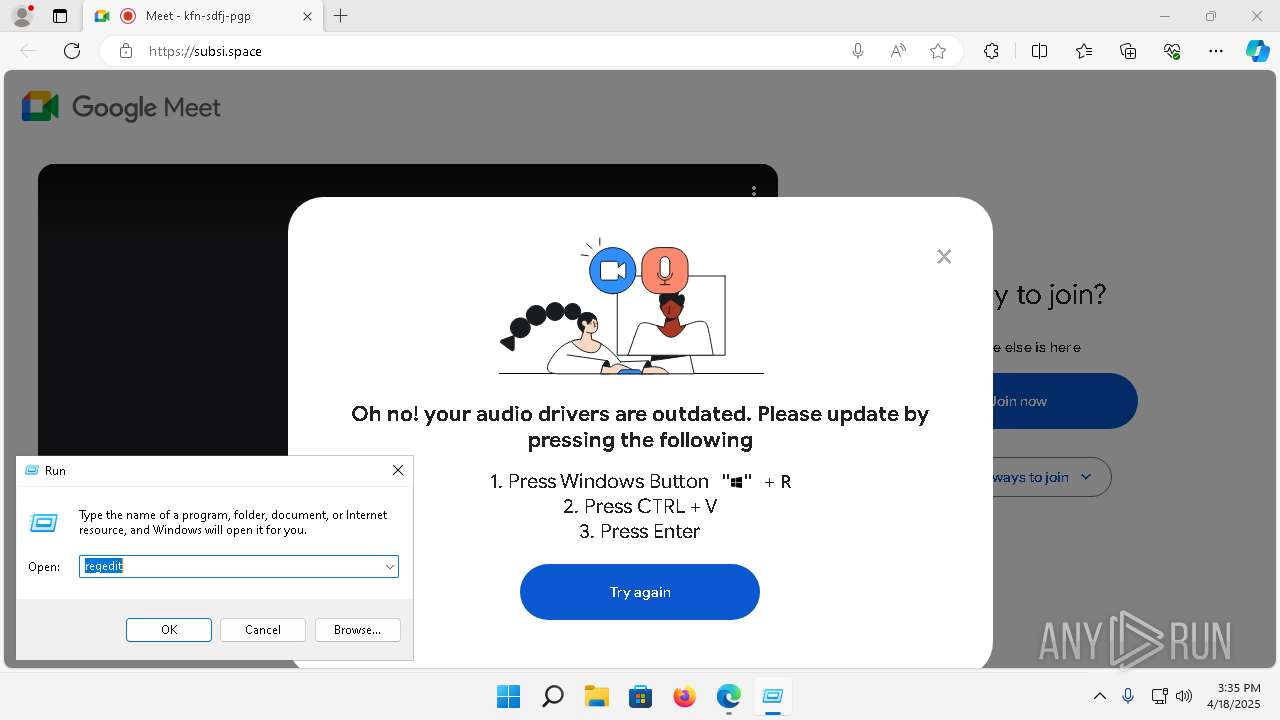
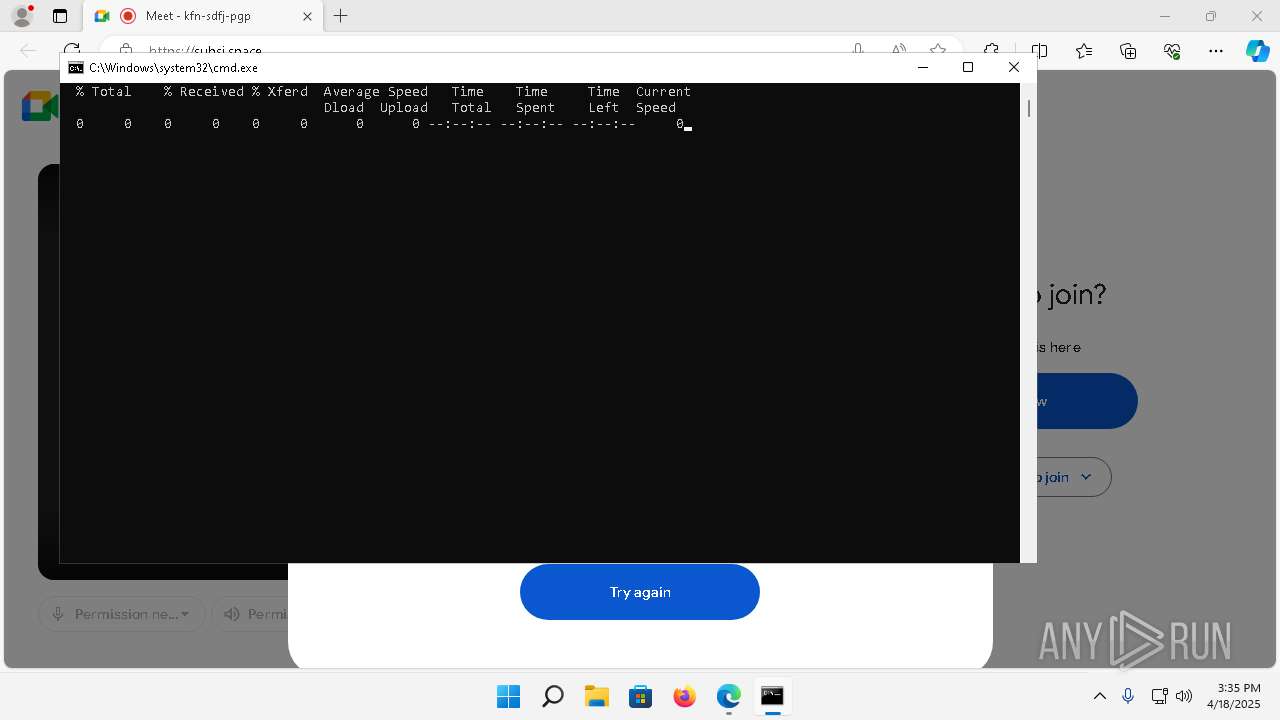
| URL: | https://subsi.space/ |
| Full analysis: | https://app.any.run/tasks/02a2df6b-b98c-47fa-bf2f-914683a9bc59 |
| Verdict: | Malicious activity |
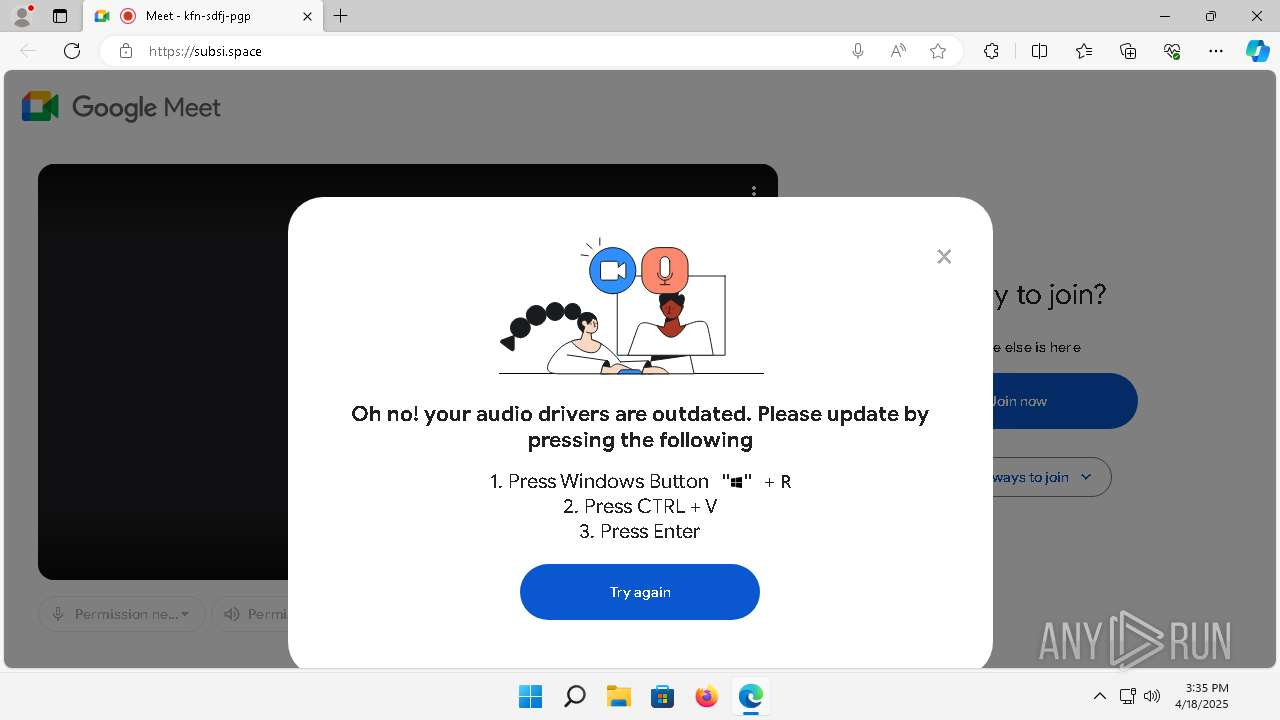
| Threats: | Rhadamanthys is a C++ information-stealing malware that extracts sensitive data from infiltrated machines. Its layered operational chain and advanced evasion tactics make it a major risk in cybersecurity landscapes. |
| Analysis date: | April 18, 2025, 15:35:01 |
| OS: | Windows 11 Professional (build: 22000, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 2CDD219D4D6DB9133B2306CFF5E021B7 |
| SHA1: | BE6C19253AC04C76ACEB3812DD7DF988DB03BC5E |
| SHA256: | ADFAB8CC3948C3824AA684E0075157907538DBD538F37E26D15FE65AD9909DC9 |
| SSDEEP: | 3:N8d2M2Ea:2sH |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 7608)
RHADAMANTHYS mutex has been found
- svchost.exe (PID: 7908)
- powershell.exe (PID: 7608)
Gets or sets the symmetric key that is used for encryption and decryption (POWERSHELL)
- powershell.exe (PID: 7608)
Uses AES cipher (POWERSHELL)
- powershell.exe (PID: 7608)
Gets or sets the initialization vector for the symmetric algorithm (POWERSHELL)
- powershell.exe (PID: 7608)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 7608)
Steals credentials from Web Browsers
- msedge.exe (PID: 388)
- msedge.exe (PID: 6768)
SUSPICIOUS
Executing commands from a ".bat" file
- cmd.exe (PID: 7440)
- cmd.exe (PID: 7536)
Application launched itself
- cmd.exe (PID: 7440)
- cmd.exe (PID: 7536)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 7440)
- cmd.exe (PID: 7536)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 7536)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 7536)
Starts application with an unusual extension
- cmd.exe (PID: 7536)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 7608)
The process checks if it is being run in the virtual environment
- svchost.exe (PID: 7908)
Reads the Internet Settings
- powershell.exe (PID: 7608)
- chrome.exe (PID: 8080)
- msedge.exe (PID: 388)
- msedge.exe (PID: 6768)
Reads settings of System Certificates
- chrome.exe (PID: 8080)
- msedge.exe (PID: 6768)
- msedge.exe (PID: 388)
Reads security settings of Internet Explorer
- msedge.exe (PID: 388)
- msedge.exe (PID: 6768)
Reads Mozilla Firefox installation path
- msedge.exe (PID: 388)
- msedge.exe (PID: 6768)
Executable content was dropped or overwritten
- wmplayer.exe (PID: 6564)
Loads DLL from Mozilla Firefox
- svchost.exe (PID: 7908)
Searches for installed software
- svchost.exe (PID: 7908)
INFO
Reads Environment values
- identity_helper.exe (PID: 6336)
- chrome.exe (PID: 8080)
- msedge.exe (PID: 388)
- msedge.exe (PID: 6768)
Application launched itself
- msedge.exe (PID: 4456)
- chrome.exe (PID: 8080)
- msedge.exe (PID: 6768)
- msedge.exe (PID: 388)
Reads the computer name
- identity_helper.exe (PID: 6336)
- MiniSearchHost.exe (PID: 6444)
- curl.exe (PID: 7492)
- chrome.exe (PID: 8080)
- msedge.exe (PID: 388)
- msedge.exe (PID: 6768)
- wmplayer.exe (PID: 6564)
Checks supported languages
- identity_helper.exe (PID: 6336)
- curl.exe (PID: 7492)
- MiniSearchHost.exe (PID: 6444)
- chrome.exe (PID: 8080)
- more.com (PID: 7640)
- msedge.exe (PID: 388)
- msedge.exe (PID: 6768)
- wmplayer.exe (PID: 6564)
Execution of CURL command
- cmd.exe (PID: 7440)
Manual execution by a user
- cmd.exe (PID: 7440)
- svchost.exe (PID: 7908)
Create files in a temporary directory
- curl.exe (PID: 7492)
- svchost.exe (PID: 7908)
- chrome.exe (PID: 8080)
- msedge.exe (PID: 388)
- msedge.exe (PID: 6768)
Checks current location (POWERSHELL)
- powershell.exe (PID: 7608)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 7608)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 7608)
Gets data length (POWERSHELL)
- powershell.exe (PID: 7608)
Checks proxy server information
- msedge.exe (PID: 388)
- chrome.exe (PID: 8080)
- msedge.exe (PID: 6768)
Reads the machine GUID from the registry
- chrome.exe (PID: 8080)
- msedge.exe (PID: 388)
- msedge.exe (PID: 6768)
- wmplayer.exe (PID: 6564)
Process checks computer location settings
- msedge.exe (PID: 388)
- msedge.exe (PID: 6768)
Process checks whether UAC notifications are on
- msedge.exe (PID: 388)
- msedge.exe (PID: 6768)
Creates files or folders in the user directory
- msedge.exe (PID: 388)
- wmplayer.exe (PID: 6564)
The sample compiled with english language support
- wmplayer.exe (PID: 6564)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
196
Monitored processes
85
Malicious processes
6
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 364 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=2244 --field-trial-handle=2044,i,16967134180117047929,14150830452335410780,262144 --variations-seed-version /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.92 Modules
| |||||||||||||||
| 388 | --user-data-dir="C:\Users\admin\AppData\Local\Temp\chrFAF0.tmp" --explicitly-allowed-ports=8000 --disable-gpu --new-window "http://127.0.0.1:8000/6764a645/5fdaec0d" | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.92 Modules
| |||||||||||||||
