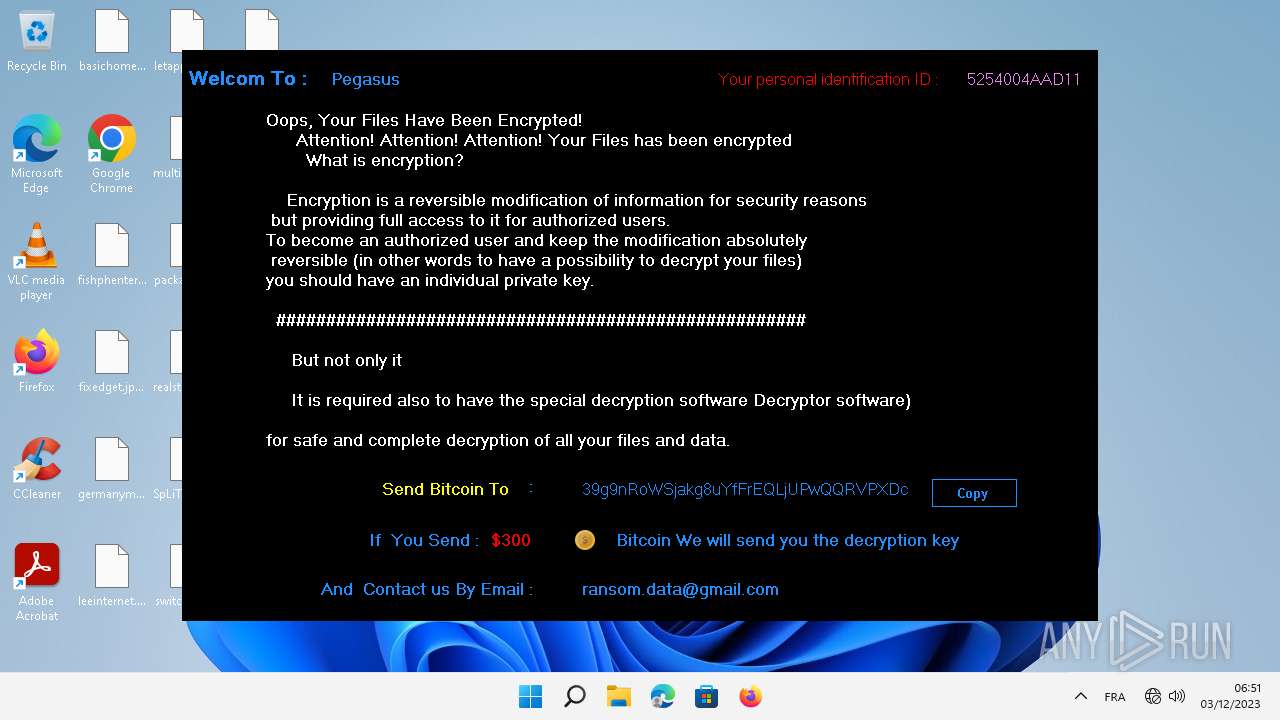
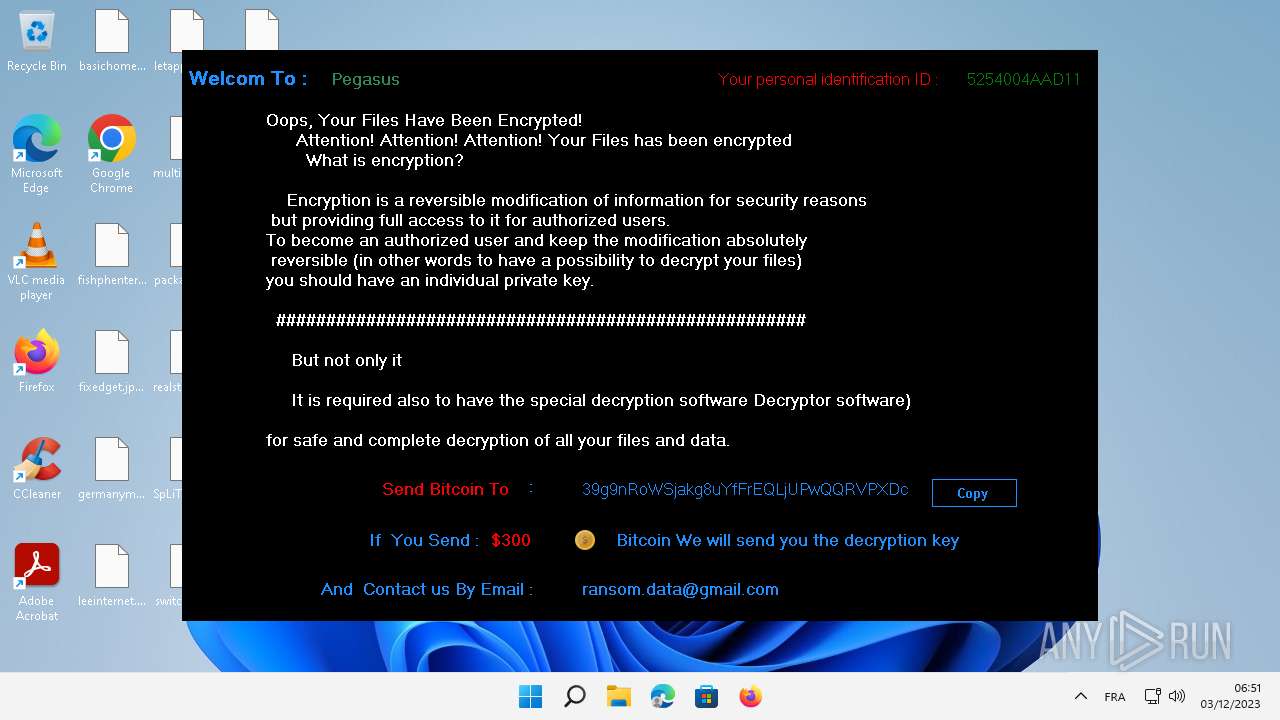
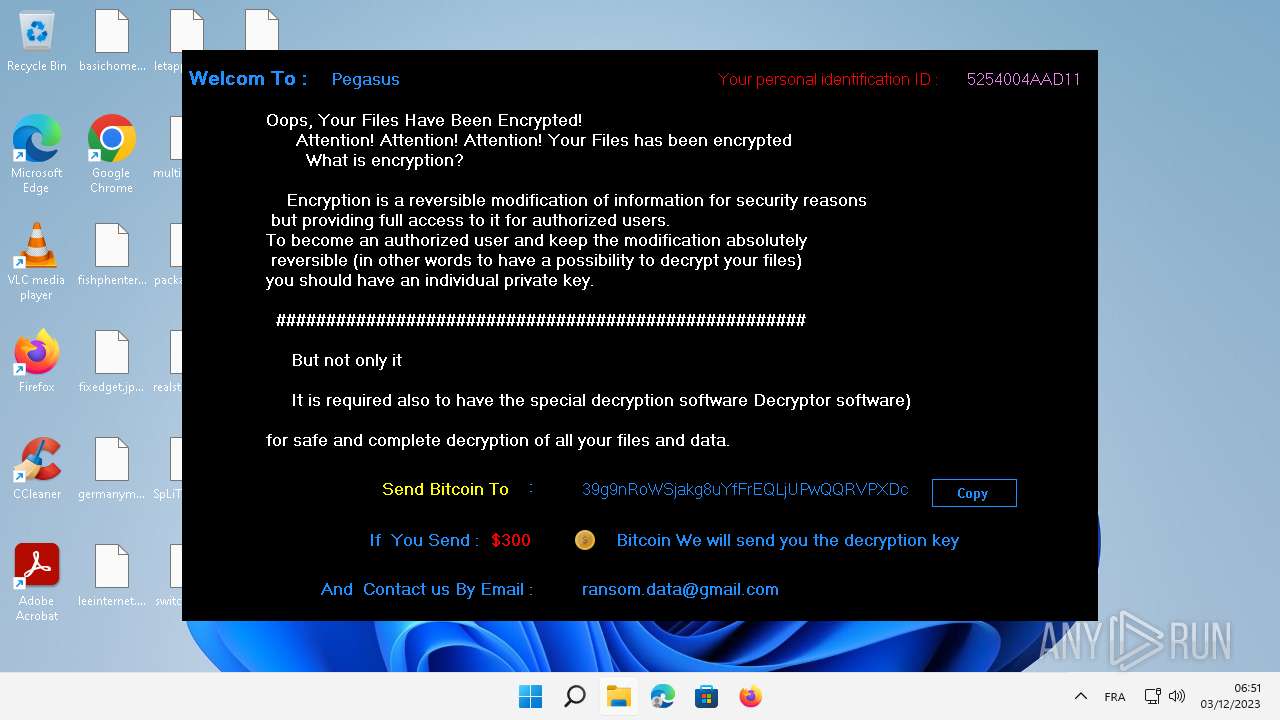
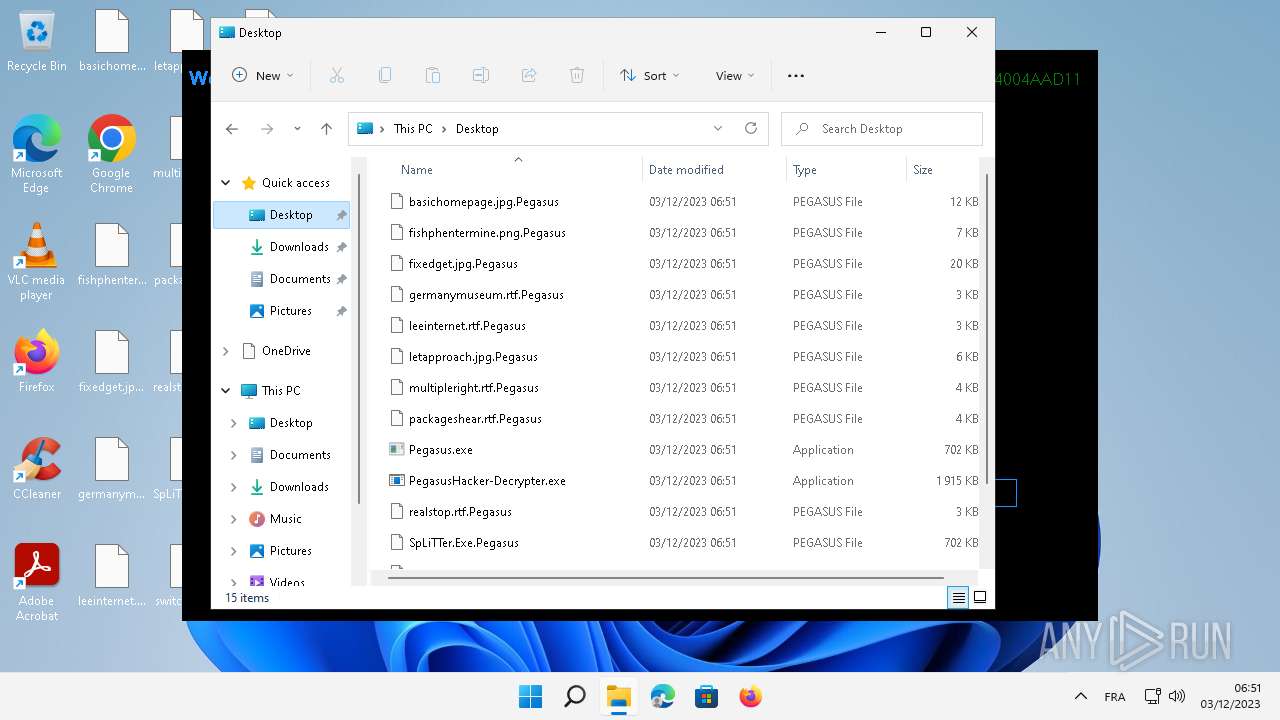
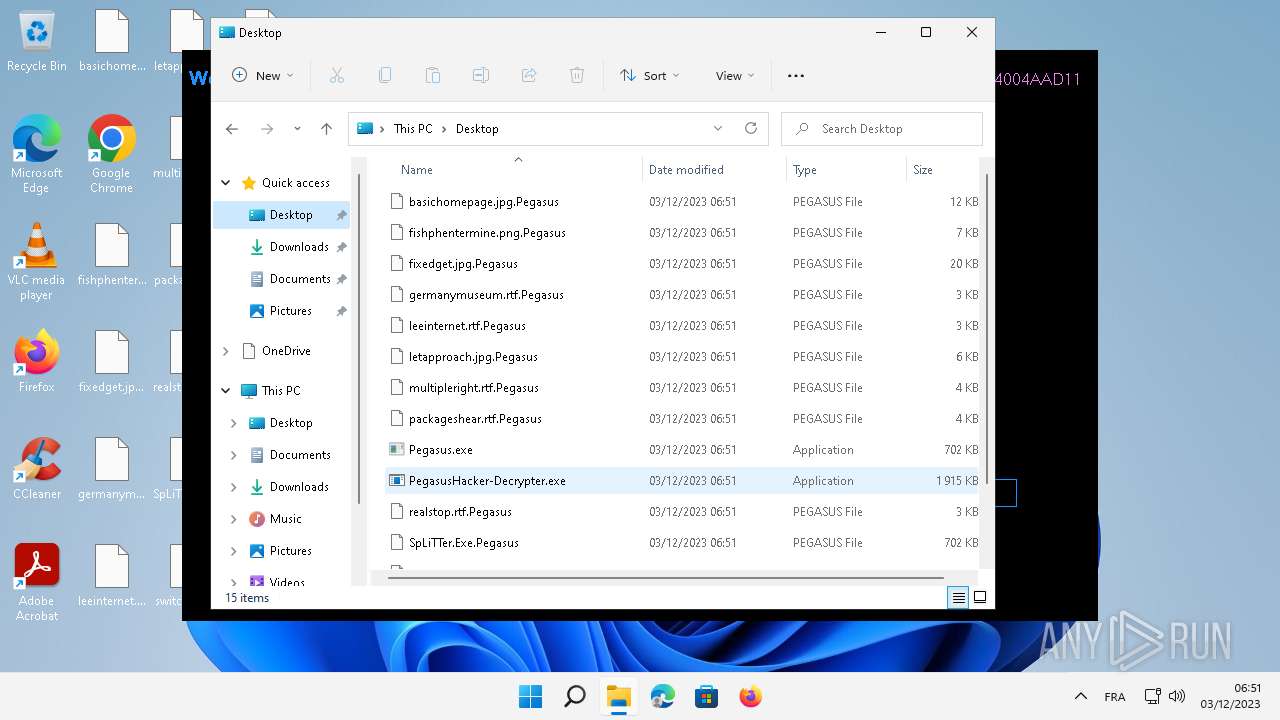
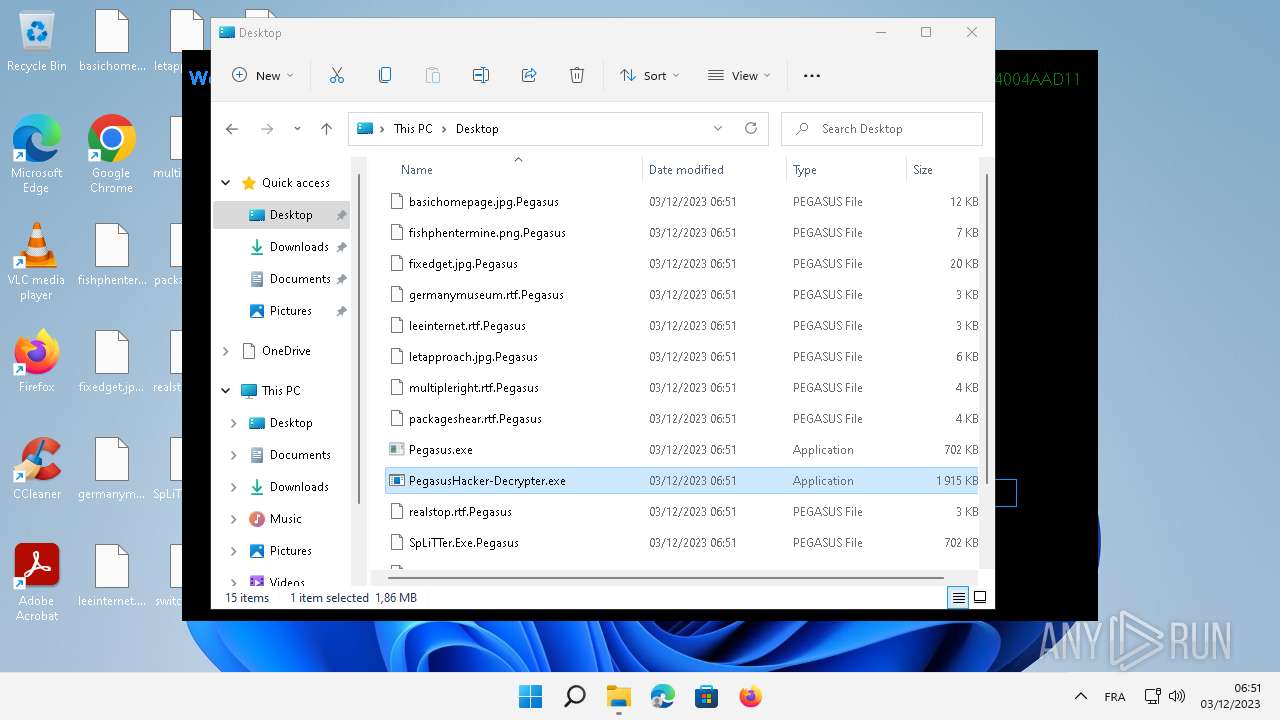
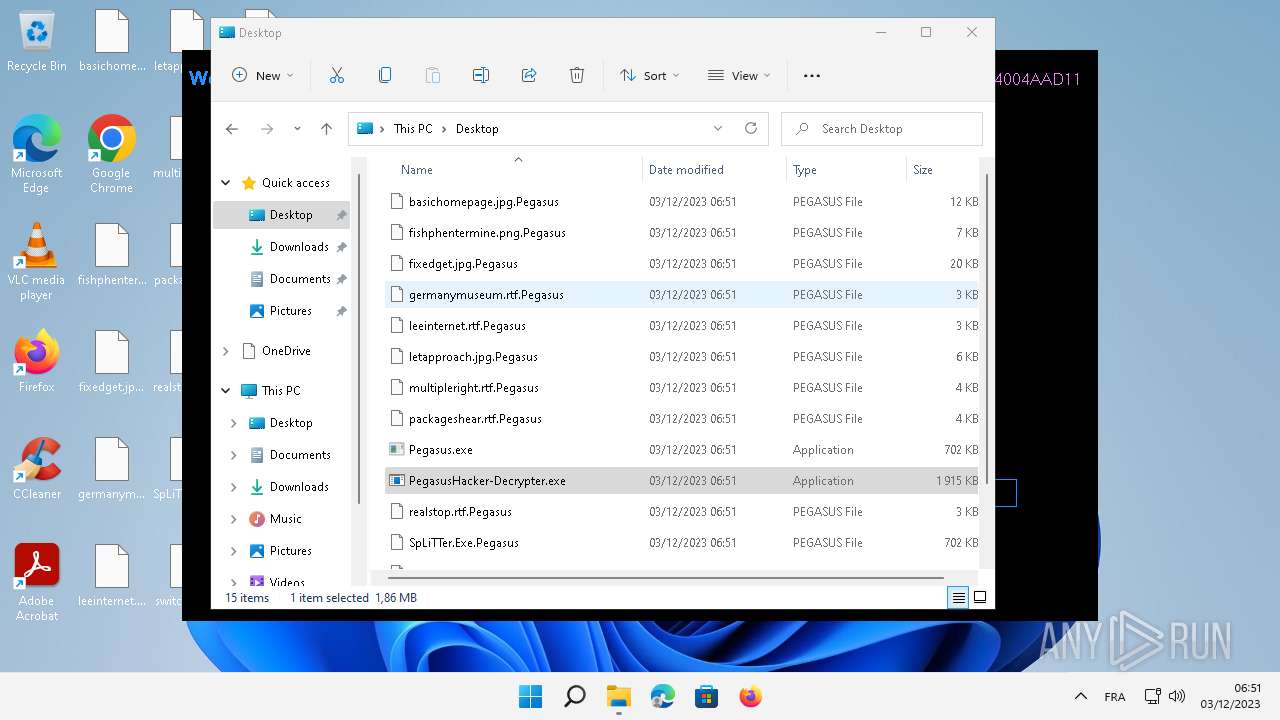
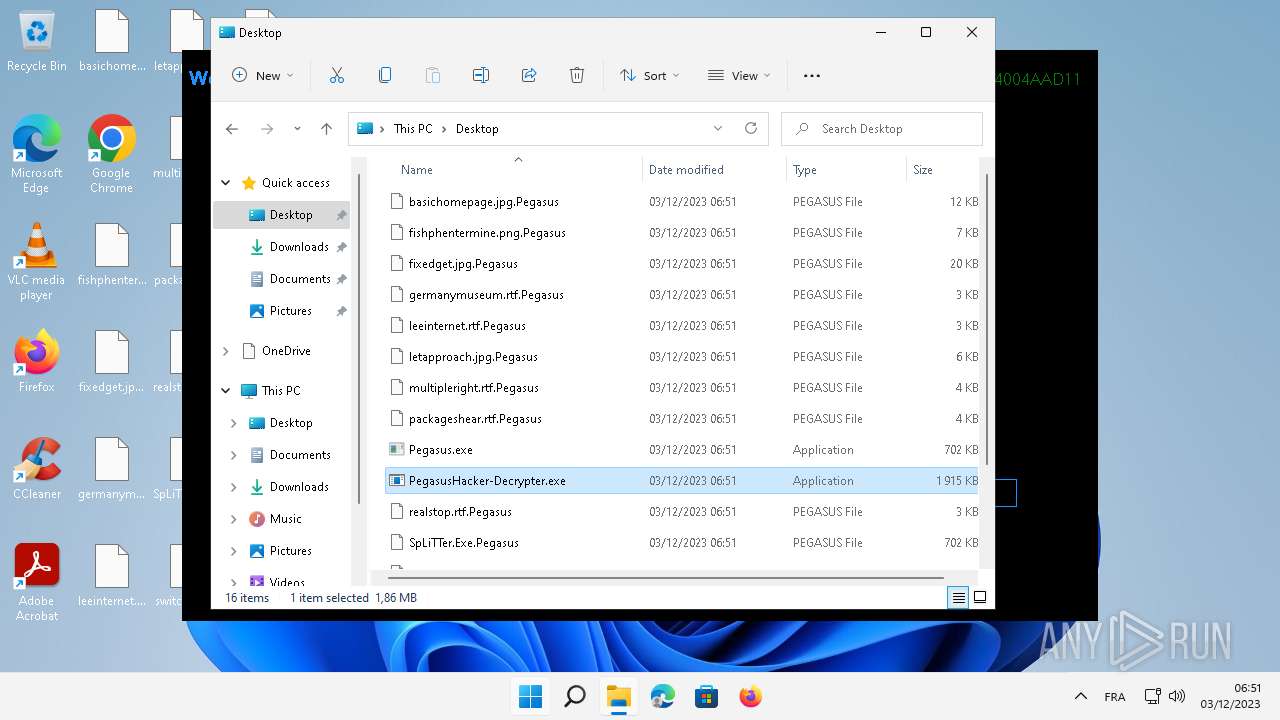
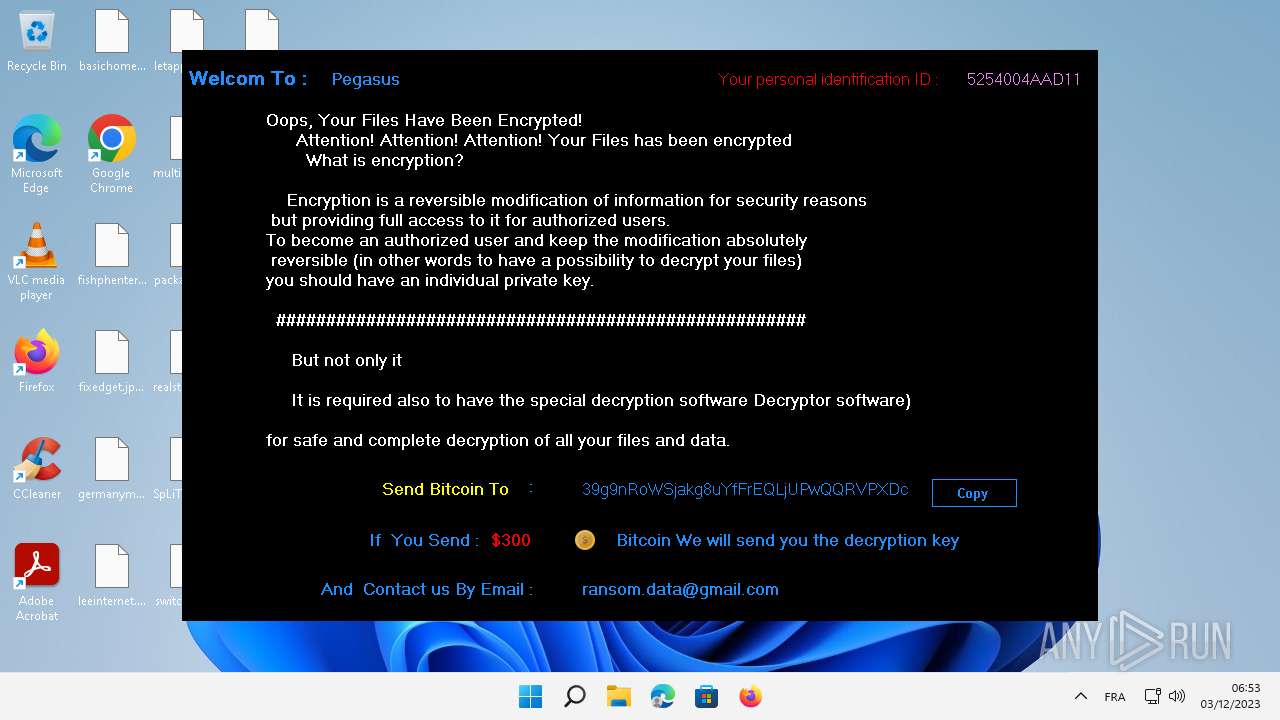
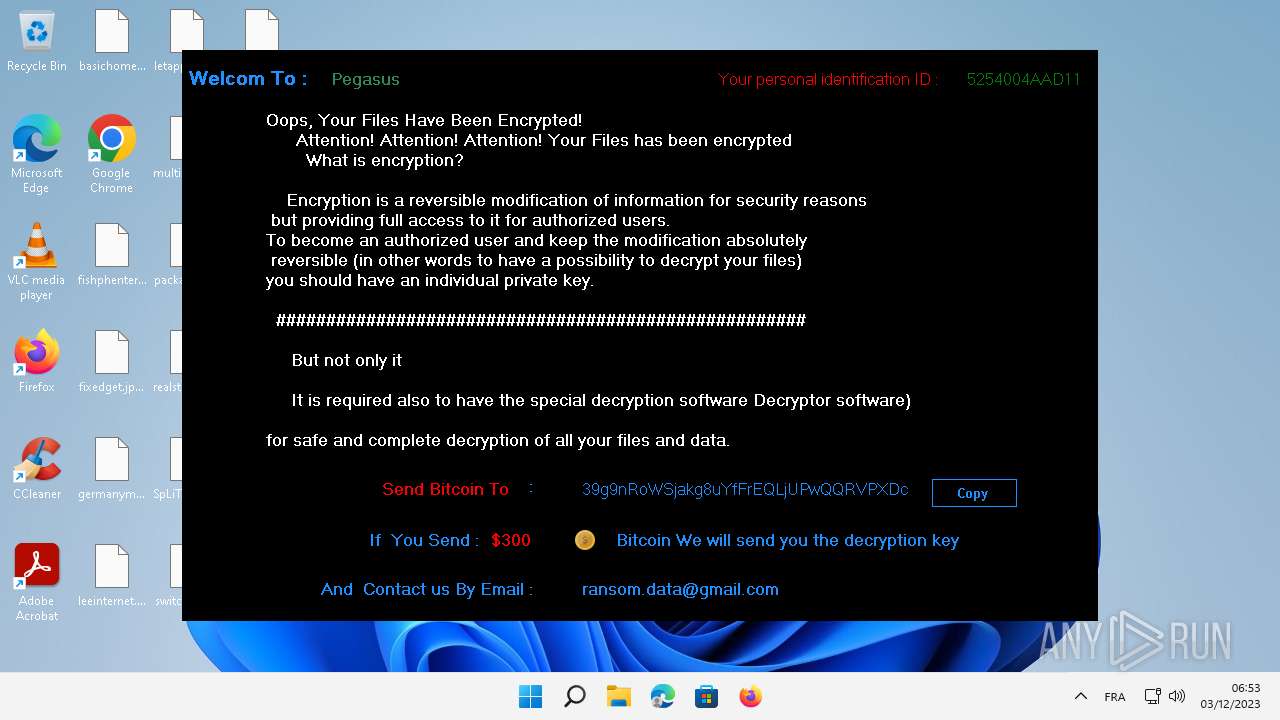
| File name: | Pegasus.exe |
| Full analysis: | https://app.any.run/tasks/a83103e5-b645-4f76-a4a5-ab0dd2490b5d |
| Verdict: | Malicious activity |
| Threats: | Ramnit is a highly modular banking trojan and worm that evolved from a file-infecting virus into a powerful cybercrime tool. It specializes in financial fraud, credential theft, remote access, and malware delivery, being a serious threat to businesses and individuals. First spotted in 2010, Ramnit became popular after the 2014 takedown of the GameOver Zeus botnet, as cybercriminals sought alternatives for banking fraud. |
| Analysis date: | December 03, 2023, 05:50:51 |
| OS: | Windows 11 Professional (build: 22000, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 1FCE09E3A00F05743C8DF2A198FEF3E4 |
| SHA1: | C39475C64560870C64182C50EF40E3F6D358A6B3 |
| SHA256: | AD71B10395D14143396A634F54D8E1066C674B91EB8926952261802972F49093 |
| SSDEEP: | 24576:/QrtStGIg0nq5M/eEEPqf1934J2NaoJxHv5xr51xbPojJtddPRjiV2cA:qtStGIg0nq5M/FESf1934J2NaqHv5xre |
MALICIOUS
Drops the executable file immediately after the start
- Tempexplorer.exe (PID: 4948)
- Pegasus.exe (PID: 5784)
- TempexplorerSrv.exe (PID: 6248)
- Tempexplorer.exe (PID: 6216)
- Pegasus.exe (PID: 5372)
- Tempexplorer.exe (PID: 1048)
- TempexplorerSrv.exe (PID: 3576)
- Tempexplorer.exe (PID: 2116)
Signature: RAMNIT has been detected
- TempexplorerSrv.exe (PID: 6248)
- Tempexplorer.exe (PID: 6216)
Renames files like ransomware
- Pegasus.exe (PID: 5784)
Bypass execution policy to execute commands
- powershell.exe (PID: 6676)
- powershell.exe (PID: 6824)
- powershell.exe (PID: 6200)
- powershell.exe (PID: 6528)
Changes powershell execution policy (Bypass)
- powershell.exe (PID: 6676)
- cmd.exe (PID: 7160)
- cmd.exe (PID: 6544)
- powershell.exe (PID: 6200)
Run PowerShell with an invisible window
- powershell.exe (PID: 6824)
- powershell.exe (PID: 6200)
- powershell.exe (PID: 6676)
- powershell.exe (PID: 6528)
Actions looks like stealing of personal data
- Tempexplorer.exe (PID: 4948)
SUSPICIOUS
Reads the date of Windows installation
- Pegasus.exe (PID: 5784)
- Tempexplorer.exe (PID: 4948)
- Tempspwak.exe (PID: 2072)
- Tempexplorer.exe (PID: 6216)
The process creates files with name similar to system file names
- Tempexplorer.exe (PID: 4948)
- Pegasus.exe (PID: 5784)
Reads the Internet Settings
- Pegasus.exe (PID: 5784)
- Tempexplorer.exe (PID: 4948)
- Tempspwak.exe (PID: 2072)
- Tempexplorer.exe (PID: 6216)
- wscript.exe (PID: 6224)
The process checks if it is being run in the virtual environment
- Pegasus.exe (PID: 5784)
The process executes VB scripts
- Tempspwak.exe (PID: 2072)
- Tempexplorer.exe (PID: 6216)
- Tempspwak.exe (PID: 2280)
- Tempexplorer.exe (PID: 1048)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 6420)
Executes application which crashes
- TempexplorerSrv.exe (PID: 6248)
- TempexplorerSrvSrv.exe (PID: 6272)
- TempexplorerSrv.exe (PID: 3576)
- TempexplorerSrvSrv.exe (PID: 876)
Gets a collection of all available drive names (SCRIPT)
- wscript.exe (PID: 6420)
Gets the drive type (SCRIPT)
- wscript.exe (PID: 6420)
Writes binary data to a Stream object (SCRIPT)
- wscript.exe (PID: 6420)
Starts CMD.EXE for commands execution
- PegasusHacker-Decrypter.exe (PID: 6548)
- PegasusHacker-Decrypter.exe (PID: 7084)
Base64-obfuscated command line is found
- cmd.exe (PID: 6544)
- cmd.exe (PID: 7160)
BASE64 encoded PowerShell command has been detected
- cmd.exe (PID: 6544)
- cmd.exe (PID: 7160)
Application launched itself
- powershell.exe (PID: 6676)
- powershell.exe (PID: 6200)
Starts POWERSHELL.EXE for commands execution
- powershell.exe (PID: 6676)
- cmd.exe (PID: 7160)
- cmd.exe (PID: 6544)
- powershell.exe (PID: 6200)
Uses REG/REGEDIT.EXE to modify registry
- powershell.exe (PID: 6676)
- powershell.exe (PID: 6200)
INFO
Checks supported languages
- Pegasus.exe (PID: 5784)
- Tempexplorer.exe (PID: 4948)
- Tempspwak.exe (PID: 2072)
- Tempexplorer.exe (PID: 6216)
- TempexplorerSrv.exe (PID: 6248)
- TempexplorerSrvSrv.exe (PID: 6272)
Reads the computer name
- Pegasus.exe (PID: 5784)
- Tempexplorer.exe (PID: 4948)
- Tempexplorer.exe (PID: 6216)
- Tempspwak.exe (PID: 2072)
Create files in a temporary directory
- Tempspwak.exe (PID: 2072)
- Tempexplorer.exe (PID: 4948)
- TempexplorerSrv.exe (PID: 6248)
- Tempexplorer.exe (PID: 6216)
Creates files or folders in the user directory
- Pegasus.exe (PID: 5784)
- WerFault.exe (PID: 6436)
- WerFault.exe (PID: 6452)
Reads the machine GUID from the registry
- Pegasus.exe (PID: 5784)
Checks proxy server information
- WerFault.exe (PID: 6436)
- WerFault.exe (PID: 6452)
Reads the Internet Settings
- WerFault.exe (PID: 6436)
- WerFault.exe (PID: 6452)
Manual execution by a user
- PegasusHacker-Decrypter.exe (PID: 6548)
- PegasusHacker-Decrypter.exe (PID: 7084)
- Pegasus.exe (PID: 5372)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (55.8) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (21) |
| .scr | | | Windows screen saver (9.9) |
| .dll | | | Win32 Dynamic Link Library (generic) (5) |
| .exe | | | Win32 Executable (generic) (3.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:10:28 04:49:33+01:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 697856 |
| InitializedDataSize: | 18432 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xac3fe |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.0.0.1 |
| ProductVersionNumber: | 2.0.0.1 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| CompanyName: | Host Process for Windows Services |
| FileDescription: | Host Process for Windows Services |
| FileVersion: | 2.0.0.1 |
| InternalName: | Stubctborgfinrrrrrrrrrrrrrrr.exe |
| LegalCopyright: | |
| OriginalFileName: | Stubctborgfinrrrrrrrrrrrrrrr.exe |
| ProductName: | Host Process for Windows Services |
| ProductVersion: | 2.0.0.1 |
| AssemblyVersion: | 2.0.0.1 |
Total processes
246
Monitored processes
32
Malicious processes
9
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 876 | C:\Users\admin\AppData\Local\Temp\3582-490\TempexplorerSrvSrv.exe | C:\Users\admin\AppData\Local\Temp\3582-490\TempexplorerSrvSrv.exe | TempexplorerSrv.exe | ||||||||||||
User: admin Company: SOFTWIN S.R.L. Integrity Level: MEDIUM Description: BitDefender Management Console Exit code: 3221225477 Version: 106.42.73.61 | |||||||||||||||
| 1048 | "C:\Users\admin\AppData\Local\Temp\3582-490\Tempexplorer.exe" | C:\Users\admin\AppData\Local\Temp\3582-490\Tempexplorer.exe | — | Tempexplorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 | |||||||||||||||
