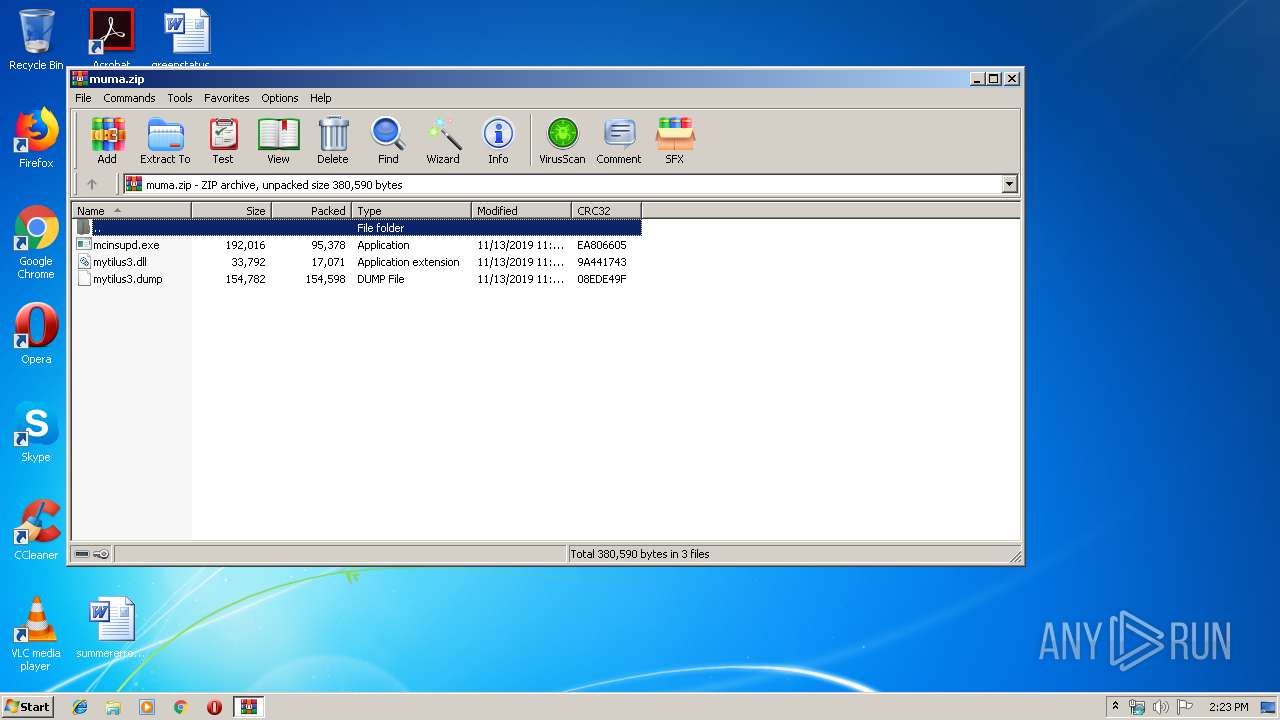
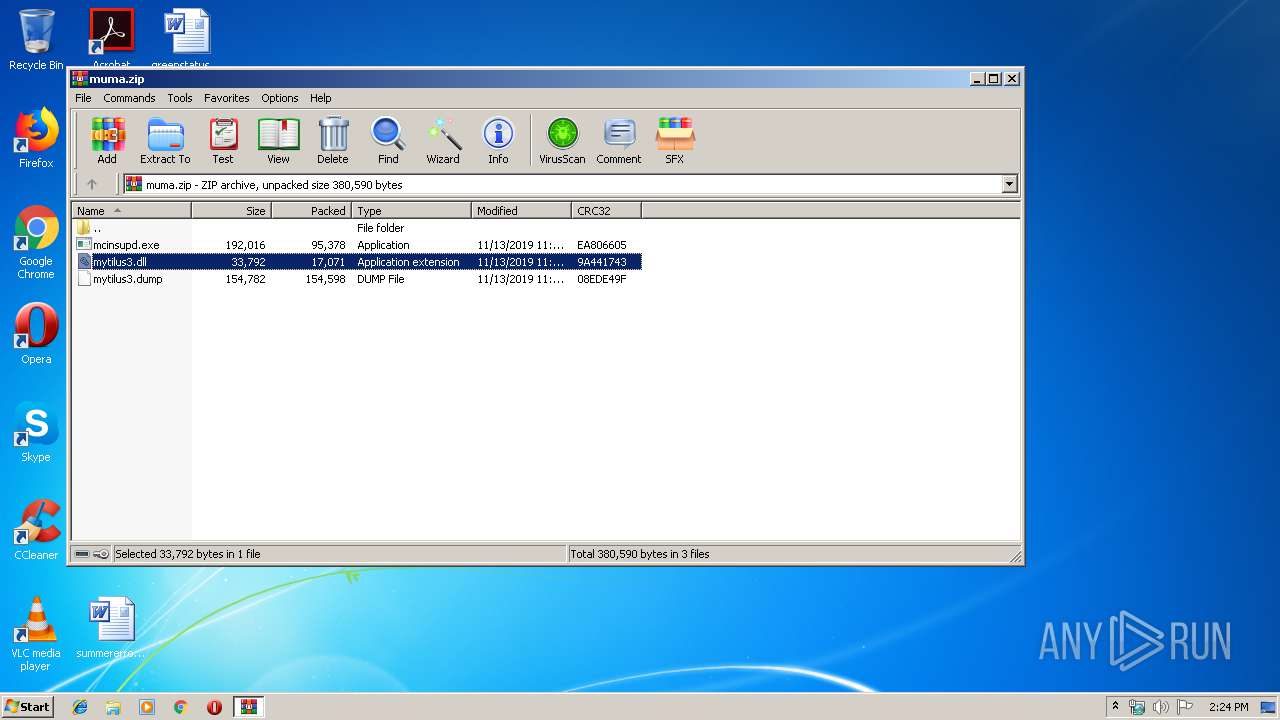
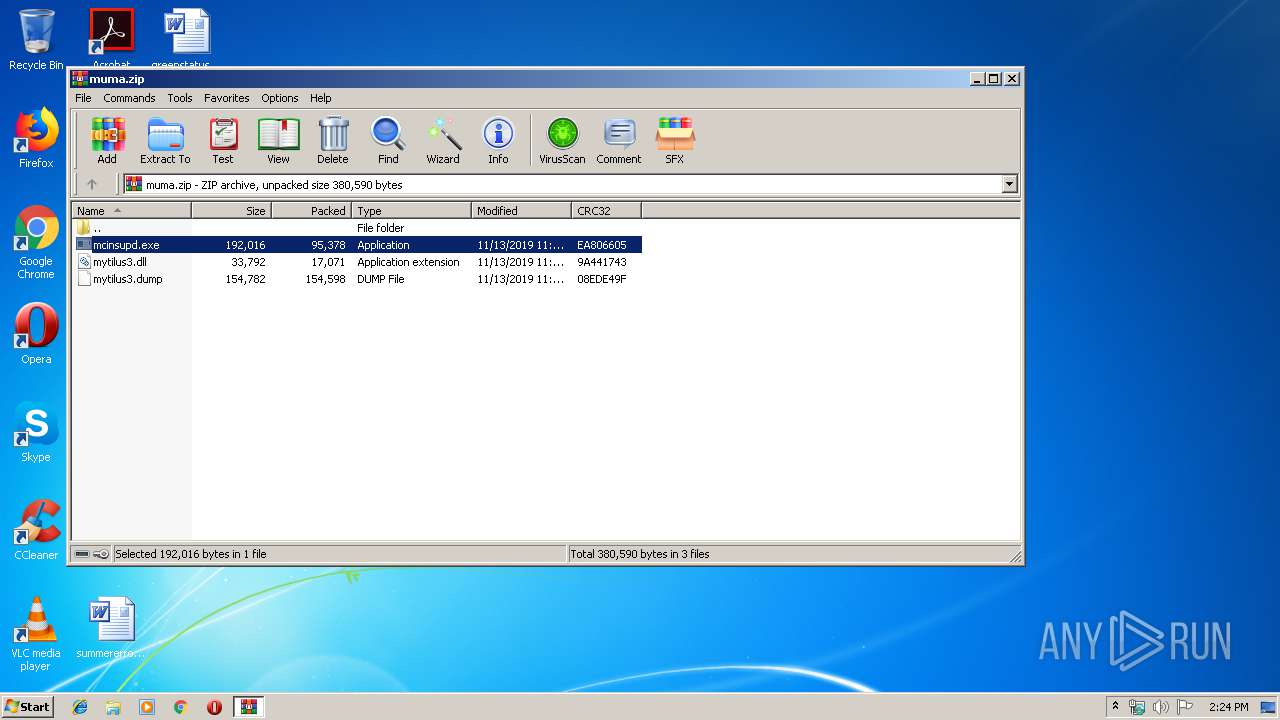
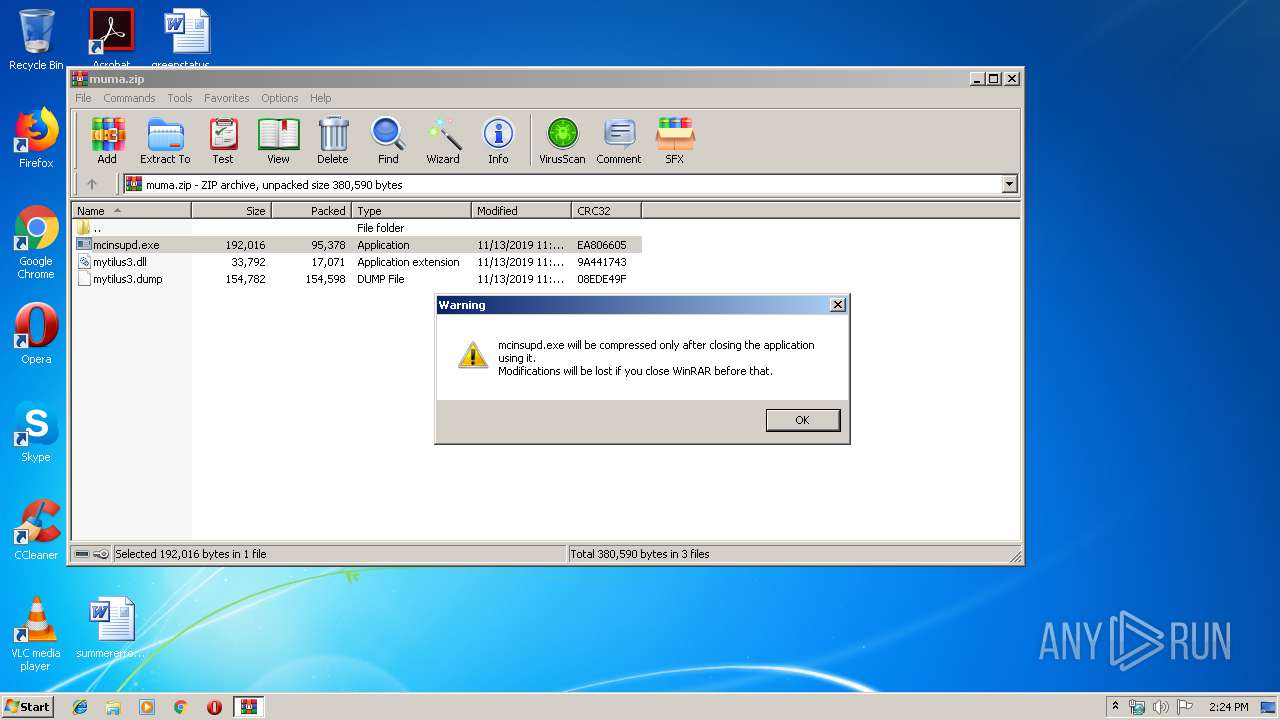
| File name: | muma.zip |
| Full analysis: | https://app.any.run/tasks/202d16cd-7803-421e-bbb8-7f8792f73b37 |
| Verdict: | Malicious activity |
| Threats: | PlugX is a remote access trojan that is used extensively by Chinese APTs. The malware is primarily employed for spying on victims and can perform a variety of malicious activities, such as logging users’ keystrokes and exfiltrating information from browsers. |
| Analysis date: | November 13, 2019, 14:23:11 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 494957415D89703B4903B085BDC54549 |
| SHA1: | E86E7322A8D61D888B981E57CA4665EAE2BB8485 |
| SHA256: | AE7DC28A973611286AF626AADDC51A8CC31BAD785E2B4086159EAF3EED427470 |
| SSDEEP: | 6144:U16jmBxZpx5VrAG06e4TIvkOvRE3ik2gEv1bbr7MbIJe2d1:UIjmtV2Se4YkORlk2gyfgbIJBf |
MALICIOUS
Loads dropped or rewritten executable
- mcinsupd.exe (PID: 3040)
- mcinsupd.exe (PID: 3904)
- mcinsupd.exe (PID: 4004)
- mcinsupd.exe (PID: 3380)
Application was dropped or rewritten from another process
- mcinsupd.exe (PID: 3904)
- mcinsupd.exe (PID: 3040)
- mcinsupd.exe (PID: 4004)
- mcinsupd.exe (PID: 3380)
Known privilege escalation attack
- DllHost.exe (PID: 2692)
Connects to CnC server
- svchost.exe (PID: 2860)
- mcinsupd.exe (PID: 3904)
PLUGX was detected
- mcinsupd.exe (PID: 3904)
