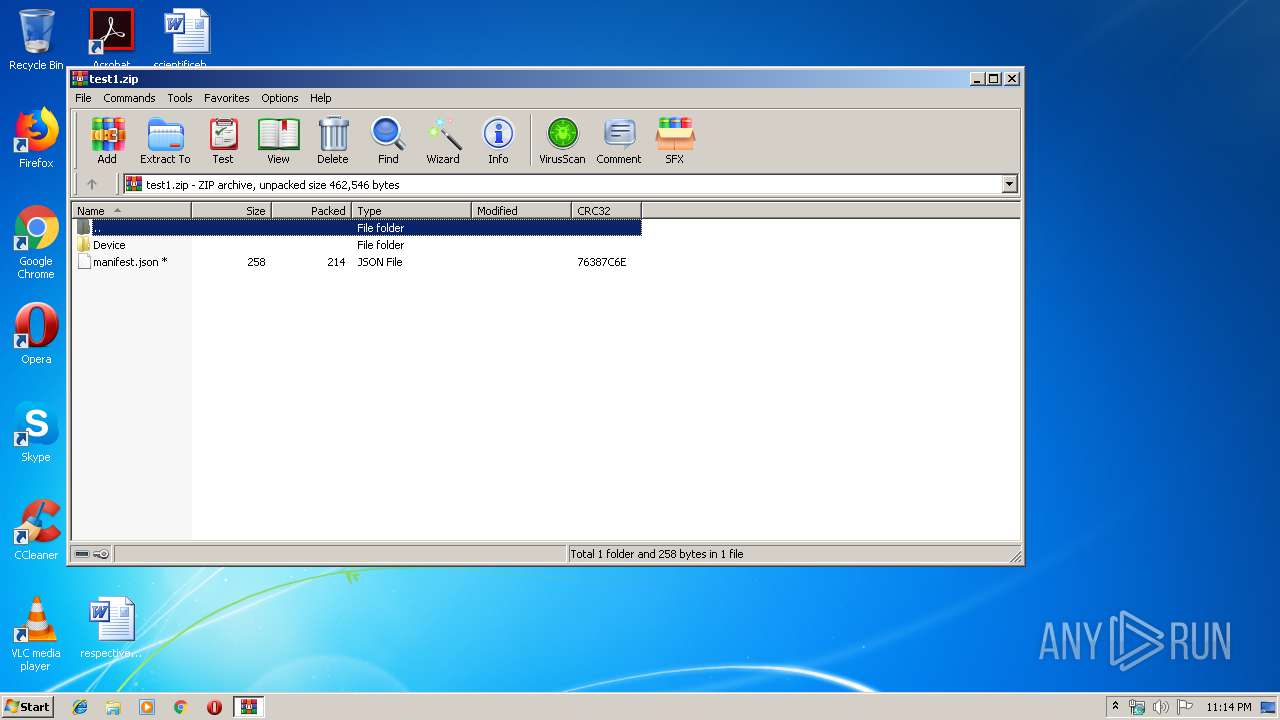
| File name: | test1.zip |
| Full analysis: | https://app.any.run/tasks/89b216b9-895e-4efe-9809-3f6f902e5b25 |
| Verdict: | Malicious activity |
| Threats: | TrickBot is an advanced banking trojan that attackers can use to steal payment credentials from the victims. It can redirect the victim to a fake banking cabinet and retrieve credentials typed in on the webpage. |
| Analysis date: | January 17, 2020, 23:14:06 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v4.5 to extract |
| MD5: | 634F3AFF60F49E0E70C3BF7A8732BBF5 |
| SHA1: | 9546999EF57B133D3047D2A941E60FDDD6873984 |
| SHA256: | ADEEBFE44F1EF737FB8BD8ABDB25C0FECF9D4CD86A597534FF4C5BB243DA362D |
| SSDEEP: | 6144:E6E3tggdqvtKYRL5Q5qB6TggO5Mcj6Idrh++cGeIZWRvXG0V7u1gMs:E6yFe5cI6jOuclE+cgmPGmH9 |
MALICIOUS
Application was dropped or rewritten from another process
- 59346383.exe (PID: 1724)
- 39324383.exe (PID: 2908)
- 59346383.exe (PID: 408)
