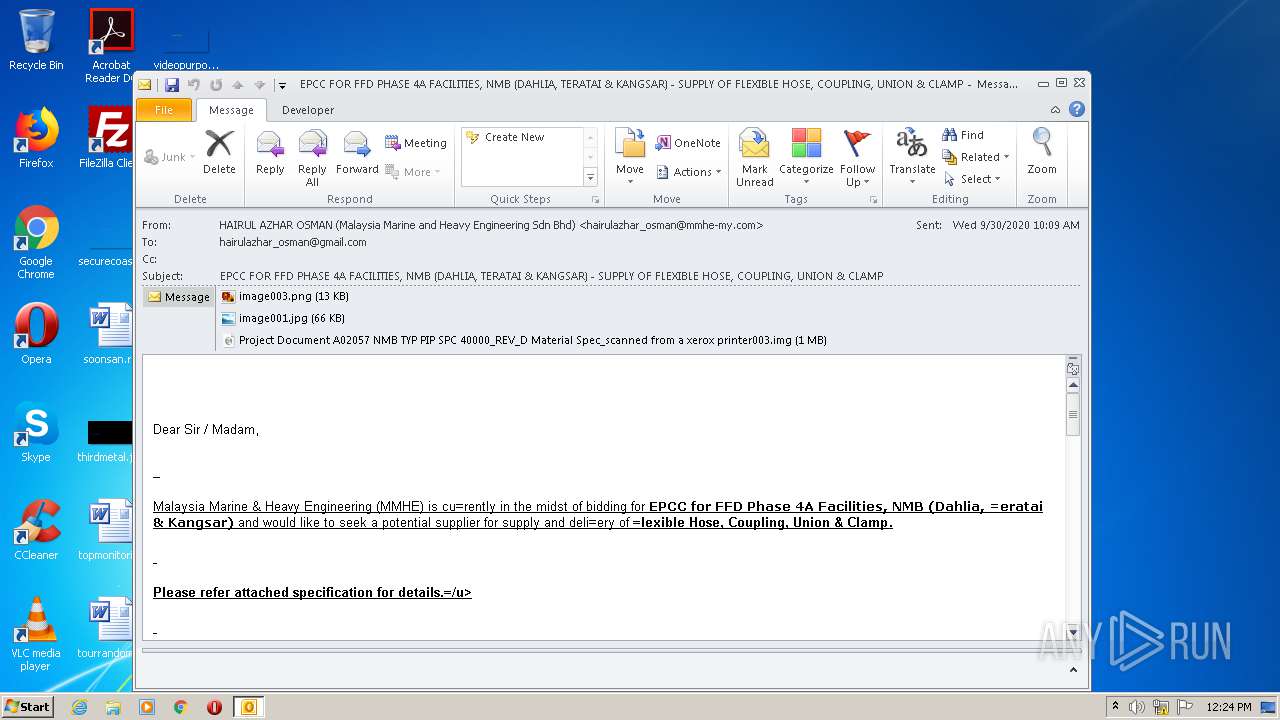
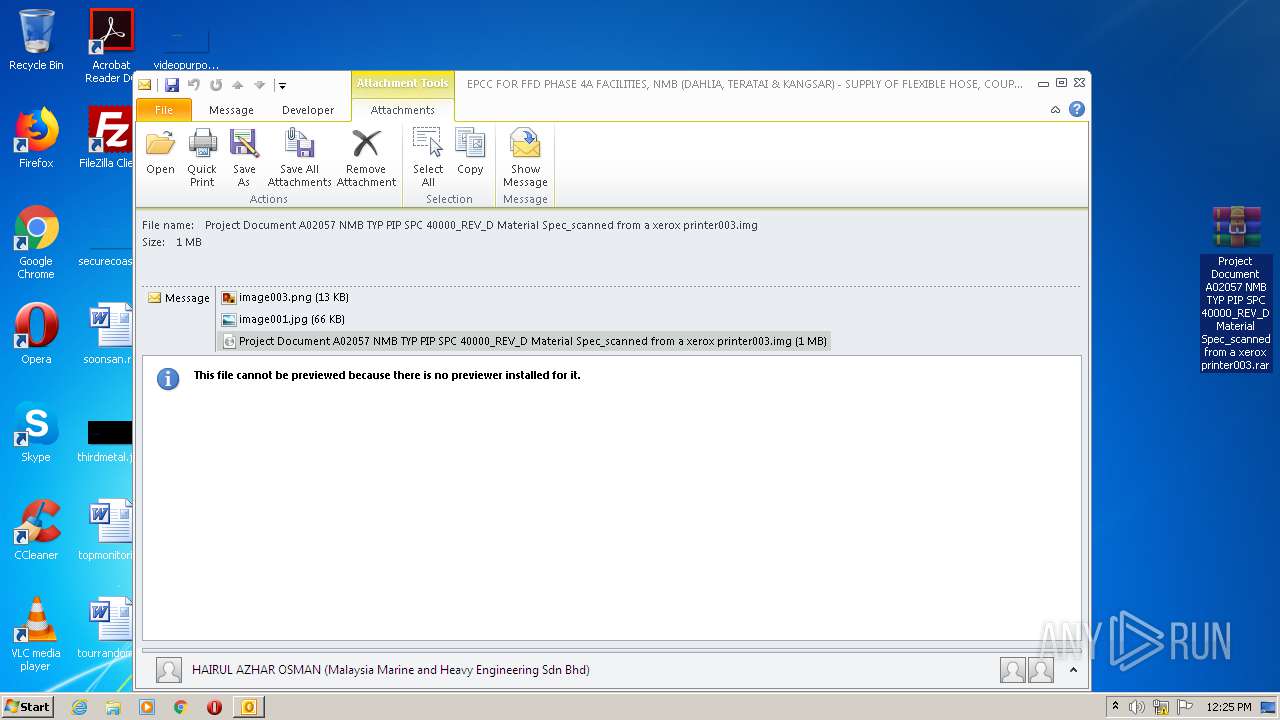
| File name: | EPCC FOR FFD PHASE 4A FACILITIES, NMB (DAHLIA, TERATAI & KANGSAR) - SUPPLY OF FLEXIBLE HOSE, COUPLING, UNION & CLAMP.eml |
| Full analysis: | https://app.any.run/tasks/c319be63-881e-401c-b1f6-1a061db3f3c9 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | September 30, 2020, 11:24:20 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | SMTP mail, ASCII text, with very long lines |
| MD5: | 13EAF45BBE0127B49E3B38658D85DBEA |
| SHA1: | 201EDA0161B9C9ACB1E10950C57EDD466F8AFEE4 |
| SHA256: | AED8E283F8493E2076FBB3918781F2750B0182C6D35B00779F30DB23919C231A |
| SSDEEP: | 12288:LYl55GhR5/Uc7m7kTGVqB+TjoQ7lSuUHt9GxWD7gwS7zteCWbFAqhs1MUAhUiJpQ:sl55GhRVdlgZSurWfgwEgjFc11cpCz |
MALICIOUS
Application was dropped or rewritten from another process
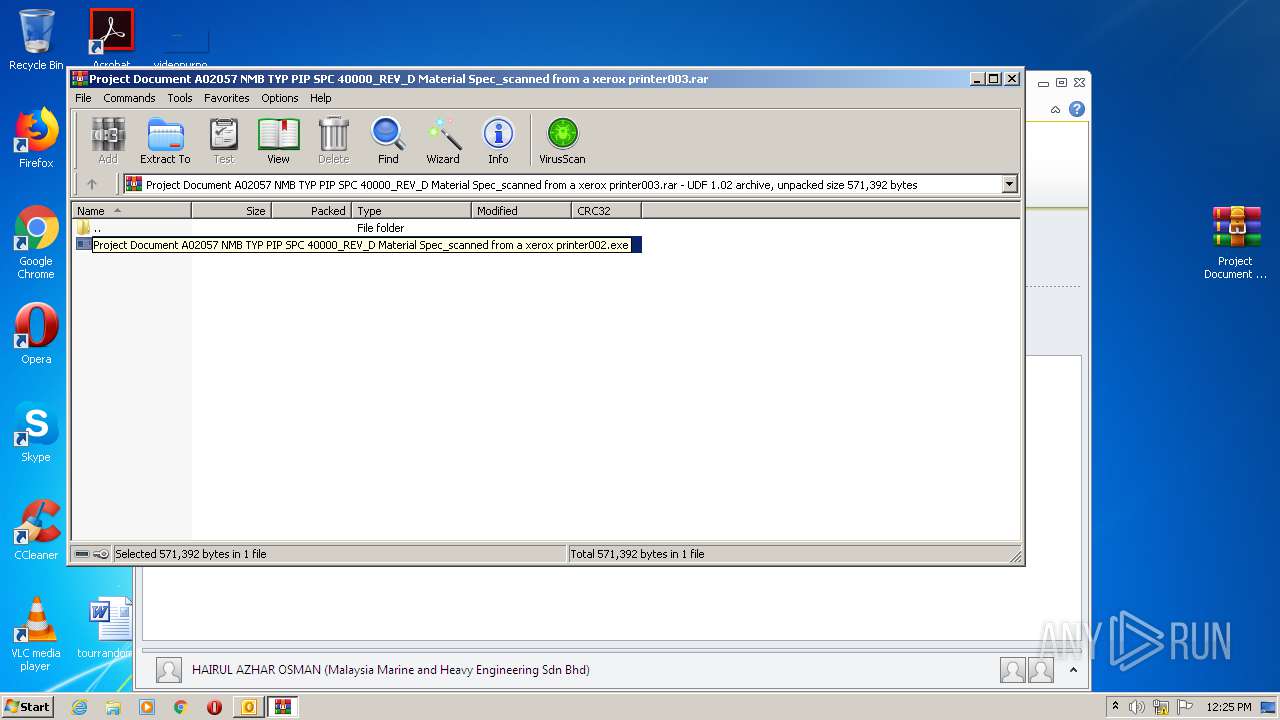
- Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer002.exe (PID: 3144)
- Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer002.exe (PID: 3592)
- Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer002.exe (PID: 2672)
- Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer002.exe (PID: 3028)
- Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer002.exe (PID: 3264)
- Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer002.exe (PID: 3396)
Uses Task Scheduler to run other applications
- Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer002.exe (PID: 3144)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 2424)
AGENTTESLA was detected
- Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer002.exe (PID: 3396)
Actions looks like stealing of personal data
- Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer002.exe (PID: 3396)
SUSPICIOUS
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 2196)
Creates files in the user directory
- OUTLOOK.EXE (PID: 2196)
- Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer002.exe (PID: 3144)
- Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer002.exe (PID: 3396)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1984)
- Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer002.exe (PID: 3144)
Application launched itself
- Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer002.exe (PID: 3144)
Reads the cookies of Mozilla Firefox
- Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer002.exe (PID: 3396)
Reads the cookies of Google Chrome
- Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer002.exe (PID: 3396)
INFO
Manual execution by user
- WinRAR.exe (PID: 1984)
- Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer002.exe (PID: 3592)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 2196)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 1) (100) |
|---|
Total processes
50
Monitored processes
10
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
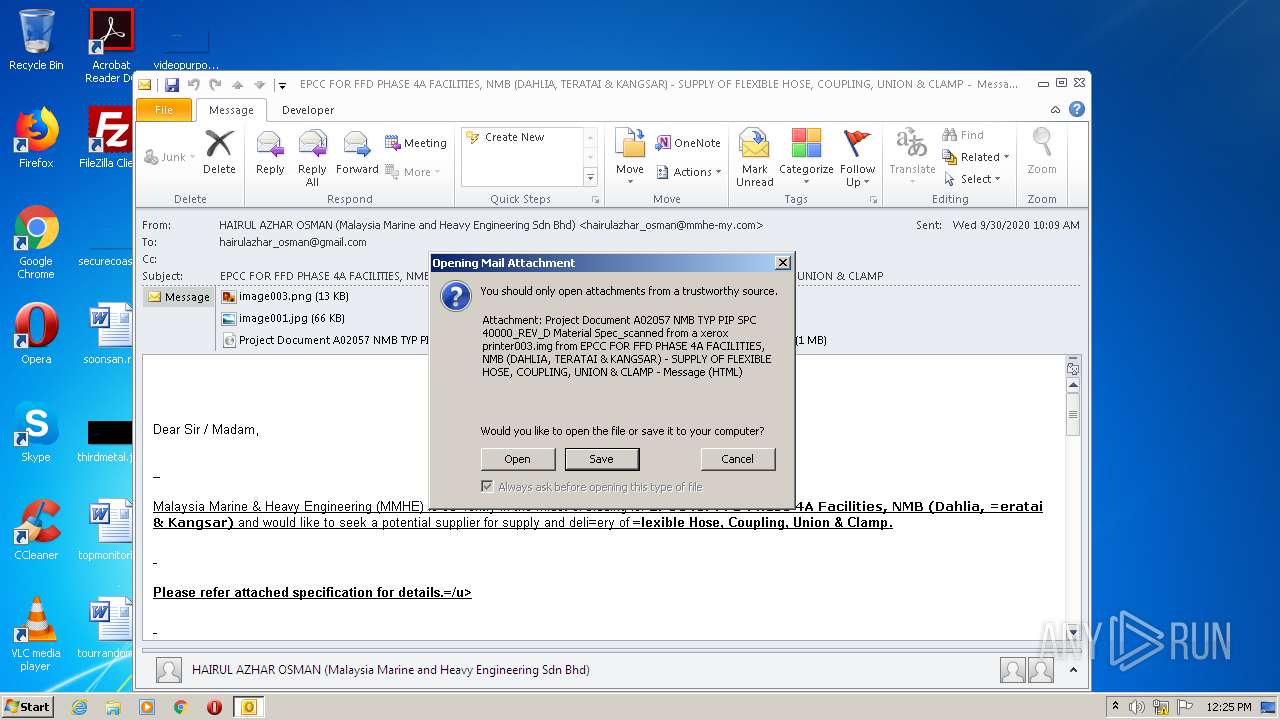
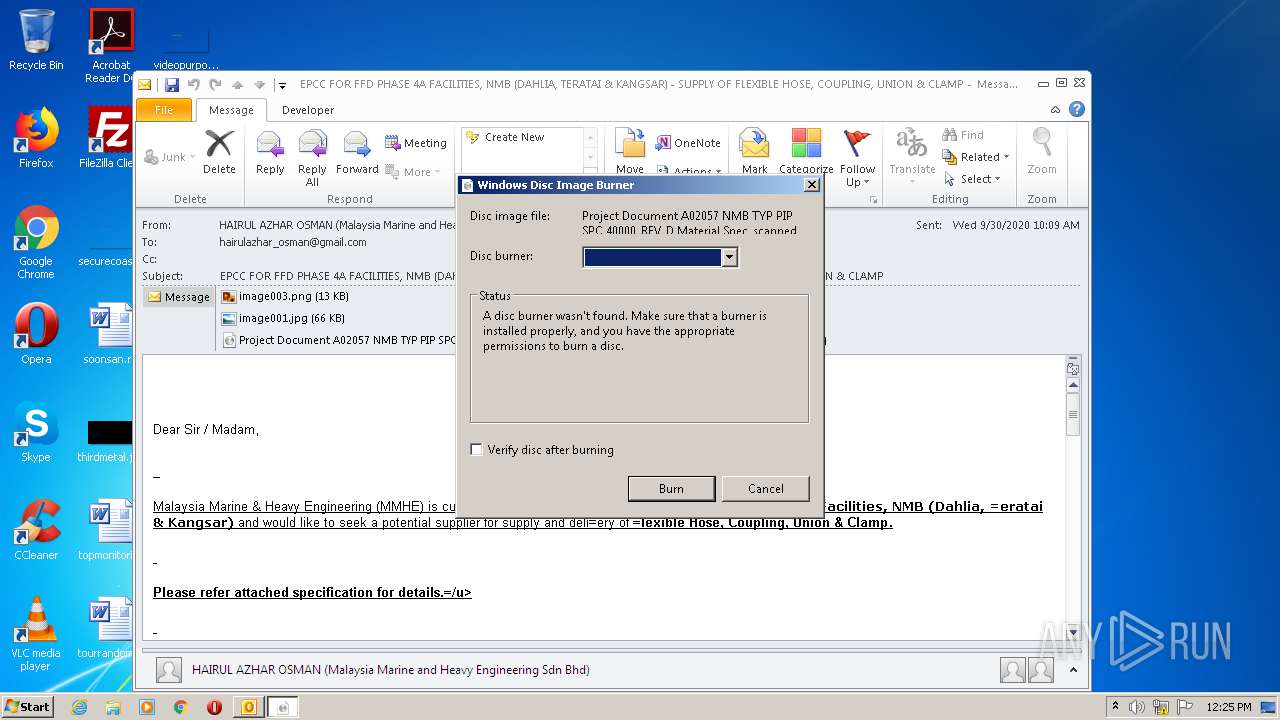
| 1900 | "C:\Windows\System32\isoburn.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\JLY8E92F\Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer003.img" | C:\Windows\System32\isoburn.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Disc Image Burning Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
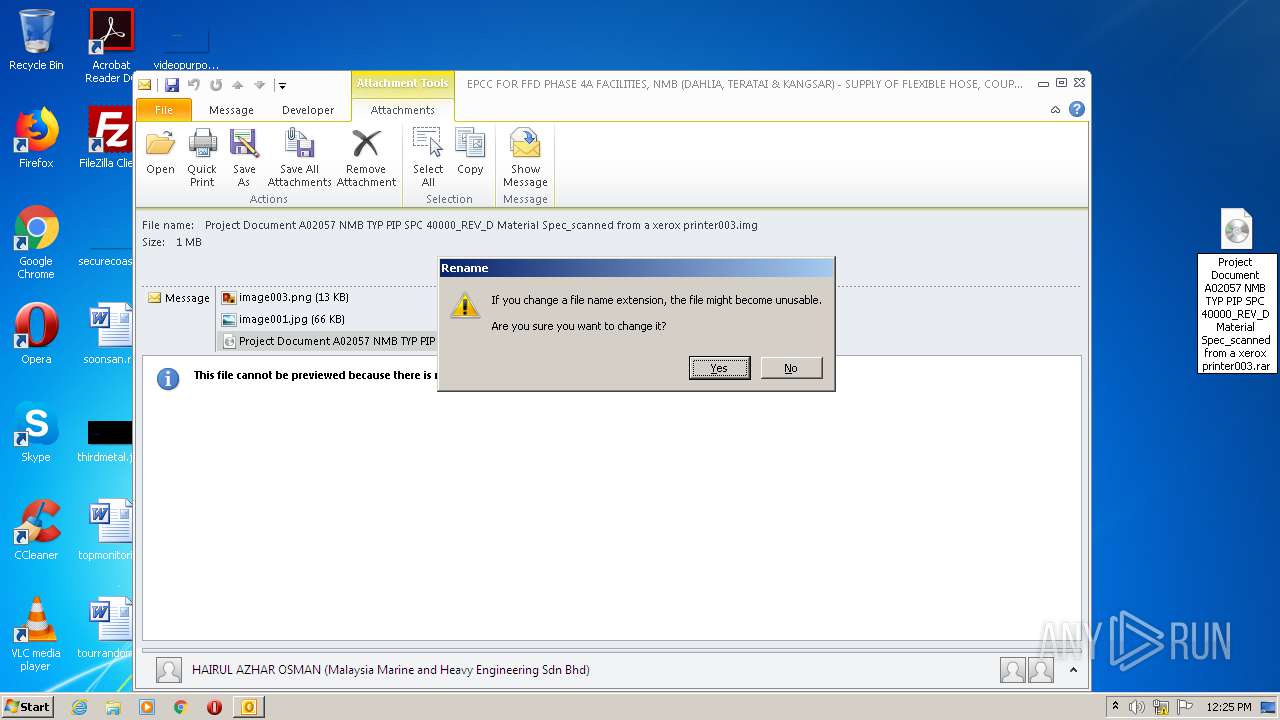
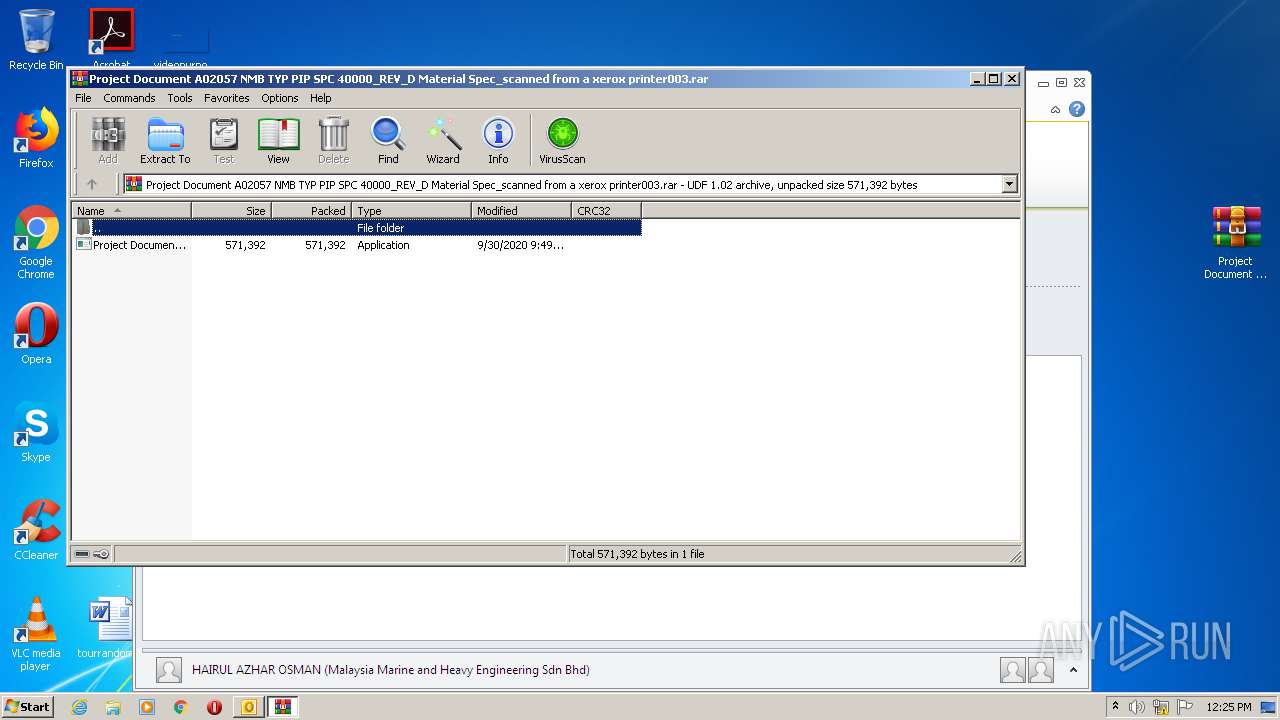
| 1984 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer003.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2196 | "C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Temp\9fc43c3f-39f1-45d1-8c6a-23da473ed500.eml" | C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 2424 | "C:\Windows\System32\schtasks.exe" /Create /TN "Updates\rahQfP" /XML "C:\Users\admin\AppData\Local\Temp\tmp505A.tmp" | C:\Windows\System32\schtasks.exe | — | Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer002.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2672 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1984.46284\Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer002.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1984.46284\Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer002.exe | — | Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer002.exe | |||||||||||
