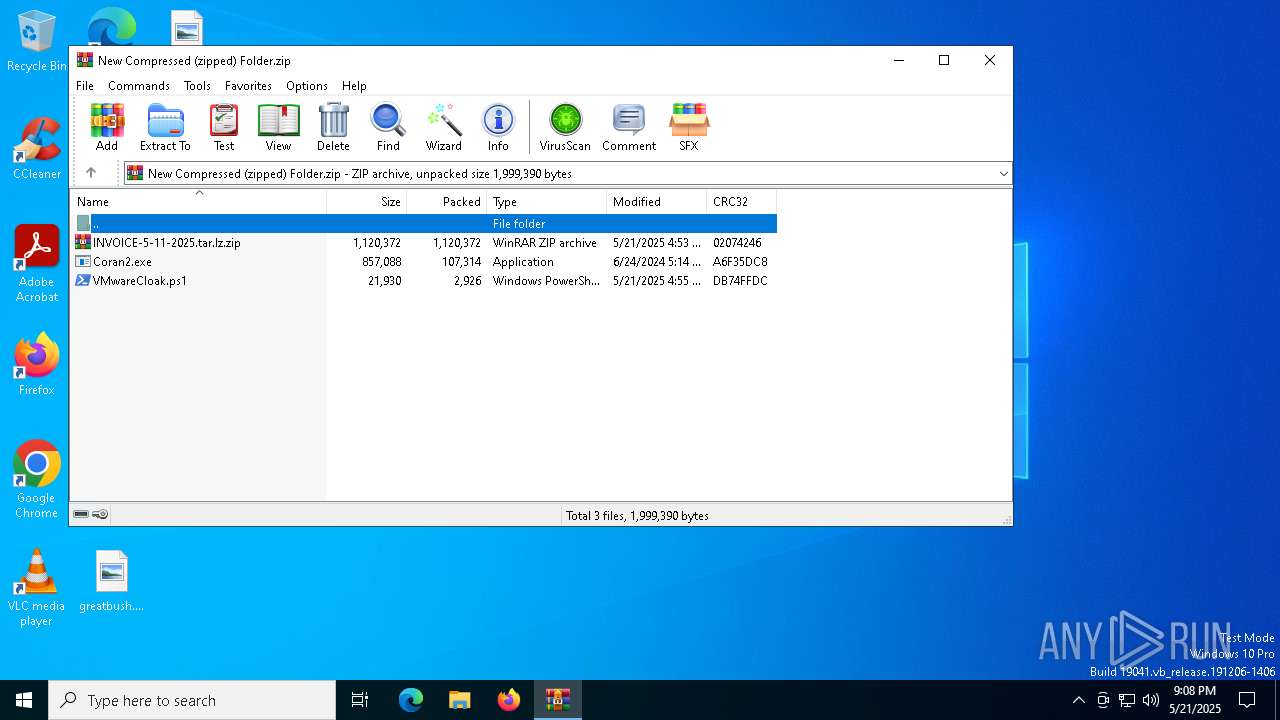
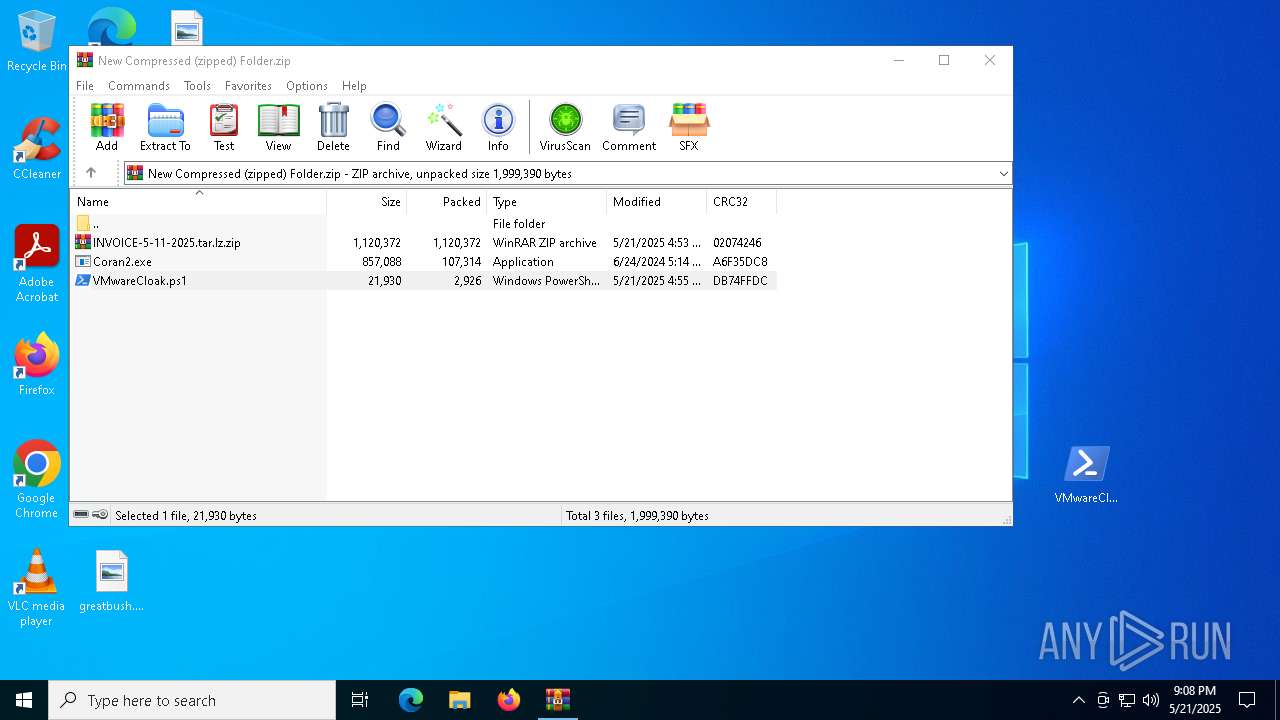
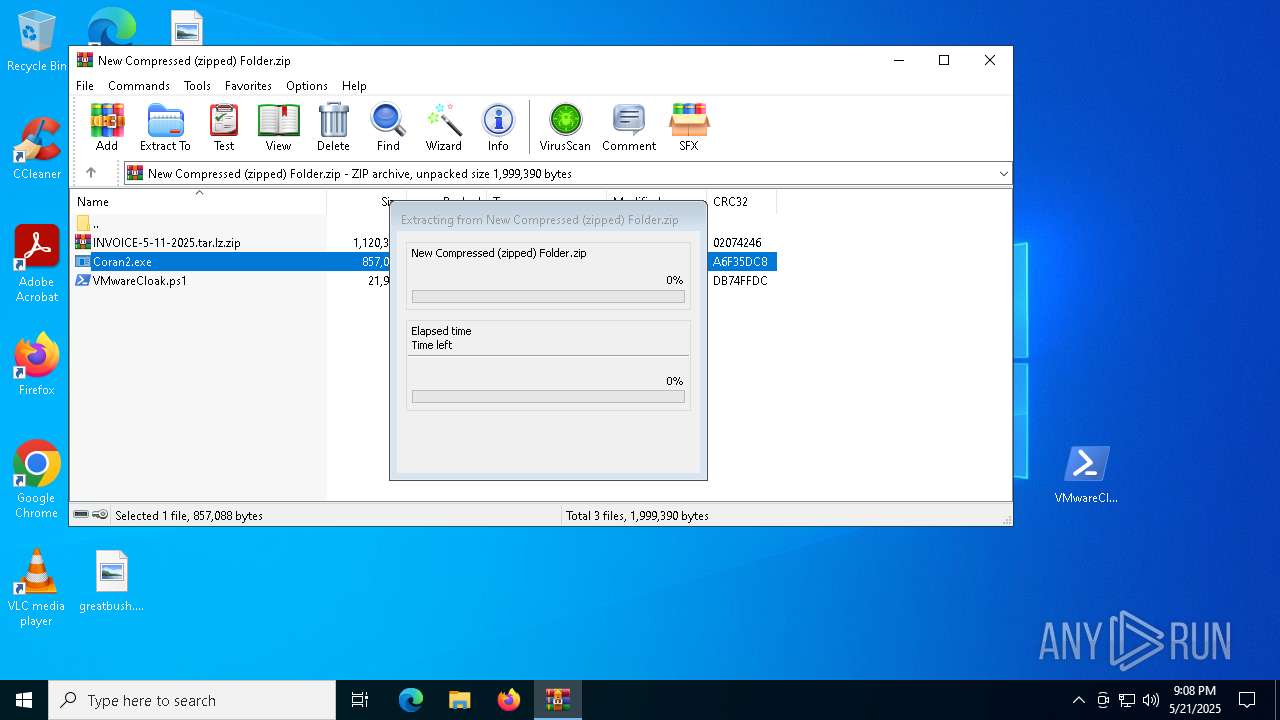
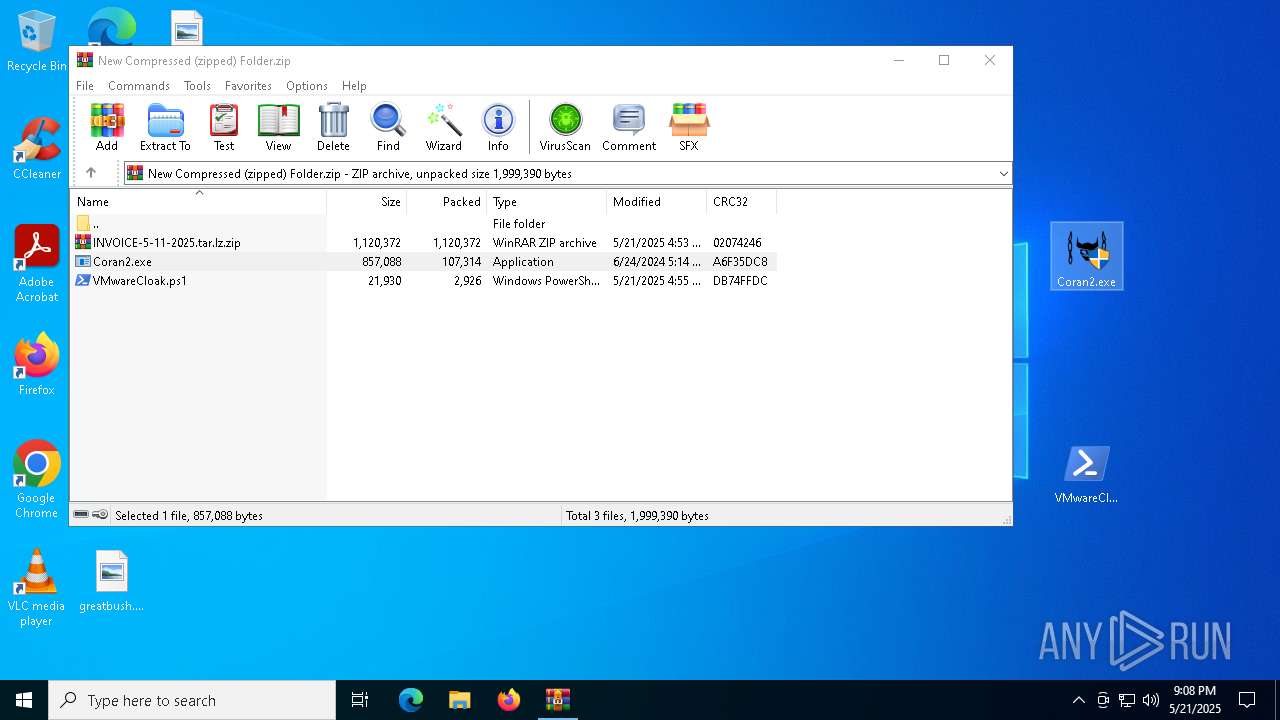
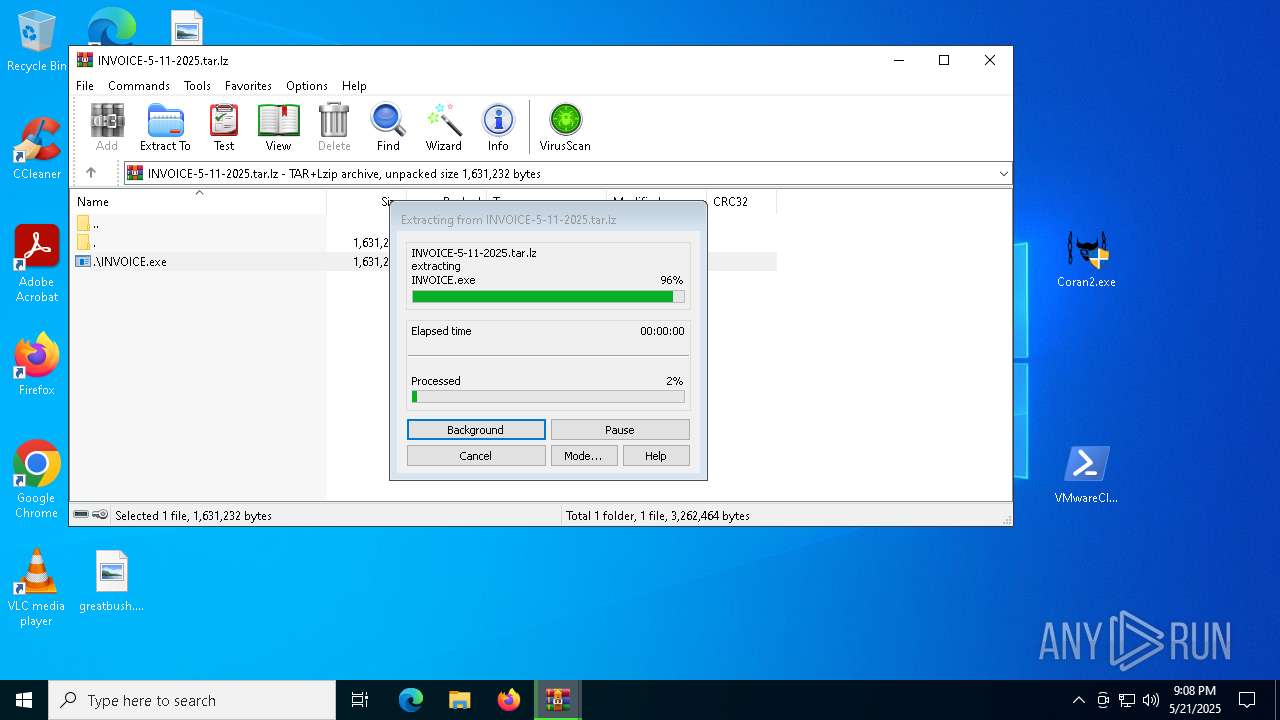
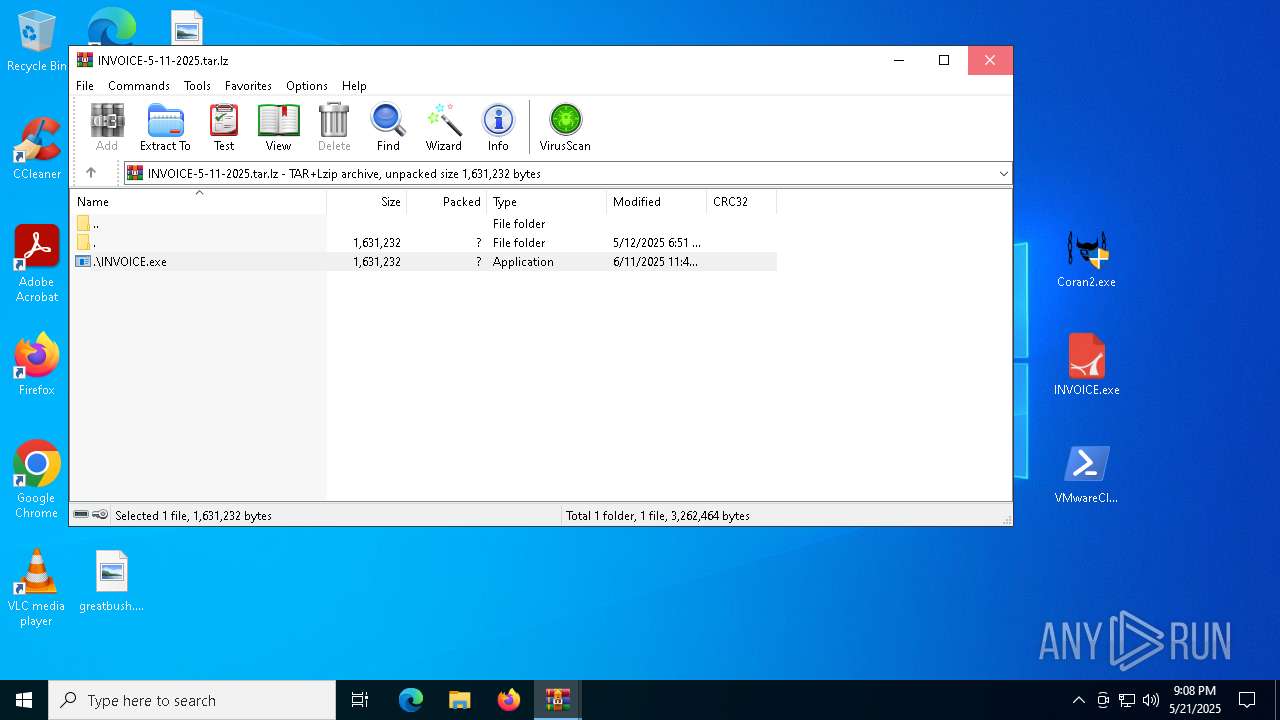
| File name: | New Compressed (zipped) Folder.zip |
| Full analysis: | https://app.any.run/tasks/3cfd800d-83a1-4f36-9a3d-1d36c04d4080 |
| Verdict: | Malicious activity |
| Threats: | DBatLoader is a loader malware used for distributing payloads of different types, including WarzoneRAT and Formbook. It is employed in multi-stage attacks that usually start with a phishing email carrying a malicious attachment. |
| Analysis date: | May 21, 2025, 21:08:04 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 00FB2ECFE6608AA171009871F8940F6C |
| SHA1: | 2C86EF46F170B51C58349CEA9EC296B2BBECA10D |
| SHA256: | AF78B1E7DC57A457FDB850112E5FDDD1F9C6DCC8A6F726A22B1FDA805C83F3F8 |
| SSDEEP: | 49152:xqj5fpYOAdSYdTmHJivhILYdgu5fKoNOo2p2zFv+HhoC5zysEbMdNQiEFLxaApHg:gjx9MZ4ESWKeq2F+BoC5ZyQNQNFdacJq |
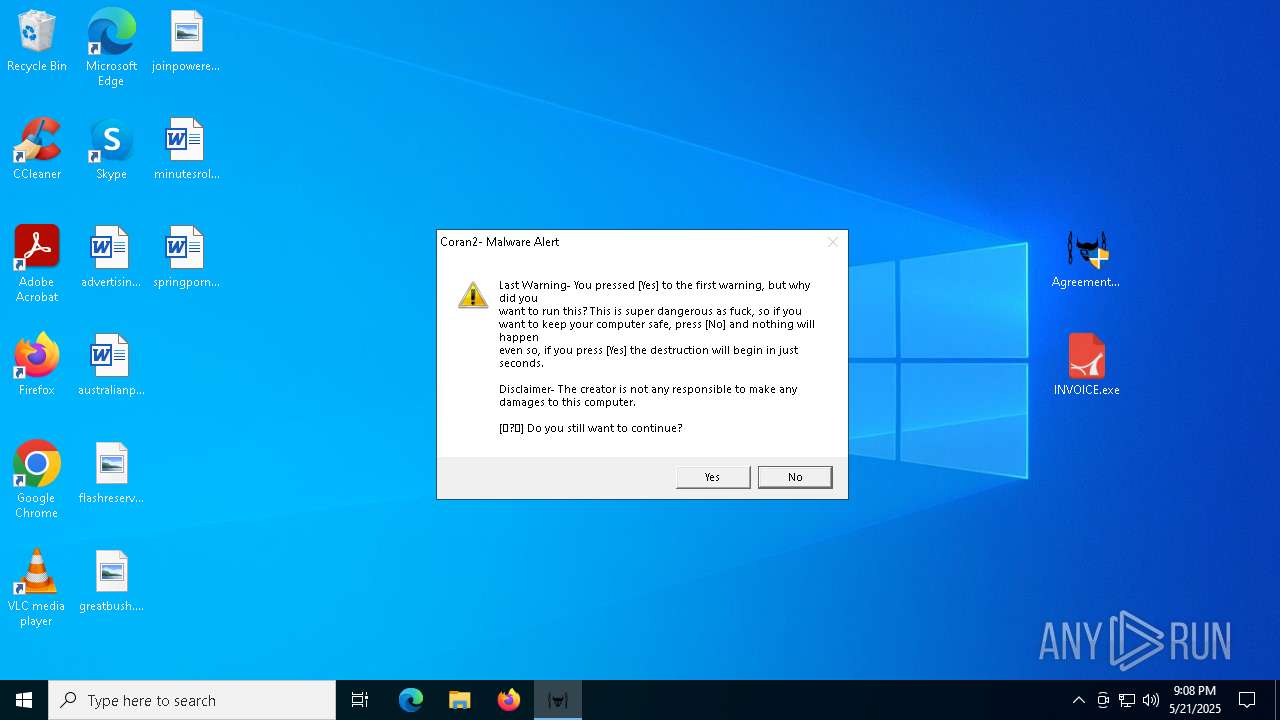
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 7912)
Generic archive extractor
- WinRAR.exe (PID: 4400)
REMCOS has been detected (SURICATA)
- colorcpl.exe (PID: 7868)
- SndVol.exe (PID: 6264)
