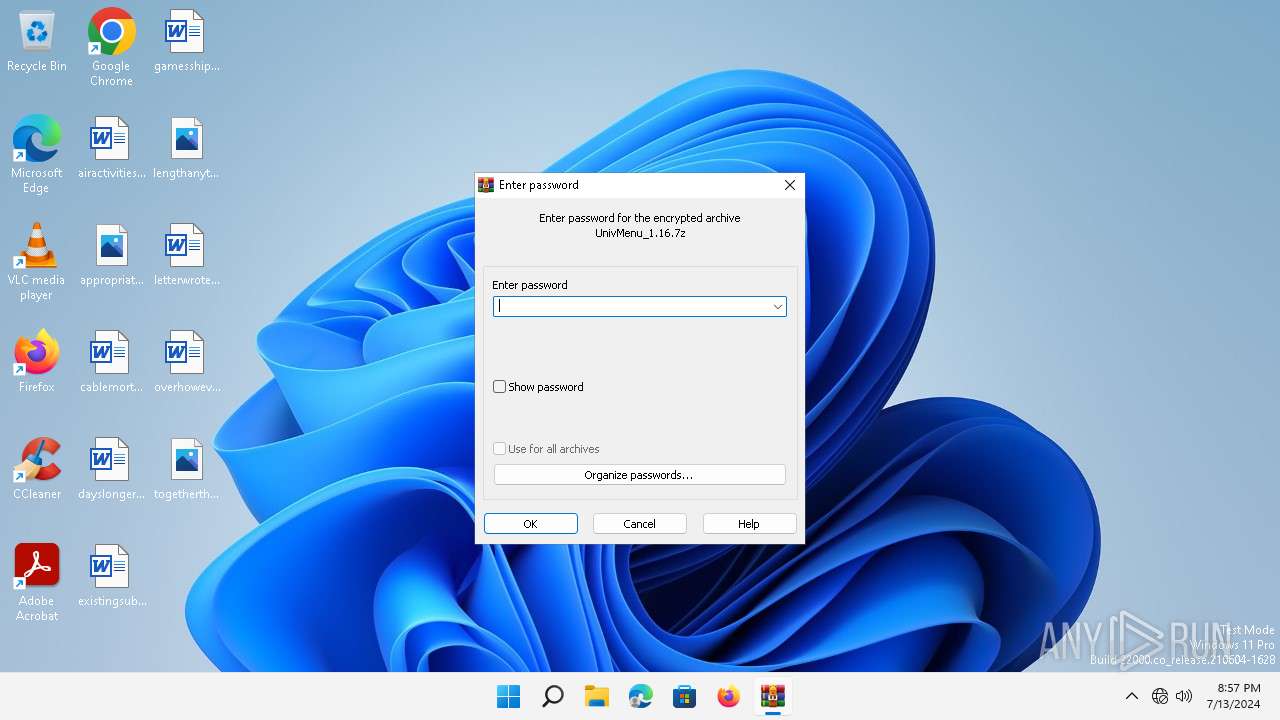
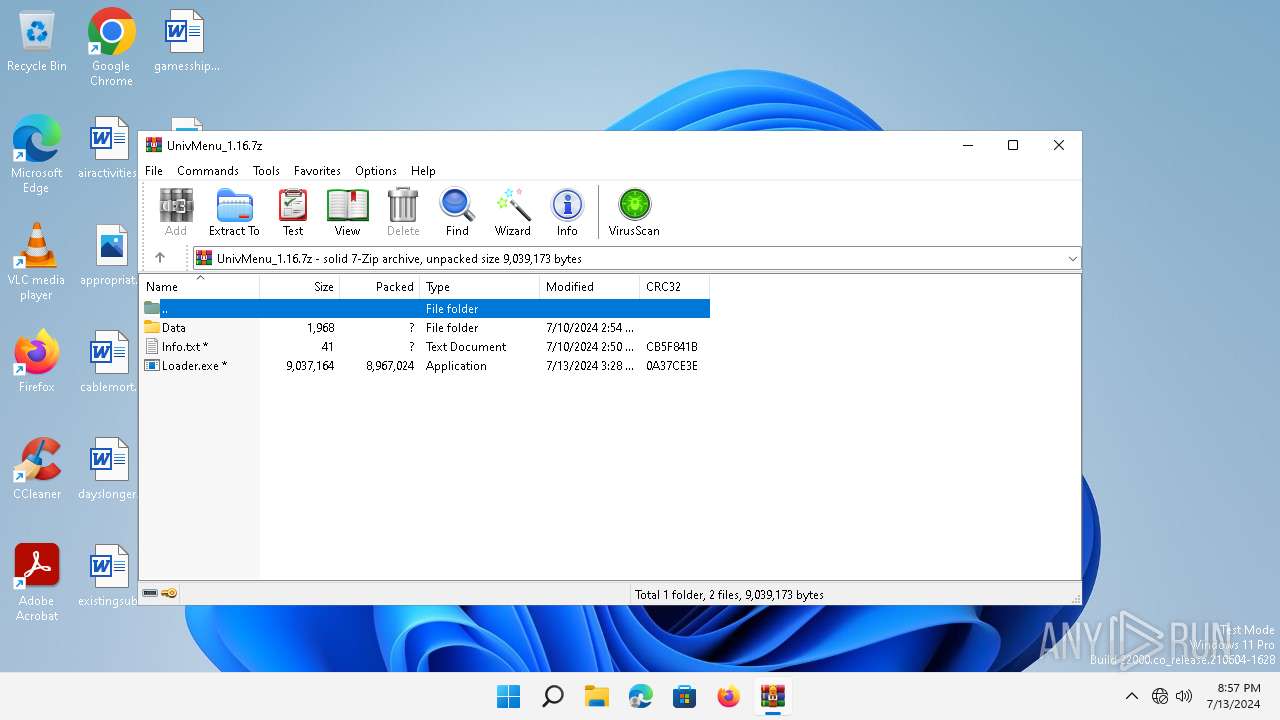
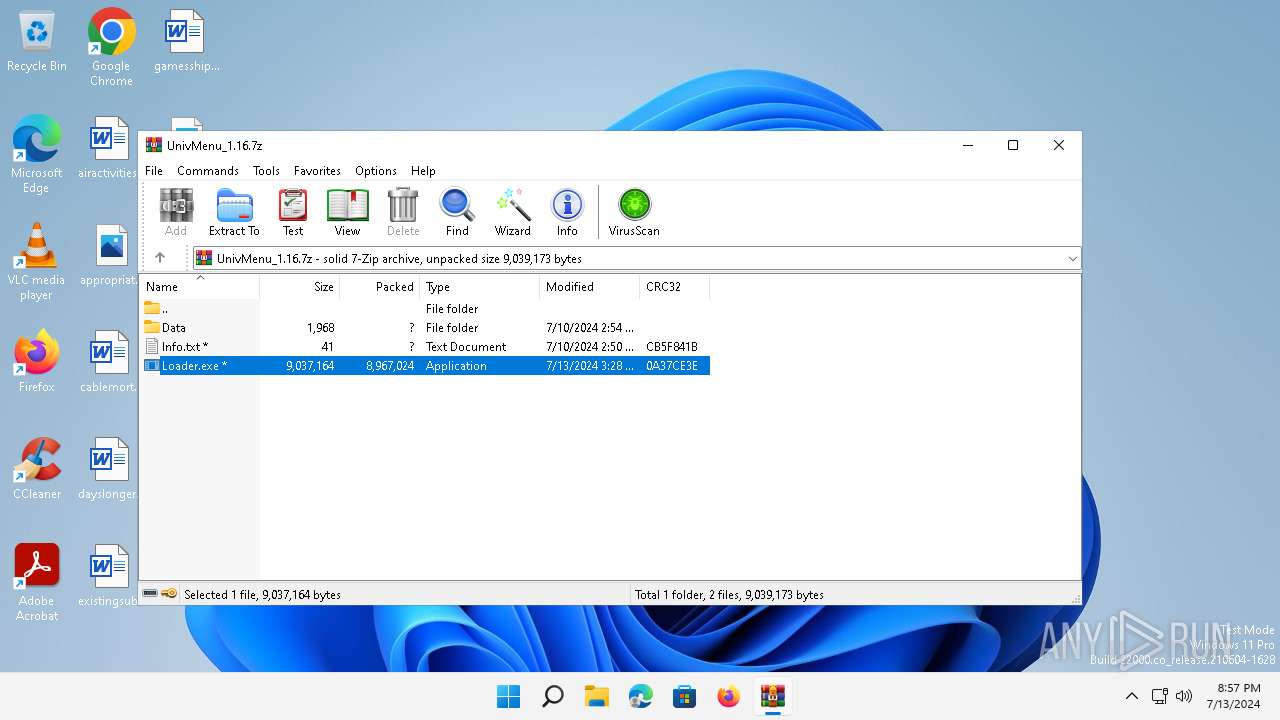
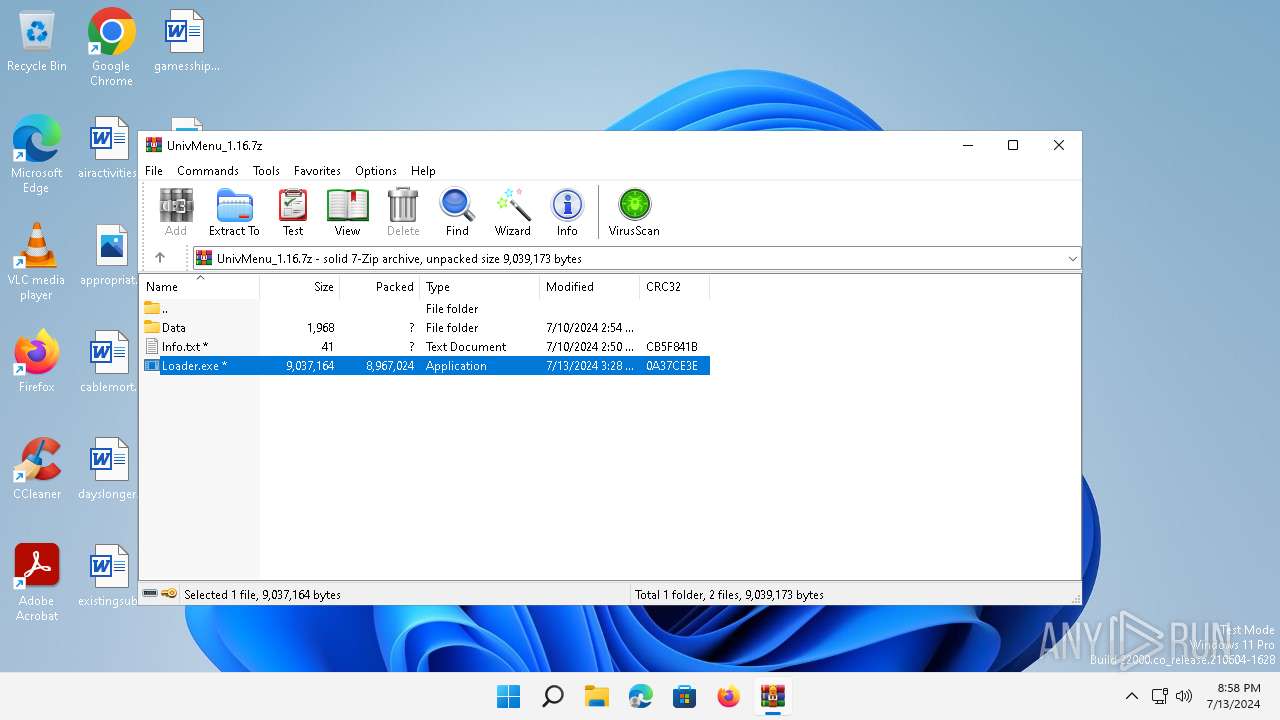
| File name: | UnivMenu_1.16.7z |
| Full analysis: | https://app.any.run/tasks/4c6a3e26-30ff-444a-9d2a-76e746e63694 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | July 13, 2024, 20:57:35 |
| OS: | Windows 11 Professional (build: 22000, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 5A643CA6DB7C42CE8EF4F7FD7C9B1F98 |
| SHA1: | DC0806360A0C41F0A8171633CA5BE6FA8B0BCA29 |
| SHA256: | B00DB80C33FFFE8E0484331C39CB8A34210A6AE5B5C553920EF038B7DE087B20 |
| SSDEEP: | 98304:D00h6ACai0icMqaj54c3vKkg4n0S99z+kvhqG2x4cP2p+jSKqKP2Oe8y6BasGdPf:hdNrDZoTBJD |
MALICIOUS
Drops the executable file immediately after the start
- wmiss.exe (PID: 4252)
- wmi.exe (PID: 504)
- update.exe (PID: 2956)
- wmis.exe (PID: 3132)
- Loader.exe (PID: 1476)
Uses Task Scheduler to run other applications
- wmi.exe (PID: 504)
Adds extension to the Windows Defender exclusion list
- wmis.exe (PID: 3132)
- update.exe (PID: 2956)
Creates a writable file in the system directory
- powershell.exe (PID: 5236)
LUMMA has been detected (SURICATA)
- aspnet_regiis.exe (PID: 1916)
SILENTCRYPTOMINER has been detected (SURICATA)
- dwm.exe (PID: 2532)
Connects to the CnC server
- dwm.exe (PID: 2532)
Actions looks like stealing of personal data
- aspnet_regiis.exe (PID: 1916)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 2796)
Executable content was dropped or overwritten
- Loader.exe (PID: 1476)
- wmiss.exe (PID: 4252)
- wmi.exe (PID: 504)
- wmis.exe (PID: 3132)
- update.exe (PID: 2956)
Reads settings of System Certificates
- aspnet_regiis.exe (PID: 1916)
Uses powercfg.exe to modify the power settings
- wmis.exe (PID: 3132)
- update.exe (PID: 2956)
Script adds exclusion extension to Windows Defender
- wmis.exe (PID: 3132)
- update.exe (PID: 2956)
Starts POWERSHELL.EXE for commands execution
- wmis.exe (PID: 3132)
- update.exe (PID: 2956)