User: admin Company: theHTPC.net Integrity Level: MEDIUM Description: Folder GUI Exit code: 4294967295 Version: 1.4.4.0 Modules
| |||||||||||||||
| 3028 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1984.46284\Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer002.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1984.46284\Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer002.exe | — | Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer002.exe | |||||||||||
User: admin Company: theHTPC.net Integrity Level: MEDIUM Description: Folder GUI Exit code: 4294967295 Version: 1.4.4.0 Modules
| |||||||||||||||
| 3144 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1984.46284\Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer002.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1984.46284\Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer002.exe | WinRAR.exe | ||||||||||||
User: admin Company: theHTPC.net Integrity Level: MEDIUM Description: Folder GUI Exit code: 0 Version: 1.4.4.0 Modules
| |||||||||||||||
| 3264 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1984.46284\Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer002.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1984.46284\Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer002.exe | — | Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer002.exe | |||||||||||
User: admin Company: theHTPC.net Integrity Level: MEDIUM Description: Folder GUI Exit code: 4294967295 Version: 1.4.4.0 Modules
| |||||||||||||||
| 3396 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1984.46284\Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer002.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1984.46284\Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer002.exe | Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer002.exe | ||||||||||||
User: admin Company: theHTPC.net Integrity Level: MEDIUM Description: Folder GUI Exit code: 0 Version: 1.4.4.0 Modules
| |||||||||||||||
| 3592 | "C:\Users\admin\Desktop\Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer002.exe" | C:\Users\admin\Desktop\Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer002.exe | explorer.exe | ||||||||||||
User: admin Company: theHTPC.net Integrity Level: MEDIUM Description: Folder GUI Exit code: 0 Version: 1.4.4.0 Modules
| |||||||||||||||
Total events
2 415
Read events
1 840
Write events
556
Delete events
19
Modification events
| (PID) Process: | (2196) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2196) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2196) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2196) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2196) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2196) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2196) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2196) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2196) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (2196) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: Off | |||
Executable files
2
Suspicious files
2
Text files
28
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2196 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRAE04.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2196 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\tmpB037.tmp | — | |
MD5:— | SHA256:— | |||
| 2196 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\JLY8E92F\Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer003 (2).img\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 1984 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1984.47056\Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer002.exe | — | |
MD5:— | SHA256:— | |||
| 3396 | Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer002.exe | C:\Users\admin\AppData\Roaming\2lceiwwx.2oe\Chrome\Default\Cookies | — | |
MD5:— | SHA256:— | |||
| 3396 | Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer002.exe | C:\Users\admin\AppData\Roaming\2lceiwwx.2oe\Firefox\Profiles\qldyz51w.default\cookies.sqlite | — | |
MD5:— | SHA256:— | |||
| 3144 | Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer002.exe | C:\Users\admin\AppData\Roaming\rahQfP.exe | executable | |
MD5:— | SHA256:— | |||
| 2196 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
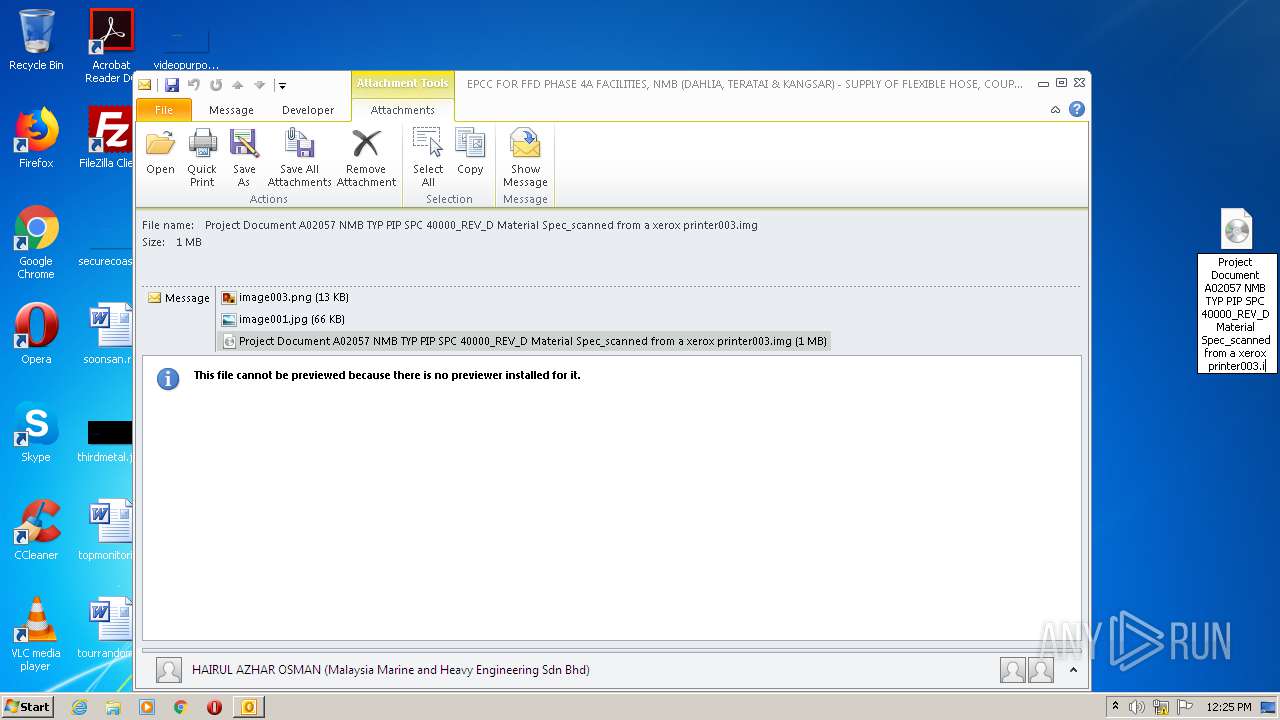
| 2196 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\JLY8E92F\Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer003.img | compressed | |
MD5:— | SHA256:— | |||
| 1984 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1984.46284\Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer002.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
3
DNS requests
2
Threats
14
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2196 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3396 | Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer002.exe | 208.91.199.225:587 | smtp.mitsoi.com | PDR | US | shared |
2196 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
smtp.mitsoi.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3396 | Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer002.exe | Generic Protocol Command Decode | SURICATA Applayer Detect protocol only one direction |
3396 | Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer002.exe | A Network Trojan was detected | SPYWARE [PTsecurity] AgentTesla Exfiltration |
3396 | Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer002.exe | Generic Protocol Command Decode | SURICATA Applayer Detect protocol only one direction |
3396 | Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer002.exe | A Network Trojan was detected | SPYWARE [PTsecurity] AgentTesla Exfiltration |
3396 | Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer002.exe | A Network Trojan was detected | ET TROJAN AgentTesla Exfil Via SMTP |
3396 | Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer002.exe | A Network Trojan was detected | AV TROJAN Win.Keylogger.AgentTesla SMTP Activity |
3396 | Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer002.exe | A Network Trojan was detected | SPYWARE [PTsecurity] AgentTesla Exfiltration |
3396 | Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer002.exe | A Network Trojan was detected | ET TROJAN AgentTesla Exfil Via SMTP |
3396 | Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer002.exe | A Network Trojan was detected | AV TROJAN Win.Keylogger.AgentTesla SMTP Activity |
3396 | Project Document A02057 NMB TYP PIP SPC 40000_REV_D Material Spec_scanned from a xerox printer002.exe | A Network Trojan was detected | SPYWARE [PTsecurity] AgentTesla Exfiltration |
4 ETPRO signatures available at the full report