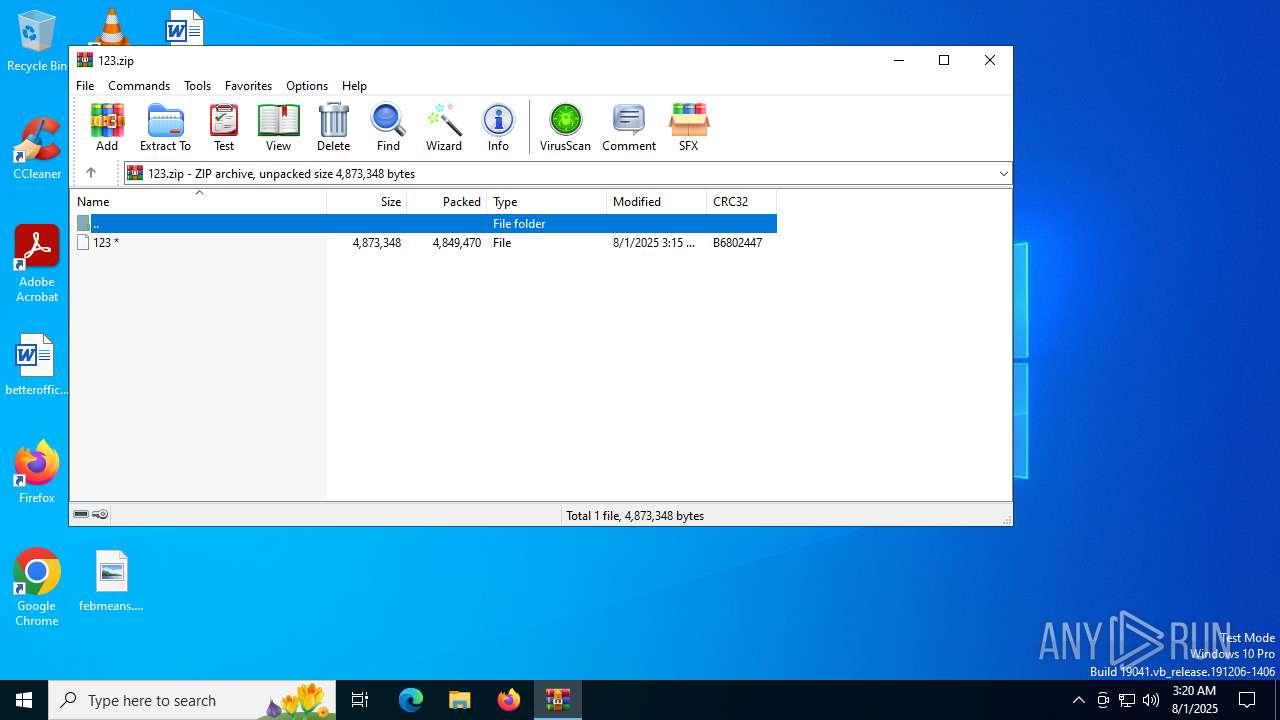
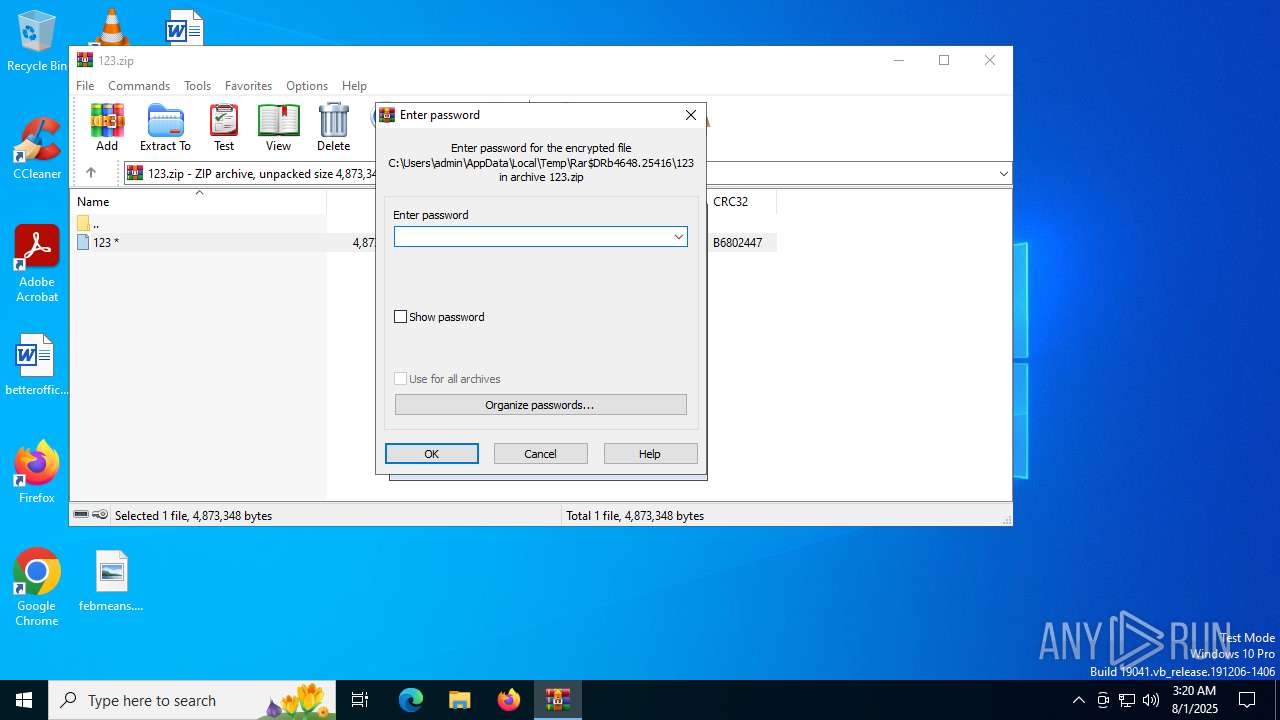
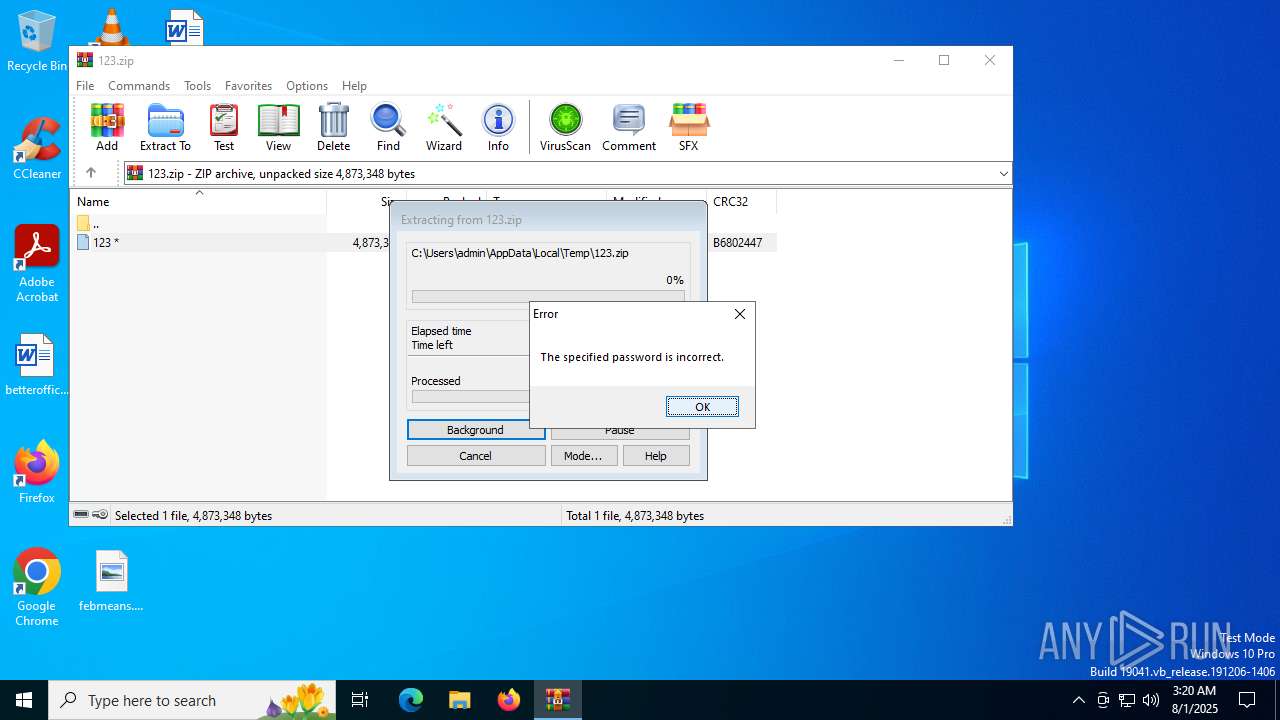
| File name: | 123.zip |
| Full analysis: | https://app.any.run/tasks/0aaf8577-5330-4872-8305-3a926b45b2a3 |
| Verdict: | Malicious activity |
| Threats: | A botnet is a group of internet-connected devices that are controlled by a single individual or group, often without the knowledge or consent of the device owners. These devices can be used to launch a variety of malicious attacks, such as distributed denial-of-service (DDoS) attacks, spam campaigns, and data theft. Botnet malware is the software that is used to infect devices and turn them into part of a botnet. |
| Analysis date: | August 01, 2025, 03:20:34 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 0FF7A0768EB3F146A4F3D678962F25F4 |
| SHA1: | F707291B8443F6F7E0C33B96B3B4ABD7956EE246 |
| SHA256: | B0AA2EBEC798A008EBA01E646C3AFEFAF6E3202D08BAA219AE9BA0533A9D4D29 |
| SSDEEP: | 98304:Bplr/0qthMbu6jbEq+Mxpvfy1ewpCQoSwg1UG5UwV+FjOGrwpUaDU1WNCRUWkGsf:Sbyrb |
MALICIOUS
SOCKS5SYSTEMZ has been found (auto)
- WinRAR.exe (PID: 4648)
SUSPICIOUS
Executable content was dropped or overwritten
- 123.exe (PID: 2320)
- 123.tmp (PID: 3624)
- xmldriveimage681.exe (PID: 5012)
The process drops C-runtime libraries
- 123.tmp (PID: 3624)
Reads the Windows owner or organization settings
- 123.tmp (PID: 3624)
Process drops legitimate windows executable
- 123.tmp (PID: 3624)
Checks for external IP
- xmldriveimage681.exe (PID: 5012)
Starts POWERSHELL.EXE for commands execution
- xmldriveimage681.exe (PID: 5012)
Reads security settings of Internet Explorer
- xmldriveimage681.exe (PID: 5012)
Connects to unusual port
- xmldriveimage681.exe (PID: 5012)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4648)
Manual execution by a user
- 123.exe (PID: 2320)
Create files in a temporary directory
- 123.tmp (PID: 3624)
- 123.exe (PID: 2320)
Reads the computer name
- 123.tmp (PID: 3624)
- xmldriveimage681.exe (PID: 5012)
Creates files or folders in the user directory
- 123.tmp (PID: 3624)
- xmldriveimage681.exe (PID: 5012)
