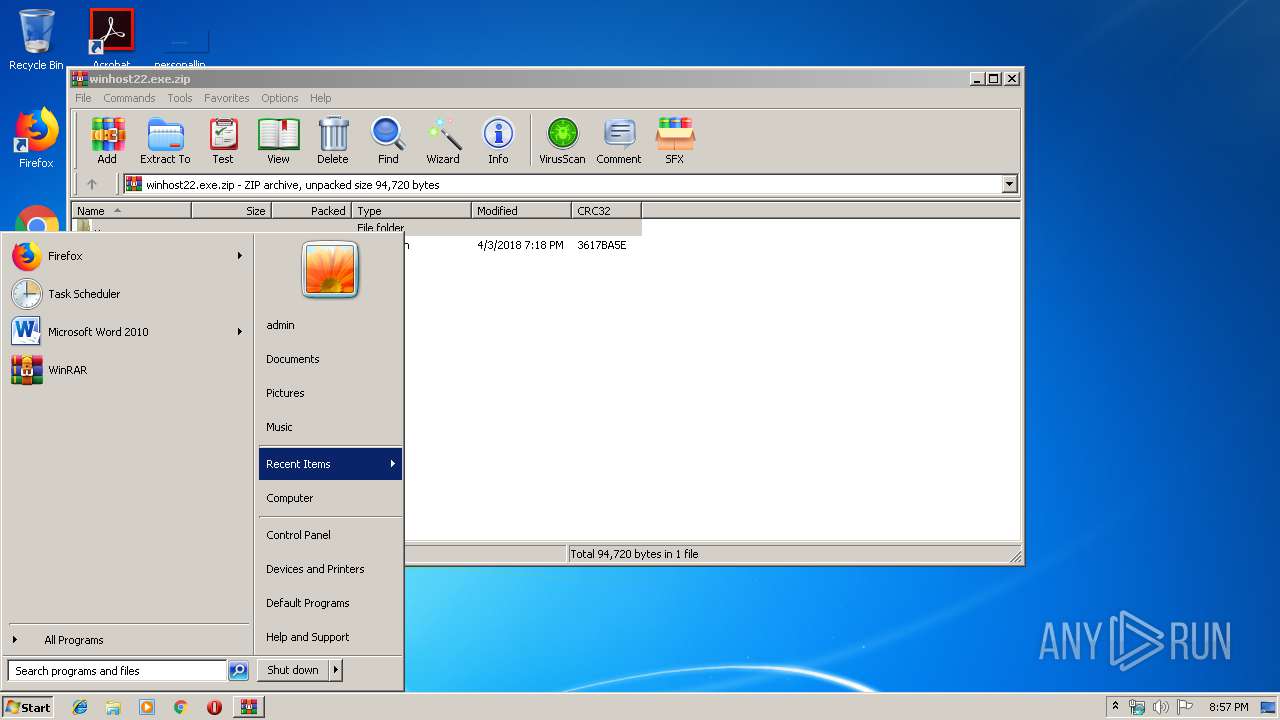
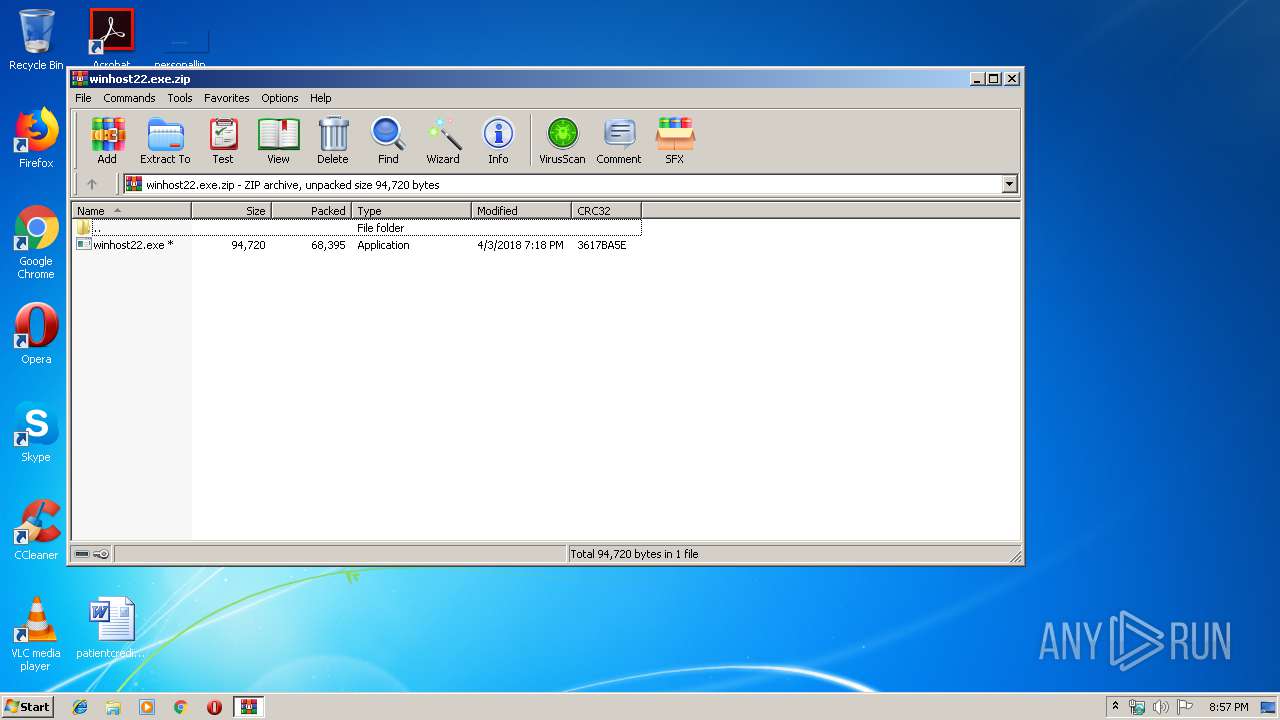
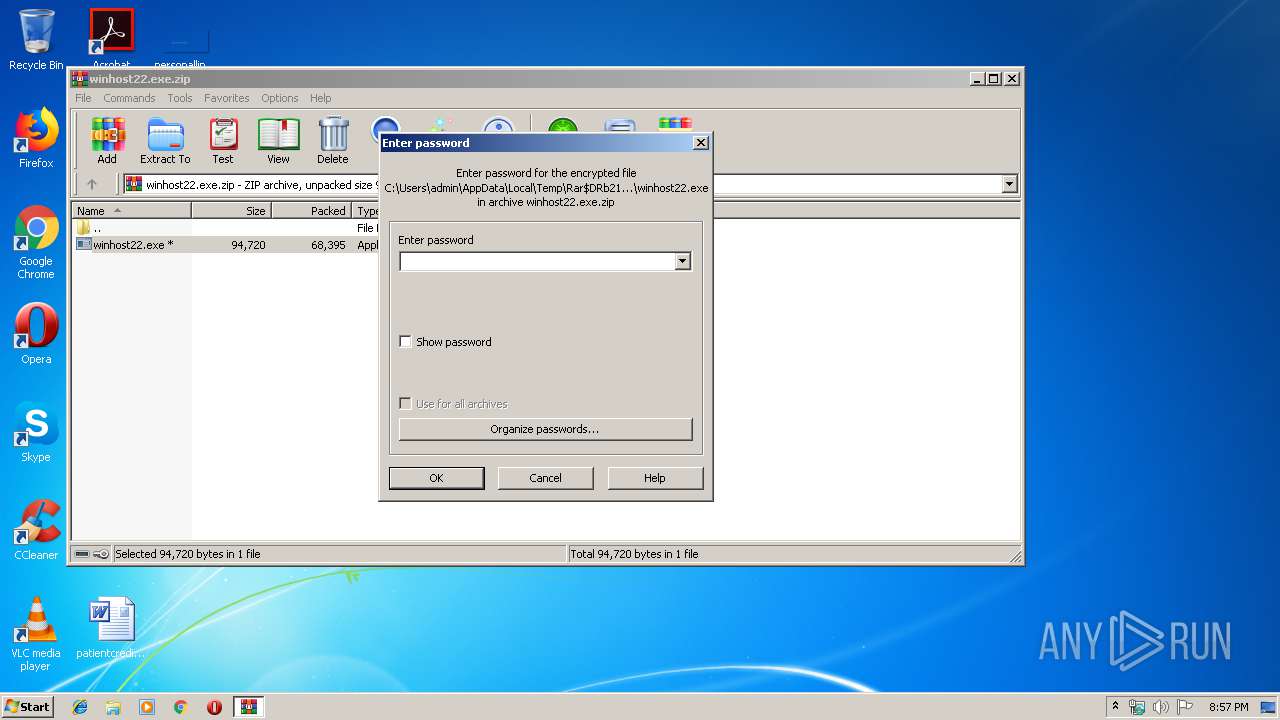
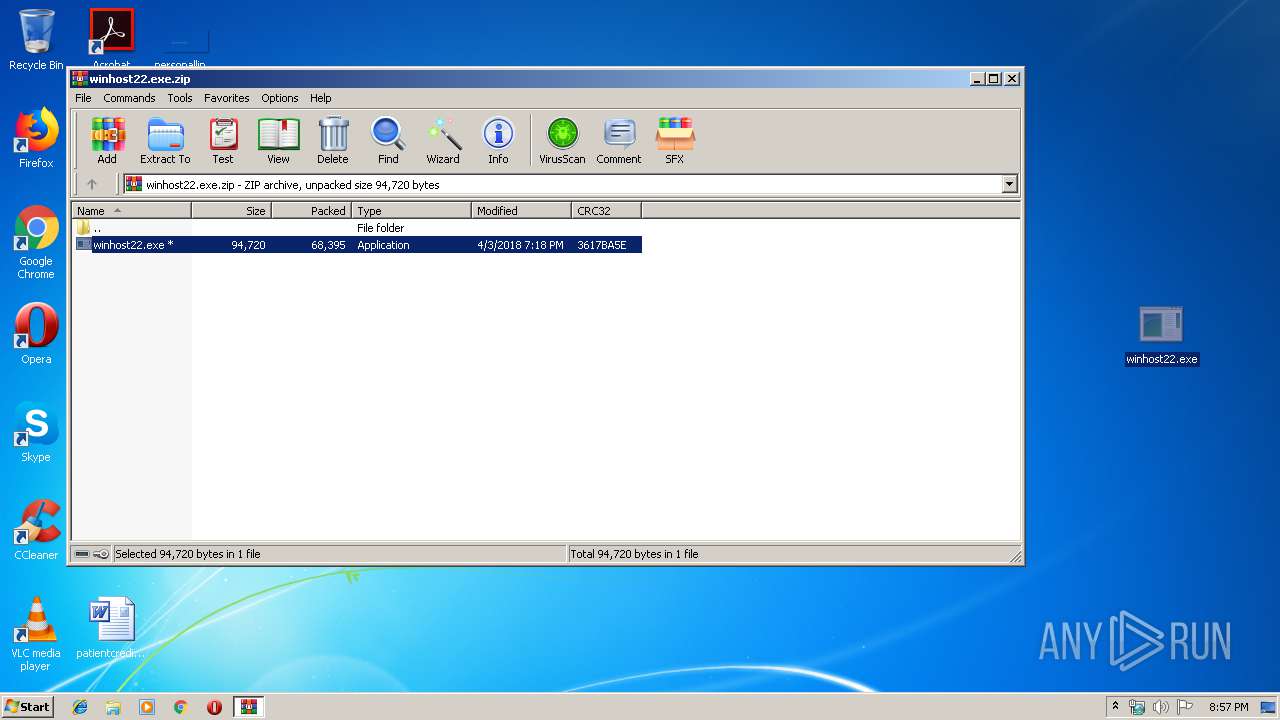
| File name: | winhost22.exe.zip |
| Full analysis: | https://app.any.run/tasks/4e46c8f1-3b01-4fe3-b260-8bd3d6b13180 |
| Verdict: | Malicious activity |
| Threats: | Dharma is advanced ransomware that has been observed in the wild since 2016. It is considered to be the second most profitable RaaS operation by the FBI. The malware targets hospitals and state organizations, encrypts files, and demands a payment to restore access to lost information. |
| Analysis date: | December 02, 2019, 20:57:16 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 449F32674EA100CA6AD23A29194902FD |
| SHA1: | 94471A829295CFDC8B245987908501B9EE5224DD |
| SHA256: | AF61AF67F159CDA5029305099B4BA22B092EFAEE4B20A66794DC7AE7A0A03A28 |
| SSDEEP: | 1536:asn9u6msnWvA0odWnGXqqJC9Pcl/37GNZUHH+gnpr:hxt50csGZAE/3KNcr |
MALICIOUS
Application was dropped or rewritten from another process
- winhost22.exe (PID: 2748)
- winhost22.exe (PID: 3820)