| 1084 | "C:\Windows\System32\wscript.exe" C:\Users\admin\AppData\Local\Temp\E0AB.tmp\spwak.vbs | C:\Windows\SysWOW64\wscript.exe | — | Tempspwak.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 | |||||||||||||||
| 2072 | "C:\Users\admin\AppData\Local\Tempspwak.exe" | C:\Users\admin\AppData\Local\Tempspwak.exe | — | Pegasus.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2116 | "C:\Users\admin\AppData\Local\Tempexplorer.exe" | C:\Users\admin\AppData\Local\Tempexplorer.exe | — | Pegasus.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 | |||||||||||||||
| 2280 | "C:\Users\admin\AppData\Local\Tempspwak.exe" | C:\Users\admin\AppData\Local\Tempspwak.exe | — | Pegasus.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 | |||||||||||||||
| 3576 | C:\Users\admin\AppData\Local\Temp\3582-490\TempexplorerSrv.exe | C:\Users\admin\AppData\Local\Temp\3582-490\TempexplorerSrv.exe | Tempexplorer.exe | ||||||||||||
User: admin Company: SOFTWIN S.R.L. Integrity Level: MEDIUM Description: BitDefender Management Console Exit code: 3221225477 Version: 106.42.73.61 | |||||||||||||||
| 4948 | "C:\Users\admin\AppData\Local\Tempexplorer.exe" | C:\Users\admin\AppData\Local\Tempexplorer.exe | Pegasus.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 5172 | "C:\Windows\System32\wscript.exe" C:\Users\admin\AppData\Local\Temp\E213.tmp\splitterrypted.vbs | C:\Windows\SysWOW64\wscript.exe | — | Tempexplorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 | |||||||||||||||
| 5252 | C:\Windows\SysWOW64\WerFault.exe -u -p 3576 -s 324 | C:\Windows\SysWOW64\WerFault.exe | — | TempexplorerSrv.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.22000.653 (WinBuild.160101.0800) | |||||||||||||||
Total events
6 693
Read events
6 633
Write events
60
Delete events
0
Modification events
| (PID) Process: | (5784) Pegasus.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (5784) Pegasus.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (5784) Pegasus.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (5784) Pegasus.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (4948) Tempexplorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (4948) Tempexplorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (4948) Tempexplorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (4948) Tempexplorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2072) Tempspwak.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2072) Tempspwak.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
11
Suspicious files
103
Text files
676
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5784 | Pegasus.exe | C:\Users\admin\Desktop\SpLiTTer.Exe | executable | |
MD5:1FCE09E3A00F05743C8DF2A198FEF3E4 | SHA256:AD71B10395D14143396A634F54D8E1066C674B91EB8926952261802972F49093 | |||
| 6216 | Tempexplorer.exe | C:\Users\admin\AppData\Local\Temp\3582-490\TempexplorerSrv.exe | executable | |
MD5:47826F2614F1FA90601DC51E40D5C29E | SHA256:947D28E57A71AB35C91B6C3EFC01734191AC2A488985F2554AA5B980EE53F8BE | |||
| 6248 | TempexplorerSrv.exe | C:\Users\admin\AppData\Local\Temp\3582-490\TempexplorerSrvSrv.exe | executable | |
MD5:FF5E1F27193CE51EEC318714EF038BEF | SHA256:FD6C69C345F1E32924F0A5BB7393E191B393A78D58E2C6413B03CED7482F2320 | |||
| 5784 | Pegasus.exe | C:\Users\admin\AppData\Local\Tempspwak.exe | executable | |
MD5:D459AC27CDA1076AF5B93BA8A573B992 | SHA256:C458B39EE9DACFECE49933E4CEAAEAB376448D8D56EB503EA519A8DF8323BCCB | |||
| 6420 | wscript.exe | C:\$Recycle.Bin\S-1-5-21-166304369-59083888-3082702900-1001\desktop.ini.Cyborg Builder Ransomware | text | |
MD5:5E7F31B8864DAF89BE5CE3EA61ED72DF | SHA256:EDC8D36C2DEDF83DA5CA164C40B22D0299C2407133F5024C759B36E7F06DC542 | |||
| 2072 | Tempspwak.exe | C:\Users\admin\AppData\Local\Temp\ECC4.tmp\spwak.vbs | text | |
MD5:E9FFD9F618CBF36AD6C910C161BB8080 | SHA256:020CA4B4574A40418B8AA4C2D74B0488E9D150E8D3F5E56E5C6DCCA6F7DFAAAC | |||
| 5784 | Pegasus.exe | C:\Users\admin\Desktop\germanymuseum.rtf | binary | |
MD5:B0DE921921304295337648D893BF3C63 | SHA256:1267A8178D925D077F8A8EBEE6C3C60440B77B2FC590899AFC9C9D369C4B6B68 | |||
| 5784 | Pegasus.exe | C:\Users\admin\Desktop\basichomepage.jpg | binary | |
MD5:A2F7C07E65C4872CB0BC7BE721B21569 | SHA256:F566B4711EA04162FED8413B722505A5A83590CE5604FBFD1ECA2DA1547C1214 | |||
| 4948 | Tempexplorer.exe | C:\Users\admin\AppData\Local\Temp\3582-490\Tempexplorer.exe | executable | |
MD5:A4D60B143B5FCC68F86B929D73D1880D | SHA256:7A55183D372C4645E8A31389D2813FA12C127389254B7412C225EC413C404044 | |||
| 6216 | Tempexplorer.exe | C:\Users\admin\AppData\Local\Temp\ED51.tmp\splitterrypted.vbs | binary | |
MD5:95101AC14DF74FA38272D4E32BA938D4 | SHA256:B7CE475D2191BE4C4CF75936D3BF3FDC6F973D4C948F86F92A854DEE52DB103B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
23
TCP/UDP connections
72
DNS requests
31
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | POST | 502 | 52.142.223.178:80 | http://dmd.metaservices.microsoft.com/metadata.svc | unknown | html | 183 b | unknown |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | binary | 313 b | unknown |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | binary | 471 b | unknown |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAxq6XzO1ZmDhpCgCp6lMhQ%3D | unknown | binary | 471 b | unknown |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | unknown | binary | 1.47 Kb | unknown |
6452 | WerFault.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?3790eb42f33335ad | unknown | compressed | 4.66 Kb | unknown |
6436 | WerFault.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?8f42e85421524a95 | unknown | compressed | 4.66 Kb | unknown |
6632 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4560 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | unknown |
— | — | 2.16.164.35:80 | — | Akamai International B.V. | NL | unknown |
6452 | WerFault.exe | 13.89.179.12:443 | umwatson.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
6436 | WerFault.exe | 13.89.179.12:443 | umwatson.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
2664 | OfficeC2RClient.exe | 52.109.28.46:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | unknown |
6452 | WerFault.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | unknown |
6436 | WerFault.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | unknown |
6632 | svchost.exe | 40.126.31.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
6632 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
umwatson.events.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
v20.events.data.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
mrodevicemgr.officeapps.live.com |
| whitelisted |
www.msftconnecttest.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
dmd.metaservices.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1396 | svchost.exe | Misc activity | ET INFO Microsoft Connection Test |
— | — | Misc activity | ET INFO Microsoft Connection Test |