| 436 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5604 --field-trial-handle=2044,i,16967134180117047929,14150830452335410780,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.92 Modules
| |||||||||||||||
| 604 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=3336 --field-trial-handle=2044,i,16967134180117047929,14150830452335410780,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.92 Modules
| |||||||||||||||
| 804 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=2472 --field-trial-handle=2044,i,16967134180117047929,14150830452335410780,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.92 Modules
| |||||||||||||||
| 1116 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --extension-process --renderer-sub-type=extension --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=13 --mojo-platform-channel-handle=4188 --field-trial-handle=2036,i,13363303913564853754,16899733897659173343,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.92 Modules
| |||||||||||||||
| 1152 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=3400 --field-trial-handle=2044,i,16967134180117047929,14150830452335410780,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.92 Modules
| |||||||||||||||
| 1164 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=2192 --field-trial-handle=2036,i,10332405191994530867,7118575077626108390,262144 --variations-seed-version /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.92 Modules
| |||||||||||||||
| 1220 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --extension-process --renderer-sub-type=extension --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --mojo-platform-channel-handle=3840 --field-trial-handle=2044,i,16967134180117047929,14150830452335410780,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.92 Modules
| |||||||||||||||
| 1304 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --extension-process --renderer-sub-type=extension --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=12 --mojo-platform-channel-handle=4444 --field-trial-handle=2036,i,10332405191994530867,7118575077626108390,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.92 Modules
| |||||||||||||||
Total events
30 949
Read events
30 724
Write events
216
Delete events
9
Modification events