Script adds exclusion path to Windows Defender
- wmis.exe (PID: 3132)
- update.exe (PID: 2956)
Searches for installed software
- aspnet_regiis.exe (PID: 1916)
Starts CMD.EXE for commands execution
- wmis.exe (PID: 3132)
- update.exe (PID: 2956)
Reads the Internet Settings
- aspnet_regiis.exe (PID: 1916)
Executes as Windows Service
- update.exe (PID: 2956)
The process creates files with name similar to system file names
- powershell.exe (PID: 5236)
Starts SC.EXE for service management
- wmis.exe (PID: 3132)
Process uninstalls Windows update
- wusa.exe (PID: 1956)
- wusa.exe (PID: 4368)
Contacting a server suspected of hosting an CnC
- aspnet_regiis.exe (PID: 1916)
Connects to unusual port
- dwm.exe (PID: 2532)
Found regular expressions for crypto-addresses (YARA)
- wmi.exe (PID: 504)
Crypto Currency Mining Activity Detected
- dwm.exe (PID: 2532)
Drops a system driver (possible attempt to evade defenses)
- update.exe (PID: 2956)
INFO
Checks supported languages
- Loader.exe (PID: 1476)
- wmis.exe (PID: 3132)
- wmiss.exe (PID: 4252)
- wmi.exe (PID: 504)
- aspnet_regiis.exe (PID: 1916)
- update.exe (PID: 2956)
Create files in a temporary directory
- Loader.exe (PID: 1476)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2796)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2796)
Reads the computer name
- wmiss.exe (PID: 4252)
- aspnet_regiis.exe (PID: 1916)
Creates files or folders in the user directory
- wmi.exe (PID: 504)
- wmiss.exe (PID: 4252)
Reads the software policy settings
- aspnet_regiis.exe (PID: 1916)
Reads the machine GUID from the registry
- aspnet_regiis.exe (PID: 1916)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 5788)
- powershell.exe (PID: 5236)
Creates files in the program directory
- wmis.exe (PID: 3132)
UPX packer has been detected
- dwm.exe (PID: 2532)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
148
Monitored processes
50
Malicious processes
8
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 504 | C:\Users\admin\AppData\Local\Temp\wmi.exe | C:\Users\admin\AppData\Local\Temp\wmi.exe | Loader.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 580 | \??\C:\Windows\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | sc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 988 | \??\C:\Windows\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1136 | \??\C:\Windows\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powercfg.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1476 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb2796.8718\Loader.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb2796.8718\Loader.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1736 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb2796.8718\Loader.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb2796.8718\Loader.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 1740 | \??\C:\Windows\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | schtasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1788 | C:\Windows\system32\cmd.exe /c wusa /uninstall /kb:890830 /quiet /norestart | C:\Windows\System32\cmd.exe | — | update.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 87 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1820 | C:\Windows\system32\powercfg.exe /x -standby-timeout-dc 0 | C:\Windows\System32\powercfg.exe | — | wmis.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Power Settings Command-Line Tool Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1856 | \??\C:\Windows\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
27 554
Read events
27 527
Write events
27
Delete events
0
Modification events
| (PID) Process: | (2796) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | VerInfo |
Value: 005B0500F0886D5067D5DA01 | |||
| (PID) Process: | (2796) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2796) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2796) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (2796) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\UnivMenu_1.16.7z | |||
| (PID) Process: | (2796) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2796) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2796) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2796) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2796) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
8
Suspicious files
3
Text files
58
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2796 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2796.8718\Data\gsdagsdg - Copy (11) - Copy.txt | text | |
MD5:A855A4B3C1CEA75E19FEA7F6A2E0281B | SHA256:6FA90940945D0FEFA4E6433238D41C208244CF7449E9646F36A542DA78D394E9 | |||
| 2796 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2796.8718\Data\gsdagsdg - Copy (10) - Copy.txt | text | |
MD5:A855A4B3C1CEA75E19FEA7F6A2E0281B | SHA256:6FA90940945D0FEFA4E6433238D41C208244CF7449E9646F36A542DA78D394E9 | |||
| 2796 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2796.8718\Data\gsdagsdg - Copy (10).txt | text | |
MD5:A855A4B3C1CEA75E19FEA7F6A2E0281B | SHA256:6FA90940945D0FEFA4E6433238D41C208244CF7449E9646F36A542DA78D394E9 | |||
| 2796 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2796.8718\Data\gsdagsdg - Copy (14).txt | text | |
MD5:A855A4B3C1CEA75E19FEA7F6A2E0281B | SHA256:6FA90940945D0FEFA4E6433238D41C208244CF7449E9646F36A542DA78D394E9 | |||
| 2796 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2796.8718\Data\gsdagsdg - Copy (19) - Copy.txt | text | |
MD5:A855A4B3C1CEA75E19FEA7F6A2E0281B | SHA256:6FA90940945D0FEFA4E6433238D41C208244CF7449E9646F36A542DA78D394E9 | |||
| 2796 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2796.8718\Data\gsdagsdg - Copy (15).txt | text | |
MD5:A855A4B3C1CEA75E19FEA7F6A2E0281B | SHA256:6FA90940945D0FEFA4E6433238D41C208244CF7449E9646F36A542DA78D394E9 | |||
| 2796 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2796.8718\Data\gsdagsdg - Copy (16) - Copy.txt | text | |
MD5:A855A4B3C1CEA75E19FEA7F6A2E0281B | SHA256:6FA90940945D0FEFA4E6433238D41C208244CF7449E9646F36A542DA78D394E9 | |||
