| File name: | b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe |
| Full analysis: | https://app.any.run/tasks/78d3a0c9-95e0-4cb6-adeb-f2a6359406a8 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | July 02, 2024, 22:48:47 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows |
| MD5: | 2B0D0F3CB0A66CF1E42DB5890DC346FC |
| SHA1: | DA018FD72ACABB1C5E9D1741F1CAB7A281BDB25A |
| SHA256: | B1F2068201C29F3B00AEEDC0911498043D7C204A860CA16B3FEF47FC19FC2B22 |
| SSDEEP: | 98304:f4/EkX8wm/uXKOhRltBlfs/2rTHKUdisSgblkpTFz0LJamtgrajQkRkKNI8ZKhp6:ItRLlx6mFw4FITbxZbT/0B |
MALICIOUS
Drops the executable file immediately after the start
- b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe (PID: 2448)
- b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe (PID: 4052)
- MyApp.exe (PID: 6324)
- b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe (PID: 5272)
- MyApp.exe (PID: 6360)
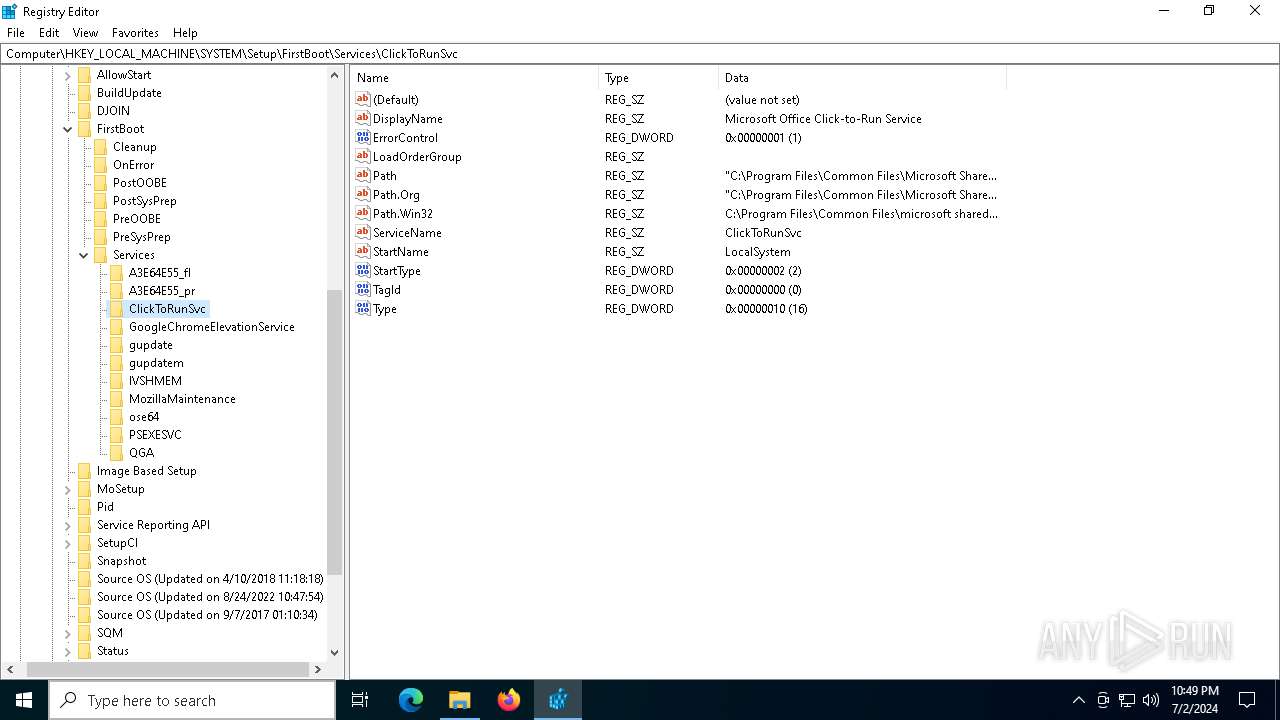