TRICKBOT was detected
- 39324383.exe (PID: 2908)
- 59346383.exe (PID: 408)
Loads the Task Scheduler COM API
- 39324383.exe (PID: 2908)
- 59346383.exe (PID: 408)
Known privilege escalation attack
- DllHost.exe (PID: 2344)
SUSPICIOUS
Executed via COM
- DllHost.exe (PID: 2344)
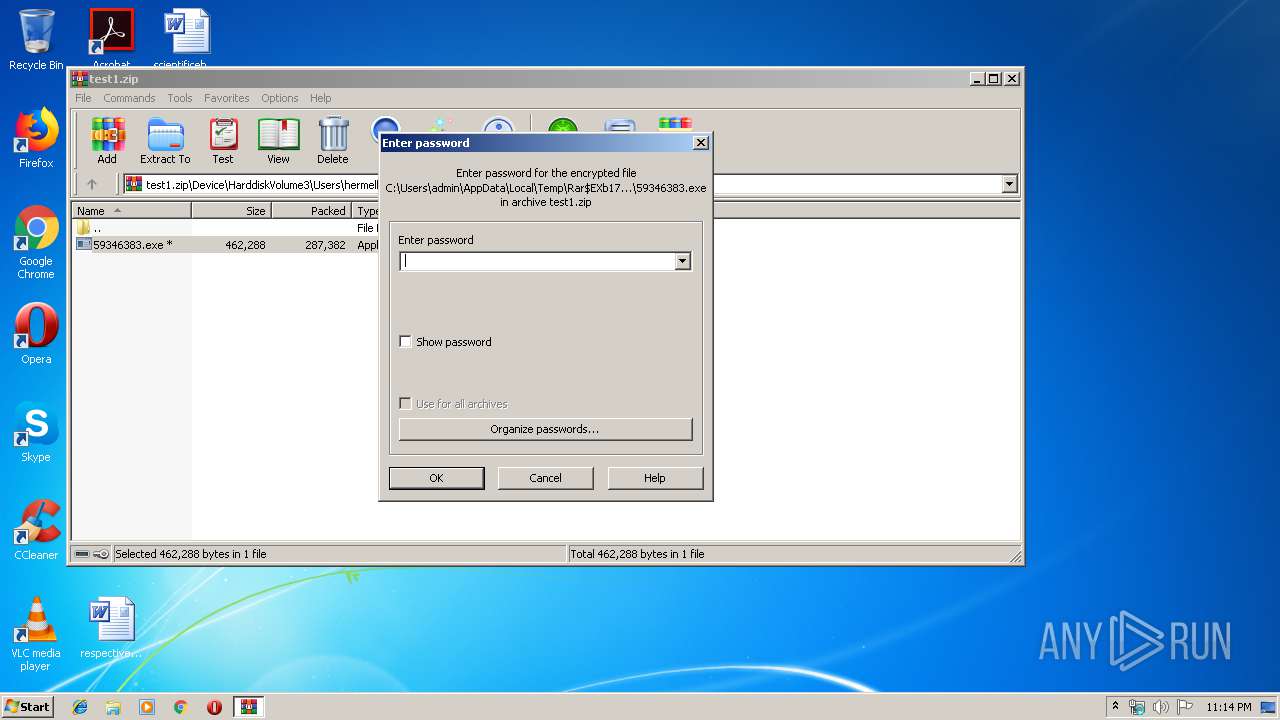
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1752)
- 59346383.exe (PID: 408)
Creates files in the user directory
- 59346383.exe (PID: 408)
- 39324383.exe (PID: 2908)
Executed via Task Scheduler
- 39324383.exe (PID: 2908)
INFO
Manual execution by user
- WINWORD.EXE (PID: 2140)
- AcroRd32.exe (PID: 1784)
Application launched itself
- RdrCEF.exe (PID: 3408)
- AcroRd32.exe (PID: 1784)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2140)
Creates files in the user directory
- WINWORD.EXE (PID: 2140)
Reads the hosts file
- RdrCEF.exe (PID: 3408)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0801 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:00:00 00:00:00 |