- SndVol.exe (PID: 2088)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 6752)
DBATLOADER has been detected (YARA)
- INVOICE.exe (PID: 5892)
SUSPICIOUS
Application launched itself
- WinRAR.exe (PID: 7736)
- WinRAR.exe (PID: 4400)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 4400)
- WinRAR.exe (PID: 7736)
- Agreementdocument.exe (PID: 4040)
- INVOICE.exe (PID: 5892)
There is functionality for taking screenshot (YARA)
- Agreementdocument.exe (PID: 4040)
- INVOICE.exe (PID: 5892)
- Cxsdjmfb.PIF (PID: 7916)
- Cxsdjmfb.PIF (PID: 2268)
Starts CMD.EXE for commands execution
- Agreementdocument.exe (PID: 4040)
- INVOICE.exe (PID: 5892)
Executing commands from ".cmd" file
- INVOICE.exe (PID: 5892)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 7500)
Likely accesses (executes) a file from the Public directory
- esentutl.exe (PID: 7636)
- alpha.pif (PID: 7464)
- alpha.pif (PID: 7496)
Executable content was dropped or overwritten
- esentutl.exe (PID: 7636)
- INVOICE.exe (PID: 5892)
Drops a file with a rarely used extension (PIF)
- esentutl.exe (PID: 7636)
Starts itself from another location
- cmd.exe (PID: 7356)
Starts a Microsoft application from unusual location
- alpha.pif (PID: 7464)
- alpha.pif (PID: 7496)
Created directory related to system
- alpha.pif (PID: 7464)
