| File name: | acb58cf1f819372ca5f461636f47ef790ec5d2748a5eaa3676104e46cdca1b19 |
| Full analysis: | https://app.any.run/tasks/8d467123-8735-4f66-898a-7a272c2f895d |
| Verdict: | Malicious activity |
| Threats: | FormBook is a data stealer that is being distributed as a MaaS. FormBook differs from a lot of competing malware by its extreme ease of use that allows even the unexperienced threat actors to use FormBook virus. |
| Analysis date: | December 06, 2018, 12:54:38 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, MSI Installer, Code page: 1252, Last Printed: Fri Sep 21 10:56:09 2012, Create Time/Date: Fri Sep 21 10:56:09 2012, Name of Creating Application: Windows Installer, Title: Exe to msi converter free, Author: www.exetomsi.com, Template: ;0, Last Saved By: devuser, Revision Number: {C35CF0AA-9B3F-4903-9F05-EBF606D58D3E}, Last Saved Time/Date: Tue May 21 12:56:44 2013, Number of Pages: 100, Number of Words: 0, Security: 0 |
| MD5: | 6D7ADA8915023EB188F47444A77D169D |
| SHA1: | F87023A7C0DE6B0FF4B0B2B799E58F41B938C332 |
| SHA256: | ACB58CF1F819372CA5F461636F47EF790EC5D2748A5EAA3676104E46CDCA1B19 |
| SSDEEP: | 12288:TEqy7sSW7kNUhBiTL1wuG2YVkp455oaomdIbTbq:TE5wzAQUTO/2SkpWon |
MALICIOUS
FORMBOOK was detected
- explorer.exe (PID: 236)
Changes the autorun value in the registry
- wscript.exe (PID: 2816)
Formbook was detected
- wscript.exe (PID: 2816)
- Firefox.exe (PID: 3136)
Connects to CnC server
- explorer.exe (PID: 236)
Actions looks like stealing of personal data
- wscript.exe (PID: 2816)
Application was dropped or rewritten from another process
- vgacjt.exe (PID: 3640)
- vgacjt.exe (PID: 2220)
Stealing of credential data
- wscript.exe (PID: 2816)
SUSPICIOUS
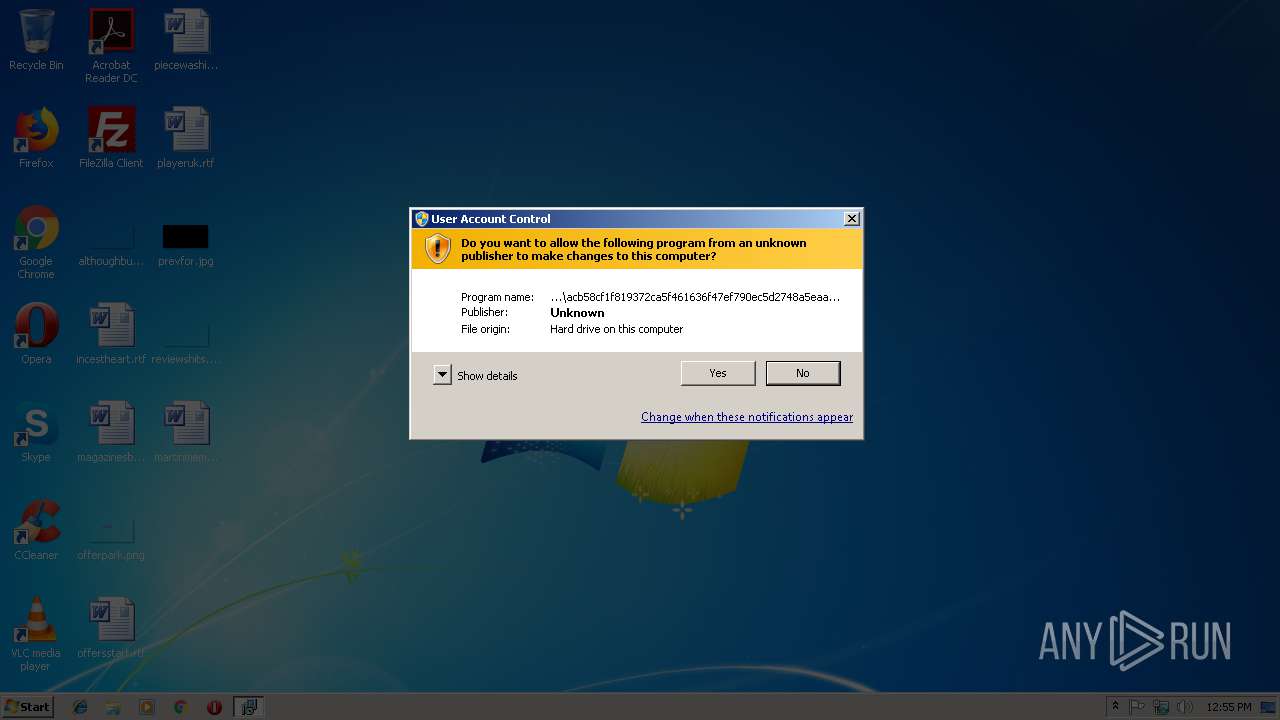
Starts Microsoft Installer
- explorer.exe (PID: 236)
Executable content was dropped or overwritten
- msiexec.exe (PID: 2252)
- DllHost.exe (PID: 3100)
- explorer.exe (PID: 236)
Drop ExeToMSI Application
- msiexec.exe (PID: 2252)
Executes scripts
- explorer.exe (PID: 236)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 2816)
Creates files in the user directory
- wscript.exe (PID: 2816)
Loads DLL from Mozilla Firefox
- wscript.exe (PID: 2816)
Application launched itself
- vgacjt.exe (PID: 3640)
Creates files in the program directory
- DllHost.exe (PID: 3100)
INFO
Low-level read access rights to disk partition
- vssvc.exe (PID: 2156)
Searches for installed software
- msiexec.exe (PID: 2252)
Dropped object may contain Bitcoin addresses
- msiexec.exe (PID: 2252)
- explorer.exe (PID: 236)
- DllHost.exe (PID: 3100)
Application was dropped or rewritten from another process
- MSIDA38.tmp (PID: 2348)
- MSIDA38.tmp (PID: 3204)
Starts application with an unusual extension
- msiexec.exe (PID: 2252)
- MSIDA38.tmp (PID: 2348)
Application launched itself
- MSIDA38.tmp (PID: 2348)
Creates files in the user directory
- Firefox.exe (PID: 3136)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Installer (100) |
|---|
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| LastPrinted: | 2012:09:21 09:56:09 |
| CreateDate: | 2012:09:21 09:56:09 |
| Software: | Windows Installer |
| Title: | Exe to msi converter free |
| Subject: | - |
| Author: | www.exetomsi.com |
| Keywords: | - |
| Comments: | - |
| Template: | ;0 |
| LastModifiedBy: | devuser |
| RevisionNumber: | {C35CF0AA-9B3F-4903-9F05-EBF606D58D3E} |
| ModifyDate: | 2013:05:21 11:56:44 |
| Pages: | 100 |
| Words: | - |
| Security: | None |
Total processes
50
Monitored processes
14
