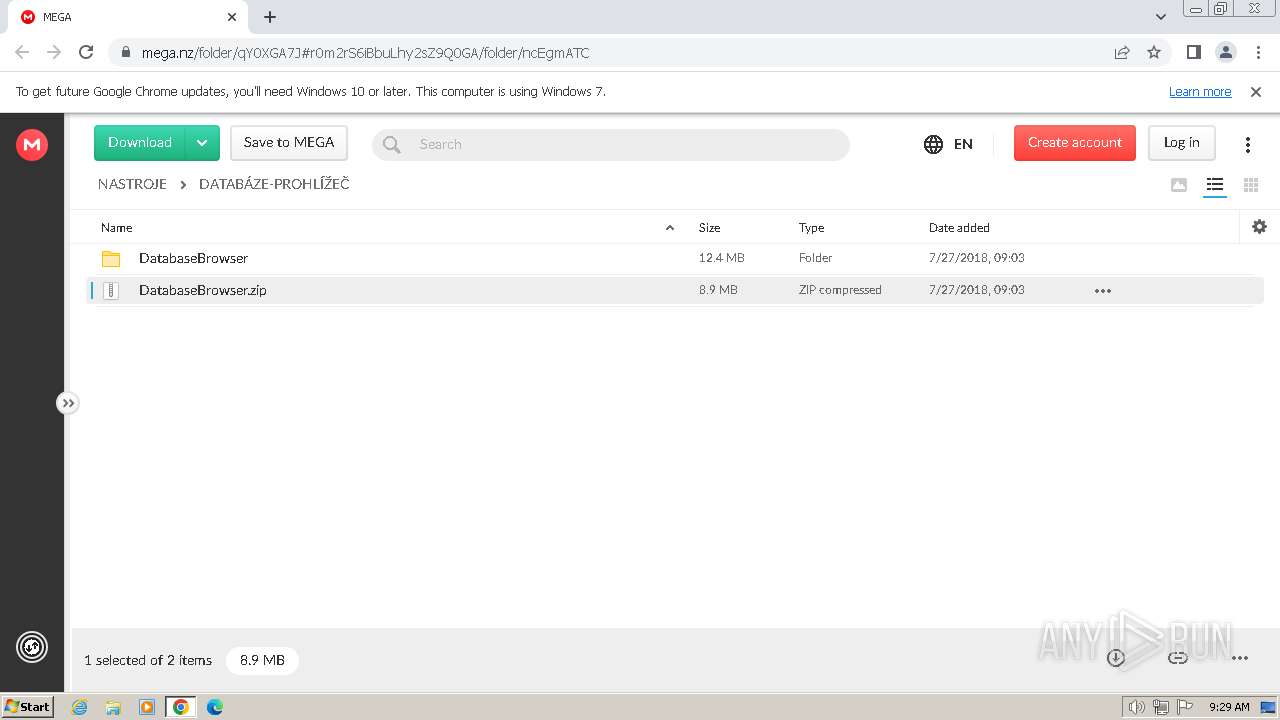
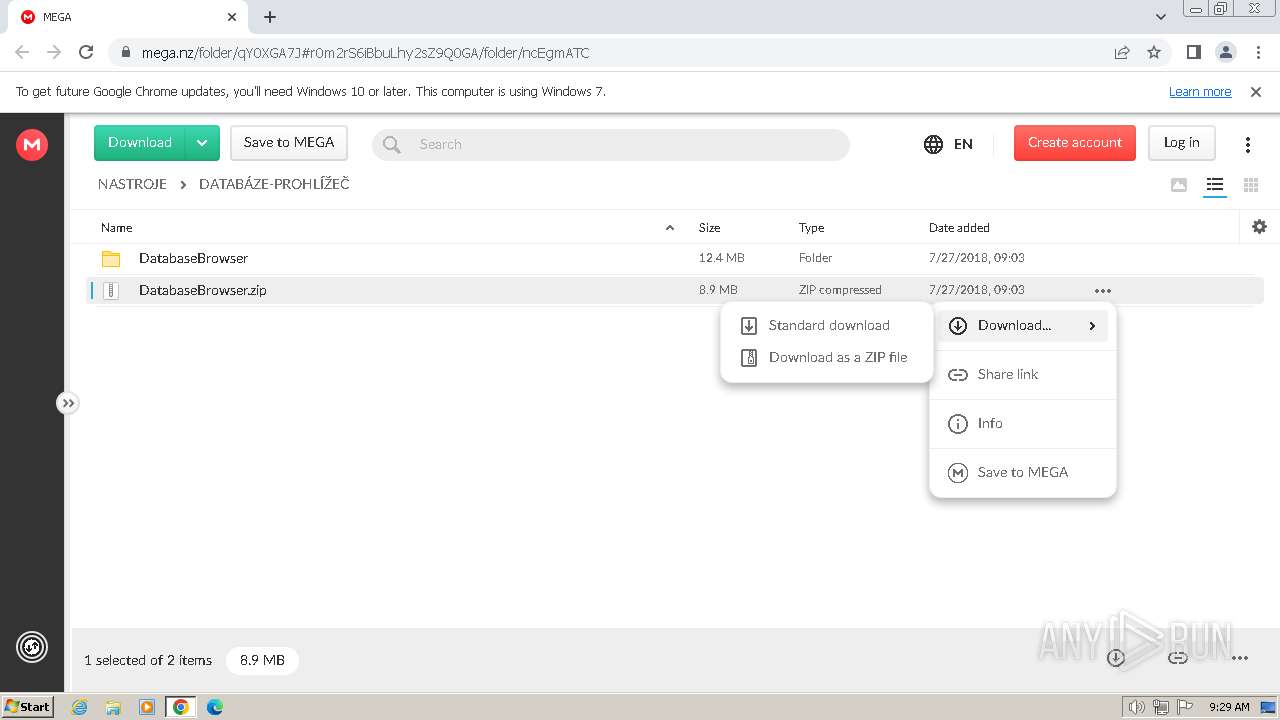
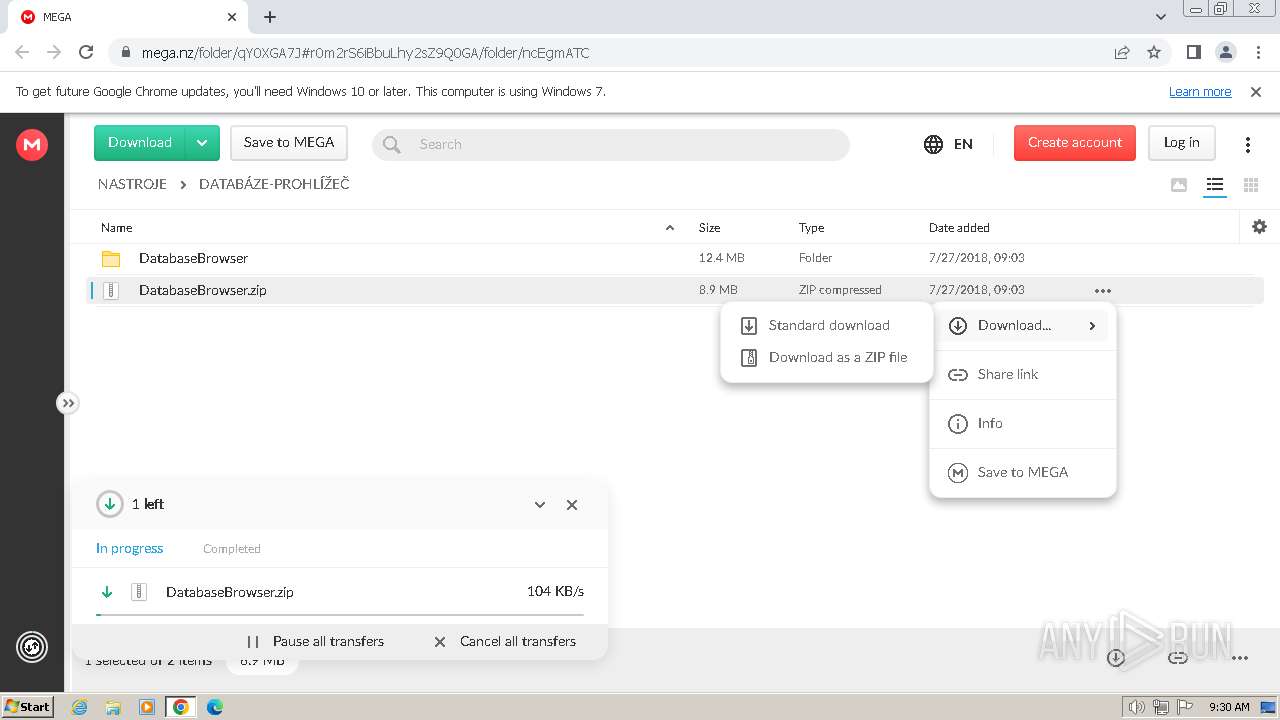
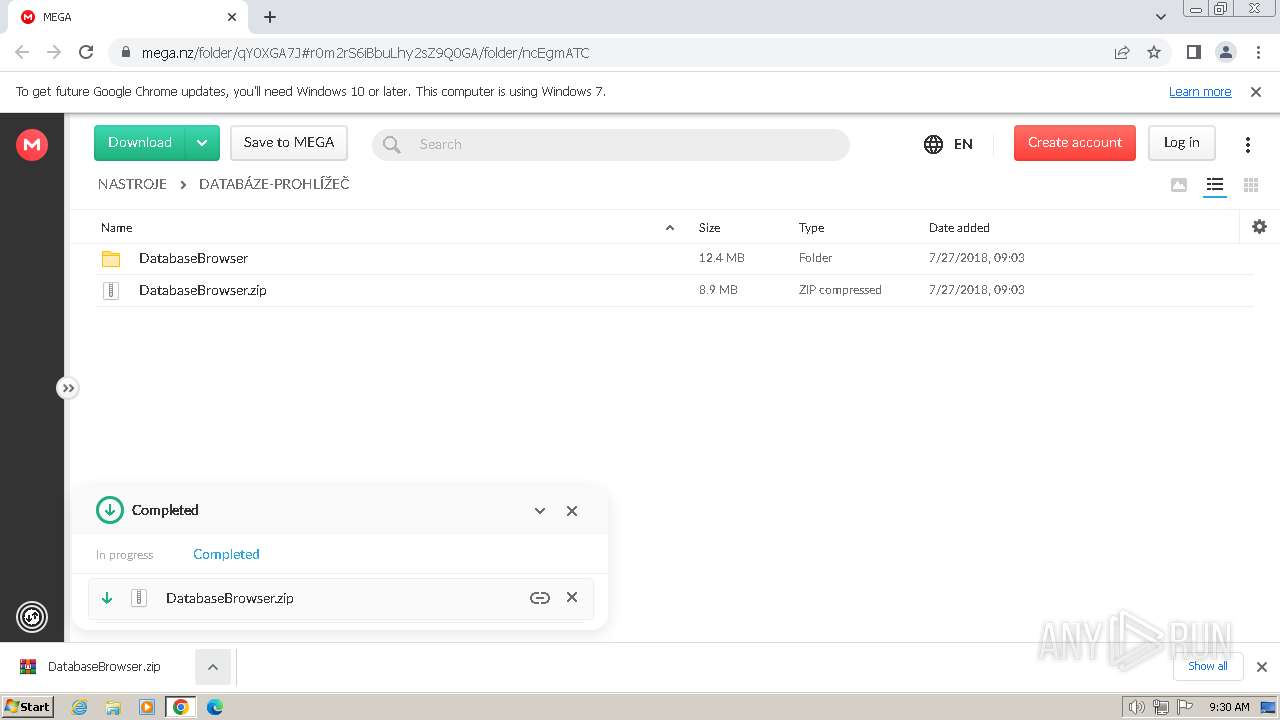
| URL: | https://mega.nz/folder/qY0XGA7J#r0m2rS6iBbuLhy2sZ9Q0GA/file/CVdGnISa |
| Full analysis: | https://app.any.run/tasks/a6f61d40-f62a-4eed-a490-2fdf7dd8dd90 |
| Verdict: | Malicious activity |
| Threats: | Metamorfo is a trojan malware family that has been active since 2018. It remains a top threat, focusing on stealing victims’ financial information, including banking credentials and other data. The malware is known for targeting users in Brazil. |
| Analysis date: | January 07, 2024, 09:29:35 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 63B0E87CB66BD06DB1D65F1996F200C0 |
| SHA1: | A9F01FED5F54E0B84F3D5E50E6869E0FB8DAD6ED |
| SHA256: | AD5158ECB306CA54834E56EDC6AD62E792260FC66E823FAD84E3E9A4769C0B58 |
| SSDEEP: | 3:N8X/iuyKPA8qdc4TwE:268A8qS4TwE |
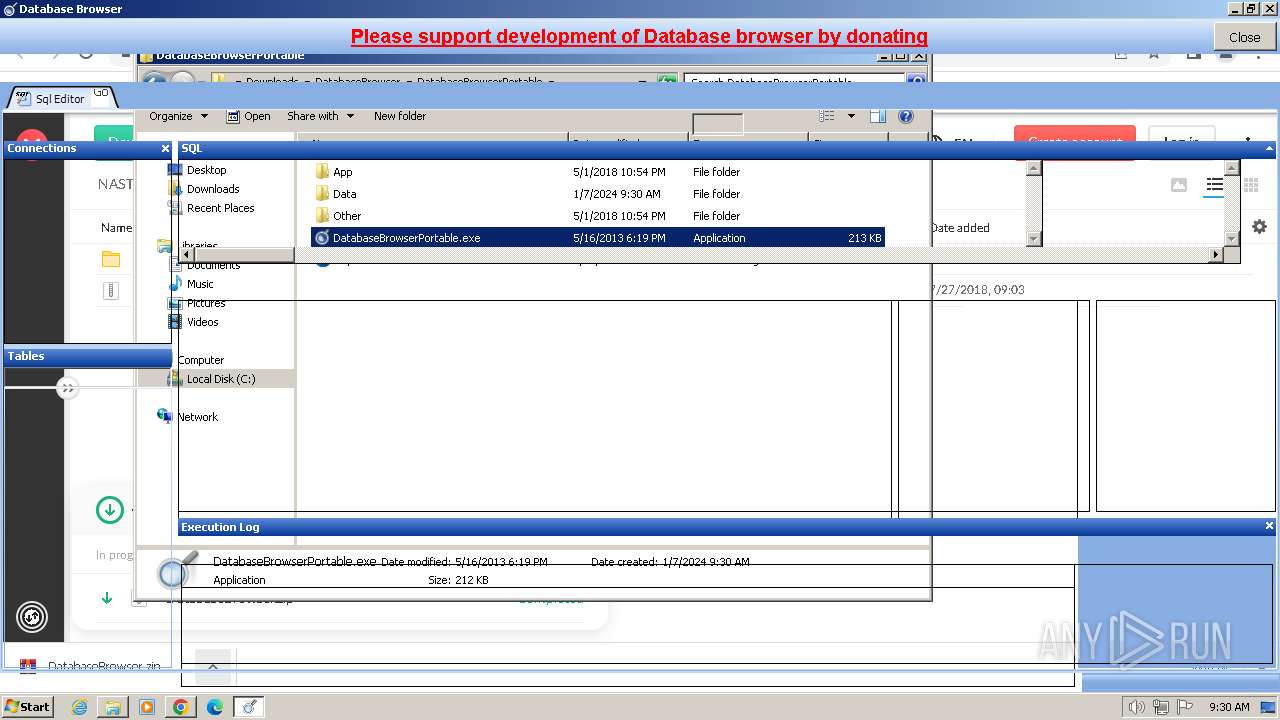
MALICIOUS
METAMORFO has been detected (YARA)
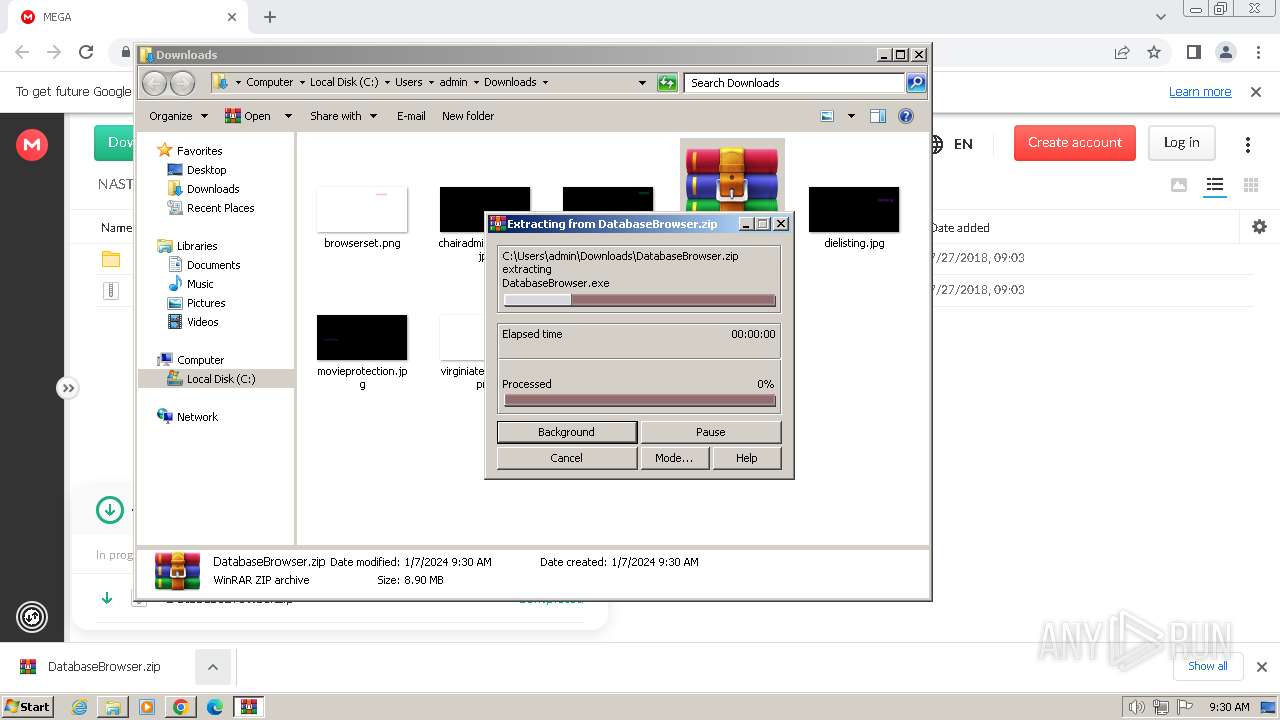
- DatabaseBrowser.exe (PID: 3120)
SUSPICIOUS
The process creates files with name similar to system file names
- DatabaseBrowserPortable.exe (PID: 3100)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 900)
- chrome.exe (PID: 240)
Manual execution by a user
- WinRAR.exe (PID: 900)
- DatabaseBrowserPortable.exe (PID: 3100)
Checks supported languages
- DatabaseBrowserPortable.exe (PID: 3100)
