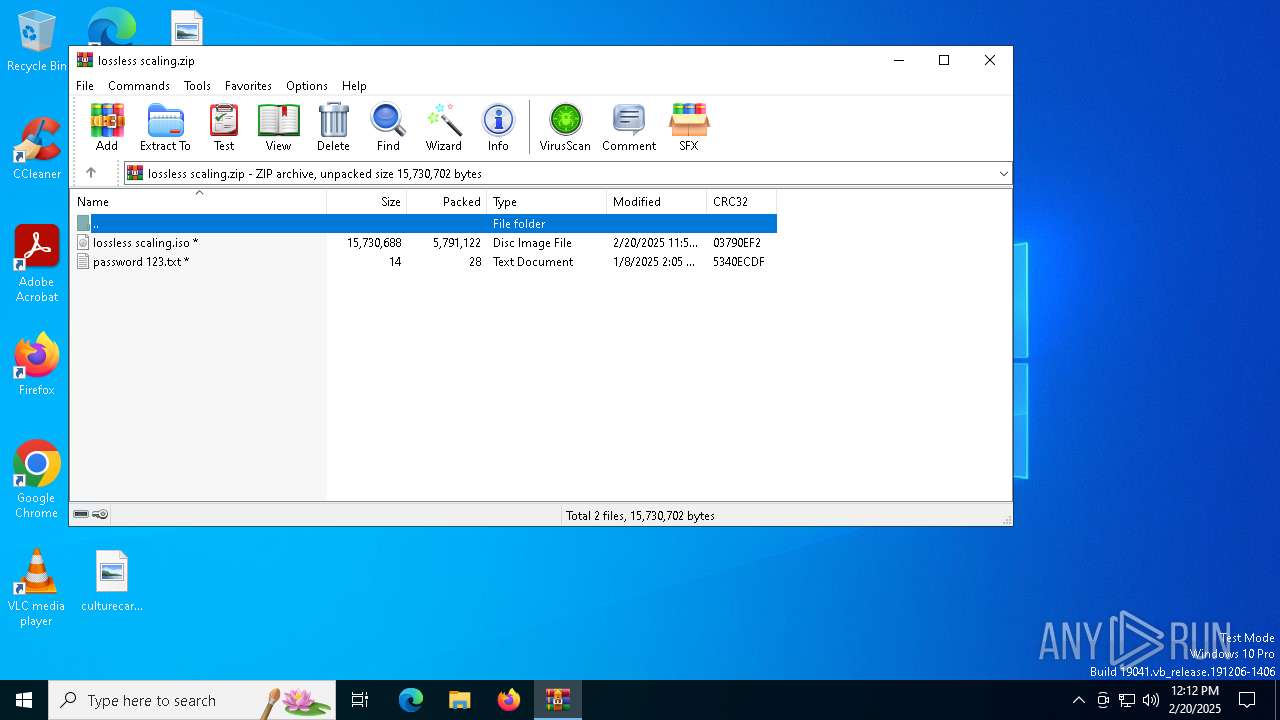
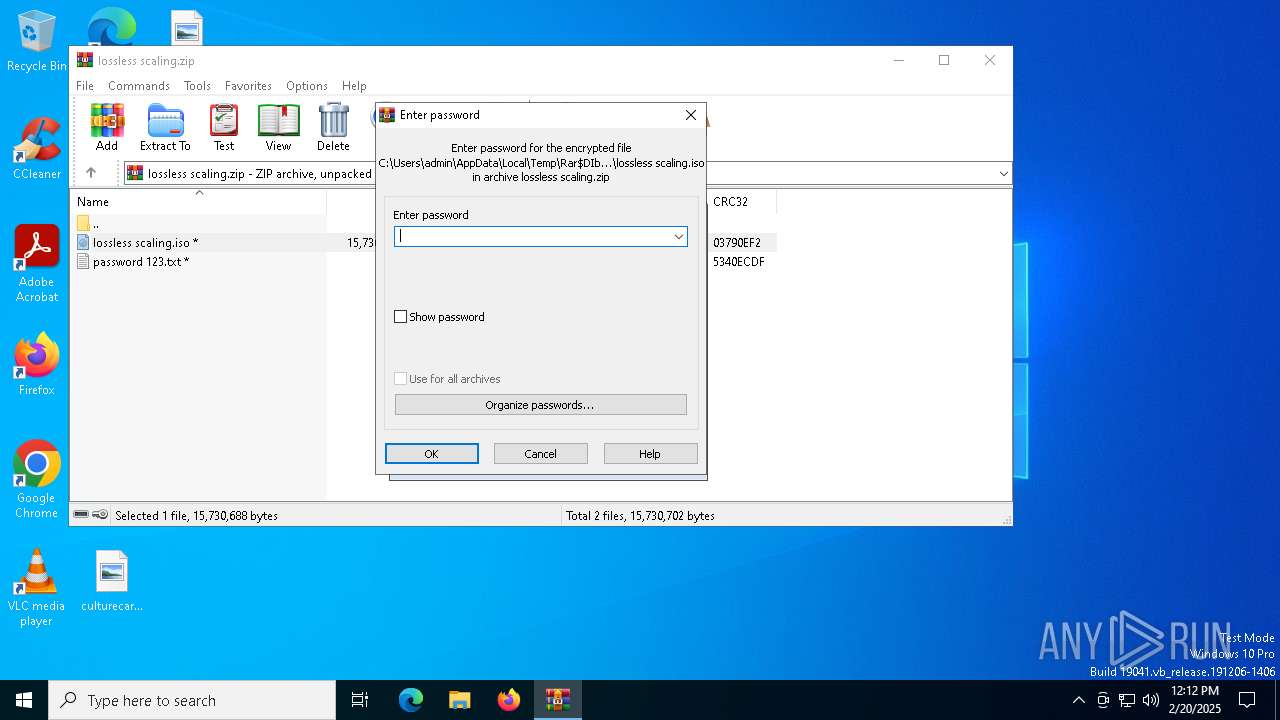
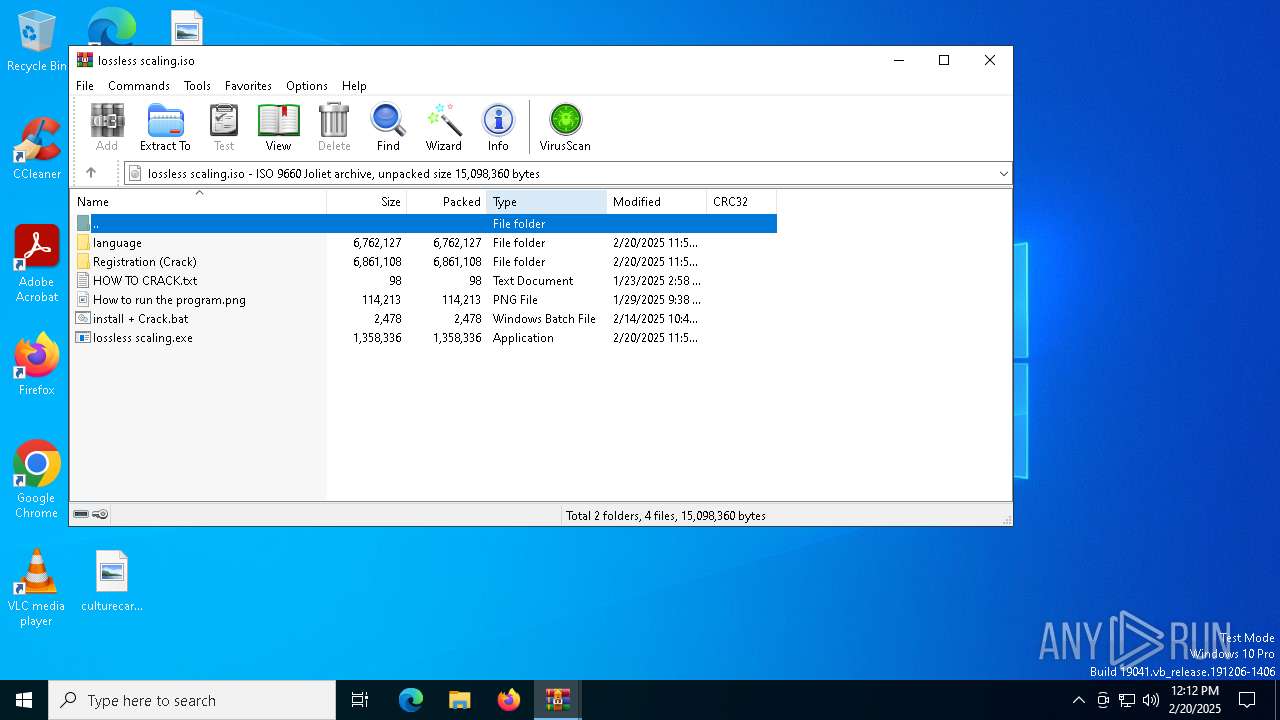
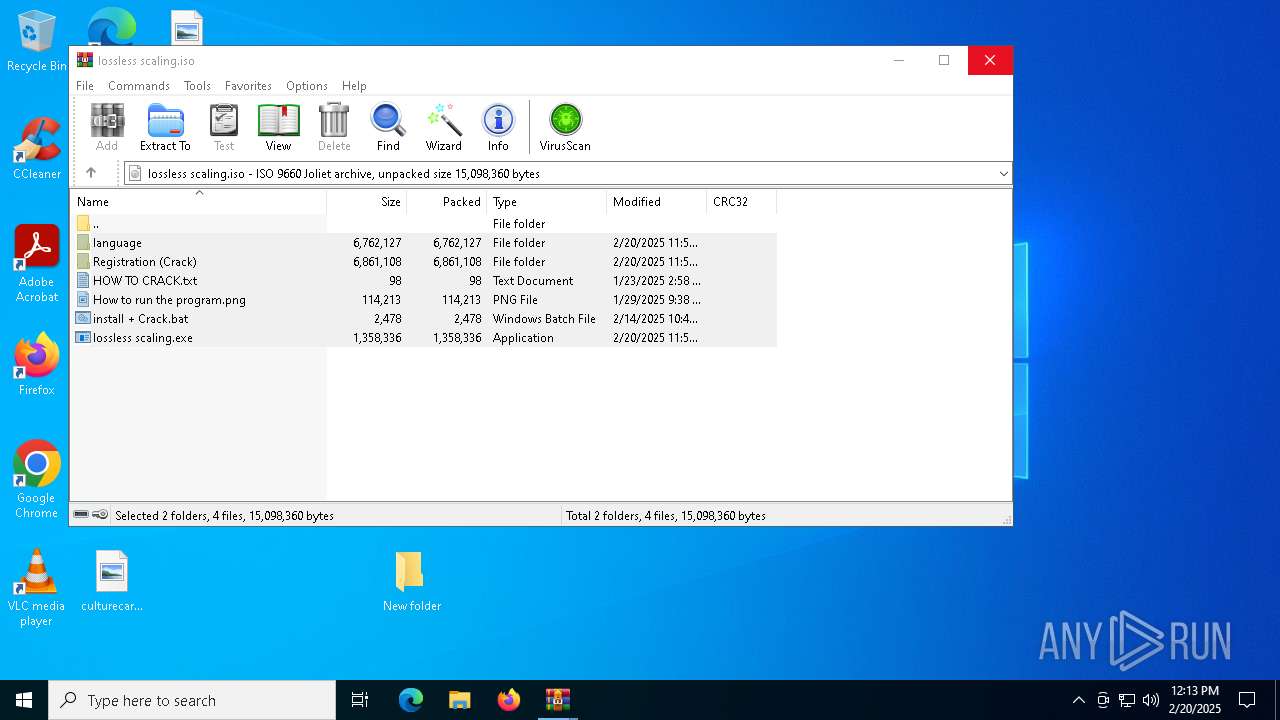
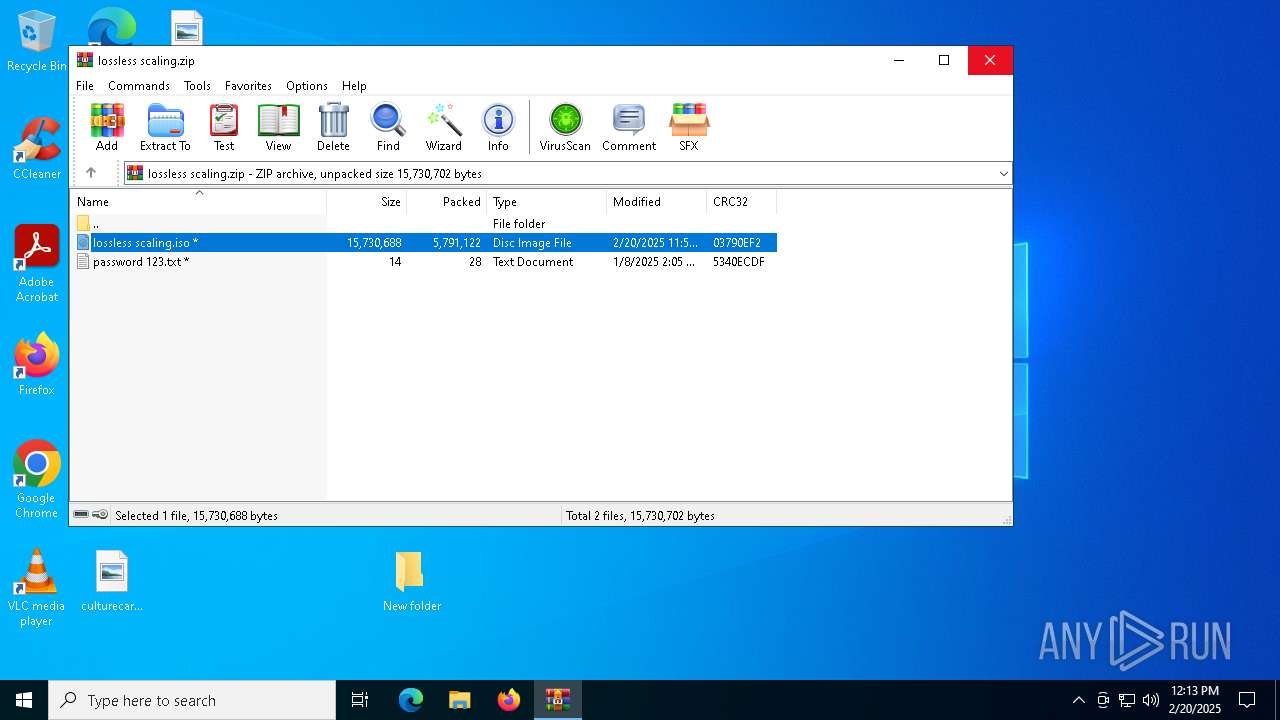
| File name: | lossless scaling.zip |
| Full analysis: | https://app.any.run/tasks/4ae86c39-5bb3-4199-af83-86a16f5f3c73 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | February 20, 2025, 12:12:42 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 65911202A006016ABA7546C0EA9A8328 |
| SHA1: | 3B6B773E4837F62040A437CBCE6E73A8F1599A70 |
| SHA256: | AD75278EE50ABBE9B6B923FFFD1B571040F74ABDE01FC4F274F7F03364E971FC |
| SSDEEP: | 98304:5mF4OoceL1b/6rmyUrxsdYqhNLc/bwR9kPUd7PSx1zs9Cft+OHyxChpqBdwfzSZU:rzsHYVpukN |
MALICIOUS
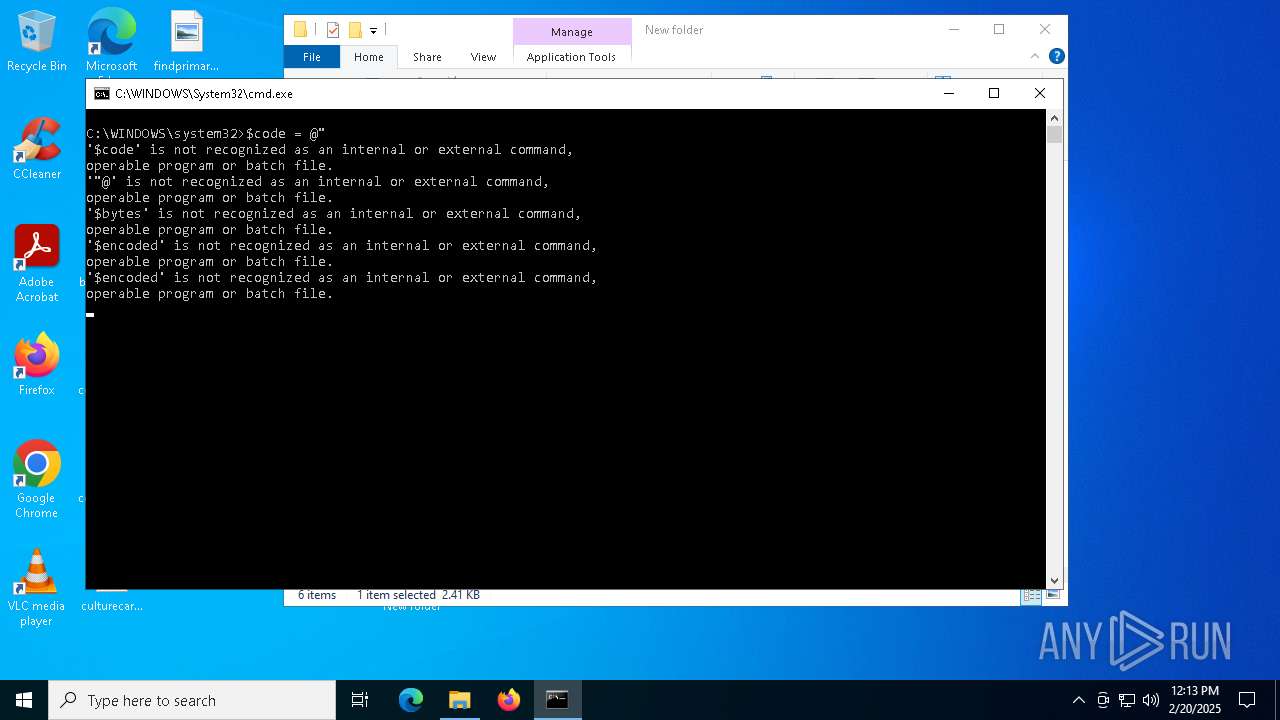
Run PowerShell with an invisible window
- powershell.exe (PID: 3540)
- powershell.exe (PID: 5972)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 3260)
- powershell.exe (PID: 3540)
- wscript.exe (PID: 6872)
- wscript.exe (PID: 6268)
- wscript.exe (PID: 5544)
Bypass execution policy to execute commands
- powershell.exe (PID: 3540)
- powershell.exe (PID: 2828)
- powershell.exe (PID: 2632)
- powershell.exe (PID: 5972)
- powershell.exe (PID: 6180)
- powershell.exe (PID: 1920)
Uses Task Scheduler to run other applications
- powershell.exe (PID: 2828)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 2632)
- powershell.exe (PID: 6180)
- powershell.exe (PID: 1920)
Actions looks like stealing of personal data
- aspnet_compiler.exe (PID: 7156)
ASYNCRAT has been detected (SURICATA)
- aspnet_compiler.exe (PID: 7156)
SUSPICIOUS
Application launched itself
- WinRAR.exe (PID: 4548)
- powershell.exe (PID: 3540)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 4548)
- a.exe (PID: 4512)
- aspnet_compiler.exe (PID: 7156)
Starts NET.EXE to display or manage information about active sessions
- cmd.exe (PID: 3260)
- net.exe (PID: 5252)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 3260)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 3260)
- powershell.exe (PID: 3540)
- wscript.exe (PID: 6872)
- wscript.exe (PID: 6268)
- wscript.exe (PID: 5544)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 3260)
- wscript.exe (PID: 6872)
- wscript.exe (PID: 6268)
- wscript.exe (PID: 5544)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 3540)
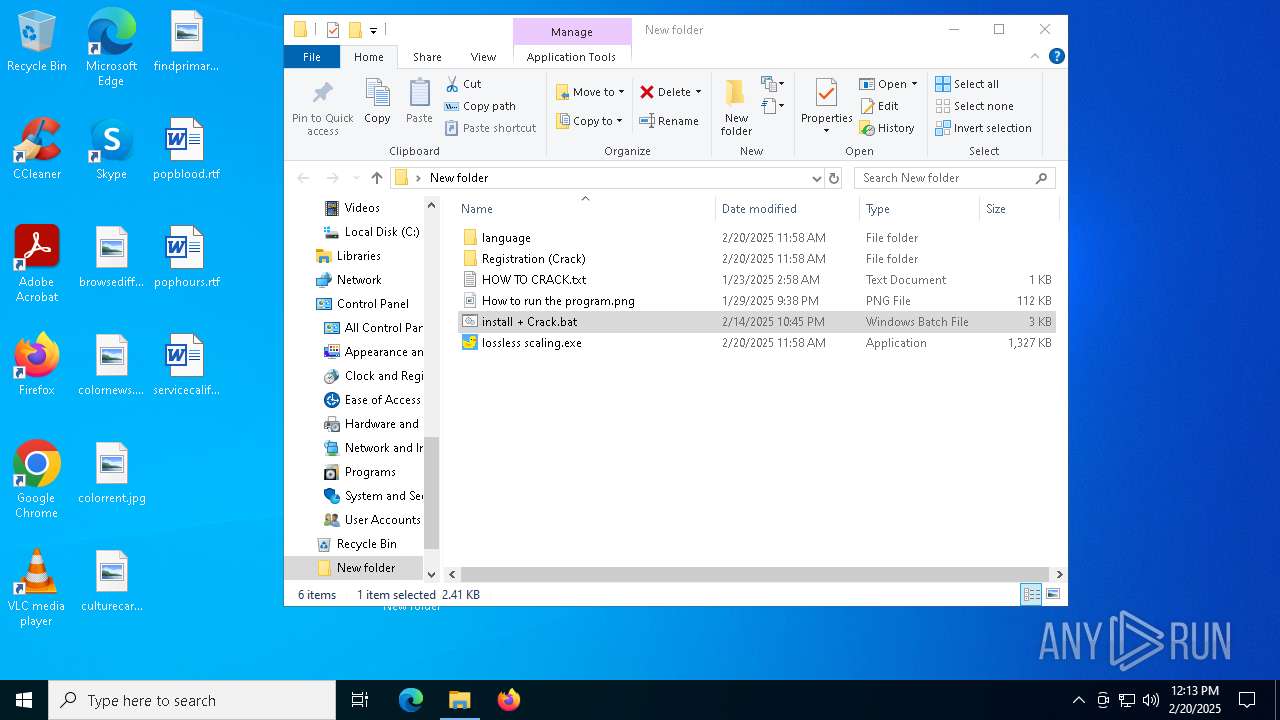
Executable content was dropped or overwritten
- powershell.exe (PID: 2828)
- Dism.exe (PID: 3488)
- vbc.exe (PID: 776)
- aspnet_compiler.exe (PID: 7156)
- msedge.exe (PID: 1544)
Uses REG/REGEDIT.EXE to modify registry
- powershell.exe (PID: 2828)
Gets path to any of the special folders (POWERSHELL)
- powershell.exe (PID: 2828)
- powershell.exe (PID: 2632)
- powershell.exe (PID: 6180)
- powershell.exe (PID: 1920)
The process executes Powershell scripts
- powershell.exe (PID: 3540)
- wscript.exe (PID: 6872)
- wscript.exe (PID: 6268)
- wscript.exe (PID: 5544)
Likely accesses (executes) a file from the Public directory
- RAR.exe (PID: 3536)
- wscript.exe (PID: 6872)
- powershell.exe (PID: 2632)
- schtasks.exe (PID: 5488)
- msedge.exe (PID: 1544)
- wscript.exe (PID: 6268)
- wscript.exe (PID: 736)
- a.exe (PID: 4512)
- cmd.exe (PID: 6504)
- powershell.exe (PID: 6180)
- wscript.exe (PID: 5544)
- powershell.exe (PID: 1920)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 6872)
- wscript.exe (PID: 6268)
- wscript.exe (PID: 5544)
The process executes VB scripts
- powershell.exe (PID: 2828)
- aspnet_compiler.exe (PID: 7156)
Lists all scheduled tasks
- schtasks.exe (PID: 6896)
- schtasks.exe (PID: 6716)
The process verifies whether the antivirus software is installed
- powershell.exe (PID: 2828)
The process creates files with name similar to system file names
- Dism.exe (PID: 3488)
Converts a specified value to an integer (POWERSHELL)
- powershell.exe (PID: 2632)
- powershell.exe (PID: 6180)
- powershell.exe (PID: 1920)
Executes as Windows Service
- VSSVC.exe (PID: 6828)
Searches for installed software
- TiWorker.exe (PID: 6964)
Runs shell command (SCRIPT)
- wscript.exe (PID: 6872)
- wscript.exe (PID: 736)
- wscript.exe (PID: 6268)
- wscript.exe (PID: 5544)
Starts a Microsoft application from unusual location
- DismHost.exe (PID: 1576)
Contacting a server suspected of hosting an CnC
- aspnet_compiler.exe (PID: 7156)
Connects to unusual port
- aspnet_compiler.exe (PID: 7156)
- RegAsm.exe (PID: 6528)
The process executes via Task Scheduler
- powershell.exe (PID: 5972)
- TypeId.exe (PID: 2736)
- wscript.exe (PID: 6268)
- wscript.exe (PID: 5544)
Loads DLL from Mozilla Firefox
- aspnet_compiler.exe (PID: 7156)
There is functionality for taking screenshot (YARA)
- LosslessScaling.exe (PID: 4400)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 736)
The process drops Mozilla's DLL files
- aspnet_compiler.exe (PID: 7156)
Process drops legitimate windows executable
- aspnet_compiler.exe (PID: 7156)
The process drops C-runtime libraries
- aspnet_compiler.exe (PID: 7156)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6800)
The sample compiled with english language support
- WinRAR.exe (PID: 6800)
- powershell.exe (PID: 2828)
- Dism.exe (PID: 3488)
- aspnet_compiler.exe (PID: 7156)
Manual execution by a user
- cmd.exe (PID: 3260)
Checks supported languages
- LosslessScaling.exe (PID: 4400)
- RAR.exe (PID: 3536)
- DismHost.exe (PID: 1576)
- aspnet_compiler.exe (PID: 7156)
- vbc.exe (PID: 776)
- msedge.exe (PID: 1544)
- TypeId.exe (PID: 2736)
- a.exe (PID: 4512)
- aspnet_compiler.exe (PID: 5556)
Reads the computer name
