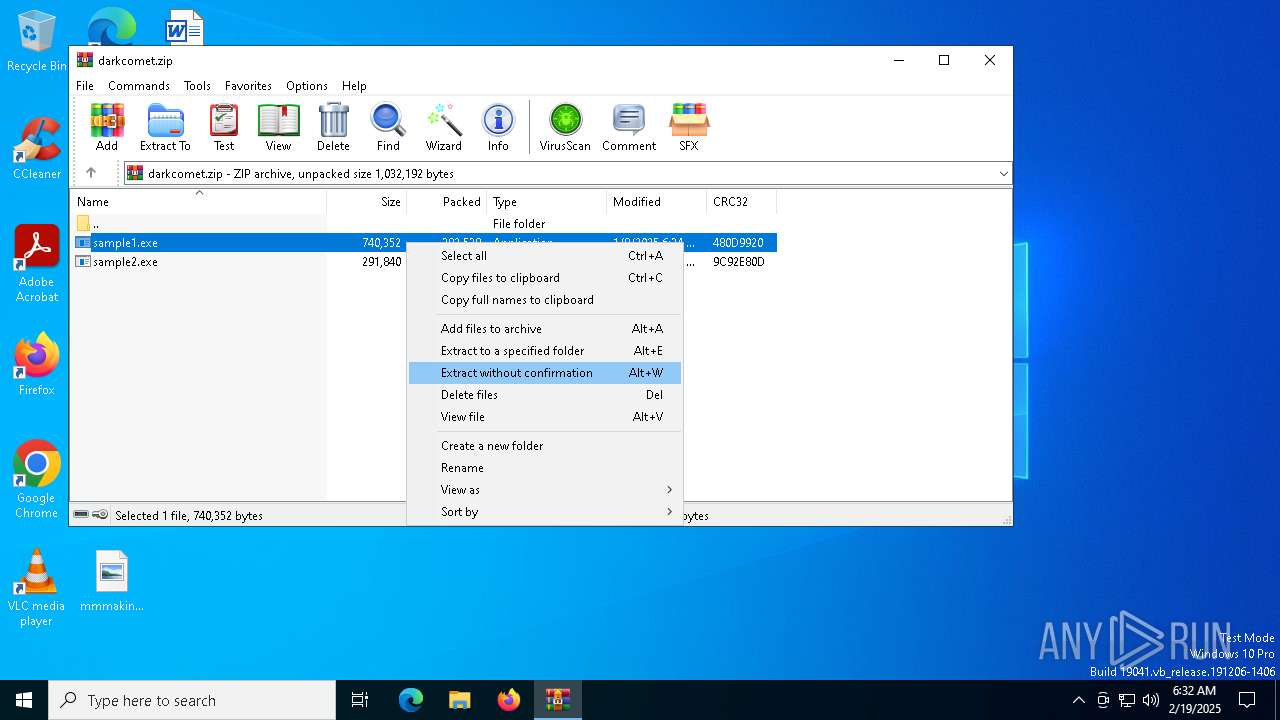
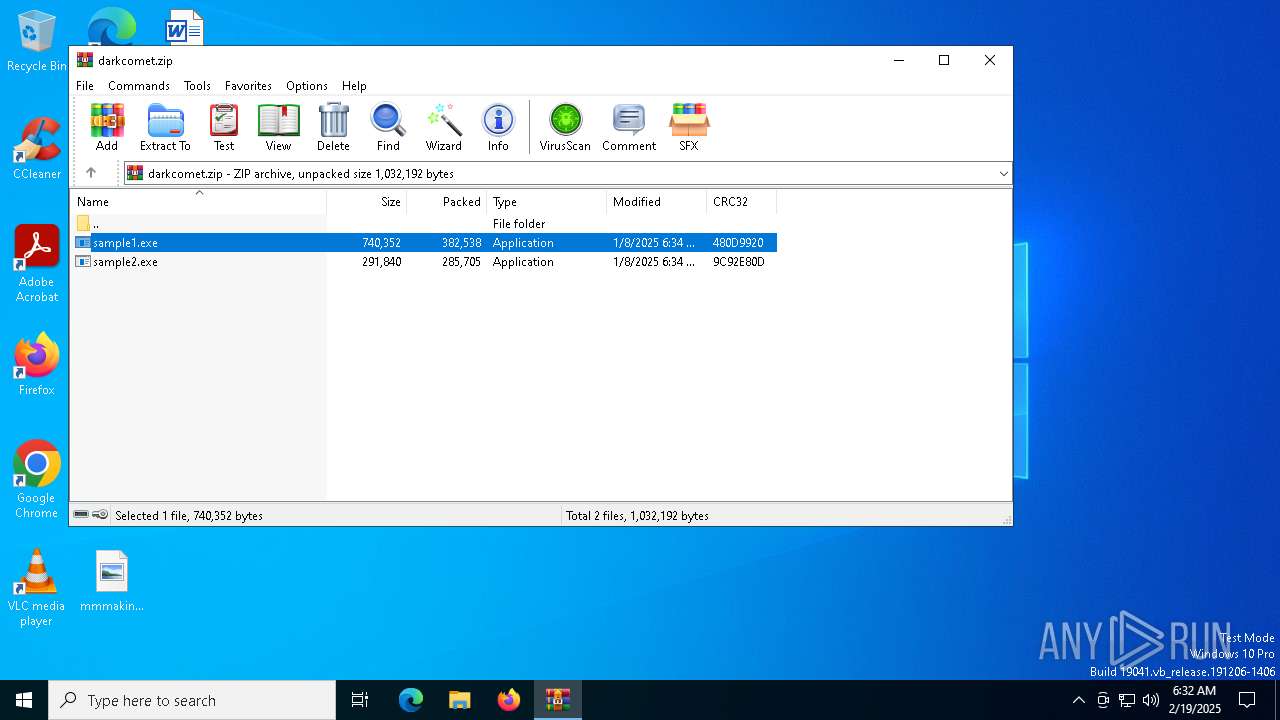
| File name: | darkcomet.zip |
| Full analysis: | https://app.any.run/tasks/a4ab6bc8-24f4-4955-9c75-450e61c262f8 |
| Verdict: | Malicious activity |
| Threats: | DarkComet RAT is a malicious program designed to remotely control or administer a victim's computer, steal private data and spy on the victim. |
| Analysis date: | February 19, 2025, 06:32:03 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 4CAB6397AD0B7E8FE3C6487FAE5C7EDE |
| SHA1: | 391DA9A905848D56ABA4512076210E8179C14CD9 |
| SHA256: | B1E51DF3D5BC49645C72B016021215C03F76E17889E256E2A085063805AF576D |
| SSDEEP: | 24576:21bZZESVvmtzyF6d9kvDZO9LgjS/DFwU+fgk+2zeTXC4K9+vlpWV1GH:21bZZESVvmtzw6d9kvDZO9LgjS/DFwUp |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 3772)
Changes the autorun value in the registry
- sample1.exe (PID: 7056)
- msdcsc.exe (PID: 6152)
Changes the login/logoff helper path in the registry
- sample1.exe (PID: 7056)
DARKCOMET mutex has been found
- msdcsc.exe (PID: 6152)
- iexplore.exe (PID: 4136)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3772)
- sample1.exe (PID: 7056)
Executable content was dropped or overwritten
- sample1.exe (PID: 7056)
Executing commands from a ".bat" file
- sample1.exe (PID: 7056)
Starts CMD.EXE for commands execution
- sample1.exe (PID: 7056)
Starts itself from another location
- sample1.exe (PID: 7056)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 7104)
- cmd.exe (PID: 7128)
INFO
Checks supported languages
- sample1.exe (PID: 7056)
- msdcsc.exe (PID: 6152)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3772)
The sample compiled with english language support
- sample1.exe (PID: 7056)
- WinRAR.exe (PID: 3772)
Reads the computer name
- sample1.exe (PID: 7056)
- msdcsc.exe (PID: 6152)
Create files in a temporary directory
- sample1.exe (PID: 7056)
Process checks computer location settings
- sample1.exe (PID: 7056)
Connects to unusual port
- iexplore.exe (PID: 4136)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0008 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:01:08 12:04:22 |
| ZipCRC: | 0x9c92e80d |
| ZipCompressedSize: | 285705 |
| ZipUncompressedSize: | 291840 |
| ZipFileName: | sample2.exe |
Total processes
137
Monitored processes
10
