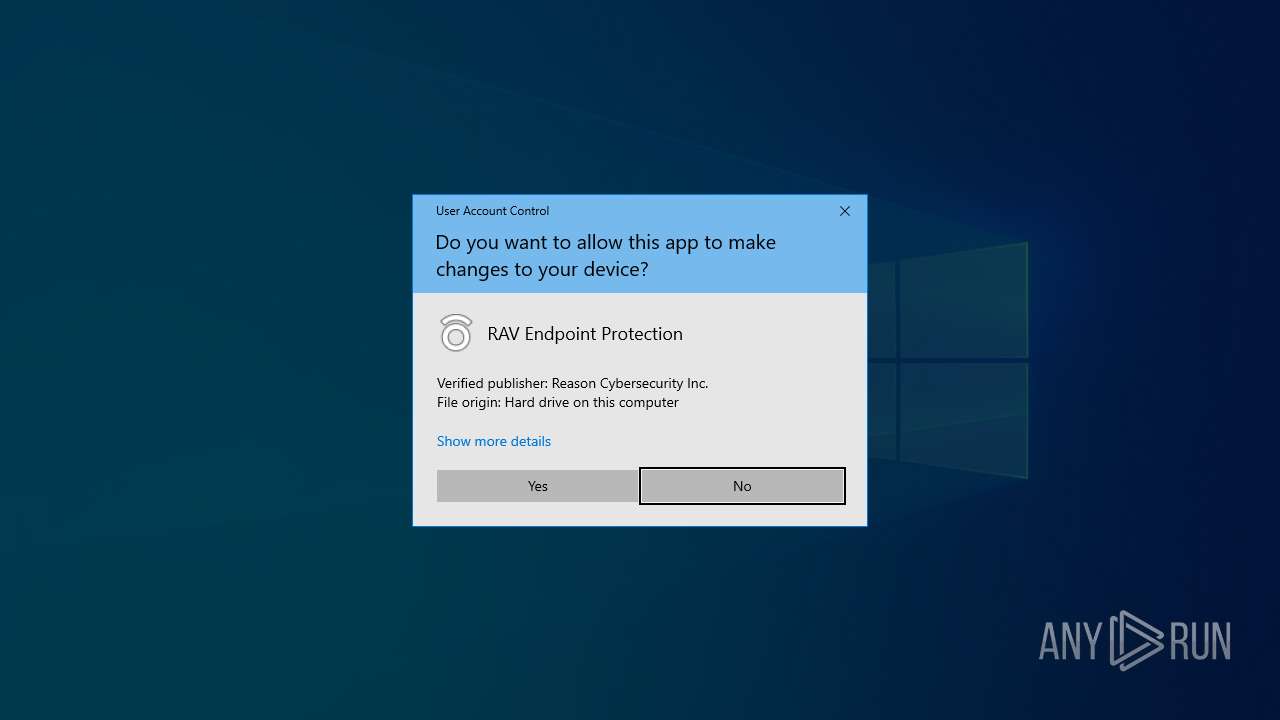
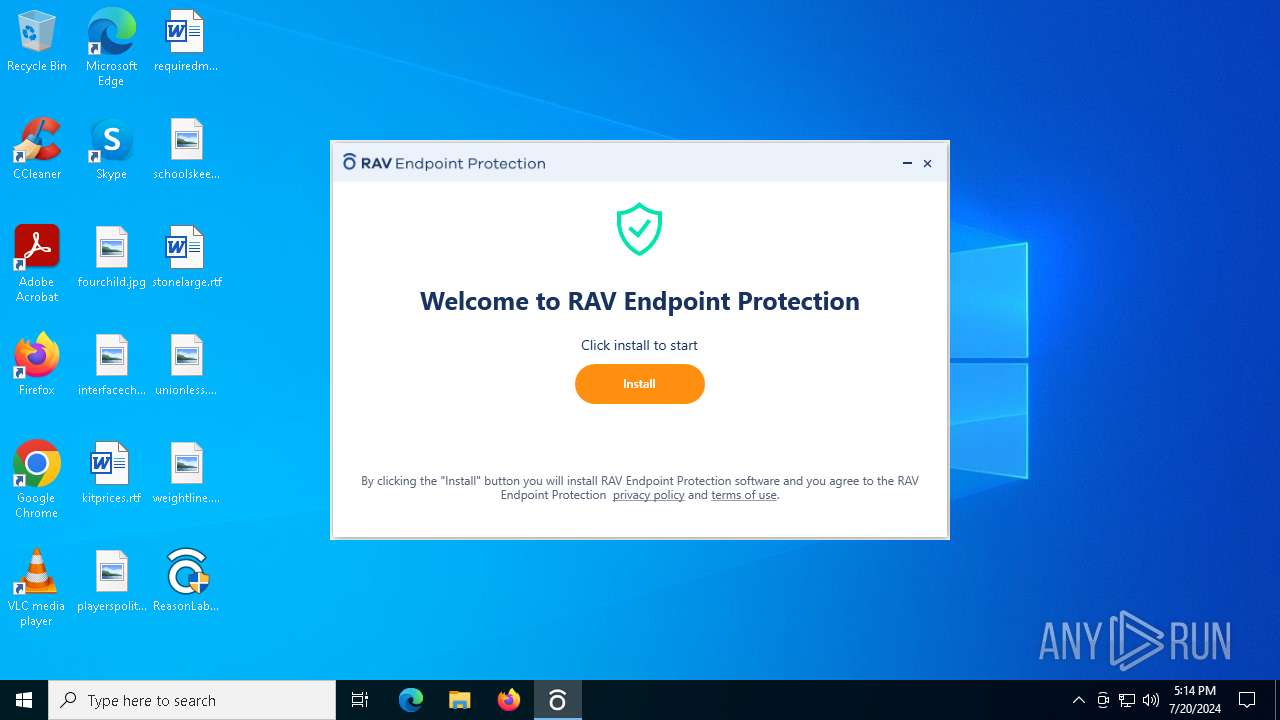
| File name: | ReasonLabs-EPP-setup.exe |
| Full analysis: | https://app.any.run/tasks/dd065bd3-5527-4bf2-bede-615a3c2acc3f |
| Verdict: | Malicious activity |
| Threats: | MetaStealer is an info-stealing malware primarily targeting sensitive data like login credentials, payment details, and browser history. It typically infects systems via phishing emails or malicious downloads and can exfiltrate data to a command and control (C2) server. MetaStealer is known for its stealthy techniques, including evasion and persistence mechanisms, which make it difficult to detect. This malware has been actively used in various cyberattacks, particularly for financial theft and credential harvesting from individuals and organizations. |
| Analysis date: | July 20, 2024, 17:14:25 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | 7E5C992DCE119ED1EC5BE91F40637CF3 |
| SHA1: | 989E7F3B1E0B18E6A3E174DFA8A9A42974E6D0D4 |
| SHA256: | AD1A6967D927BF514233371B5AD7BF2B4BEED79D517ECCF43BAB671B2390BAFB |
| SSDEEP: | 98304:nEcjJjfl+zlWb/hZZV8fB+kc881Qv1Oq6ULHxnaDPjyFXVWBMJjObR+DsL4rzoYU:bjV |
MALICIOUS
Drops the executable file immediately after the start
- ReasonLabs-EPP-setup.exe (PID: 7228)
- ReasonLabs-EPP-setup.exe (PID: 2072)
- RAVEndPointProtection-installer.exe (PID: 6840)
Actions looks like stealing of personal data
- RAVEndPointProtection-installer.exe (PID: 6840)
- rsEngineSvc.exe (PID: 4888)
Changes the autorun value in the registry
- rundll32.exe (PID: 7796)
METASTEALER has been detected (YARA)
- rsEngineSvc.exe (PID: 4888)
- rsAppUI.exe (PID: 4288)
CYBERGATE has been detected (YARA)
- rsEngineSvc.exe (PID: 4888)
SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- ReasonLabs-EPP-setup.exe (PID: 7228)
- ReasonLabs-EPP-setup.exe (PID: 2072)
Executable content was dropped or overwritten
- ReasonLabs-EPP-setup.exe (PID: 7228)
- ReasonLabs-EPP-setup.exe (PID: 2072)
- RAVEndPointProtection-installer.exe (PID: 6840)
The process creates files with name similar to system file names
- ReasonLabs-EPP-setup.exe (PID: 7228)
- ReasonLabs-EPP-setup.exe (PID: 2072)
- RAVEndPointProtection-installer.exe (PID: 6840)
Reads security settings of Internet Explorer
- ReasonLabs-EPP-setup.exe (PID: 7228)
- RAVEndPointProtection-installer.exe (PID: 6840)
- rsWSC.exe (PID: 2620)
- rsEngineSvc.exe (PID: 7624)
- rsEDRSvc.exe (PID: 2276)
- rsEngineSvc.exe (PID: 4888)
Starts itself from another location
- ReasonLabs-EPP-setup.exe (PID: 7228)
Process drops legitimate windows executable
- ReasonLabs-EPP-setup.exe (PID: 2072)
- RAVEndPointProtection-installer.exe (PID: 6840)
Executes as Windows Service
- rsSyncSvc.exe (PID: 7772)
- rsWSC.exe (PID: 5444)
- rsClientSvc.exe (PID: 3404)
- rsEngineSvc.exe (PID: 4888)
- rsEDRSvc.exe (PID: 7428)
- WmiApSrv.exe (PID: 7760)
The process drops C-runtime libraries
- RAVEndPointProtection-installer.exe (PID: 6840)
Drops a system driver (possible attempt to evade defenses)
- RAVEndPointProtection-installer.exe (PID: 6840)
Creates or modifies Windows services
- RAVEndPointProtection-installer.exe (PID: 6840)
- rundll32.exe (PID: 7796)
Uses RUNDLL32.EXE to load library
- RAVEndPointProtection-installer.exe (PID: 6840)
Creates files in the driver directory
- RAVEndPointProtection-installer.exe (PID: 6840)
Checks Windows Trust Settings
- rsWSC.exe (PID: 2620)
- rsWSC.exe (PID: 5444)
- rsEngineSvc.exe (PID: 7624)
- rsEDRSvc.exe (PID: 2276)
- rsEDRSvc.exe (PID: 7428)
- rsEngineSvc.exe (PID: 4888)
Uses WEVTUTIL.EXE to install publishers and event logs from the manifest
- RAVEndPointProtection-installer.exe (PID: 6840)
Drops 7-zip archiver for unpacking
- RAVEndPointProtection-installer.exe (PID: 6840)
Searches for installed software
- RAVEndPointProtection-installer.exe (PID: 6840)
Creates a software uninstall entry
- RAVEndPointProtection-installer.exe (PID: 6840)
Adds/modifies Windows certificates
- rsWSC.exe (PID: 2620)
- rsEngineSvc.exe (PID: 7624)
- rsEDRSvc.exe (PID: 7428)
Reads the date of Windows installation
- rsEngineSvc.exe (PID: 4888)
- rsEDRSvc.exe (PID: 7428)
Dropped object may contain URLs of mainers pools
- rsEngineSvc.exe (PID: 4888)
Reads the BIOS version
- rsEDRSvc.exe (PID: 7428)
- rsEngineSvc.exe (PID: 4888)
Process checks is Powershell's Script Block Logging on
- rsEDRSvc.exe (PID: 7428)
The process checks if it is being run in the virtual environment
- rsEngineSvc.exe (PID: 4888)
Application launched itself
- rsAppUI.exe (PID: 4288)
There is functionality for taking screenshot (YARA)
- rsEngineSvc.exe (PID: 4888)
There is functionality for communication over UDP network (YARA)
- rsEngineSvc.exe (PID: 4888)
INFO
Checks supported languages
- ReasonLabs-EPP-setup.exe (PID: 7228)
- ReasonLabs-EPP-setup.exe (PID: 2072)
- RAVEndPointProtection-installer.exe (PID: 6840)
- rsSyncSvc.exe (PID: 4984)
- rsSyncSvc.exe (PID: 7772)
- rsWSC.exe (PID: 2620)
- rsClientSvc.exe (PID: 1936)
- rsWSC.exe (PID: 5444)
- rsClientSvc.exe (PID: 3404)