Starts application with an unusual extension
- cmd.exe (PID: 7356)
- rundll32.exe (PID: 7940)
- rundll32.exe (PID: 1228)
- rundll32.exe (PID: 6028)
- rundll32.exe (PID: 7452)
The process executes via Task Scheduler
- rundll32.exe (PID: 7940)
- rundll32.exe (PID: 1228)
- rundll32.exe (PID: 6028)
- rundll32.exe (PID: 7452)
Connects to unusual port
- colorcpl.exe (PID: 7868)
- SndVol.exe (PID: 6264)
- SndVol.exe (PID: 2088)
Contacting a server suspected of hosting an CnC
- colorcpl.exe (PID: 7868)
- SndVol.exe (PID: 6264)
- SndVol.exe (PID: 2088)
Executes application which crashes
- colorcpl.exe (PID: 7868)
- SndVol.exe (PID: 6264)
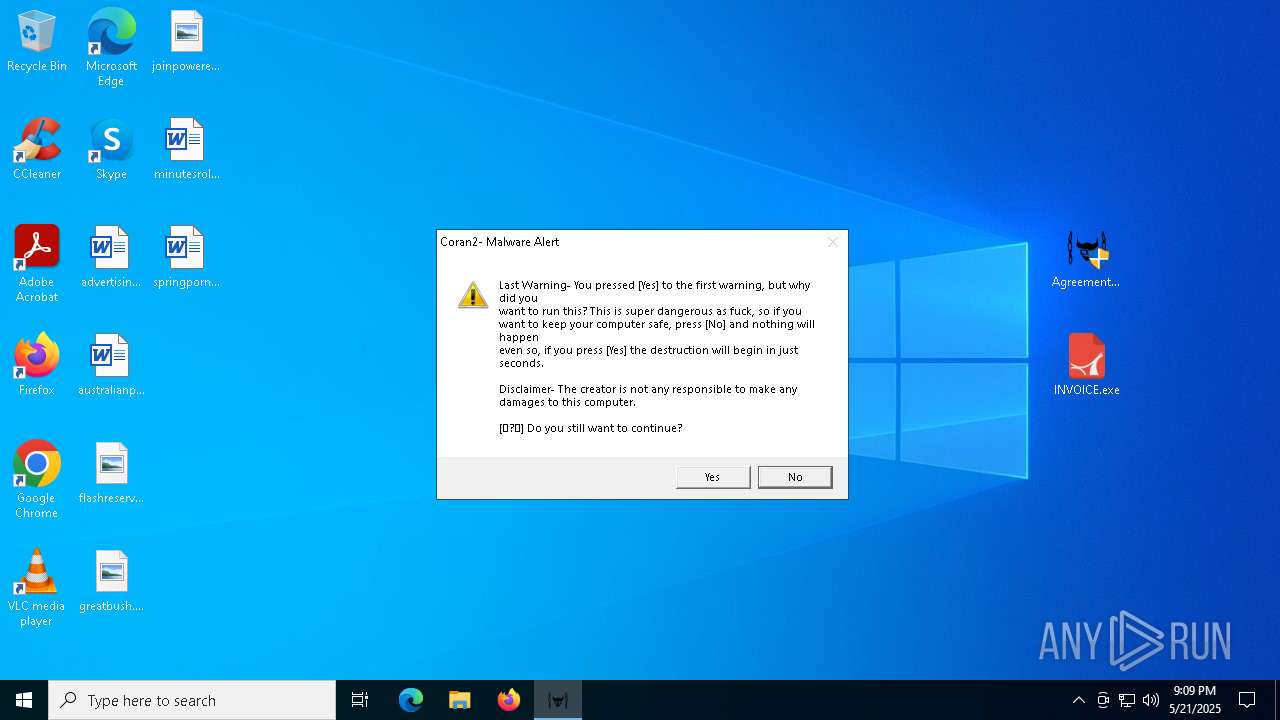
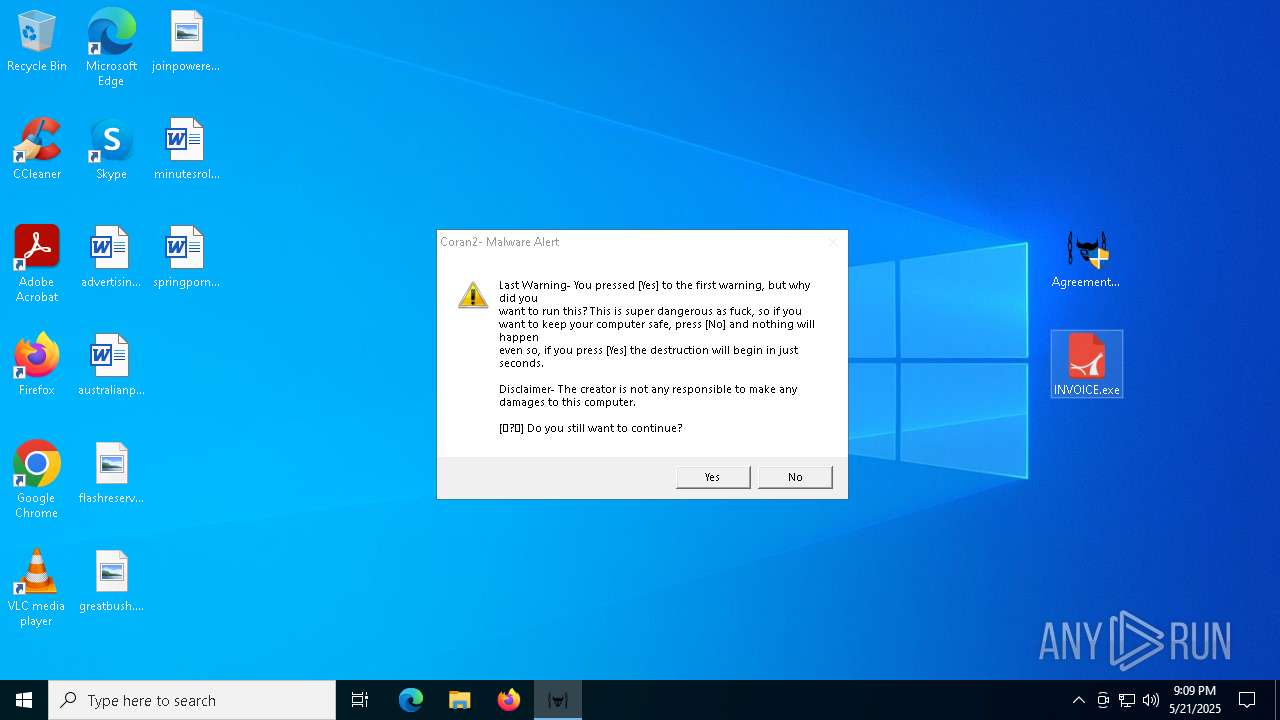
Start notepad (likely ransomware note)
- Agreementdocument.exe (PID: 4040)
Starts POWERSHELL.EXE for commands execution
- Agreementdocument.exe (PID: 4040)
INFO
Manual execution by a user
- powershell.exe (PID: 7912)
- Agreementdocument.exe (PID: 3100)
- Agreementdocument.exe (PID: 4040)
- INVOICE.exe (PID: 5892)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7804)
- WinRAR.exe (PID: 4400)
Reads the computer name
- Agreementdocument.exe (PID: 4040)
- INVOICE.exe (PID: 5892)
Checks supported languages
- Agreementdocument.exe (PID: 4040)
- INVOICE.exe (PID: 5892)
- alpha.pif (PID: 7464)
- alpha.pif (PID: 7496)
Process checks computer location settings
- Agreementdocument.exe (PID: 4040)
Checks proxy server information
- INVOICE.exe (PID: 5892)
Creates files in the program directory
- INVOICE.exe (PID: 5892)
Compiled with Borland Delphi (YARA)
- INVOICE.exe (PID: 5892)
- Cxsdjmfb.PIF (PID: 7916)
- Cxsdjmfb.PIF (PID: 2268)
The sample compiled with english language support
- esentutl.exe (PID: 7636)
Reads the software policy settings
- slui.exe (PID: 7316)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 7444)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:05:21 16:53:20 |
| ZipCRC: | 0x02074246 |
| ZipCompressedSize: | 1120372 |
| ZipUncompressedSize: | 1120372 |
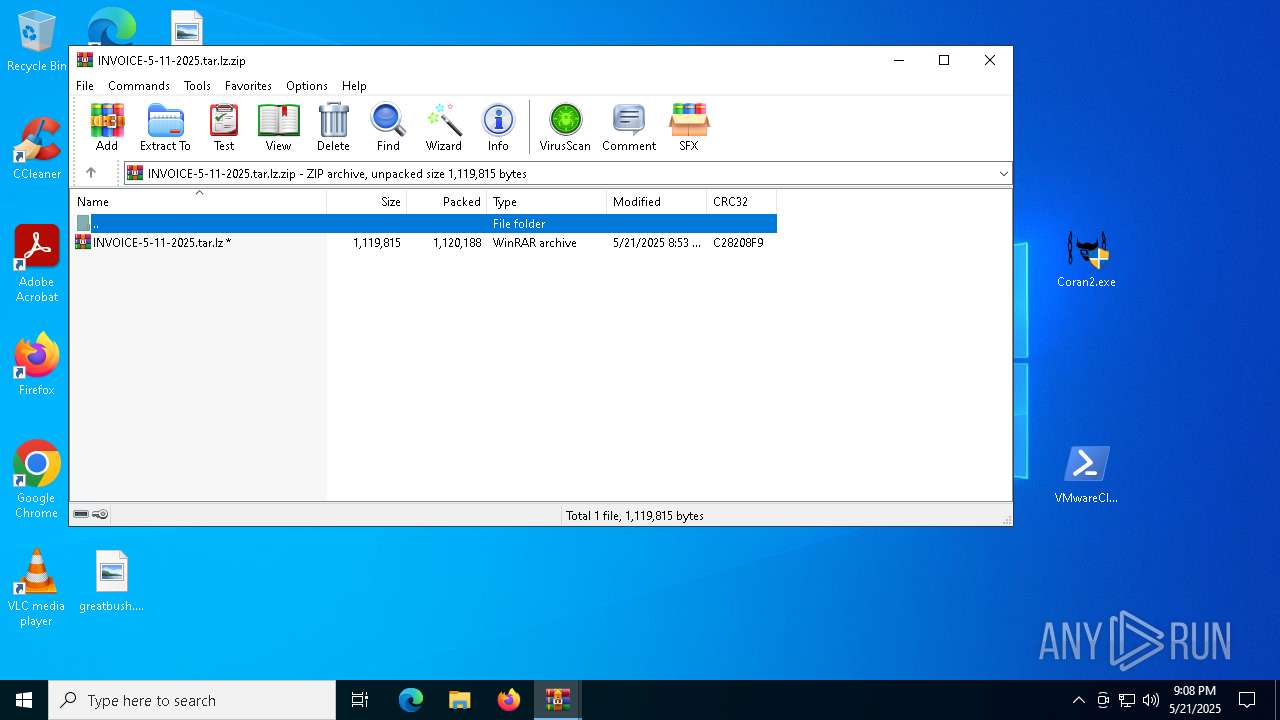
| ZipFileName: | INVOICE-5-11-2025.tar.lz.zip |
Total processes
214
Monitored processes
79
Malicious processes
10
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 668 | "C:\Windows\System32\cmd.exe" | C:\Windows\SysWOW64\cmd.exe | — | Agreementdocument.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 684 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 7868 -s 1456 | C:\Windows\SysWOW64\WerFault.exe | — | colorcpl.