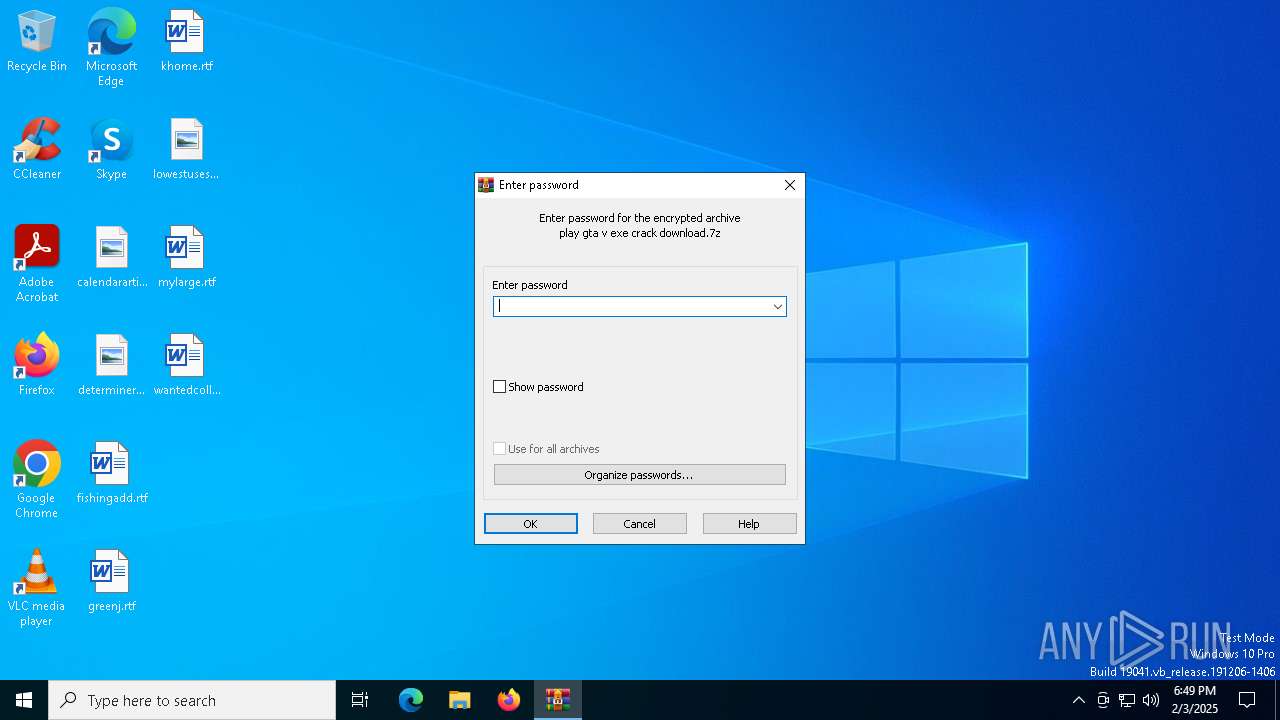
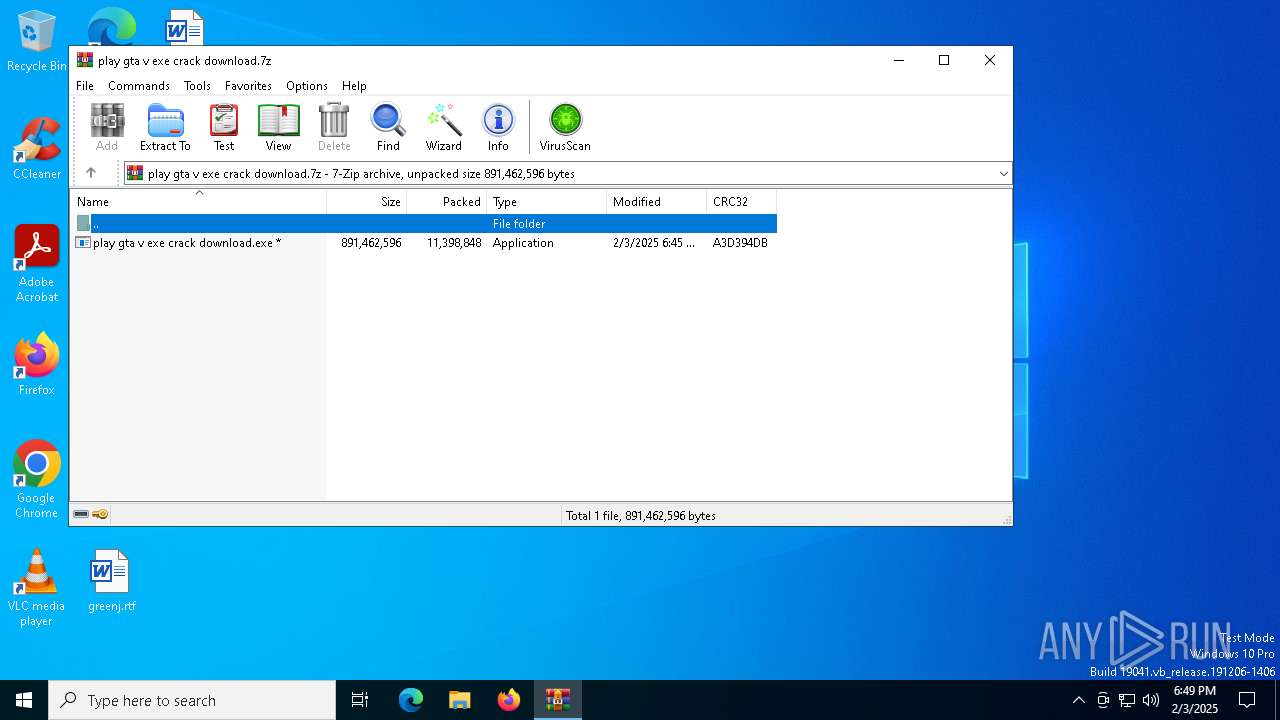
| File name: | play gta v exe crack download.7z |
| Full analysis: | https://app.any.run/tasks/fd240ea7-f2fd-4452-9af1-a7f8b20d7d47 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | February 03, 2025, 18:49:27 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 2F41D6BA830A6F88E05FB4CE2A850868 |
| SHA1: | AF6B2D42CE27C1247349C001CDA1EB7D099BF917 |
| SHA256: | ADFD631FB7566DE1538CAEBA21106E2E2104BD54759AB8235F729BDACCA23A89 |
| SSDEEP: | 98304:M9/zo6YrO+ox6AsRgrnIFdd+3EyIXNMrZ77SoBBXev9zFgo3BpLgWL+FoCk1EIE/:FosazuLnzGBxGbmQgKtScY6iLTcOpaQ |
MALICIOUS
AutoIt loader has been detected (YARA)
- Asp.com (PID: 3876)
LUMMA mutex has been found
- Asp.com (PID: 3876)
Steals credentials from Web Browsers
- Asp.com (PID: 3876)
Actions looks like stealing of personal data
- Asp.com (PID: 3876)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6636)
- play gta v exe crack download.exe (PID: 5920)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 4444)
Starts CMD.EXE for commands execution
- play gta v exe crack download.exe (PID: 5920)
- cmd.exe (PID: 4444)
Get information on the list of running processes
- cmd.exe (PID: 4444)
Executing commands from ".cmd" file
- play gta v exe crack download.exe (PID: 5920)
The executable file from the user directory is run by the CMD process
- Asp.com (PID: 3876)
Application launched itself
- cmd.exe (PID: 4444)
Starts application with an unusual extension
- cmd.exe (PID: 4444)
Starts the AutoIt3 executable file
- cmd.exe (PID: 4444)
There is functionality for taking screenshot (YARA)
- play gta v exe crack download.exe (PID: 5920)
- Asp.com (PID: 3876)
Searches for installed software
- Asp.com (PID: 3876)
INFO
Checks supported languages
- play gta v exe crack download.exe (PID: 5920)
- extrac32.exe (PID: 4388)
- Asp.com (PID: 3876)
Process checks computer location settings
- play gta v exe crack download.exe (PID: 5920)
Create files in a temporary directory
- play gta v exe crack download.exe (PID: 5920)
- extrac32.exe (PID: 4388)
Creates a new folder
- cmd.exe (PID: 2676)
Reads the computer name
- extrac32.exe (PID: 4388)
- play gta v exe crack download.exe (PID: 5920)
- Asp.com (PID: 3876)
Reads mouse settings
- Asp.com (PID: 3876)
Reads the software policy settings
- Asp.com (PID: 3876)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|
Total processes
141
Monitored processes
16
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1356 | choice /d y /t 5 | C:\Windows\SysWOW64\choice.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Offers the user a choice Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2676 | cmd /c md 532222 | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3060 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3140 | findstr /I "opssvc wrsa" | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3524 | tasklist | C:\Windows\SysWOW64\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3876 | Asp.com F | C:\Users\admin\AppData\Local\Temp\532222\Asp.com | cmd.exe | ||||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script (Beta) Exit code: 0 Version: 3, 3, 15, 5 Modules
| |||||||||||||||
| 4052 | cmd /c copy /b ..\Cookies + ..\Duplicate + ..\Printing + ..\Scheme + ..\Looks + ..\Potter + ..\Bathrooms F | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4264 | findstr /V "mails" Retro | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4388 | extrac32 /Y /E Rounds | C:\Windows\SysWOW64\extrac32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® CAB File Extract Utility Exit code: 0 Version: 5.00 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
2 991
Read events
2 972
Write events
19
Delete events
0
Modification events
| (PID) Process: | (6636) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (6636) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6636) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6636) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6636) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\play gta v exe crack download.7z | |||
| (PID) Process: | (6636) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6636) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6636) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6636) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6636) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
Executable files
0
Suspicious files
22
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6636 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb6636.39570\play gta v exe crack download.exe | — | |
MD5:— | SHA256:— | |||
| 5920 | play gta v exe crack download.exe | C:\Users\admin\AppData\Local\Temp\Potter | binary | |
MD5:38BBDDC451FCD419FD59D1E3780C4741 | SHA256:F97F291F7BC8FD1B5094FBCB7DA2EDE33ACA17F335FFCEA0F8937445E38D3813 | |||
| 5920 | play gta v exe crack download.exe | C:\Users\admin\AppData\Local\Temp\Rounds | compressed | |
MD5:3B72CA69833E3724EF12685AFB8FCF2F | SHA256:DCD7BC6369F41577CEECCB9264080BFBA7AA674CECDF59B9BD6DCA42C579A296 | |||
| 5920 | play gta v exe crack download.exe | C:\Users\admin\AppData\Local\Temp\Cookies | binary | |
MD5:FF99E54FCAE37D2FA8B5E6D787D6D657 | SHA256:6C1BE0FF1E5A33A98F54C275B5234D2E25C66E84F46358C031174BA4CD5BE041 | |||
| 5920 | play gta v exe crack download.exe | C:\Users\admin\AppData\Local\Temp\Bathrooms | binary | |
MD5:BA9A1A76B5929930DB92D993217F52D7 | SHA256:044F77C5F146CF9A29CE2E5EA3C6C6CAE614C4881645AD8D1FE269142271619F | |||
| 4388 | extrac32.exe | C:\Users\admin\AppData\Local\Temp\Documented | binary | |
MD5:A63FED71003AE4ABF95E7C091BE37C53 | SHA256:C44E40488EEFBC0D317EF334566F6D47B7A6E08671ACE25FFB10DA875C53826F | |||
| 5920 | play gta v exe crack download.exe | C:\Users\admin\AppData\Local\Temp\Looks | binary | |
MD5:9A57B66BD6B8DCEDB5E6B880BB7F8446 | SHA256:C5B40394D6E12B93A04D5DFEA2321EBFFE2E7BE1651F6F6D38595289788FBFAF | |||
| 4444 | cmd.exe | C:\Users\admin\AppData\Local\Temp\Grip.cmd | text | |
MD5:B1C856B6C8AC03CE943A63E628B9382D | SHA256:88A22ED428B328F0E61D28FFF29285E27E3B13EACDB43F469F6C16CAE8E824E2 | |||
| 4388 | extrac32.exe | C:\Users\admin\AppData\Local\Temp\Serum | binary | |
MD5:C34D807E18360CA17006969788665A70 | SHA256:CFC5558CC00B98ED2028596AD4D6F54D014D693B2B2ED71133F8EF5CFB29F99A | |||
| 4388 | extrac32.exe | C:\Users\admin\AppData\Local\Temp\Recovery | binary | |
MD5:B2FDA6055842C518CEF0743DC3BF1491 | SHA256:9AAB3E0CFACF1311EE6E5DB388D323EA9098AFC404D8636C83EEEBC9B3863B27 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
35
DNS requests
18
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6184 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7052 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7052 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 2.21.65.132:443 | www.bing.com | Akamai International B.V. | NL | whitelisted |
— | — | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1176 | svchost.exe | 20.190.159.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1076 | svchost.exe | 184.28.89.167:443 | go.microsoft.com | AKAMAI-AS | US | whitelisted |
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6184 | backgroundTaskHost.exe | 20.31.169.57:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |