| File name: | b0cce111400d44468c36721e44d0bd661b795d49d017e1b4dbe0b4d0d79669a0.zip |
| Full analysis: | https://app.any.run/tasks/420e3dcb-5262-4431-a1e0-35abbacd993b |
| Verdict: | Malicious activity |
| Threats: | DarkComet RAT is a malicious program designed to remotely control or administer a victim's computer, steal private data and spy on the victim. |
| Analysis date: | December 22, 2024, 06:02:12 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | 7341D5F29F668CEE8B576B2CE60FDF68 |
| SHA1: | 922BE2DF23F9C2133A575A4D4CCD86223883ADE5 |
| SHA256: | B0CCE111400D44468C36721E44D0BD661B795D49D017E1B4DBE0B4D0D79669A0 |
| SSDEEP: | 3072:a1wIrcLRbpuNGsPmvtSS9UutxwcOgbWGrcuaTo5/TCa:a15gVUssPmvYSbmGwuada |
MALICIOUS
DARKCOMET mutex has been found
- iexplore.exe (PID: 6032)
LUMMA mutex has been found
- iexplore.exe (PID: 5876)
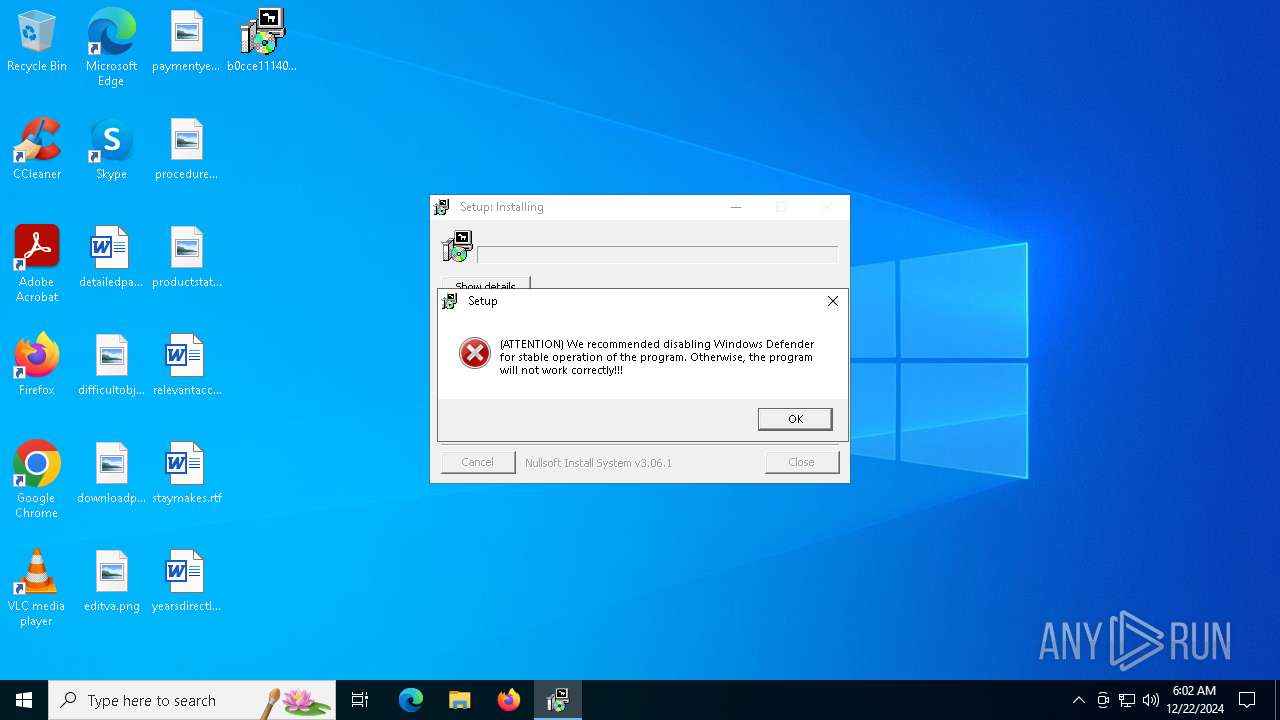
Changes the autorun value in the registry
- pythonw.exe (PID: 2072)
DARKCOMET has been detected (SURICATA)
- iexplore.exe (PID: 6032)
SUSPICIOUS
Reads security settings of Internet Explorer
- b0cce111400d44468c36721e44d0bd661b795d49d017e1b4dbe0b4d0d79669a0.zip.exe (PID: 3524)
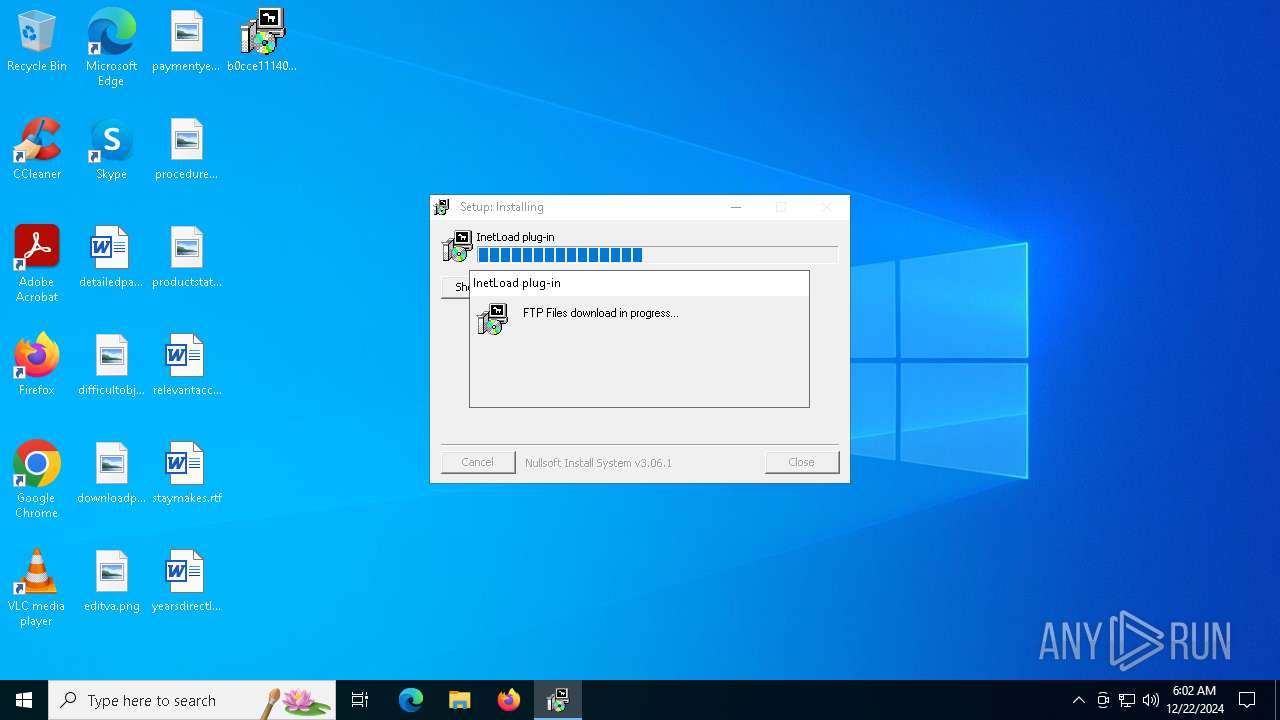
Connects to FTP
- b0cce111400d44468c36721e44d0bd661b795d49d017e1b4dbe0b4d0d79669a0.zip.exe (PID: 3524)
- pythonw.exe (PID: 448)
- pythonw.exe (PID: 1876)
- pythonw.exe (PID: 5880)
- pythonw.exe (PID: 4516)
- pythonw.exe (PID: 2072)
Connects to unusual port
- b0cce111400d44468c36721e44d0bd661b795d49d017e1b4dbe0b4d0d79669a0.zip.exe (PID: 3524)
- pythonw.exe (PID: 448)
- pythonw.exe (PID: 1876)
- pythonw.exe (PID: 5880)
- pythonw.exe (PID: 4516)
- pythonw.exe (PID: 2072)
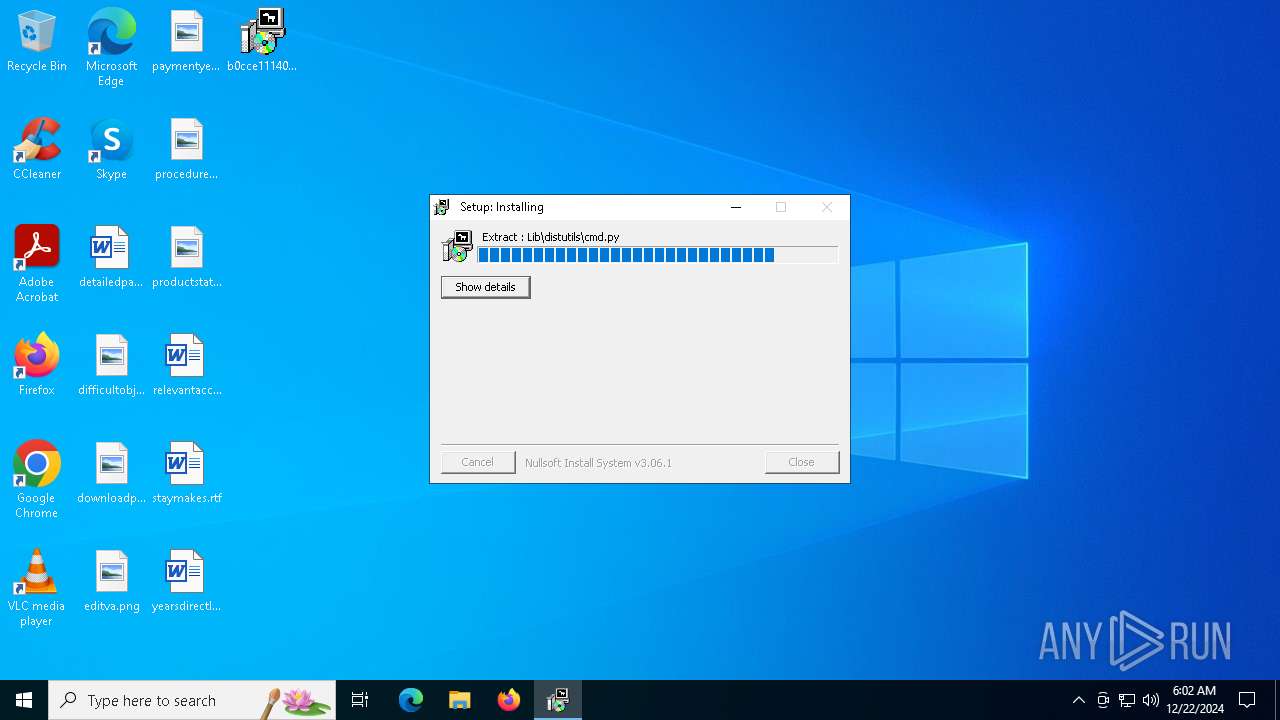
The process drops C-runtime libraries
- b0cce111400d44468c36721e44d0bd661b795d49d017e1b4dbe0b4d0d79669a0.zip.exe (PID: 3524)
Executable content was dropped or overwritten
- b0cce111400d44468c36721e44d0bd661b795d49d017e1b4dbe0b4d0d79669a0.zip.exe (PID: 3524)
Process drops legitimate windows executable
- b0cce111400d44468c36721e44d0bd661b795d49d017e1b4dbe0b4d0d79669a0.zip.exe (PID: 3524)
Process drops python dynamic module
- b0cce111400d44468c36721e44d0bd661b795d49d017e1b4dbe0b4d0d79669a0.zip.exe (PID: 3524)
The executable file from the user directory is run by the CMD process
- pythonw.exe (PID: 1876)
- pythonw.exe (PID: 448)
- pythonw.exe (PID: 2072)
- pythonw.exe (PID: 5880)
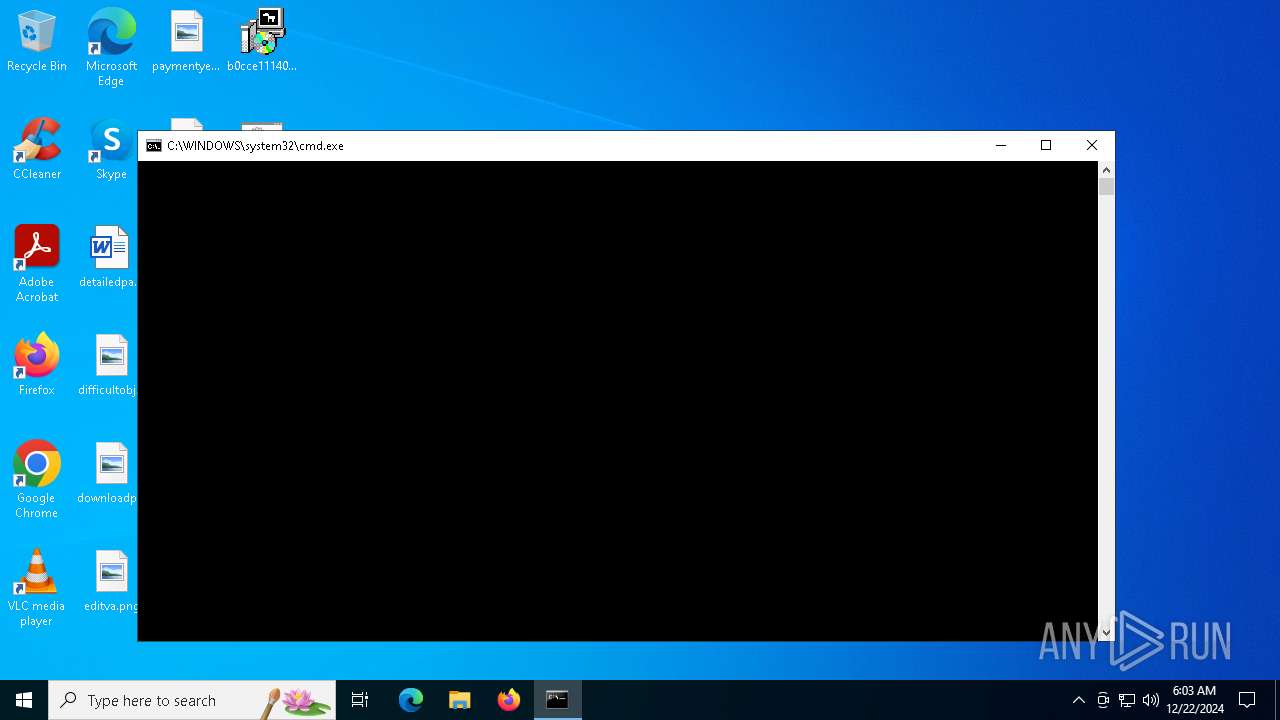
Starts CMD.EXE for commands execution
- b0cce111400d44468c36721e44d0bd661b795d49d017e1b4dbe0b4d0d79669a0.zip.exe (PID: 3524)
Executing commands from a ".bat" file
- b0cce111400d44468c36721e44d0bd661b795d49d017e1b4dbe0b4d0d79669a0.zip.exe (PID: 3524)
Loads Python modules
- pythonw.exe (PID: 448)
- pythonw.exe (PID: 5880)
- pythonw.exe (PID: 2072)
- pythonw.exe (PID: 1876)
- pythonw.exe (PID: 2072)
INFO
The sample compiled with english language support
- b0cce111400d44468c36721e44d0bd661b795d49d017e1b4dbe0b4d0d79669a0.zip.exe (PID: 3524)
Reads the computer name
- b0cce111400d44468c36721e44d0bd661b795d49d017e1b4dbe0b4d0d79669a0.zip.exe (PID: 3524)
- pythonw.exe (PID: 1876)
- pythonw.exe (PID: 448)
- pythonw.exe (PID: 2072)
- pythonw.exe (PID: 5880)
- pythonw.exe (PID: 2072)
- pythonw.exe (PID: 4516)
Create files in a temporary directory
- b0cce111400d44468c36721e44d0bd661b795d49d017e1b4dbe0b4d0d79669a0.zip.exe (PID: 3524)
Checks proxy server information
- b0cce111400d44468c36721e44d0bd661b795d49d017e1b4dbe0b4d0d79669a0.zip.exe (PID: 3524)
Checks supported languages
- b0cce111400d44468c36721e44d0bd661b795d49d017e1b4dbe0b4d0d79669a0.zip.exe (PID: 3524)
- pythonw.exe (PID: 1876)
- pythonw.exe (PID: 448)
- pythonw.exe (PID: 2072)
- pythonw.exe (PID: 5880)
- pythonw.exe (PID: 2072)
- pythonw.exe (PID: 4516)
Reads the machine GUID from the registry
- pythonw.exe (PID: 1876)
- pythonw.exe (PID: 448)
- pythonw.exe (PID: 2072)
- pythonw.exe (PID: 5880)
- pythonw.exe (PID: 2072)
- pythonw.exe (PID: 4516)
Creates files or folders in the user directory
- pythonw.exe (PID: 448)
- b0cce111400d44468c36721e44d0bd661b795d49d017e1b4dbe0b4d0d79669a0.zip.exe (PID: 3524)