- LosslessScaling.exe (PID: 4400)
- aspnet_compiler.exe (PID: 7156)
- DismHost.exe (PID: 1576)
- vbc.exe (PID: 776)
- TypeId.exe (PID: 2736)
- msedge.exe (PID: 1544)
- aspnet_compiler.exe (PID: 5556)
Reads the machine GUID from the registry
- LosslessScaling.exe (PID: 4400)
- RAR.exe (PID: 3536)
- vbc.exe (PID: 776)
- aspnet_compiler.exe (PID: 7156)
- msedge.exe (PID: 1544)
- TypeId.exe (PID: 2736)
- RegAsm.exe (PID: 6528)
- a.exe (PID: 4512)
LOSSLESSSCALING mutex has been found
- LosslessScaling.exe (PID: 4400)
Creates files or folders in the user directory
- LosslessScaling.exe (PID: 4400)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 2828)
- powershell.exe (PID: 2632)
- powershell.exe (PID: 5972)
- powershell.exe (PID: 6180)
- powershell.exe (PID: 1920)
Creates files in the program directory
- powershell.exe (PID: 2828)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 2828)
- powershell.exe (PID: 2632)
- powershell.exe (PID: 5972)
- powershell.exe (PID: 6180)
- powershell.exe (PID: 1920)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 2828)
Reads Environment values
- DismHost.exe (PID: 1576)
Create files in a temporary directory
- Dism.exe (PID: 3488)
Reads the software policy settings
- aspnet_compiler.exe (PID: 7156)
- vbc.exe (PID: 776)
- TiWorker.exe (PID: 6964)
Process checks computer location settings
- vbc.exe (PID: 776)
- aspnet_compiler.exe (PID: 7156)
Checks proxy server information
- vbc.exe (PID: 776)
Disables trace logs
- vbc.exe (PID: 776)
Manages system restore points
- SrTasks.exe (PID: 5036)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:02:20 03:58:04 |
| ZipCRC: | 0x03790ef2 |
| ZipCompressedSize: | 5791122 |
| ZipUncompressedSize: | 15730688 |
| ZipFileName: | lossless scaling.iso |
Total processes
180
Monitored processes
46
Malicious processes
9
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 424 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 628 | C:\WINDOWS\system32\net1 session | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\Public\External\Components\11.vbs" | C:\Windows\SysWOW64\wscript.exe | — | aspnet_compiler.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 776 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\vbc.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\vbc.exe | aspnet_compiler.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Visual Basic Command Line Compiler Exit code: 0 Version: 14.8.9037.0 Modules
| |||||||||||||||
| 1200 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1228 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1544 | "C:\Users\Public\msedge.exe" | C:\Users\Public\msedge.exe | vbc.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1572 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1576 | C:\Users\admin\AppData\Local\Temp\0190B358-AEE7-460E-9391-438F56B5FE8E\dismhost.exe {838B5575-3AB2-45C3-BC4B-4B825B9CA60B} | C:\Users\admin\AppData\Local\Temp\0190B358-AEE7-460E-9391-438F56B5FE8E\DismHost.exe | Dism.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Dism Host Servicing Process Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1920 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ExecutionPolicy Bypass iex([IO.File]::ReadAllText('C:\Users\Public\IObitUnlocker\Report.ps1')) | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
89 677
Read events
89 119
Write events
414
Delete events
144
Modification events
| (PID) Process: | (4548) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4548) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4548) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4548) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\lossless scaling.zip | |||
| (PID) Process: | (4548) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4548) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4548) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4548) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4548) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (6800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
Executable files
162
Suspicious files
1 370
Text files
1 422
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4548 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb4548.38118\lossless scaling.iso | — | |
MD5:— | SHA256:— | |||
| 6800 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6800.40875\language\en-US\UK.dll | text | |
MD5:B573EB820A0233ACBA7B6E33D1D8ED28 | SHA256:919C8006BCF5C03AC8B4D83DFC824E4F918A6D3D2FCABD6BD905494EC79513AE | |||
| 6800 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6800.40875\language\en-US\Devn.exe | executable | |
MD5:857F8A07B6C9AD9BD3BB6E4C047FEE45 | SHA256:7083023D5BA4768A6398A92DFC6F8A7556EFBEAFB6A4D60347AEA0F69B2E89AF | |||
| 6800 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6800.40875\language\en-US\RU.dll | text | |
MD5:83BF9BA8BECAC139CB05C1AB68468E62 | SHA256:7BFD69BDD83904D39A4E09C55FE6E380F027A2F13593C167ACF92160BB9CF125 | |||
| 6800 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6800.40875\language\en-US\Lan.vbs | text | |
MD5:49AF07D132592C9A62EAAEF421E3E589 | SHA256:487985D63734CD4828EAF03284E0D1D2FA684AFC2D46DA489C99D498F31A83AB | |||
| 6800 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6800.40875\language\en-US\EN.dll | compressed | |
MD5:6A3A38B32089B21D7D696E215FCD7B60 | SHA256:5E086E3E03BC5A6561EFF58BE1D04BB4A5458F1FD8A0C25E0A1E6277FFB55337 | |||
| 6800 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6800.40875\language\diagerr.xml | csv | |