Checks supported languages
- 123.tmp (PID: 3624)
- xmldriveimage681.exe (PID: 5012)
- 123.exe (PID: 2320)
Creates files in the program directory
- xmldriveimage681.exe (PID: 5012)
The sample compiled with english language support
- 123.tmp (PID: 3624)
- xmldriveimage681.exe (PID: 5012)
Creates a software uninstall entry
- 123.tmp (PID: 3624)
Process checks computer location settings
- xmldriveimage681.exe (PID: 5012)
Detects InnoSetup installer (YARA)
- 123.tmp (PID: 3624)
- 123.exe (PID: 2320)
Changes the registry key values via Powershell
- xmldriveimage681.exe (PID: 5012)
Compiled with Borland Delphi (YARA)
- 123.tmp (PID: 3624)
Checks proxy server information
- slui.exe (PID: 6004)
- xmldriveimage681.exe (PID: 5012)
Reads the software policy settings
- slui.exe (PID: 6004)
- xmldriveimage681.exe (PID: 5012)
Reads the machine GUID from the registry
- xmldriveimage681.exe (PID: 5012)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:07:31 20:15:26 |
| ZipCRC: | 0xb6802447 |
| ZipCompressedSize: | 4849470 |
| ZipUncompressedSize: | 4873348 |
| ZipFileName: | 123 |
Total processes
152
Monitored processes
7
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2320 | "C:\Users\admin\Desktop\123.exe" | C:\Users\admin\Desktop\123.exe | explorer.exe | ||||||||||||
User: admin Company: Integrity Level: MEDIUM Description: XML Drive Image Setup Version: Modules
| |||||||||||||||
| 2632 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -c Set-ItemProperty -Path "HKCU:\Software\Microsoft\Windows\CurrentVersion\Run" -Name "XDriveIMG" -Value "C:\ProgramData\XMLDriveImage\XMLDriveImage.exe" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | xmldriveimage681.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3624 | "C:\Users\admin\AppData\Local\Temp\is-3C9F2.tmp\123.tmp" /SL5="$D02EA,4625181,54272,C:\Users\admin\Desktop\123.exe" | C:\Users\admin\AppData\Local\Temp\is-3C9F2.tmp\123.tmp | 123.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Version: 51.52.0.0 Modules
| |||||||||||||||
| 4648 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\123.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 5012 | "C:\Users\admin\AppData\Local\XML Drive Image 0.58.0.4681\xmldriveimage681.exe" -i | C:\Users\admin\AppData\Local\XML Drive Image 0.58.0.4681\xmldriveimage681.exe | 123.tmp | ||||||||||||
User: admin Integrity Level: MEDIUM Description: XML Drive Image Version: 0.58.0.4681 Modules
| |||||||||||||||
| 6004 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6240 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
10 259
Read events
10 229
Write events
30
Delete events
0
Modification events
| (PID) Process: | (4648) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (4648) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (4648) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4648) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4648) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4648) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\123.zip | |||
| (PID) Process: | (4648) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4648) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4648) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4648) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
27
Suspicious files
5
Text files
4
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4648 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb4648.25416\123 | executable | |
MD5:F0B31BDEFA1DFF785DCBEEEA9D728FE5 | SHA256:88F29EBF0FB26F74A6E58202822B240A7F886FEA2C3E76CADE2A1017E87AE2DB | |||
| 2320 | 123.exe | C:\Users\admin\AppData\Local\Temp\is-3C9F2.tmp\123.tmp | executable | |
MD5:2F699DD6985220D236F66253422526C5 | SHA256:662B1420DB85EF8D3FE233C5F6E99D668084A69BCE195C81545E393B0E3E7B32 | |||
| 3624 | 123.tmp | C:\Users\admin\AppData\Local\XML Drive Image 0.58.0.4681\uninstall\is-RL4T4.tmp | executable | |
MD5:C077CFEB288FE31F3448815B6C453DB2 | SHA256:CA35A27F164486E22E5B4AB9930C7E0BF6EFC9FFF410512E299646F04B31E778 | |||
| 3624 | 123.tmp | C:\Users\admin\AppData\Local\Temp\is-GV1QG.tmp\_isetup\_setup64.tmp | executable | |
MD5:4FF75F505FDDCC6A9AE62216446205D9 | SHA256:A4C86FC4836AC728D7BD96E7915090FD59521A9E74F1D06EF8E5A47C8695FD81 | |||
| 3624 | 123.tmp | C:\Users\admin\AppData\Local\XML Drive Image 0.58.0.4681\uninstall\unins000.exe | executable | |
MD5:C077CFEB288FE31F3448815B6C453DB2 | SHA256:CA35A27F164486E22E5B4AB9930C7E0BF6EFC9FFF410512E299646F04B31E778 | |||
| 3624 | 123.tmp | C:\Users\admin\AppData\Local\XML Drive Image 0.58.0.4681\is-FOIRV.tmp | executable | |
MD5:EAE56B896A718C3BC87A4253832A5650 | SHA256:EE1D7D8F396D627FEE7DCF2655FB5ACFE5A1EE2A5DEEDA764EF311E75B94CEA1 | |||
| 3624 | 123.tmp | C:\Users\admin\AppData\Local\XML Drive Image 0.58.0.4681\is-G3OMK.tmp | — | |
MD5:— | SHA256:— | |||
| 3624 | 123.tmp | C:\Users\admin\AppData\Local\XML Drive Image 0.58.0.4681\xmldriveimage681.exe | — | |
MD5:— | SHA256:— | |||
| 3624 | 123.tmp | C:\Users\admin\AppData\Local\XML Drive Image 0.58.0.4681\icuin51.dll | executable | |
MD5:A7F201C0B9AC05E950ECC55D4403EC16 | SHA256:173092C4E256958B100683A6AB2CE0D1C9895EC63F222198F9DE485E61C728CA | |||
| 3624 | 123.tmp | C:\Users\admin\AppData\Local\XML Drive Image 0.58.0.4681\msvcr100.dll | executable | |
MD5:BF38660A9125935658CFA3E53FDC7D65 | SHA256:60C06E0FA4449314DA3A0A87C1A9D9577DF99226F943637E06F61188E5862EFA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
39
DNS requests
26
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2528 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4768 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4768 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 72.246.169.163:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
5012 | xmldriveimage681.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | unknown | — | — | whitelisted |
5012 | xmldriveimage681.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | unknown | — | — | whitelisted |
5012 | xmldriveimage681.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECEQD4YMPNfNbP1JKHdHRDbiB0 | unknown | — | — | whitelisted |
6368 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6584 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
2528 | svchost.exe | 20.190.160.17:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2528 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |