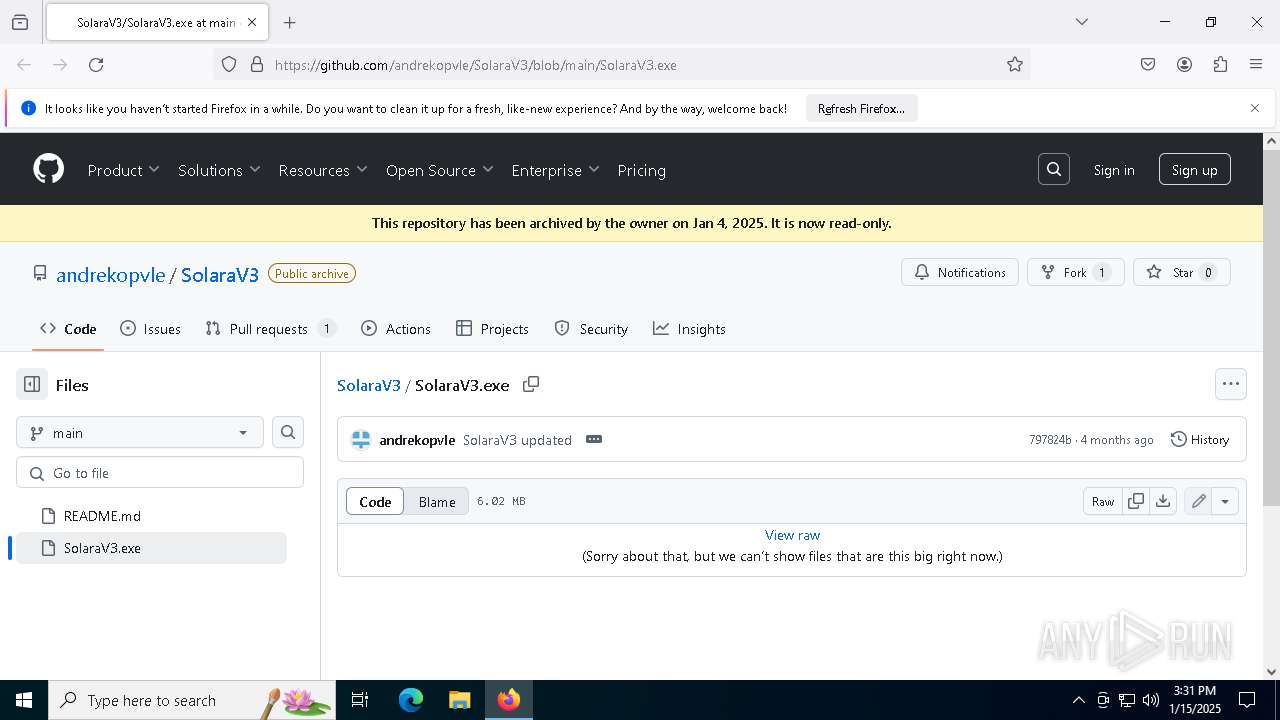
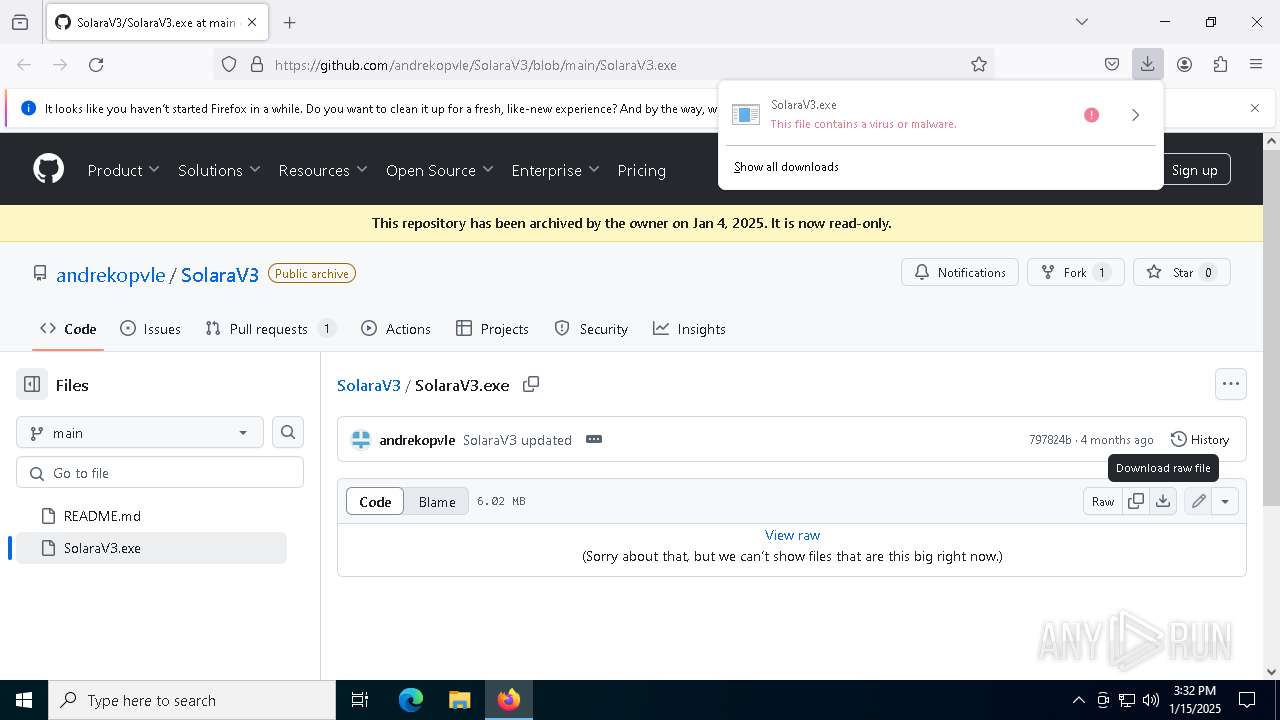
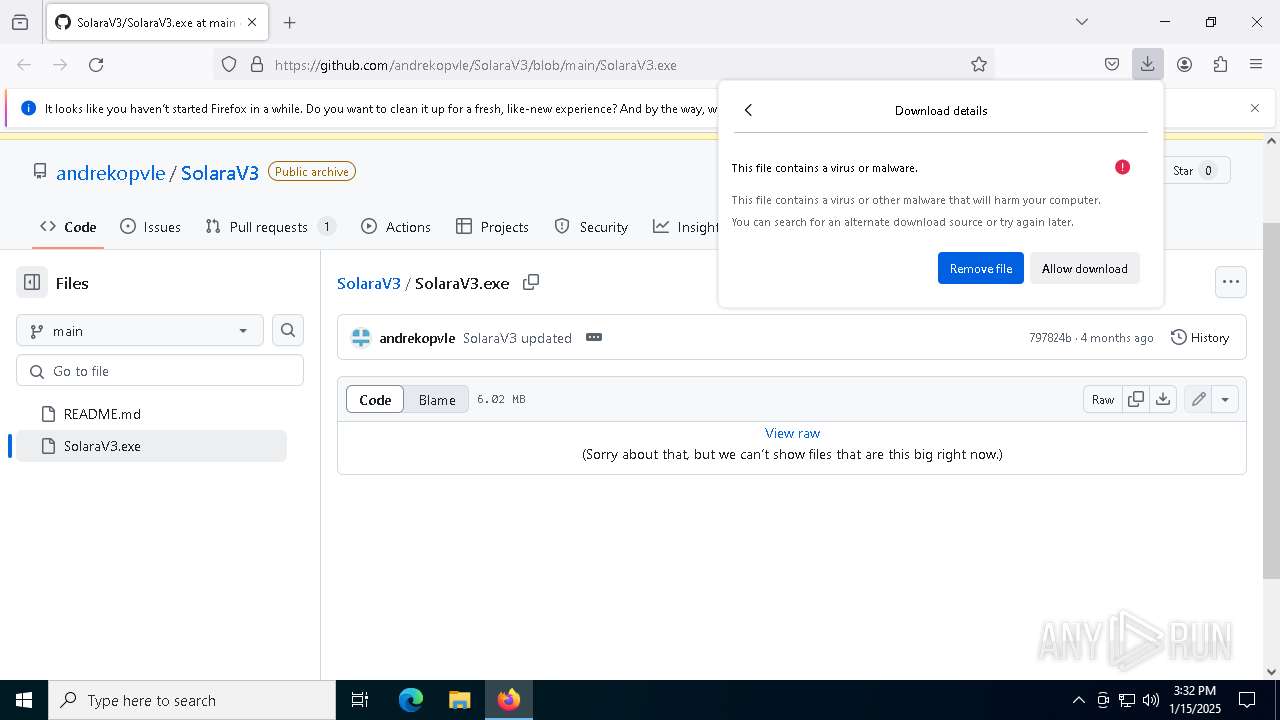
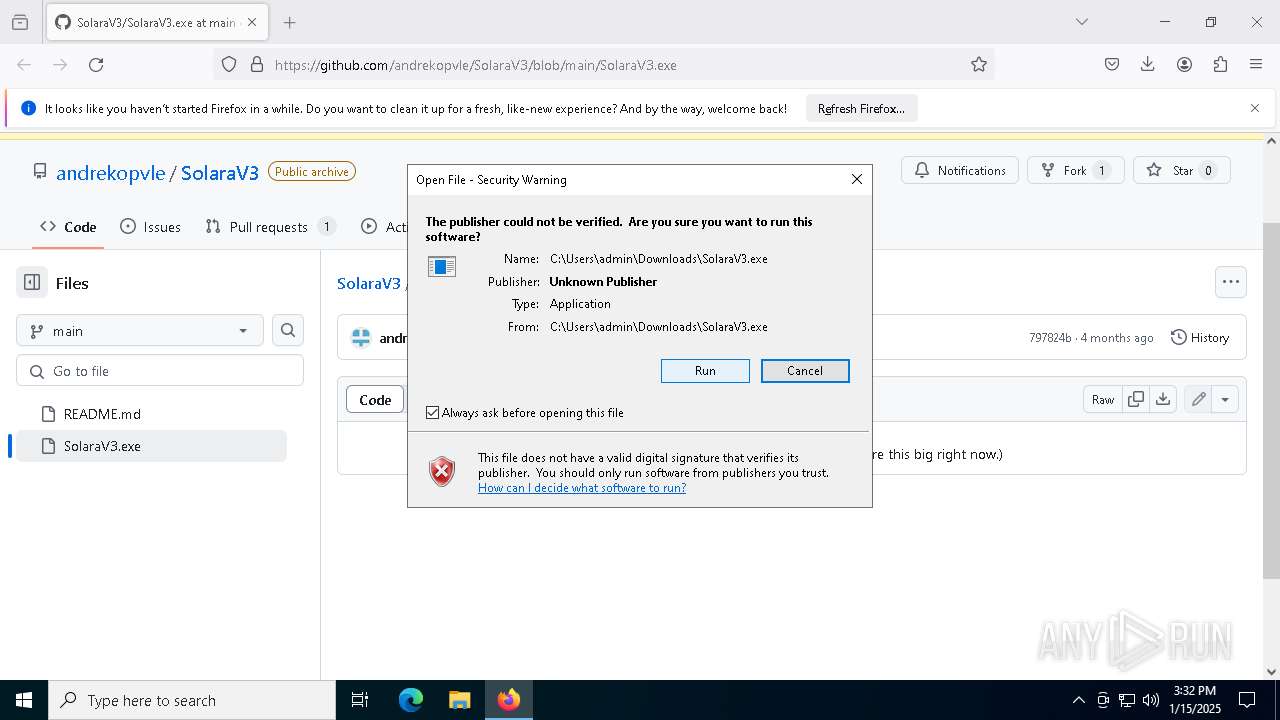
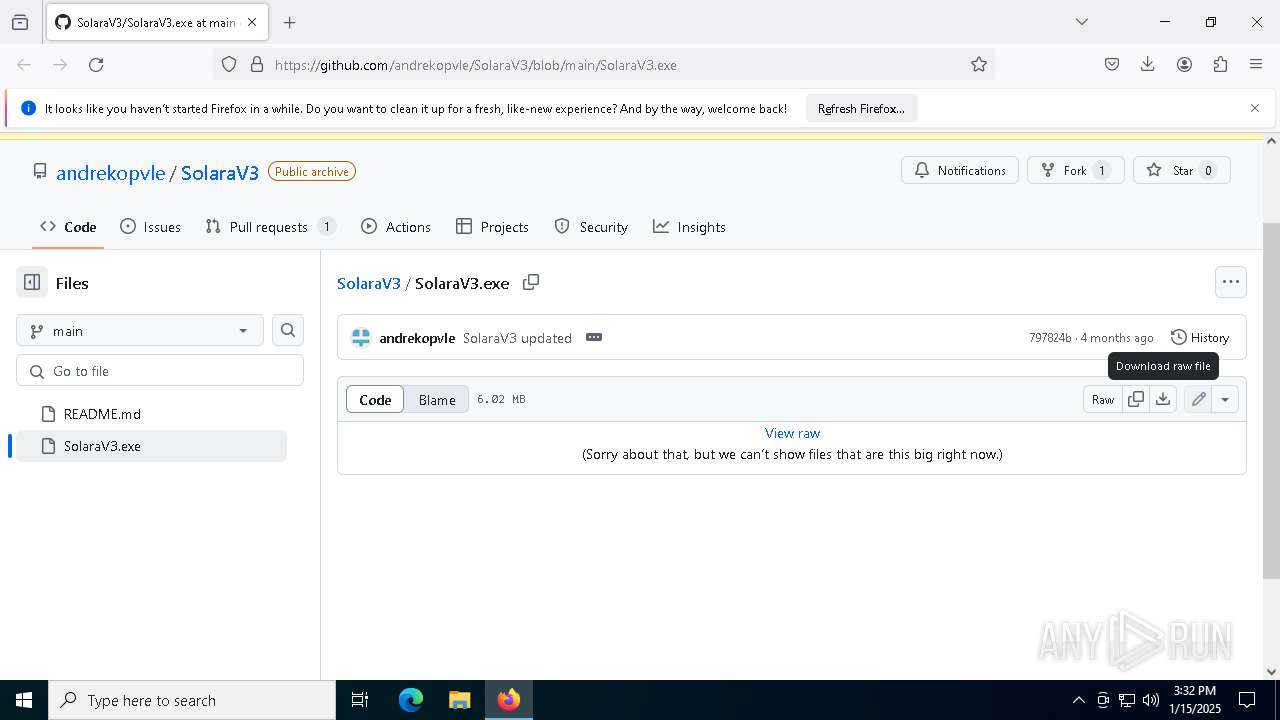
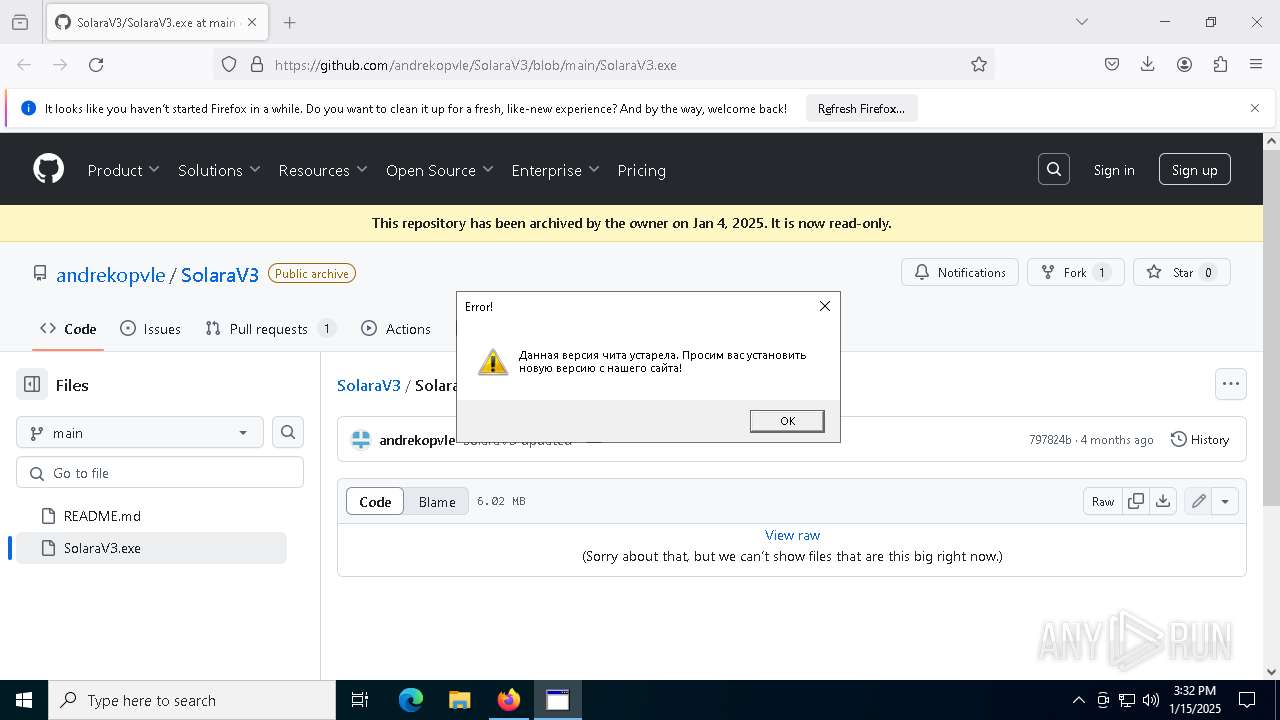
| URL: | https://github.com/andrekopvle/SolaraV3/blob/main/SolaraV3.exe |
| Full analysis: | https://app.any.run/tasks/ded81170-e9d4-450b-84b6-b2d768f7a375 |
| Verdict: | Malicious activity |
| Threats: | Blank Grabber is an infostealer written in Python. It is designed to steal a wide array of data, such as browser login credentials, crypto wallets, Telegram sessions, and Discord tokens. It is an open-source malware, with its code available on GitHub and regularly receiving updates. Blank Grabber builder’s simple interface lets threat actors even with basic skills to deploy it and conduct attacks. |
| Analysis date: | January 15, 2025, 15:31:34 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | C4649FF50D9ED9291551C8B33E8E9154 |
| SHA1: | EA0628726D36063C8F6B503416F5BCA2DBCDFCD5 |
| SHA256: | AFAFE7F5B56EB089D4408809DA527C2069780D6C6A4DBBD56F2079397CEBF9CA |
| SSDEEP: | 3:N8tEd01JtXdKkqIERAXdLAdA:2uiNXdTsydLAdA |
MALICIOUS
BlankGrabber has been detected
- SolaraV3.exe (PID: 7840)
- SolaraV3.exe (PID: 7368)
Executing a file with an untrusted certificate
- SolaraV3.exe (PID: 7864)
- SolaraV3.exe (PID: 7840)
- SolaraV3.exe (PID: 7368)
- SolaraV3.exe (PID: 6084)
Bypass User Account Control (ComputerDefaults)
- ComputerDefaults.exe (PID: 7308)
Adds path to the Windows Defender exclusion list
- SolaraV3.exe (PID: 6084)
- cmd.exe (PID: 2508)
- cmd.exe (PID: 7856)
VOBFUS mutex has been found
- SolaraV3.exe (PID: 6084)
Antivirus name has been found in the command line (generic signature)
- cmd.exe (PID: 3836)
Changes settings for real-time protection
- powershell.exe (PID: 3140)
Changes settings for checking scripts for malicious actions
- powershell.exe (PID: 3140)
Changes settings for reporting to Microsoft Active Protection Service (MAPS)
- powershell.exe (PID: 3140)
Changes Controlled Folder Access settings
- powershell.exe (PID: 3140)
Changes settings for sending potential threat samples to Microsoft servers
- powershell.exe (PID: 3140)
Changes settings for protection against network attacks (IPS)
- powershell.exe (PID: 3140)
Changes antivirus protection settings for downloading files from the Internet (IOAVProtection)
- powershell.exe (PID: 3140)
Create files in the Startup directory
- SolaraV3.exe (PID: 6084)
Bypass execution policy to execute commands
- powershell.exe (PID: 8220)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 8164)
Actions looks like stealing of personal data
- SolaraV3.exe (PID: 6084)
Resets Windows Defender malware definitions to the base version
- MpCmdRun.exe (PID: 8524)
GROWTOPIA has been detected (YARA)
- SolaraV3.exe (PID: 6084)
DISCORDGRABBER has been detected (YARA)
- SolaraV3.exe (PID: 6084)
UMBRALSTEALER has been detected (YARA)
- SolaraV3.exe (PID: 6084)
BLANKGRABBER has been detected (SURICATA)
- SolaraV3.exe (PID: 6084)
Starts CMD.EXE for self-deleting
- SolaraV3.exe (PID: 6084)
SUSPICIOUS
The process drops C-runtime libraries
- SolaraV3.exe (PID: 7840)
- SolaraV3.exe (PID: 7368)
Process drops python dynamic module
- SolaraV3.exe (PID: 7840)
- SolaraV3.exe (PID: 7368)
Process drops legitimate windows executable
- SolaraV3.exe (PID: 7840)
- firefox.exe (PID: 1468)
- SolaraV3.exe (PID: 7368)
- SolaraV3.exe (PID: 6084)
Executable content was dropped or overwritten
- SolaraV3.exe (PID: 7840)
- SolaraV3.exe (PID: 7368)
- SolaraV3.exe (PID: 6084)
- csc.exe (PID: 4536)
Application launched itself
- SolaraV3.exe (PID: 7840)
- SolaraV3.exe (PID: 7368)
Loads Python modules
- SolaraV3.exe (PID: 7864)
- SolaraV3.exe (PID: 6084)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 7884)
- cmd.exe (PID: 7976)
- cmd.exe (PID: 7036)
Found strings related to reading or modifying Windows Defender settings
- SolaraV3.exe (PID: 7864)
- SolaraV3.exe (PID: 6084)
Uses WEVTUTIL.EXE to query events from a log or log file
- cmd.exe (PID: 8068)
- cmd.exe (PID: 5748)
Starts CMD.EXE for commands execution
- SolaraV3.exe (PID: 7864)
- SolaraV3.exe (PID: 6084)
Get information on the list of running processes
- cmd.exe (PID: 1752)
- cmd.exe (PID: 7808)
- SolaraV3.exe (PID: 6084)
- cmd.exe (PID: 7804)
- cmd.exe (PID: 8120)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 2508)
- cmd.exe (PID: 3836)
- cmd.exe (PID: 7856)
- cmd.exe (PID: 8088)
- cmd.exe (PID: 8164)
- cmd.exe (PID: 8952)
- cmd.exe (PID: 7416)
- cmd.exe (PID: 8976)
- cmd.exe (PID: 8356)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 2508)
- cmd.exe (PID: 7856)
Script disables Windows Defender's IPS
- cmd.exe (PID: 3836)
Script disables Windows Defender's real-time protection
- cmd.exe (PID: 3836)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 4512)
- cmd.exe (PID: 8184)
- cmd.exe (PID: 9140)
Accesses product unique identifier via WMI (SCRIPT)
- WMIC.exe (PID: 7912)
- WMIC.exe (PID: 8260)
Uses WMIC.EXE to obtain a list of video controllers
- cmd.exe (PID: 6844)
- cmd.exe (PID: 7336)
- cmd.exe (PID: 8240)
Accesses video controller name via WMI (SCRIPT)
- WMIC.exe (PID: 6952)
- WMIC.exe (PID: 4428)
