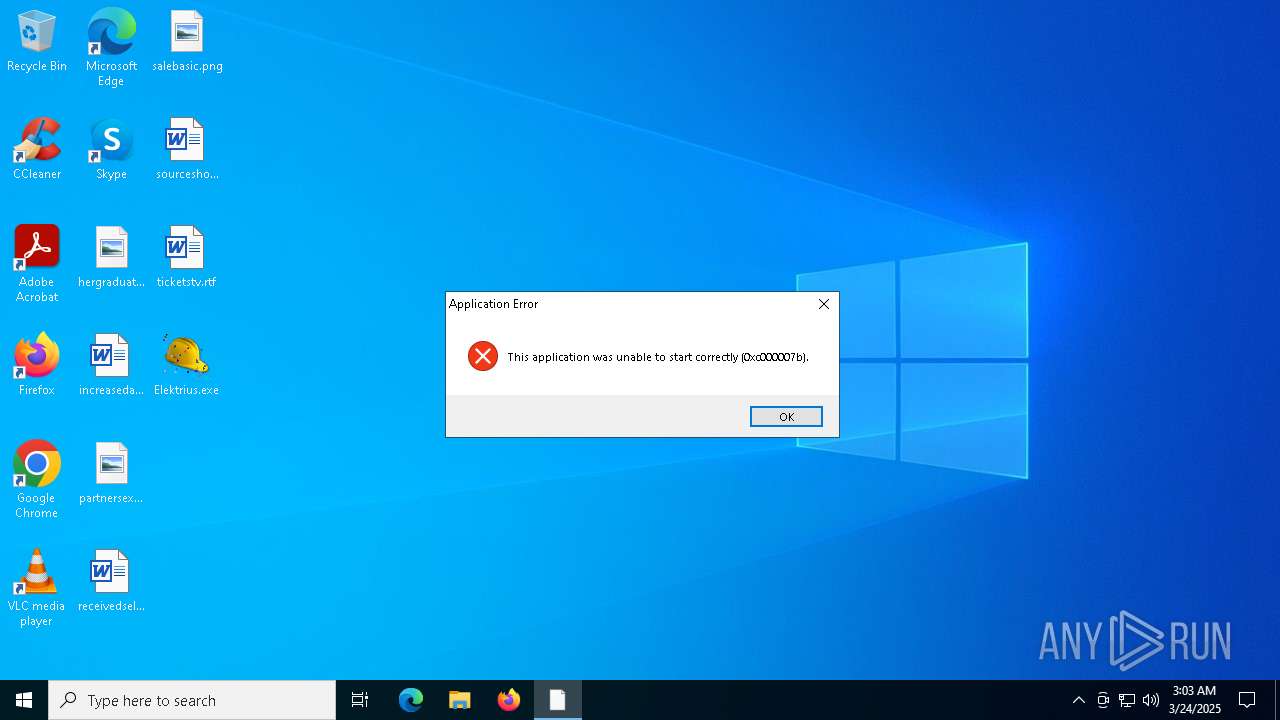
| File name: | Elektrius.exe |
| Full analysis: | https://app.any.run/tasks/e36e3d58-4805-4e0f-a546-a671d3e602ac |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | March 24, 2025, 03:02:57 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | 1A73ED0DE709E84C1D853FE2DB12480D |
| SHA1: | 33C0A0FA66B6E2AD4611580492171E12F4DEC2F7 |
| SHA256: | AD26040171AD3CF68F4DB6C3E72D177518008BF93467503C22D501267D1A1293 |
| SSDEEP: | 49152:paYikUgDXKjRcr/SHq9luGdXsPMdirhgAwsMBjI5OnZcaXvfF+jSLgBATOOUqaSs:3XX/SKDvOXh0/JlnZLv9DgBATOFqaS1m |
MALICIOUS
AutoIt loader has been detected (YARA)
- Castle.com (PID: 4400)
LUMMA mutex has been found
- Castle.com (PID: 4400)
Actions looks like stealing of personal data
- Castle.com (PID: 4400)
Steals credentials from Web Browsers
- Castle.com (PID: 4400)
SUSPICIOUS
Reads security settings of Internet Explorer
- Elektrius.exe (PID: 5112)
Get information on the list of running processes
- cmd.exe (PID: 6644)
Starts CMD.EXE for commands execution
- Elektrius.exe (PID: 5112)
- cmd.exe (PID: 6644)
Executing commands from a ".bat" file
- Elektrius.exe (PID: 5112)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 6644)
Application launched itself
- cmd.exe (PID: 6644)
Starts the AutoIt3 executable file
- cmd.exe (PID: 6644)
The executable file from the user directory is run by the CMD process
- Castle.com (PID: 4400)
Starts application with an unusual extension
- cmd.exe (PID: 6644)
There is functionality for taking screenshot (YARA)
- Castle.com (PID: 4400)
Searches for installed software
- Castle.com (PID: 4400)
INFO
Reads the computer name
- Elektrius.exe (PID: 5112)
- extrac32.exe (PID: 6032)
- Castle.com (PID: 4400)
Checks supported languages
- expand.exe (PID: 4696)
- Elektrius.exe (PID: 5112)
- extrac32.exe (PID: 6032)
- Castle.com (PID: 4400)
Create files in a temporary directory
- Elektrius.exe (PID: 5112)
- expand.exe (PID: 4696)
- extrac32.exe (PID: 6032)
Process checks computer location settings
- Elektrius.exe (PID: 5112)
Creates a new folder
- cmd.exe (PID: 2564)
Reads the machine GUID from the registry
- Castle.com (PID: 4400)
Reads the software policy settings
- Castle.com (PID: 4400)
- slui.exe (PID: 2340)
Checks proxy server information
- slui.exe (PID: 2340)
Reads mouse settings
- Castle.com (PID: 4400)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:09:25 21:53:44+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26624 |
| InitializedDataSize: | 3806720 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x350a |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 5.1.4.4 |
| ProductVersionNumber: | 5.1.4.4 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| CompanyName: | Elektrius LLC |
| FileDescription: | Unified library of game modifications. |
| FileVersion: | 1.1 |
| InternalName: | Elektrius |
| LegalCopyright: | Copyright (C) 2024-2025 Elektrius LLC. All rights reserved. |
| OriginalFileName: | Elektrius.exe |
| ProductName: | Elektrius |
| ProductVersion: | 1.1 |
Total processes
139
Monitored processes
16
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 664 | cmd /c copy /b ..\Dat.flv + ..\Geometry.flv + ..\Ga.flv + ..\Calculation.flv + ..\Pole.flv + ..\Bernard.flv + ..\Greensboro.flv + ..\Richard.flv q | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 728 | choice /d y /t 5 | C:\Windows\SysWOW64\choice.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Offers the user a choice Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 812 | findstr "SophosHealth bdservicehost AvastUI AVGUI nsWscSvc ekrn" | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2340 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2564 | cmd /c md 582573 | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4112 | findstr /V "detect" Testimony | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4400 | Castle.com q | C:\Users\admin\AppData\Local\Temp\582573\Castle.com | cmd.exe | ||||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script (Beta) Version: 3, 3, 15, 5 Modules
| |||||||||||||||
| 4436 | tasklist | C:\Windows\SysWOW64\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4608 | cmd /c copy /b 582573\Castle.com + Isaac + Flight + About + Saddam + Revenge + Surgeon + Sperm + Tex + Touch + Many 582573\Castle.com | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4696 | expand Functional.flv Functional.flv.bat | C:\Windows\SysWOW64\expand.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: LZ Expansion Utility Exit code: 0 Version: 5.00 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
7 310
Read events
7 310
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
21
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6032 | extrac32.exe | C:\Users\admin\AppData\Local\Temp\Surgeon | binary | |
MD5:184168DEF5D79B0F9FFA159CD5BC7AE1 | SHA256:5AE21144A64681F49B719FE211AC5199AEAA42909E5CB5A60CE5A82C8B49997B | |||
| 5112 | Elektrius.exe | C:\Users\admin\AppData\Local\Temp\Richard.flv | binary | |
MD5:27D07C77F67DC2E10A577F8C9C2931A9 | SHA256:D16B2E83F87B6D76775245D8C8CF8326734E5004EA8E5827BABF4680436FEF53 | |||
| 5112 | Elektrius.exe | C:\Users\admin\AppData\Local\Temp\Functional.flv | text | |
MD5:5BEF20432E8702EBF7A1A2A02723DFC6 | SHA256:B8CE5BA814133BCD41F75B27F2A5D96C69FF2DDE327CD989FA67332ACA639BB5 | |||
| 6032 | extrac32.exe | C:\Users\admin\AppData\Local\Temp\Tex | binary | |
MD5:FE5206FCA4AAE480B7E06C6FE6600EA4 | SHA256:BF6137157D0A328EB0946232DE257FB59D1DD743D81D1E2376A1C4DB95E09AD0 | |||
| 5112 | Elektrius.exe | C:\Users\admin\AppData\Local\Temp\Calculation.flv | binary | |
MD5:1B1BA9D4EDF27BB4DB24153F4CF75167 | SHA256:10D1986321C72A60FFDAD10877C1A30B650FEC203231824BE0B2B3243EA92A1C | |||
| 5112 | Elektrius.exe | C:\Users\admin\AppData\Local\Temp\Bernard.flv | binary | |
MD5:5010A680CA46B591082C2DD3B4DA4D56 | SHA256:6B6015CC55D2FCB3EDCEB5B32A3DF32F76AF7D5D6943A4606611F67C710663D4 | |||
| 5112 | Elektrius.exe | C:\Users\admin\AppData\Local\Temp\Dat.flv | binary | |
MD5:6FB0BFE3CFDCD4879A35AB527CC1343E | SHA256:B10DBE7622ED9F5645282D233AF1D24E1178720DE0B3914DFAEE941970EB3907 | |||
| 4696 | expand.exe | C:\Users\admin\AppData\Local\Temp\functional.flv.bat | text | |
MD5:5BEF20432E8702EBF7A1A2A02723DFC6 | SHA256:B8CE5BA814133BCD41F75B27F2A5D96C69FF2DDE327CD989FA67332ACA639BB5 | |||
| 5112 | Elektrius.exe | C:\Users\admin\AppData\Local\Temp\Greensboro.flv | binary | |
MD5:069F97C19F82982012633883B5A16451 | SHA256:006F66886FB889E0C3945FC89AADC524105F7F428E69DFDB2314B921BF5AA2D1 | |||
| 6032 | extrac32.exe | C:\Users\admin\AppData\Local\Temp\About | binary | |
MD5:79CBE8B9E0DFD7A3DC2BC4201C4089EF | SHA256:5B613B140DF3799C37369601AD56782980F510E5C44135B400E48A2D79C3BD46 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
27
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | svchost.exe | GET | 200 | 2.16.164.72:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 104.21.38.122:443 | https://atirflee.world/KEnsj | unknown | binary | 32.8 Kb | unknown |
— | — | POST | 200 | 172.67.222.162:443 | https://atirflee.world/KEnsj | unknown | binary | 69 b | unknown |
— | — | POST | 200 | 104.21.38.122:443 | https://atirflee.world/KEnsj | unknown | binary | 69 b | unknown |
— | — | POST | 200 | 172.67.222.162:443 | https://atirflee.world/KEnsj | unknown | binary | 69 b | unknown |
— | — | POST | 200 | 104.21.38.122:443 | https://atirflee.world/KEnsj | unknown | binary | 69 b | unknown |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 200 | 172.67.222.162:443 | https://atirflee.world/KEnsj | unknown | binary | 69 b | unknown |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 200 | 104.21.38.122:443 | https://atirflee.world/KEnsj | unknown | binary | 10.1 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2104 | svchost.exe | 2.16.164.72:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4400 | Castle.com | 172.67.222.162:443 | atirflee.world | CLOUDFLARENET | US | unknown |
6436 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2340 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
IMZGNLfCsfJxaXiecmt.IMZGNLfCsfJxaXiecmt |
| unknown |
atirflee.world |
| unknown |
activation-v2.sls.microsoft.com |
| whitelisted |