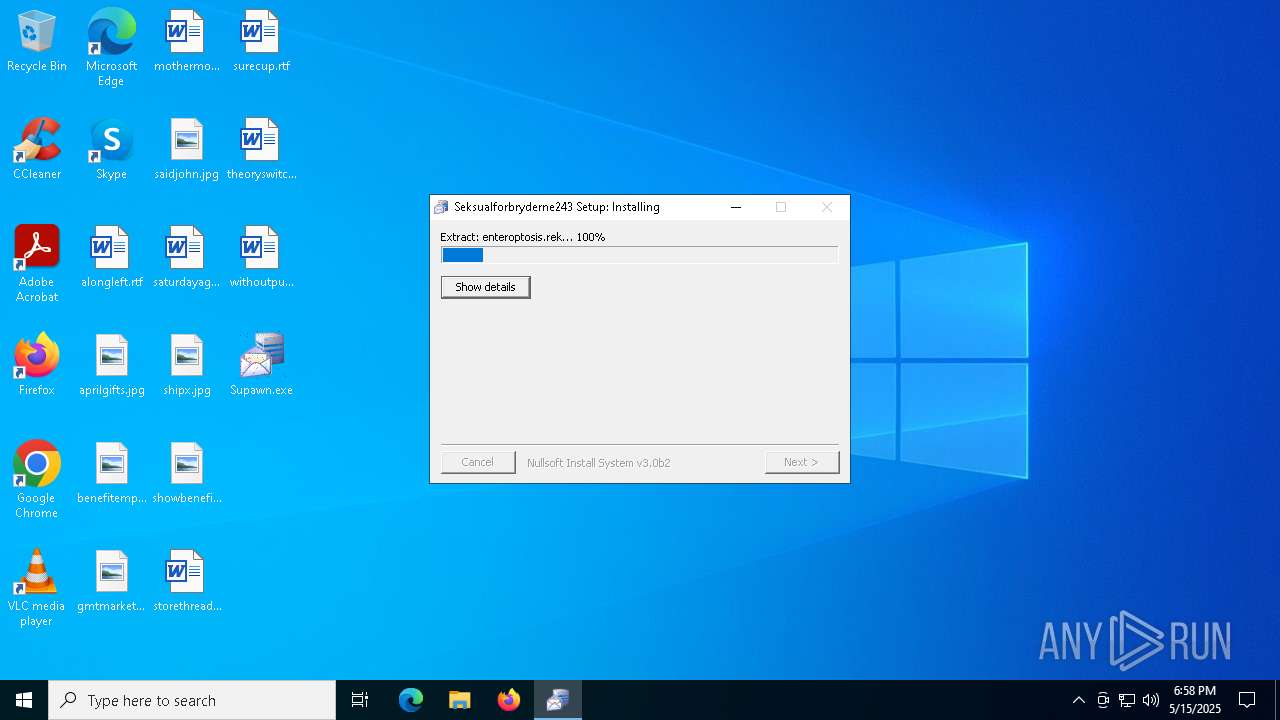
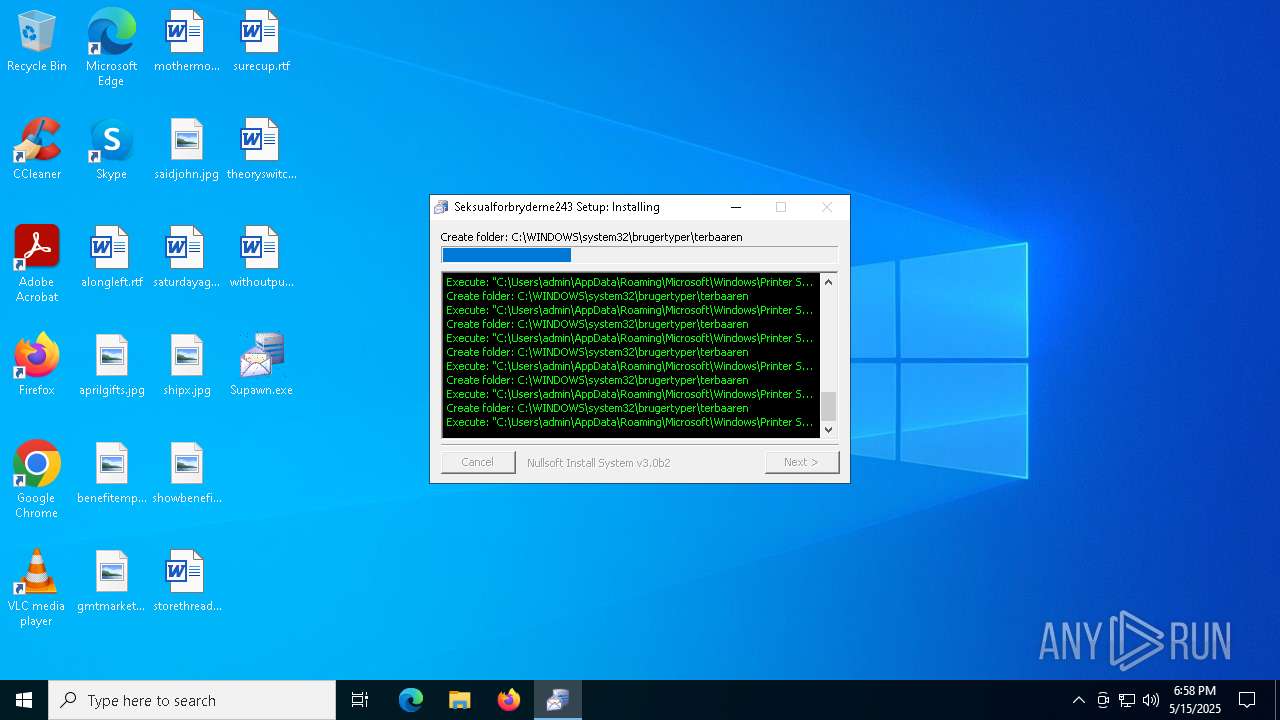
| File name: | Supawn.exe |
| Full analysis: | https://app.any.run/tasks/870c06da-8624-4b76-afb4-16e74f4c1f76 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | May 15, 2025, 18:58:17 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | 2C852E539235C1F4F5CE34F64C9EBD3F |
| SHA1: | 04606D114D8AE890C2876F5F3963E6C792107298 |
| SHA256: | B11F7FA0B1BED64E97EF2AA2D0DD763E27A23BD99D347318457B60C67C185CF0 |
| SSDEEP: | 49152:T/C/7dZvM0BsKo+GOuVa+mZjby1L10Df96++LR5Lg1tWlcDem7tl35UrdQsDcfXk:dhJlOwzmBy15eFUcnDeUtreWTzhSIDrC |
MALICIOUS
Executing a file with an untrusted certificate
- Supawn.exe (PID: 7612)
- Supawn.exe (PID: 7968)
AGENTTESLA has been detected (YARA)
- Supawn.exe (PID: 7968)
Steals credentials from Web Browsers
- Supawn.exe (PID: 7968)
Actions looks like stealing of personal data
- Supawn.exe (PID: 7968)
AGENTTESLA has been detected (SURICATA)
- Supawn.exe (PID: 7968)
SUSPICIOUS
Executable content was dropped or overwritten
- Supawn.exe (PID: 7612)
The process creates files with name similar to system file names
- Supawn.exe (PID: 7612)
Malware-specific behavior (creating "System.dll" in Temp)
- Supawn.exe (PID: 7612)
There is functionality for taking screenshot (YARA)
- Supawn.exe (PID: 7612)
- Supawn.exe (PID: 7968)
Reads security settings of Internet Explorer
- Supawn.exe (PID: 7968)
Application launched itself
- Supawn.exe (PID: 7612)
Connects to the server without a host name
- Supawn.exe (PID: 7968)
Checks for external IP
- Supawn.exe (PID: 7968)
- svchost.exe (PID: 2196)
Connects to FTP
- Supawn.exe (PID: 7968)
Connects to unusual port
- Supawn.exe (PID: 7968)
INFO
Checks supported languages
- Supawn.exe (PID: 7612)
- Supawn.exe (PID: 7968)
The sample compiled with english language support
- Supawn.exe (PID: 7612)
Reads the computer name
- Supawn.exe (PID: 7612)
- Supawn.exe (PID: 7968)
Create files in a temporary directory
- Supawn.exe (PID: 7612)
Reads the machine GUID from the registry
- Supawn.exe (PID: 7968)
Checks proxy server information
- Supawn.exe (PID: 7968)
- slui.exe (PID: 7392)
Disables trace logs
- Supawn.exe (PID: 7968)
Reads the software policy settings
- slui.exe (PID: 7392)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2015:08:05 00:46:24+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 24064 |
| InitializedDataSize: | 141824 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x31ff |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.0.0.0 |
| ProductVersionNumber: | 3.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| Comments: | United Auto Group Inc |
| CompanyName: | R.R. Donnelley & Sons Company |
| FileDescription: | ACT Manufacturing Inc. |
| FileVersion: | 3.0.0.0 |
| LegalCopyright: | Texas Instruments Incorporated |
| LegalTrademarks: | Hawaiian Electric Industries Inc. |
| OriginalFileName: | antiforureningens strafcellerne.exe |
Total processes
129
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7392 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7612 | "C:\Users\admin\Desktop\Supawn.exe" | C:\Users\admin\Desktop\Supawn.exe | explorer.exe | ||||||||||||
User: admin Company: R.R. Donnelley & Sons Company Integrity Level: MEDIUM Description: ACT Manufacturing Inc. Exit code: 0 Version: 3.0.0.0 Modules
| |||||||||||||||
| 7968 | "C:\Users\admin\Desktop\Supawn.exe" | C:\Users\admin\Desktop\Supawn.exe | Supawn.exe | ||||||||||||
User: admin Company: R.R. Donnelley & Sons Company Integrity Level: MEDIUM Description: ACT Manufacturing Inc. Version: 3.0.0.0 Modules
| |||||||||||||||
Total events
5 341
Read events
4 871
Write events
470
Delete events
0
Modification events
| (PID) Process: | (7612) Supawn.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Locales Approx |
| Operation: | write | Name: | C Langs |
Value: u | |||
| (PID) Process: | (7612) Supawn.exe | Key: | HKEY_CURRENT_USER\Nondivulging188\adagietto\frustrate |
| Operation: | write | Name: | deletimen |
Value: 8E23 | |||
| (PID) Process: | (7612) Supawn.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Locales Approx |
| Operation: | write | Name: | C Langs |
Value: us | |||
| (PID) Process: | (7612) Supawn.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Locales Approx |
| Operation: | write | Name: | C Langs |
Value: use | |||
| (PID) Process: | (7612) Supawn.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Locales Approx |
| Operation: | write | Name: | C Langs |
Value: user | |||
| (PID) Process: | (7612) Supawn.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Locales Approx |
| Operation: | write | Name: | C Langs |
Value: user3 | |||
| (PID) Process: | (7612) Supawn.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Locales Approx |
| Operation: | write | Name: | C Langs |
Value: user32 | |||
| (PID) Process: | (7612) Supawn.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Locales Approx |
| Operation: | write | Name: | C Langs |
Value: user32: | |||
| (PID) Process: | (7612) Supawn.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Locales Approx |
| Operation: | write | Name: | C Langs |
Value: user32:: | |||
| (PID) Process: | (7612) Supawn.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Locales Approx |
| Operation: | write | Name: | C Langs |
Value: user32::S | |||
Executable files
1
Suspicious files
6
Text files
9
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7612 | Supawn.exe | C:\Users\admin\hundredfold\optativs\Uncontainableness\Sammenhftet.doi | — | |
MD5:— | SHA256:— | |||
| 7612 | Supawn.exe | C:\Users\admin\hundredfold\optativs\Uncontainableness\Opkvikkende\indsprjtendes.men | — | |
MD5:— | SHA256:— | |||
| 7612 | Supawn.exe | C:\Users\admin\hundredfold\optativs\Uncontainableness\Decaying4.jpg | image | |
MD5:D1700D41EA6D5C123BFFD67CBB35D092 | SHA256:89AB11AC727C380ED9BC50AF6AB2AD2E21D2BF4486FD49CC8516C78A8F11BC29 | |||
| 7612 | Supawn.exe | C:\Users\admin\hundredfold\optativs\Uncontainableness\Opkvikkende\realised.ini | text | |
MD5:52D77E755CDD905FE98C8300C244AF91 | SHA256:EC36E666F59E94A0B9F762773FE8A0EFB0CE0A10B6CEE58FA4B48FF370F06D66 | |||
| 7612 | Supawn.exe | C:\Users\admin\hundredfold\optativs\Uncontainableness\Simulanter.Hyp | binary | |
MD5:BB89E8BCBB8E8FC5B1C2209907063F4D | SHA256:B5B52310295B515F8A9D30C5DCE6D3AB2CC2FD434882484DAF43CA68C4ACFA2B | |||
| 7612 | Supawn.exe | C:\Users\admin\hundredfold\optativs\Uncontainableness\colorin.kap | binary | |
MD5:6BE901BE1094379E98B35FC4B91C2AFA | SHA256:83D9FB108522808A6E9AAE1925303B6A613DA65A57259C021C67887E463B7728 | |||
| 7612 | Supawn.exe | C:\Users\admin\hundredfold\optativs\Uncontainableness\Opkvikkende\figwort.ini | text | |
MD5:DF7D47F5A4CDDFEF00D9C85849D531C1 | SHA256:4A2F78F3C47A69BE3088DC8821102855CBB4519F948839B03B76D12C49A8A80F | |||
| 7612 | Supawn.exe | C:\Users\admin\hundredfold\optativs\Uncontainableness\Opkvikkende\galvanically.ini | text | |
MD5:4A2F65362C73B4254B305D9DA68CBC99 | SHA256:4F2785E875C03597EA770311298E7E4144301FC09BC8EF63A62FD93BE79BCD4F | |||
| 7612 | Supawn.exe | C:\Users\admin\hundredfold\optativs\Uncontainableness\enteroptosis.rek | binary | |
MD5:2215256C443913E86FB9BD1669D43737 | SHA256:D7C60D7E29BD6A502DF080FCC5EB66D8784686702ECDA2E332F6F24B5B7CA2F8 | |||
| 7612 | Supawn.exe | C:\Users\admin\hundredfold\optativs\Uncontainableness\Opkvikkende\fdestedskriterium.ini | text | |
MD5:0633FD2A9C4A93C00580D86E53BD26D2 | SHA256:6A31C758AC6E348C10C2D57FC873097D6191036C7FE8E631A24F17EDD0807255 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
26
DNS requests
8
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | svchost.exe | GET | 200 | 23.48.23.175:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7968 | Supawn.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | whitelisted |
7968 | Supawn.exe | GET | 200 | 75.127.7.164:80 | http://75.127.7.164/txfSfTnuPdarHRbAIuPqmWHzLHj225.bin | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 23.48.23.175:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 69.192.161.161:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
7968 | Supawn.exe | 75.127.7.164:80 | — | AS-COLOCROSSING | US | unknown |
7968 | Supawn.exe | 208.95.112.1:80 | ip-api.com | TUT-AS | US | whitelisted |
7968 | Supawn.exe | 89.39.83.184:21 | ftp.horeca-bucuresti.ro | ROMARG SRL | RO | malicious |
7968 | Supawn.exe | 89.39.83.184:49979 | ftp.horeca-bucuresti.ro | ROMARG SRL | RO | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ip-api.com |
| whitelisted |
ftp.horeca-bucuresti.ro |
| unknown |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7968 | Supawn.exe | Potentially Bad Traffic | ET HUNTING Generic .bin download from Dotted Quad |
7968 | Supawn.exe | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External Hosting Lookup by ip-api |
2196 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
7968 | Supawn.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
7968 | Supawn.exe | A Network Trojan was detected | ET MALWARE AgentTesla Exfil via FTP |
7968 | Supawn.exe | Misc activity | INFO [ANY.RUN] FTP protocol command for uploading a file |
7968 | Supawn.exe | A Network Trojan was detected | STEALER [ANY.RUN] AgentTesla Exfiltration (raw TCP) |
7968 | Supawn.exe | A Network Trojan was detected | STEALER [ANY.RUN] AgentTesla Exfiltration (raw TCP) |
7968 | Supawn.exe | Misc activity | INFO [ANY.RUN] FTP server is ready for the new user |