- rsEngineSvc.exe (PID: 7624)
- rsEngineSvc.exe (PID: 4888)
- rsEDRSvc.exe (PID: 2276)
- rsHelper.exe (PID: 2056)
- rsEDRSvc.exe (PID: 7428)
- EPP.exe (PID: 8044)
- rsAppUI.exe (PID: 4288)
- rsLitmus.A.exe (PID: 4508)
- rsAppUI.exe (PID: 3800)
- rsAppUI.exe (PID: 4928)
- rsAppUI.exe (PID: 6980)
- rsAppUI.exe (PID: 7092)
- rsAppUI.exe (PID: 1736)
Create files in a temporary directory
- ReasonLabs-EPP-setup.exe (PID: 7228)
- ReasonLabs-EPP-setup.exe (PID: 2072)
- RAVEndPointProtection-installer.exe (PID: 6840)
- rsAppUI.exe (PID: 4288)
Reads the computer name
- ReasonLabs-EPP-setup.exe (PID: 7228)
- RAVEndPointProtection-installer.exe (PID: 6840)
- rsSyncSvc.exe (PID: 4984)
- rsSyncSvc.exe (PID: 7772)
- rsWSC.exe (PID: 2620)
- rsWSC.exe (PID: 5444)
- rsClientSvc.exe (PID: 3404)
- rsClientSvc.exe (PID: 1936)
- rsEngineSvc.exe (PID: 4888)
- rsEngineSvc.exe (PID: 7624)
- rsHelper.exe (PID: 2056)
- rsEDRSvc.exe (PID: 2276)
- rsEDRSvc.exe (PID: 7428)
- rsAppUI.exe (PID: 4288)
- rsAppUI.exe (PID: 3800)
- rsAppUI.exe (PID: 4928)
- rsAppUI.exe (PID: 1736)
Reads Environment values
- RAVEndPointProtection-installer.exe (PID: 6840)
- rsEngineSvc.exe (PID: 4888)
- rsEDRSvc.exe (PID: 7428)
- rsAppUI.exe (PID: 4288)
Reads the machine GUID from the registry
- RAVEndPointProtection-installer.exe (PID: 6840)
- rsWSC.exe (PID: 2620)
- rsWSC.exe (PID: 5444)
- rsEngineSvc.exe (PID: 7624)
- rsEngineSvc.exe (PID: 4888)
- rsHelper.exe (PID: 2056)
- rsEDRSvc.exe (PID: 2276)
- rsEDRSvc.exe (PID: 7428)
- rsAppUI.exe (PID: 4288)
- rsAppUI.exe (PID: 1736)
Disables trace logs
- RAVEndPointProtection-installer.exe (PID: 6840)
- rsEngineSvc.exe (PID: 4888)
- rsEDRSvc.exe (PID: 7428)
Reads the software policy settings
- RAVEndPointProtection-installer.exe (PID: 6840)
- rsWSC.exe (PID: 2620)
- rsEngineSvc.exe (PID: 7624)
- rsEngineSvc.exe (PID: 4888)
- rsWSC.exe (PID: 5444)
- rsEDRSvc.exe (PID: 2276)
- rsEDRSvc.exe (PID: 7428)
Creates files in the program directory
- RAVEndPointProtection-installer.exe (PID: 6840)
- rsWSC.exe (PID: 2620)
- rsEngineSvc.exe (PID: 4888)
- rsEngineSvc.exe (PID: 7624)
- rsEDRSvc.exe (PID: 2276)
- rsEDRSvc.exe (PID: 7428)
.NET Reactor protector has been detected
- RAVEndPointProtection-installer.exe (PID: 6840)
- rsWSC.exe (PID: 5444)
- rsEngineSvc.exe (PID: 4888)
- rsHelper.exe (PID: 2056)
- rsEDRSvc.exe (PID: 7428)
- rsAppUI.exe (PID: 4288)
Checks proxy server information
- RAVEndPointProtection-installer.exe (PID: 6840)
- rsWSC.exe (PID: 2620)
- rsEngineSvc.exe (PID: 7624)
- rsAppUI.exe (PID: 4288)
Reads the time zone
- runonce.exe (PID: 5400)
- rsEngineSvc.exe (PID: 4888)
- rsEDRSvc.exe (PID: 7428)
Reads security settings of Internet Explorer
- runonce.exe (PID: 5400)
- Taskmgr.exe (PID: 2072)
Creates files or folders in the user directory
- rsWSC.exe (PID: 2620)
- rsEngineSvc.exe (PID: 7624)
- rsEngineSvc.exe (PID: 4888)
- rsAppUI.exe (PID: 4288)
- rsAppUI.exe (PID: 4928)
- rsAppUI.exe (PID: 1736)
Reads product name
- rsEngineSvc.exe (PID: 4888)
- rsEDRSvc.exe (PID: 7428)
- rsAppUI.exe (PID: 4288)
Reads CPU info
- rsEngineSvc.exe (PID: 4888)
- rsEDRSvc.exe (PID: 7428)
Process checks computer location settings
- rsAppUI.exe (PID: 6980)
- rsAppUI.exe (PID: 4288)
- rsAppUI.exe (PID: 7092)
Process checks whether UAC notifications are on
- rsEDRSvc.exe (PID: 7428)
Manual execution by a user
- Taskmgr.exe (PID: 2072)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:09:25 21:55:49+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26112 |
| InitializedDataSize: | 141824 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x34f7 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 5.6.1.0 |
| ProductVersionNumber: | 5.6.1.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| Comments: | RAV Endpoint Protection |
| CompanyName: | Reason Cybersecurity Inc. |
| FileDescription: | RAV Endpoint Protection |
| FileVersion: | 5.6.1 |
| LegalCopyright: | Copyright (C) 2022 Reason Cybersecurity Inc. |
| LegalTrademarks: | RAV Endpoint Protection is a trademark of Reason Cybersecurity Inc. |
| ProductName: | RAV Endpoint Protection |
| ProductVersion: | 5.6.1 |
Total processes
188
Monitored processes
39
Malicious processes
8
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
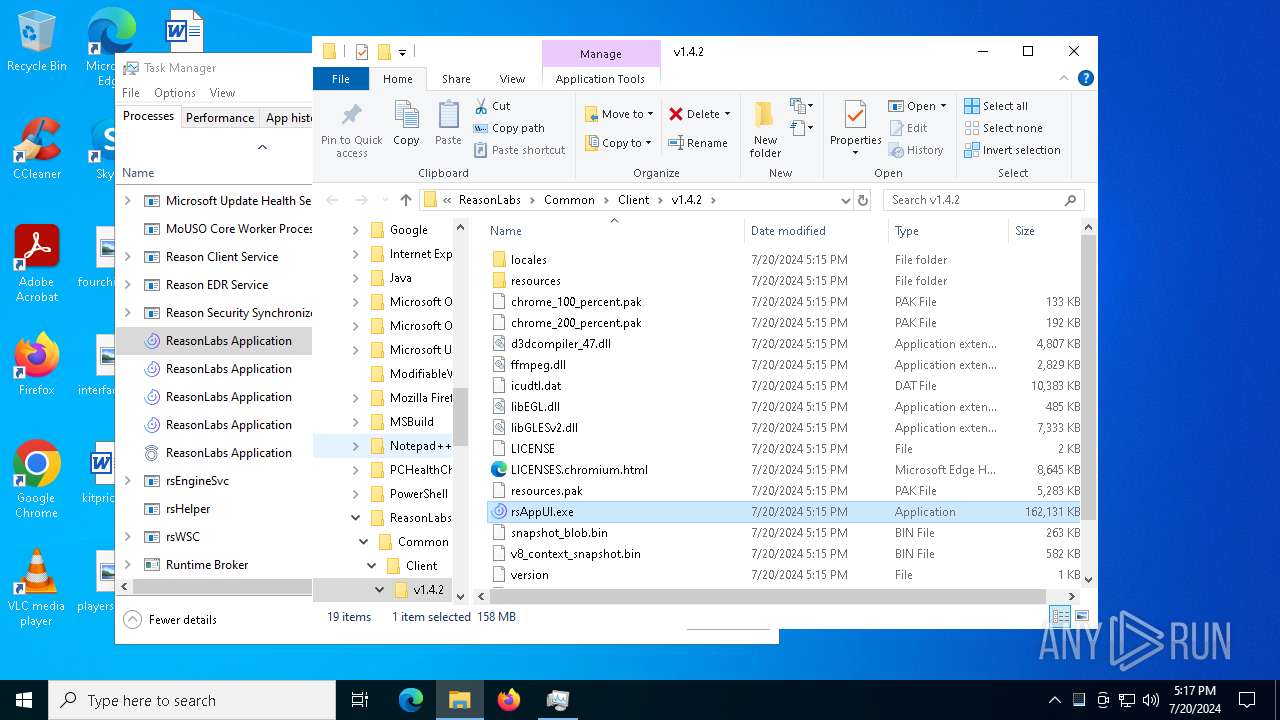
| 1736 | "C:\Program Files\ReasonLabs\Common\Client\v1.4.2\rsAppUI.exe" --type=gpu-process --disable-gpu-sandbox --use-gl=disabled --gpu-vendor-id=5140 --gpu-device-id=140 --gpu-sub-system-id=0 --gpu-revision=0 --gpu-driver-version=10.0.19041.3636 --user-data-dir="C:\Users\admin\AppData\Roaming\ReasonLabs\EPP" --gpu-preferences=WAAAAAAAAADoAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAABEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=3972 --field-trial-handle=2320,i,10521272550430091050,2267665900403106448,262144 --disable-features=SpareRendererForSitePerProcess,WinDelaySpellcheckServiceInit,WinRetrieveSuggestionsOnlyOnDemand /prefetch:2 | C:\Program Files\ReasonLabs\Common\Client\v1.4.2\rsAppUI.exe | — | rsAppUI.exe | |||||||||||