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2156 | C:\Windows\system32\vssvc.exe | C:\Windows\system32\vssvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2220 | "C:\Program Files\Uy4j89dw\vgacjt.exe" | C:\Program Files\Uy4j89dw\vgacjt.exe | — | vgacjt.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: right.Properties Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2252 | C:\Windows\system32\msiexec.exe /V | C:\Windows\system32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2348 | "C:\Windows\Installer\MSIDA38.tmp" | C:\Windows\Installer\MSIDA38.tmp | msiexec.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: right.Properties Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2620 | DrvInst.exe "1" "200" "STORAGE\VolumeSnapshot\HarddiskVolumeSnapshot18" "" "" "6792c44eb" "00000000" "000003AC" "00000488" | C:\Windows\system32\DrvInst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2816 | "C:\Windows\System32\wscript.exe" | C:\Windows\System32\wscript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2844 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\AppData\Local\Temp\acb58cf1f819372ca5f461636f47ef790ec5d2748a5eaa3676104e46cdca1b19.msi" | C:\Windows\System32\msiexec.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3100 | C:\Windows\system32\DllHost.exe /Processid:{3AD05575-8857-4850-9277-11B85BDB8E09} | C:\Windows\system32\DllHost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3136 | "C:\Program Files\Mozilla Firefox\Firefox.exe" | C:\Program Files\Mozilla Firefox\Firefox.exe | wscript.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 61.0.2 Modules
| |||||||||||||||
Total events
574
Read events
389
Write events
173
Delete events
12
Modification events
| (PID) Process: | (2252) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4000000000000000900C0DE0628DD401CC080000980F0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2252) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4000000000000000900C0DE0628DD401CC080000980F0000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2252) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 20 | |||
| (PID) Process: | (2252) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4000000000000000924365E0628DD401CC080000980F0000D3070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2252) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000924365E0628DD401CC080000340F0000E8030000010000000000000000000000A3F1717A3D824544845C6483412A3F000000000000000000 | |||
| (PID) Process: | (2156) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000AE9173E0628DD4016C080000B00A0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2156) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000AE9173E0628DD4016C080000AC0A0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2156) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000AE9173E0628DD4016C08000054090000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2156) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000AE9173E0628DD4016C0800005C090000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2156) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 4000000000000000BCB87AE0628DD4016C080000B00A0000E8030000000000000100000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
4
Suspicious files
79
Text files
60
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2252 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 2156 | vssvc.exe | C: | — | |
MD5:— | SHA256:— | |||
| 2252 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\~DF37D8F6B8F86EF487.TMP | — | |
MD5:— | SHA256:— | |||
| 2252 | msiexec.exe | C:\Config.Msi\13c7fa.rbs | — | |
MD5:— | SHA256:— | |||
| 2252 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\~DF5B5DD80EAC7A744B.TMP | — | |
MD5:— | SHA256:— | |||
| 2252 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{7a71f1a3-823d-4445-845c-6483412a3f00}_OnDiskSnapshotProp | binary | |
MD5:— | SHA256:— | |||
| 2620 | DrvInst.exe | C:\Windows\INF\setupapi.ev1 | binary | |
MD5:— | SHA256:— | |||
| 2620 | DrvInst.exe | C:\Windows\INF\setupapi.dev.log | ini | |
MD5:— | SHA256:— | |||
| 2620 | DrvInst.exe | C:\Windows\INF\setupapi.ev3 | binary | |