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1052 | "C:\Windows\System32\notepad.exe" | C:\Windows\SysWOW64\notepad.exe | — | Agreementdocument.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1228 | C:\WINDOWS\system32\rundll32.exe "C:\WINDOWS\system32\ieframe.dll",OpenURL C:\\ProgramData\\Cxsdjmfb.url | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1328 | "C:\Windows\System32\control.exe" | C:\Windows\SysWOW64\control.exe | — | Agreementdocument.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Control Panel Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1452 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1676 | "C:\Windows\System32\notepad.exe" | C:\Windows\SysWOW64\notepad.exe | — | Agreementdocument.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2040 | schtasks /create /sc minute /mo 1 /tn "Cxsdjmfb" /tr C:\\ProgramData\\Cxsdjmfb.url" | C:\Windows\SysWOW64\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2088 | C:\Windows\System32\SndVol.exe | C:\Windows\SysWOW64\SndVol.exe | Cxsdjmfb.PIF | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Volume Mixer Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
57 510
Read events
57 360
Write events
146
Delete events
4
Modification events
| (PID) Process: | (4400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\New Compressed (zipped) Folder.zip | |||
| (PID) Process: | (4400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7736) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7736) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
Executable files
4
Suspicious files
29
Text files
23
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4040 | Agreementdocument.exe | \Device\Harddisk0\DR0 | — | |
MD5:— | SHA256:— | |||
| 4400 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa4400.784\INVOICE-5-11-2025.tar.lz.zip | compressed | |
MD5:D1652EAA3569B566104E34FE4D0B63FF | SHA256:660B25FBB09AA30F644783D14110759C8DAC66254CDE0068E282830DE53C14E7 | |||
| 7912 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF1106d3.TMP | binary | |
MD5:D040F64E9E7A2BB91ABCA5613424598E | SHA256:D04E0A6940609BD6F3B561B0F6027F5CA4E8C5CF0FB0D0874B380A0374A8D670 | |||
| 7912 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:5C41CC17812226009462B79FC3C83D37 | SHA256:0D6012A0C6DEA014DFE72263F13D3097A71AC1D5223B58A48F38D91BD134F922 | |||
| 7912 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\YVHJWCRTGC31EQ3FFU37.temp | binary | |
MD5:5C41CC17812226009462B79FC3C83D37 | SHA256:0D6012A0C6DEA014DFE72263F13D3097A71AC1D5223B58A48F38D91BD134F922 | |||
| 5892 | INVOICE.exe | C:\ProgramData\Cxsdjmfb.url | binary | |
MD5:5BE1AA05EAD63222AA3525E32A6018B3 | SHA256:6C88B52B6F59D6EF689C714829C2523F84D169287BD8702FFFCC2E3174F4CD80 | |||
| 7912 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_2gtx4r5k.iac.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7444 | Taskmgr.exe | C:\Users\admin\AppData\Local\D3DSCache\3e2651cb230b5698\F4EB2D6C-ED2B-4BDD-AD9D-F913287E6768.idx | binary | |
MD5:956714757F0C01587D52367FF646889D | SHA256:E70C02A9DF8D4A65B124FCD6A4070B18F04577F237BE158AF9CCFB6853059394 | |||
| 684 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_colorcpl.exe_b69e27ab5d6baa5decac1422331ef9a8217_ddba1c1d_f7e7e143-6a0c-47e6-af59-33916c0eb54a\Report.wer | — | |
MD5:— | SHA256:— | |||
| 5892 | INVOICE.exe | C:\Users\admin\Links\Cxsdjmfb.PIF | executable | |
MD5:D287492545807FDCB71CB470F330B4ED | SHA256:4FB126F79CD46AF8853B90196AAE99044C5AA4C520AA5D568B26858BB41ED755 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
30
DNS requests
20
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
8144 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6264 | SndVol.exe | GET | 200 | 178.237.33.50:80 | http://geoplugin.net/json.gp | unknown | — | — | whitelisted |
2088 | SndVol.exe | GET | 200 | 178.237.33.50:80 | http://geoplugin.net/json.gp | unknown | — | — | whitelisted |
8144 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7868 | colorcpl.exe | GET | 200 | 178.237.33.50:80 | http://geoplugin.net/json.gp | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
— | — | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.32.72:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Misc activity | ET DYN_DNS DYNAMIC_DNS Query to *.duckdns. Domain |
2196 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.duckdns .org Domain |
7868 | colorcpl.exe | A Network Trojan was detected | REMOTE [ANY.RUN] REMCOS TLS Connection JA3 Hash |
7868 | colorcpl.exe | Malware Command and Control Activity Detected | ET JA3 Hash - Remcos 3.x/4.x TLS Connection |
6264 | SndVol.exe | A Network Trojan was detected | REMOTE [ANY.RUN] REMCOS TLS Connection JA3 Hash |
6264 | SndVol.exe | Malware Command and Control Activity Detected | ET JA3 Hash - Remcos 3.x/4.x TLS Connection |
2196 | svchost.exe | Misc activity | ET DYN_DNS DYNAMIC_DNS Query to *.duckdns. Domain |
2196 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.duckdns .org Domain |
2088 | SndVol.exe | A Network Trojan was detected | REMOTE [ANY.RUN] REMCOS TLS Connection JA3 Hash |
2088 | SndVol.exe | Malware Command and Control Activity Detected | ET JA3 Hash - Remcos 3.x/4.x TLS Connection |