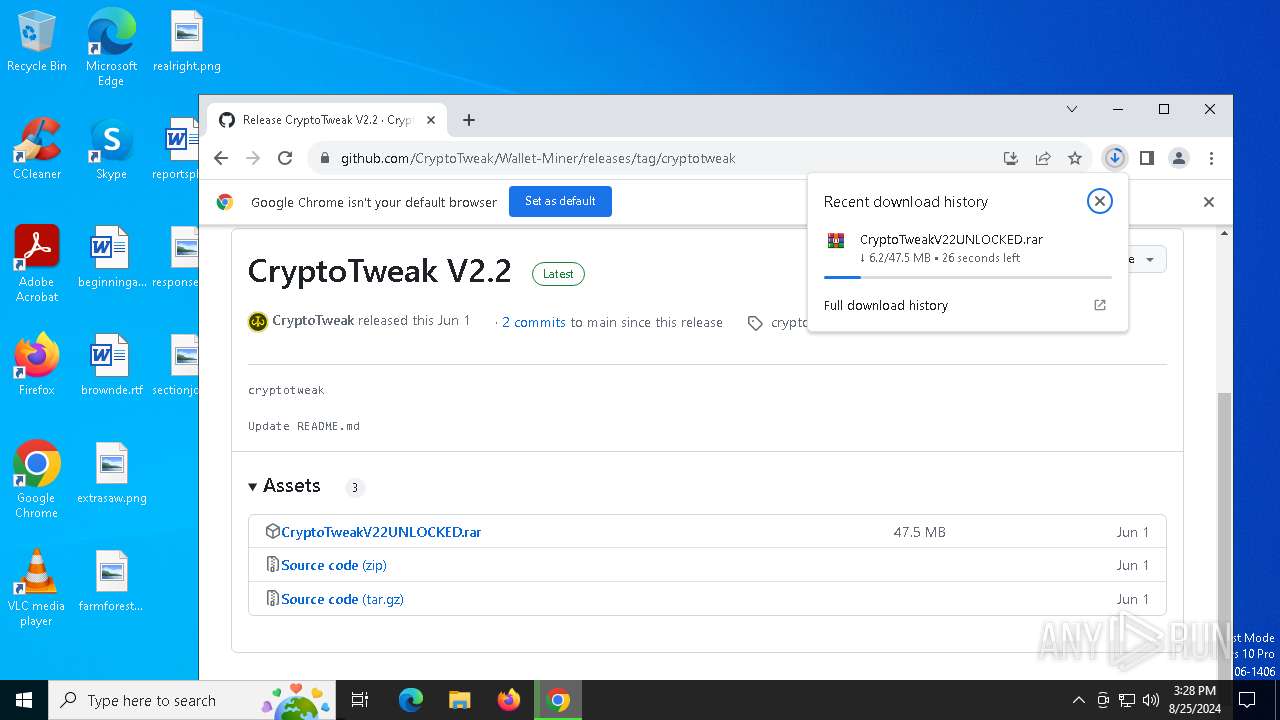
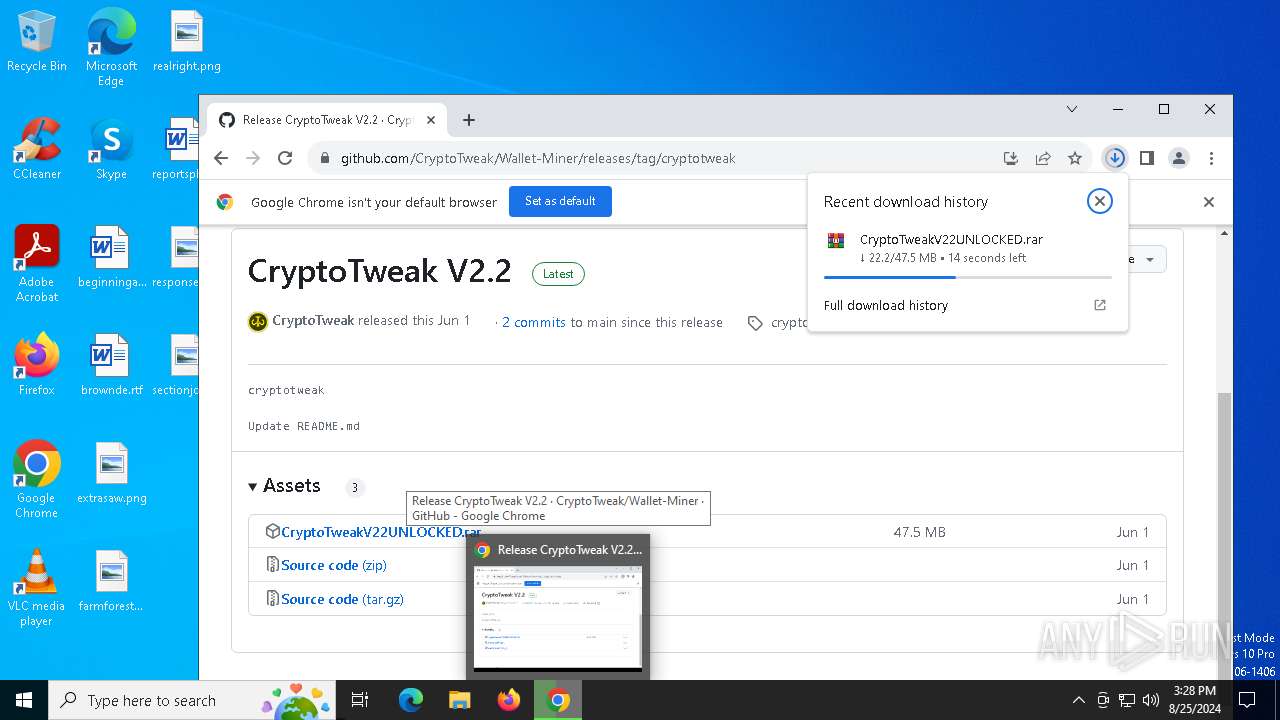
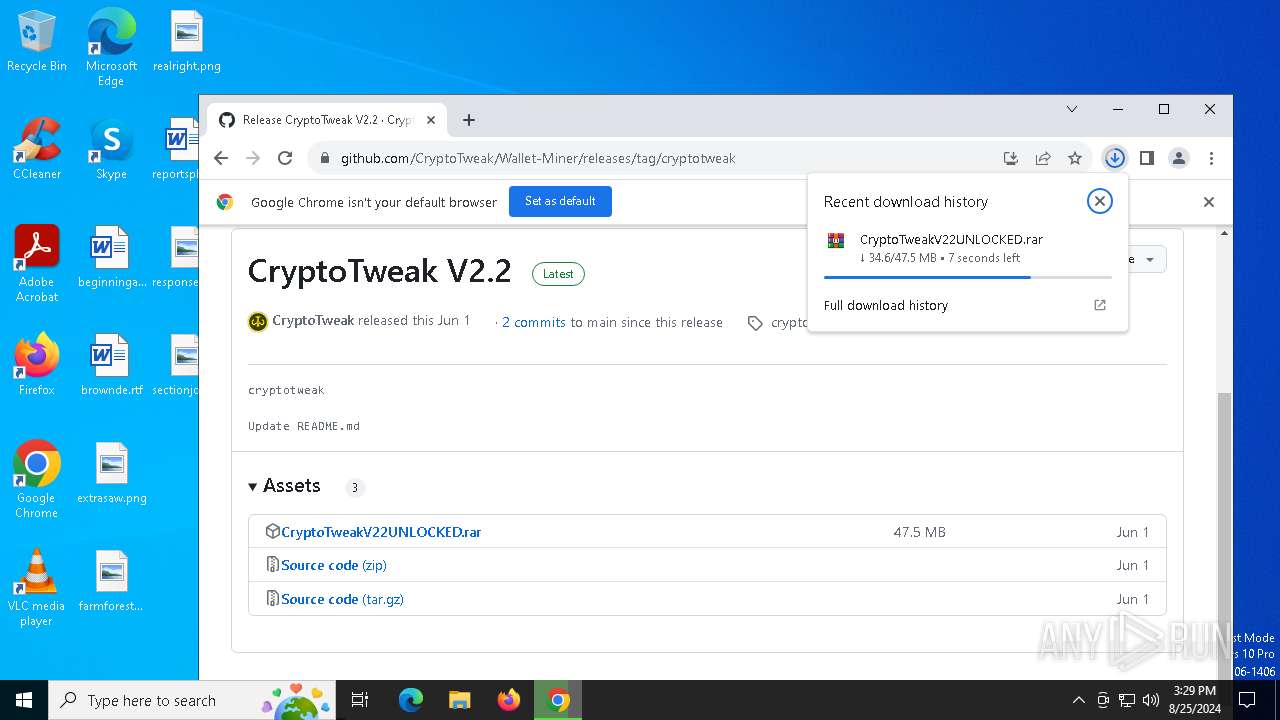
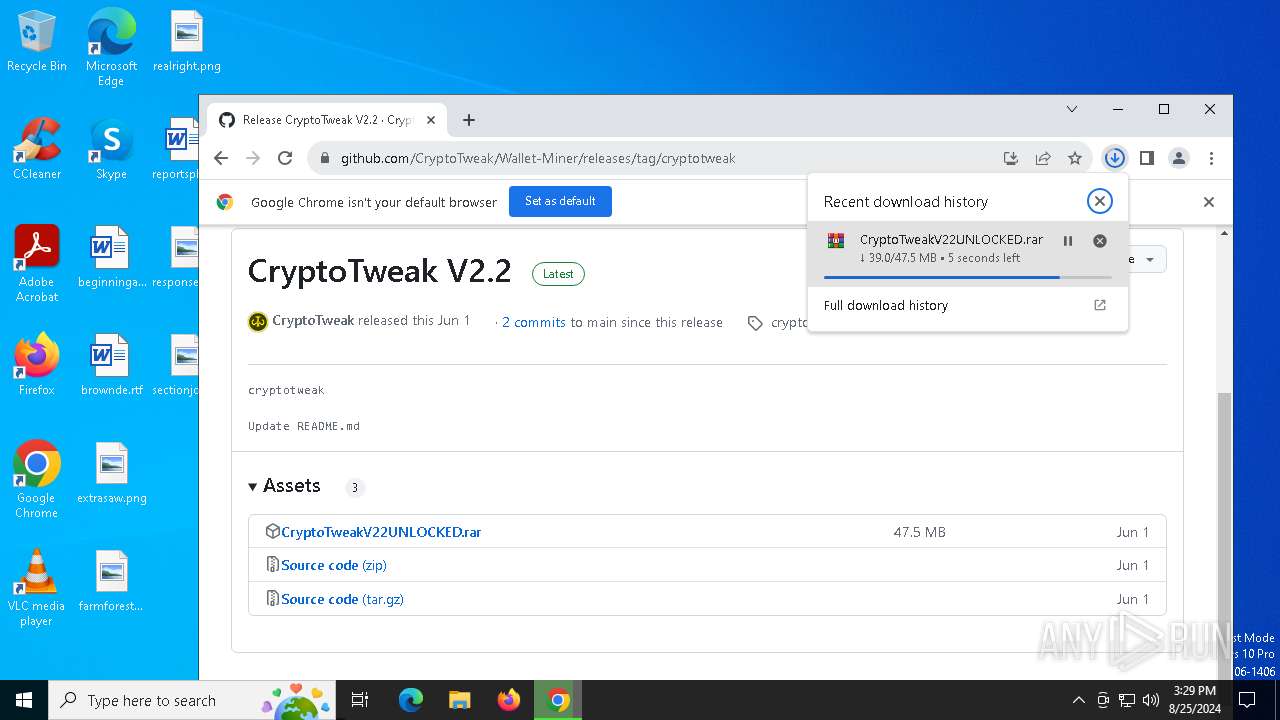
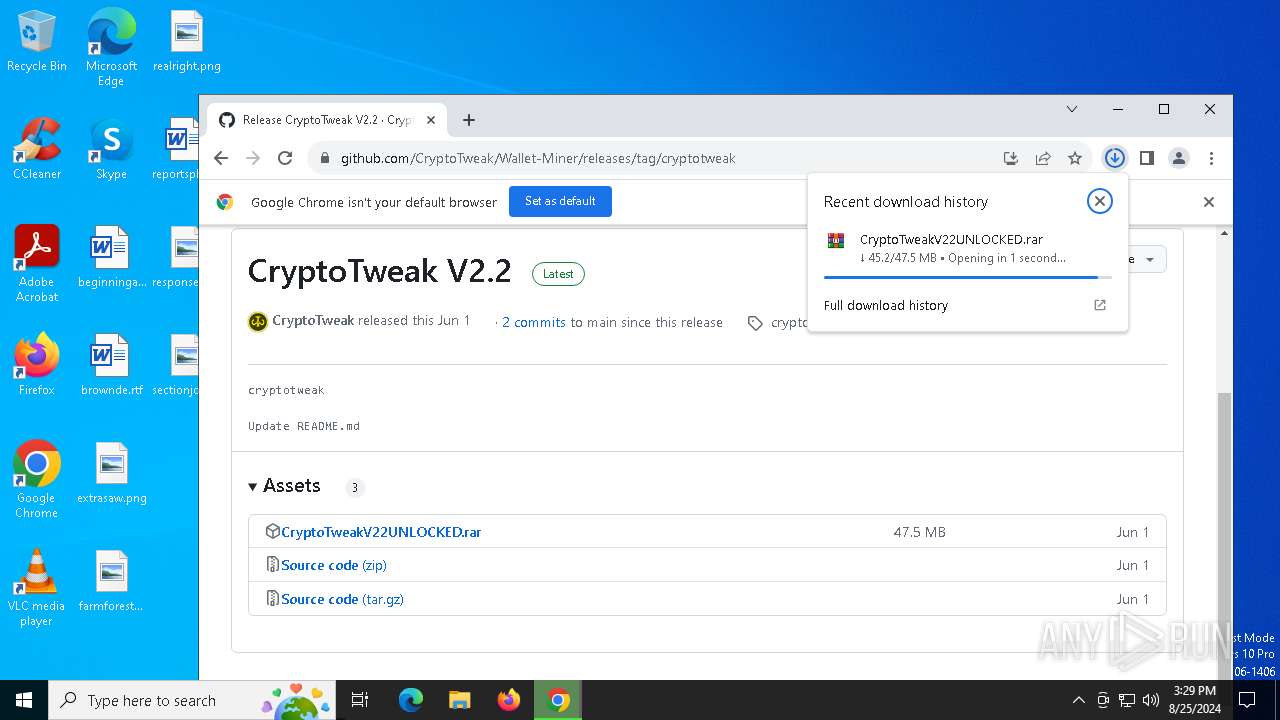
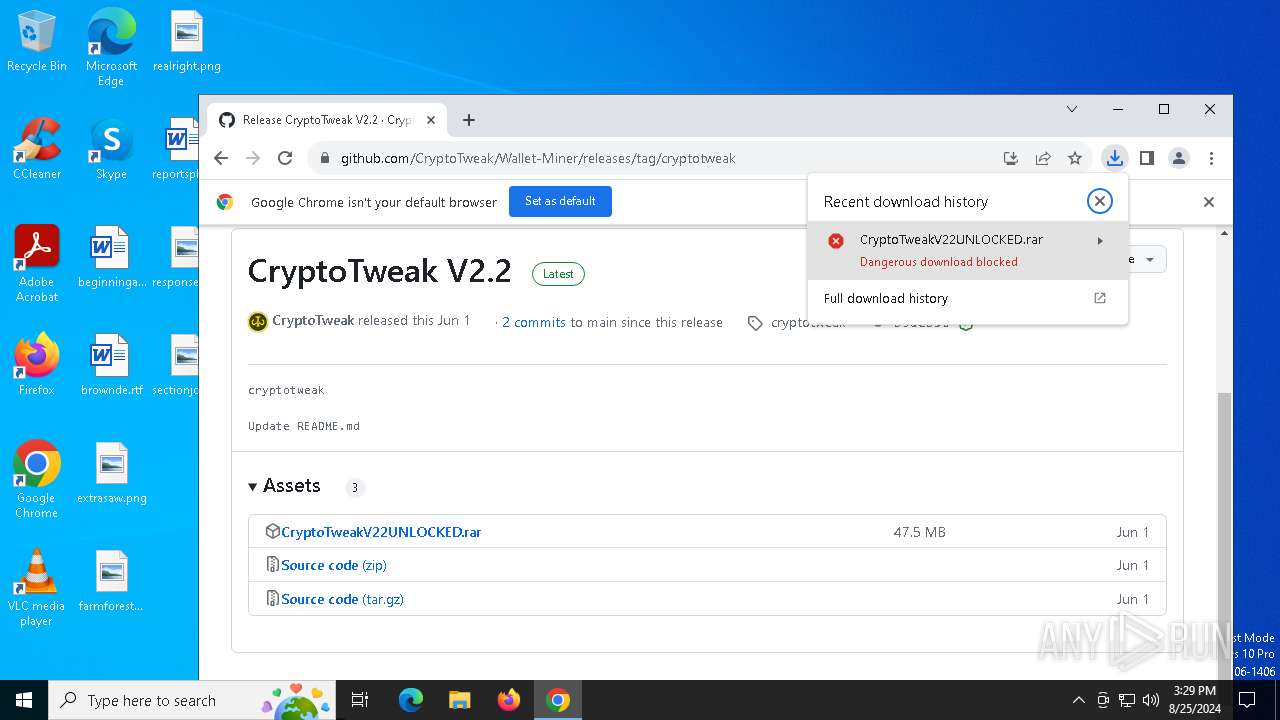
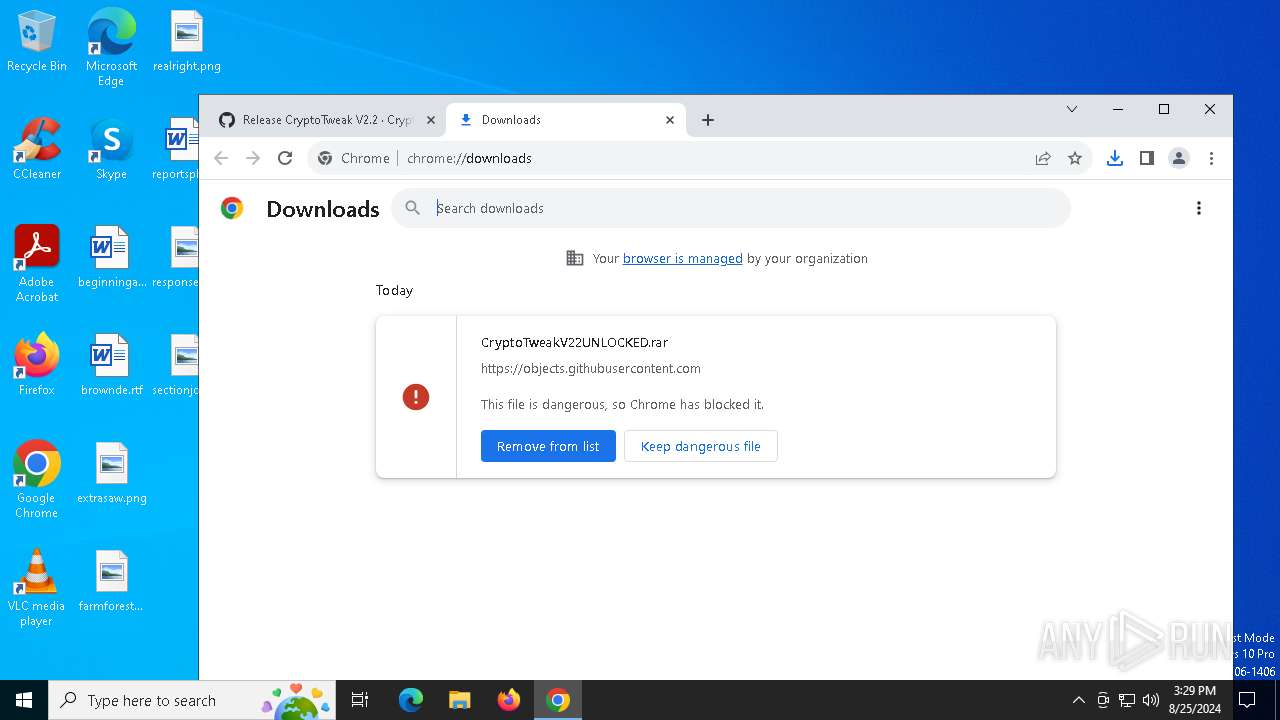
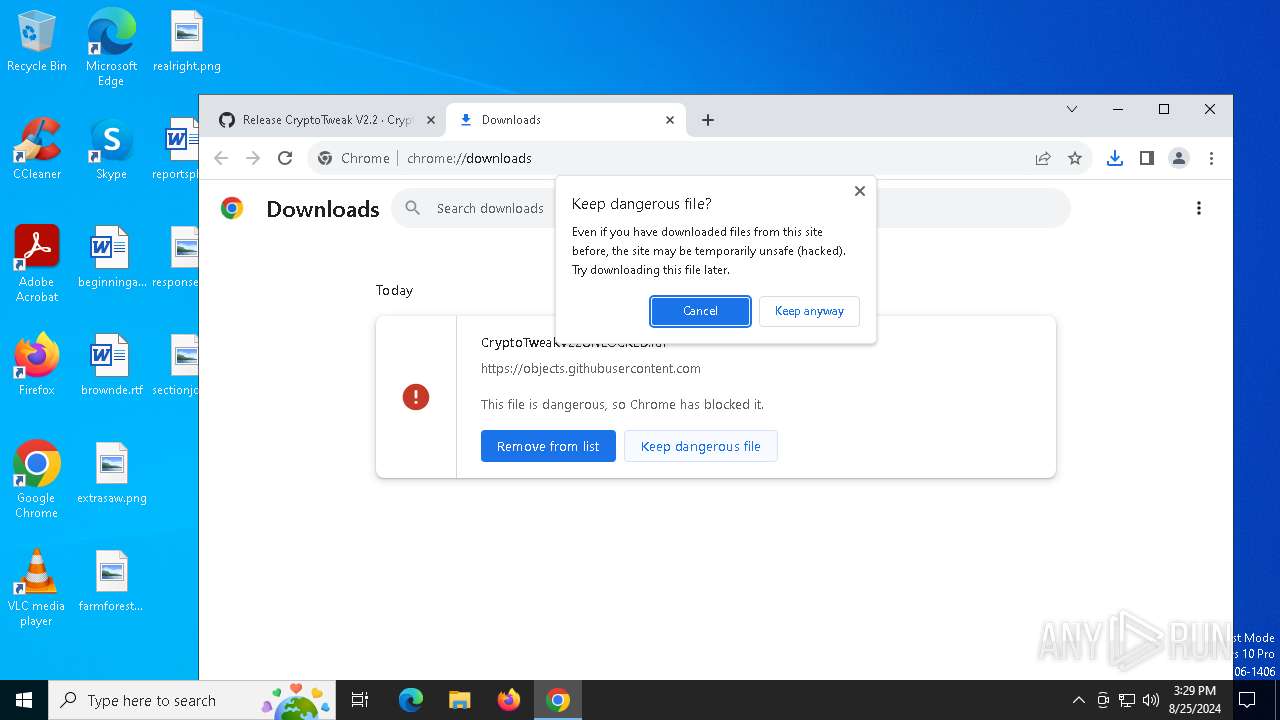
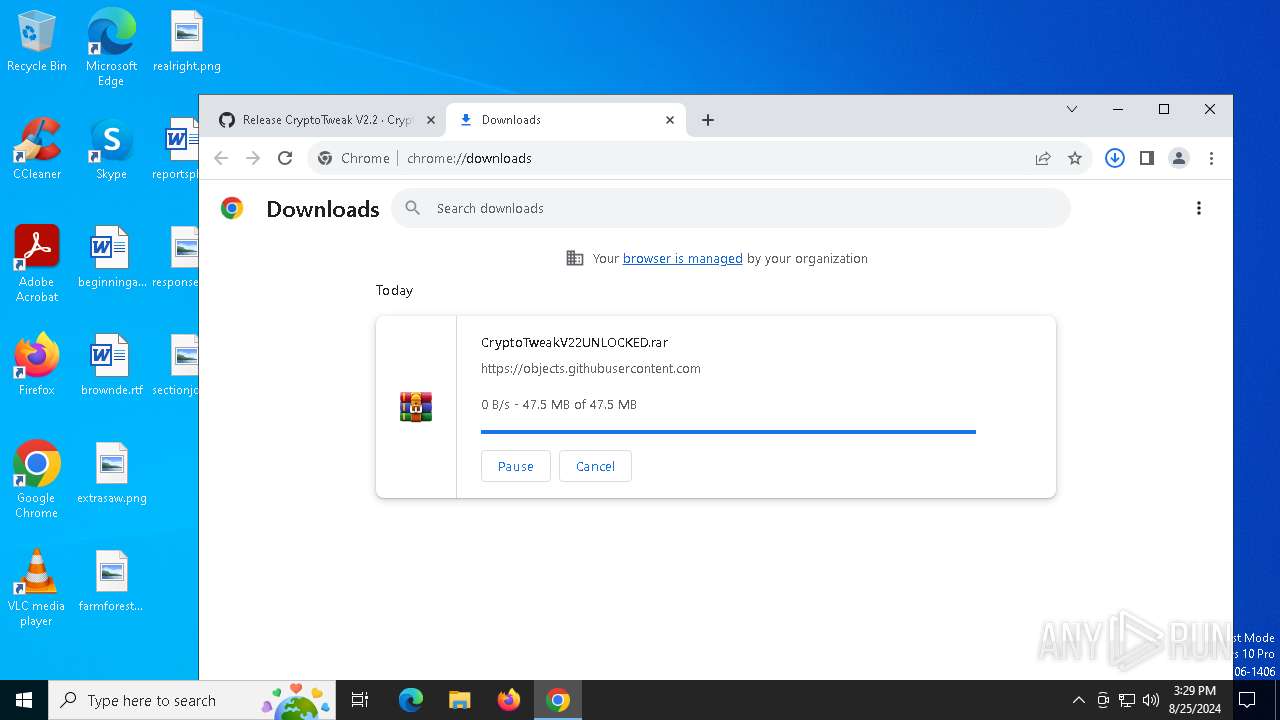
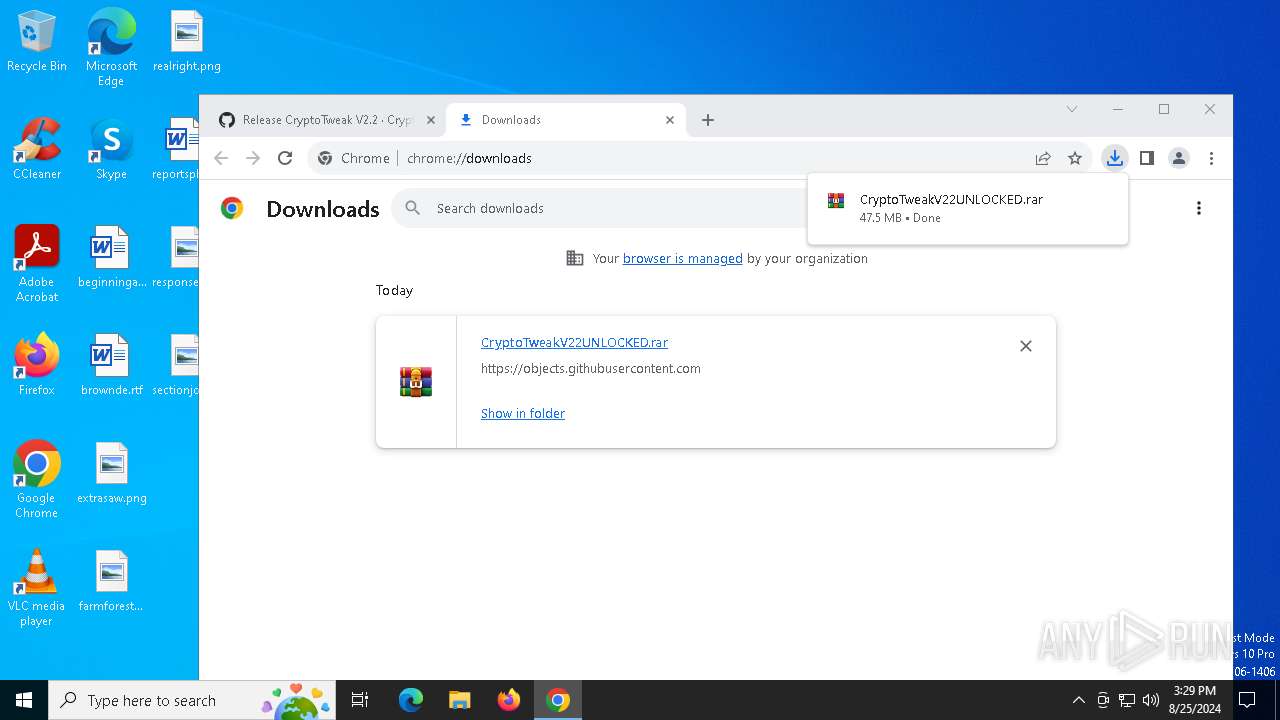
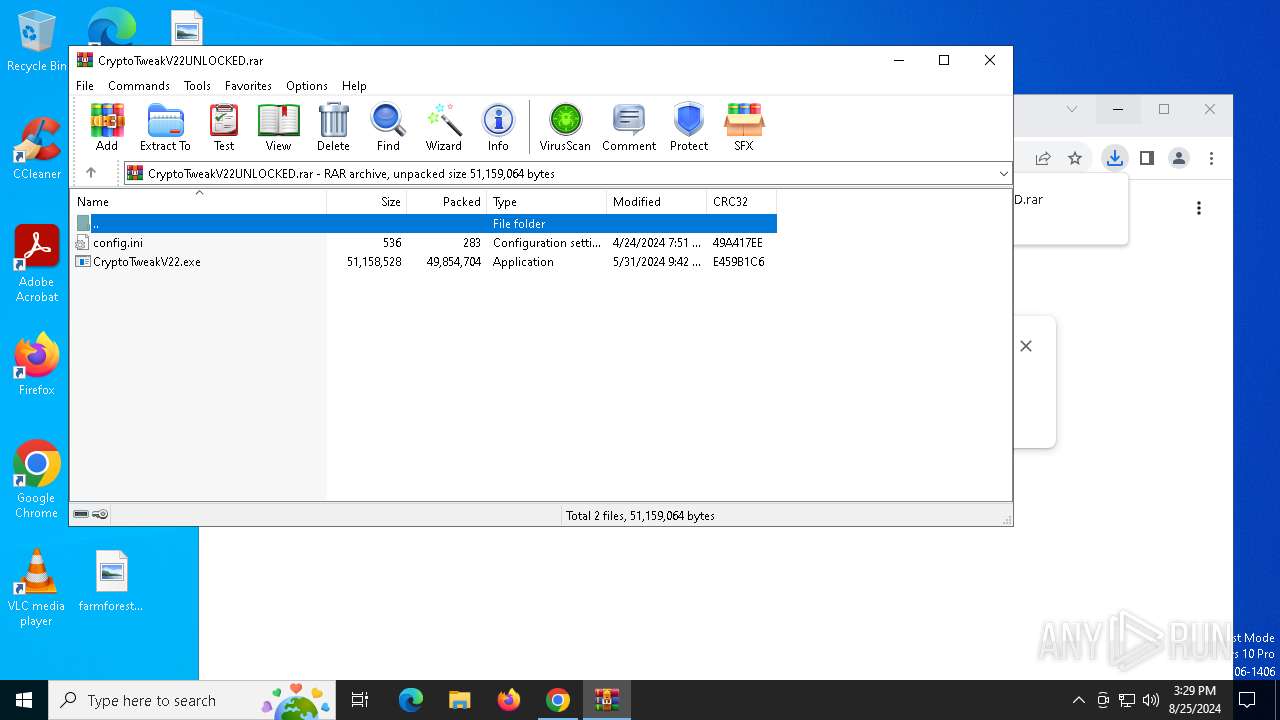
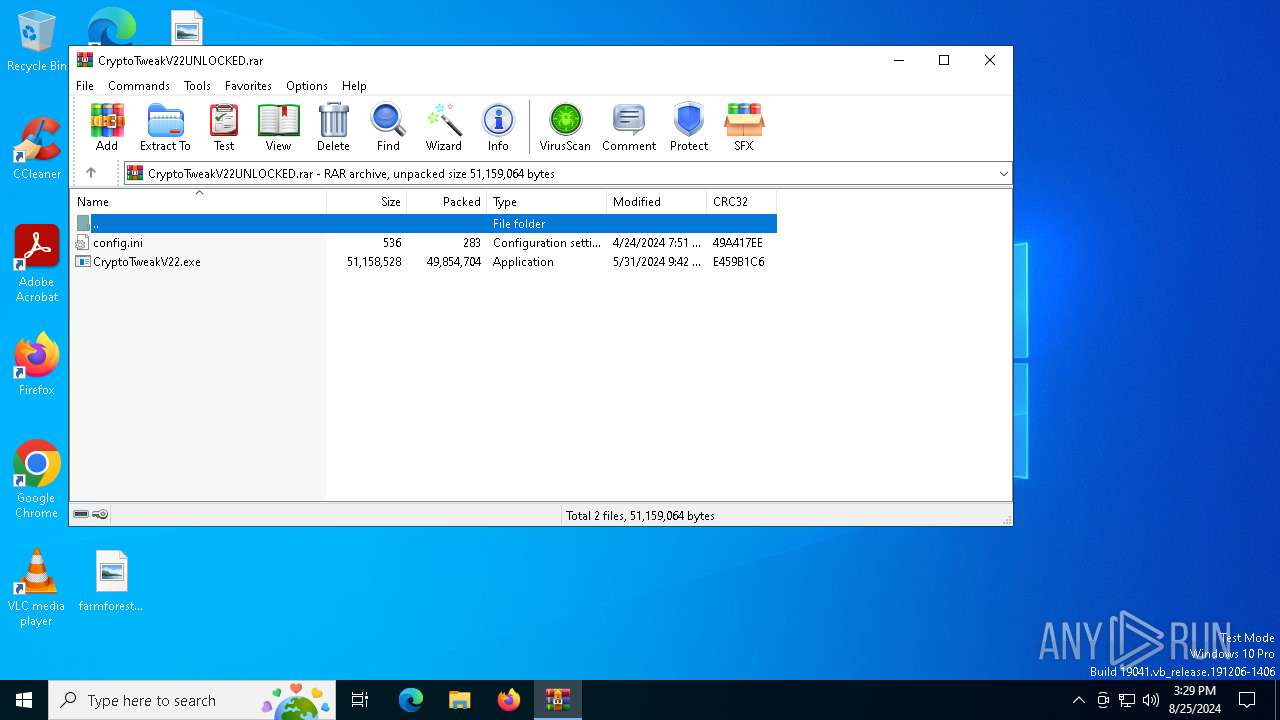
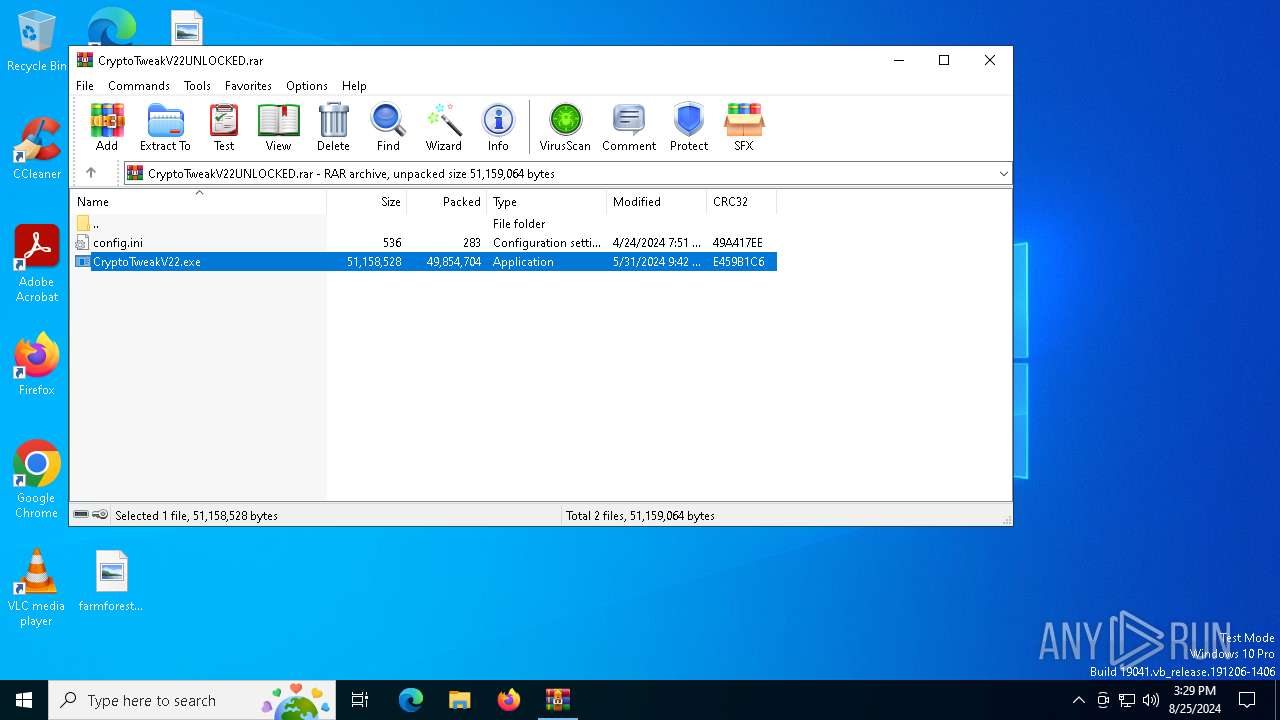
| URL: | https://github.com/CryptoTweak/Wallet-Miner |
| Full analysis: | https://app.any.run/tasks/0d2160d5-eb0f-446f-a4dd-bed8a31b3e9c |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | August 25, 2024, 15:28:23 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 2F3845BAB4DA557BC7B916FC67CC9852 |
| SHA1: | 6E16CC69E121FB8BB465A47548CDD079B7B9A5DC |
| SHA256: | B2C93ECCBF52FD368A0C439D885D55F29BF63C301B6C0208936F0D1AD113B00F |
| SSDEEP: | 3:N8tEdJ7KUAKZ+xn:2uP7KZKZUn |
MALICIOUS
Actions looks like stealing of personal data
- EwQLxOSLxoJkxT.exe (PID: 5548)
Create files in the Startup directory
- EwQLxOSLxoJkxT.exe (PID: 5548)
WASPSTEALER has been detected (YARA)
- EwQLxOSLxoJkxT.exe (PID: 5548)
DISCORDGRABBER has been detected (YARA)
- EwQLxOSLxoJkxT.exe (PID: 5548)
Adds extension to the Windows Defender exclusion list
- CryptoTweakV22.exe (PID: 6444)
- hghufrrlpzqp.exe (PID: 6292)
Application was injected by another process
- svchost.exe (PID: 1200)
- svchost.exe (PID: 1272)
- svchost.exe (PID: 476)
- svchost.exe (PID: 1408)
- winlogon.exe (PID: 684)
- lsass.exe (PID: 768)
- svchost.exe (PID: 1208)
- svchost.exe (PID: 1620)
- svchost.exe (PID: 1816)
- dwm.exe (PID: 852)
- svchost.exe (PID: 1364)
- svchost.exe (PID: 1508)
- svchost.exe (PID: 1036)
- svchost.exe (PID: 1316)
- svchost.exe (PID: 1600)
- svchost.exe (PID: 1472)
- svchost.exe (PID: 1588)
- svchost.exe (PID: 1796)