MD5:— | SHA256:— | |||
| 2252 | msiexec.exe | C:\Windows\Installer\MSID98B.tmp | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
6
DNS requests
8
Threats
16
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
236 | explorer.exe | GET | — | 173.236.183.227:80 | http://www.seattlepetadventures.com/ai/?oLv=+NF6fKO4+sNoFSvA9ydZPX2tEAxFaECdmO6MFoZMYbf7UBOz4BWLqkgGlYhSyAJHhQSHSw==&mLVDc=WZzhBBv0x0QLaRG&sql=1 | US | — | — | malicious |
236 | explorer.exe | GET | 301 | 91.216.107.156:80 | http://www.midiomalinea.com/ai/?oLv=KbWunvhw/zpXP5wW0UeZ7BJvggAhLiR/U+yWF01r9OQaPoLd46pZ4MbN2sk8HpOuCMpePQ==&mLVDc=WZzhBBv0x0QLaRG | FR | html | 429 b | malicious |
236 | explorer.exe | POST | — | 160.153.32.192:80 | http://www.brickellwatches.com/ai/ | US | — | — | malicious |
236 | explorer.exe | POST | — | 160.153.32.192:80 | http://www.brickellwatches.com/ai/ | US | — | — | malicious |
236 | explorer.exe | POST | — | 160.153.32.192:80 | http://www.brickellwatches.com/ai/ | US | — | — | malicious |
236 | explorer.exe | GET | 500 | 160.153.32.192:80 | http://www.brickellwatches.com/ai/?oLv=vANF0Oa22qgZseUw97TB+Swa2IWzfYKx3GaNAFricu5mcpvlFr62mhXvJ/dKFT11hcAXHQ==&mLVDc=WZzhBBv0x0QLaRG&sql=1 | US | html | 686 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
236 | explorer.exe | 91.216.107.156:80 | www.midiomalinea.com | ADISTA SAS | FR | malicious |
236 | explorer.exe | 160.153.32.192:80 | www.brickellwatches.com | GoDaddy.com, LLC | US | malicious |
236 | explorer.exe | 173.236.183.227:80 | www.seattlepetadventures.com | New Dream Network, LLC | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.uaevas.com |
| unknown |
www.midiomalinea.com |
| malicious |
www.solutionfull.com |
| malicious |
www.christianmarketinggifts.com |
| unknown |
www.theapschool.com |
| unknown |
www.riseupfloridakeys.com |
| unknown |
www.brickellwatches.com |
| malicious |
www.seattlepetadventures.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
236 | explorer.exe | A Network Trojan was detected | SC TROJAN_DOWNLOADER Suspicious HTTP-GET request with body and minimal header |
236 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (GET) |
236 | explorer.exe | A Network Trojan was detected | SC TROJAN_DOWNLOADER Suspicious HTTP-GET request with body and minimal header |
236 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (GET) |
236 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (POST) |
236 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] TrojanSpy:FormBook CnC Checkin (POST) |
236 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (POST) |
236 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] TrojanSpy:FormBook CnC Checkin (POST) |
236 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (POST) |
236 | explorer.exe | A Network Trojan was detected | SC TROJAN_DOWNLOADER Suspicious HTTP-GET request with body and minimal header |
5 ETPRO signatures available at the full report
Process | Message |
|---|---|
MSIDA38.tmp |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1391
|
MSIDA38.tmp |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\identityauthority.cpp, line 278
|
MSIDA38.tmp |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1391
|
MSIDA38.tmp |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\identityauthority.cpp, line 278
|
MSIDA38.tmp |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1391
|
MSIDA38.tmp |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\identityauthority.cpp, line 278
|
MSIDA38.tmp |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1391
|
MSIDA38.tmp |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\identityauthority.cpp, line 278
|
vgacjt.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1391
|
vgacjt.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\identityauthority.cpp, line 278
|