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3772 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\darkcomet.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 3984 | attrib "C:\Users\admin\AppData\Local\Temp\Rar$EXa3772.7348" +s +h | C:\Windows\SysWOW64\attrib.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Attribute Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4136 | "C:\Program Files (x86)\Internet Explorer\iexplore.exe" | C:\Program Files (x86)\Internet Explorer\iexplore.exe | msdcsc.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4308 | attrib "C:\Users\admin\AppData\Local\Temp\Rar$EXa3772.7348" +s +h | C:\Windows\SysWOW64\attrib.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Attribute Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6152 | "C:\Users\admin\Documents\MSDCSC\msdcsc.exe" | C:\Users\admin\Documents\MSDCSC\msdcsc.exe | sample1.exe | ||||||||||||
User: admin Company: Microsoft Corp. Integrity Level: MEDIUM Description: Remote Service Application Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 7056 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3772.7348\sample1.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3772.7348\sample1.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corp. Integrity Level: MEDIUM Description: Remote Service Application Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 7104 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\tmpcmd.bat" " | C:\Windows\SysWOW64\cmd.exe | — | sample1.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7112 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7128 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\tmpcmd.bat" " | C:\Windows\SysWOW64\cmd.exe | — | sample1.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7148 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
2 874
Read events
2 860
Write events
14
Delete events
0
Modification events
| (PID) Process: | (3772) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (3772) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (3772) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (3772) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\darkcomet.zip | |||
| (PID) Process: | (3772) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3772) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3772) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3772) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7056) sample1.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | MicroUpdate |
Value: C:\Users\admin\Documents\MSDCSC\msdcsc.exe | |||
| (PID) Process: | (7056) sample1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon |
| Operation: | write | Name: | UserInit |
Value: C:\Windows\system32\userinit.exe,C:\Users\admin\Documents\MSDCSC\msdcsc.exe | |||
Executable files
4
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7056 | sample1.exe | C:\Users\admin\Documents\MSDCSC\msdcsc.exe | executable | |
MD5:C1F59C6B996C64CEF3DAEB5B04396BE7 | SHA256:6D1D39E43E4817E5728567F78FF84590AA7EC99DD5C0A75E96DE0108340B69EB | |||
| 3772 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3772.7348\sample2.exe | executable | |
MD5:D42C586A9191BBF1E2398CB6DEB9E04D | SHA256:C315EB79C4068A189B74F3E03E37420D5C97933DE5C2A81C320CFABD0DB3BCCC | |||
| 7056 | sample1.exe | C:\Users\admin\AppData\Local\Temp\tmpcmd.bat | text | |
MD5:ED2B48660F8E133B77D28BBEAE045080 | SHA256:5732971D350AE125A5A96A437D2B403D1A9CF0EA4F6A79148DA9B1892011C06D | |||
| 3772 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3772.7348\sample1.exe | executable | |
MD5:C1F59C6B996C64CEF3DAEB5B04396BE7 | SHA256:6D1D39E43E4817E5728567F78FF84590AA7EC99DD5C0A75E96DE0108340B69EB | |||
| 3772 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\sample1.exe | executable | |
MD5:C1F59C6B996C64CEF3DAEB5B04396BE7 | SHA256:6D1D39E43E4817E5728567F78FF84590AA7EC99DD5C0A75E96DE0108340B69EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
34
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3508 | svchost.exe | GET | 200 | 23.32.238.128:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3508 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6868 | SIHClient.exe | GET | 200 | 23.38.73.129:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6868 | SIHClient.exe | GET | 200 | 23.38.73.129:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6412 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2396 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3508 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3508 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3508 | svchost.exe | 23.32.238.128:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
3508 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5064 | SearchApp.exe | 2.19.80.90:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
1176 | svchost.exe | 20.190.160.5:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |