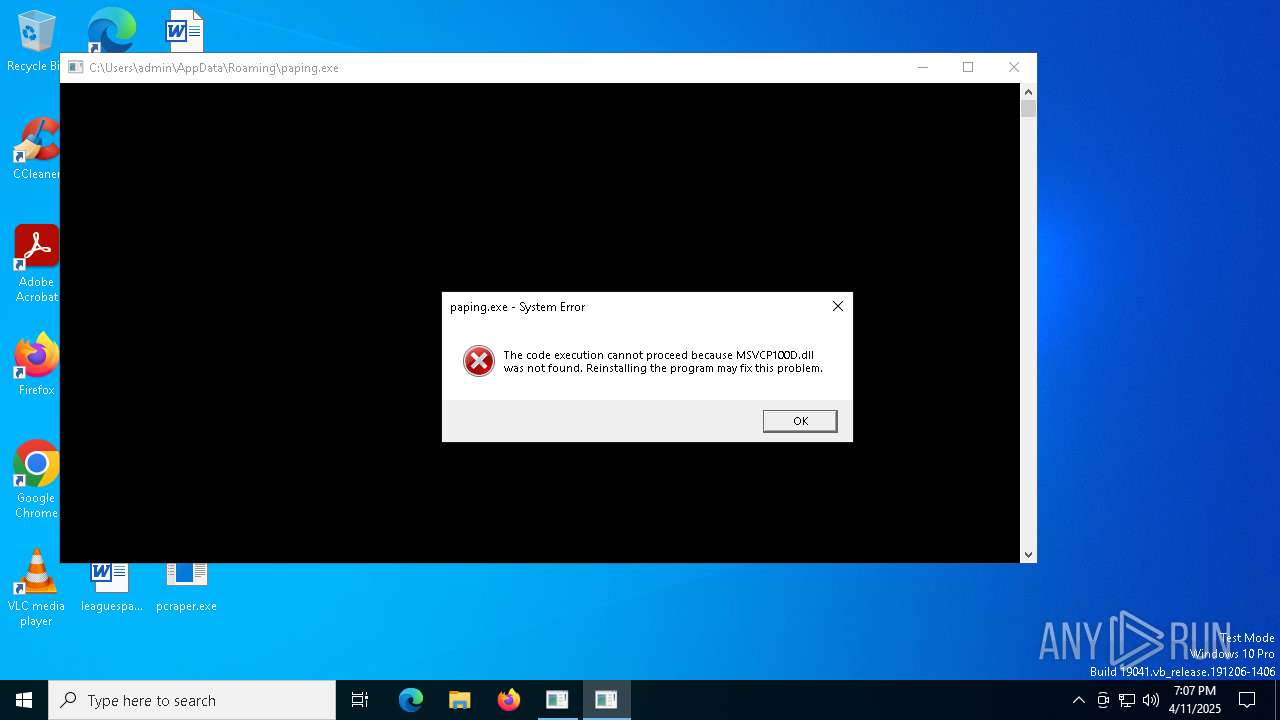
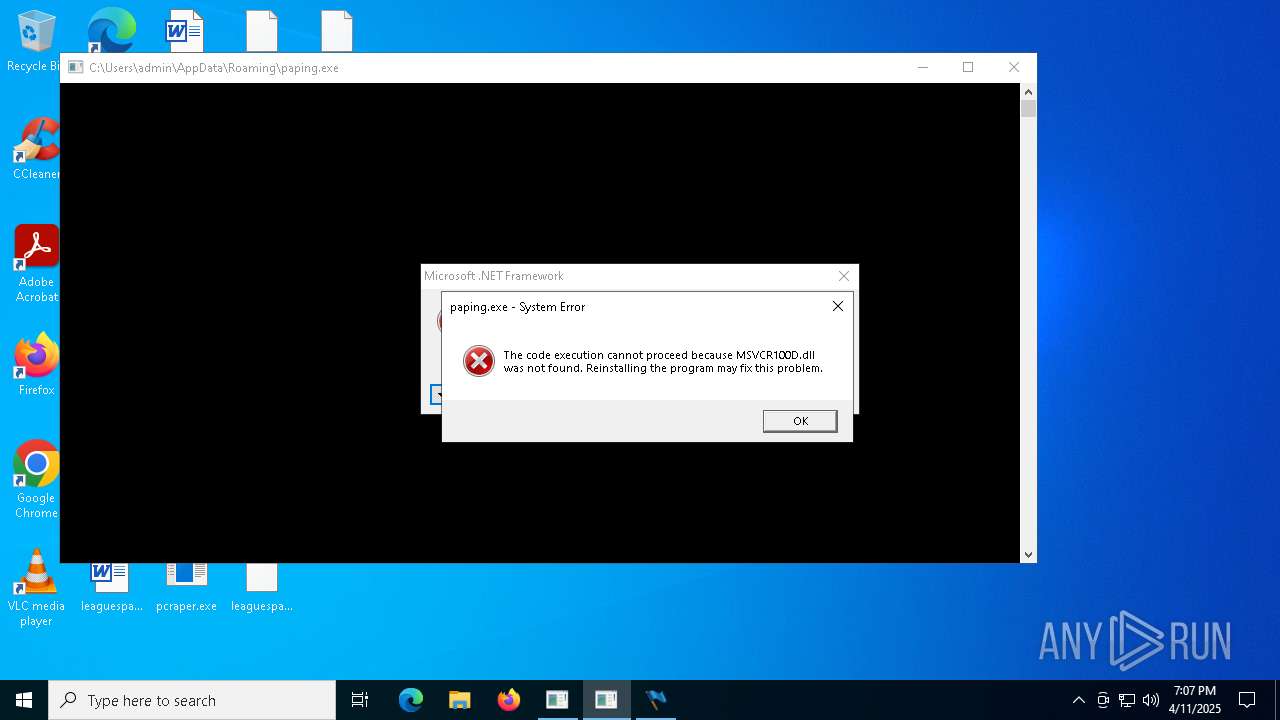
| File name: | pcraper.exe |
| Full analysis: | https://app.any.run/tasks/fff84610-9ad5-489b-b182-294baf74f5b3 |
| Verdict: | Malicious activity |
| Threats: | Arkei is a stealer type malware capable of collecting passwords, autosaved forms, cryptocurrency wallet credentials, and files. |
| Analysis date: | April 11, 2025, 19:07:08 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows, 4 sections |
| MD5: | 769BF15770789DE44C623B22536B9AF8 |
| SHA1: | 201BC12C782591A524B76A03C815251558BC0E21 |
| SHA256: | ADFD4E9F51BCD27935F153E44B060B6978F55DA9135F34CC62361DBBF2D2DB57 |
| SSDEEP: | 393216:eigWOT7pkSmtK0NsDrAggcSYwybUG7Syl3SIspfXvYKiTSOQ1edHpDnWK:e8MOSkqvAggG1QmSycIifXvzTPK |
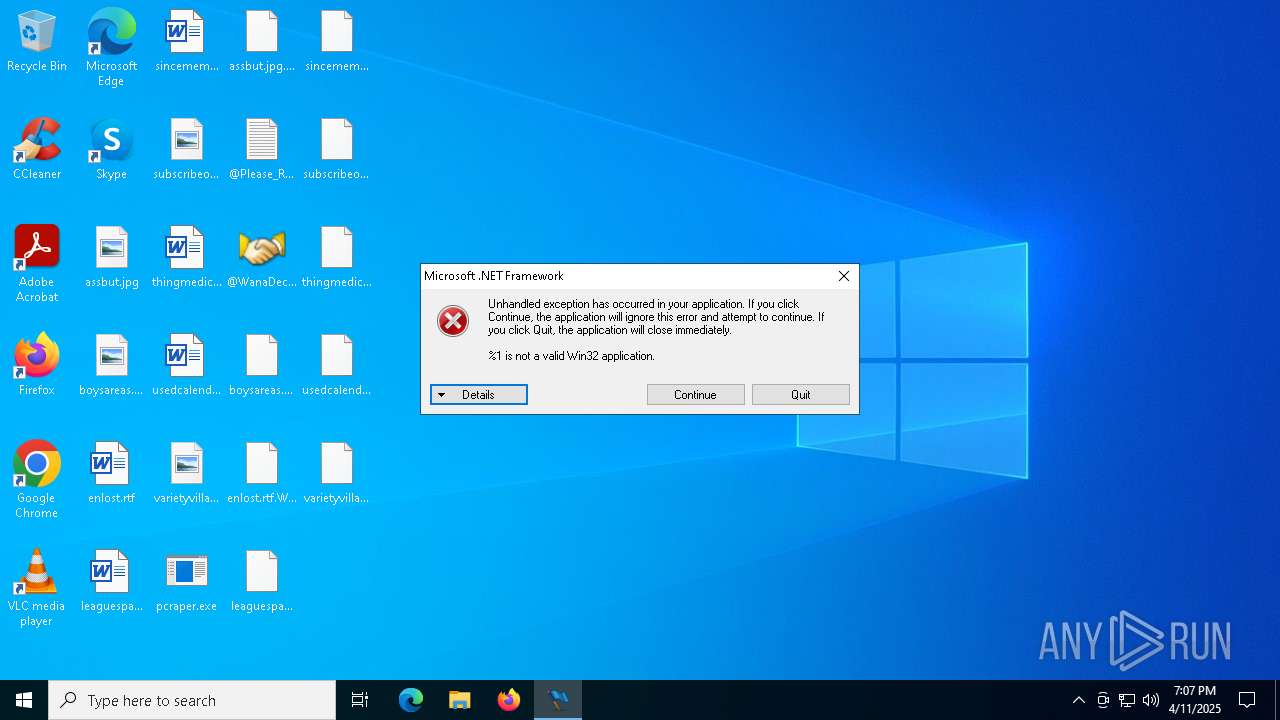
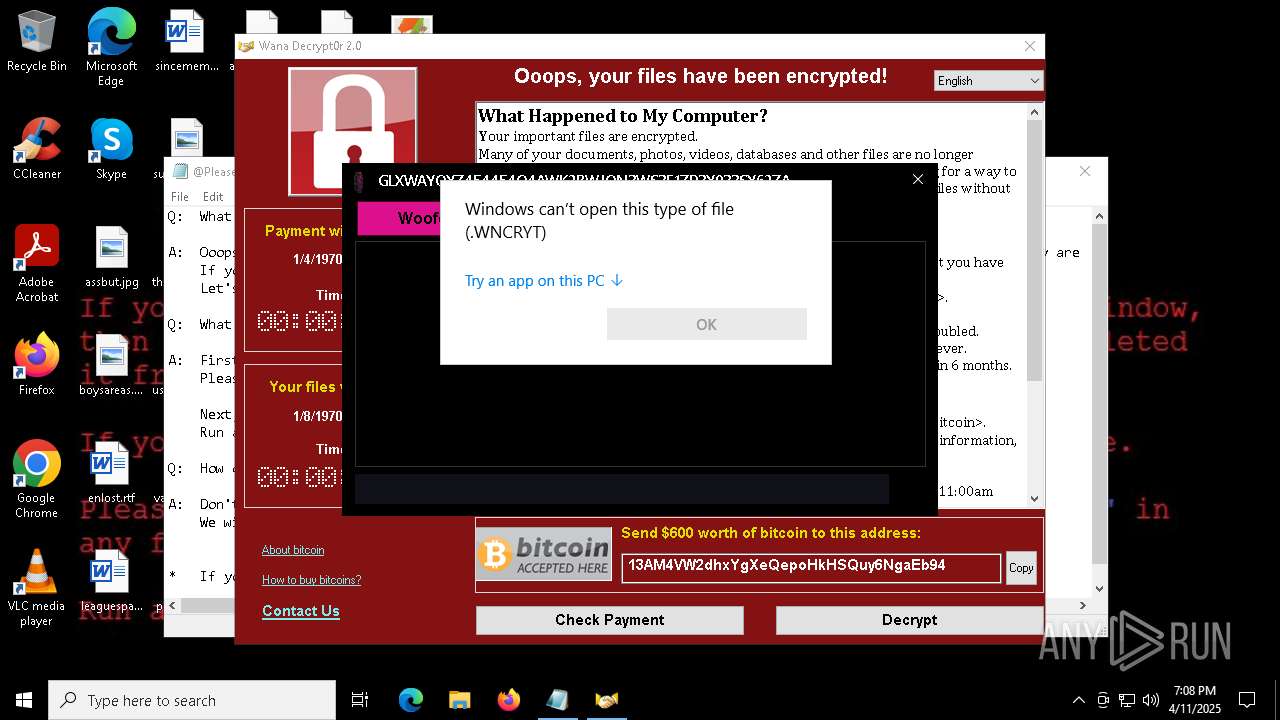
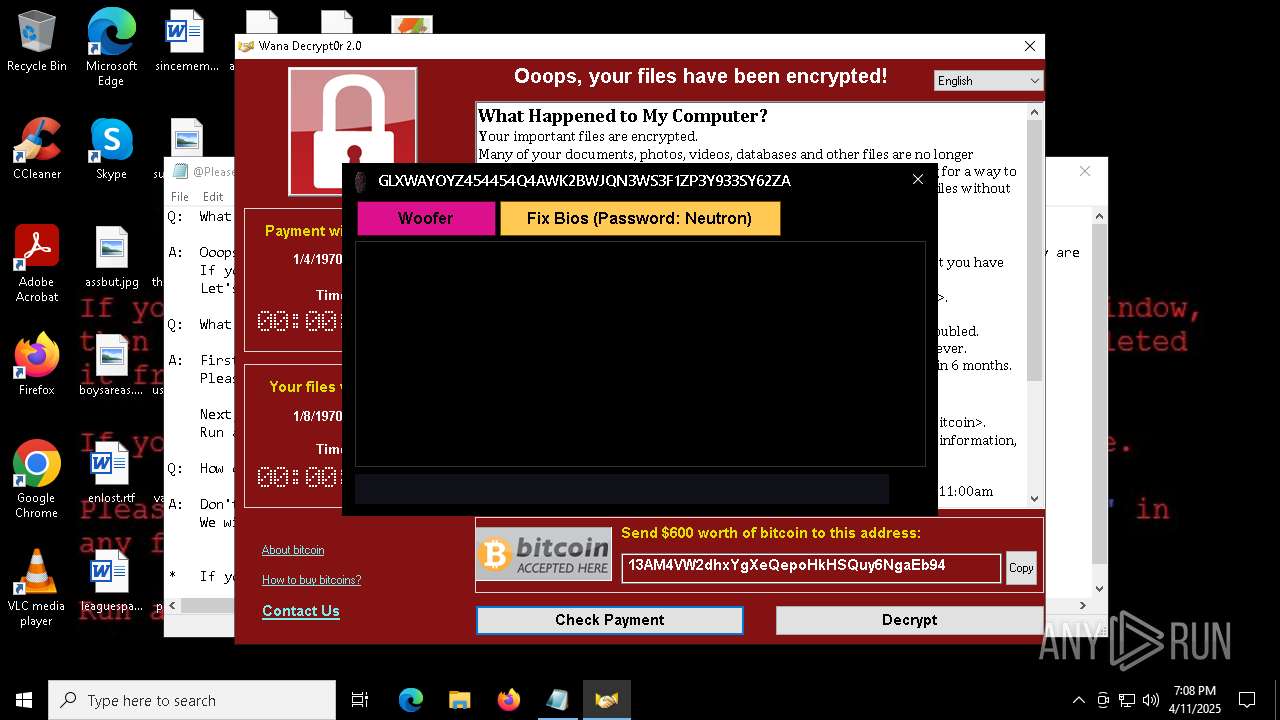
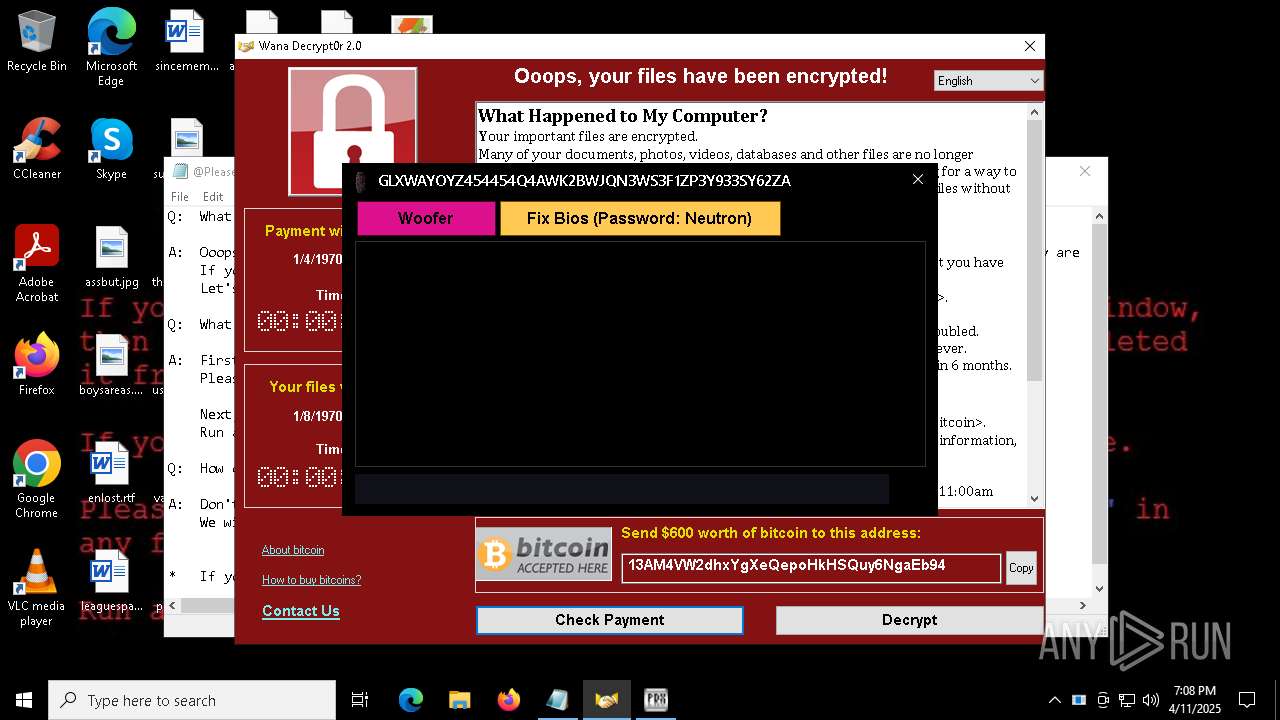
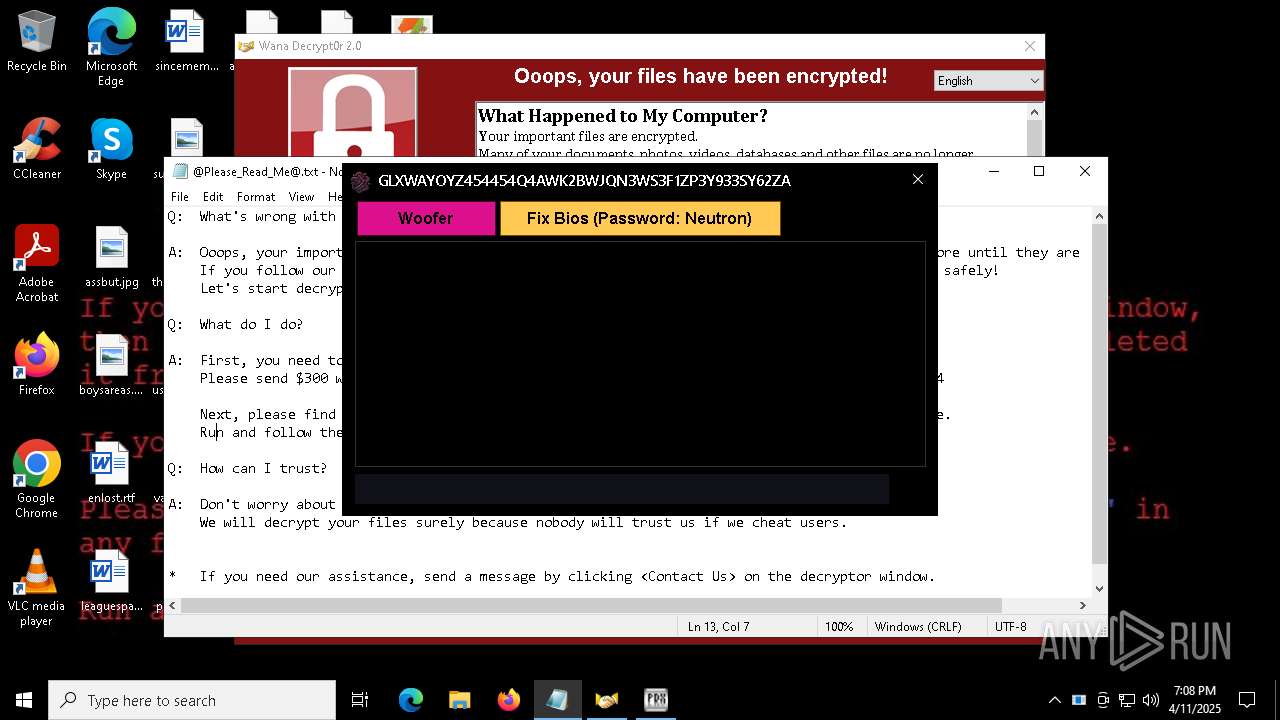
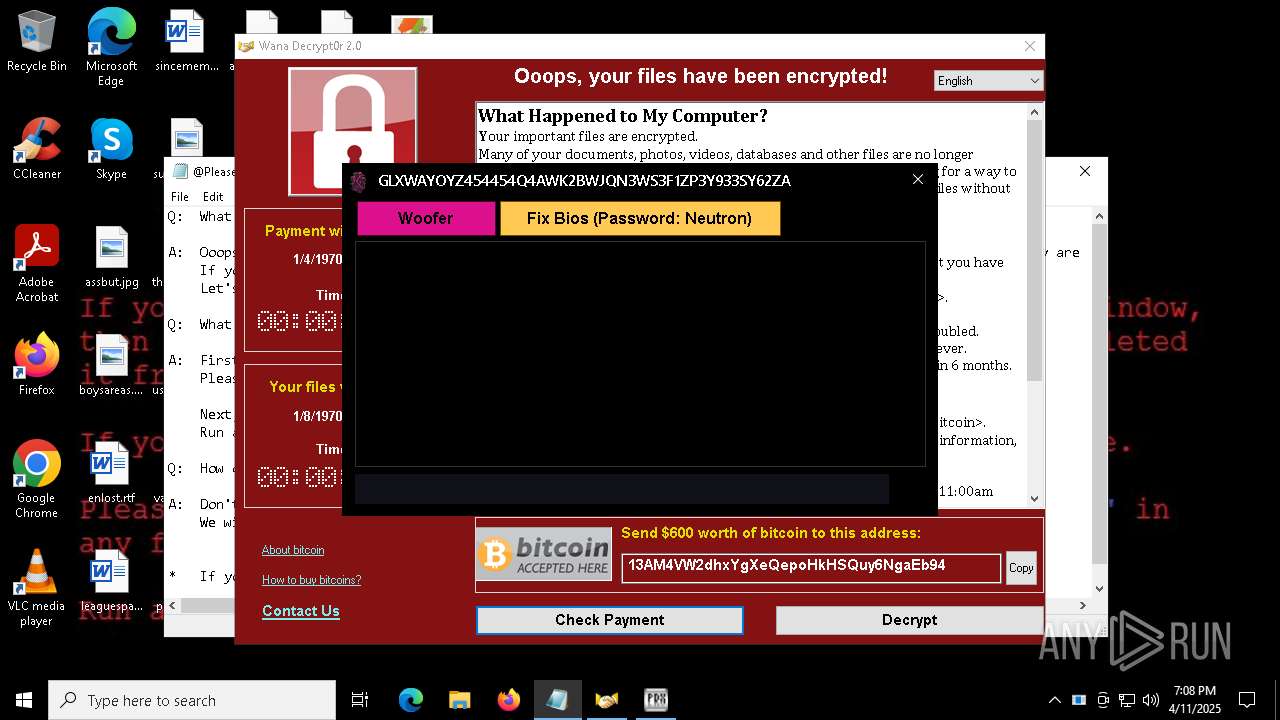
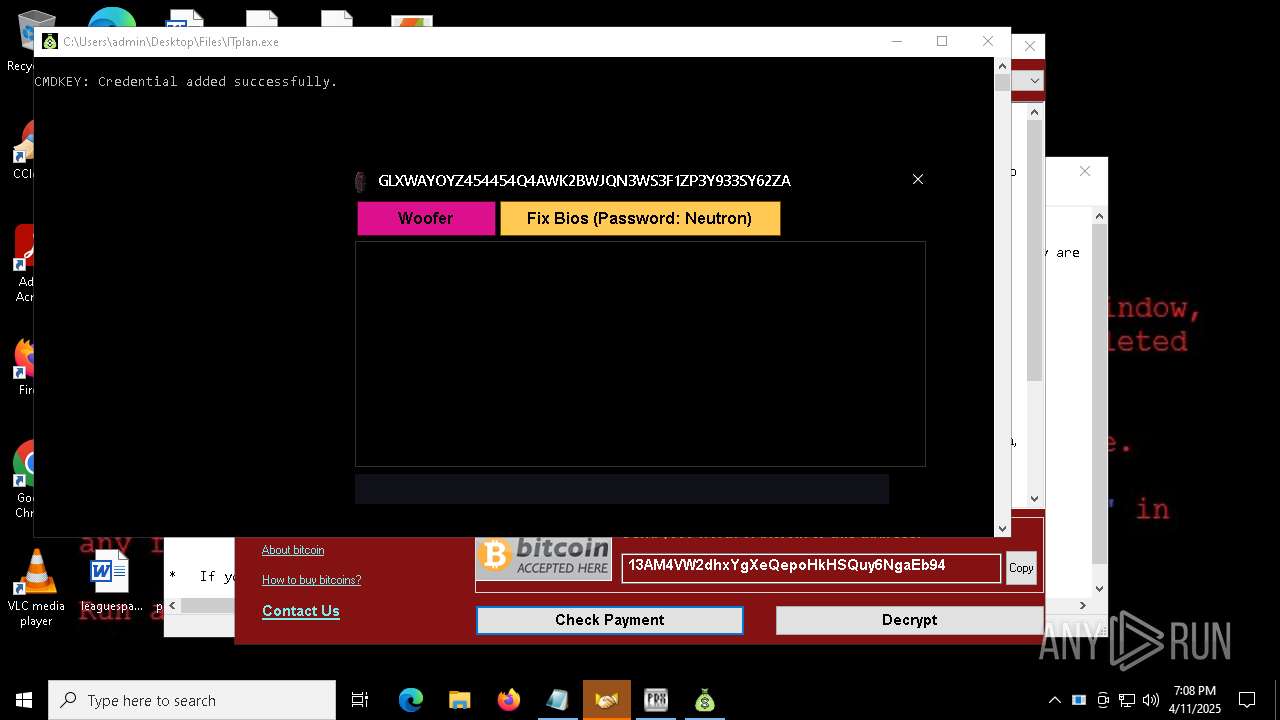
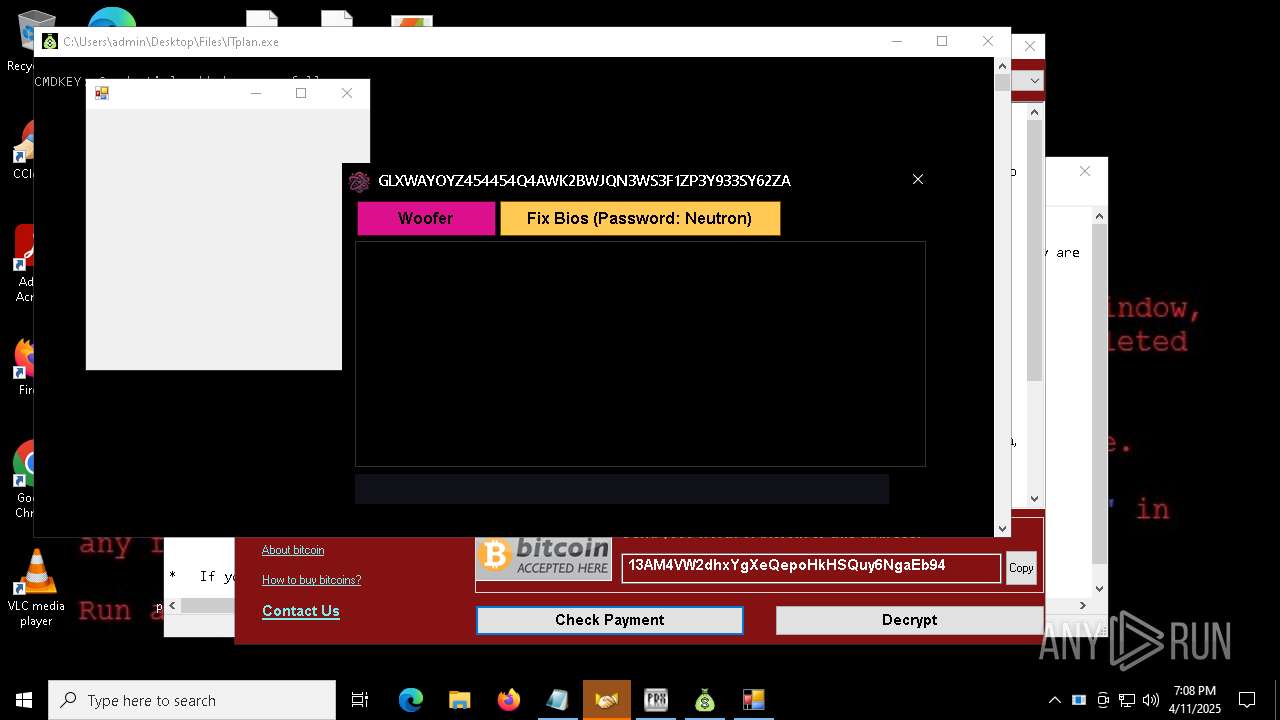
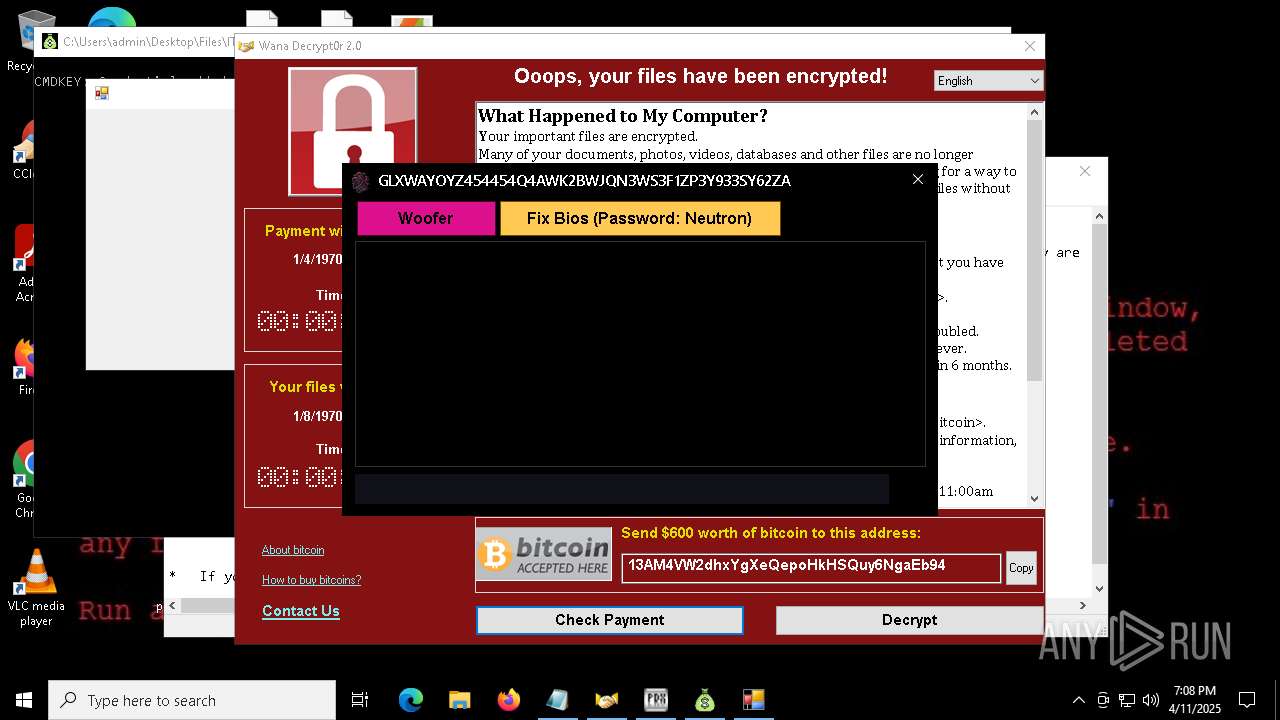
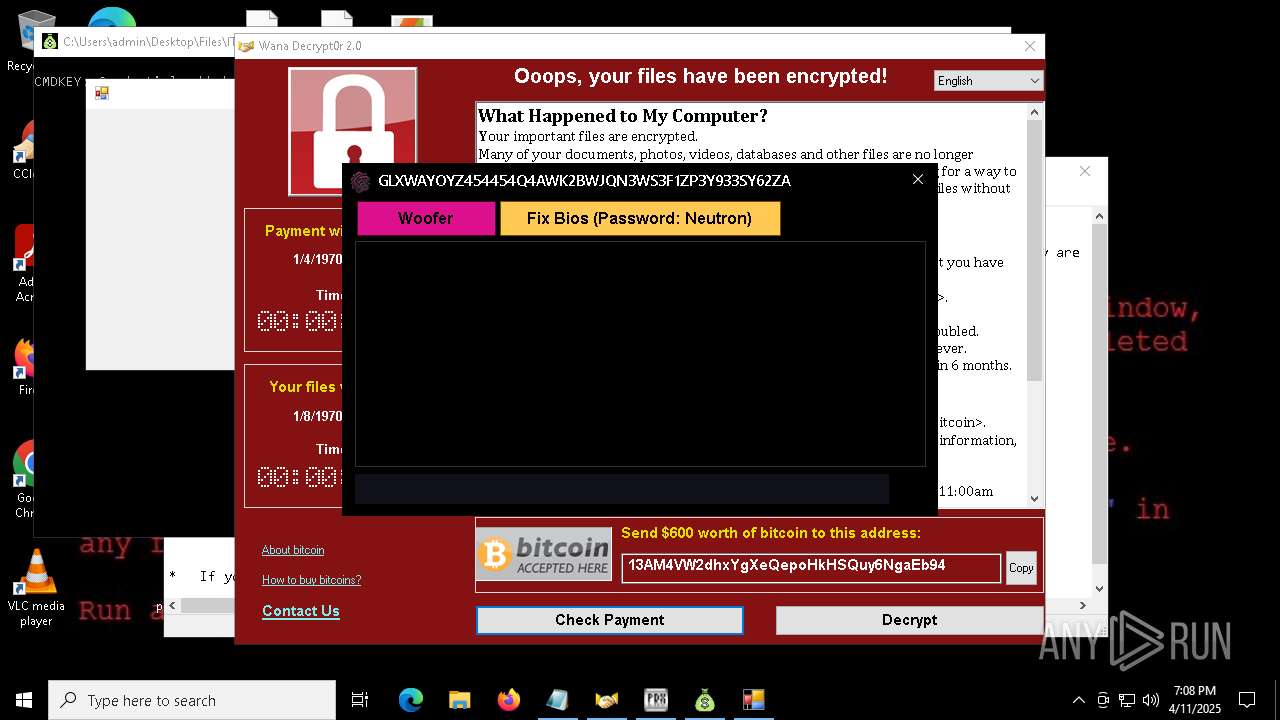
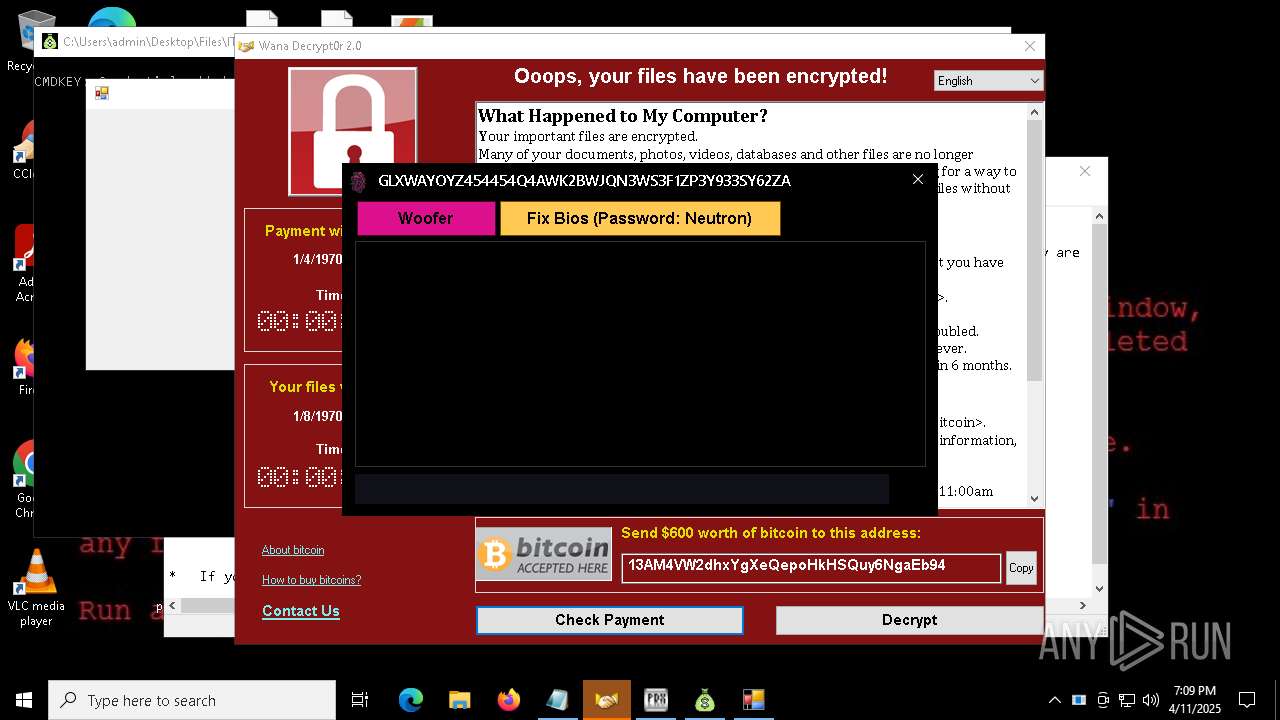
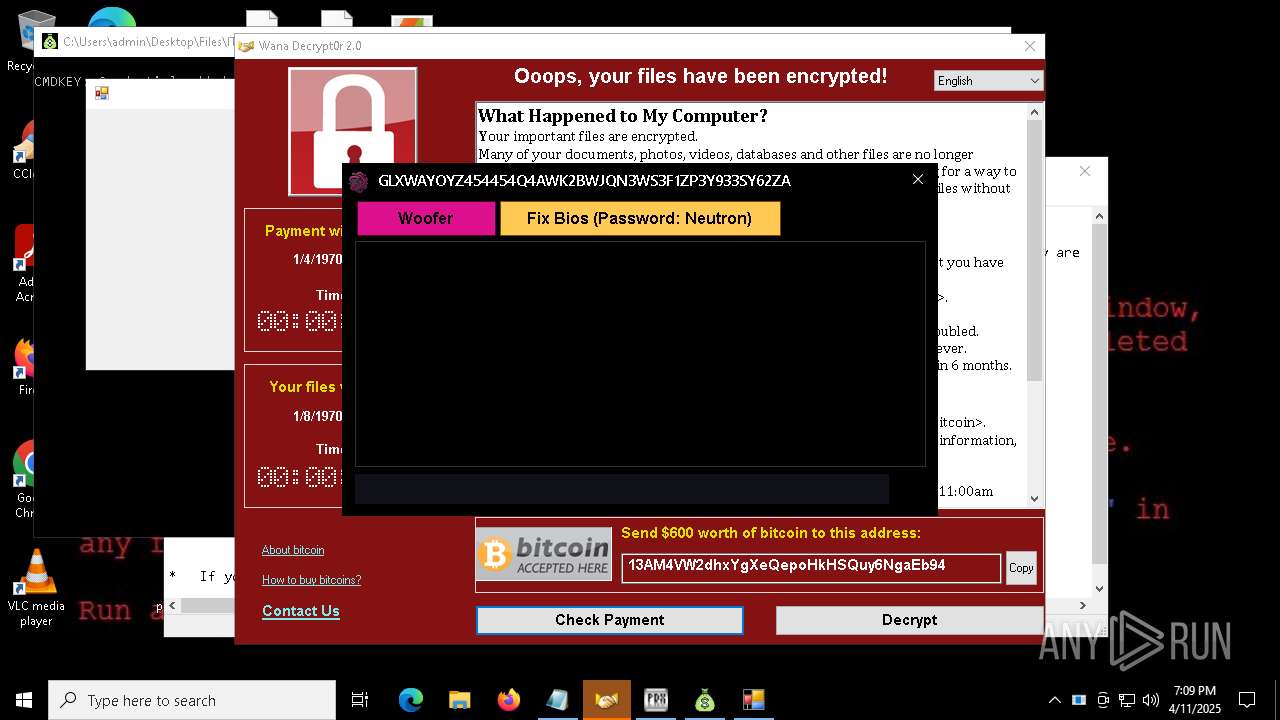
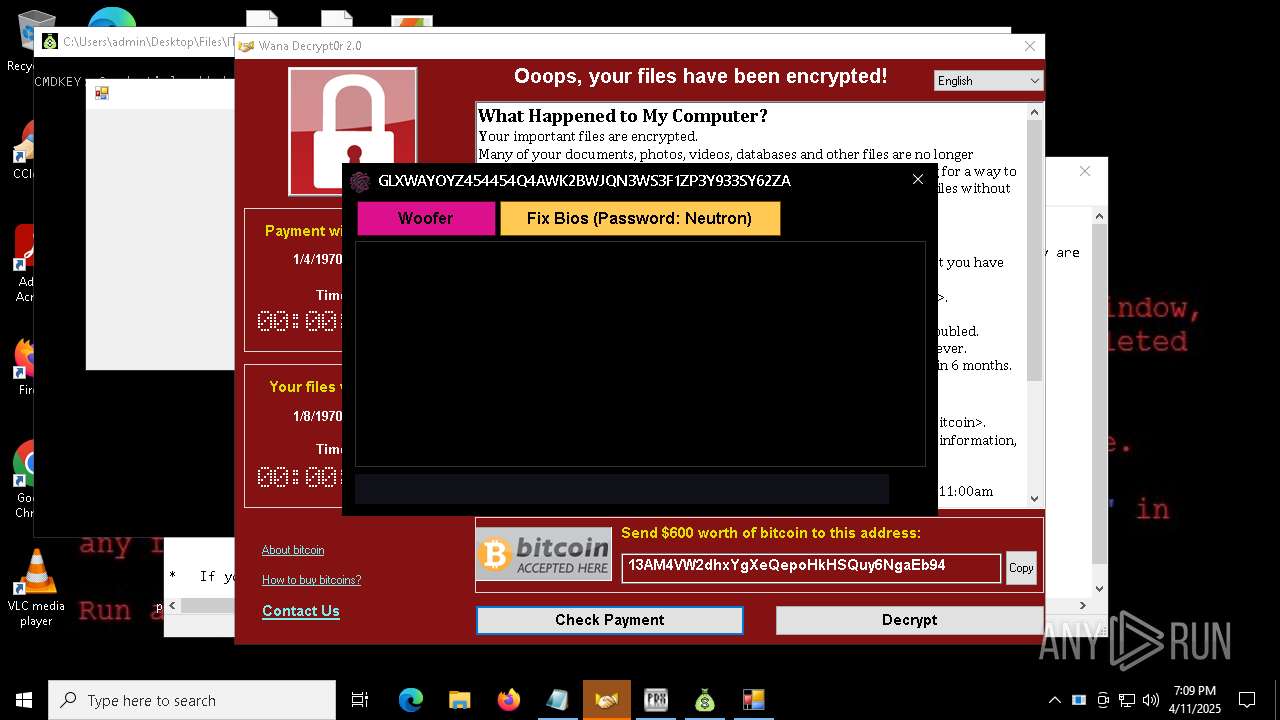
MALICIOUS
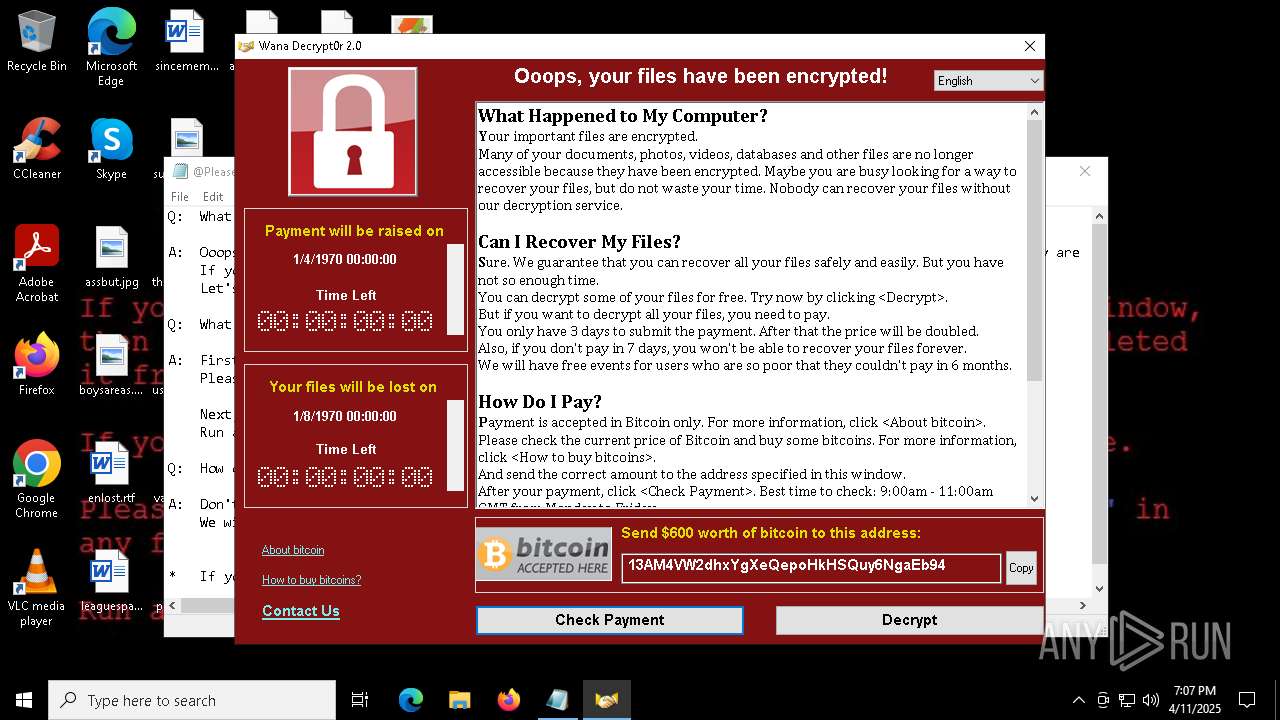
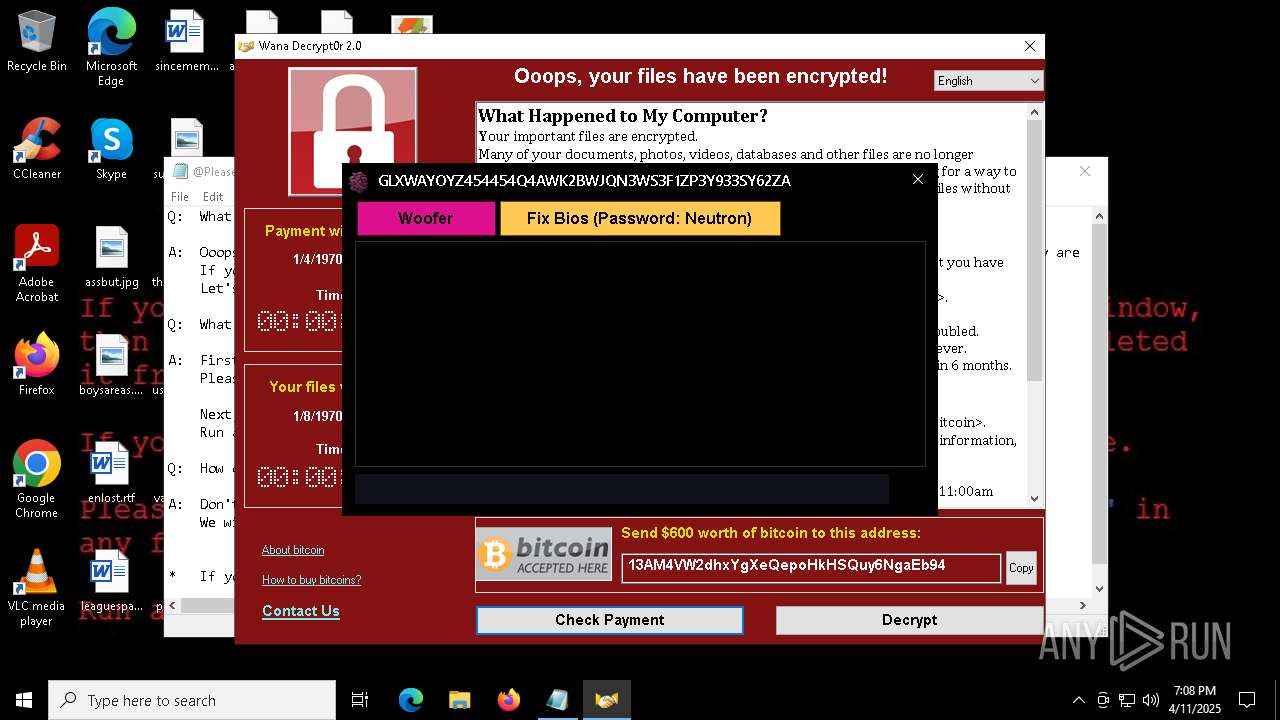
WANNACRY has been detected
- ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe (PID: 7748)
- @WanaDecryptor@.exe (PID: 10192)
WANNACRY mutex has been found
- ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe (PID: 7748)
Actions looks like stealing of personal data
- ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe (PID: 7748)
- icacls.exe (PID: 7872)
- asena.exe (PID: 7360)
- postbox.exe (PID: 11076)
- 4363463463464363463463463.exe (PID: 7324)
- csrss.exe (PID: 5824)
- MSBuild.exe (PID: 7532)
- 2482031186.exe (PID: 6744)
Changes the autorun value in the registry
- explorer.exe (PID: 4980)
- tdrpload.exe (PID: 10556)
- 172721198.exe (PID: 10728)
- rundll32.exe (PID: 10260)
Deletes shadow copies
- asena.exe (PID: 7360)
RANSOMWARE has been detected
- asena.exe (PID: 7360)
- ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe (PID: 7748)
Create files in the Startup directory
- explorer.exe (PID: 4980)
- 16.exe (PID: 7632)
- cmd.exe (PID: 10324)
Connects to the CnC server
- svchost.exe (PID: 5608)
- sysldpsvc.exe (PID: 10864)
- sysldsvp.exe (PID: 11044)
- rundll32.exe (PID: 10260)
- dwm.exe (PID: 9872)
CRYPTOWALL has been detected (SURICATA)
- svchost.exe (PID: 5608)
WANNACRY has been detected (YARA)
- ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe (PID: 7748)
Writes a file to the Word startup folder
- ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe (PID: 7748)
MARSSTEALER has been detected (YARA)
- Cry.exe (PID: 7776)
- a76e49df84ba2a7b33e8ea959995b5e6faecb90d551ef169d8272ce9042c35a5.exe (PID: 7348)
Modifies files in the Chrome extension folder
- ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe (PID: 7748)
Wannacry exe files
- @WanaDecryptor@.exe (PID: 10192)
XWORM has been detected (SURICATA)
- 21.exe (PID: 7552)
- 20.exe (PID: 7468)
- 8.exe (PID: 1096)
- 5.exe (PID: 7812)
- 9.exe (PID: 2420)
HAUSBOMBER has been detected (YARA)
- 4363463463464363463463463.exe (PID: 7324)
COINMINER has been found (auto)
- 4363463463464363463463463.exe (PID: 7324)
- tdrpload.exe (PID: 10556)
QUASARRAT has been found (auto)
- CondoGenerator.exe (PID: 10324)
- 4363463463464363463463463.exe (PID: 7324)
- 4363463463464363463463463.exe (PID: 7324)
- defender64.exe (PID: 11004)
Uses Task Scheduler to autorun other applications
- CondoGenerator.exe (PID: 10324)
- Client.exe (PID: 10652)
- Client.exe (PID: 3968)
- JUSCHED.EXE (PID: 10236)
- jusched.exe (PID: 8468)
- Client.exe (PID: 10556)
- defender64.exe (PID: 11004)
- defenderx64.exe (PID: 10380)
- Client.exe (PID: 3140)
- defenderx64.exe (PID: 7104)
- Client.exe (PID: 9952)
- defenderx64.exe (PID: 11000)
- Client.exe (PID: 4996)
- defenderx64.exe (PID: 5212)
- Client.exe (PID: 7300)
- defenderx64.exe (PID: 9900)
- Client.exe (PID: 8700)
- defenderx64.exe (PID: 10828)
PHORPIEX has been detected (SURICATA)
- sysldpsvc.exe (PID: 10864)
- sysldsvp.exe (PID: 11044)
ARKEI has been detected (YARA)
- a76e49df84ba2a7b33e8ea959995b5e6faecb90d551ef169d8272ce9042c35a5.exe (PID: 7348)
VIDAR has been found (auto)
- 4363463463464363463463463.exe (PID: 7324)
VIDAR mutex has been found
- MSBuild.exe (PID: 7532)
NJRAT has been found (auto)
- njrat.exe (PID: 10372)
- rundll32.exe (PID: 10260)
Steals credentials from Web Browsers
- MSBuild.exe (PID: 7532)
NjRAT is detected
- rundll32.exe (PID: 10260)
NJRAT has been detected (SURICATA)
- rundll32.exe (PID: 10260)
MINER has been found (auto)
- 1107813431.exe (PID: 10384)
- 3120222861.exe (PID: 10588)
Vulnerable driver has been detected
- sysdoruhgsf.exe (PID: 7940)
MINER has been detected (SURICATA)
- dwm.exe (PID: 9872)
SUSPICIOUS
Process drops legitimate windows executable
- pcraper.exe (PID: 7696)
- ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe (PID: 7748)
- 2482031186.exe (PID: 6744)
Reads security settings of Internet Explorer
- pcraper.exe (PID: 7696)
- Cry.exe (PID: 7776)
- Bomb.exe (PID: 7336)
- a76e49df84ba2a7b33e8ea959995b5e6faecb90d551ef169d8272ce9042c35a5.exe (PID: 7348)
- 4363463463464363463463463.exe (PID: 7324)
- Client.exe (PID: 10652)
- sysldpsvc.exe (PID: 10864)
- MSBuild.exe (PID: 7532)
- Client.exe (PID: 3968)
- VidsUsername.exe (PID: 10480)
- npp.exe (PID: 6268)
- CritScript.exe (PID: 2980)
- njrat.exe (PID: 10372)
- sysldsvp.exe (PID: 11044)
- Client.exe (PID: 10556)
- defenderx64.exe (PID: 10380)
- 1107813431.exe (PID: 10384)
- Client.exe (PID: 3140)
- defenderx64.exe (PID: 7104)
- 112331725.exe (PID: 8256)
- Client.exe (PID: 9952)
- defenderx64.exe (PID: 11000)
- Earl.pif (PID: 9896)
- Client.exe (PID: 4996)
- defenderx64.exe (PID: 5212)
- defenderx64.exe (PID: 9900)
- Client.exe (PID: 7300)
- defenderx64.exe (PID: 10828)
- Client.exe (PID: 8700)
Executable content was dropped or overwritten
- pcraper.exe (PID: 7696)
- ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe (PID: 7748)
- explorer.exe (PID: 4980)
- Cry.exe (PID: 7776)
- Bomb.exe (PID: 7336)
- 13.exe (PID: 7232)
- 4363463463464363463463463.exe (PID: 7324)
- CondoGenerator.exe (PID: 10324)
- tdrpload.exe (PID: 10556)
- cmd.exe (PID: 10604)
- npp.exe (PID: 6268)
- 172721198.exe (PID: 10728)
- Earl.pif (PID: 10960)
- JUSCHED.EXE (PID: 10236)
- CritScript.exe (PID: 2980)
- njrat.exe (PID: 10372)
- defender64.exe (PID: 11004)
- rundll32.exe (PID: 10260)
- 1107813431.exe (PID: 10384)
- 3120222861.exe (PID: 10588)
- sysdoruhgsf.exe (PID: 7940)
- 2482031186.exe (PID: 6744)
- asena.exe (PID: 7360)
- 112331725.exe (PID: 8256)
Uses ATTRIB.EXE to modify file attributes
- ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe (PID: 7748)
Uses ICACLS.EXE to modify access control lists
- ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe (PID: 7748)
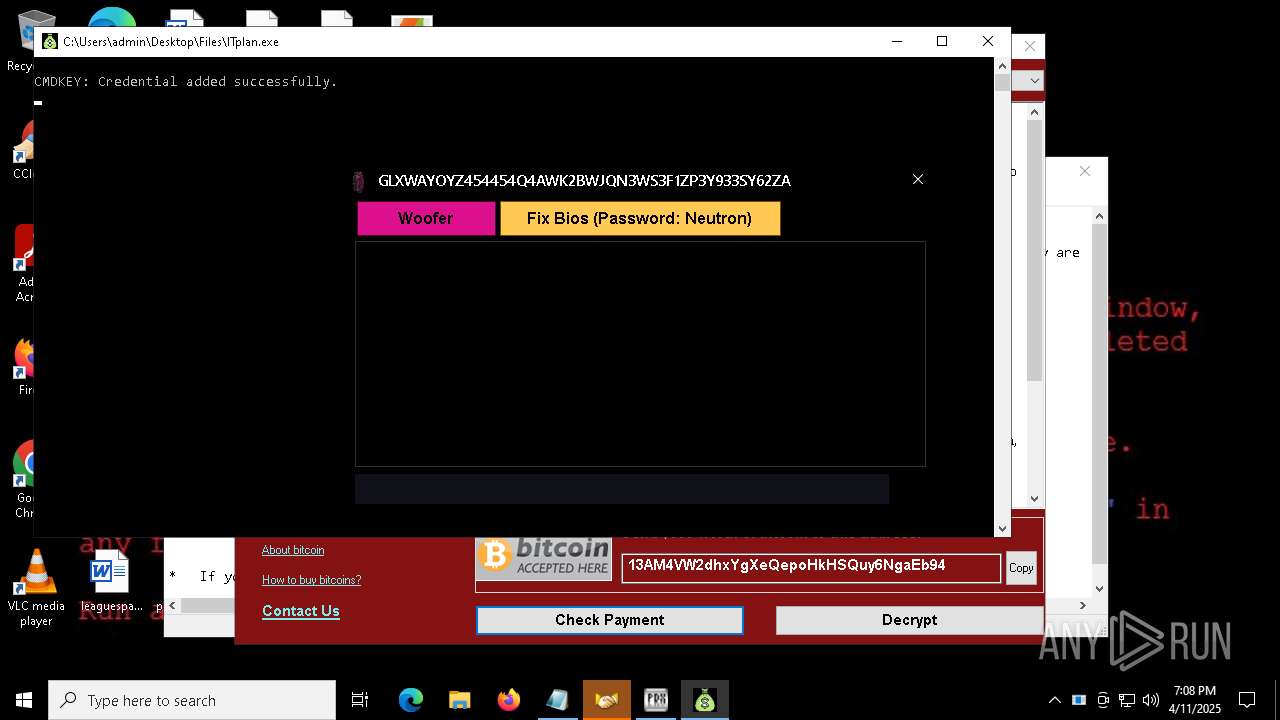
Starts CMD.EXE for commands execution
- ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe (PID: 7748)
- Client.exe (PID: 10652)
- Client.exe (PID: 3968)
- VidsUsername.exe (PID: 10480)
- cmd.exe (PID: 10604)
- ITplan.exe (PID: 10824)
- Client.exe (PID: 10556)
- defenderx64.exe (PID: 10380)
- Client.exe (PID: 3140)
- defenderx64.exe (PID: 7104)
- Client.exe (PID: 9952)
- defenderx64.exe (PID: 11000)
- Client.exe (PID: 4996)
- defenderx64.exe (PID: 5212)
- defenderx64.exe (PID: 9900)
- Client.exe (PID: 7300)
- defenderx64.exe (PID: 10828)
- Client.exe (PID: 8700)
The process executes VB scripts
- cmd.exe (PID: 8076)
Executing commands from a ".bat" file
- ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe (PID: 7748)
- Client.exe (PID: 10652)
- Client.exe (PID: 3968)
- VidsUsername.exe (PID: 10480)
- ITplan.exe (PID: 10824)
- Client.exe (PID: 10556)
- defenderx64.exe (PID: 10380)
- Client.exe (PID: 3140)
- defenderx64.exe (PID: 7104)
- Client.exe (PID: 9952)
- defenderx64.exe (PID: 11000)
- Client.exe (PID: 4996)
- defenderx64.exe (PID: 5212)
- defenderx64.exe (PID: 9900)
- Client.exe (PID: 7300)
- Client.exe (PID: 8700)
- defenderx64.exe (PID: 10828)
Reads the date of Windows installation
- Bomb.exe (PID: 7336)
- Client.exe (PID: 10652)
- Client.exe (PID: 3968)
- Client.exe (PID: 10556)
- defenderx64.exe (PID: 10380)
- Client.exe (PID: 3140)
- defenderx64.exe (PID: 7104)
- Client.exe (PID: 9952)
- defenderx64.exe (PID: 11000)
- Client.exe (PID: 4996)
- defenderx64.exe (PID: 5212)
- Client.exe (PID: 7300)
- defenderx64.exe (PID: 9900)
- defenderx64.exe (PID: 10828)
- Client.exe (PID: 8700)
Checks for external IP
- svchost.exe (PID: 5608)
- svchost.exe (PID: 2196)
- 20.exe (PID: 7468)
- 25.exe (PID: 6488)
- 18.exe (PID: 7492)
- 11.exe (PID: 7688)
- 23.exe (PID: 6044)
- 9.exe (PID: 2420)
- 19.exe (PID: 7452)
- 13.exe (PID: 7232)
- 15.exe (PID: 7540)
- 10.exe (PID: 1388)
- 24.exe (PID: 7176)
- 12.exe (PID: 4756)
- 14.exe (PID: 6148)
- 21.exe (PID: 7552)
- 6.exe (PID: 7772)
- 16.exe (PID: 7632)
- 5.exe (PID: 7812)
- 2.exe (PID: 7864)
- 4.exe (PID: 7712)
- 3.exe (PID: 7736)
- 1.exe (PID: 7860)
- 8.exe (PID: 1096)
- 22.exe (PID: 6156)
- 7.exe (PID: 6752)
- 17.exe (PID: 7528)
The process creates files with name similar to system file names
- pcraper.exe (PID: 7696)
- njrat.exe (PID: 10372)
- rundll32.exe (PID: 10260)
Connects to unusual port
- 9.exe (PID: 2420)
- 17.exe (PID: 7528)
- 16.exe (PID: 7632)
- 14.exe (PID: 6148)
- 12.exe (PID: 4756)
- 22.exe (PID: 6156)
- 8.exe (PID: 1096)
- 10.exe (PID: 1388)
- 6.exe (PID: 7772)
- 24.exe (PID: 7176)
- 25.exe (PID: 6488)
- 19.exe (PID: 7452)
- 18.exe (PID: 7492)
- 23.exe (PID: 6044)
- 20.exe (PID: 7468)
- 3.exe (PID: 7736)
- 21.exe (PID: 7552)
- 1.exe (PID: 7860)
- 15.exe (PID: 7540)
- 4.exe (PID: 7712)
- 11.exe (PID: 7688)
- 5.exe (PID: 7812)
- 13.exe (PID: 7232)
- 2.exe (PID: 7864)
- 7.exe (PID: 6752)
- access.exe (PID: 8284)
- jusched.exe (PID: 8468)
- mstsc.exe (PID: 10792)
- 4363463463464363463463463.exe (PID: 7324)
- rundll32.exe (PID: 10260)
- dwm.exe (PID: 9872)