MD5:44317C4008BFB84314D098A68944A0D6 | SHA256:DD43C2C0A8F53036AA4B346DE52DA6C0254C4747D129FE4130ECE4E078BB0A10 | |||
| 6800 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6800.40875\language\en-US\HKCU.ps1 | text | |
MD5:61784C5B761FD222F9FC4CD0AAD1CE94 | SHA256:C3B21F00FB1451AAE184E534311BD368B5677B61DA75E52DF7C9DBAD7BCF5BE0 | |||
| 6800 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6800.40875\Registration (Crack)\language\diagerr.xml | csv | |
MD5:44317C4008BFB84314D098A68944A0D6 | SHA256:DD43C2C0A8F53036AA4B346DE52DA6C0254C4747D129FE4130ECE4E078BB0A10 | |||
| 6800 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6800.40875\lossless scaling.exe | executable | |
MD5:8B804C81839F1016F5317FCACC47E4E8 | SHA256:9D30E1B24E18184798267B67872BFF48FD79CB7FFD120B8642ECF8FA0B33B996 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
46
DNS requests
24
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4308 | svchost.exe | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4308 | svchost.exe | GET | 200 | 23.222.10.99:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.222.10.99:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6436 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6960 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6960 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3040 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.19.11.120:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
4308 | svchost.exe | 2.19.11.120:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.222.10.99:80 | www.microsoft.com | AKAMAI-AS | US | whitelisted |
4308 | svchost.exe | 23.222.10.99:80 | www.microsoft.com | AKAMAI-AS | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4308 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 2.23.227.208:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.kozow .com Domain |