- svchost.exe (PID: 1864)
- svchost.exe (PID: 2184)
- svchost.exe (PID: 1872)
- svchost.exe (PID: 2304)
- svchost.exe (PID: 2072)
- svchost.exe (PID: 2256)
- spoolsv.exe (PID: 2592)
- svchost.exe (PID: 2312)
- svchost.exe (PID: 2496)
- svchost.exe (PID: 2788)
- svchost.exe (PID: 2412)
- svchost.exe (PID: 2692)
- svchost.exe (PID: 2344)
- svchost.exe (PID: 2996)
- svchost.exe (PID: 3020)
- svchost.exe (PID: 1628)
- svchost.exe (PID: 2160)
- svchost.exe (PID: 2000)
- svchost.exe (PID: 3012)
- svchost.exe (PID: 4184)
- svchost.exe (PID: 3220)
- svchost.exe (PID: 3260)
- svchost.exe (PID: 3200)
- svchost.exe (PID: 3496)
- svchost.exe (PID: 3340)
- svchost.exe (PID: 4140)
- svchost.exe (PID: 4332)
- svchost.exe (PID: 3408)
- svchost.exe (PID: 3888)
- sihost.exe (PID: 4112)
- svchost.exe (PID: 4300)
- svchost.exe (PID: 4532)
- svchost.exe (PID: 3084)
- OfficeClickToRun.exe (PID: 2656)
- svchost.exe (PID: 3056)
- svchost.exe (PID: 2968)
- ctfmon.exe (PID: 4356)
- MoUsoCoreWorker.exe (PID: 2120)
- dllhost.exe (PID: 5568)
- dllhost.exe (PID: 3312)
- RuntimeBroker.exe (PID: 776)
- svchost.exe (PID: 5416)
- svchost.exe (PID: 4000)
- ApplicationFrameHost.exe (PID: 4052)
- svchost.exe (PID: 1824)
- UserOOBEBroker.exe (PID: 2744)
- svchost.exe (PID: 5236)
- uhssvc.exe (PID: 536)
- svchost.exe (PID: 5256)
- svchost.exe (PID: 5036)
- svchost.exe (PID: 1452)
- svchost.exe (PID: 4808)
- svchost.exe (PID: 4324)
- explorer.exe (PID: 4552)
- RuntimeBroker.exe (PID: 4244)
- RuntimeBroker.exe (PID: 5560)
- dllhost.exe (PID: 4424)
- svchost.exe (PID: 5796)
- WmiPrvSE.exe (PID: 6824)
- svchost.exe (PID: 7128)
- svchost.exe (PID: 2212)
- svchost.exe (PID: 3140)
- svchost.exe (PID: 6400)
- svchost.exe (PID: 2636)
- WmiPrvSE.exe (PID: 6516)
- RuntimeBroker.exe (PID: 6728)
Runs injected code in another process
- dialer.exe (PID: 3672)
- dialer.exe (PID: 3268)
MINER has been detected (SURICATA)
- svchost.exe (PID: 2256)
SUSPICIOUS