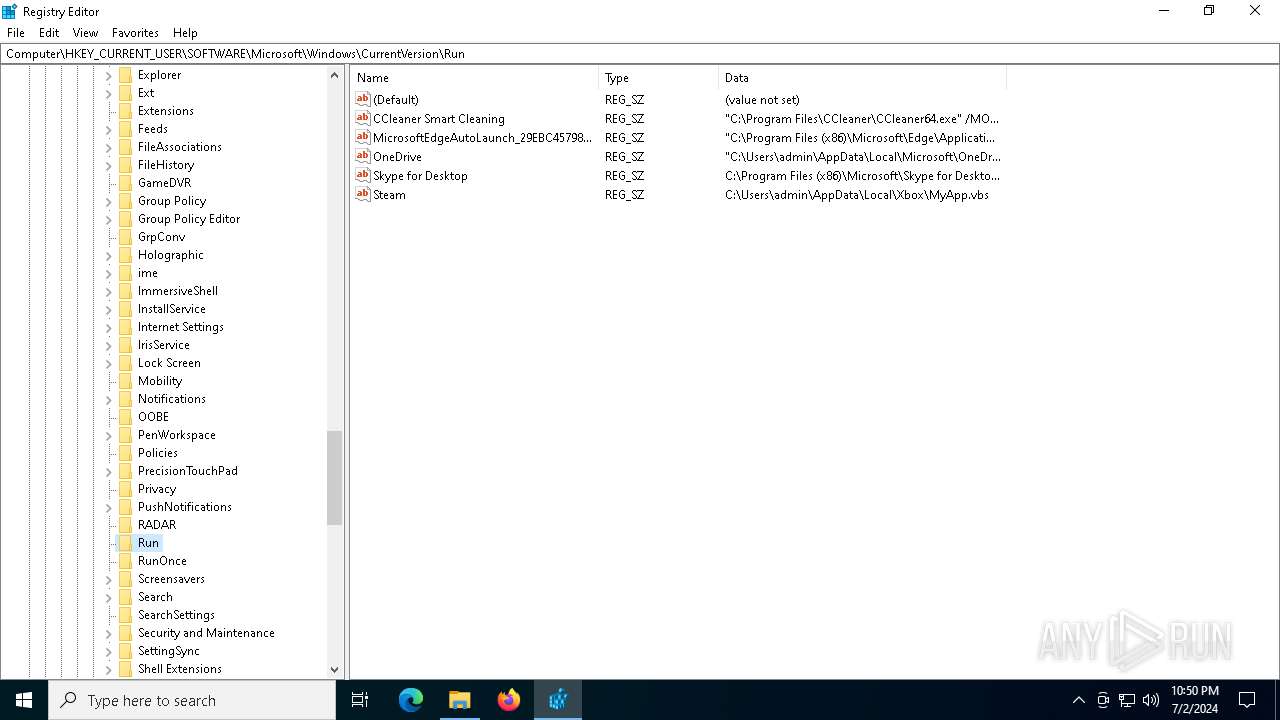
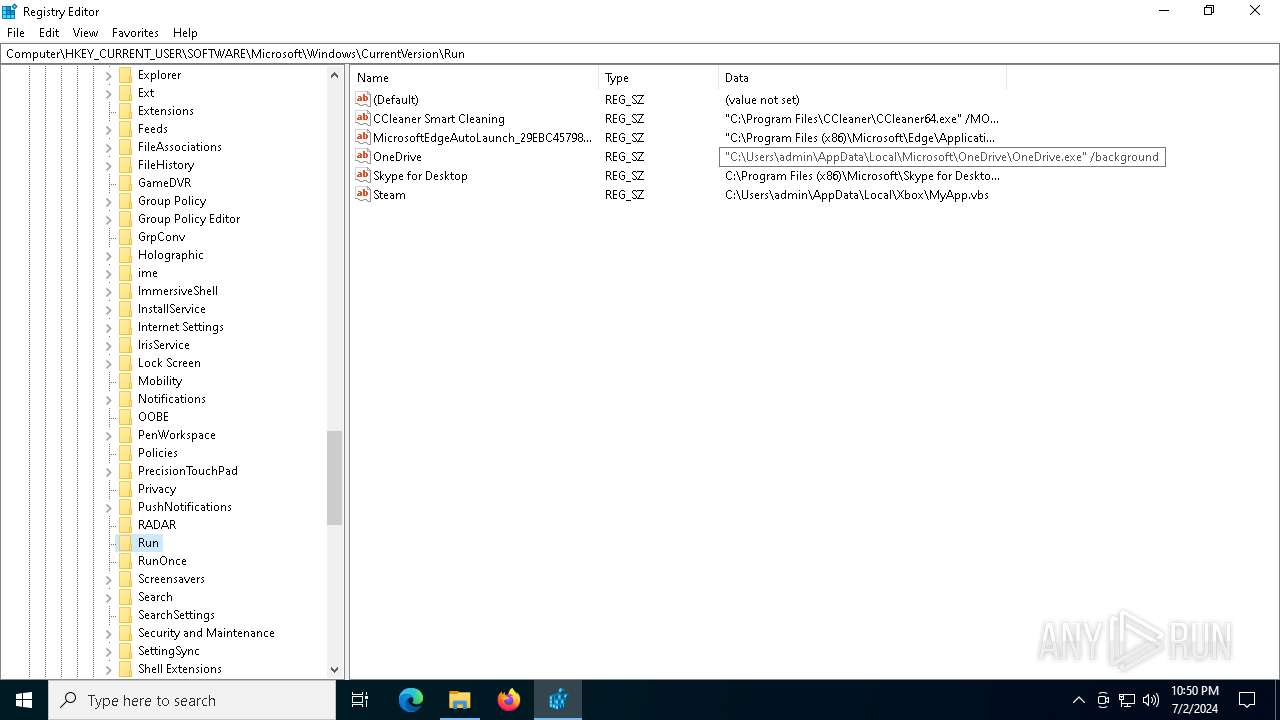
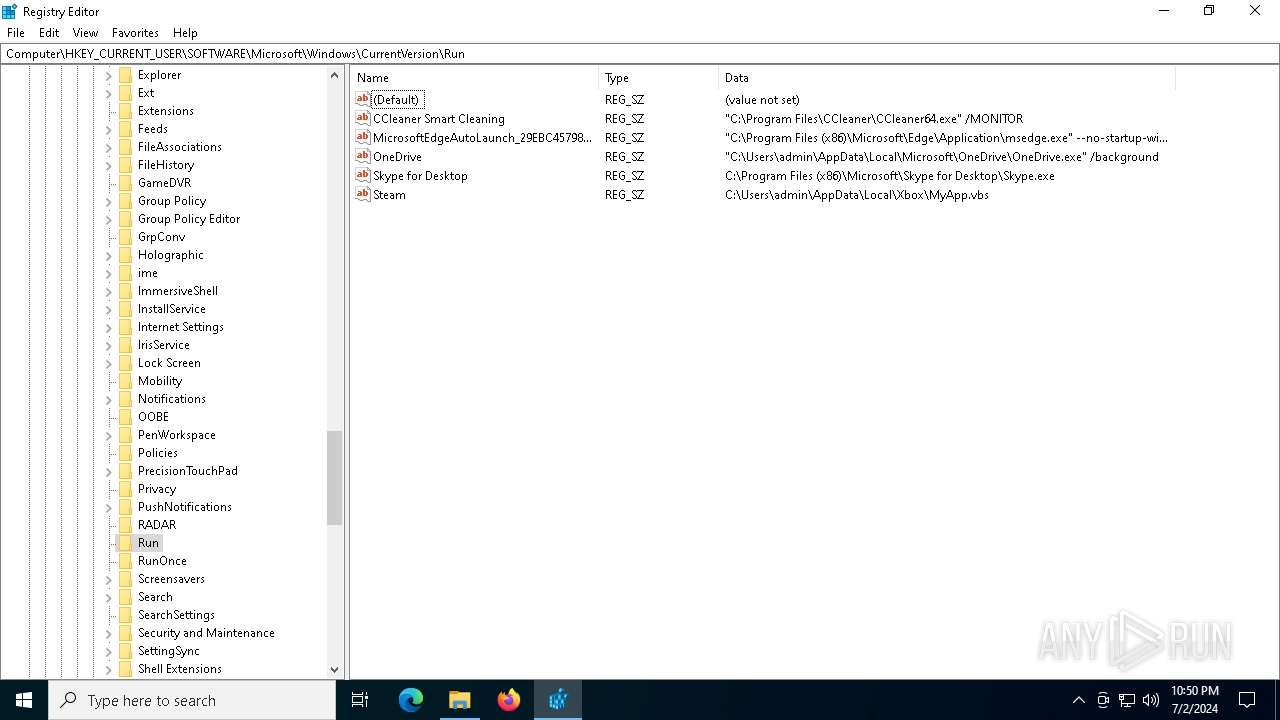
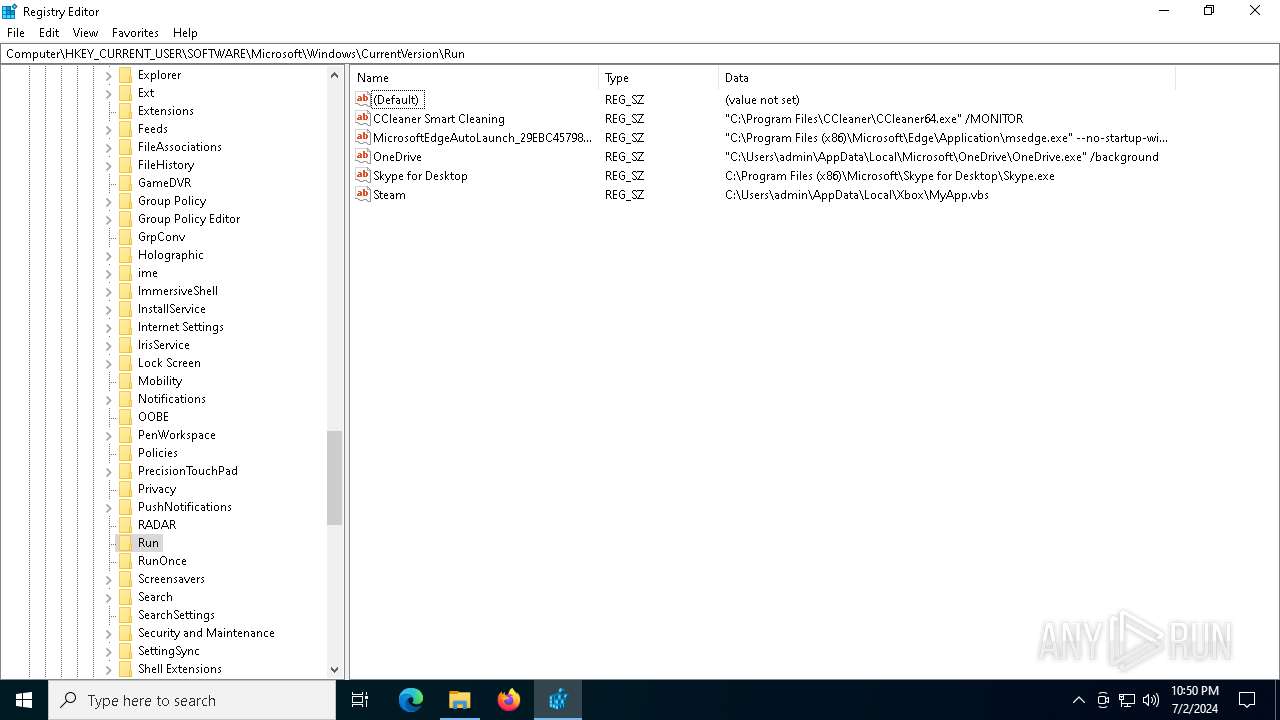
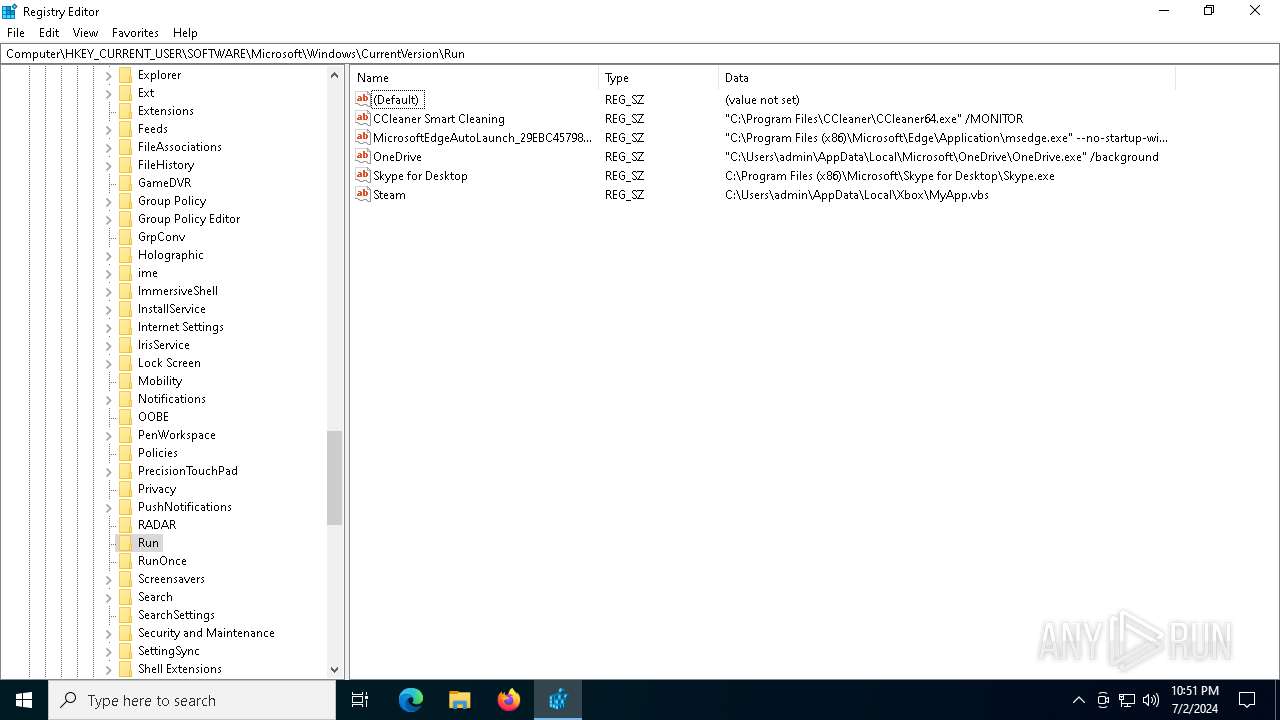
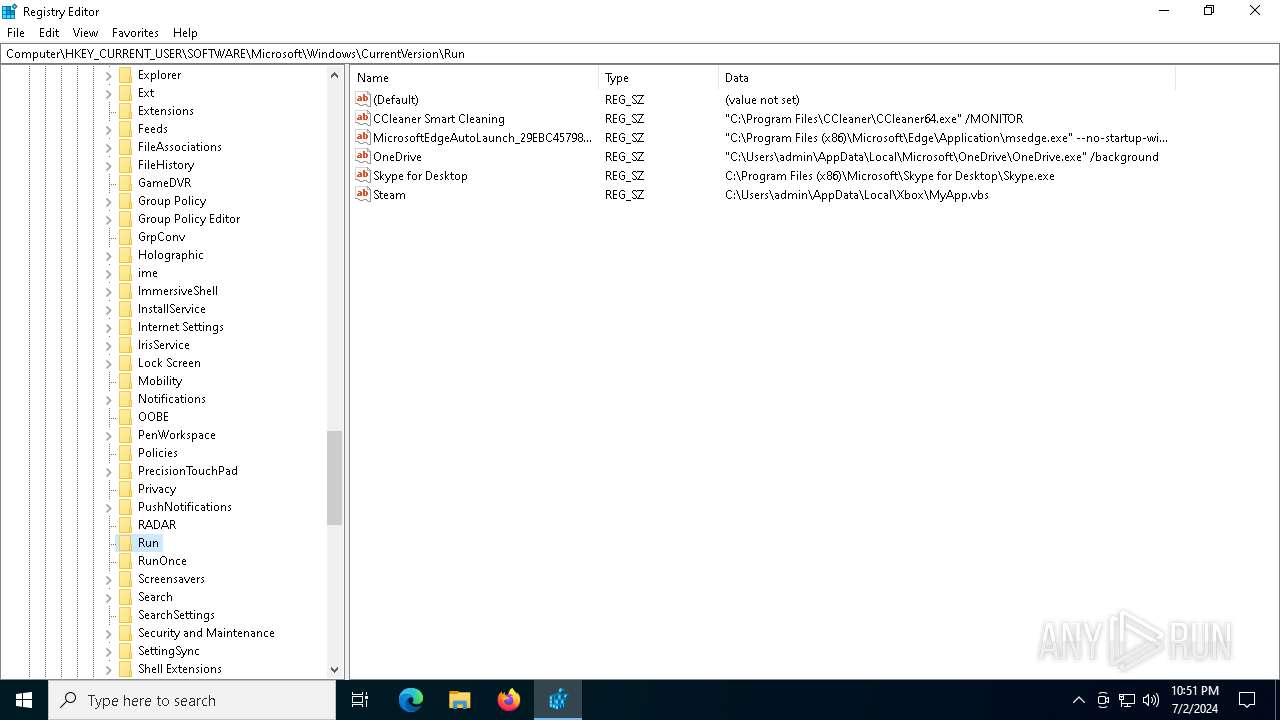
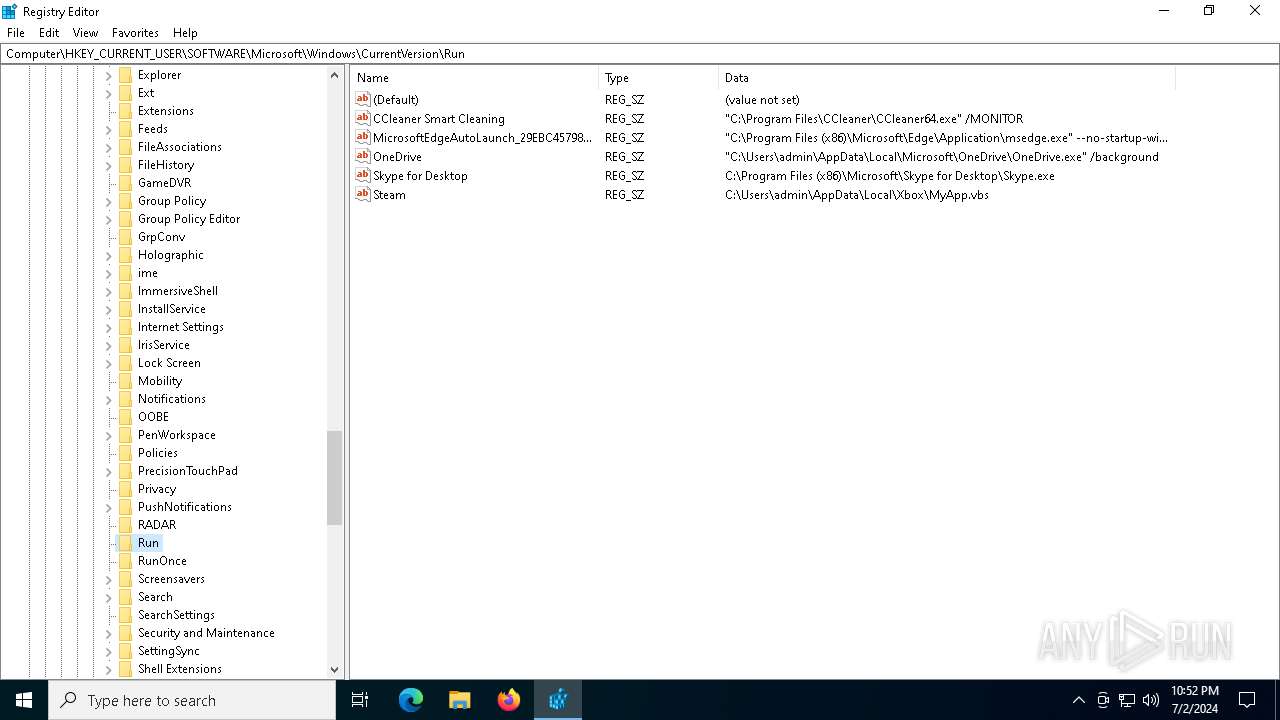
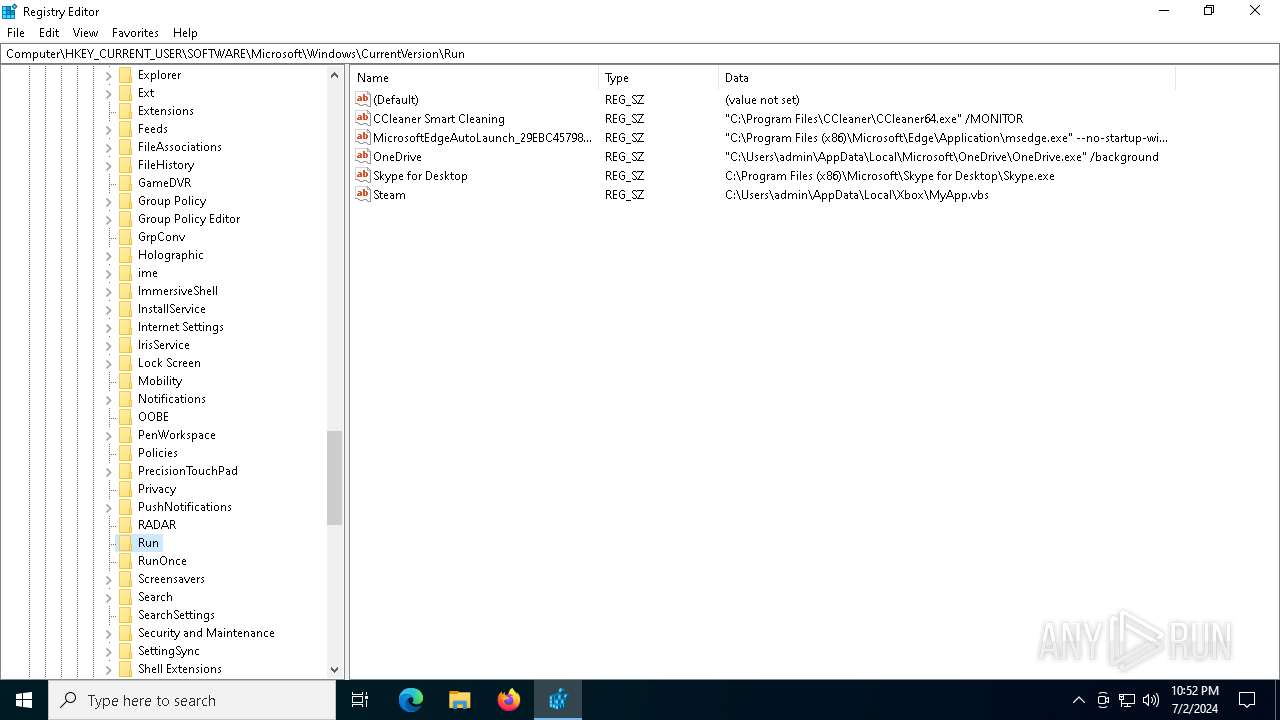
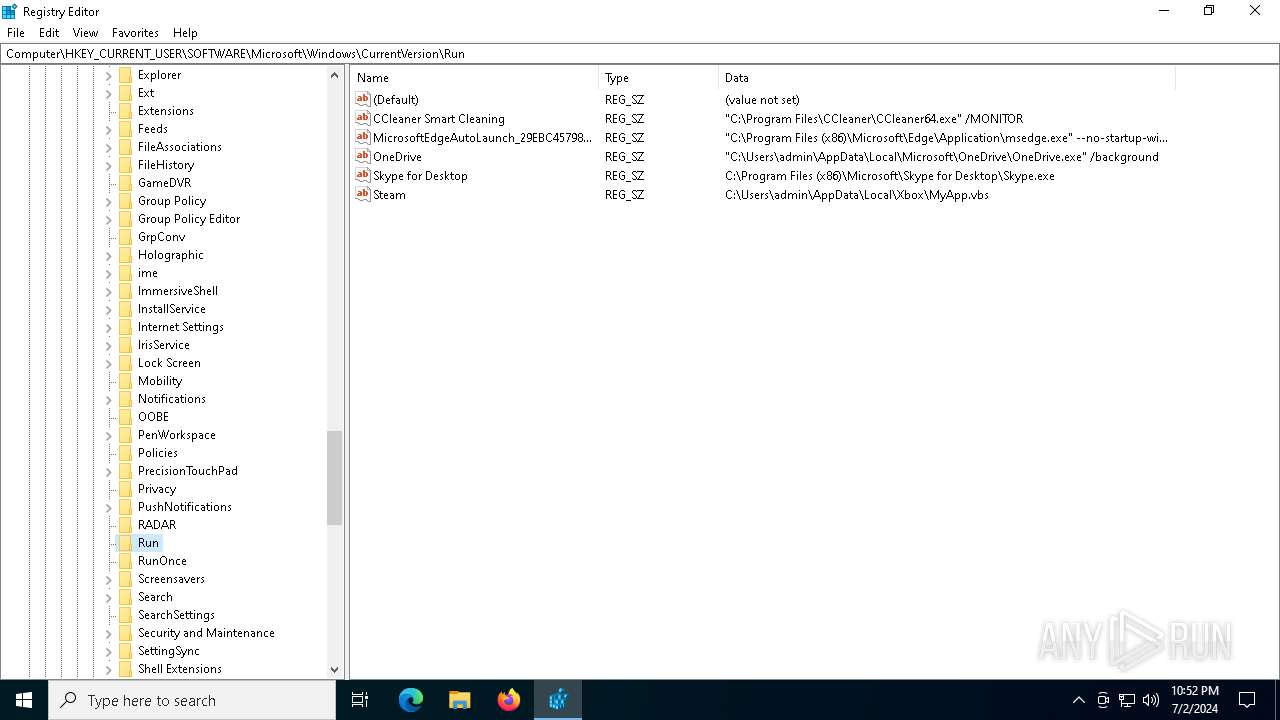
Changes the autorun value in the registry
- b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe (PID: 4052)
ASYNCRAT has been detected (MUTEX)
- cvtres.exe (PID: 7012)
ASYNCRAT has been detected (YARA)
- cvtres.exe (PID: 7012)
SUSPICIOUS
Process drops legitimate windows executable
- b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe (PID: 2448)
- MyApp.exe (PID: 6324)
- b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe (PID: 5272)
- MyApp.exe (PID: 6360)
The process drops C-runtime libraries
- b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe (PID: 2448)