Changes the autorun value in the registry
- winhost22.exe (PID: 2748)
- winhost22.exe (PID: 3820)
Writes to a start menu file
- winhost22.exe (PID: 2748)
- winhost22.exe (PID: 3820)
Runs app for hidden code execution
- winhost22.exe (PID: 2748)
- winhost22.exe (PID: 3820)
Deletes shadow copies
- cmd.exe (PID: 3876)
- cmd.exe (PID: 3992)
Dharma/Crysis was detected
- winhost22.exe (PID: 2748)
- winhost22.exe (PID: 3820)
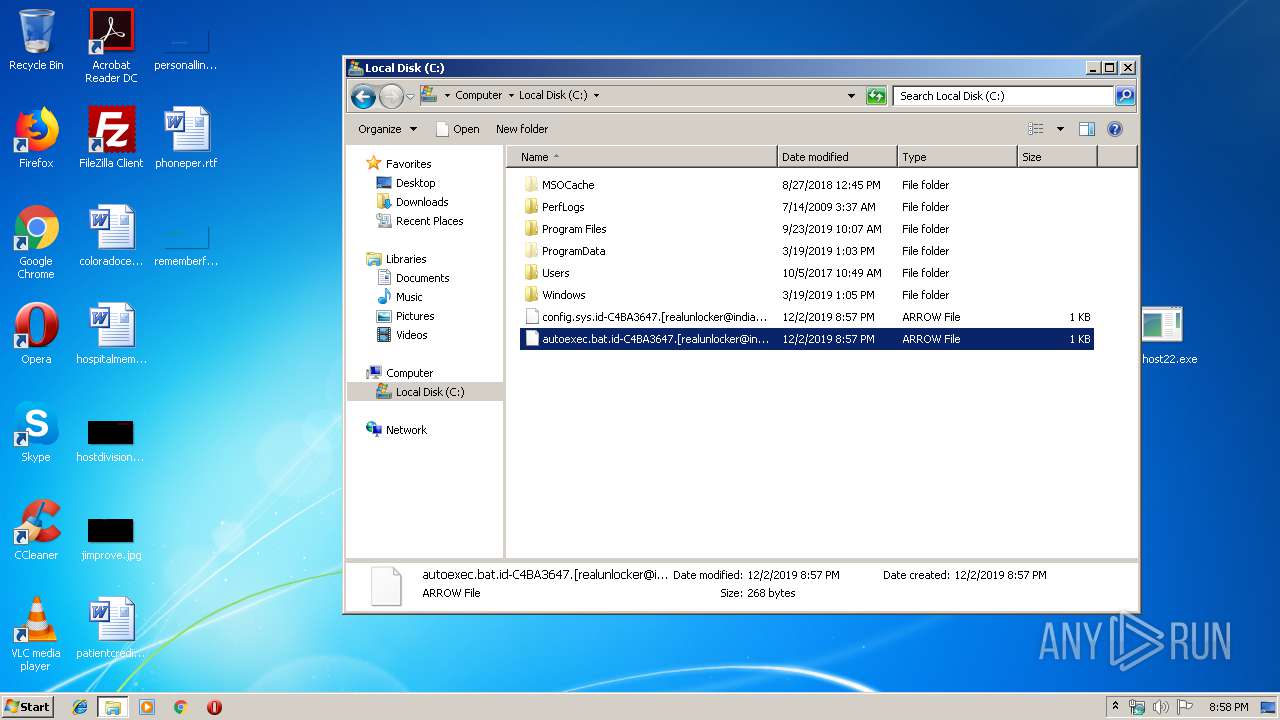
Renames files like Ransomware
- winhost22.exe (PID: 3820)
SUSPICIOUS
Starts CMD.EXE for commands execution
- winhost22.exe (PID: 2748)
- winhost22.exe (PID: 3820)
Creates files in the user directory
- winhost22.exe (PID: 2748)
Executable content was dropped or overwritten
- winhost22.exe (PID: 2748)
- winhost22.exe (PID: 3820)
Application launched itself
- winhost22.exe (PID: 2748)
Creates files in the Windows directory
- winhost22.exe (PID: 3820)
Executed as Windows Service
- vssvc.exe (PID: 3752)
Creates files in the program directory
- winhost22.exe (PID: 2748)
- winhost22.exe (PID: 3820)
INFO
Manual execution by user
- winhost22.exe (PID: 2748)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 788 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2018:04:03 20:18:28 |
| ZipCRC: | 0x3617ba5e |
| ZipCompressedSize: | 68395 |
| ZipUncompressedSize: | 94720 |
| ZipFileName: | winhost22.exe |
Total processes
54
Monitored processes
12
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 616 | mode con cp select=1251 | C:\Windows\system32\mode.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: DOS Device MODE Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 792 | vssadmin delete shadows /all /quiet | C:\Windows\system32\vssadmin.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Command Line Interface for Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2076 | mode con cp select=1251 | C:\Windows\system32\mode.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: DOS Device MODE Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2124 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\winhost22.exe.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2748 | "C:\Users\admin\Desktop\winhost22.exe" | C:\Users\admin\Desktop\winhost22.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3148 | mode con cp select=1251 | C:\Windows\system32\mode.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: DOS Device MODE Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3752 | C:\Windows\system32\vssvc.exe | C:\Windows\system32\vssvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3820 | "C:\Users\admin\Desktop\winhost22.exe" -a | C:\Users\admin\Desktop\winhost22.exe | winhost22.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3876 | "C:\Windows\system32\cmd.exe" | C:\Windows\system32\cmd.exe | — | winhost22.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3992 | "C:\Windows\system32\cmd.exe" | C:\Windows\system32\cmd.exe | — | winhost22.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
504
Read events
477
Write events
27
Delete events
0
Modification events
| (PID) Process: | (2124) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2124) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2124) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2124) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\winhost22.exe.zip | |||
| (PID) Process: | (2124) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2124) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2124) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2124) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2124) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (2748) winhost22.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | winhost22.exe |
Value: C:\Users\admin\AppData\Roaming\winhost22.exe | |||
Executable files
5
Suspicious files
397
Text files
2
Unknown types
25
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2124 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2124.26247\winhost22.exe | — | |
MD5:— | SHA256:— | |||
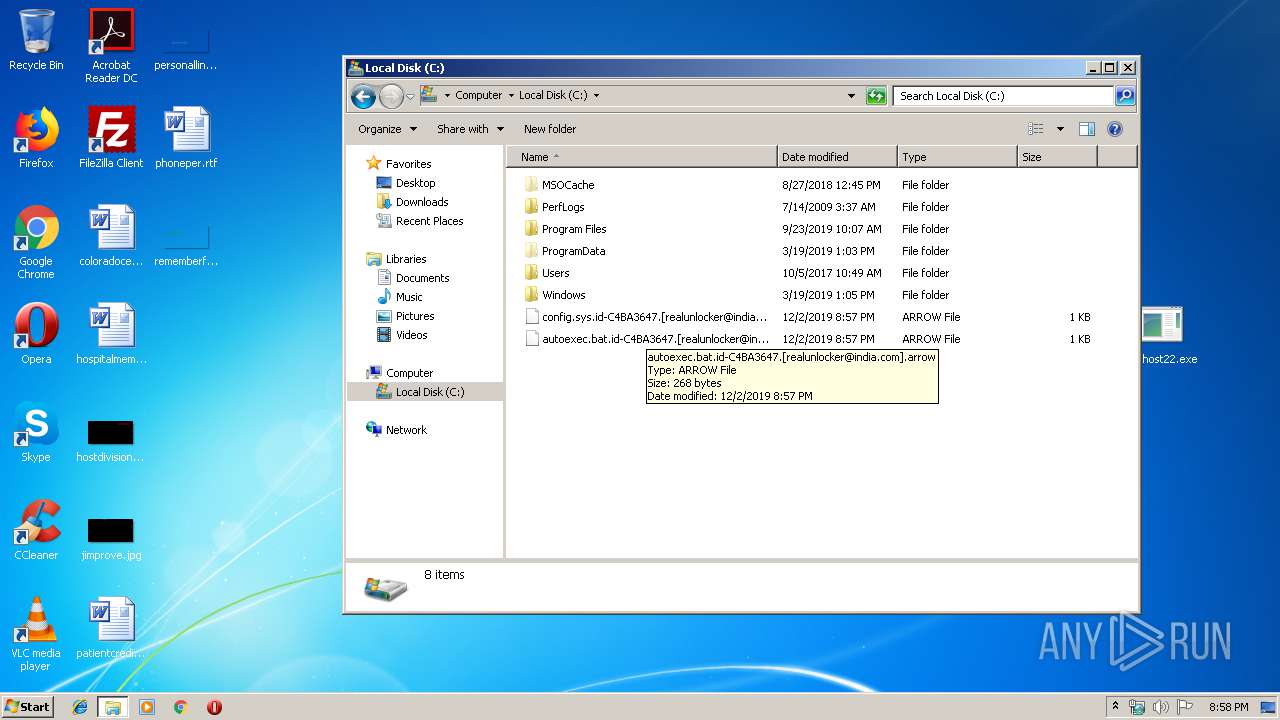
| 2748 | winhost22.exe | C:\$Recycle.Bin\S-1-5-21-1302019708-1500728564-335382590-1000\desktop.ini | — | |
MD5:— | SHA256:— | |||
| 2748 | winhost22.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\Adobe\Acrobat Reader DC\Leame.htm | — | |
MD5:— | SHA256:— | |||
| 2748 | winhost22.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\Adobe\Acrobat Reader DC\Benioku.htm | — | |
MD5:— | SHA256:— | |||
| 2748 | winhost22.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\Adobe\Acrobat Reader DC\Berime.htm | — | |
MD5:— | SHA256:— | |||
| 2748 | winhost22.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\Adobe\Acrobat Reader DC\IrakHau.htm | — | |
MD5:— | SHA256:— | |||
| 2748 | winhost22.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\Adobe\Acrobat Reader DC\Reader\AcroApp\CAT\Comments.aapp | — | |
MD5:— | SHA256:— | |||
| 2748 | winhost22.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\Adobe\Acrobat Reader DC\Reader\AcroApp\CAT\AppCenter_R.aapp | — | |
MD5:— | SHA256:— | |||
| 2748 | winhost22.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\Adobe\Acrobat Reader DC\Reader\AcroApp\CAT\Combine_R_RHP.aapp | — | |
MD5:— | SHA256:— | |||
| 2748 | winhost22.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\Adobe\Acrobat Reader DC\Reader\AcroApp\CAT\Certificates_R.aapp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report