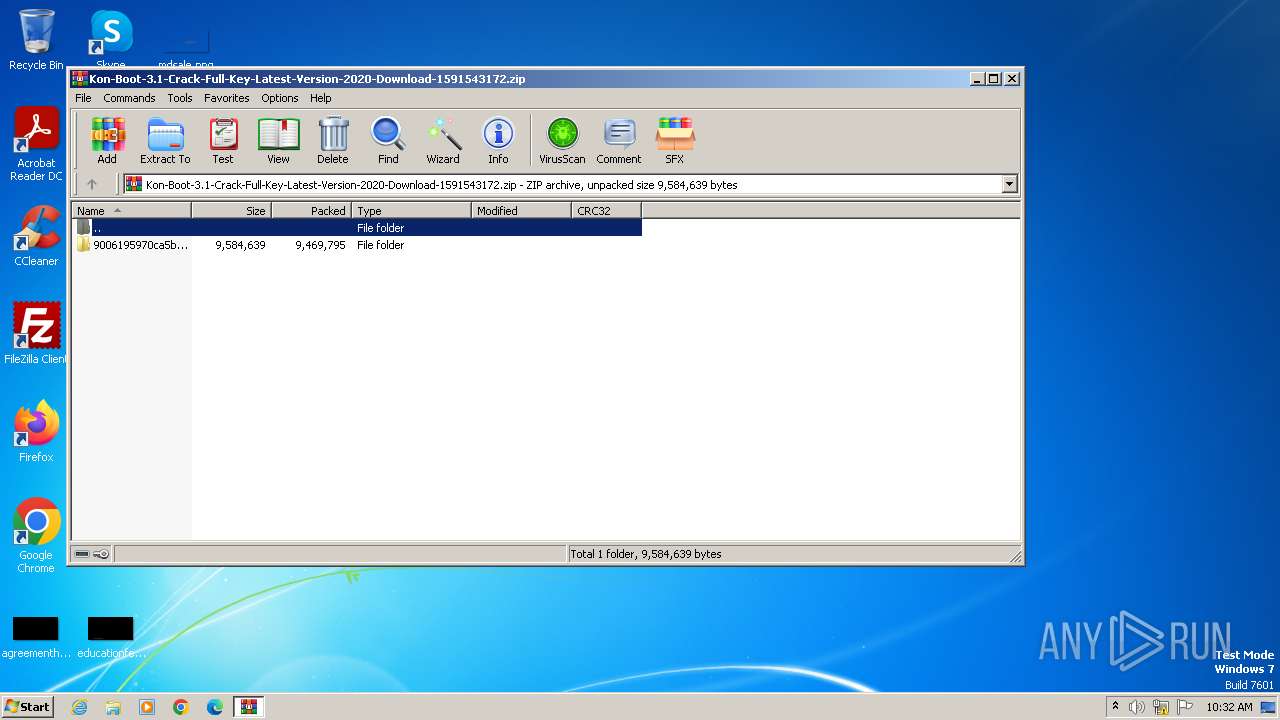
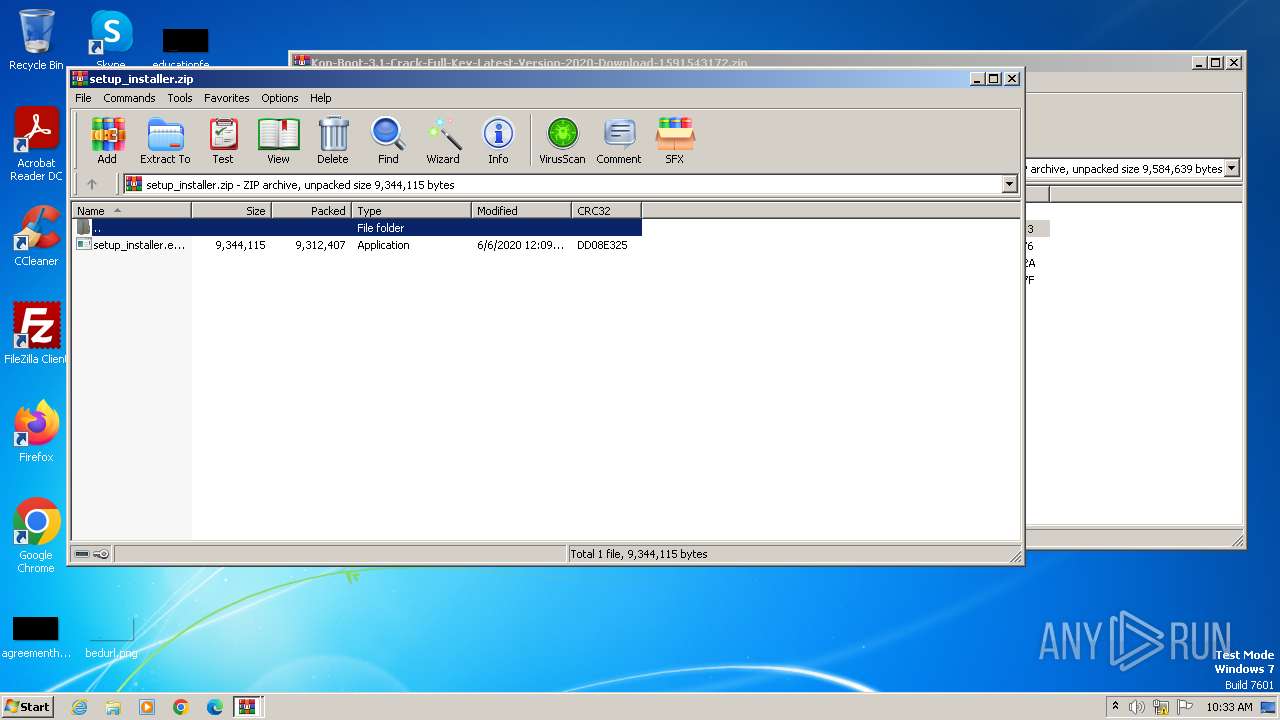
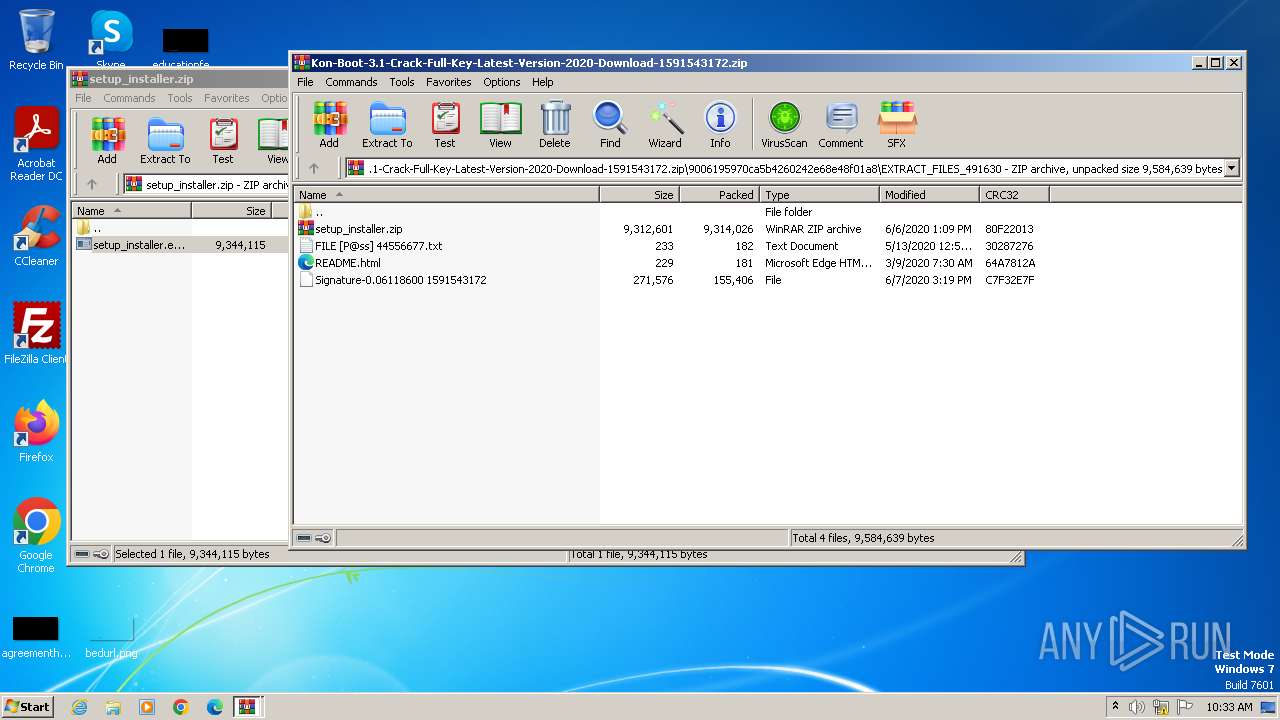
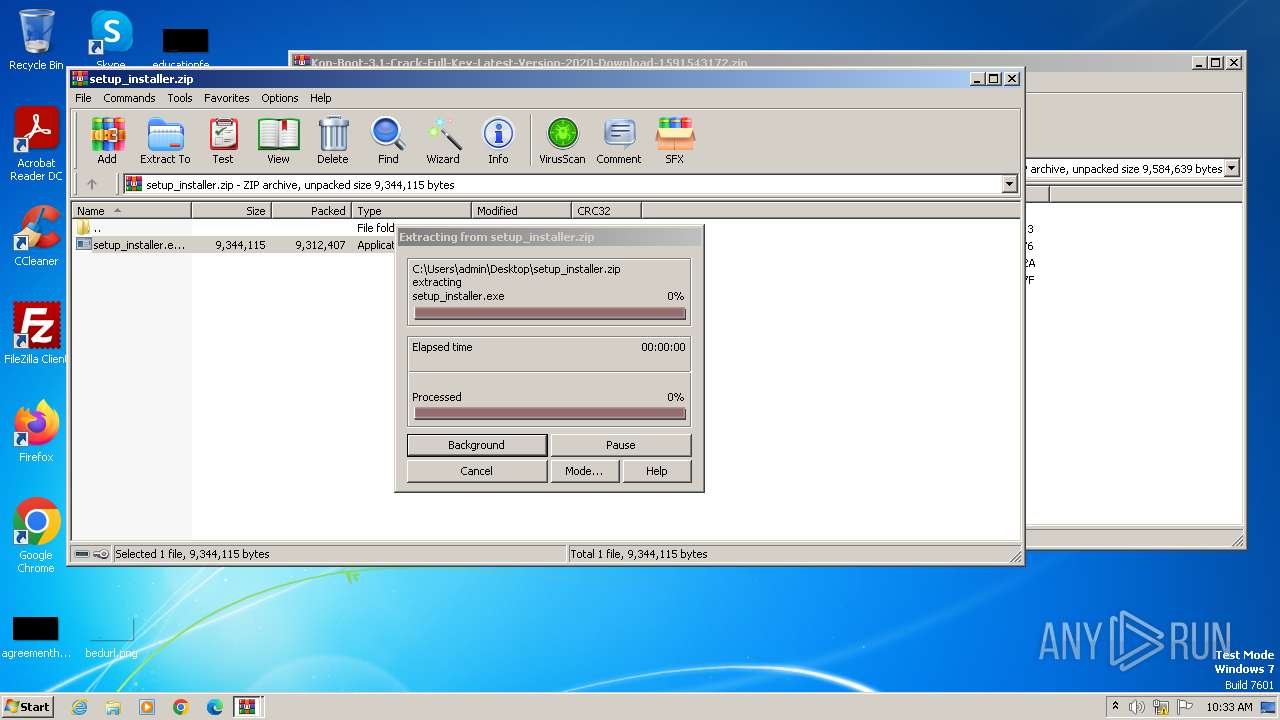
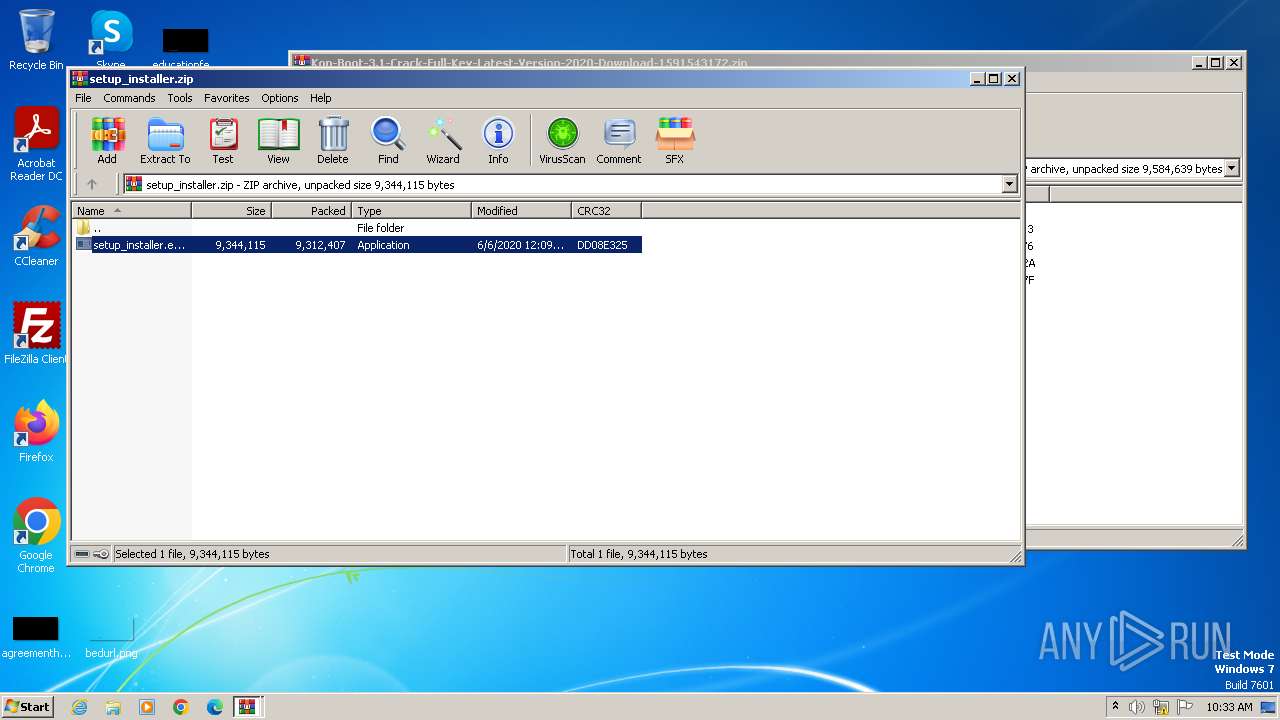
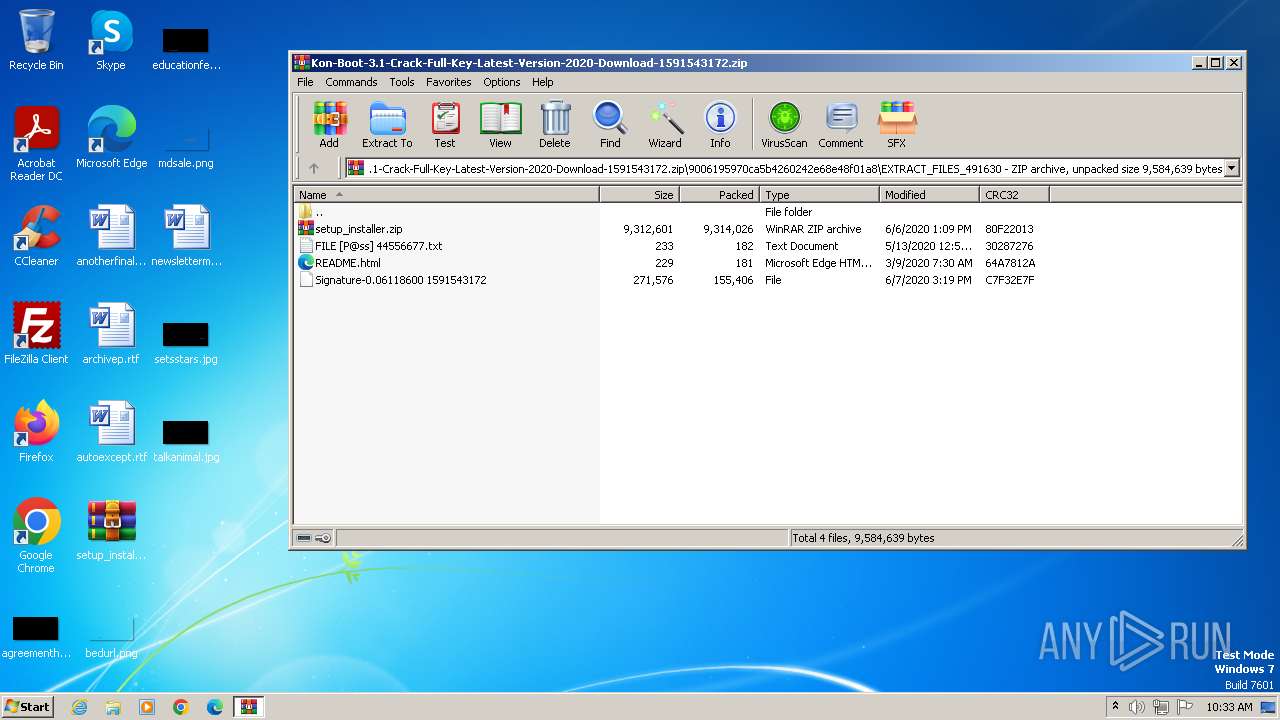
| File name: | Kon-Boot-3.1-Crack-Full-Key-Latest-Version-2020-Download-1591543172.zip |
| Full analysis: | https://app.any.run/tasks/63076179-214f-4b5d-b4cb-89193e83e178 |
| Verdict: | Malicious activity |
| Threats: | CryptBot is an advanced Windows-targeting infostealer delivered via pirate sites with "cracked" software. It has been first observed in the wild in 2019. |
| Analysis date: | May 14, 2024, 09:32:26 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | EEDD623921FC0840874D7037D293066F |
| SHA1: | 1660F4435A0CCD5960AF9299652A2BF3D6DA6BE6 |
| SHA256: | ACF30E8205B816F5A6FF7A98292134983C0A8BC57A1239FAB0BF14A702380AFC |
| SSDEEP: | 98304:Z+rWD2efB4Eh2qP2w0EI4IT0ZkappNpoRBsTkFBdZnbHmn2DbkOgcaGy1mqoth2C:M52PECGO5xlc |
MALICIOUS
Drops the executable file immediately after the start
- setup_installer.exe (PID: 336)
- setup_installer.exe (PID: 1612)
Opens an HTTP connection (SCRIPT)
- cscript.exe (PID: 1580)
Creates internet connection object (SCRIPT)
- cscript.exe (PID: 1580)
Steals credentials
- 09.exe (PID: 1112)
- herok.exe (PID: 2180)
Steals credentials from Web Browsers
- 09.exe (PID: 1112)
- herok.exe (PID: 2180)
Sends HTTP request (SCRIPT)
- cscript.exe (PID: 1580)
Unusual connection from system programs
- cscript.exe (PID: 1580)
CRYPTBOT has been detected (YARA)
- 09.exe (PID: 1112)
- herok.exe (PID: 2180)
Starts CMD.EXE for self-deleting
- herok.exe (PID: 1964)
- 09.exe (PID: 2168)
Actions looks like stealing of personal data
- 09.exe (PID: 1112)
- herok.exe (PID: 2180)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 4056)
- herok.exe (PID: 2180)
- 09.exe (PID: 1112)
- 9.exe (PID: 2304)
Executable content was dropped or overwritten
- setup_installer.exe (PID: 336)
- setup_installer.exe (PID: 1612)
Starts application with an unusual extension
- setup_installer.exe (PID: 336)
- setup_installer.exe (PID: 1612)
Reads the BIOS version
- 09.exe (PID: 1112)
- herok.exe (PID: 2180)
- 9.exe (PID: 2304)
The process executes VB scripts
- nsE284.tmp (PID: 2312)
- nsA2D6.tmp (PID: 2656)
Reads the Internet Settings
- cscript.exe (PID: 1580)
- herok.exe (PID: 2180)
- 09.exe (PID: 1112)
- 9.exe (PID: 2304)
Loads DLL from Mozilla Firefox
- herok.exe (PID: 2180)
Reads browser cookies
- 09.exe (PID: 1112)
Adds/modifies Windows certificates
- cscript.exe (PID: 1580)
Searches for installed software
- herok.exe (PID: 2180)
- 09.exe (PID: 1112)
Checks for external IP
- cscript.exe (PID: 1580)
- herok.exe (PID: 2180)
Potential Corporate Privacy Violation
- cscript.exe (PID: 1580)
- herok.exe (PID: 2180)
Device Retrieving External IP Address Detected
- herok.exe (PID: 2180)
Starts CMD.EXE for commands execution
- herok.exe (PID: 1964)
- 09.exe (PID: 2168)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 2688)
- cmd.exe (PID: 2412)
Reads settings of System Certificates
- cscript.exe (PID: 1580)
INFO
Manual execution by a user
- WinRAR.exe (PID: 4056)
- wmpnscfg.exe (PID: 2124)
- WinRAR.exe (PID: 2556)
Checks supported languages
- setup_installer.exe (PID: 336)
- herok.exe (PID: 2180)
- 09.exe (PID: 1112)
- 9.exe (PID: 2304)
- nsE284.tmp (PID: 2312)
- wmpnscfg.exe (PID: 2124)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4056)
- WinRAR.exe (PID: 2556)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 4056)
- WinRAR.exe (PID: 2556)
Process checks whether UAC notifications are on
- herok.exe (PID: 2180)
- 9.exe (PID: 2304)
- 09.exe (PID: 1112)
Reads the computer name
- setup_installer.exe (PID: 336)
- 09.exe (PID: 1112)
- wmpnscfg.exe (PID: 2124)
- 9.exe (PID: 2304)
- herok.exe (PID: 2180)
Creates files in the program directory
- setup_installer.exe (PID: 336)
- 09.exe (PID: 1112)
- herok.exe (PID: 2180)
Create files in a temporary directory
- setup_installer.exe (PID: 336)
- herok.exe (PID: 2180)
- 09.exe (PID: 1112)
- cscript.exe (PID: 1580)
Reads security settings of Internet Explorer
- cscript.exe (PID: 1580)
Reads the machine GUID from the registry
- 09.exe (PID: 1112)
- herok.exe (PID: 2180)
- 9.exe (PID: 2304)
Checks proxy server information
- cscript.exe (PID: 1580)
- herok.exe (PID: 2180)
- 09.exe (PID: 1112)
- 9.exe (PID: 2304)
Reads the software policy settings
- cscript.exe (PID: 1580)
Creates files or folders in the user directory
- herok.exe (PID: 2180)
- 09.exe (PID: 1112)
- cscript.exe (PID: 1580)
Reads product name
- herok.exe (PID: 2180)
- 09.exe (PID: 1112)
Reads Environment values
- herok.exe (PID: 2180)
- 09.exe (PID: 1112)
Reads CPU info
- herok.exe (PID: 2180)
- 09.exe (PID: 1112)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2020:06:07 15:19:32 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | 9006195970ca5b4260242e68e48f01a8/EXTRACT_FILES_491630/ |
Total processes
68
Monitored processes
22
Malicious processes
8
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
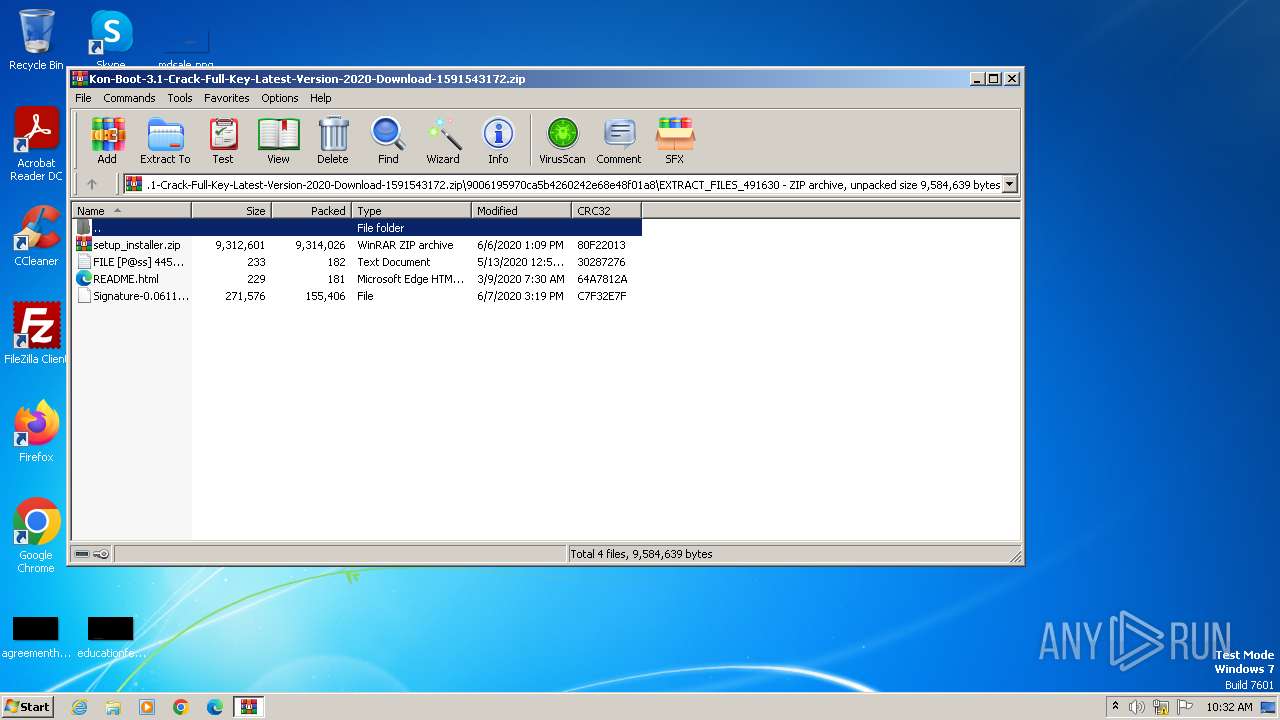
| 336 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb4056.49475\setup_installer.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb4056.49475\setup_installer.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 3.9.0.8 Modules
| |||||||||||||||
| 928 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb4056.49475\setup_installer.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb4056.49475\setup_installer.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Version: 3.9.0.8 Modules
| |||||||||||||||
| 1112 | "C:\Program Files\Gotol\rom\jon\09.exe" | C:\Program Files\Gotol\rom\jon\09.exe | setup_installer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 1344 | "C:\Program Files\Gotol\rom\jon\9.exe" | C:\Program Files\Gotol\rom\jon\9.exe | — | setup_installer.exe | |||||||||||
User: admin Integrity Level: HIGH Version: 1.1.32.00 | |||||||||||||||
| 1576 | "C:\Windows\system32\CScript.exe" "C:\Program Files\Gotol\rom\jon\9.vbs" //e:vbscript //B //NOLOGO | C:\Windows\System32\cscript.exe | — | nsA2D6.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 | |||||||||||||||
| 1580 | "C:\Windows\system32\CScript.exe" "C:\Program Files\Gotol\rom\jon\9.vbs" //e:vbscript //B //NOLOGO | C:\Windows\System32\cscript.exe | nsE284.tmp | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 1612 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb2556.5186\setup_installer.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb2556.5186\setup_installer.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 3.9.0.8 | |||||||||||||||
| 1964 | "C:\Program Files\Gotol\rom\jon\herok.exe" | C:\Program Files\Gotol\rom\jon\herok.exe | — | setup_installer.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 | |||||||||||||||
| 2124 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2168 | "C:\Program Files\Gotol\rom\jon\09.exe" | C:\Program Files\Gotol\rom\jon\09.exe | — | setup_installer.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 | |||||||||||||||
Total events
22 806
Read events
22 592
Write events
182
Delete events
32
Modification events
| (PID) Process: | (3960) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3960) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3960) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3960) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3960) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3960) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3960) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Kon-Boot-3.1-Crack-Full-Key-Latest-Version-2020-Download-1591543172.zip | |||
| (PID) Process: | (3960) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3960) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3960) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
11
Suspicious files
11
Text files
87
Unknown types
14
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4056 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb4056.49475\setup_installer.exe | executable | |
MD5:76D6750D02D12E05996BFB79C3C30207 | SHA256:3A84E101BFB17E961265EE466E30F5A77C54068C0ED38BE39F216738369B1E92 | |||
| 336 | setup_installer.exe | C:\Program Files\Gotol\rom\jon\09.exe | executable | |
MD5:6F03D1D878EB94DF3C9A5F4204C21D59 | SHA256:4F04CE2322C4F894AFE2A0517DC7702C2DCF3282993D2CA01B5A3DD6BF399228 | |||
| 336 | setup_installer.exe | C:\Users\admin\AppData\Local\Temp\nsgE031.tmp\nsE284.tmp | executable | |
MD5:132E6153717A7F9710DCEA4536F364CD | SHA256:D29AFCE2588D8DD7BB94C00CA91CAC0E85B80FFA6B221F5FFCB83A2497228EB2 | |||
| 3960 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3960.48973\9006195970ca5b4260242e68e48f01a8\EXTRACT_FILES_491630\setup_installer.zip | compressed | |
MD5:C43550F2017BC2675D59486C7903BD0A | SHA256:F9D139D44E724DF8C655DF1F936E6B2994C7DA62E7B50CEA5ECE98C8DA8C9DE9 | |||
| 2180 | herok.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\LoginDataCopy | sqlite | |
MD5:52E51471E9281235323F633CD0DEA56C | SHA256:147F3137B387FE4FBE3215B7864568404580A799D031009FE9C718F4C2EF87D0 | |||
| 336 | setup_installer.exe | C:\Program Files\Gotol\rom\jon\9.vbs | text | |
MD5:732D3599F7F4AAC60F9D08E487E62BF5 | SHA256:545E19A6FF51F52D0A0AEFF7C481055352005CC7B9A9F683552248CA5934F0B8 | |||
| 336 | setup_installer.exe | C:\Program Files\Gotol\rom\jon\herok.exe | executable | |
MD5:55F1453C26185AAE173B5A77B4741CDC | SHA256:4CB81BB210EF2CEF947EE7C63B4993DF2EF5A9658DFC445C51036537DE8F9A04 | |||
| 336 | setup_installer.exe | C:\Program Files\Gotol\rom\jon\9.exe | executable | |
MD5:5685A156F68907141595D813701E5EF7 | SHA256:AC6469E29E1BD6FB97A5B61C8F6B6ED05693246A0A0BA15B47CDBD26A3B970D3 | |||
| 336 | setup_installer.exe | C:\Users\admin\AppData\Local\Temp\nsgE031.tmp\UAC.dll | executable | |
MD5:ADB29E6B186DAA765DC750128649B63D | SHA256:2F7F8FC05DC4FD0D5CDA501B47E4433357E887BBFED7292C028D99C73B52DC08 | |||
| 336 | setup_installer.exe | C:\Users\admin\AppData\Local\Temp\nsgE031.tmp\nsExec.dll | executable | |
MD5:132E6153717A7F9710DCEA4536F364CD | SHA256:D29AFCE2588D8DD7BB94C00CA91CAC0E85B80FFA6B221F5FFCB83A2497228EB2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
17
DNS requests
12
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1580 | cscript.exe | GET | 304 | 23.32.238.241:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?4da6785990e888eb | unknown | — | — | unknown |
1580 | cscript.exe | GET | 200 | 2.19.217.103:80 | http://x1.c.lencr.org/ | unknown | — | — | unknown |
2180 | herok.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line | unknown | — | — | unknown |
1580 | cscript.exe | GET | 200 | 2.19.217.103:80 | http://x2.c.lencr.org/ | unknown | — | — | unknown |
1580 | cscript.exe | GET | 200 | 23.32.238.241:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?26d1fce40f3a4787 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1580 | cscript.exe | 104.21.4.208:443 | iplogger.org | CLOUDFLARENET | — | unknown |
1580 | cscript.exe | 23.32.238.241:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
1580 | cscript.exe | 2.19.217.103:80 | x1.c.lencr.org | Akamai International B.V. | NL | unknown |
2180 | herok.exe | 208.95.112.1:80 | ip-api.com | TUT-AS | US | unknown |
1112 | 09.exe | 49.13.77.253:80 | cedss03.top | Hetzner Online GmbH | DE | unknown |
2180 | herok.exe | 49.13.77.253:80 | cedss03.top | Hetzner Online GmbH | DE | unknown |
2304 | 9.exe | 49.13.77.253:80 | cedss03.top | Hetzner Online GmbH | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
iplogger.org |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
ip-api.com |
| shared |
x2.c.lencr.org |
| whitelisted |
cedss03.top |
| unknown |
moraa10.top |
| unknown |
hhhload07.top |
| unknown |
dns.msftncsi.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1088 | svchost.exe | Potential Corporate Privacy Violation | ET POLICY IP Check Domain (iplogger .org in DNS Lookup) |
1580 | cscript.exe | Potential Corporate Privacy Violation | ET POLICY IP Check Domain (iplogger .org in TLS SNI) |
2180 | herok.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
2180 | herok.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
1088 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
— | — | Potential Corporate Privacy Violation | ET POLICY IP Check Domain (iplogger .org in TLS SNI) |