7156 | aspnet_compiler.exe | Domain Observed Used for C2 Detected | REMOTE [ANY.RUN] AsyncRAT SSL certificate |
7156 | aspnet_compiler.exe | Domain Observed Used for C2 Detected | ET MALWARE Generic AsyncRAT/zgRAT Style SSL Cert |
7156 | aspnet_compiler.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Malicious SSL Cert (AsyncRAT Server) |
7156 | aspnet_compiler.exe | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] AsyncRAT Successful Connection |
2192 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.ddnsgeek .com Domain |
Process | Message |
|---|---|
Dism.exe | PID=3488 TID=3912 Provider has not previously been encountered. Attempting to initialize the provider. - CDISMProviderStore::Internal_GetProvider |
Dism.exe | PID=3488 TID=3912 Attempting to initialize the logger from the Image Session. - CDISMProviderStore::Final_OnConnect |
Dism.exe | PID=3488 TID=3912 Initializing a provider store for the LOCAL session type. - CDISMProviderStore::Final_OnConnect |
Dism.exe | PID=3488 TID=3912 Loading Provider from location C:\WINDOWS\system32\Dism\LogProvider.dll - CDISMProviderStore::Internal_GetProvider |
Dism.exe | PID=3488 TID=3912 Instantiating the Provider Store. - CDISMImageSession::get_ProviderStore |
Dism.exe | PID=3488 TID=3912 Connecting to the provider located at C:\WINDOWS\system32\Dism\LogProvider.dll. - CDISMProviderStore::Internal_LoadProvider |
DismHost.exe | PID=1576 TID=7080 Disconnecting the provider store - CDISMImageSession::Final_OnDisconnect |
DismHost.exe | PID=1576 TID=7080 Disconnecting Provider: DISMLogger - CDISMProviderStore::Internal_DisconnectProvider |
DismHost.exe | PID=1576 TID=7080 Encountered a loaded provider DISMLogger. - CDISMProviderStore::Internal_DisconnectProvider |
Dism.exe | PID=3488 TID=3912 Disconnecting the provider store - CDISMImageSession::Final_OnDisconnect |