- pythonw.exe (PID: 2072)
Python executable
- pythonw.exe (PID: 448)
- pythonw.exe (PID: 1876)
- pythonw.exe (PID: 2072)
- pythonw.exe (PID: 5880)
- pythonw.exe (PID: 2072)
- pythonw.exe (PID: 1796)
- pythonw.exe (PID: 4516)
Creates files in the program directory
- iexplore.exe (PID: 2076)
Drops encrypted VBS script (Microsoft Script Encoder)
- pythonw.exe (PID: 2072)
Drops encrypted JS script (Microsoft Script Encoder)
- pythonw.exe (PID: 2072)
Attempting to use instant messaging service
- iexplore.exe (PID: 2076)
Application launched itself
- msedge.exe (PID: 6356)
- chrome.exe (PID: 4520)
Manual execution by a user
- cmd.exe (PID: 6228)
- cmd.exe (PID: 2124)
- cmd.exe (PID: 3848)
Connects to unusual port
- iexplore.exe (PID: 6032)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:08:01 02:44:50+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26112 |
| InitializedDataSize: | 162816 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x3348 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 16306.39764.32702.60026 |
| ProductVersionNumber: | 16306.39764.32702.60026 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| FileDescription: | wrasfgeqagbnbarweGB sasfdwrктнеawrsgdfbawrgeabwе4руф5ынкер4уекнфыре4уткнrgsрsfef |
| FileVersion: | 432234233425345634253445243423.23423423434123534354423.2342343413245245231234.234423423563554544234234 |
| LegalCopyright: | ARSDGWBHRqeawtegbr wrasgdeqagwea dsfbwadgeqregd4еукып5р4уекныеs етfqEGRWFegsrb |
| ProductName: | rsb eanwregb arwsgbrwgaed wкнерукп45ре45нц4р5тнкуерreagdWEAD |
Total processes
162
Monitored processes
41
Malicious processes
7
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 448 | C:\Users\admin\AppData\Roaming\pythonw.exe C:\Users\admin\AppData\Roaming\python.dll | C:\Users\admin\AppData\Roaming\pythonw.exe | cmd.exe | ||||||||||||
User: admin Company: Python Software Foundation Integrity Level: MEDIUM Description: Python Exit code: 0 Version: 3.6.2 Modules
| |||||||||||||||