Uses SVCHOST.EXE for hidden code execution
- mcinsupd.exe (PID: 3380)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2576)
- mcinsupd.exe (PID: 3040)
- mcinsupd.exe (PID: 3904)
Creates files in the program directory
- mcinsupd.exe (PID: 3904)
- mcinsupd.exe (PID: 3040)
Executed via WMI
- rundll32.exe (PID: 3696)
- mcinsupd.exe (PID: 3040)
Executed via COM
- DllHost.exe (PID: 2692)
Executed as Windows Service
- mcinsupd.exe (PID: 3380)
INFO
Reads the hosts file
- mcinsupd.exe (PID: 3904)
- svchost.exe (PID: 2860)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:11:13 06:53:15 |
| ZipCRC: | 0x9a441743 |
| ZipCompressedSize: | 17071 |
| ZipUncompressedSize: | 33792 |
| ZipFileName: | mytilus3.dll |
Total processes
44
Monitored processes
9
Malicious processes
5
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1556 | C:\Windows\system32\msiexec.exe 209 2860 | C:\Windows\system32\msiexec.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2576 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\muma.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2692 | C:\Windows\system32\DllHost.exe /Processid:{3E5FC7F9-9A51-4367-9063-A120244FBEC7} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2860 | C:\Windows\system32\svchost.exe 201 0 | C:\Windows\system32\svchost.exe | mcinsupd.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3040 | "C:\ProgramData\Windows NT\accessories\mcinsupd.exe" 100 3904 | C:\ProgramData\Windows NT\accessories\mcinsupd.exe | wmiprvse.exe | ||||||||||||
User: admin Company: McAfee, Inc. Integrity Level: MEDIUM Description: McAfee VirusScan API Daily Update Module Exit code: 1223 Version: 13,11,102,0 Modules
| |||||||||||||||
| 3380 | "C:\ProgramData\Windows NT\accessories\mcinsupd.exe" 200 0 | C:\ProgramData\Windows NT\accessories\mcinsupd.exe | — | services.exe | |||||||||||
User: SYSTEM Company: McAfee, Inc. Integrity Level: SYSTEM Description: McAfee VirusScan API Daily Update Module Exit code: 1223 Version: 13,11,102,0 Modules
| |||||||||||||||
| 3696 | C:\Windows\System32\rundll32.exe "C:\ProgramData\Windows NT\accessories\debug.hlp" BypassUAC "C:\ProgramData\Windows NT\accessories\mcinsupd.exe" 100 3904 | C:\Windows\System32\rundll32.exe | — | wmiprvse.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3904 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2576.5053\mcinsupd.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2576.5053\mcinsupd.exe | WinRAR.exe | ||||||||||||
User: admin Company: McAfee, Inc. Integrity Level: MEDIUM Description: McAfee VirusScan API Daily Update Module Exit code: 0 Version: 13,11,102,0 Modules
| |||||||||||||||
| 4004 | "C:\ProgramData\Windows NT\accessories\mcinsupd.exe" 100 3904 | C:\ProgramData\Windows NT\accessories\mcinsupd.exe | — | DllHost.exe | |||||||||||
User: admin Company: McAfee, Inc. Integrity Level: HIGH Description: McAfee VirusScan API Daily Update Module Exit code: 1223 Version: 13,11,102,0 Modules
| |||||||||||||||
Total events
493
Read events
475
Write events
18
Delete events
0
Modification events
| (PID) Process: | (2576) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2576) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2576) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2576) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\muma.zip | |||
| (PID) Process: | (2576) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2576) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2576) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2576) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2576) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2576) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
5
Suspicious files
2
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2576 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2576.5053\mytilus3.dump | binary | |
MD5:— | SHA256:— | |||
| 3904 | mcinsupd.exe | C:\ProgramData\Windows NT\accessories\mytilus3.dump | binary | |
MD5:— | SHA256:— | |||
| 3904 | mcinsupd.exe | C:\ProgramData\Windows NT\accessories\mytilus3.dll | executable | |
MD5:— | SHA256:— | |||
| 2576 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2576.5053\mcinsupd.exe | executable | |
MD5:53C1F090734129FBCCC2693D6B4AFA04 | SHA256:507D49186748DD83D808281743A17FCA4B226883C410EC76EB305360CBC8C091 | |||
| 3040 | mcinsupd.exe | C:\ProgramData\Windows NT\accessories\debug.hlp | executable | |
MD5:— | SHA256:— | |||
| 2576 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2576.5053\mytilus3.dll | executable | |
MD5:— | SHA256:— | |||
| 3904 | mcinsupd.exe | C:\ProgramData\Windows NT\accessories\mcinsupd.exe | executable | |
MD5:53C1F090734129FBCCC2693D6B4AFA04 | SHA256:507D49186748DD83D808281743A17FCA4B226883C410EC76EB305360CBC8C091 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
40
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Threats
PID | Process | Class | Message |
|---|---|---|---|
2860 | svchost.exe | A Network Trojan was detected | MALWARE [PTsecurity] Backdoor.PlugX Checkin |
3904 | mcinsupd.exe | unknown | SURICATA DNS malformed request data |
2860 | svchost.exe | unknown | SURICATA DNS malformed request data |
2860 | svchost.exe | A Network Trojan was detected | MALWARE [PTsecurity] Backdoor.PlugX Checkin |
2860 | svchost.exe | unknown | SURICATA DNS malformed response data |
2860 | svchost.exe | unknown | SURICATA DNS malformed request data |
2860 | svchost.exe | unknown | SURICATA DNS malformed response data |
2860 | svchost.exe | unknown | SURICATA DNS malformed request data |
2860 | svchost.exe | unknown | SURICATA DNS malformed response data |
2860 | svchost.exe | unknown | SURICATA DNS malformed request data |
6 ETPRO signatures available at the full report