| 2796 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2796.8718\Data\gsdagsdg - Copy (18) - Copy.txt | text | |
MD5:A855A4B3C1CEA75E19FEA7F6A2E0281B | SHA256:6FA90940945D0FEFA4E6433238D41C208244CF7449E9646F36A542DA78D394E9 | |||
| 2796 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2796.8718\Data\gsdagsdg - Copy (16).txt | text | |
MD5:A855A4B3C1CEA75E19FEA7F6A2E0281B | SHA256:6FA90940945D0FEFA4E6433238D41C208244CF7449E9646F36A542DA78D394E9 | |||
| 2796 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2796.8718\Data\gsdagsdg - Copy (17).txt | text | |
MD5:A855A4B3C1CEA75E19FEA7F6A2E0281B | SHA256:6FA90940945D0FEFA4E6433238D41C208244CF7449E9646F36A542DA78D394E9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
24
TCP/UDP connections
30
DNS requests
10
Threats
20
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | HEAD | 200 | 23.35.236.109:443 | https://fs.microsoft.com/fs/windows/config.json | unknown | — | — | unknown |
1332 | svchost.exe | GET | 200 | 88.221.110.147:80 | http://www.msftconnecttest.com/connecttest.txt | unknown | — | — | whitelisted |
3984 | svchost.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?4853f0d6c45594a7 | unknown | — | — | whitelisted |
1088 | svchost.exe | POST | 403 | 184.28.89.167:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
1088 | svchost.exe | POST | 403 | 184.28.89.167:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
1088 | svchost.exe | POST | 403 | 184.28.89.167:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
1088 | svchost.exe | POST | 403 | 184.28.89.167:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
1088 | svchost.exe | POST | 403 | 184.28.89.167:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
1088 | svchost.exe | POST | 403 | 184.28.89.167:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
1088 | svchost.exe | POST | 403 | 184.28.89.167:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4552 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1332 | svchost.exe | 88.221.110.216:80 | — | Akamai International B.V. | DE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1504 | svchost.exe | 23.43.61.160:443 | fs.microsoft.com | Akamai International B.V. | US | unknown |
1332 | svchost.exe | 88.221.110.147:80 | — | Akamai International B.V. | DE | unknown |
3984 | svchost.exe | 20.190.160.22:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3984 | svchost.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
2844 | svchost.exe | 20.189.173.26:443 | v10.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
2844 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1088 | svchost.exe | 184.28.89.167:80 | go.microsoft.com | AKAMAI-AS | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
fs.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
v10.events.data.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
bitchsafettyudjwu.shop |
| malicious |
xmr-eu1.nanopool.org |
| whitelisted |
pastebin.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1332 | svchost.exe | Misc activity | ET INFO Microsoft Connection Test |
1656 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Lumma Stealer Related CnC Domain in DNS Lookup |
1916 | aspnet_regiis.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Lumma Stealer Related Domain |
— | — | A Network Trojan was detected | ET MALWARE Lumma Stealer Related Activity |
— | — | A Network Trojan was detected | ET MALWARE Lumma Stealer Related Activity M2 |
— | — | Malware Command and Control Activity Detected | STEALER [ANY.RUN] Win32/Lumma Stealer Check-In |
1916 | aspnet_regiis.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Lumma Stealer Related Domain |
— | — | Malware Command and Control Activity Detected | ET MALWARE [ANY.RUN] Win32/Lumma Stealer Exfiltration |
— | — | Malware Command and Control Activity Detected | STEALER [ANY.RUN] Win32/Lumma Stealer Exfiltration |
1916 | aspnet_regiis.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Lumma Stealer Related Domain |
2 ETPRO signatures available at the full report