User: admin Company: Reason Cybersecurity Ltd. Integrity Level: MEDIUM Description: ReasonLabs Application Exit code: 0 Version: 1.4.2 Modules
| |||||||||||||||
| 1936 | "C:\Program Files\ReasonLabs\EPP\rsClientSvc.exe" -i | C:\Program Files\ReasonLabs\EPP\rsClientSvc.exe | — | RAVEndPointProtection-installer.exe | |||||||||||
User: admin Company: Reason Software Company Inc. Integrity Level: HIGH Description: Reason Client Service Exit code: 0 Version: 5.32.2 Modules
| |||||||||||||||
| 2056 | "c:\program files\reasonlabs\epp\rsHelper.exe" | C:\Program Files\ReasonLabs\EPP\rsHelper.exe | rsEngineSvc.exe | ||||||||||||
User: admin Company: Reason Software Company Inc. Integrity Level: MEDIUM Description: rsHelper Version: 3.2.0.0 Modules
| |||||||||||||||
| 2072 | "C:\Users\admin\AppData\Local\Temp\nsh9ED1.tmp\ReasonLabs-EPP-setup.exe" | C:\Users\admin\AppData\Local\Temp\nsh9ED1.tmp\ReasonLabs-EPP-setup.exe | ReasonLabs-EPP-setup.exe | ||||||||||||
User: admin Company: Reason Cybersecurity Inc. Integrity Level: HIGH Description: RAV Endpoint Protection Exit code: 0 Version: 5.6.1 Modules
| |||||||||||||||
| 2072 | "C:\WINDOWS\system32\taskmgr.exe" /7 | C:\Windows\System32\Taskmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2116 | "fltmc.exe" load rsKernelEngine | C:\Windows\System32\fltMC.exe | — | RAVEndPointProtection-installer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Filter Manager Control Program Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2276 | "C:\Program Files\ReasonLabs\EDR\rsEDRSvc.exe" -i | C:\Program Files\ReasonLabs\EDR\rsEDRSvc.exe | — | RAVEndPointProtection-installer.exe | |||||||||||
User: admin Company: Reason Cybersecurity Ltd. Integrity Level: HIGH Description: Reason EDR Service Exit code: 0 Version: 2.1.0 Modules
| |||||||||||||||
| 2620 | "C:\Program Files\ReasonLabs\EPP\rsWSC.exe" -i | C:\Program Files\ReasonLabs\EPP\rsWSC.exe | RAVEndPointProtection-installer.exe | ||||||||||||
User: admin Company: Reason Software Company Inc. Integrity Level: HIGH Description: rsWSC Exit code: 0 Version: 6.0.3.0 Modules
| |||||||||||||||
| 2768 | "C:\WINDOWS\system32\wevtutil.exe" im C:\Program Files\ReasonLabs\EPP\elam\evntdrv.xml | C:\Windows\System32\wevtutil.exe | — | RAVEndPointProtection-installer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Eventing Command Line Utility Exit code: 87 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3220 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
58 289
Read events
58 061
Write events
181
Delete events
47
Modification events
| (PID) Process: | (7228) ReasonLabs-EPP-setup.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\Session Manager |
| Operation: | write | Name: | PendingFileRenameOperations |
Value: \??\C:\Users\admin\AppData\Local\Temp\nsh9ED1.tmp\ReasonLabs-EPP-setup.exe | |||
| (PID) Process: | (6840) RAVEndPointProtection-installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RAVEndPointProtection-installer_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6840) RAVEndPointProtection-installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RAVEndPointProtection-installer_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (6840) RAVEndPointProtection-installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RAVEndPointProtection-installer_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (6840) RAVEndPointProtection-installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RAVEndPointProtection-installer_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (6840) RAVEndPointProtection-installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RAVEndPointProtection-installer_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (6840) RAVEndPointProtection-installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RAVEndPointProtection-installer_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (6840) RAVEndPointProtection-installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RAVEndPointProtection-installer_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (6840) RAVEndPointProtection-installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RAVEndPointProtection-installer_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6840) RAVEndPointProtection-installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RAVEndPointProtection-installer_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
Executable files
495
Suspicious files
155
Text files
44
Unknown types
21
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7228 | ReasonLabs-EPP-setup.exe | C:\Users\admin\AppData\Local\Temp\nsh9ED0.tmp\System.dll | executable | |
MD5:CFF85C549D536F651D4FB8387F1976F2 | SHA256:8DC562CDA7217A3A52DB898243DE3E2ED68B80E62DDCB8619545ED0B4E7F65A8 | |||
| 2072 | ReasonLabs-EPP-setup.exe | C:\Users\admin\AppData\Local\Temp\nss9FAB.tmp\System.dll | executable | |
MD5:CFF85C549D536F651D4FB8387F1976F2 | SHA256:8DC562CDA7217A3A52DB898243DE3E2ED68B80E62DDCB8619545ED0B4E7F65A8 | |||
| 2072 | ReasonLabs-EPP-setup.exe | C:\Users\admin\AppData\Local\Temp\nsh9FBB.tmp\System.ValueTuple.dll | executable | |
MD5:E186977FDB4AF4FC2C157CFA306389E8 | SHA256:0346F8F8A64BB5A3BC74378352252E6C1787310AE31FF969E8A1C1AF2BCA98C9 | |||
| 7228 | ReasonLabs-EPP-setup.exe | C:\Users\admin\AppData\Local\Temp\nsh9ED1.tmp\ReasonLabs-EPP-setup.exe | executable | |
MD5:7E5C992DCE119ED1EC5BE91F40637CF3 | SHA256:AD1A6967D927BF514233371B5AD7BF2B4BEED79D517ECCF43BAB671B2390BAFB | |||
| 2072 | ReasonLabs-EPP-setup.exe | C:\Users\admin\AppData\Local\Temp\nsh9FBB.tmp\ArchiveUtilityx64.dll | executable | |
MD5:B104F3C5615F0D77452DE8C7D6714441 | SHA256:54329ADBF13F43AA42FC0CEE286058B1FB7E1BAD5AB7F716BD1965AF1F160CCC | |||
| 2072 | ReasonLabs-EPP-setup.exe | C:\Users\admin\AppData\Local\Temp\nsh9FBB.tmp\rsTime.dll | executable | |
MD5:87678C116DFCCED2109724EDAFCC24B1 | SHA256:1D886EE4EB27C47CCA78DB93C89D44D8EC9C26EE305B0BA0EA381E3018096EE2 | |||
| 2072 | ReasonLabs-EPP-setup.exe | C:\Users\admin\AppData\Local\Temp\nsh9FBB.tmp\da-DK\RavStub.resources.dll | executable | |
MD5:6A9EFAA4A794867C94F3BEB1953EC277 | SHA256:1141A4572FF7829F7C44C58E251741CF17F7E1380E88A5F2B30370126D302542 | |||
| 2072 | ReasonLabs-EPP-setup.exe | C:\Users\admin\AppData\Local\Temp\nsh9FBB.tmp\rsSyncSvc.exe | executable | |
MD5:245D68860868023B81F3C8F373455D23 | SHA256:F908E104E1386BD4ABBD45430CDC4A58BC437D33F60F09C7CCBBC2209F759F30 | |||
| 2072 | ReasonLabs-EPP-setup.exe | C:\Users\admin\AppData\Local\Temp\nsh9FBB.tmp\rsLogger.dll | executable | |
MD5:8AE8DDC3FD55E624659E1710DEC8167A | SHA256:D124AE3F63900D0802F69917D0F5BD7FAABFECB2154C2E02226F0E5106CBBD1C | |||
| 2072 | ReasonLabs-EPP-setup.exe | C:\Users\admin\AppData\Local\Temp\nsh9FBB.tmp\rsStubLib.dll | executable | |
MD5:84A52F42935F346D7D1025795DF1F643 | SHA256:F8972413F716EBD9695F7D5DAD1CAFE882D2F3C006844EF67AB25DE55D4BE21C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
24
TCP/UDP connections
88
DNS requests
33
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2620 | rsWSC.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEQCeArDpSs6yEJyh6YNr4MLb | unknown | — | — | whitelisted |
2620 | rsWSC.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQRz3ETyLz2DaZTxGOH%2BA%2BjK7MkGAQUJGWTmAgB6E7U1kzqZFXhwPr7z7MCEAeSK29bdU5YKBXAnjHx1BY%3D | unknown | — | — | whitelisted |
7428 | rsEDRSvc.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSdE3gf41WAic8Uh9lF92%2BIJqh5qwQUMuuSmv81lkgvKEBCcCA2kVwXheYCEGIdbQxSAZ47kHkVIIkhHAo%3D | unknown | — | — | whitelisted |
7428 | rsEDRSvc.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTjzY2p9Pa8oibmj%2BNSMWsz63kmWgQUuhbZbU2FL3MpdpovdYxqII%2BeyG8CEAVEr%2FOUnQg5pr%2FbP1%2FlYRY%3D | unknown | — | — | whitelisted |
7428 | rsEDRSvc.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
7624 | rsEngineSvc.exe | GET | 200 | 204.79.197.203:80 | http://oneocsp.microsoft.com/ocsp/MFQwUjBQME4wTDAJBgUrDgMCGgUABBTDHsfuqfubd3pihvq4mgQVWgHWNwQUyH7SaoUqG8oZmAQHJ89QEE9oqKICEzMAAAAHh6M0o3uljhwAAAAAAAc%3D | unknown | — | — | whitelisted |
7624 | rsEngineSvc.exe | GET | 200 | 204.79.197.203:80 | http://oneocsp.microsoft.com/ocsp/MFQwUjBQME4wTDAJBgUrDgMCGgUABBTOQYLFSE5GO%2FpaRVfYu7d9gZEbQAQU2UEpsA8PY2zvadf1zSmepEhqMOYCEzMAAAAHN4xbodlbjNQAAAAAAAc%3D | unknown | — | — | whitelisted |
7624 | rsEngineSvc.exe | GET | 200 | 204.79.197.203:80 | http://oneocsp.microsoft.com/ocsp/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRBq81UG1MnDOVNKqff0SSEz6JuZwQU6IPEM9fcnwycdpoKptTfh6ZeWO4CEzMAATXj8%2BWM%2BdRgn3UAAAABNeM%3D | unknown | — | — | whitelisted |
7428 | rsEDRSvc.exe | GET | 200 | 204.79.197.203:80 | http://oneocsp.microsoft.com/ocsp/MFQwUjBQME4wTDAJBgUrDgMCGgUABBTDHsfuqfubd3pihvq4mgQVWgHWNwQUyH7SaoUqG8oZmAQHJ89QEE9oqKICEzMAAAAHh6M0o3uljhwAAAAAAAc%3D | unknown | — | — | whitelisted |
7428 | rsEDRSvc.exe | GET | 200 | 204.79.197.203:80 | http://oneocsp.microsoft.com/ocsp/MFQwUjBQME4wTDAJBgUrDgMCGgUABBTOQYLFSE5GO%2FpaRVfYu7d9gZEbQAQU2UEpsA8PY2zvadf1zSmepEhqMOYCEzMAAAAHN4xbodlbjNQAAAAAAAc%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4716 | svchost.exe | 20.190.160.20:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5620 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7856 | svchost.exe | 4.209.32.67:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2760 | svchost.exe | 40.113.110.67:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6840 | RAVEndPointProtection-installer.exe | 52.44.62.116:443 | track.analytics-data.io | AMAZON-AES | US | unknown |
6840 | RAVEndPointProtection-installer.exe | 65.9.86.8:443 | update.reasonsecurity.com | AMAZON-02 | US | unknown |
6840 | RAVEndPointProtection-installer.exe | 18.66.102.77:443 | electron-shell.reasonsecurity.com | — | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
track.analytics-data.io |
| malicious |
update.reasonsecurity.com |
| unknown |
electron-shell.reasonsecurity.com |
| unknown |
activation-v2.sls.microsoft.com |
| whitelisted |
licensing.mp.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
arc.msn.com |
| whitelisted |