| (PID) Process: | (4456) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (4456) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (4456) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (4456) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (4456) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (4456) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\EdgeUpdate\ClientState\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (4456) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (4456) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge |
| Operation: | write | Name: | UsageStatsInSample |
Value: 1 | |||
| (PID) Process: | (4456) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-166304369-59083888-3082702900-1001 |
Value: 8D71F48BA5912F00 | |||
| (PID) Process: | (4456) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\IEToEdge |
| Operation: | delete value | Name: | DisabledPendingAutoUpdateConsent |
Value: | |||
Executable files
22
Suspicious files
524
Text files
139
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4456 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Profile 1\parcel_tracking_db\LOG.old~RF1638f7.TMP | — | |
MD5:— | SHA256:— | |||
| 4456 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Profile 1\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4456 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Profile 1\commerce_subscription_db\LOG.old~RF1638f7.TMP | — | |
MD5:— | SHA256:— | |||
| 4456 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Profile 1\discounts_db\LOG.old~RF163906.TMP | — | |
MD5:— | SHA256:— | |||
| 4456 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Profile 1\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4456 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Profile 1\PersistentOriginTrials\LOG.old~RF163906.TMP | — | |
MD5:— | SHA256:— | |||
| 4456 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Profile 1\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4456 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Profile 1\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4456 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Profile 1\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF163916.TMP | — | |
MD5:— | SHA256:— | |||
| 4456 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Profile 1\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
24
TCP/UDP connections
103
DNS requests
111
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1340 | smartscreen.exe | GET | 200 | 23.50.131.200:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?64e5c29e2a3a5980 | unknown | — | — | whitelisted |
1340 | smartscreen.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
3640 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4752 | SearchHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1352 | svchost.exe | GET | 200 | 88.221.110.216:80 | http://www.msftconnecttest.com/connecttest.txt | unknown | — | — | whitelisted |
4752 | SearchHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
744 | lsass.exe | GET | 200 | 23.209.209.135:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
744 | lsass.exe | GET | 200 | 2.19.120.159:80 | http://r11.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBQaUrm0WeTDM5ghfoZtS72KO9ZnzgQUCLkRO6XQhRi06g%2BgrZ%2BGHo78OCcCEgY1566wtYtSlQa1xPdHQT7zQA%3D%3D | unknown | — | — | whitelisted |
6108 | svchost.exe | HEAD | 200 | 2.16.168.112:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9b9f8fb4-8a65-41e4-bda3-5416858f0aeb?P1=1745356201&P2=404&P3=2&P4=T5zHb9KTBHEYs9sEKqUqW11Y%2bNGLGqsrTKiAJ9fB2BeMLj77DtD0H9Otevjh7dgXbsIwxHXfNWneUgqoWfGlrQ%3d%3d | unknown | — | — | whitelisted |
2768 | svchost.exe | GET | 200 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/pinrulesstl.cab?0cde1ba27ffa6121 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1352 | svchost.exe | 88.221.110.147:80 | — | Akamai International B.V. | DE | unknown |
1340 | smartscreen.exe | 4.175.223.124:443 | checkappexec.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1340 | smartscreen.exe | 23.50.131.200:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | whitelisted |
1340 | smartscreen.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
364 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4456 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
364 | msedge.exe | 178.255.245.105:443 | subsi.space | — | IT | unknown |
364 | msedge.exe | 150.171.27.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
364 | msedge.exe | 13.107.6.158:443 | business.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
checkappexec.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
subsi.space |
| unknown |
ocsp.digicert.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
clients2.google.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1352 | svchost.exe | Misc activity | ET INFO Microsoft Connection Test |
7908 | svchost.exe | Misc activity | ET INFO Cloudflare DNS Over HTTPS Certificate Inbound |
7908 | svchost.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 32 |
Process | Message |
|---|---|
chrome.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Temp\chrE890.tmp directory exists )
|
msedge.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Temp\chrFAF0.tmp directory exists )
|
msedge.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Temp\chr428.tmp directory exists )
|