Reads security settings of Internet Explorer
- CryptoTweakV22.exe (PID: 2660)
- CryptoTweakV22.exe (PID: 4284)
Reads the date of Windows installation
- CryptoTweakV22.exe (PID: 2660)
Base64-obfuscated command line is found
- CryptoTweakV22.exe (PID: 2660)
BASE64 encoded PowerShell command has been detected
- CryptoTweakV22.exe (PID: 2660)
Starts POWERSHELL.EXE for commands execution
- CryptoTweakV22.exe (PID: 2660)
- CryptoTweakV22.exe (PID: 4392)
- CryptoTweakV22.exe (PID: 6444)
- hghufrrlpzqp.exe (PID: 6292)
Drops the executable file immediately after the start
- CryptoTweakV22.exe (PID: 2660)
- EwQLxOSLxoJkxT.exe (PID: 5888)
- CryptoTweakV22.exe (PID: 4284)
- EwQLxOSLxoJkxT.exe (PID: 5548)
- CryptoTweakV22.exe (PID: 6444)
- hghufrrlpzqp.exe (PID: 6292)
Executable content was dropped or overwritten
- CryptoTweakV22.exe (PID: 2660)
- EwQLxOSLxoJkxT.exe (PID: 5888)
- CryptoTweakV22.exe (PID: 4284)
- EwQLxOSLxoJkxT.exe (PID: 5548)
- CryptoTweakV22.exe (PID: 6444)
- hghufrrlpzqp.exe (PID: 6292)
Powershell scripting: start process
- CryptoTweakV22.exe (PID: 4392)
Process drops python dynamic module
- CryptoTweakV22.exe (PID: 4284)
- EwQLxOSLxoJkxT.exe (PID: 5888)
The process drops C-runtime libraries
- EwQLxOSLxoJkxT.exe (PID: 5888)
- CryptoTweakV22.exe (PID: 4284)
Process drops legitimate windows executable
- EwQLxOSLxoJkxT.exe (PID: 5888)
- CryptoTweakV22.exe (PID: 4284)
Starts CMD.EXE for commands execution
- EwQLxOSLxoJkxT.exe (PID: 5548)
- lol.exe (PID: 1076)
- CryptoTweakV22.exe (PID: 6444)
- hghufrrlpzqp.exe (PID: 6292)
Checks for external IP
- svchost.exe (PID: 2256)
- EwQLxOSLxoJkxT.exe (PID: 5548)
Application launched itself
- EwQLxOSLxoJkxT.exe (PID: 5888)
Data upload via CURL
- curl.exe (PID: 5768)
- curl.exe (PID: 6260)
- curl.exe (PID: 4252)
- curl.exe (PID: 7152)
- curl.exe (PID: 4820)
- curl.exe (PID: 5532)
Loads Python modules
- lol.exe (PID: 1076)
Connects to unusual port
- lol.exe (PID: 1076)
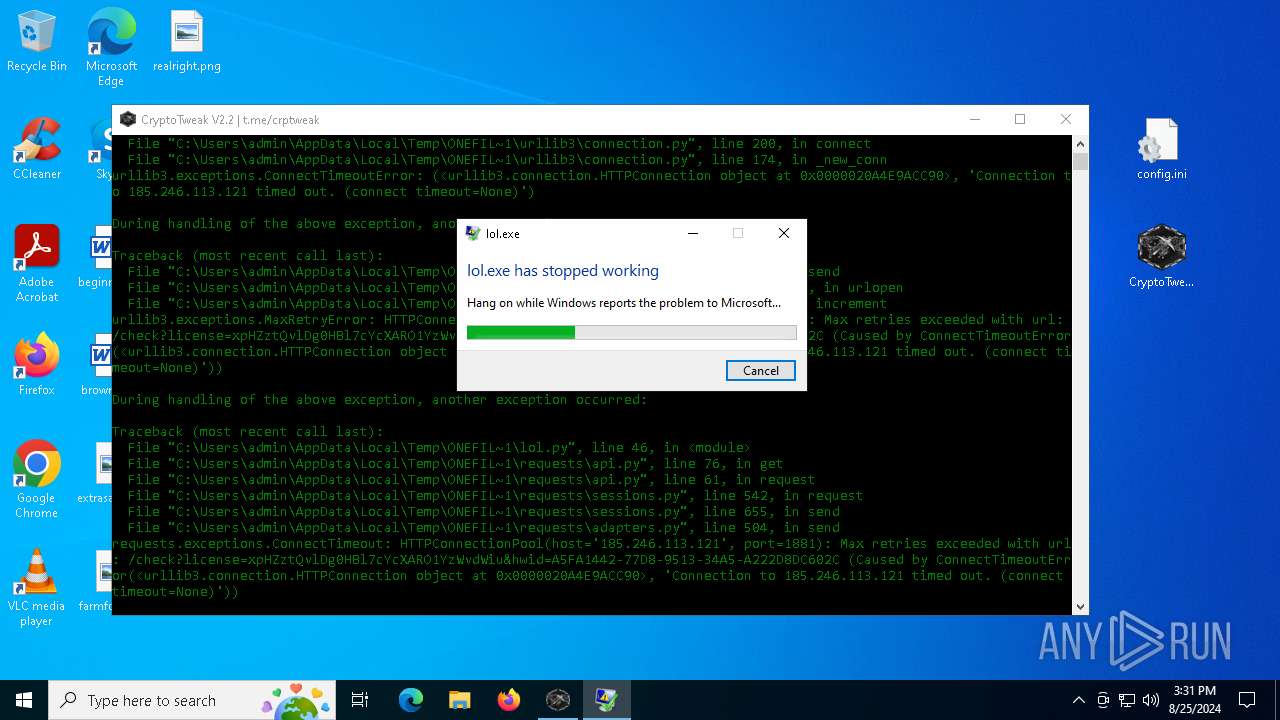