- WMIC.exe (PID: 8348)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 1296)
Checks for external IP
- SolaraV3.exe (PID: 6084)
- svchost.exe (PID: 2192)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 8164)
Uses NETSH.EXE to obtain data on the network
- cmd.exe (PID: 6772)
Base64-obfuscated command line is found
- cmd.exe (PID: 8164)
BASE64 encoded PowerShell command has been detected
- cmd.exe (PID: 8164)
Starts application with an unusual extension
- cmd.exe (PID: 7288)
- cmd.exe (PID: 8468)
- cmd.exe (PID: 8608)
- cmd.exe (PID: 8760)
- cmd.exe (PID: 9072)
- cmd.exe (PID: 8880)
Uses SYSTEMINFO.EXE to read the environment
- cmd.exe (PID: 5888)
Accesses antivirus product name via WMI (SCRIPT)
- WMIC.exe (PID: 8228)
CSC.EXE is used to compile C# code
- csc.exe (PID: 4536)
Captures screenshot (POWERSHELL)
- powershell.exe (PID: 8220)
The executable file from the user directory is run by the CMD process
- rar.exe (PID: 7484)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 8860)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 8904)
Accesses operating system name via WMI (SCRIPT)
- WMIC.exe (PID: 8152)
Possible usage of Discord/Telegram API has been detected (YARA)
- SolaraV3.exe (PID: 6084)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- SolaraV3.exe (PID: 6084)
Hides command output
- cmd.exe (PID: 1760)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 1760)
INFO
Application launched itself
- firefox.exe (PID: 3564)
- firefox.exe (PID: 1468)
The sample compiled with english language support
- SolaraV3.exe (PID: 7840)
- firefox.exe (PID: 1468)
- SolaraV3.exe (PID: 7368)
- SolaraV3.exe (PID: 6084)
Create files in a temporary directory
- SolaraV3.exe (PID: 7840)
- SolaraV3.exe (PID: 7864)
- SolaraV3.exe (PID: 7368)
- SolaraV3.exe (PID: 6084)
- csc.exe (PID: 4536)
- MpCmdRun.exe (PID: 8524)
Reads the machine GUID from the registry
- SolaraV3.exe (PID: 7864)
- csc.exe (PID: 4536)
- rar.exe (PID: 7484)
Checks supported languages
- SolaraV3.exe (PID: 7864)
- tree.com (PID: 9016)
- csc.exe (PID: 4536)
- rar.exe (PID: 7484)
Executable content was dropped or overwritten
- firefox.exe (PID: 1468)
The process uses the downloaded file
- firefox.exe (PID: 1468)
Creates files in the program directory
- SolaraV3.exe (PID: 6084)
The Powershell gets current clipboard
- powershell.exe (PID: 7296)
Checks the directory tree
- tree.com (PID: 8236)
- tree.com (PID: 8572)
- tree.com (PID: 8660)
- tree.com (PID: 8848)
- tree.com (PID: 9016)
- tree.com (PID: 8312)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7956)
- powershell.exe (PID: 7836)
- powershell.exe (PID: 9124)
- powershell.exe (PID: 3140)
- powershell.exe (PID: 6720)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 7836)
- powershell.exe (PID: 3140)
- powershell.exe (PID: 7956)
PyInstaller has been detected (YARA)
- SolaraV3.exe (PID: 7368)
- SolaraV3.exe (PID: 6084)
Displays MAC addresses of computer network adapters
- getmac.exe (PID: 8604)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 8152)
Found Base64 encoded reflection usage via PowerShell (YARA)
- SolaraV3.exe (PID: 6084)
UPX packer has been detected
- SolaraV3.exe (PID: 6084)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
281
Monitored processes
151
Malicious processes
10
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | C:\WINDOWS\system32\cmd.exe /c "getmac" | C:\Windows\System32\cmd.exe | — | SolaraV3.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 524 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 536 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1144 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1144 | attrib +h +s "C:\Users\admin\Downloads\SolaraV3.exe" | C:\Windows\System32\attrib.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Attribute Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1296 | C:\WINDOWS\system32\cmd.exe /c "attrib +h +s "C:\Users\admin\Downloads\SolaraV3.exe"" | C:\Windows\System32\cmd.exe | — | SolaraV3.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1468 | "C:\Program Files\Mozilla Firefox\firefox.exe" https://github.com/andrekopvle/SolaraV3/blob/main/SolaraV3.exe | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 1612 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1752 | C:\WINDOWS\system32\cmd.exe /c "tasklist /FO LIST" | C:\Windows\System32\cmd.exe | — | SolaraV3.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1760 | C:\WINDOWS\system32\cmd.exe /c "ping localhost -n 3 > NUL && del /A H /F "C:\Users\admin\Downloads\SolaraV3.exe"" | C:\Windows\System32\cmd.exe | — | SolaraV3.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
75 958
Read events
75 941
Write events
13
Delete events
4
Modification events
| (PID) Process: | (1468) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (1468) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (8044) reg.exe | Key: | HKEY_CLASSES_ROOT\ms-settings\shell\open\command |
| Operation: | write | Name: | DelegateExecute |
Value: | |||
| (PID) Process: | (7308) ComputerDefaults.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7308) ComputerDefaults.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (7308) ComputerDefaults.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (7308) ComputerDefaults.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (7436) reg.exe | Key: | HKEY_CLASSES_ROOT\ms-settings\shell\open\command |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7436) reg.exe | Key: | HKEY_CLASSES_ROOT\ms-settings\shell\open |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7436) reg.exe | Key: | HKEY_CLASSES_ROOT\ms-settings\shell |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
44
Suspicious files
175
Text files
105
Unknown types
36
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1468 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 1468 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\urlCache-current.bin | binary | |
MD5:297E88D7CEB26E549254EC875649F4EB | SHA256:8B75D4FB1845BAA06122888D11F6B65E6A36B140C54A72CC13DF390FD7C95702 | |||
| 1468 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 1468 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-child-current.bin | binary | |
MD5:C95DDC2B1A525D1A243E4C294DA2F326 | SHA256:3A5919E086BFB31E36110CF636D2D5109EB51F2C410B107F126126AB25D67363 | |||
| 1468 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 1468 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 1468 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 1468 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 1468 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 1468 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1657114595AmcateirvtiSty.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
36
TCP/UDP connections
117
DNS requests
143
Threats
11
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1468 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
1468 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
1468 | firefox.exe | POST | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/ | unknown | — | — | whitelisted |
1468 | firefox.exe | POST | 200 | 142.250.186.99:80 | http://o.pki.goog/s/wr3/jLM | unknown | — | — | whitelisted |
1468 | firefox.exe | POST | 200 | 184.24.77.83:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
1468 | firefox.exe | POST | 200 | 184.24.77.57:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
1468 | firefox.exe | POST | 200 | 142.250.186.99:80 | http://o.pki.goog/s/wr3/3cs | unknown | — | — | whitelisted |
1468 | firefox.exe | POST | — | 184.24.77.83:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 92.123.104.7:443 | — | Akamai International B.V. | DE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1468 | firefox.exe | 140.82.121.3:443 | github.com | GITHUB | US | whitelisted |
1468 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
1468 | firefox.exe | 34.117.188.166:443 | contile.services.mozilla.com | GOOGLE-CLOUD-PLATFORM | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
github.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
spocs.getpocket.com |
| whitelisted |
content-signature-2.cdn.mozilla.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
6084 | SolaraV3.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
2192 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2192 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
2192 | svchost.exe | Misc activity | SUSPICIOUS [ANY.RUN] Possible sending an external IP address to Telegram |
6084 | SolaraV3.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
2192 | svchost.exe | Misc activity | ET HUNTING Telegram API Domain in DNS Lookup |
— | — | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |