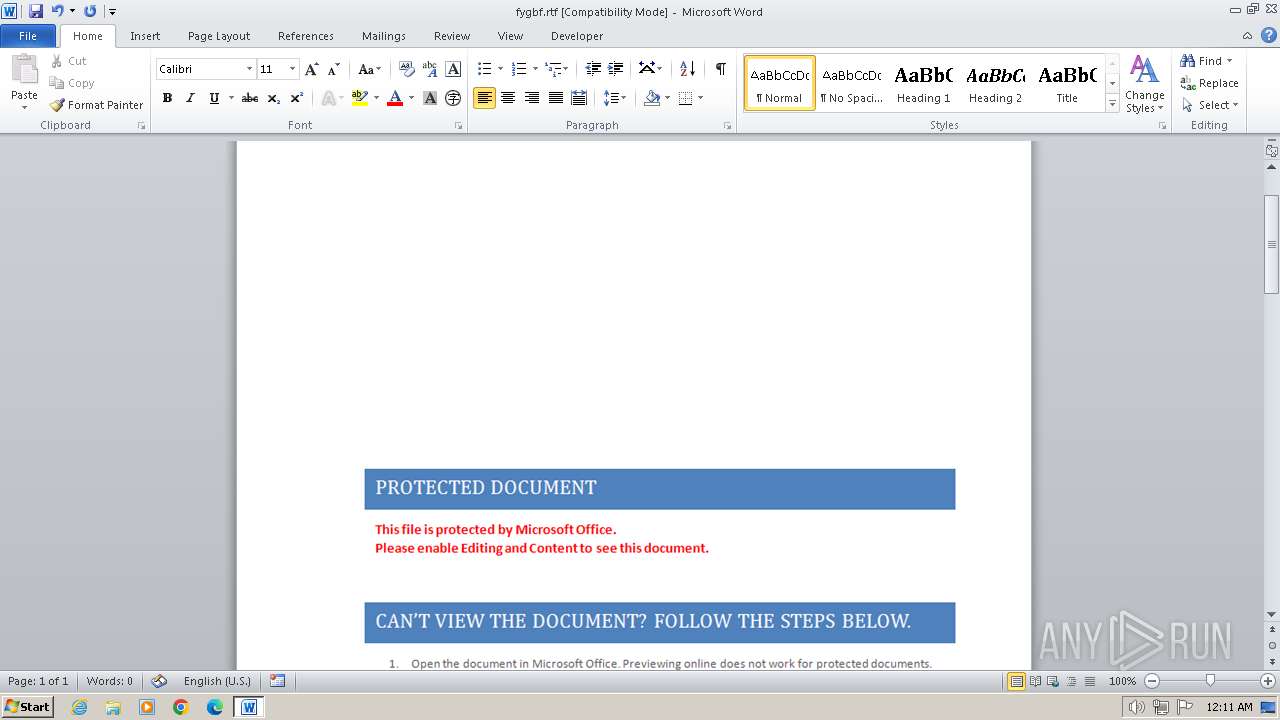
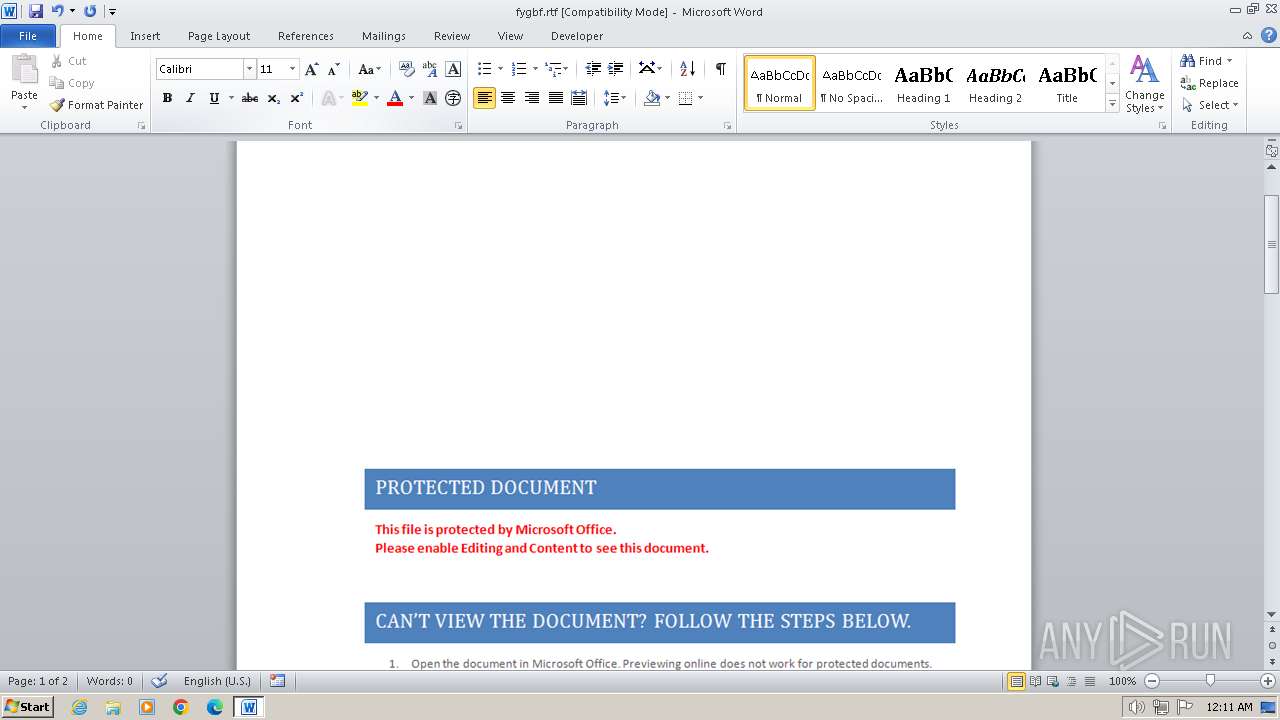
| File name: | metrofax.doc |
| Full analysis: | https://app.any.run/tasks/edeb5b27-3ff9-4524-be64-e9c93db3209d |
| Verdict: | Malicious activity |
| Threats: | Pony is a malware with two main functions — stealing information and dropping other viruses with different tasks on infected machines. It has been around since 2011, and it still actively attacks users in Europe and America. |
| Analysis date: | March 01, 2024, 00:11:03 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, Code page: 1251, Template: Normal.dotm, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Tue Dec 22 08:04:00 2015, Last Saved Time/Date: Tue Dec 22 13:09:00 2015, Number of Pages: 1, Number of Words: 6, Number of Characters: 37, Security: 0 |
| MD5: | 28E855032F83ADBD2D8499AF6D2D0E22 |
| SHA1: | 6B590325E2E465D9762FA5D1877846667268558A |
| SHA256: | B13B29772C29CCB412D6AB360FF38525836FCF0F65BE637A7945A83A446DFD5E |
| SSDEEP: | 3072:zVIfFuR6AqFMa2fL3NtkWL90y7K4mlQCww7zDTW6HNRn0nPmawH:zVIf8RsOtZclptz78PkH |
MALICIOUS
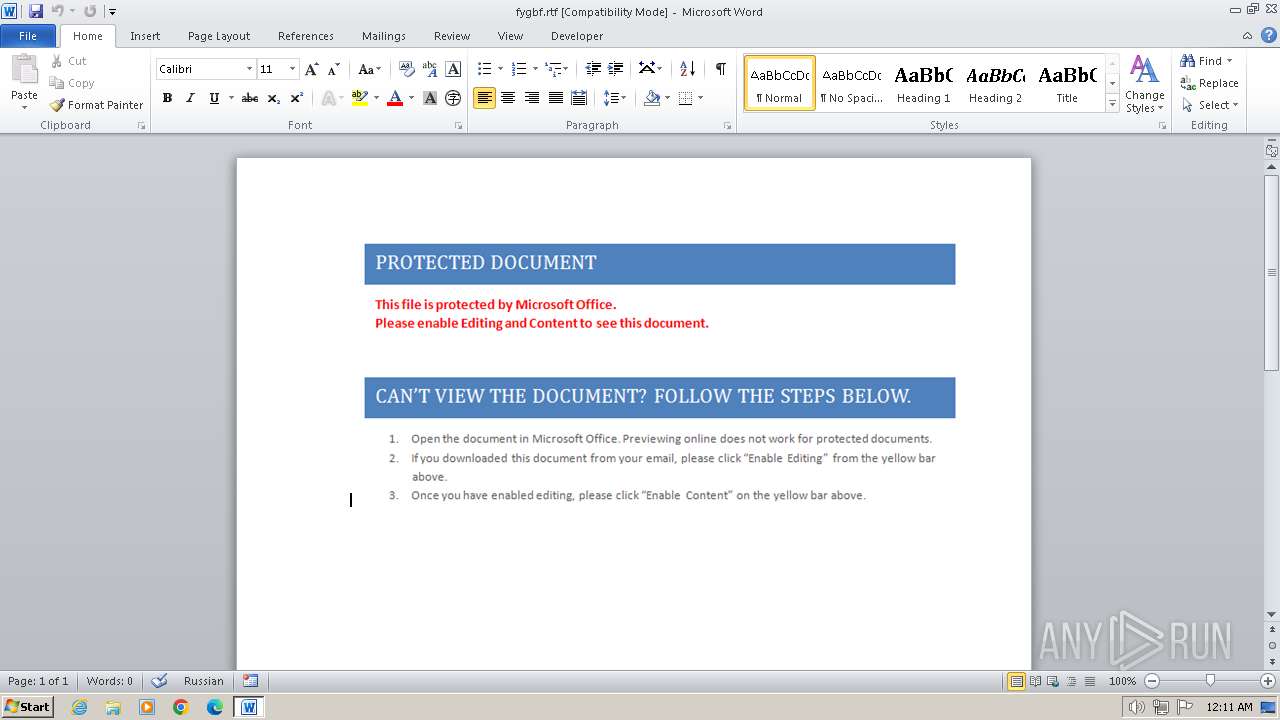
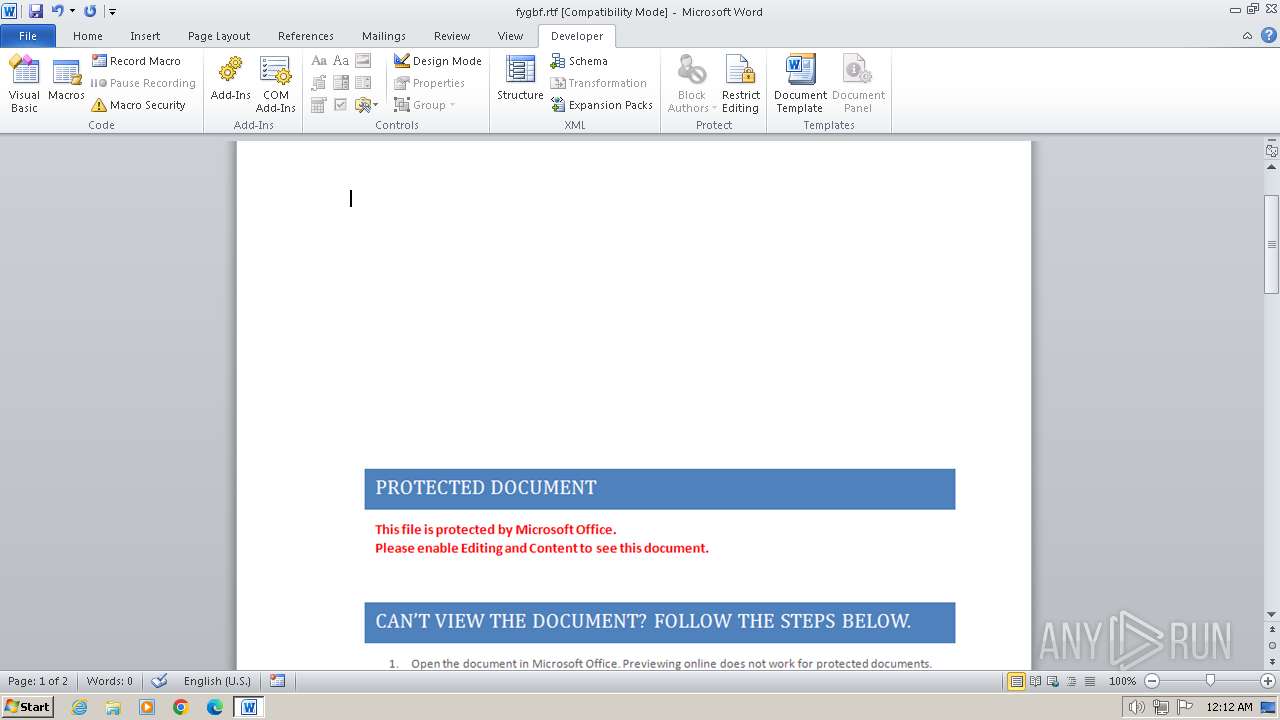
Drops the executable file immediately after the start
- WINWORD.EXE (PID: 2472)
Executable content was dropped or overwritten
- WINWORD.EXE (PID: 3216)
Unusual execution from MS Office
- WINWORD.EXE (PID: 2472)
Pony/Fareit Trojan is detected
- 8tr.exe (PID: 3228)
Raccoon mutex has been detected
- 8tr.exe (PID: 3228)
Steals credentials from Web Browsers
- 8tr.exe (PID: 3228)
Actions looks like stealing of personal data
- 8tr.exe (PID: 3228)
SUSPICIOUS
Searches for installed software
- 8tr.exe (PID: 3228)
Starts CMD.EXE for commands execution
- 8tr.exe (PID: 3228)
Loads DLL from Mozilla Firefox
- 8tr.exe (PID: 3228)
Reads the Internet Settings
- 8tr.exe (PID: 3228)
- sipnotify.exe (PID: 1456)
The process executes via Task Scheduler
- sipnotify.exe (PID: 1456)
- ctfmon.exe (PID: 1684)
Runs shell command (SCRIPT)
- WINWORD.EXE (PID: 2472)
Reads settings of System Certificates
- sipnotify.exe (PID: 1456)
Accesses Microsoft Outlook profiles
- 8tr.exe (PID: 3228)
INFO
The process uses the downloaded file
- WINWORD.EXE (PID: 3216)
Drops the executable file immediately after the start
- WINWORD.EXE (PID: 3216)
Checks supported languages
- 8tr.exe (PID: 3228)
- IMEKLMG.EXE (PID: 2052)
- IMEKLMG.EXE (PID: 2060)
- wmpnscfg.exe (PID: 2304)
- wmpnscfg.exe (PID: 2324)
Reads the computer name
- 8tr.exe (PID: 3228)
- IMEKLMG.EXE (PID: 2052)
- IMEKLMG.EXE (PID: 2060)
- wmpnscfg.exe (PID: 2304)
- wmpnscfg.exe (PID: 2324)
Manual execution by a user
- IMEKLMG.EXE (PID: 2052)
- IMEKLMG.EXE (PID: 2060)
- wmpnscfg.exe (PID: 2304)
- wmpnscfg.exe (PID: 2324)
Process checks whether UAC notifications are on
- IMEKLMG.EXE (PID: 2060)
- IMEKLMG.EXE (PID: 2052)
Reads security settings of Internet Explorer
- sipnotify.exe (PID: 1456)
Reads the software policy settings
- sipnotify.exe (PID: 1456)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (35.9) |
|---|---|---|
| .xls | | | Microsoft Excel sheet (33.7) |
| .doc | | | Microsoft Word document (old ver.) (21.3) |
EXIF
FlashPix
| Identification: | Word 8.0 |
|---|---|
| LanguageCode: | Russian |
| DocFlags: | Has picture, 1Table, ExtChar |
| System: | Windows |
| Word97: | No |
| Title: | - |
| Subject: | - |
| Author: | - |
| Keywords: | - |
| Comments: | - |
| Template: | Normal.dotm |
| LastModifiedBy: | - |
| Software: | Microsoft Office Word |
| CreateDate: | 2015:12:22 08:04:00 |
| ModifyDate: | 2015:12:22 13:09:00 |
| Security: | None |
| CodePage: | Windows Cyrillic |
| Company: | - |
| CharCountWithSpaces: | 42 |
| AppVersion: | 15 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | ???????? Microsoft Word 97-2003 |
| LastPrinted: | 0000:00:00 00:00:00 |
| RevisionNumber: | 1 |
| TotalEditTime: | - |
| Words: | 6 |
| Characters: | 37 |
| Pages: | 1 |
| Paragraphs: | 1 |
| Lines: | 1 |
Total processes
92
Monitored processes
10
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1456 | C:\Windows\system32\sipnotify.exe -LogonOrUnlock | C:\Windows\System32\sipnotify.exe | taskeng.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: sipnotify Exit code: 0 Version: 6.1.7602.20480 (win7sp1_ldr_escrow.191010-1716) Modules
| |||||||||||||||
| 1492 | cmd /K | C:\Windows\System32\cmd.exe | — | 8tr.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1073807364 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1684 | C:\Windows\System32\ctfmon.exe | C:\Windows\System32\ctfmon.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CTF Loader Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2052 | "C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /JPN /Log | C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 Modules
| |||||||||||||||
| 2060 | "C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /KOR /Log | C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 Modules
| |||||||||||||||
| 2304 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2324 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2472 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\metrofax.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 1073807364 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3216 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /Automation -Embedding | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3228 | C:\Users\admin\AppData\Local\Temp\8tr.exe | C:\Users\admin\AppData\Local\Temp\8tr.exe | WINWORD.EXE | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1073807364 Modules
| |||||||||||||||
Total events
48 892
Read events
37 644
Write events
10 742
Delete events
506
Modification events
| (PID) Process: | (2472) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | 5j& |
Value: 356A2600A8090000010000000000000000000000 | |||
| (PID) Process: | (2472) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2472) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2472) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2472) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2472) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2472) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2472) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2472) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2472) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
1
Suspicious files
16
Text files
14
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2472 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRF695.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3216 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR2D9.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2472 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$trofax.doc | binary | |
MD5:48511C25A0F5FE9B43F8EE52E049C943 | SHA256:6AA8C97B37880EA433E9BA531B91694216D6311CB95EE3806ABF9A925DF6F731 | |||
| 2472 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\vbhja.rtf | text | |
MD5:915FD7925C9DD50D54F937003A2DE548 | SHA256:A1FA7AC100F8DF1C0C1602CC3F0135A63841D76F5F531628217F343EBA6845BC | |||
| 2472 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\163E8979.emf | binary | |
MD5:0ED5BC16545D23C325D756013579A697 | SHA256:3E430584CD9774EA3B21D8E19B485B48212FE356776158DD5F3C5F63A5BDE7D3 | |||
| 2472 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:280D2B65A6285DCE35099F1721B7999D | SHA256:9C481BFD497634B56792F1F82F7323677D76F0ECD94EC28D527714D4DEF38B52 | |||
| 3216 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{43FE5951-5C47-468E-BD4C-A4841D39A676}.tmp | binary | |
MD5:1D1D5624AC961874740A0EB9D9D8032E | SHA256:A7C658E861B66C331B4A6F8DE985F2B877D602BA8C8AB4B565E92E864EC7EE12 | |||
