| File name: | metrofax.doc |
| Full analysis: | https://app.any.run/tasks/c39a0869-52dd-479c-947b-061186743cee |
| Verdict: | Malicious activity |
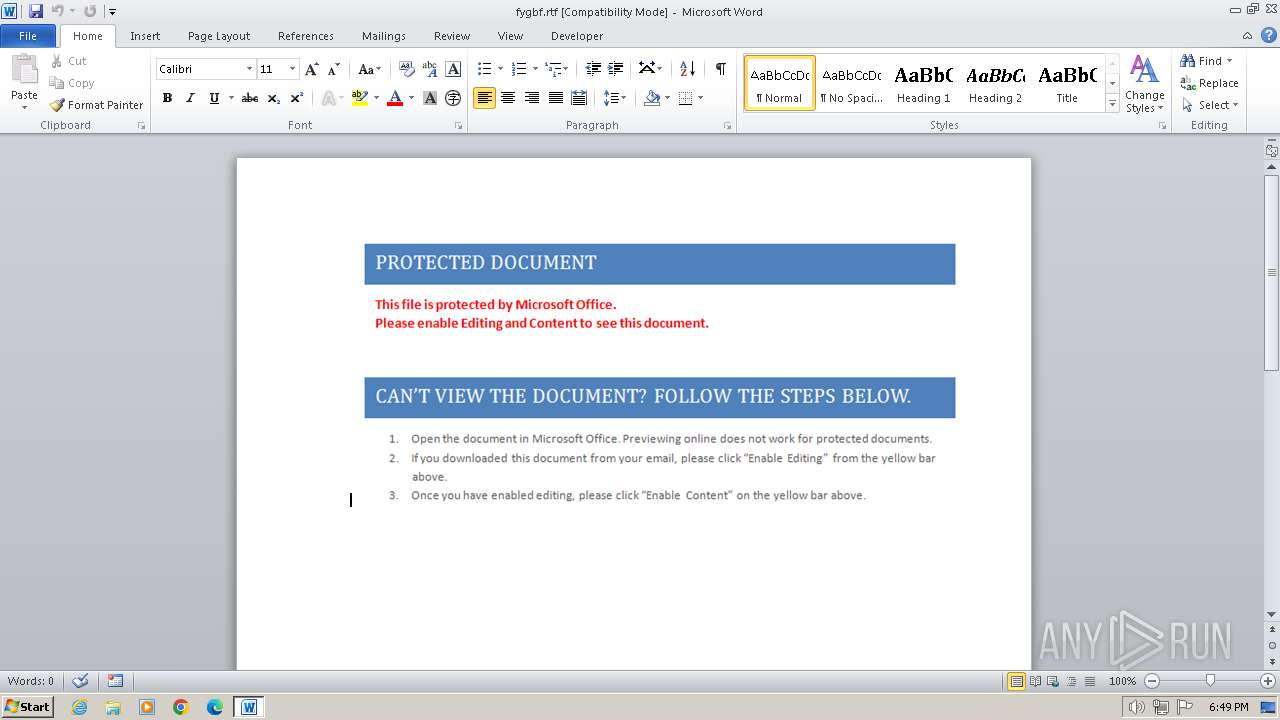
| Threats: | Pony is a malware with two main functions — stealing information and dropping other viruses with different tasks on infected machines. It has been around since 2011, and it still actively attacks users in Europe and America. |
| Analysis date: | February 13, 2024, 18:48:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, Code page: 1251, Template: Normal.dotm, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Tue Dec 22 08:04:00 2015, Last Saved Time/Date: Tue Dec 22 13:09:00 2015, Number of Pages: 1, Number of Words: 6, Number of Characters: 37, Security: 0 |
| MD5: | 28E855032F83ADBD2D8499AF6D2D0E22 |
| SHA1: | 6B590325E2E465D9762FA5D1877846667268558A |
| SHA256: | B13B29772C29CCB412D6AB360FF38525836FCF0F65BE637A7945A83A446DFD5E |
| SSDEEP: | 3072:zVIfFuR6AqFMa2fL3NtkWL90y7K4mlQCww7zDTW6HNRn0nPmawH:zVIf8RsOtZclptz78PkH |
MALICIOUS
Drops the executable file immediately after the start
- WINWORD.EXE (PID: 3668)
Executable content was dropped or overwritten
- WINWORD.EXE (PID: 2036)
Unusual execution from MS Office
- WINWORD.EXE (PID: 3668)
Raccoon mutex has been detected
- 8tr.exe (PID: 3948)
Pony/Fareit Trojan is detected
- 8tr.exe (PID: 3948)
Steals credentials from Web Browsers
- 8tr.exe (PID: 3948)
Actions looks like stealing of personal data
- 8tr.exe (PID: 3948)
SUSPICIOUS
Starts CMD.EXE for commands execution
- 8tr.exe (PID: 3948)
Searches for installed software
- 8tr.exe (PID: 3948)
Loads DLL from Mozilla Firefox
- 8tr.exe (PID: 3948)
Runs shell command (SCRIPT)
- WINWORD.EXE (PID: 3668)
Process requests binary or script from the Internet
- 8tr.exe (PID: 3948)
Reads the Internet Settings
- 8tr.exe (PID: 3948)
Reads security settings of Internet Explorer
- 8tr.exe (PID: 3948)
Executing commands from a ".bat" file
- 8tr.exe (PID: 3948)
Accesses Microsoft Outlook profiles
- 8tr.exe (PID: 3948)
INFO
Drops the executable file immediately after the start
- WINWORD.EXE (PID: 2036)
The process uses the downloaded file
- WINWORD.EXE (PID: 2036)
Reads the computer name
- 8tr.exe (PID: 3948)
Checks supported languages
- 8tr.exe (PID: 3948)
Manual execution by a user
- WINWORD.EXE (PID: 2908)
Create files in a temporary directory
- 8tr.exe (PID: 3948)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (35.9) |
|---|---|---|
| .xls | | | Microsoft Excel sheet (33.7) |
| .doc | | | Microsoft Word document (old ver.) (21.3) |
EXIF
FlashPix
| Identification: | Word 8.0 |
|---|---|
| LanguageCode: | Russian |
| DocFlags: | Has picture, 1Table, ExtChar |
| System: | Windows |
| Word97: | No |
| Title: | - |
| Subject: | - |
| Author: | - |
| Keywords: | - |
| Comments: | - |
| Template: | Normal.dotm |
| LastModifiedBy: | - |
| Software: | Microsoft Office Word |
| CreateDate: | 2015:12:22 08:04:00 |
| ModifyDate: | 2015:12:22 13:09:00 |
| Security: | None |
| CodePage: | Windows Cyrillic |
| Company: | - |
| CharCountWithSpaces: | 42 |
| AppVersion: | 15 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | ???????? Microsoft Word 97-2003 |
| LastPrinted: | 0000:00:00 00:00:00 |
| RevisionNumber: | 1 |
| TotalEditTime: | - |
| Words: | 6 |
| Characters: | 37 |
| Pages: | 1 |
| Paragraphs: | 1 |
| Lines: | 1 |
Total processes
50
Monitored processes
7
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1368 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\1790312.bat" "C:\Users\admin\AppData\Local\Temp\8tr.exe" " | C:\Windows\System32\cmd.exe | — | 8tr.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1836 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2036 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /Automation -Embedding | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2908 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\willdisease.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3668 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\metrofax.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3932 | cmd /K | C:\Windows\System32\cmd.exe | — | 8tr.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3948 | C:\Users\admin\AppData\Local\Temp\8tr.exe | C:\Users\admin\AppData\Local\Temp\8tr.exe | WINWORD.EXE | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
22 663
Read events
20 790
Write events
1 135
Delete events
738
Modification events
| (PID) Process: | (3668) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | 9h& |
Value: 39682600540E0000010000000000000000000000 | |||
| (PID) Process: | (3668) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3668) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (3668) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (3668) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (3668) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (3668) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (3668) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (3668) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (3668) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
2
Suspicious files
12
Text files
6
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3668 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRF099.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2036 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRFB77.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2908 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRF018.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3668 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$vbhja.rtf | binary | |
MD5:DB3F5EF7307927B21AC8FFAEAF891702 | SHA256:506990E7A3FB23F802FE9FA2376A7EE1F1F5D5A9DD74A1F91B487066FC9EFE55 | |||
| 3668 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\fygbf.rtf | text | |
MD5:3DC31A6ADCBDB1202E44750C1F4D301C | SHA256:5EF217FB8C06FDBE335F85C215A33648F966AF22853F6164260DDF6D729DB556 | |||
| 3668 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\vbhja.rtf | text | |
MD5:266D5AD67EE3C4FEAF46EE0B22A13DDC | SHA256:44D3CAB03C1B908631C8F21DD34AB6462FDEA653BD565A8D721A457A00DAE91C | |||
| 3668 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~WRD0000.tmp | text | |
MD5:266D5AD67EE3C4FEAF46EE0B22A13DDC | SHA256:44D3CAB03C1B908631C8F21DD34AB6462FDEA653BD565A8D721A457A00DAE91C | |||
| 2036 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{E520CFFF-616F-4B26-B1A4-BA190B8515E4}.tmp | binary | |
MD5:5D4D94EE7E06BBB0AF9584119797B23A | SHA256:4826C0D860AF884D3343CA6460B0006A7A2CE7DBCCC4D743208585D997CC5FD1 | |||
| 3668 | WINWORD.EXE | C:\Users\admin\Desktop\~$lldisease.rtf | binary | |
MD5:461EFD41B99C5EE53CEFF6EEB3B3AA7A | SHA256:9BD4C358CEC0567B654AC13723799DC9FF0E886021FA20288A99FE81C01C833E | |||
| 2036 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{7D2C2A76-EC4C-44E2-B0A0-20A13AD11BAB}.tmp | binary | |
MD5:3CA11973C0FFB871666E74BC49DC6CD3 | SHA256:546D2AA3D947BC062D9325D3FC492AEEB259CA0E7436D3C6B605CBDD22410925 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
6
DNS requests
9
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3948 | 8tr.exe | GET | 404 | 177.53.141.201:80 | http://www.dgfcomercial.com.br/wp-content/plugins/prism-highlight/opera1.exe | unknown | html | 315 b | unknown |
3948 | 8tr.exe | GET | 301 | 177.53.141.201:80 | http://dgfcomercial.com.br/wp-content/plugins/prism-highlight/opera1.exe | unknown | html | 284 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3948 | 8tr.exe | 177.53.141.201:80 | dgfcomercial.com.br | Brasil Site Informatica LTDA | BR | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
fouseevenghedt.ru |
| unknown |
biledroben.ru |
| unknown |
rohironrof.ru |
| unknown |
eloraestate.com |
| unknown |
edmontonlimo247.com |
| unknown |
dgfcomercial.com.br |
| unknown |
www.dgfcomercial.com.br |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3948 | 8tr.exe | A Network Trojan was detected | ET MALWARE Possible Graftor EXE Download Common Header Order |
3948 | 8tr.exe | A Network Trojan was detected | ET MALWARE EXE Download Request To Wordpress Folder Likely Malicious |
3948 | 8tr.exe | A Network Trojan was detected | ET MALWARE Possible Graftor EXE Download Common Header Order |
3948 | 8tr.exe | A Network Trojan was detected | ET MALWARE EXE Download Request To Wordpress Folder Likely Malicious |