| 1416 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1796 | C:\Users\admin\AppData\Roaming\pythonw.exe C:\Users\admin\AppData\Roaming\1890.py | C:\Users\admin\AppData\Roaming\pythonw.exe | — | cmd.exe | |||||||||||
User: admin Company: Python Software Foundation Integrity Level: MEDIUM Description: Python Version: 3.6.2 | |||||||||||||||
| 1876 | C:\Users\admin\AppData\Roaming\pythonw.exe C:\Users\admin\AppData\Roaming\server.dll | C:\Users\admin\AppData\Roaming\pythonw.exe | cmd.exe | ||||||||||||
User: admin Company: Python Software Foundation Integrity Level: MEDIUM Description: Python Exit code: 0 Version: 3.6.2 Modules
| |||||||||||||||
| 1876 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --extension-process --no-appcompat-clear --remote-debugging-port=9223 --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --mojo-platform-channel-handle=3644 --field-trial-handle=1872,i,469195656591376719,7459936180349465745,262144 --variations-seed-version /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2012 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 2072 | C:\Users\admin\AppData\Roaming\pythonw.exe C:\Users\admin\AppData\Roaming\aynchat.dll | C:\Users\admin\AppData\Roaming\pythonw.exe | cmd.exe | ||||||||||||
User: admin Company: Python Software Foundation Integrity Level: MEDIUM Description: Python Exit code: 0 Version: 3.6.2 Modules
| |||||||||||||||
| 2072 | C:\Users\admin\AppData\Roaming\pythonw.exe C:\Users\admin\AppData\Roaming\python.dll | C:\Users\admin\AppData\Roaming\pythonw.exe | cmd.exe | ||||||||||||
User: admin Company: Python Software Foundation Integrity Level: MEDIUM Description: Python Exit code: 0 Version: 3.6.2 Modules
| |||||||||||||||
| 2076 | "C:\Program Files (x86)\Internet Explorer\iexplore.exe" | C:\Program Files (x86)\Internet Explorer\iexplore.exe | pythonw.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2124 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\setup.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
16 625
Read events
16 603
Write events
22
Delete events
0
Modification events