| ZipCRC: | 0x39220635 |
| ZipCompressedSize: | 287382 |
| ZipUncompressedSize: | 462288 |
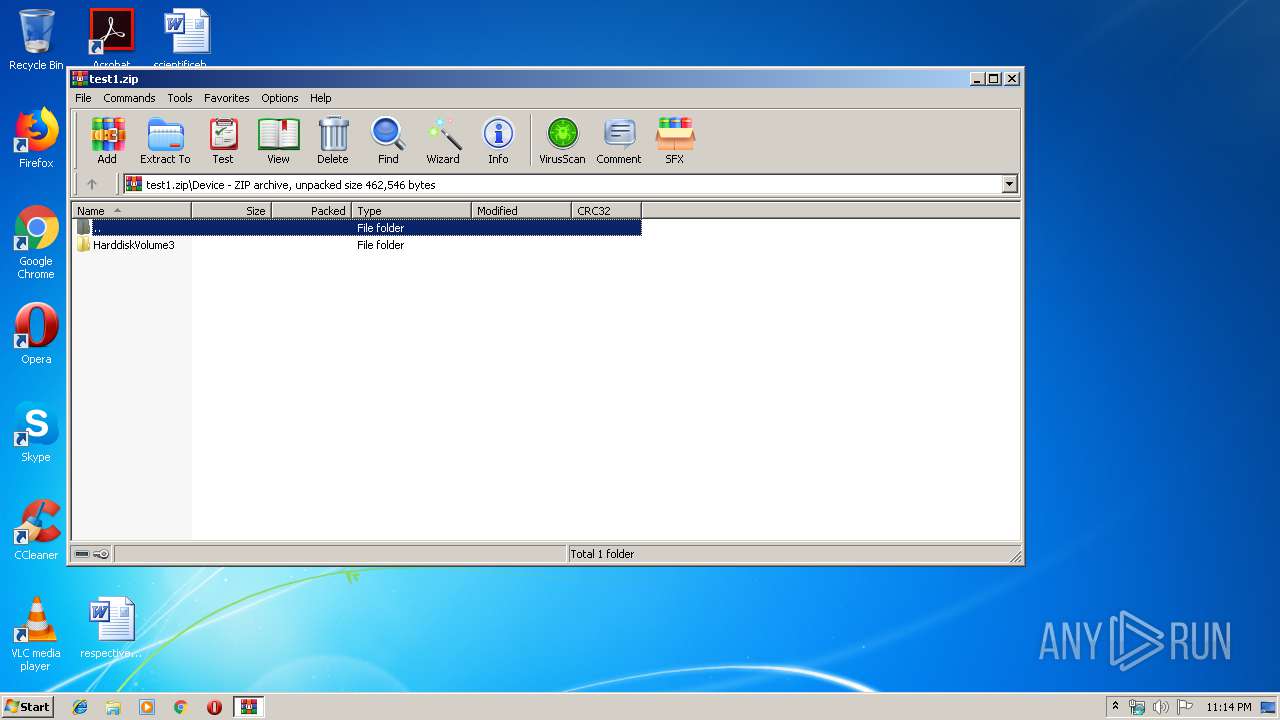
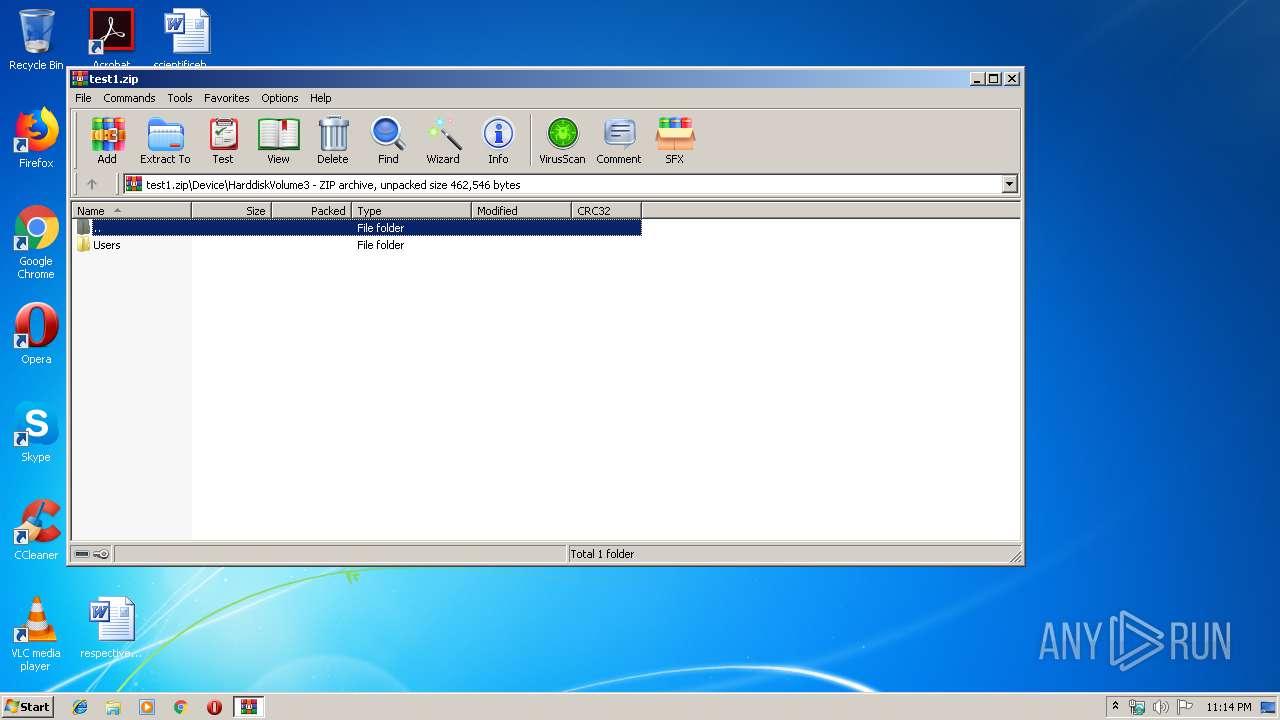
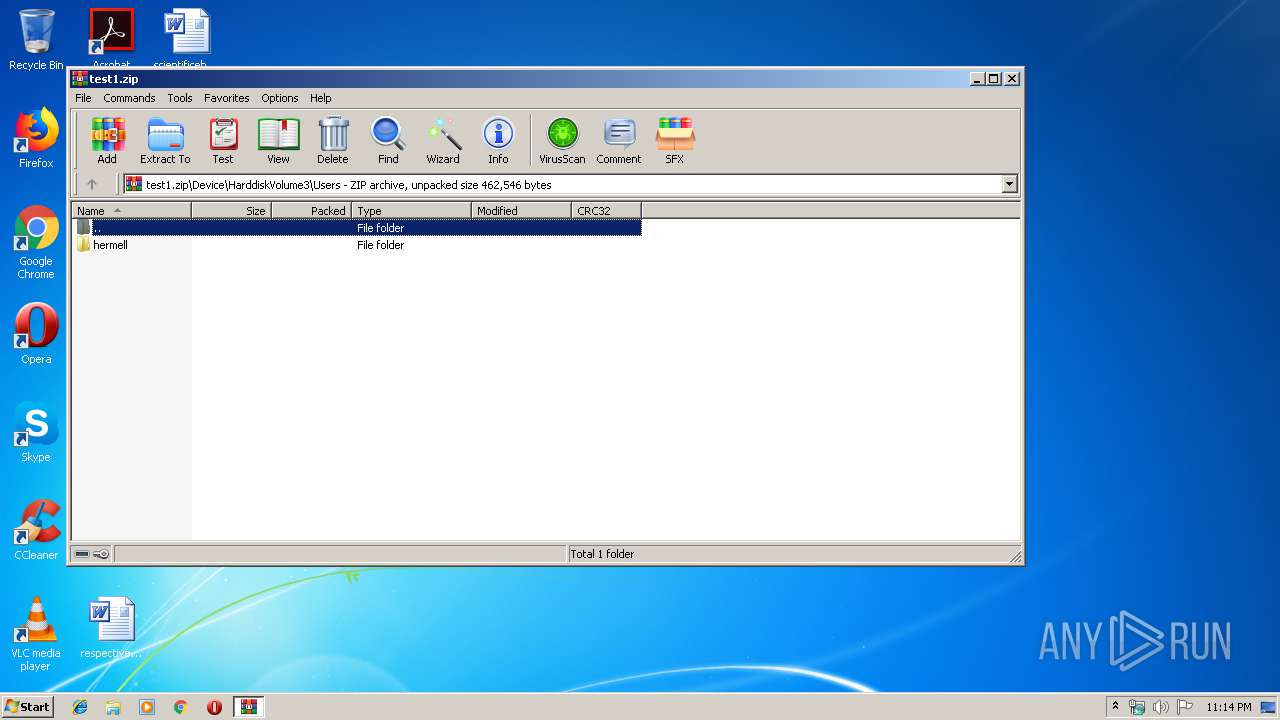
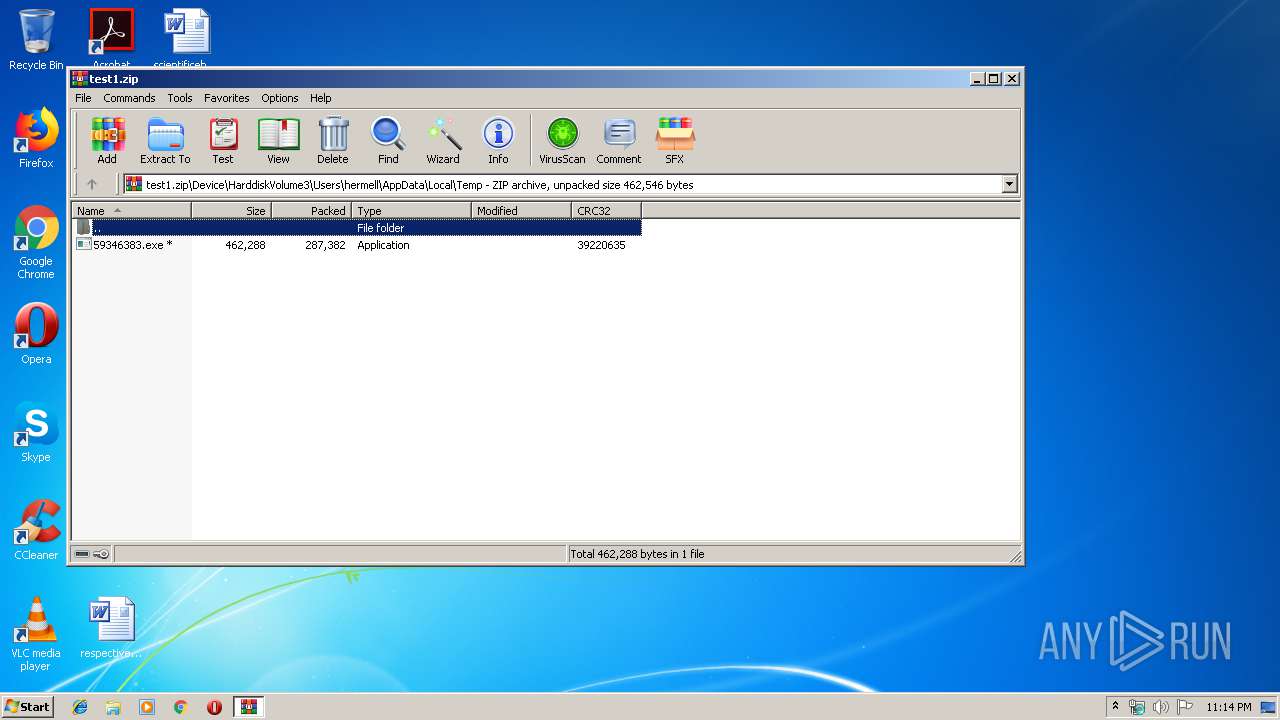
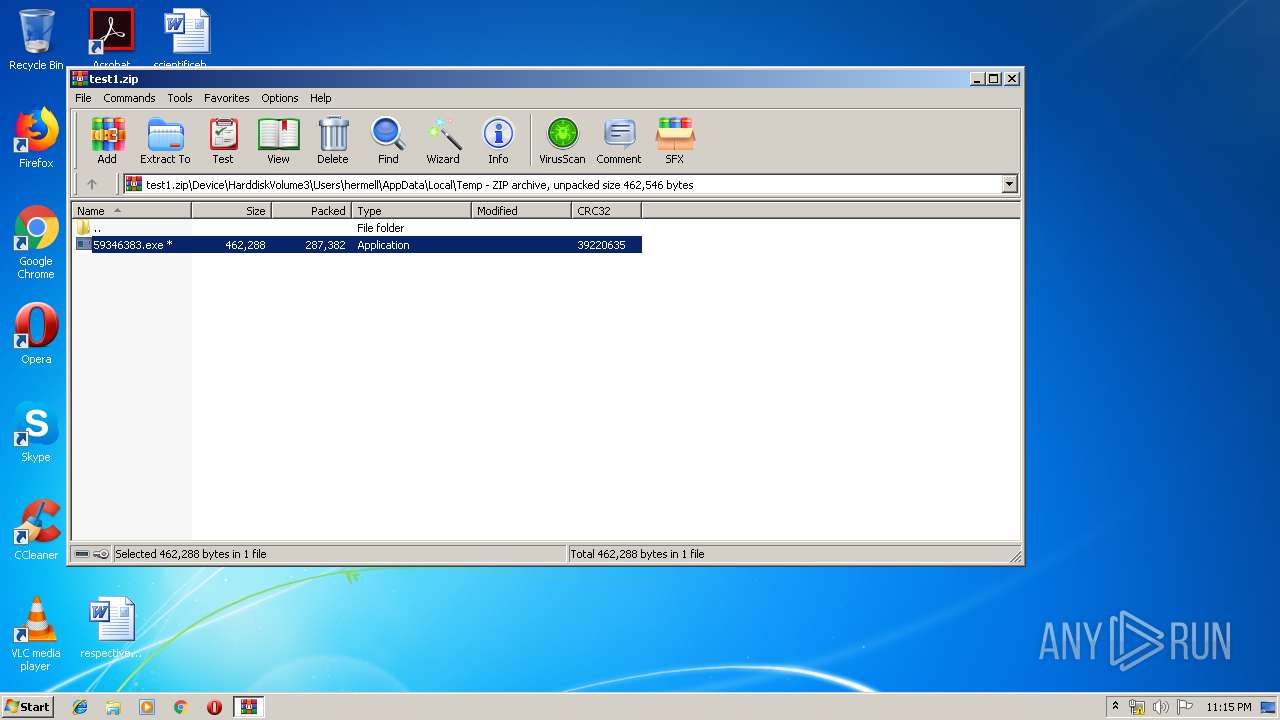
| ZipFileName: | Device/HarddiskVolume3/Users/hermell/AppData/Local/Temp/59346383.exe |
Total processes
50
Monitored processes
10
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 408 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb1752.37255\Device\HarddiskVolume3\Users\hermell\AppData\Local\Temp\59346383.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb1752.37255\Device\HarddiskVolume3\Users\hermell\AppData\Local\Temp\59346383.exe | DllHost.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1188 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --disable-3d-apis --disable-databases --disable-direct-npapi-requests --disable-file-system --disable-notifications --disable-shared-workers --disable-direct-write --lang=en-US --lang=en-US --log-severity=disable --product-version="ReaderServices/15.23.20053 Chrome/45.0.2454.85" --device-scale-factor=1 --enable-delegated-renderer --num-raster-threads=2 --gpu-rasterization-msaa-sample-count=8 --content-image-texture-target=3553 --video-image-texture-target=3553 --disable-accelerated-video-decode --disable-webrtc-hw-encoding --disable-gpu-compositing --channel="3408.0.524815997\476436060" --allow-no-sandbox-job /prefetch:673131151 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 1724 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb1752.37255\Device\HarddiskVolume3\Users\hermell\AppData\Local\Temp\59346383.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb1752.37255\Device\HarddiskVolume3\Users\hermell\AppData\Local\Temp\59346383.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1752 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\test1.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 1784 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | explorer.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Reader DC Exit code: 1 Version: 15.23.20070.215641 Modules
| |||||||||||||||
| 2140 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\respectivewords.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2344 | C:\Windows\system32\DllHost.exe /Processid:{3E5FC7F9-9A51-4367-9063-A120244FBEC7} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2908 | C:\Users\admin\AppData\Roaming\WinNetCore\39324383.exe | C:\Users\admin\AppData\Roaming\WinNetCore\39324383.exe | taskeng.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 0 Modules
| |||||||||||||||
| 3304 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" --type=renderer | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Reader DC Exit code: 1 Version: 15.23.20070.215641 Modules
| |||||||||||||||
| 3408 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --backgroundcolor=16448250 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
Total events
1 694
Read events
1 324
Write events
231
Delete events
139
Modification events
| (PID) Process: | (1752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1752) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\test1.zip | |||
| (PID) Process: | (1752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (1752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
2
Suspicious files
1
Text files
4
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2140 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRAB49.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2140 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{90512652-8747-4905-AC02-E6CC89EF6D8B}.tmp | — | |
MD5:— | SHA256:— | |||
| 2140 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{EB404F54-B6AB-4219-8385-F70BAEDC0F78}.tmp | — | |
MD5:— | SHA256:— | |||
| 2140 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRF{47417411-CFF5-4BD4-BF3F-87B0FC7240FF}.tmp | — | |
MD5:— | SHA256:— | |||
| 2908 | 39324383.exe | C:\Users\admin\AppData\Roaming\WinNetCore\settings.ini | text | |
MD5:— | SHA256:— | |||
| 2140 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:— | SHA256:— | |||
| 3304 | AcroRd32.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\IconCacheRdr65536.dat | binary | |
MD5:— | SHA256:— | |||
| 1752 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb1752.37255\manifest.json | text | |
MD5:— | SHA256:— | |||
| 408 | 59346383.exe | C:\Users\admin\AppData\Roaming\WinNetCore\39324383.exe | executable | |
MD5:— | SHA256:— | |||
| 2140 | WINWORD.EXE | C:\Users\admin\Desktop\~$spectivewords.rtf | pgc | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2908 | 39324383.exe | 5.182.210.246:443 | — | — | — | malicious |