| 3216 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRF{0E6A627A-9327-48AB-A122-1ADF189C7B44}.tmp | binary | |
MD5:5FB87A99D94A8B05A168FB615C53F735 | SHA256:E5FE05840CDC91992D2B35552A14C7FD5B45A9752D1DDE5C82E79F4AD4C99813 | |||
| 3216 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\F3FFBBCB.emf | emf | |
MD5:0ED5BC16545D23C325D756013579A697 | SHA256:3E430584CD9774EA3B21D8E19B485B48212FE356776158DD5F3C5F63A5BDE7D3 | |||
| 3216 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\8tr.exe | executable | |
MD5:C028F68109FD975E9AED790087FE1457 | SHA256:5C05DB8164A6D51DD483CBE8EDDB1D0C21AECF432EF75F5DC5A0A2FC0B711657 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
9
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1456 | sipnotify.exe | HEAD | 200 | 104.79.47.248:80 | http://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2JgkA?v=133537255833750000 | unknown | — | — | unknown |
2472 | WINWORD.EXE | GET | 200 | 52.109.28.46:80 | http://office14client.microsoft.com/config14?UILCID=1033&CLCID=1033&ILCID=1033&HelpLCID=1033&App={019C826E-445A-4649-A5B0-0BF08FCC4EEE}&build=14.0.6023 | unknown | xml | 1.97 Kb | unknown |
2472 | WINWORD.EXE | GET | 200 | 52.109.28.46:80 | http://office14client.microsoft.com/config14?UILCID=1033&CLCID=1033&ILCID=1033&HelpLCID=1033&App={019C826E-445A-4649-A5B0-0BF08FCC4EEE}&build=14.0.6023 | unknown | xml | 1.97 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2472 | WINWORD.EXE | 52.109.28.46:80 | office14client.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | unknown |
1456 | sipnotify.exe | 104.79.47.248:80 | query.prod.cms.rt.microsoft.com | Akamai International B.V. | US | unknown |
1116 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
fouseevenghedt.ru |
| unknown |
office14client.microsoft.com |
| whitelisted |
biledroben.ru |
| unknown |
query.prod.cms.rt.microsoft.com |
| whitelisted |