- MyApp.exe (PID: 6324)
- b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe (PID: 5272)
- MyApp.exe (PID: 6360)
Application launched itself
- b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe (PID: 2448)
- MyApp.exe (PID: 6324)
- b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe (PID: 5272)
- MyApp.exe (PID: 6360)
Executable content was dropped or overwritten
- b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe (PID: 2448)
- b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe (PID: 4052)
- MyApp.exe (PID: 6324)
- MyApp.exe (PID: 6360)
- b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe (PID: 5272)
Process drops python dynamic module
- b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe (PID: 2448)
- MyApp.exe (PID: 6324)
- MyApp.exe (PID: 6360)
- b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe (PID: 5272)
Loads Python modules
- b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe (PID: 4052)
- MyApp.exe (PID: 6476)
- b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe (PID: 6316)
- MyApp.exe (PID: 6400)
Reads security settings of Internet Explorer
- b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe (PID: 4052)
- MyApp.exe (PID: 6476)
- b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe (PID: 6316)
- MyApp.exe (PID: 6400)
The process checks if it is being run in the virtual environment
- b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe (PID: 4052)
Reads the date of Windows installation
- b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe (PID: 4052)
- b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe (PID: 6316)
Starts itself from another location
- b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe (PID: 4052)
- b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe (PID: 6316)
Connects to unusual port
- cvtres.exe (PID: 7012)
INFO
Checks supported languages
- b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe (PID: 2448)
- b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe (PID: 4052)
- TextInputHost.exe (PID: 2120)
- MyApp.exe (PID: 6476)
- MyApp.exe (PID: 6324)
- cvtres.exe (PID: 7012)
- b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe (PID: 5272)
- MyApp.exe (PID: 6360)
- b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe (PID: 6316)
- MyApp.exe (PID: 6400)
Reads the computer name
- b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe (PID: 2448)
- b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe (PID: 4052)
- TextInputHost.exe (PID: 2120)
- MyApp.exe (PID: 6476)
- MyApp.exe (PID: 6324)
- cvtres.exe (PID: 7012)
- b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe (PID: 5272)
- MyApp.exe (PID: 6360)
- b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe (PID: 6316)
- MyApp.exe (PID: 6400)
Create files in a temporary directory
- b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe (PID: 2448)
- b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe (PID: 4052)
- MyApp.exe (PID: 6324)
- MyApp.exe (PID: 6476)
- b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe (PID: 5272)
- b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe (PID: 6316)
- MyApp.exe (PID: 6360)
- MyApp.exe (PID: 6400)
Reads the machine GUID from the registry
- b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe (PID: 4052)
- MyApp.exe (PID: 6476)
- cvtres.exe (PID: 7012)
- b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe (PID: 6316)
- MyApp.exe (PID: 6400)
Manual execution by a user
- regedit.exe (PID: 5224)
- regedit.exe (PID: 5324)
- b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe (PID: 5272)
Process checks computer location settings
- b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe (PID: 4052)
- b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe (PID: 6316)
Creates files or folders in the user directory
- b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe (PID: 4052)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AsyncRat
(PID) Process(7012) cvtres.exe
C2 (1)newws.eu
Ports (1)2005
Version| Edit by Vinom Rat
Options
AutoRunfalse
MutexAsyncMutex_ruiewDFG4
InstallFolder%AppData%
Certificates
Cert1MIIE8jCCAtqgAwIBAgIQAIu8YgLOOykBZes0C87FDTANBgkqhkiG9w0BAQ0FADAaMRgwFgYDVQQDDA9Bc3luY1JBVCBTZXJ2ZXIwIBcNMjMxMDIwMTk0MTA2WhgPOTk5OTEyMzEyMzU5NTlaMBoxGDAWBgNVBAMMD0FzeW5jUkFUIFNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAKWlVzOxwMVEpaMaG8aMhHnYLKFx9LQ/W6aVV1ma0KSSEBfJ7SBrW3z1/rZ+oO2EqQDV9uYdfSc3...
Server_SignatureNbDWHBZxQGv5uN8HLnA+QBLcvhMgEbLlNZ0BZIVsPyYvfTzvNn0Tid64vT0op/T4iXUDzNvzYnItMc+dv80/BYBG4/J9G1ddp6oyMVF4AKznNWpOTZgU7JVg+We4OpFTwOtBCgJP6pq8D+mC+Or77evf7pnbehCNI1e/0fBWebPrlqJ6yqSeYFZ6EClRP8GT24aA4ZhRG4irRjPrRtSXDqQqoWsqaMAyPDdx/sPYLouRo0z4xFDpcSWF7ST4XrXXa+d7zzpkIc8tUHukc92O/cpJvG3zlOMUIAztfBHjnBBR...
