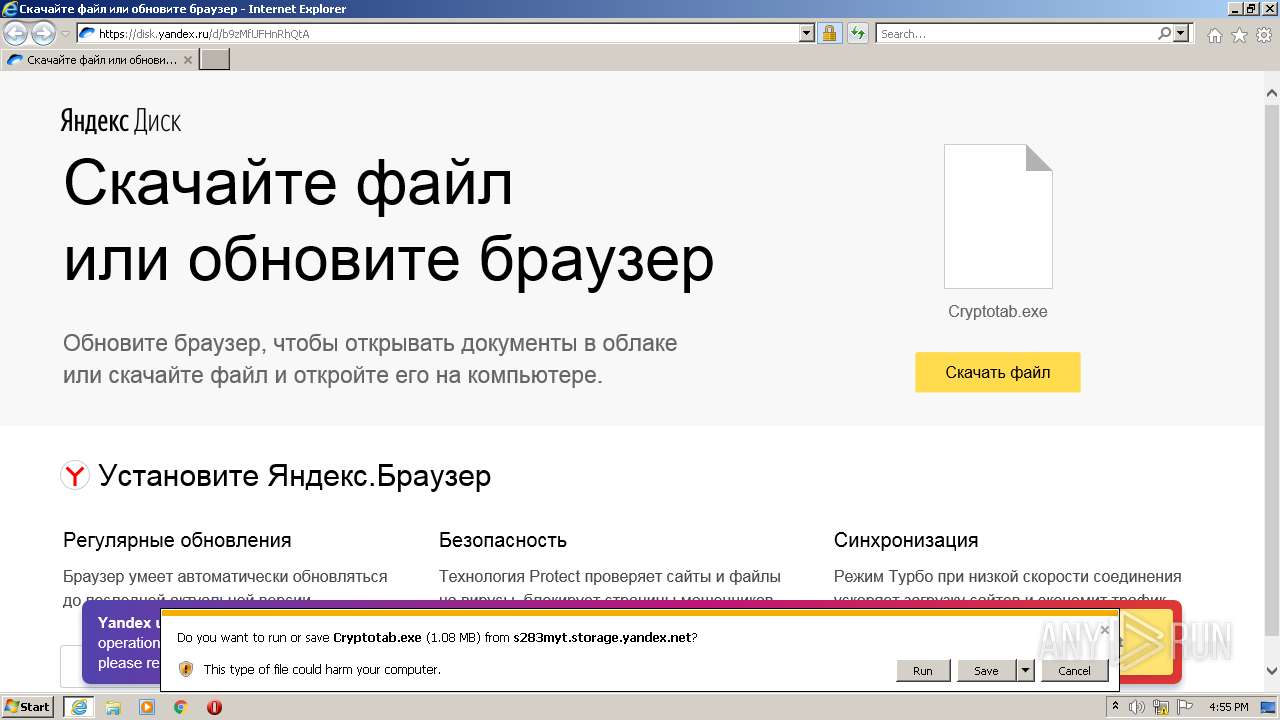
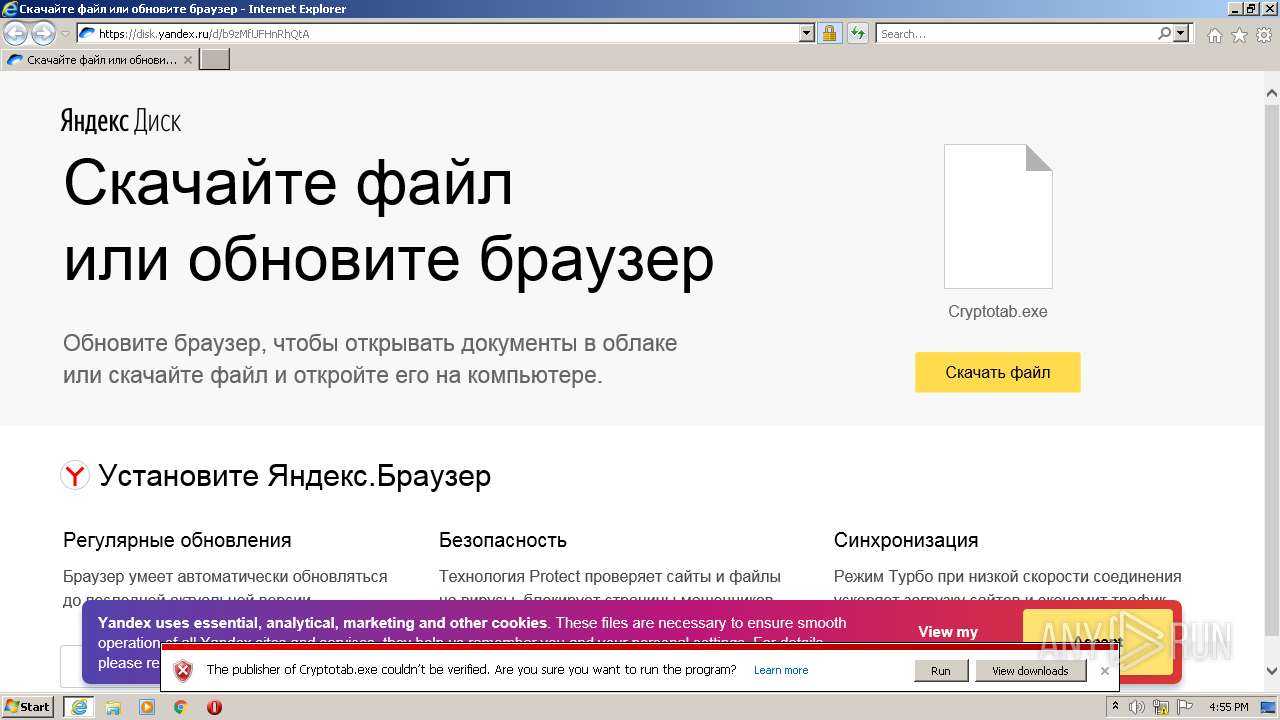
| URL: | https://disk.yandex.ru/d/b9zMfUFHnRhQtA |
| Full analysis: | https://app.any.run/tasks/7f03f3ea-bf79-462e-a5e3-42b2862eec2f |
| Verdict: | Malicious activity |
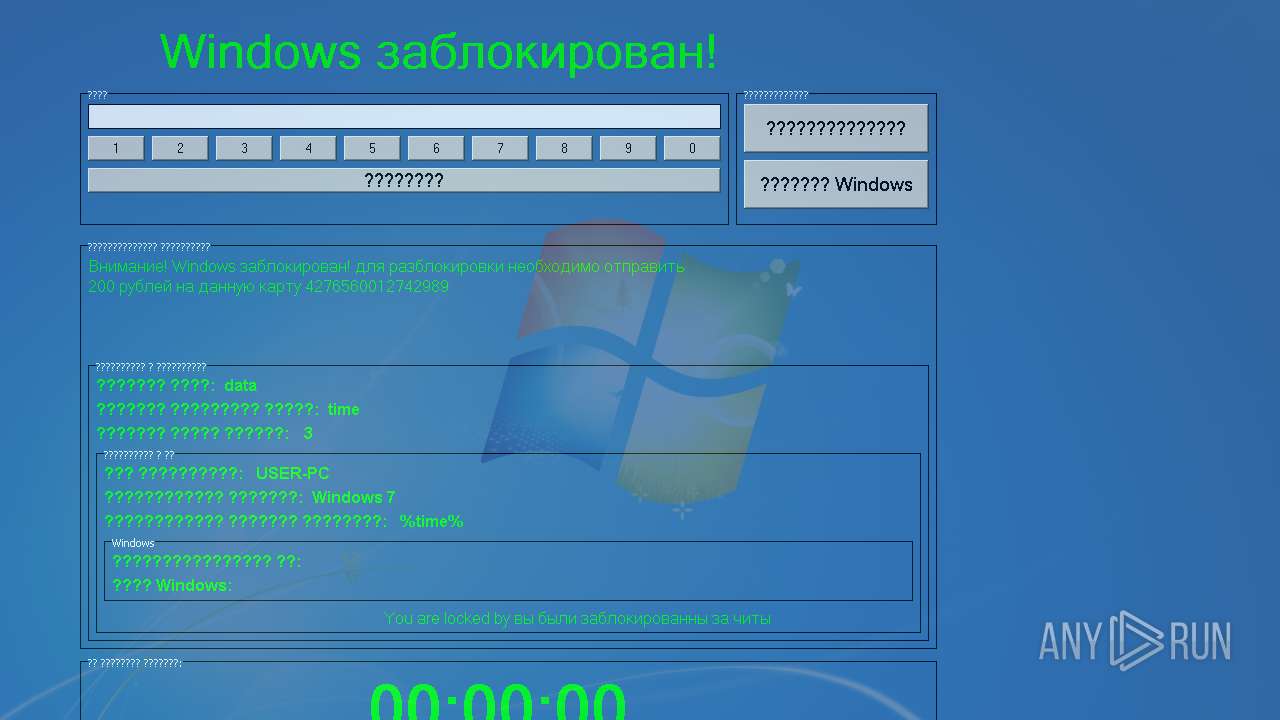
| Threats: | njRAT is a remote access trojan. It is one of the most widely accessible RATs on the market that features an abundance of educational information. Interested attackers can even find tutorials on YouTube. This allows it to become one of the most popular RATs in the world. |
| Analysis date: | February 02, 2022, 16:55:06 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 0D712D0D3A5F430A93070837B83418F0 |
| SHA1: | ACE976CFBA9B005BC1CB955FF4514BB35F5919DC |
| SHA256: | B23F35FDBFAB8482057BD631581488E93106D70374E0F58D5653B9CF98C9072D |
| SSDEEP: | 3:N8U2WuoC5j:2U27oCF |
MALICIOUS
Application was dropped or rewritten from another process
- Cryptotab.exe (PID: 2440)
- server.exe (PID: 1788)
- StUpdate.exe (PID: 2776)
- StUpdate.exe (PID: 1780)
- tmp6AD1.tmp.exe (PID: 3988)
- tmp6AD1.tmp.exe (PID: 2344)
Writes to a start menu file
- server.exe (PID: 1788)
Uses Task Scheduler to run other applications
- server.exe (PID: 1788)
Connects to CnC server
- server.exe (PID: 1788)
NJRAT was detected
- server.exe (PID: 1788)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 2148)
Changes the login/logoff helper path in the registry
- tmp6AD1.tmp.exe (PID: 2344)
Changes the autorun value in the registry
- tmp6AD1.tmp.exe (PID: 2344)
Drops executable file immediately after starts
- tmp6AD1.tmp.exe (PID: 3988)
SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3264)
- iexplore.exe (PID: 3764)
Drops a file with a compile date too recent
- iexplore.exe (PID: 3264)
- iexplore.exe (PID: 3764)
- Cryptotab.exe (PID: 2440)
- server.exe (PID: 1788)
Executable content was dropped or overwritten
- iexplore.exe (PID: 3264)
- iexplore.exe (PID: 3764)
- Cryptotab.exe (PID: 2440)
- server.exe (PID: 1788)
- tmp6AD1.tmp.exe (PID: 3988)
Checks supported languages
- Cryptotab.exe (PID: 2440)
- server.exe (PID: 1788)
- StUpdate.exe (PID: 1780)
- tmp6AD1.tmp.exe (PID: 3988)
- tmp6AD1.tmp.exe (PID: 2344)
Creates files in the user directory
- Cryptotab.exe (PID: 2440)
- server.exe (PID: 1788)
Reads the computer name
- Cryptotab.exe (PID: 2440)
- server.exe (PID: 1788)