| (PID) Process: | (3524) b0cce111400d44468c36721e44d0bd661b795d49d017e1b4dbe0b4d0d79669a0.zip.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3524) b0cce111400d44468c36721e44d0bd661b795d49d017e1b4dbe0b4d0d79669a0.zip.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3524) b0cce111400d44468c36721e44d0bd661b795d49d017e1b4dbe0b4d0d79669a0.zip.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2076) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2076) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2076) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2072) pythonw.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Internet VPS |
Value: C:\Users\admin\AppData\Roaming\pythonw.exe C:\Users\admin\AppData\Roaming\1890.py | |||
| (PID) Process: | (2072) pythonw.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | |
Value: C:\Users\admin\AppData\Roaming\pythonw.exe C:\Users\admin\AppData\Roaming\1890.py | |||
| (PID) Process: | (4520) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (4520) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
Executable files
33
Suspicious files
263
Text files
690
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3524 | b0cce111400d44468c36721e44d0bd661b795d49d017e1b4dbe0b4d0d79669a0.zip.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\ASA[1].zip | compressed | |
MD5:B5CC6067C040540BE40C8CAEA1AD66D9 | SHA256:0A3DB2A868C2B6F4EA1218E39F9A3E5AE8A8F7DC59B1806DDDBF0E87C5A19401 | |||
| 3524 | b0cce111400d44468c36721e44d0bd661b795d49d017e1b4dbe0b4d0d79669a0.zip.exe | C:\Users\admin\AppData\Roaming\DLLs\pyd.ico | image | |
MD5:1A8230030D821CF8EA57CE03AAEAD737 | SHA256:C4EC1845A5724B2A83500F3BD940355E2FE26EFC6B4FE6C208365359A6130DA1 | |||
| 3524 | b0cce111400d44468c36721e44d0bd661b795d49d017e1b4dbe0b4d0d79669a0.zip.exe | C:\Users\admin\AppData\Roaming\DLLs\python_lib.cat | binary | |
MD5:E1285F1B913AB82C796BFAE654CD39F0 | SHA256:AC1B76AFF8FBE54A254F885B91DB276ADEEAF56E9EDBE2CA99F8E0879360C48F | |||
| 3524 | b0cce111400d44468c36721e44d0bd661b795d49d017e1b4dbe0b4d0d79669a0.zip.exe | C:\Users\admin\AppData\Roaming\vcruntime140.dll | executable | |
MD5:A2523EA6950E248CBDF18C9EA1A844F6 | SHA256:6823B98C3E922490A2F97F54862D32193900077E49F0360522B19E06E6DA24B4 | |||
| 3524 | b0cce111400d44468c36721e44d0bd661b795d49d017e1b4dbe0b4d0d79669a0.zip.exe | C:\Users\admin\AppData\Roaming\ASA.zip | compressed | |
MD5:B5CC6067C040540BE40C8CAEA1AD66D9 | SHA256:0A3DB2A868C2B6F4EA1218E39F9A3E5AE8A8F7DC59B1806DDDBF0E87C5A19401 | |||
| 3524 | b0cce111400d44468c36721e44d0bd661b795d49d017e1b4dbe0b4d0d79669a0.zip.exe | C:\Users\admin\AppData\Roaming\DLLs\pyc.ico | image | |
MD5:B1C9980131A3F20E344AA3AA2C8DEA49 | SHA256:FDA28A734788A3F175CB6AED4DAEB5F05F0E49F6A272CCD2051BA337F7B3B42F | |||
| 3524 | b0cce111400d44468c36721e44d0bd661b795d49d017e1b4dbe0b4d0d79669a0.zip.exe | C:\Users\admin\AppData\Roaming\DLLs\pyexpat.pyd | executable | |
MD5:CBA7C3A0A2CD8A823F767678F5C43AD9 | SHA256:FEF4D45CF715C41DC494044C0FE28C66F7801D11419750D1A1621402CD978EDC | |||
| 3524 | b0cce111400d44468c36721e44d0bd661b795d49d017e1b4dbe0b4d0d79669a0.zip.exe | C:\Users\admin\AppData\Roaming\DLLs\py.ico | image | |
MD5:B35F68A3086562C4D5453FAAD5A3474E | SHA256:150C470F9943B806B44312EFDEC85755F22F8D7D52B31F93A9AF3C43E8627381 | |||
| 3524 | b0cce111400d44468c36721e44d0bd661b795d49d017e1b4dbe0b4d0d79669a0.zip.exe | C:\Users\admin\AppData\Local\Temp\nsf9678.tmp\InetLoad.dll | executable | |
MD5:994669C5737B25C26642C94180E92FA2 | SHA256:BF01A1F272E0DAF82DF3407690B646E0FF6B2C562E36E47CF177EDA71CCB6F6C | |||
| 3524 | b0cce111400d44468c36721e44d0bd661b795d49d017e1b4dbe0b4d0d79669a0.zip.exe | C:\Users\admin\AppData\Roaming\DLLs\_bz2.pyd | executable | |
MD5:1C1132C6C1FBAEA66584A7AC0A275346 | SHA256:ACE8CA107D874102F3B7423F5BE473EC75B97E4E480CE98F7585D2255F172D99 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
111
TCP/UDP connections
133
DNS requests
57
Threats
12
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
880 | svchost.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2624 | RUXIMICS.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
880 | svchost.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2624 | RUXIMICS.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 142.250.186.100:443 | https://toptek.sbs/ | unknown | — | — | unknown |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | — | 142.250.186.100:443 | https://www.google.com/async/ddljson?async=ntp:2 | unknown | — | — | unknown |
— | — | POST | 200 | 104.21.112.1:443 | https://driblbemris.lat/api | unknown | text | 2 b | unknown |
— | — | GET | 200 | 149.154.167.99:443 | https://t.me/k04ael | unknown | html | 12.0 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2624 | RUXIMICS.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
880 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.21.110.146:443 | www.bing.com | AKAMAI-AS | DE | whitelisted |
880 | svchost.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2624 | RUXIMICS.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
880 | svchost.exe | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
driblbemris.lat |
| unknown |
t.me |
| whitelisted |
toptek.sbs |
| unknown |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3524 | b0cce111400d44468c36721e44d0bd661b795d49d017e1b4dbe0b4d0d79669a0.zip.exe | Misc activity | ET HUNTING ZIP file download over raw TCP |
3524 | b0cce111400d44468c36721e44d0bd661b795d49d017e1b4dbe0b4d0d79669a0.zip.exe | Misc activity | INFO [ANY.RUN] FTP server is ready for the new user |
448 | pythonw.exe | Misc activity | INFO [ANY.RUN] FTP server is ready for the new user |
2076 | iexplore.exe | Misc activity | ET INFO Observed Telegram Domain (t .me in TLS SNI) |
1876 | pythonw.exe | Misc activity | INFO [ANY.RUN] FTP server is ready for the new user |
5880 | pythonw.exe | Misc activity | INFO [ANY.RUN] FTP server is ready for the new user |
2072 | pythonw.exe | Misc activity | INFO [ANY.RUN] FTP server is ready for the new user |
4516 | pythonw.exe | Misc activity | INFO [ANY.RUN] FTP server is ready for the new user |
— | — | Misc activity | INFO [ANY.RUN] FTP server is ready for the new user |
3 ETPRO signatures available at the full report