Keys
AES3fb683534c3083cded8ac77ec52e49b7aefaab0159b97d0c6f5c9d2f01701cd5
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:05:06 18:01:15+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.36 |
| CodeSize: | 166400 |
| InitializedDataSize: | 95232 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb340 |
| OSVersion: | 5.2 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 4.0.0.0 |
| ProductVersionNumber: | 4.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | IIOII |
| FileDescription: | IIOII |
| FileVersion: | 6.2.6.0 |
| InternalName: | 6.2.6.0 |
| LegalCopyright: | @IIOII |
| OriginalFileName: | - |
| ProductName: | 6.2.6.0 |
| ProductVersion: | 6.2.6.0 |
Total processes
149
Monitored processes
12
Malicious processes
8
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2120 | "C:\WINDOWS\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe" -ServerName:InputApp.AppXjd5de1g66v206tj52m9d0dtpppx4cgpn.mca | C:\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Version: 123.26505.0.0 Modules
| |||||||||||||||
| 2448 | "C:\Users\admin\Desktop\b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe" | C:\Users\admin\Desktop\b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 4052 | "C:\Users\admin\Desktop\b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe" | C:\Users\admin\Desktop\b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe | b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 5224 | "C:\WINDOWS\regedit.exe" | C:\Windows\regedit.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Editor Exit code: 3221226540 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5272 | "C:\Users\admin\Desktop\b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe" | C:\Users\admin\Desktop\b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 5324 | "C:\WINDOWS\regedit.exe" | C:\Windows\regedit.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Editor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6316 | "C:\Users\admin\Desktop\b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe" | C:\Users\admin\Desktop\b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe | — | b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 6324 | "C:\Users\admin\AppData\Local\Microsoft\MyApp.exe" | C:\Users\admin\AppData\Local\Microsoft\MyApp.exe | b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 6360 | "C:\Users\admin\AppData\Local\Microsoft\MyApp.exe" | C:\Users\admin\AppData\Local\Microsoft\MyApp.exe | b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 6400 | "C:\Users\admin\AppData\Local\Microsoft\MyApp.exe" | C:\Users\admin\AppData\Local\Microsoft\MyApp.exe | — | MyApp.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
Total events
10 415
Read events
10 382
Write events
33
Delete events
0
Modification events
| (PID) Process: | (4052) b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (4052) b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (4052) b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (4052) b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (4052) b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Steam |
Value: C:\Users\admin\AppData\Local\Xbox\MyApp.vbs | |||
| (PID) Process: | (6476) MyApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6476) MyApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6476) MyApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6476) MyApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6316) b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
125
Suspicious files
8
Text files
66
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2448 | b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe | C:\Users\admin\AppData\Local\Temp\_MEI24482\_decimal.pyd | executable | |
MD5:75A0542682D8F534F4A1BA48EB32218F | SHA256:5767525D2CDD2A89DE97A11784EC0769C30935302C135F087B09894F8865BE8B | |||
| 2448 | b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe | C:\Users\admin\AppData\Local\Temp\_MEI24482\VCRUNTIME140.dll | executable | |
MD5:89A24C66E7A522F1E0016B1D0B4316DC | SHA256:3096CAFB6A21B6D28CF4FE2DD85814F599412C0FE1EF090DD08D1C03AFFE9AB6 | |||
| 2448 | b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe | C:\Users\admin\AppData\Local\Temp\_MEI24482\_bz2.pyd | executable | |
MD5:CF77513525FC652BAD6C7F85E192E94B | SHA256:8BCE02E8D44003C5301608B1722F7E26AADA2A03D731FA92A48C124DB40E2E41 | |||
| 2448 | b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe | C:\Users\admin\AppData\Local\Temp\_MEI24482\_lzma.pyd | executable | |
MD5:5FBB728A3B3ABBDD830033586183A206 | SHA256:F9BC6036D9E4D57D08848418367743FB608434C04434AB07DA9DABE4725F9A9B | |||
| 2448 | b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe | C:\Users\admin\AppData\Local\Temp\_MEI24482\_elementtree.pyd | executable | |
MD5:7D0C4AB57FDC1BD30C0E8E42CCC2AA35 | SHA256:EE8C4A8FE8EAA918A4FEE353D46F4191BD161582098B400C33220847D84797DB | |||
| 2448 | b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe | C:\Users\admin\AppData\Local\Temp\_MEI24482\_multiprocessing.pyd | executable | |
MD5:3CF091905D3CC49070B0C39848F0D48B | SHA256:7A0A1D04A326E21636A08F5F9772625F8B07BA1CE3FB2C78052BEC3CF795704A | |||
| 2448 | b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe | C:\Users\admin\AppData\Local\Temp\_MEI24482\_hashlib.pyd | executable | |
MD5:B32CB9615A9BADA55E8F20DCEA2FBF48 | SHA256:CA4F433A68C3921526F31F46D8A45709B946BBD40F04A4CFC6C245CB9EE0EAB5 | |||
| 2448 | b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe | C:\Users\admin\AppData\Local\Temp\_MEI24482\_socket.pyd | executable | |
MD5:8EA18D0EEAE9044C278D2EA7A1DBAE36 | SHA256:9822C258A9D25062E51EAFC45D62ED19722E0450A212668F6737EB3BFE3A41C2 | |||
| 2448 | b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe | C:\Users\admin\AppData\Local\Temp\_MEI24482\_queue.pyd | executable | |
MD5:C0A70188685E44E73576E3CD63FC1F68 | SHA256:E499824D58570C3130BA8EF1AC2D503E71F916C634B2708CC22E95C223F83D0A | |||
| 2448 | b1f2068201c29f3b00aeedc0911498043d7c204a860ca16b3fef47fc19fc2b22.exe | C:\Users\admin\AppData\Local\Temp\_MEI24482\_ssl.pyd | executable | |
MD5:5A393BB4F3AE499541356E57A766EB6A | SHA256:B6593B3AF0E993FD5043A7EAB327409F4BF8CDCD8336ACA97DBE6325AEFDB047 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
82
DNS requests
28
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2276 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
2276 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
3040 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | unknown |
4656 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | unknown |
1544 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
1776 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
4656 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | unknown |
5288 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
1776 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
1428 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4524 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2276 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3168 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2276 | svchost.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
2276 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
3040 | OfficeClickToRun.exe | 20.42.65.94:443 | self.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
3040 | OfficeClickToRun.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.bing.com |
| whitelisted |
r.bing.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
login.live.com |
| whitelisted |
mcr-ring-fallback.msedge.net |
| unknown |