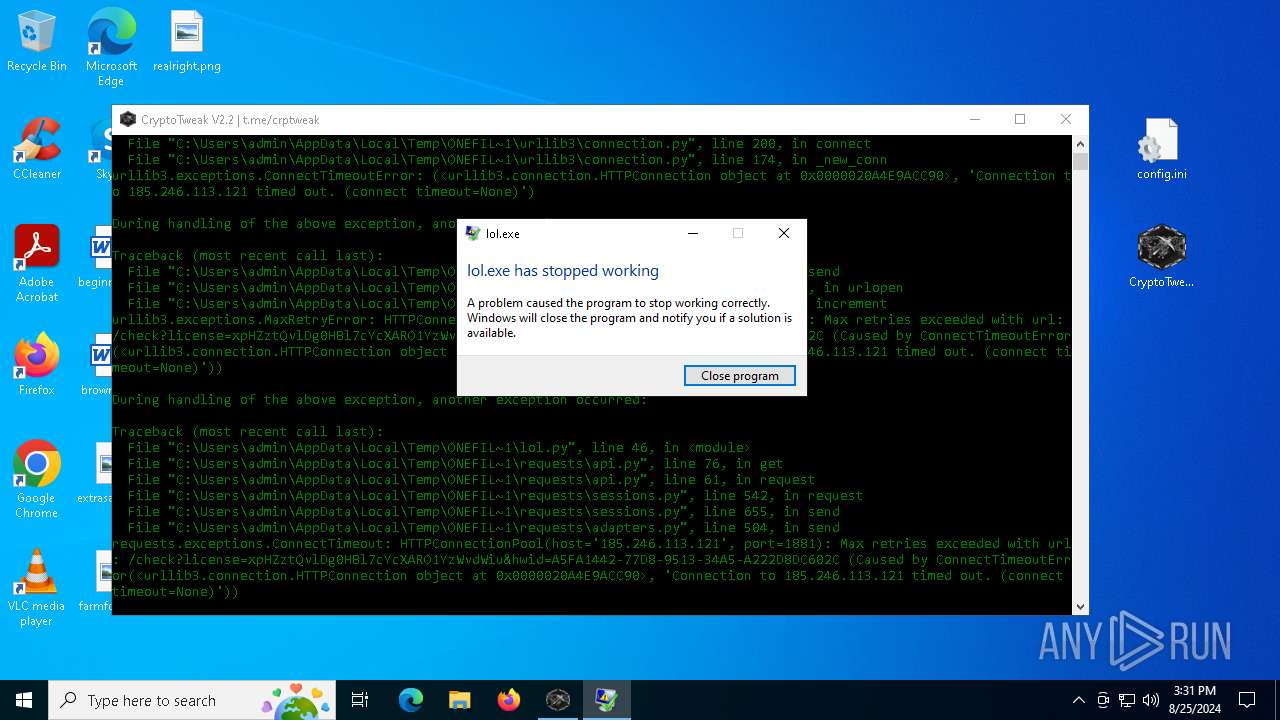
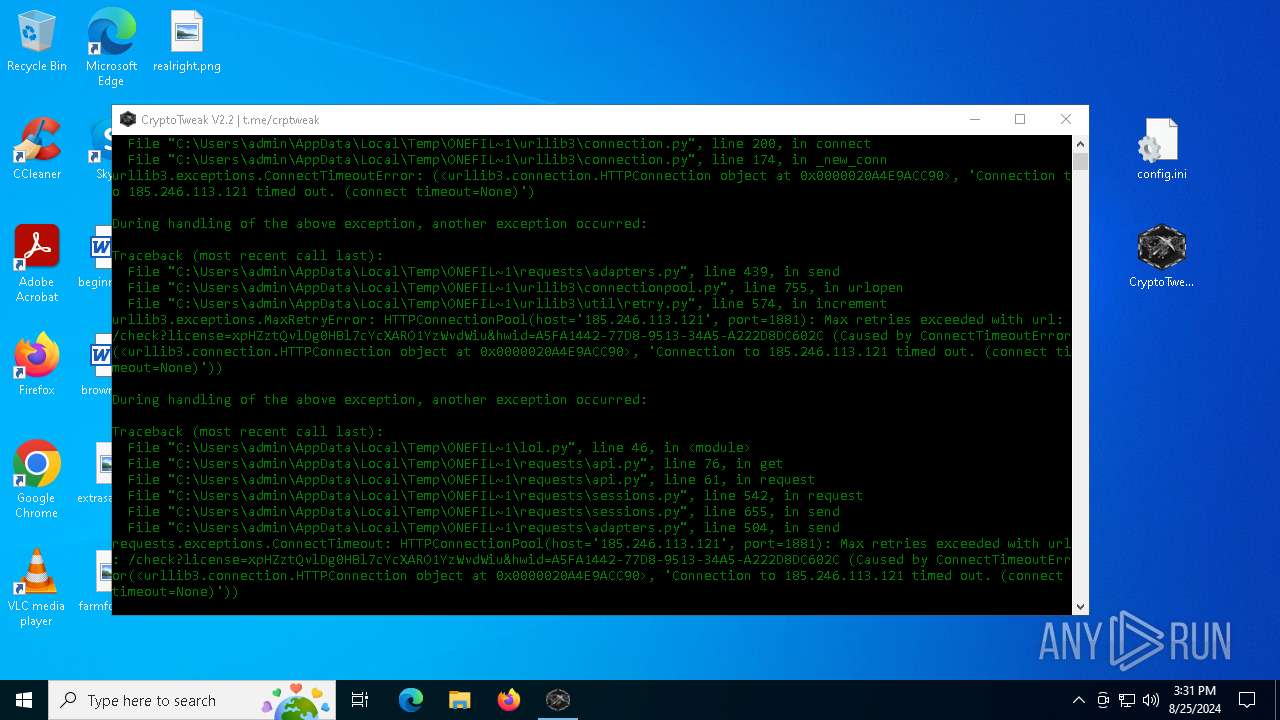
Executes application which crashes
- lol.exe (PID: 1076)
Script adds exclusion path to Windows Defender
- CryptoTweakV22.exe (PID: 6444)
- hghufrrlpzqp.exe (PID: 6292)
Script adds exclusion extension to Windows Defender
- CryptoTweakV22.exe (PID: 6444)
- hghufrrlpzqp.exe (PID: 6292)
Process uninstalls Windows update
- wusa.exe (PID: 2616)
- wusa.exe (PID: 2820)
Uses powercfg.exe to modify the power settings
- CryptoTweakV22.exe (PID: 6444)
- hghufrrlpzqp.exe (PID: 6292)
Executes as Windows Service
- hghufrrlpzqp.exe (PID: 6292)
Starts SC.EXE for service management
- CryptoTweakV22.exe (PID: 6444)
- hghufrrlpzqp.exe (PID: 6292)
Drops a system driver (possible attempt to evade defenses)
- hghufrrlpzqp.exe (PID: 6292)
Crypto Currency Mining Activity Detected
- svchost.exe (PID: 2256)
INFO
Application launched itself
- chrome.exe (PID: 6580)
Reads Microsoft Office registry keys
- chrome.exe (PID: 6580)
- OfficeClickToRun.exe (PID: 2656)
Creates files in the program directory
- MoUsoCoreWorker.exe (PID: 2120)
- svchost.exe (PID: 3140)
- CryptoTweakV22.exe (PID: 6444)
Reads security settings of Internet Explorer
- explorer.exe (PID: 4552)
- RuntimeBroker.exe (PID: 6728)
Reads the time zone
- svchost.exe (PID: 2692)
Reads the computer name
- CryptoTweakV22.exe (PID: 2660)
- EwQLxOSLxoJkxT.exe (PID: 5888)
- EwQLxOSLxoJkxT.exe (PID: 5548)
- curl.exe (PID: 5768)
- curl.exe (PID: 6260)
- curl.exe (PID: 4252)
- CryptoTweakV22.exe (PID: 4284)
Process checks computer location settings
- CryptoTweakV22.exe (PID: 2660)
Checks supported languages
- CryptoTweakV22.exe (PID: 2660)
- EwQLxOSLxoJkxT.exe (PID: 5888)
- CryptoTweakV22.exe (PID: 4284)
- CryptoTweakV22.exe (PID: 4392)
- CryptoTweakV22.exe (PID: 6444)
- EwQLxOSLxoJkxT.exe (PID: 5548)
- curl.exe (PID: 5768)
- curl.exe (PID: 4252)
- curl.exe (PID: 7152)
- curl.exe (PID: 6260)
- lol.exe (PID: 1076)
- curl.exe (PID: 4820)
- curl.exe (PID: 5532)
- hghufrrlpzqp.exe (PID: 6292)
Manual execution by a user
- CryptoTweakV22.exe (PID: 2660)
Reads the software policy settings
- lsass.exe (PID: 768)
- WerFault.exe (PID: 3356)
Create files in a temporary directory
- CryptoTweakV22.exe (PID: 2660)
- EwQLxOSLxoJkxT.exe (PID: 5888)
- CryptoTweakV22.exe (PID: 4284)
- EwQLxOSLxoJkxT.exe (PID: 5548)
Creates files or folders in the user directory
- CryptoTweakV22.exe (PID: 2660)
- EwQLxOSLxoJkxT.exe (PID: 5548)
- WerFault.exe (PID: 3356)
The executable file from the user directory is run by the Powershell process
- CryptoTweakV22.exe (PID: 6444)
Checks proxy server information
- EwQLxOSLxoJkxT.exe (PID: 5548)
- lol.exe (PID: 1076)
- WerFault.exe (PID: 3356)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 4164)
- powershell.exe (PID: 420)
- powershell.exe (PID: 4004)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 4164)
- powershell.exe (PID: 420)
- powershell.exe (PID: 4004)
PyInstaller has been detected (YARA)
- EwQLxOSLxoJkxT.exe (PID: 5888)
- EwQLxOSLxoJkxT.exe (PID: 5548)
Checks operating system version
- EwQLxOSLxoJkxT.exe (PID: 5548)
Attempting to use instant messaging service
- EwQLxOSLxoJkxT.exe (PID: 5548)
- svchost.exe (PID: 2256)
UPX packer has been detected
- EwQLxOSLxoJkxT.exe (PID: 5548)
- dialer.exe (PID: 5304)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
243
Monitored processes
190
Malicious processes
89
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 240 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | sc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 420 | C:\WINDOWS\system32\WindowsPowerShell\v1.0\powershell.exe Add-MpPreference -ExclusionPath @($env:UserProfile, $env:ProgramData) -ExclusionExtension '.exe' -Force | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | CryptoTweakV22.