- sysldpsvc.exe (PID: 10864)
- sysldsvp.exe (PID: 11044)
Contacting a server suspected of hosting an CnC
- 21.exe (PID: 7552)
- 20.exe (PID: 7468)
- 9.exe (PID: 2420)
- 8.exe (PID: 1096)
- 5.exe (PID: 7812)
- sysldpsvc.exe (PID: 10864)
- sysldsvp.exe (PID: 11044)
- rundll32.exe (PID: 10260)
Reads the BIOS version
- pro_protected.exe (PID: 10112)
Process requests binary or script from the Internet
- 4363463463464363463463463.exe (PID: 7324)
- npp.exe (PID: 6268)
- 1107813431.exe (PID: 10384)
- 112331725.exe (PID: 8256)
Potential Corporate Privacy Violation
- 4363463463464363463463463.exe (PID: 7324)
- npp.exe (PID: 6268)
- mstsc.exe (PID: 10792)
- svchost.exe (PID: 2196)
- 1107813431.exe (PID: 10384)
- 112331725.exe (PID: 8256)
- dwm.exe (PID: 9872)
Starts itself from another location
- CondoGenerator.exe (PID: 10324)
- tdrpload.exe (PID: 10556)
- 172721198.exe (PID: 10728)
- JUSCHED.EXE (PID: 10236)
- njrat.exe (PID: 10372)
- defender64.exe (PID: 11004)
Connects to the server without a host name
- 4363463463464363463463463.exe (PID: 7324)
- sysldpsvc.exe (PID: 10864)
- sysldsvp.exe (PID: 11044)
- 1107813431.exe (PID: 10384)
- 112331725.exe (PID: 8256)
Starts application with an unusual extension
- cmd.exe (PID: 10916)
- cmd.exe (PID: 10536)
- cmd.exe (PID: 10604)
- cmd.exe (PID: 11260)
- cmd.exe (PID: 10608)
- cmd.exe (PID: 10676)
- cmd.exe (PID: 10900)
- Earl.pif (PID: 10960)
- cmd.exe (PID: 10304)
- cmd.exe (PID: 10400)
- cmd.exe (PID: 11096)
- cmd.exe (PID: 6828)
- cmd.exe (PID: 11092)
- cmd.exe (PID: 10648)
- cmd.exe (PID: 10368)
- cmd.exe (PID: 8260)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 10916)
- cmd.exe (PID: 10536)
- cmd.exe (PID: 11260)
- cmd.exe (PID: 10608)
- cmd.exe (PID: 10676)
- cmd.exe (PID: 10900)
- cmd.exe (PID: 10304)
- cmd.exe (PID: 10400)
- cmd.exe (PID: 11096)
- cmd.exe (PID: 6828)
- cmd.exe (PID: 10648)
- cmd.exe (PID: 11092)
- cmd.exe (PID: 8260)
- cmd.exe (PID: 10368)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- MSBuild.exe (PID: 7532)
The executable file from the user directory is run by the CMD process
- Client.exe (PID: 3968)
- Earl.pif (PID: 10960)
- Client.exe (PID: 10556)
- Client.exe (PID: 3140)
- defenderx64.exe (PID: 7104)
- Client.exe (PID: 9952)
- defenderx64.exe (PID: 11000)
- Client.exe (PID: 4996)
- defenderx64.exe (PID: 5212)
- defenderx64.exe (PID: 9900)
- Client.exe (PID: 7300)
- Client.exe (PID: 8700)
- defenderx64.exe (PID: 10828)
Application launched itself
- cmd.exe (PID: 10604)
- RegAsm.exe (PID: 10464)
- Earl.pif (PID: 10960)
Get information on the list of running processes
- cmd.exe (PID: 10604)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 10604)
Drops a file with a rarely used extension (PIF)
- cmd.exe (PID: 10604)
Starts the AutoIt3 executable file
- cmd.exe (PID: 10604)
- Earl.pif (PID: 10960)
Searches for installed software
- MSBuild.exe (PID: 7532)
Reads the history of recent RDP connections
- mstsc.exe (PID: 10792)
Uses NETSH.EXE to add a firewall rule or allowed programs
- rundll32.exe (PID: 10260)
Creates file in the systems drive root
- rundll32.exe (PID: 10260)
- 2482031186.exe (PID: 6744)
Windows service management via SC.EXE
- sc.exe (PID: 7524)
- sc.exe (PID: 2772)
Creates a new Windows service
- sc.exe (PID: 7556)
Starts SC.EXE for service management
- 3120222861.exe (PID: 10588)
Executes as Windows Service
- sysdoruhgsf.exe (PID: 7940)
Stops a currently running service
- sc.exe (PID: 5384)
Drops a system driver (possible attempt to evade defenses)
- sysdoruhgsf.exe (PID: 7940)
INFO
Checks supported languages
- pcraper.exe (PID: 7696)
- Cry.exe (PID: 7776)
- tcping.exe (PID: 7784)
- taskdl.exe (PID: 8044)
- ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe (PID: 7748)
- 4363463463464363463463463.exe (PID: 7324)
- a76e49df84ba2a7b33e8ea959995b5e6faecb90d551ef169d8272ce9042c35a5.exe (PID: 7348)
- asena.exe (PID: 7360)
- Bomb.exe (PID: 7336)
- CryptoWall.exe (PID: 5048)
- 25.exe (PID: 6488)
- 24.exe (PID: 7176)
- 23.exe (PID: 6044)
- 22.exe (PID: 6156)
- 21.exe (PID: 7552)
- 20.exe (PID: 7468)
- 19.exe (PID: 7452)
- 18.exe (PID: 7492)
- 17.exe (PID: 7528)
- 16.exe (PID: 7632)
- 15.exe (PID: 7540)
- 13.exe (PID: 7232)
- 14.exe (PID: 6148)
- 12.exe (PID: 4756)
- 11.exe (PID: 7688)
- 10.exe (PID: 1388)
- 9.exe (PID: 2420)
- 8.exe (PID: 1096)
- 7.exe (PID: 6752)
- 6.exe (PID: 7772)
- 5.exe (PID: 7812)
- 1.exe (PID: 7860)
- 3.exe (PID: 7736)
- 2.exe (PID: 7864)
- 4.exe (PID: 7712)
- @WanaDecryptor@.exe (PID: 10192)
- taskdl.exe (PID: 10204)
- pro_protected.exe (PID: 10112)
- npp.exe (PID: 6268)
- tdrpload.exe (PID: 10556)
- CondoGenerator.exe (PID: 10324)
- Client.exe (PID: 10652)
- sysldpsvc.exe (PID: 10864)
- keygen.exe (PID: 10680)
- chcp.com (PID: 10976)
- postbox.exe (PID: 11076)
- crypted.54.exe (PID: 11256)
- MSBuild.exe (PID: 7532)
- access.exe (PID: 8284)
- Client.exe (PID: 3968)
- VidsUsername.exe (PID: 10480)
- njrat.exe (PID: 10372)
- chcp.com (PID: 10516)
- 172721198.exe (PID: 10728)
- Earl.pif (PID: 10960)
- sysldsvp.exe (PID: 11044)
- JUSCHED.EXE (PID: 10236)
- CritScript.exe (PID: 2980)
- RambledMime.exe (PID: 8060)
- jusched.exe (PID: 8468)
- rundll32.exe (PID: 10260)
- RegAsm.exe (PID: 10464)
- ITplan.exe (PID: 10824)
- Client.exe (PID: 10556)
- taskdl.exe (PID: 1132)
- RegAsm.exe (PID: 10812)
- defender64.exe (PID: 11004)
- chcp.com (PID: 668)
- 1107813431.exe (PID: 10384)
- defenderx64.exe (PID: 10380)
- chcp.com (PID: 9580)
- 2482031186.exe (PID: 6744)
- Client.exe (PID: 3140)
- chcp.com (PID: 10668)
- defenderx64.exe (PID: 7104)
- chcp.com (PID: 7188)
- 3120222861.exe (PID: 10588)
- sysdoruhgsf.exe (PID: 7940)
- 112331725.exe (PID: 8256)
- 1958020195.exe (PID: 9968)
- Client.exe (PID: 9952)
- BitLockerToGo.exe (PID: 11028)
- chcp.com (PID: 10340)
- defenderx64.exe (PID: 11000)
- taskdl.exe (PID: 5244)
- Client.exe (PID: 4996)
- chcp.com (PID: 5592)
- Earl.pif (PID: 9896)
- chcp.com (PID: 10316)
- defenderx64.exe (PID: 5212)
- defenderx64.exe (PID: 9900)
- chcp.com (PID: 7364)
- Client.exe (PID: 7300)
- taskdl.exe (PID: 10892)
- defenderx64.exe (PID: 10828)
- Client.exe (PID: 8700)
- chcp.com (PID: 2356)
- chcp.com (PID: 7548)
- chcp.com (PID: 7148)
- chcp.com (PID: 10940)
Creates files or folders in the user directory
- pcraper.exe (PID: 7696)
- ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe (PID: 7748)
- cscript.exe (PID: 8128)
- explorer.exe (PID: 4980)
- 13.exe (PID: 7232)
- 16.exe (PID: 7632)
- CondoGenerator.exe (PID: 10324)
- asena.exe (PID: 7360)
- MSBuild.exe (PID: 7532)
- npp.exe (PID: 6268)
- Earl.pif (PID: 10960)
- JUSCHED.EXE (PID: 10236)
- sysldpsvc.exe (PID: 10864)
- defender64.exe (PID: 11004)
- 1107813431.exe (PID: 10384)
- 2482031186.exe (PID: 6744)
- sysldsvp.exe (PID: 11044)
- 112331725.exe (PID: 8256)
The sample compiled with english language support
- pcraper.exe (PID: 7696)
- ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe (PID: 7748)
- 4363463463464363463463463.exe (PID: 7324)
- Earl.pif (PID: 10960)
- 2482031186.exe (PID: 6744)
Reads the computer name
- pcraper.exe (PID: 7696)
- ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe (PID: 7748)
- Cry.exe (PID: 7776)
- asena.exe (PID: 7360)
- Bomb.exe (PID: 7336)
- 4363463463464363463463463.exe (PID: 7324)
- 24.exe (PID: 7176)
- 25.exe (PID: 6488)
- 23.exe (PID: 6044)
- 22.exe (PID: 6156)
- 20.exe (PID: 7468)
- 18.exe (PID: 7492)
- 19.exe (PID: 7452)
- 17.exe (PID: 7528)
- 16.exe (PID: 7632)
- 21.exe (PID: 7552)
- 14.exe (PID: 6148)
- 13.exe (PID: 7232)
- 15.exe (PID: 7540)
- 10.exe (PID: 1388)
- 12.exe (PID: 4756)
- 11.exe (PID: 7688)
- 9.exe (PID: 2420)
- 8.exe (PID: 1096)
- 7.exe (PID: 6752)
- 6.exe (PID: 7772)
- 5.exe (PID: 7812)
- 2.exe (PID: 7864)
- 4.exe (PID: 7712)
- 3.exe (PID: 7736)
- 1.exe (PID: 7860)
- a76e49df84ba2a7b33e8ea959995b5e6faecb90d551ef169d8272ce9042c35a5.exe (PID: 7348)
- @WanaDecryptor@.exe (PID: 10192)
- pro_protected.exe (PID: 10112)
- CondoGenerator.exe (PID: 10324)
- keygen.exe (PID: 10680)
- Client.exe (PID: 10652)
- sysldpsvc.exe (PID: 10864)
- postbox.exe (PID: 11076)
- MSBuild.exe (PID: 7532)
- Client.exe (PID: 3968)
- VidsUsername.exe (PID: 10480)
- npp.exe (PID: 6268)
- Earl.pif (PID: 10960)
- JUSCHED.EXE (PID: 10236)
- CritScript.exe (PID: 2980)
- jusched.exe (PID: 8468)
- njrat.exe (PID: 10372)
- RegAsm.exe (PID: 10464)
- sysldsvp.exe (PID: 11044)
- Client.exe (PID: 10556)
- RegAsm.exe (PID: 10812)
- defender64.exe (PID: 11004)
- defenderx64.exe (PID: 10380)
- rundll32.exe (PID: 10260)
- 1107813431.exe (PID: 10384)
- Client.exe (PID: 3140)
- defenderx64.exe (PID: 7104)
- Client.exe (PID: 9952)
- 112331725.exe (PID: 8256)
- BitLockerToGo.exe (PID: 11028)
- defenderx64.exe (PID: 11000)
- Earl.pif (PID: 9896)
- Client.exe (PID: 4996)
- defenderx64.exe (PID: 5212)
- Client.exe (PID: 7300)
- defenderx64.exe (PID: 9900)
- defenderx64.exe (PID: 10828)
- Client.exe (PID: 8700)
Process checks computer location settings
- pcraper.exe (PID: 7696)
- Cry.exe (PID: 7776)
- Bomb.exe (PID: 7336)
- 4363463463464363463463463.exe (PID: 7324)
- Client.exe (PID: 10652)
- Client.exe (PID: 3968)
- VidsUsername.exe (PID: 10480)
- CritScript.exe (PID: 2980)
- njrat.exe (PID: 10372)
- Client.exe (PID: 10556)
- defenderx64.exe (PID: 10380)
- Client.exe (PID: 3140)
- defenderx64.exe (PID: 7104)
- Client.exe (PID: 9952)
- defenderx64.exe (PID: 11000)
- Client.exe (PID: 4996)
- defenderx64.exe (PID: 5212)
- defenderx64.exe (PID: 9900)
- Client.exe (PID: 7300)
- Client.exe (PID: 8700)
- defenderx64.exe (PID: 10828)
Reads the machine GUID from the registry
- ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe (PID: 7748)
- Cry.exe (PID: 7776)
- asena.exe (PID: 7360)
- CryptoWall.exe (PID: 5048)
- Bomb.exe (PID: 7336)
- 24.exe (PID: 7176)
- 23.exe (PID: 6044)
- 21.exe (PID: 7552)
- 20.exe (PID: 7468)
- 19.exe (PID: 7452)
- 17.exe (PID: 7528)
- 22.exe (PID: 6156)
- 15.exe (PID: 7540)
- 14.exe (PID: 6148)
- 16.exe (PID: 7632)
- 12.exe (PID: 4756)
- 11.exe (PID: 7688)
- 10.exe (PID: 1388)
- 9.exe (PID: 2420)
- 8.exe (PID: 1096)
- 7.exe (PID: 6752)
- 6.exe (PID: 7772)
- 4.exe (PID: 7712)
- 4363463463464363463463463.exe (PID: 7324)
- 13.exe (PID: 7232)
- 25.exe (PID: 6488)
- 18.exe (PID: 7492)
- 5.exe (PID: 7812)
- 2.exe (PID: 7864)
- 1.exe (PID: 7860)
- 3.exe (PID: 7736)
- pro_protected.exe (PID: 10112)
- CondoGenerator.exe (PID: 10324)
- Client.exe (PID: 10652)
- Client.exe (PID: 3968)
- MSBuild.exe (PID: 7532)
- JUSCHED.EXE (PID: 10236)
- jusched.exe (PID: 8468)
- RegAsm.exe (PID: 10464)
- Client.exe (PID: 10556)
- defender64.exe (PID: 11004)
- RegAsm.exe (PID: 10812)
- defenderx64.exe (PID: 10380)
- rundll32.exe (PID: 10260)
- Client.exe (PID: 3140)
- defenderx64.exe (PID: 7104)
- BitLockerToGo.exe (PID: 11028)
- Client.exe (PID: 9952)
- defenderx64.exe (PID: 11000)
- sysldpsvc.exe (PID: 10864)
- Earl.pif (PID: 9896)
- Client.exe (PID: 4996)
- defenderx64.exe (PID: 5212)
- sysldsvp.exe (PID: 11044)
- Client.exe (PID: 7300)
- defenderx64.exe (PID: 9900)
- Client.exe (PID: 8700)
- defenderx64.exe (PID: 10828)
Reads security settings of Internet Explorer
- cscript.exe (PID: 8128)
- WMIC.exe (PID: 7220)
- svchost.exe (PID: 5608)
- notepad.exe (PID: 10164)
- mstsc.exe (PID: 10792)
Create files in a temporary directory
- Cry.exe (PID: 7776)
- Bomb.exe (PID: 7336)
- Client.exe (PID: 10652)
- VidsUsername.exe (PID: 10480)
- Client.exe (PID: 3968)
- npp.exe (PID: 6268)
- ITplan.exe (PID: 10824)
- sysldpsvc.exe (PID: 10864)
- Client.exe (PID: 10556)
- defenderx64.exe (PID: 10380)
- 1107813431.exe (PID: 10384)
- Client.exe (PID: 3140)
- defenderx64.exe (PID: 7104)
- sysldsvp.exe (PID: 11044)
- 112331725.exe (PID: 8256)
- Client.exe (PID: 9952)
- defenderx64.exe (PID: 11000)
- Client.exe (PID: 4996)
- defenderx64.exe (PID: 5212)
- Client.exe (PID: 7300)
- defenderx64.exe (PID: 9900)
- defenderx64.exe (PID: 10828)
- CritScript.exe (PID: 2980)
Reads Environment values
- asena.exe (PID: 7360)
- 8.exe (PID: 1096)
- 18.exe (PID: 7492)
- 24.exe (PID: 7176)
- 14.exe (PID: 6148)
- 9.exe (PID: 2420)
- 17.exe (PID: 7528)
- 23.exe (PID: 6044)
- 22.exe (PID: 6156)
- 16.exe (PID: 7632)
- 11.exe (PID: 7688)
- 7.exe (PID: 6752)
- 13.exe (PID: 7232)
- 12.exe (PID: 4756)
- 10.exe (PID: 1388)
- 25.exe (PID: 6488)
- 21.exe (PID: 7552)
- 15.exe (PID: 7540)
- 19.exe (PID: 7452)
- 20.exe (PID: 7468)
- 6.exe (PID: 7772)
- 2.exe (PID: 7864)
- 4.exe (PID: 7712)
- 3.exe (PID: 7736)
- 5.exe (PID: 7812)
- 1.exe (PID: 7860)
- CondoGenerator.exe (PID: 10324)
- Client.exe (PID: 10652)
- Client.exe (PID: 3968)
- MSBuild.exe (PID: 7532)
- JUSCHED.EXE (PID: 10236)
- jusched.exe (PID: 8468)
- Client.exe (PID: 10556)
- defender64.exe (PID: 11004)
- defenderx64.exe (PID: 10380)
- Client.exe (PID: 3140)
- defenderx64.exe (PID: 7104)
- Client.exe (PID: 9952)
- defenderx64.exe (PID: 11000)
- Client.exe (PID: 4996)
- defenderx64.exe (PID: 5212)
- Client.exe (PID: 7300)
- defenderx64.exe (PID: 9900)
- defenderx64.exe (PID: 10828)
- Client.exe (PID: 8700)
Reads product name
- asena.exe (PID: 7360)
- MSBuild.exe (PID: 7532)
Checks proxy server information
- svchost.exe (PID: 5608)
- 4363463463464363463463463.exe (PID: 7324)
- 7.exe (PID: 6752)
- 14.exe (PID: 6148)
- 25.exe (PID: 6488)
- 13.exe (PID: 7232)
- 24.exe (PID: 7176)
- 18.exe (PID: 7492)
- 21.exe (PID: 7552)
- 10.exe (PID: 1388)
- 8.exe (PID: 1096)
- 23.exe (PID: 6044)
- 15.exe (PID: 7540)
- 16.exe (PID: 7632)
- 20.exe (PID: 7468)
- 11.exe (PID: 7688)
- 9.exe (PID: 2420)
- 12.exe (PID: 4756)
- 17.exe (PID: 7528)
- 22.exe (PID: 6156)
- 2.exe (PID: 7864)
- 6.exe (PID: 7772)
- 4.exe (PID: 7712)
- 19.exe (PID: 7452)
- 5.exe (PID: 7812)
- 1.exe (PID: 7860)
- 3.exe (PID: 7736)
- a76e49df84ba2a7b33e8ea959995b5e6faecb90d551ef169d8272ce9042c35a5.exe (PID: 7348)
- sysldpsvc.exe (PID: 10864)
- MSBuild.exe (PID: 7532)
- npp.exe (PID: 6268)
- sysldsvp.exe (PID: 11044)
- 1107813431.exe (PID: 10384)
- 112331725.exe (PID: 8256)
- Earl.pif (PID: 9896)
- slui.exe (PID: 10448)
Disables trace logs
- 4363463463464363463463463.exe (PID: 7324)
- 17.exe (PID: 7528)
- 24.exe (PID: 7176)
- 14.exe (PID: 6148)
- 18.exe (PID: 7492)
- 11.exe (PID: 7688)
- 7.exe (PID: 6752)
- 23.exe (PID: 6044)
- 15.exe (PID: 7540)
- 12.exe (PID: 4756)
- 10.exe (PID: 1388)
- 16.exe (PID: 7632)
- 13.exe (PID: 7232)
- 9.exe (PID: 2420)
- 19.exe (PID: 7452)
- 22.exe (PID: 6156)
- 21.exe (PID: 7552)
- 25.exe (PID: 6488)
- 20.exe (PID: 7468)
- 8.exe (PID: 1096)
- 2.exe (PID: 7864)
- 6.exe (PID: 7772)
- 4.exe (PID: 7712)
- 3.exe (PID: 7736)
- 5.exe (PID: 7812)
- 1.exe (PID: 7860)
Reads the software policy settings
- 4363463463464363463463463.exe (PID: 7324)
- MSBuild.exe (PID: 7532)
- BitLockerToGo.exe (PID: 11028)
- Earl.pif (PID: 9896)
- slui.exe (PID: 10448)
Manual execution by a user
- notepad.exe (PID: 10164)
- @WanaDecryptor@.exe (PID: 10192)
- OpenWith.exe (PID: 8684)
- OpenWith.exe (PID: 5740)
- OpenWith.exe (PID: 9796)
- OpenWith.exe (PID: 9808)
- OpenWith.exe (PID: 10248)
- OpenWith.exe (PID: 10332)
- OpenWith.exe (PID: 10408)
- OpenWith.exe (PID: 10488)
- cmd.exe (PID: 10324)
Creates files in the program directory
- ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe (PID: 7748)
- MSBuild.exe (PID: 7532)
- 3120222861.exe (PID: 10588)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 9796)
- OpenWith.exe (PID: 8684)
- OpenWith.exe (PID: 9808)
- OpenWith.exe (PID: 5740)
- OpenWith.exe (PID: 10332)
- OpenWith.exe (PID: 10488)
- OpenWith.exe (PID: 10248)
- OpenWith.exe (PID: 10408)
- OpenWith.exe (PID: 1324)
Process checks whether UAC notifications are on
- pro_protected.exe (PID: 10112)
Changes the display of characters in the console
- cmd.exe (PID: 10916)
- cmd.exe (PID: 10536)
- cmd.exe (PID: 11260)
- cmd.exe (PID: 10608)
- cmd.exe (PID: 10676)
- cmd.exe (PID: 10900)
- cmd.exe (PID: 10304)
- cmd.exe (PID: 10400)
- cmd.exe (PID: 11096)
- cmd.exe (PID: 6828)
- cmd.exe (PID: 11092)
- cmd.exe (PID: 10648)
- cmd.exe (PID: 10368)
- cmd.exe (PID: 8260)
Creates a new folder
- cmd.exe (PID: 10800)
Reads CPU info
- MSBuild.exe (PID: 7532)
Reads mouse settings
- Earl.pif (PID: 10960)
The sample compiled with japanese language support
- sysdoruhgsf.exe (PID: 7940)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Arkei
(PID) Process(7348) a76e49df84ba2a7b33e8ea959995b5e6faecb90d551ef169d8272ce9042c35a5.exe
C2 (1)http://kenesrakishev.net/wp-admin/admin-ajax.php
Strings (618)LoadLibraryA
GetProcAddress
ExitProcess
advapi32.dll
crypt32.dll
GetTickCount
Sleep
GetUserDefaultLangID
CreateMutexA
GetLastError
HeapAlloc
GetProcessHeap
GetComputerNameA
VirtualProtect
GetCurrentProcess
VirtualAllocExNuma
GetUserNameA
CryptStringToBinaryA
HAL9TH
JohnDoe
21/04/2022 20:00:00
http://
Default
%hu/%hu/%hu %hu:%hu:%hu
open
sqlite3.dll
C:\ProgramData\sqlite3.dll
freebl3.dll
C:\ProgramData\freebl3.dll
mozglue.dll
C:\ProgramData\mozglue.dll
msvcp140.dll
C:\ProgramData\msvcp140.dll
nss3.dll
C:\ProgramData\nss3.dll
softokn3.dll
C:\ProgramData\softokn3.dll
vcruntime140.dll
C:\ProgramData\vcruntime140.dll
.zip
Tag:
IP: IP?
Country: Country?
Working Path:
Local Time:
TimeZone:
Display Language:
Keyboard Languages:
Is Laptop:
Processor:
Installed RAM:
OS:
(
Bit)
Videocard:
Display Resolution:
PC name:
User name:
Domain name:
MachineID:
GUID:
Installed Software:
system.txt
Grabber\%s.zip
%APPDATA%
%LOCALAPPDATA%
%USERPROFILE%
%DESKTOP%
Wallets\
Ethereum
\Ethereum\
keystore
Electrum
\Electrum\wallets\
*.*
ElectrumLTC
\Electrum-LTC\wallets\
Exodus
\Exodus\
exodus.conf.json
window-state.json
\Exodus\exodus.wallet\
passphrase.json
seed.seco
info.seco
ElectronCash
\ElectronCash\wallets\
default_wallet
MultiDoge
\MultiDoge\
multidoge.wallet
JAXX
\jaxx\Local Storage\
file__0.localstorage
Atomic
\atomic\Local Storage\leveldb\
000003.log
CURRENT
LOCK
LOG
MANIFEST-000001
0000*
Binance
\Binance\
app-store.json
Coinomi
\Coinomi\Coinomi\wallets\
*.wallet
*.config
*wallet*.dat
GetSystemTime
lstrcatA
SystemTimeToFileTime
ntdll.dll
sscanf
memset
memcpy
wininet.dll
user32.dll
gdi32.dll
netapi32.dll
psapi.dll
bcrypt.dll
vaultcli.dll
shlwapi.dll
shell32.dll
gdiplus.dll
ole32.dll
dbghelp.dll
CreateFileA
WriteFile
CloseHandle
GetFileSize
lstrlenA
LocalAlloc
GlobalFree
ReadFile
OpenProcess
SetFilePointer
SetEndOfFile
GetCurrentProcessId
GetLocalTime
GetTimeZoneInformation
GetUserDefaultLocaleName
LocalFree
GetSystemPowerStatus
GetSystemInfo
GlobalMemoryStatusEx
IsWow64Process
GetTempPathA
GetLocaleInfoA
GetFileSizeEx
GetFileAttributesA
FindFirstFileA
FindNextFileA
FindClose
GetCurrentDirectoryA
CopyFileA
DeleteFileA
lstrcmpW
GlobalAlloc
FreeLibrary
SetCurrentDirectoryA
CreateFileMappingA
MapViewOfFile
UnmapViewOfFile
FileTimeToSystemTime
GetFileInformationByHandle
GlobalLock
GlobalSize
WideCharToMultiByte
GetWindowsDirectoryA
GetVolumeInformationA
GetVersionExA
GetModuleFileNameA
CreateFileW
CreateFileMappingW
MultiByteToWideChar
CreateThread
GetEnvironmentVariableA
SetEnvironmentVariableA
lstrcpyA
lstrcpynA
InternetOpenA
InternetConnectA
HttpOpenRequestA
HttpSendRequestA
HttpQueryInfoA
InternetCloseHandle
InternetReadFile
InternetSetOptionA
InternetOpenUrlA
InternetCrackUrlA
wsprintfA
CharToOemW
GetKeyboardLayoutList
EnumDisplayDevicesA
ReleaseDC
GetDC
GetSystemMetrics
GetDesktopWindow
GetWindowRect
GetWindowDC
CloseWindow
RegOpenKeyExA
RegQueryValueExA
RegCloseKey
GetCurrentHwProfileA
RegEnumKeyExA
RegGetValueA
CreateDCA
GetDeviceCaps
CreateCompatibleDC
CreateCompatibleBitmap
SelectObject
BitBlt
DeleteObject
StretchBlt
GetObjectW
GetDIBits
SaveDC
CreateDIBSection
DeleteDC
RestoreDC
DsRoleGetPrimaryDomainInformation
GetModuleFileNameExA
CryptUnprotectData
BCryptCloseAlgorithmProvider
BCryptDestroyKey
BCryptOpenAlgorithmProvider
BCryptSetProperty
BCryptGenerateSymmetricKey
BCryptDecrypt
VaultOpenVault
VaultCloseVault
VaultEnumerateItems
VaultGetItemWin8
VaultGetItemWin7
VaultFree
StrCmpCA
StrStrA
PathMatchSpecA
SHGetFolderPathA
ShellExecuteExA
GdipGetImageEncodersSize
GdipGetImageEncoders
GdipCreateBitmapFromHBITMAP
GdiplusStartup
GdiplusShutdown
GdipSaveImageToStream
GdipDisposeImage
GdipFree
CreateStreamOnHGlobal
GetHGlobalFromStream
SymMatchString
HEAD
HTTP/1.1
GET
POST
file
Content-Type: multipart/form-data; boundary=----
Content-Disposition: form-data; name="
Content-Disposition: form-data; name="file"; filename="
Content-Type: application/octet-stream
Content-Transfer-Encoding: binary
SOFT:
PROF: ?
PROF:
HOST:
USER:
PASS:
sqlite3_open
sqlite3_prepare_v2
sqlite3_step
sqlite3_column_text
sqlite3_finalize
sqlite3_close
sqlite3_column_bytes
sqlite3_column_blob
encrypted_key
"}
PATH
PATH=
NSS_Init
NSS_Shutdown
PK11_GetInternalKeySlot
PK11_FreeSlot
PK11_Authenticate
PK11SDR_Decrypt
SELECT origin_url, username_value, password_value FROM logins
Cookies\%s_%s.txt
SELECT HOST_KEY, is_httponly, path, is_secure, (expires_utc/1000000)-11644480800, name, encrypted_value from cookies
TRUE
FALSE
Autofill\%s_%s.txt
SELECT name, value FROM autofill
CC\%s_%s.txt
SELECT name_on_card, expiration_month, expiration_year, card_number_encrypted FROM credit_cards
Card number:
Name on card:
Expiration date:
History\%s_%s.txt
SELECT url FROM urls
Downloads\%s_%s.txt
SELECT target_path, tab_url from downloads
Login Data
Cookies
Web Data
History
SELECT host, isHttpOnly, path, isSecure, expiry, name, value FROM moz_cookies
logins.json
formSubmitURL
usernameField
encryptedUsername
encryptedPassword
guid
SELECT fieldname, value FROM moz_formhistory
SELECT url FROM moz_places
cookies.sqlite
formhistory.sqlite
places.sqlite
\Local State
..\profiles.ini
C:\ProgramData\
Chrome
\Google\Chrome\User Data
ChromeBeta
\Google\Chrome Beta\User Data
ChromeCanary
\Google\Chrome SxS\User Data
Chromium
\Chromium\User Data
Edge_Chromium
\Microsoft\Edge\User Data
Kometa
\Kometa\User Data
Amigo
\Amigo\User Data
Torch
\Torch\User Data
Orbitum
\Orbitum\User Data
Comodo
\Comodo\Dragon\User Data
Nichrome
\Nichrome\User Data
Maxthon5
\Maxthon5\Users
Sputnik
\Sputnik\User Data
EPB
\Epic Privacy Browser\User Data
Vivaldi
\Vivaldi\User Data
CocCoc
\CocCoc\Browser\User Data
Uran
\uCozMedia\Uran\User Data
QIP
\QIP Surf\User Data
Cent
\CentBrowser\User Data
Elements
\Elements Browser\User Data
TorBro
\TorBro\Profile
CryptoTab
\CryptoTab Browser\User Data
Brave
\BraveSoftware\Brave-Browser\User Data
Opera
\Opera Software\Opera Stable\
OperaGX
\Opera Software\Opera GX Stable\
OperaNeon
\Opera Software\Opera Neon\User Data
Firefox
\Mozilla\Firefox\Profiles\
SlimBrowser
\FlashPeak\SlimBrowser\Profiles\
PaleMoon
\Moonchild Productions\Pale Moon\Profiles\
Waterfox
\Waterfox\Profiles\
Cyberfox
\8pecxstudios\Cyberfox\Profiles\
BlackHawk
\NETGATE Technologies\BlackHawk\Profiles\
IceCat
\Mozilla\icecat\Profiles\
KMeleon
\K-Meleon\
Thunderbird
\Thunderbird\Profiles\
passwords.txt
ibnejdfjmmkpcnlpebklmnkoeoihofec
TronLink
nkbihfbeogaeaoehlefnkodbefgpgknn
MetaMask
fhbohimaelbohpjbbldcngcnapndodjp
Binance Chain Wallet
ffnbelfdoeiohenkjibnmadjiehjhajb
Yoroi
jbdaocneiiinmjbjlgalhcelgbejmnid
Nifty Wallet
afbcbjpbpfadlkmhmclhkeeodmamcflc
Math Wallet
hnfanknocfeofbddgcijnmhnfnkdnaad
Coinbase Wallet
hpglfhgfnhbgpjdenjgmdgoeiappafln
Guarda
blnieiiffboillknjnepogjhkgnoapac
EQUAL Wallet
cjelfplplebdjjenllpjcblmjkfcffne
Jaxx Liberty
fihkakfobkmkjojpchpfgcmhfjnmnfpi
BitApp Wallet
kncchdigobghenbbaddojjnnaogfppfj
iWallet
amkmjjmmflddogmhpjloimipbofnfjih
Wombat
nlbmnnijcnlegkjjpcfjclmcfggfefdm
MEW CX
nanjmdknhkinifnkgdcggcfnhdaammmj
GuildWallet
nkddgncdjgjfcddamfgcmfnlhccnimig
Saturn Wallet
fnjhmkhhmkbjkkabndcnnogagogbneec
Ronin Wallet
cphhlgmgameodnhkjdmkpanlelnlohao
NeoLine
nhnkbkgjikgcigadomkphalanndcapjk
Clover Wallet
kpfopkelmapcoipemfendmdcghnegimn
Liquality Wallet
aiifbnbfobpmeekipheeijimdpnlpgpp
Terra Station
dmkamcknogkgcdfhhbddcghachkejeap
Keplr
fhmfendgdocmcbmfikdcogofphimnkno
Sollet
cnmamaachppnkjgnildpdmkaakejnhae
Auro Wallet
jojhfeoedkpkglbfimdfabpdfjaoolaf
Polymesh Wallet
flpiciilemghbmfalicajoolhkkenfel
ICONex
nknhiehlklippafakaeklbeglecifhad
Nabox Wallet
hcflpincpppdclinealmandijcmnkbgn
KHC
ookjlbkiijinhpmnjffcofjonbfbgaoc
Temple
mnfifefkajgofkcjkemidiaecocnkjeh
TezBox
dkdedlpgdmmkkfjabffeganieamfklkm
Cyano Wallet
nlgbhdfgdhgbiamfdfmbikcdghidoadd
Byone
infeboajgfhgbjpjbeppbkgnabfdkdaf
OneKey
cihmoadaighcejopammfbmddcmdekcje
LeafWallet
lodccjjbdhfakaekdiahmedfbieldgik
DAppPlay
ijmpgkjfkbfhoebgogflfebnmejmfbml
BitClip
lkcjlnjfpbikmcmbachjpdbijejflpcm
Steem Keychain
onofpnbbkehpmmoabgpcpmigafmmnjhl
Nash Extension
bcopgchhojmggmffilplmbdicgaihlkp
Hycon Lite Client
klnaejjgbibmhlephnhpmaofohgkpgkd
ZilPay
aeachknmefphepccionboohckonoeemg
Coin98 Wallet
bfnaelmomeimhlpmgjnjophhpkkoljpa
Phantom
hifafgmccdpekplomjjkcfgodnhcellj
Crypto.com
dngmlblcodfobpdpecaadgfbcggfjfnm
Maiar DeFi Wallet
ppdadbejkmjnefldpcdjhnkpbjkikoip
Oasis
hpbgcgmiemanfelegbndmhieiigkackl
MonstaWallet
fcckkdbjnoikooededlapcalpionmalo
MOBOX
jccapkebeeiajkkdemacblkjhhhboiek
Crust Wallet
mgffkfbidihjpoaomajlbgchddlicgpn
Pali Wallet
nphplpgoakhhjchkkhmiggakijnkhfnd
TON Wallet
ldinpeekobnhjjdofggfgjlcehhmanlj
Hiro Wallet
pocmplpaccanhmnllbbkpgfliimjljgo
Slope Wallet
bhhhlbepdkbapadjdnnojkbgioiodbic
Solflare Wallet
pgiaagfkgcbnmiiolekcfmljdagdhlcm
Stargazer Wallet
cgeeodpfagjceefieflmdfphplkenlfk
EVER Wallet
gjkdbeaiifkpoencioahhcilildpjhgh
partisia-wallet
bgjogpoidejdemgoochpnkmdjpocgkha
Ecto Wallet
ifckdpamphokdglkkdomedpdegcjhjdp
ONTO Wallet
agechnindjilpccclelhlbjphbgnobpf
Fractal Wallet
algblmhagnobbnmakepomicmfljlbehg
ADS Wallet
imijjbmbnebfnbmonjeileijahaipglj
Moonlet Wallet
kpjdchaapjheajadlaakiiigcbhoppda
ZEBEDEE
dlcobpjiigpikoobohmabehhmhfoodbb
Argent X StarkNet Wallet
bofddndhbegljegmpmnlbhcejofmjgbn
X-Wallet
mapbhaebnddapnmifbbkgeedkeplgjmf
Biport Wallet
kfdniefadaanbjodldohaedphafoffoh
Typhon Wallet
jaooiolkmfcmloonphpiiogkfckgciom
Twetch Wallet
aijcbedoijmgnlmjeegjaglmepbmpkpi
Leap Wallet
fhfffofbcgbjjojdnpcfompojdjjhdim
Lamden Wallet
agkfnefiabmfpanochlcakggnkdfmmjd
Earth Wallet
lpfcbjknijpeeillifnkikgncikgfhdo
Nami
fecfflganphcinpahcklgahckeohalog
Coin Wallet
ilhaljfiglknggcoegeknjghdgampffk
Beam Web Wallet
dklmlehijiaepdijfnbbhncfpcoeeljf
FShares Wallet
fkhebcilafocjhnlcngogekljmllgdhd
WAGMIswap.io Wallet
laphpbhjhhgigmjoflgcchgodbbclahk
BLUE - Worlds Safest and Simplest Wallet
mkjjflkhdddfjhonakofipfojoepfndk
Unification Web Wallet
jnldfbidonfeldmalbflbmlebbipcnle
Infinity Wallet
ellkdbaphhldpeajbepobaecooaoafpg
Fetch.ai Network Wallet
iokeahhehimjnekafflcihljlcjccdbe
Alby Wallet
omajpeaffjgmlpmhbfdjepdejoemifpe
xBull Wallet
pgojdfajgcjjpjnbpfaelnpnjocakldb
Sugarchain Wallet
pnndplcbkakcplkjnolgbkdgjikjednm
Tronium
fnnegphlobjdpkhecapkijjdkgcjhkib
Harmony
fhilaheimglignddkjgofkcbgekhenbh
Oxygen
cmbagcoinhmacpcgmbiniijboejgiahi
JustLiquidity Wallet
kmmolakhbgdlpkjkcjkebenjheonagdm
AlgoSigner
fnabdmcgpkkjjegokfcnfbpneacddpfh
Goldmint Lite Wallet
bgpipimickeadkjlklgciifhnalhdjhe
GeroWallet
hoighigmnhgkkdaenafgnefkcmipfjon
EO.Finance
nlgnepoeokdfodgjkjiblkadkjbdfmgd
Multi Wallet
nhihjlnjgibefgjhobhcphmnckoogdea
Waves Enterprise Wallet
ehibhohmlpipbaogcknmpmiibbllplph
Bluehelix Wallet
magbanejlegnbcppjljfhnmfmghialkl
Nebulas Wallet
fgkaeeikaoeiiggggbgdcjchmdfmamla
Vtimes
pnlfjmlcjdjgkddecgincndfgegkecke
Crocobit Wallet
bhghoamapcdpbohphigoooaddinpkbai
Authenticator
gaedmjdfmmahhbjefcbgaolhhanlaolb
Authy
oeljdldpnmdbchonielidgobddffflal
EOS Authenticator
ilgcnhelpchnceeipipijaljkblbcobl
GAuth Authenticator
imloifkgjagghnncjkhggdhalmcnfklk
Trezor Password Manager
%s\%s\Local Extension Settings\%s
%s\CURRENT
%s\%s\Sync Extension Settings\%s
%s\%s\IndexedDB\chrome-extension_%s_0.indexeddb.leveldb
Plugins\
HARDWARE\DESCRIPTION\System\CentralProcessor\0
ProcessorNameString
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
x64
x86
DISPLAY
SOFTWARE\Microsoft\Cryptography
MachineGuid
SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall
DisplayName
DisplayVersion
screenshot.jpg
ABCDEFGHIJKLMNOPQRSTUVWXYZ1234567890
/c timeout /t 5 & del /f /q "%s" & exit
C:\Windows\System32\cmd.exe
MarsStealer
(PID) Process(7348) a76e49df84ba2a7b33e8ea959995b5e6faecb90d551ef169d8272ce9042c35a5.exe
C2kenesrakishev.net/wp-admin/admin-ajax.php
Keys
XOR
Base64_Encoded_KeyMzFiZGFlOGIzMWJkYWU4YjgzYzM2NjMxYmRhZThiOAA=
PurposeC2 domain
Base64_Encoded_KeyMzFiZGFlOGI4M2MzNjhiODNjMzZhNmI5ZTQ0NDQ2YQA=
PurposeC2 route
Base64_Encoded_KeyMzFiMzFiMzFiZGFlOGI4M2MzNmE2YjllNDllNDQ2YQA=
PurposeCode encryption
Strings (618)LoadLibraryA
GetProcAddress
ExitProcess
advapi32.dll
crypt32.dll
GetTickCount
Sleep
GetUserDefaultLangID
CreateMutexA
GetLastError
HeapAlloc
GetProcessHeap
GetComputerNameA
VirtualProtect
GetCurrentProcess
VirtualAllocExNuma
GetUserNameA
CryptStringToBinaryA
HAL9TH
JohnDoe
21/04/2022 20:00:00
http://
Default
%hu/%hu/%hu %hu:%hu:%hu
open
sqlite3.dll
C:\ProgramData\sqlite3.dll
freebl3.dll
C:\ProgramData\freebl3.dll
mozglue.dll
C:\ProgramData\mozglue.dll
msvcp140.dll
C:\ProgramData\msvcp140.dll
nss3.dll
C:\ProgramData\nss3.dll
softokn3.dll
C:\ProgramData\softokn3.dll
vcruntime140.dll
C:\ProgramData\vcruntime140.dll
.zip
Tag:
IP: IP?
Country: Country?
Working Path:
Local Time:
TimeZone:
Display Language:
Keyboard Languages:
Is Laptop:
Processor:
Installed RAM:
OS:
(
Bit)
Videocard:
Display Resolution:
PC name:
User name:
Domain name:
MachineID:
GUID:
Installed Software:
system.txt
Grabber\%s.zip
%APPDATA%
%LOCALAPPDATA%
%USERPROFILE%
%DESKTOP%
Wallets\
Ethereum
\Ethereum\
keystore
Electrum
\Electrum\wallets\
*.*
ElectrumLTC
\Electrum-LTC\wallets\
Exodus
\Exodus\
exodus.conf.json
window-state.json
\Exodus\exodus.wallet\
passphrase.json
seed.seco
info.seco
ElectronCash
\ElectronCash\wallets\
default_wallet
MultiDoge
\MultiDoge\
multidoge.wallet
JAXX
\jaxx\Local Storage\
file__0.localstorage
Atomic
\atomic\Local Storage\leveldb\
000003.log
CURRENT
LOCK
LOG
MANIFEST-000001
0000*
Binance
\Binance\
app-store.json
Coinomi
\Coinomi\Coinomi\wallets\
*.wallet
*.config
*wallet*.dat
GetSystemTime
lstrcatA
SystemTimeToFileTime
ntdll.dll
sscanf
memset
memcpy
wininet.dll
user32.dll
gdi32.dll
netapi32.dll
psapi.dll
bcrypt.dll
vaultcli.dll
shlwapi.dll
shell32.dll
gdiplus.dll
ole32.dll
dbghelp.dll
CreateFileA
WriteFile
CloseHandle
GetFileSize
lstrlenA
LocalAlloc
GlobalFree
ReadFile
OpenProcess
SetFilePointer
SetEndOfFile
GetCurrentProcessId
GetLocalTime
GetTimeZoneInformation
GetUserDefaultLocaleName
LocalFree
GetSystemPowerStatus
GetSystemInfo
GlobalMemoryStatusEx
IsWow64Process
GetTempPathA
GetLocaleInfoA
GetFileSizeEx
GetFileAttributesA
FindFirstFileA
FindNextFileA
FindClose
GetCurrentDirectoryA
CopyFileA
DeleteFileA
lstrcmpW
GlobalAlloc
FreeLibrary
SetCurrentDirectoryA
CreateFileMappingA
MapViewOfFile
UnmapViewOfFile
FileTimeToSystemTime
GetFileInformationByHandle
GlobalLock
GlobalSize
WideCharToMultiByte
GetWindowsDirectoryA
GetVolumeInformationA
GetVersionExA
GetModuleFileNameA
CreateFileW
CreateFileMappingW
MultiByteToWideChar
CreateThread
GetEnvironmentVariableA
SetEnvironmentVariableA
lstrcpyA
lstrcpynA
InternetOpenA
InternetConnectA
HttpOpenRequestA
HttpSendRequestA
HttpQueryInfoA
InternetCloseHandle
InternetReadFile
InternetSetOptionA
InternetOpenUrlA
InternetCrackUrlA
wsprintfA
CharToOemW
GetKeyboardLayoutList
EnumDisplayDevicesA
ReleaseDC
GetDC
GetSystemMetrics
GetDesktopWindow
GetWindowRect
GetWindowDC
CloseWindow
RegOpenKeyExA
RegQueryValueExA
RegCloseKey
GetCurrentHwProfileA
RegEnumKeyExA
RegGetValueA
CreateDCA
GetDeviceCaps
CreateCompatibleDC
CreateCompatibleBitmap
SelectObject
BitBlt
DeleteObject
StretchBlt
GetObjectW
GetDIBits
SaveDC
CreateDIBSection
DeleteDC
RestoreDC
DsRoleGetPrimaryDomainInformation
GetModuleFileNameExA
CryptUnprotectData
BCryptCloseAlgorithmProvider
BCryptDestroyKey
BCryptOpenAlgorithmProvider
BCryptSetProperty
BCryptGenerateSymmetricKey
BCryptDecrypt
VaultOpenVault
VaultCloseVault
VaultEnumerateItems
VaultGetItemWin8
VaultGetItemWin7
VaultFree
StrCmpCA
StrStrA
PathMatchSpecA
SHGetFolderPathA
ShellExecuteExA
GdipGetImageEncodersSize
GdipGetImageEncoders
GdipCreateBitmapFromHBITMAP
GdiplusStartup
GdiplusShutdown
GdipSaveImageToStream
GdipDisposeImage
GdipFree
CreateStreamOnHGlobal
GetHGlobalFromStream
SymMatchString
HEAD
HTTP/1.1
GET
POST
file
Content-Type: multipart/form-data; boundary=----
Content-Disposition: form-data; name="
Content-Disposition: form-data; name="file"; filename="
Content-Type: application/octet-stream
Content-Transfer-Encoding: binary
SOFT:
PROF: ?
PROF:
HOST:
USER:
PASS:
sqlite3_open
sqlite3_prepare_v2
sqlite3_step
sqlite3_column_text
sqlite3_finalize
sqlite3_close
sqlite3_column_bytes
sqlite3_column_blob
encrypted_key
"}
PATH
PATH=
NSS_Init
NSS_Shutdown
PK11_GetInternalKeySlot
PK11_FreeSlot
PK11_Authenticate
PK11SDR_Decrypt
SELECT origin_url, username_value, password_value FROM logins
Cookies\%s_%s.txt
SELECT HOST_KEY, is_httponly, path, is_secure, (expires_utc/1000000)-11644480800, name, encrypted_value from cookies
TRUE
FALSE
Autofill\%s_%s.txt
SELECT name, value FROM autofill
CC\%s_%s.txt
SELECT name_on_card, expiration_month, expiration_year, card_number_encrypted FROM credit_cards
Card number:
Name on card:
Expiration date:
History\%s_%s.txt
SELECT url FROM urls
Downloads\%s_%s.txt
SELECT target_path, tab_url from downloads
Login Data
Cookies
Web Data
History
SELECT host, isHttpOnly, path, isSecure, expiry, name, value FROM moz_cookies
logins.json
formSubmitURL
usernameField
encryptedUsername
encryptedPassword
guid
SELECT fieldname, value FROM moz_formhistory
SELECT url FROM moz_places
cookies.sqlite
formhistory.sqlite
places.sqlite
\Local State
..\profiles.ini
C:\ProgramData\
Chrome
\Google\Chrome\User Data
ChromeBeta
\Google\Chrome Beta\User Data
ChromeCanary
\Google\Chrome SxS\User Data
Chromium
\Chromium\User Data
Edge_Chromium
\Microsoft\Edge\User Data
Kometa
\Kometa\User Data
Amigo
\Amigo\User Data
Torch
\Torch\User Data
Orbitum
\Orbitum\User Data
Comodo
\Comodo\Dragon\User Data
Nichrome
\Nichrome\User Data
Maxthon5
\Maxthon5\Users
Sputnik
\Sputnik\User Data
EPB
\Epic Privacy Browser\User Data
Vivaldi
\Vivaldi\User Data
CocCoc
\CocCoc\Browser\User Data
Uran
\uCozMedia\Uran\User Data
QIP
\QIP Surf\User Data
Cent
\CentBrowser\User Data
Elements
\Elements Browser\User Data
TorBro
\TorBro\Profile
CryptoTab
\CryptoTab Browser\User Data
Brave
\BraveSoftware\Brave-Browser\User Data
Opera
\Opera Software\Opera Stable\
OperaGX
\Opera Software\Opera GX Stable\
OperaNeon
\Opera Software\Opera Neon\User Data
Firefox
\Mozilla\Firefox\Profiles\
SlimBrowser
\FlashPeak\SlimBrowser\Profiles\
PaleMoon
\Moonchild Productions\Pale Moon\Profiles\
Waterfox
\Waterfox\Profiles\
Cyberfox
\8pecxstudios\Cyberfox\Profiles\
BlackHawk
\NETGATE Technologies\BlackHawk\Profiles\
IceCat
\Mozilla\icecat\Profiles\
KMeleon
\K-Meleon\
Thunderbird
\Thunderbird\Profiles\
passwords.txt
ibnejdfjmmkpcnlpebklmnkoeoihofec
TronLink
nkbihfbeogaeaoehlefnkodbefgpgknn
MetaMask
fhbohimaelbohpjbbldcngcnapndodjp
Binance Chain Wallet
ffnbelfdoeiohenkjibnmadjiehjhajb
Yoroi
jbdaocneiiinmjbjlgalhcelgbejmnid
Nifty Wallet
afbcbjpbpfadlkmhmclhkeeodmamcflc
Math Wallet
hnfanknocfeofbddgcijnmhnfnkdnaad
Coinbase Wallet
hpglfhgfnhbgpjdenjgmdgoeiappafln
Guarda
blnieiiffboillknjnepogjhkgnoapac
EQUAL Wallet
cjelfplplebdjjenllpjcblmjkfcffne
Jaxx Liberty
fihkakfobkmkjojpchpfgcmhfjnmnfpi
BitApp Wallet
kncchdigobghenbbaddojjnnaogfppfj
iWallet
amkmjjmmflddogmhpjloimipbofnfjih
Wombat
nlbmnnijcnlegkjjpcfjclmcfggfefdm
MEW CX
nanjmdknhkinifnkgdcggcfnhdaammmj
GuildWallet
nkddgncdjgjfcddamfgcmfnlhccnimig
Saturn Wallet
fnjhmkhhmkbjkkabndcnnogagogbneec
Ronin Wallet
cphhlgmgameodnhkjdmkpanlelnlohao
NeoLine
nhnkbkgjikgcigadomkphalanndcapjk
Clover Wallet
kpfopkelmapcoipemfendmdcghnegimn
Liquality Wallet
aiifbnbfobpmeekipheeijimdpnlpgpp
Terra Station
dmkamcknogkgcdfhhbddcghachkejeap
Keplr
fhmfendgdocmcbmfikdcogofphimnkno
Sollet
cnmamaachppnkjgnildpdmkaakejnhae
Auro Wallet
jojhfeoedkpkglbfimdfabpdfjaoolaf
Polymesh Wallet
flpiciilemghbmfalicajoolhkkenfel
ICONex
nknhiehlklippafakaeklbeglecifhad
Nabox Wallet
hcflpincpppdclinealmandijcmnkbgn
KHC
ookjlbkiijinhpmnjffcofjonbfbgaoc
Temple
mnfifefkajgofkcjkemidiaecocnkjeh
TezBox
dkdedlpgdmmkkfjabffeganieamfklkm
Cyano Wallet
nlgbhdfgdhgbiamfdfmbikcdghidoadd
Byone
infeboajgfhgbjpjbeppbkgnabfdkdaf
OneKey
cihmoadaighcejopammfbmddcmdekcje
LeafWallet
lodccjjbdhfakaekdiahmedfbieldgik
DAppPlay
ijmpgkjfkbfhoebgogflfebnmejmfbml
BitClip
lkcjlnjfpbikmcmbachjpdbijejflpcm
Steem Keychain
onofpnbbkehpmmoabgpcpmigafmmnjhl
Nash Extension
bcopgchhojmggmffilplmbdicgaihlkp
Hycon Lite Client
klnaejjgbibmhlephnhpmaofohgkpgkd
ZilPay
aeachknmefphepccionboohckonoeemg
Coin98 Wallet
bfnaelmomeimhlpmgjnjophhpkkoljpa
Phantom
hifafgmccdpekplomjjkcfgodnhcellj
Crypto.com
dngmlblcodfobpdpecaadgfbcggfjfnm
Maiar DeFi Wallet
ppdadbejkmjnefldpcdjhnkpbjkikoip
Oasis
hpbgcgmiemanfelegbndmhieiigkackl
MonstaWallet
fcckkdbjnoikooededlapcalpionmalo
MOBOX
jccapkebeeiajkkdemacblkjhhhboiek
Crust Wallet
mgffkfbidihjpoaomajlbgchddlicgpn
Pali Wallet
nphplpgoakhhjchkkhmiggakijnkhfnd
TON Wallet
ldinpeekobnhjjdofggfgjlcehhmanlj
Hiro Wallet
pocmplpaccanhmnllbbkpgfliimjljgo
Slope Wallet
bhhhlbepdkbapadjdnnojkbgioiodbic
Solflare Wallet
pgiaagfkgcbnmiiolekcfmljdagdhlcm
Stargazer Wallet
cgeeodpfagjceefieflmdfphplkenlfk
EVER Wallet
gjkdbeaiifkpoencioahhcilildpjhgh
partisia-wallet
bgjogpoidejdemgoochpnkmdjpocgkha
Ecto Wallet
ifckdpamphokdglkkdomedpdegcjhjdp
ONTO Wallet
agechnindjilpccclelhlbjphbgnobpf
Fractal Wallet
algblmhagnobbnmakepomicmfljlbehg
ADS Wallet
imijjbmbnebfnbmonjeileijahaipglj
Moonlet Wallet
kpjdchaapjheajadlaakiiigcbhoppda
ZEBEDEE
dlcobpjiigpikoobohmabehhmhfoodbb
Argent X StarkNet Wallet
bofddndhbegljegmpmnlbhcejofmjgbn
X-Wallet
mapbhaebnddapnmifbbkgeedkeplgjmf
Biport Wallet
kfdniefadaanbjodldohaedphafoffoh
Typhon Wallet
jaooiolkmfcmloonphpiiogkfckgciom
Twetch Wallet
aijcbedoijmgnlmjeegjaglmepbmpkpi
Leap Wallet
fhfffofbcgbjjojdnpcfompojdjjhdim
Lamden Wallet
agkfnefiabmfpanochlcakggnkdfmmjd
Earth Wallet
lpfcbjknijpeeillifnkikgncikgfhdo
Nami
fecfflganphcinpahcklgahckeohalog
Coin Wallet
ilhaljfiglknggcoegeknjghdgampffk
Beam Web Wallet
dklmlehijiaepdijfnbbhncfpcoeeljf
FShares Wallet
fkhebcilafocjhnlcngogekljmllgdhd
WAGMIswap.io Wallet
laphpbhjhhgigmjoflgcchgodbbclahk
BLUE - Worlds Safest and Simplest Wallet
mkjjflkhdddfjhonakofipfojoepfndk
Unification Web Wallet
jnldfbidonfeldmalbflbmlebbipcnle
Infinity Wallet
ellkdbaphhldpeajbepobaecooaoafpg
Fetch.ai Network Wallet
iokeahhehimjnekafflcihljlcjccdbe
Alby Wallet
omajpeaffjgmlpmhbfdjepdejoemifpe
xBull Wallet
pgojdfajgcjjpjnbpfaelnpnjocakldb
Sugarchain Wallet
pnndplcbkakcplkjnolgbkdgjikjednm
Tronium
fnnegphlobjdpkhecapkijjdkgcjhkib
Harmony
fhilaheimglignddkjgofkcbgekhenbh
Oxygen
cmbagcoinhmacpcgmbiniijboejgiahi
JustLiquidity Wallet
kmmolakhbgdlpkjkcjkebenjheonagdm
AlgoSigner
fnabdmcgpkkjjegokfcnfbpneacddpfh
Goldmint Lite Wallet
bgpipimickeadkjlklgciifhnalhdjhe
GeroWallet
hoighigmnhgkkdaenafgnefkcmipfjon
EO.Finance
nlgnepoeokdfodgjkjiblkadkjbdfmgd
Multi Wallet
nhihjlnjgibefgjhobhcphmnckoogdea
Waves Enterprise Wallet
ehibhohmlpipbaogcknmpmiibbllplph
Bluehelix Wallet
magbanejlegnbcppjljfhnmfmghialkl
Nebulas Wallet
fgkaeeikaoeiiggggbgdcjchmdfmamla
Vtimes
pnlfjmlcjdjgkddecgincndfgegkecke
Crocobit Wallet
bhghoamapcdpbohphigoooaddinpkbai
Authenticator
gaedmjdfmmahhbjefcbgaolhhanlaolb
Authy
oeljdldpnmdbchonielidgobddffflal
EOS Authenticator
ilgcnhelpchnceeipipijaljkblbcobl
GAuth Authenticator
imloifkgjagghnncjkhggdhalmcnfklk
Trezor Password Manager
%s\%s\Local Extension Settings\%s
%s\CURRENT
%s\%s\Sync Extension Settings\%s
%s\%s\IndexedDB\chrome-extension_%s_0.indexeddb.leveldb
Plugins\
HARDWARE\DESCRIPTION\System\CentralProcessor\0
ProcessorNameString
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
x64
x86
DISPLAY
SOFTWARE\Microsoft\Cryptography
MachineGuid
SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall
DisplayName
DisplayVersion
screenshot.jpg
ABCDEFGHIJKLMNOPQRSTUVWXYZ1234567890
/c timeout /t 5 & del /f /q "%s" & exit
C:\Windows\System32\cmd.exe
TRiD
| .exe | | | Win32 Executable (generic) (42.6) |
|---|---|---|
| .exe | | | Win16/32 Executable Delphi generic (19.5) |
| .exe | | | Generic Win/DOS Executable (18.9) |
| .exe | | | DOS Executable Generic (18.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 0000:00:00 00:00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit, No debug |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 2048 |
| InitializedDataSize: | 27351552 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x14f1 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
366
Monitored processes
241
Malicious processes
66
Suspicious processes
13
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 536 | vssadmin delete shadows /all /quiet | C:\Windows\System32\vssadmin.exe | — | asena.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Command Line Interface for Microsoft® Volume Shadow Copy Service Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 668 | chcp 65001 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Change CodePage Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 680 | ping -n 10 localhost | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 960 | netsh firewall add allowedprogram "C:\WINDOWS\rundll32.exe" "rundll32.exe" ENABLE | C:\Windows\SysWOW64\netsh.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1096 | "C:\Users\admin\AppData\Local\Temp\8.exe" | C:\Users\admin\AppData\Local\Temp\8.exe | Bomb.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Version: 1.0.0.0 Modules
| |||||||||||||||
| 1116 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | vssadmin.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1132 | taskdl.exe | C:\Users\admin\AppData\Roaming\taskdl.exe | — | ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: SQL Client Configuration Utility EXE Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1324 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1388 | "C:\Users\admin\AppData\Local\Temp\10.exe" | C:\Users\admin\AppData\Local\Temp\10.exe | Bomb.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Version: 1.0.0.0 Modules
| |||||||||||||||
| 1748 | ping -n 10 localhost | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
99 879
Read events
99 329
Write events
550
Delete events
0
Modification events
| (PID) Process: | (7748) ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WanaCrypt0r |
| Operation: | write | Name: | wd |
Value: C:\Users\admin\AppData\Roaming | |||
| (PID) Process: | (4980) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | 81dfcd3 |
Value: C:\81dfcd3e\81dfcd3e.exe | |||
| (PID) Process: | (4980) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | *1dfcd3 |
Value: C:\81dfcd3e\81dfcd3e.exe | |||
| (PID) Process: | (4980) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | 81dfcd3e |
Value: C:\Users\admin\AppData\Roaming\81dfcd3e.exe | |||
| (PID) Process: | (4980) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | *1dfcd3e |
Value: C:\Users\admin\AppData\Roaming\81dfcd3e.exe | |||
| (PID) Process: | (7324) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (7324) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (7324) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (7324) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (7324) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
Executable files
98
Suspicious files
2 549
Text files
259
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7748 | ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe | C:\Users\admin\AppData\Roaming\msg\m_croatian.wnry | text | |
MD5:17194003FA70CE477326CE2F6DEEB270 | SHA256:3F33734B2D34CCE83936CE99C3494CD845F1D2C02D7F6DA31D42DFC1CA15A171 | |||
| 7748 | ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe | C:\Users\admin\AppData\Roaming\b.wnry | image | |
MD5:C17170262312F3BE7027BC2CA825BF0C | SHA256:D5E0E8694DDC0548D8E6B87C83D50F4AB85C1DEBADB106D6A6A794C3E746F4FA | |||
| 7696 | pcraper.exe | C:\Users\admin\AppData\Roaming\ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe | executable | |
MD5:84C82835A5D21BBCF75A61706D8AB549 | SHA256:ED01EBFBC9EB5BBEA545AF4D01BF5F1071661840480439C6E5BABE8E080E41AA | |||
| 7748 | ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe | C:\Users\admin\AppData\Roaming\msg\m_bulgarian.wnry | text | |
MD5:95673B0F968C0F55B32204361940D184 | SHA256:40B37E7B80CF678D7DD302AAF41B88135ADE6DDF44D89BDBA19CF171564444BD | |||
| 7748 | ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe | C:\Users\admin\AppData\Roaming\msg\m_finnish.wnry | text | |
MD5:35C2F97EEA8819B1CAEBD23FEE732D8F | SHA256:1ADFEE058B98206CB4FBE1A46D3ED62A11E1DEE2C7FF521C1EEF7C706E6A700E | |||
| 7748 | ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe | C:\Users\admin\AppData\Roaming\msg\m_dutch.wnry | text | |
MD5:7A8D499407C6A647C03C4471A67EAAD7 | SHA256:2C95BEF914DA6C50D7BDEDEC601E589FBB4FDA24C4863A7260F4F72BD025799C | |||
| 7748 | ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe | C:\Users\admin\AppData\Roaming\msg\m_czech.wnry | text | |
MD5:537EFEECDFA94CC421E58FD82A58BA9E | SHA256:5AFA4753AFA048C6D6C39327CE674F27F5F6E5D3F2A060B7A8AED61725481150 | |||
| 7748 | ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe | C:\Users\admin\AppData\Roaming\msg\m_chinese (simplified).wnry | text | |
MD5:0252D45CA21C8E43C9742285C48E91AD | SHA256:845D0E178AEEBD6C7E2A2E9697B2BF6CF02028C50C288B3BA88FE2918EA2834A | |||
| 7748 | ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe | C:\Users\admin\AppData\Roaming\msg\m_german.wnry | text | |
MD5:3D59BBB5553FE03A89F817819540F469 | SHA256:2ADC900FAFA9938D85CE53CB793271F37AF40CF499BCC454F44975DB533F0B61 | |||
| 7748 | ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe | C:\Users\admin\AppData\Roaming\msg\m_chinese (traditional).wnry | text | |
MD5:2EFC3690D67CD073A9406A25005F7CEA | SHA256:5C7F6AD1EC4BC2C8E2C9C126633215DABA7DE731AC8B12BE10CA157417C97F3A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
132
TCP/UDP connections
249
DNS requests
55
Threats
314
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | svchost.exe | GET | 200 | 23.48.23.162:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5608 | svchost.exe | GET | 308 | 188.165.164.184:80 | http://ip-addr.es/ | unknown | — | — | shared |
5608 | svchost.exe | POST | — | 94.247.31.19:8080 | http://proxy2-2-2.i2p/244cd3im11s | unknown | — | — | malicious |
6752 | 7.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | whitelisted |
7688 | 11.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | whitelisted |
7468 | 20.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | whitelisted |
2420 | 9.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | whitelisted |
7492 | 18.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | whitelisted |
6044 | 23.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | whitelisted |
1096 | 8.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2104 | svchost.exe | 23.48.23.162:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6544 | svchost.exe | 40.126.31.129:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5608 | svchost.exe | 188.165.164.184:80 | ip-addr.es | OVH SAS | FR | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ip-addr.es |
| shared |
urlhaus.abuse.ch |
| whitelisted |
ip-api.com |
| whitelisted |
pub-6c72ff8278934f2895f21413f6d49880.r2.dev |
| unknown |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5608 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO HTTP Request for External IP Check (ip-addr .es) |
— | — | Device Retrieving External IP Address Detected | ET INFO HTTP Request for External IP Check (ip-addr .es) |
5608 | svchost.exe | A Network Trojan was detected | ET MALWARE CryptoWall CryptoWall 3.0 Check-in |
2196 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
6752 | 7.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |
6752 | 7.exe | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External Hosting Lookup by ip-api |
6752 | 7.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |
6752 | 7.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |
6752 | 7.exe | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External Hosting Lookup by ip-api |