- DatabaseBrowser.exe (PID: 3120)
Reads the computer name
- DatabaseBrowserPortable.exe (PID: 3100)
- DatabaseBrowser.exe (PID: 3120)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 900)
- DatabaseBrowserPortable.exe (PID: 3100)
Create files in a temporary directory
- DatabaseBrowserPortable.exe (PID: 3100)
- DatabaseBrowser.exe (PID: 3120)
Malware-specific behavior (creating "System.dll" in Temp)
- DatabaseBrowserPortable.exe (PID: 3100)
Reads the machine GUID from the registry
- DatabaseBrowserPortable.exe (PID: 3100)
- DatabaseBrowser.exe (PID: 3120)
Application launched itself
- chrome.exe (PID: 1072)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
55
Monitored processes
18
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 240 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=3840 --field-trial-handle=1116,i,1947617097184001191,2097970823900110954,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 480 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgACAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1084 --field-trial-handle=1116,i,1947617097184001191,2097970823900110954,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
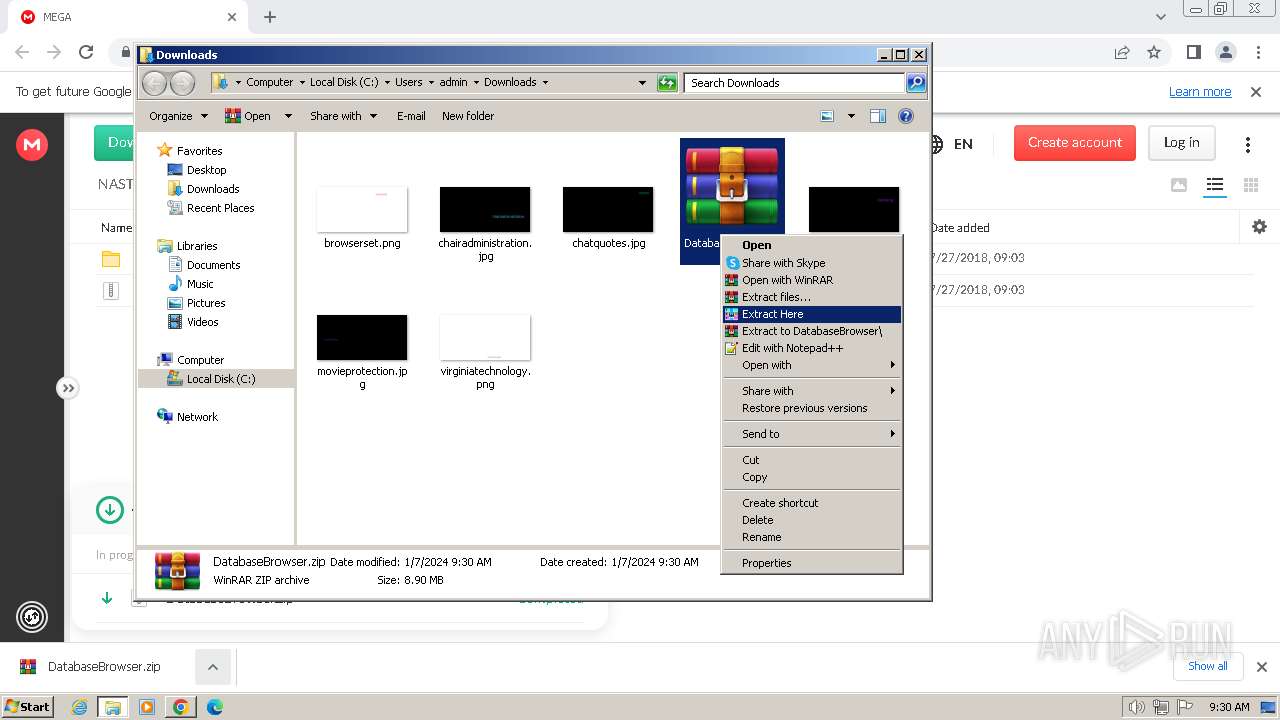
| 900 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Downloads\DatabaseBrowser.zip" C:\Users\admin\Downloads\DatabaseBrowser\ | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 908 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=3336 --field-trial-handle=1116,i,1947617097184001191,2097970823900110954,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1040 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=1260 --field-trial-handle=1116,i,1947617097184001191,2097970823900110954,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1072 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --disk-cache-dir=null --disk-cache-size=1 --media-cache-size=1 --disable-gpu-shader-disk-cache --disable-background-networking --disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints "https://mega.nz/folder/qY0XGA7J#r0m2rS6iBbuLhy2sZ9Q0GA/file/CVdGnISa" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1288 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=109.0.5414.120 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x6e608b38,0x6e608b48,0x6e608b54 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1768 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=audio.mojom.AudioService --lang=en-US --service-sandbox-type=audio --disable-quic --mojo-platform-channel-handle=3512 --field-trial-handle=1116,i,1947617097184001191,2097970823900110954,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1772 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=1504 --field-trial-handle=1116,i,1947617097184001191,2097970823900110954,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1796 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2024 --field-trial-handle=1116,i,1947617097184001191,2097970823900110954,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
Total events
4 645
Read events
4 569
Write events
75
Delete events
1
Modification events
| (PID) Process: | (1072) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (1072) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (1072) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (1072) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (1072) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (1072) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 1 | |||
| (PID) Process: | (1072) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (1072) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (1072) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid_installdate |
Value: 0 | |||
| (PID) Process: | (1072) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid_enableddate |
Value: 0 | |||
Executable files
10
Suspicious files
69
Text files
61
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1072 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RFe13e1.TMP | — | |
MD5:— | SHA256:— | |||
| 1072 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1072 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RFe13e1.TMP | text | |
MD5:05CF4C3C5148DA6355D3561A9EAA5E8A | SHA256:8D720243F6876898E4F197C8867C4CEE69F1C7335C55B8A29C120B1028D93E41 | |||
| 1072 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\metadata\LOG.old | text | |
MD5:4E2B7997F4C3647F8D1ADA88339BBBA5 | SHA256:C33226C460208AA10537A23CB5128FD887DCBAA335C7DC8BFFBE08A607CCFDF5 | |||
| 1072 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Local Storage\leveldb\LOG.old~RFe1633.TMP | text | |
MD5:C383FD120B14BB0E98E99C1BCC9B43F6 | SHA256:56A3A5EACBD28BEE1CF8C1D0052321A5C27EE858BEF7B2FA1DE20806A0823CC1 | |||
| 1072 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:358570F689377CE6838812643E03734B | SHA256:5B41FCC2E1A843AEAB9437B06E27B798870FF10D86A51B163BF48862BCD32590 | |||
| 1072 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RFe1ccb.TMP | — | |
MD5:— | SHA256:— | |||
| 1072 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1072 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Local Storage\leveldb\LOG.old | text | |
MD5:AD0DB8476493577A67FA94A162B646C4 | SHA256:304FB5B4FD83D4A9FF1EF4CF20232A1783169C148297BFE37ED24A1D22A74F2B | |||
| 1072 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\104a7c3d-b432-4f08-b51e-b94d1ff929d8.tmp | binary | |
MD5:5058F1AF8388633F609CADB75A75DC9D | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
52
DNS requests
35
Threats
27
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
856 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad3rm3ciqs3fjr4bc4x5vwuildeq_9.49.1/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.49.1_all_ixzyrcu7pvmgu5pjv6enfqq6wa.crx3 | unknown | — | — | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad3rm3ciqs3fjr4bc4x5vwuildeq_9.49.1/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.49.1_all_ixzyrcu7pvmgu5pjv6enfqq6wa.crx3 | unknown | binary | 5.38 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad3rm3ciqs3fjr4bc4x5vwuildeq_9.49.1/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.49.1_all_ixzyrcu7pvmgu5pjv6enfqq6wa.crx3 | unknown | binary | 10.0 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad3rm3ciqs3fjr4bc4x5vwuildeq_9.49.1/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.49.1_all_ixzyrcu7pvmgu5pjv6enfqq6wa.crx3 | unknown | binary | 9.48 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad3rm3ciqs3fjr4bc4x5vwuildeq_9.49.1/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.49.1_all_ixzyrcu7pvmgu5pjv6enfqq6wa.crx3 | unknown | binary | 9.32 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1040 | chrome.exe | 108.177.15.84:443 | accounts.google.com | GOOGLE | US | unknown |
1072 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1040 | chrome.exe | 31.216.144.5:443 | mega.nz | Datacenter Luxembourg S.A. | LU | unknown |
1040 | chrome.exe | 142.250.186.42:443 | content-autofill.googleapis.com | GOOGLE | US | whitelisted |
1040 | chrome.exe | 66.203.124.37:443 | eu.static.mega.co.nz | Datacenter Luxembourg S.A. | LU | unknown |
1040 | chrome.exe | 66.203.125.12:443 | g.api.mega.co.nz | Datacenter Luxembourg S.A. | LU | unknown |
1040 | chrome.exe | 142.250.186.68:443 | www.google.com | GOOGLE | US | whitelisted |
1072 | chrome.exe | 224.0.0.251:5353 | — | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
accounts.google.com |
| shared |
mega.nz |
| whitelisted |
content-autofill.googleapis.com |
| whitelisted |
eu.static.mega.co.nz |
| shared |
g.api.mega.co.nz |
| shared |
www.google.com |
| whitelisted |
gfs206n174.userstorage.mega.co.nz |
| unknown |
gfs208n165.userstorage.mega.co.nz |
| unknown |
gfs204n166.userstorage.mega.co.nz |
| unknown |
gfs214n160.userstorage.mega.co.nz |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1040 | chrome.exe | Misc activity | ET INFO File Sharing Related Domain in DNS Lookup (mega .nz) |
1040 | chrome.exe | Misc activity | ET INFO File Sharing Related Domain in DNS Lookup (mega .nz) |
1040 | chrome.exe | Misc activity | ET INFO File Sharing Domain Observed in TLS SNI (mega .nz) |
1040 | chrome.exe | Misc activity | ET INFO Observed DNS Query to Filesharing Service (mega .co .nz) |
1040 | chrome.exe | Misc activity | ET INFO Observed DNS Query to Filesharing Service (mega .co .nz) |
1040 | chrome.exe | Misc activity | ET INFO File Sharing Domain Observed in TLS SNI (mega .nz) |
1040 | chrome.exe | Misc activity | ET INFO Observed DNS Query to Filesharing Service (mega .co .nz) |
1040 | chrome.exe | Misc activity | ET INFO Observed DNS Query to Filesharing Service (mega .co .nz) |
1040 | chrome.exe | Misc activity | ET INFO File Sharing Domain Observed in TLS SNI (mega .nz) |
1040 | chrome.exe | Misc activity | ET INFO File Sharing Domain Observed in TLS SNI (mega .nz) |