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 476 | C:\WINDOWS\system32\svchost.exe -k DcomLaunch -p -s LSM | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 488 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | CryptoTweakV22.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 536 | "C:\Program Files\Microsoft Update Health Tools\uhssvc.exe" | C:\Program Files\Microsoft Update Health Tools\uhssvc.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Update Health Service Version: 10.0.19041.3626 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 684 | winlogon.exe | C:\Windows\System32\winlogon.exe | — | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Logon Application Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 768 | C:\WINDOWS\system32\lsass.exe | C:\Windows\System32\lsass.exe | wininit.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Local Security Authority Process Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 776 | C:\Windows\System32\RuntimeBroker.exe -Embedding | C:\Windows\System32\RuntimeBroker.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Runtime Broker Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 852 | "dwm.exe" | C:\Windows\System32\dwm.exe | winlogon.exe | ||||||||||||
User: DWM-1 Company: Microsoft Corporation Integrity Level: SYSTEM Description: Desktop Window Manager Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 964 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | sc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
177 824
Read events
176 918
Write events
588
Delete events
318
Modification events
| (PID) Process: | (4552) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:000000000005025A |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456033BCEE44DE41B4E8AEC331E84F566D2 | |||
| (PID) Process: | (4552) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FeatureUsage\AppBadgeUpdated |
| Operation: | write | Name: | Chrome |
Value: 5 | |||
| (PID) Process: | (6580) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6580) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6580) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (6580) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (6580) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6580) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (6580) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6580) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
Executable files
181
Suspicious files
316
Text files
1 652
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6580 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6580 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6580 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF11e8f6.TMP | — | |
MD5:— | SHA256:— | |||
| 6580 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6580 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6580 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF11e8f6.TMP | — | |
MD5:— | SHA256:— | |||
| 6580 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6580 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6580 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:723783C35EAEEE1492EDB30847AE6750 | SHA256:C29323F784CF873BF34992E7A2B4630B19641BF42980109E31D5AF2D487DF6F8 | |||
| 1620 | svchost.exe | C:\Windows\Prefetch\SVCHOST.EXE-2E4E3AC7.pf | binary | |
MD5:205F8C295F23F9E6E54B1E59C4245AB7 | SHA256:734A71FF66263D752B250666BE16D009C5C20A66A2C7ABA41143F572F10AEF5B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
90
DNS requests
56
Threats
41
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2212 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1168 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1168 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6832 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
2968 | svchost.exe | GET | 304 | 2.23.197.184:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2468 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6836 | chrome.exe | 140.82.121.3:443 | github.com | GITHUB | US | unknown |
6580 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6836 | chrome.exe | 108.177.127.84:443 | accounts.google.com | GOOGLE | US | unknown |
6836 | chrome.exe | 185.199.110.154:443 | github.githubassets.com | FASTLY | US | unknown |
6836 | chrome.exe | 185.199.110.133:443 | avatars.githubusercontent.com | FASTLY | US | unknown |
6836 | chrome.exe | 185.199.111.133:443 | avatars.githubusercontent.com | FASTLY | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
github.com |
| shared |
accounts.google.com |
| whitelisted |
github.githubassets.com |
| whitelisted |
avatars.githubusercontent.com |
| whitelisted |
camo.githubusercontent.com |
| shared |
github-cloud.s3.amazonaws.com |
| shared |
user-images.githubusercontent.com |
| whitelisted |
content-autofill.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Misc activity | ET INFO Pastebin Service Domain in DNS Lookup (rentry .co) |
5548 | EwQLxOSLxoJkxT.exe | Misc activity | ET INFO Observed Pastebin Service Domain (rentry .co in TLS SNI) |
5548 | EwQLxOSLxoJkxT.exe | Misc activity | ET INFO Observed Pastebin Service Domain (rentry .co in TLS SNI) |
5548 | EwQLxOSLxoJkxT.exe | Misc activity | ET INFO Observed Pastebin Service Domain (rentry .co in TLS SNI) |
5548 | EwQLxOSLxoJkxT.exe | Misc activity | ET INFO Observed Pastebin Service Domain (rentry .co in TLS SNI) |
2256 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
5548 | EwQLxOSLxoJkxT.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
2256 | svchost.exe | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
5548 | EwQLxOSLxoJkxT.exe | Misc activity | ET INFO File Sharing Related Domain in TLS SNI (gofile .io) |
2256 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain in DNS Lookup (geolocation-db .com) |
1 ETPRO signatures available at the full report