- tmp6AD1.tmp.exe (PID: 3988)
- StUpdate.exe (PID: 1780)
- tmp6AD1.tmp.exe (PID: 2344)
Starts itself from another location
- Cryptotab.exe (PID: 2440)
Uses NETSH.EXE for network configuration
- server.exe (PID: 1788)
Reads Environment values
- netsh.exe (PID: 3352)
- netsh.exe (PID: 3840)
- netsh.exe (PID: 2248)
- server.exe (PID: 1788)
Executed via Task Scheduler
- StUpdate.exe (PID: 2776)
- StUpdate.exe (PID: 1780)
Drops a file with too old compile date
- server.exe (PID: 1788)
- tmp6AD1.tmp.exe (PID: 3988)
INFO
Reads settings of System Certificates
- iexplore.exe (PID: 3764)
- iexplore.exe (PID: 3264)
Reads internet explorer settings
- iexplore.exe (PID: 3264)
Reads the computer name
- iexplore.exe (PID: 3764)
- iexplore.exe (PID: 3264)
- netsh.exe (PID: 3352)
- netsh.exe (PID: 3840)
- netsh.exe (PID: 2248)
- schtasks.exe (PID: 2148)
Creates files in the user directory
- iexplore.exe (PID: 3264)
- iexplore.exe (PID: 3764)
Changes settings of System certificates
- iexplore.exe (PID: 3764)
Application launched itself
- iexplore.exe (PID: 3764)
Checks Windows Trust Settings
- iexplore.exe (PID: 3264)
- iexplore.exe (PID: 3764)
Modifies the phishing filter of IE
- iexplore.exe (PID: 3764)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3764)
Checks supported languages
- iexplore.exe (PID: 3764)
- iexplore.exe (PID: 3264)
- netsh.exe (PID: 3352)
- netsh.exe (PID: 3840)
- schtasks.exe (PID: 2148)
- netsh.exe (PID: 2248)
Changes internet zones settings
- iexplore.exe (PID: 3764)
Reads the date of Windows installation
- iexplore.exe (PID: 3764)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
56
Monitored processes
12
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1780 | C:\Users\admin\AppData\Local\Temp/StUpdate.exe | C:\Users\admin\AppData\Local\Temp\StUpdate.exe | taskeng.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1788 | "C:\Users\admin\AppData\Local\Temp\server.exe" | C:\Users\admin\AppData\Local\Temp\server.exe | Cryptotab.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2148 | schtasks /create /sc minute /mo 1 /tn StUpdate /tr C:\Users\admin\AppData\Local\Temp/StUpdate.exe | C:\Windows\system32\schtasks.exe | — | server.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2248 | netsh firewall add allowedprogram "C:\Users\admin\AppData\Local\Temp\server.exe" "server.exe" ENABLE | C:\Windows\system32\netsh.exe | — | server.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2344 | "C:\Users\admin\AppData\Local\Temp\3582-490\tmp6AD1.tmp.exe" | C:\Users\admin\AppData\Local\Temp\3582-490\tmp6AD1.tmp.exe | tmp6AD1.tmp.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2440 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\Cryptotab.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\Cryptotab.exe | iexplore.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2776 | C:\Users\admin\AppData\Local\Temp/StUpdate.exe | C:\Users\admin\AppData\Local\Temp\StUpdate.exe | — | taskeng.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 3264 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3764 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3352 | netsh firewall add allowedprogram "C:\Users\admin\AppData\Local\Temp\server.exe" "server.exe" ENABLE | C:\Windows\system32\netsh.exe | — | server.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3764 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://disk.yandex.ru/d/b9zMfUFHnRhQtA" | C:\Program Files\Internet Explorer\iexplore.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
20 957
Read events
20 620
Write events
332
Delete events
5
Modification events
| (PID) Process: | (3764) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3764) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3764) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30939221 | |||
| (PID) Process: | (3764) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3764) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30939221 | |||
| (PID) Process: | (3764) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3764) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3764) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3764) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3764) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
34
Suspicious files
23
Text files
20
Unknown types
16
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3264 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 3264 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\68FAF71AF355126BCA00CE2E73CC7374_77B682CF3AAC7B00161DFFF7DEA4CC8C | der | |
MD5:— | SHA256:— | |||
| 3264 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\1B1F4BA66CDBFEC85A20E11BF729AF23_AA85F8F9DAFF33153B5AEC2E983B94B6 | der | |
MD5:— | SHA256:— | |||
| 3264 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\1B1F4BA66CDBFEC85A20E11BF729AF23_AA85F8F9DAFF33153B5AEC2E983B94B6 | binary | |
MD5:— | SHA256:— | |||
| 3264 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E887E036775F4159E2816B7B9E527E5F_D0F3378B0A5E09534CCA8798569940EB | binary | |
MD5:— | SHA256:— | |||
| 3264 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\68FAF71AF355126BCA00CE2E73CC7374_77B682CF3AAC7B00161DFFF7DEA4CC8C | binary | |
MD5:— | SHA256:— | |||
| 3264 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E887E036775F4159E2816B7B9E527E5F_ADE58CF9589C2D8854882E94BDAA0990 | der | |
MD5:— | SHA256:— | |||
| 3264 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E887E036775F4159E2816B7B9E527E5F_D0F3378B0A5E09534CCA8798569940EB | der | |
MD5:— | SHA256:— | |||
| 3264 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\OK70E33S.txt | text | |
MD5:— | SHA256:— | |||
| 3264 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E887E036775F4159E2816B7B9E527E5F_ADE58CF9589C2D8854882E94BDAA0990 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
35
DNS requests
18
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3264 | iexplore.exe | GET | 200 | 2.16.186.163:80 | http://subca.ocsp-certum.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBR5iK7tYk9tqQEoeQhZNkKcAol9bgQUjEPEy22YwaechGnr30oNYJY6w%2FsCEQCTkoVAAWVxX5R%2FKI%2FvyZso | unknown | der | 1.50 Kb | whitelisted |
3264 | iexplore.exe | GET | 200 | 5.45.205.243:80 | http://yandex.ocsp-responder.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBStniMGfahyWUWDEeSLUFbNR9JLAgQUN1zjGeCyjqGoTtLPq9Dc4wtcNU0CEFDje3I7MASsbiBNGm3xtrE%3D | RU | der | 1.48 Kb | whitelisted |
3264 | iexplore.exe | GET | 200 | 5.45.205.243:80 | http://yandex.ocsp-responder.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBStniMGfahyWUWDEeSLUFbNR9JLAgQUN1zjGeCyjqGoTtLPq9Dc4wtcNU0CEDOB3I9UeYBPeBwD%2BBgMzcg%3D | RU | der | 1.48 Kb | whitelisted |
3264 | iexplore.exe | GET | 200 | 5.45.205.243:80 | http://yandex.ocsp-responder.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBStniMGfahyWUWDEeSLUFbNR9JLAgQUN1zjGeCyjqGoTtLPq9Dc4wtcNU0CEHoHzpzggMLl%2Fc8M87bvClo%3D | RU | der | 1.48 Kb | whitelisted |
3264 | iexplore.exe | GET | 200 | 5.45.205.243:80 | http://yandex.ocsp-responder.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBStniMGfahyWUWDEeSLUFbNR9JLAgQUN1zjGeCyjqGoTtLPq9Dc4wtcNU0CED3qPfT1yuXcCePg2RUC75o%3D | RU | der | 1.48 Kb | whitelisted |
3264 | iexplore.exe | GET | 200 | 5.45.205.243:80 | http://yandex.ocsp-responder.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBStniMGfahyWUWDEeSLUFbNR9JLAgQUN1zjGeCyjqGoTtLPq9Dc4wtcNU0CEGlTKIPuh018TJJ9M3J8QXw%3D | RU | der | 1.48 Kb | whitelisted |
3264 | iexplore.exe | GET | 200 | 2.16.186.163:80 | http://subca.ocsp-certum.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTYOkzrrCGQj08njZXbUQQpkoUmuQQUCHbNywf%2FJPbFze27kLzihDdGdfcCEQDkBUeDDgxkUpdvejVJwN1I | unknown | der | 1.54 Kb | whitelisted |
3764 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
3264 | iexplore.exe | GET | 200 | 23.32.238.232:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?ee603c9ebd0850fb | US | compressed | 4.70 Kb | whitelisted |
3764 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3264 | iexplore.exe | 93.158.134.119:443 | mc.yandex.ru | YANDEX LLC | RU | whitelisted |
3764 | iexplore.exe | 13.107.22.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
3264 | iexplore.exe | 87.250.250.50:443 | disk.yandex.ru | YANDEX LLC | RU | whitelisted |
3764 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3764 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3264 | iexplore.exe | 77.88.21.127:443 | downloader.disk.yandex.ru | YANDEX LLC | RU | whitelisted |
3264 | iexplore.exe | 213.180.200.12:443 | s283myt.storage.yandex.net | YANDEX LLC | RU | whitelisted |
1788 | server.exe | 82.202.167.205:5552 | — | JSC ISPsystem | RU | malicious |
3764 | iexplore.exe | 87.250.250.50:443 | disk.yandex.ru | YANDEX LLC | RU | whitelisted |
3264 | iexplore.exe | 178.154.131.217:443 | yastatic.net | YANDEX LLC | RU | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
disk.yandex.ru |
| shared |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
subca.ocsp-certum.com |
| whitelisted |
yandex.ocsp-responder.com |
| whitelisted |
mc.yandex.ru |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
yastatic.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1788 | server.exe | A Network Trojan was detected | ET TROJAN Generic njRAT/Bladabindi CnC Activity (ll) |
1788 | server.exe | A Network Trojan was detected | ET TROJAN njrat ver 0.7d Malware CnC Callback (Remote Desktop) |
3 ETPRO signatures available at the full report