| File name: | External24.exe |
| Full analysis: | https://app.any.run/tasks/c9a75375-f72f-4026-9441-7c9cb74d881c |
| Verdict: | Malicious activity |
| Threats: | RisePro, an information-stealing malware, targets a wide range of sensitive data, including credit cards, passwords, and cryptocurrency wallets. By compromising infected devices, RisePro can steal valuable information and potentially cause significant financial and personal losses for victims. |
| Analysis date: | April 11, 2025, 23:06:16 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 6 sections |
| MD5: | E8AF10713A9E8EE414A1A0865C2379F2 |
| SHA1: | 12193121A75325CA4A32E7260D82E6D8C85FE0D4 |
| SHA256: | ACAD873DA34AAB461E8A7B87DD2C6D98C3B2B187F5CA868415BAC26AF1516DA5 |
| SSDEEP: | 98304:T7z4iQ229IPCDV7hePTT0yQG0NiKks3WCVGIiuKYQZvbl0Y08Z/Msb3bMPc/W424:cbgCk |
MALICIOUS
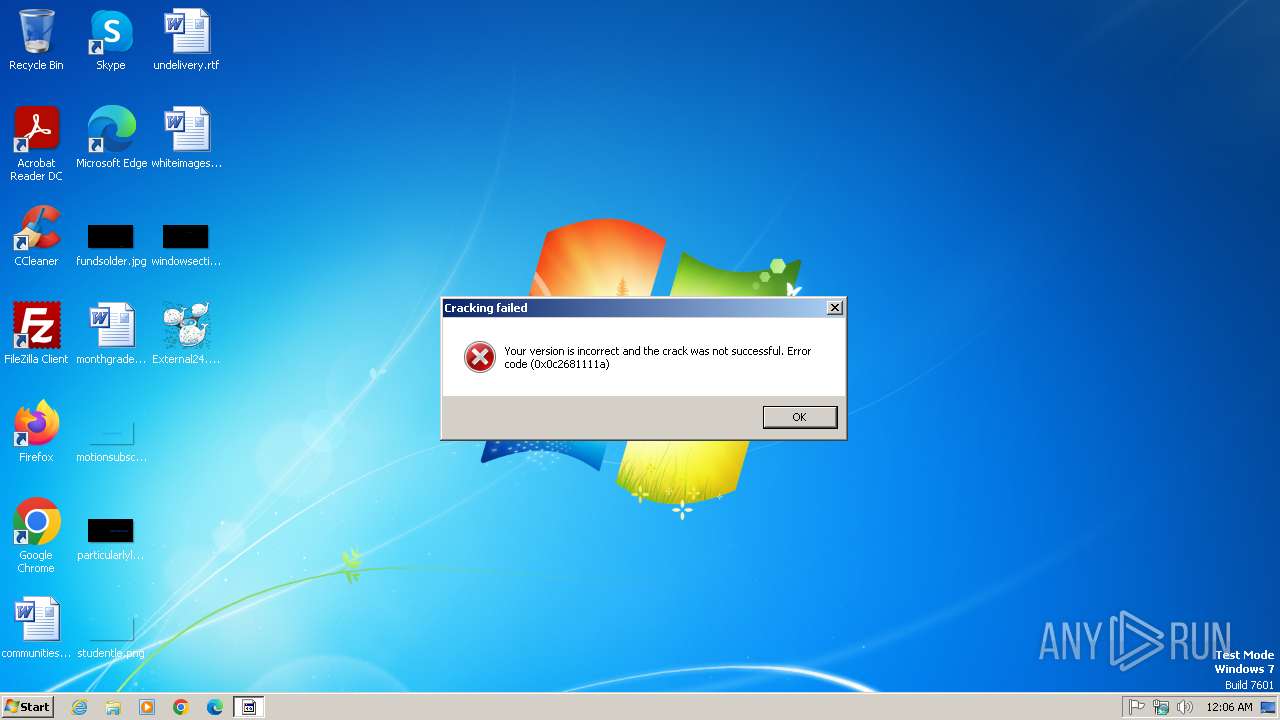
Executing a file with an untrusted certificate
- External24.exe (PID: 2848)
- External24.exe (PID: 1548)
Antivirus name has been found in the command line (generic signature)
- findstr.exe (PID: 752)
- findstr.exe (PID: 1880)
- findstr.exe (PID: 1268)
- findstr.exe (PID: 1396)
Uses Task Scheduler to autorun other applications
- Lawyers.pif (PID: 3312)
AutoIt loader has been detected (YARA)
- Lawyers.pif (PID: 3312)
RISEPRO has been detected (YARA)
- Lawyers.pif (PID: 3632)
Changes the Windows auto-update feature
- Lawyers.pif (PID: 3632)
SUSPICIOUS
Reads the Internet Settings
- External24.exe (PID: 2848)
- Lawyers.pif (PID: 3016)
- External24.exe (PID: 1548)
Reads security settings of Internet Explorer
- External24.exe (PID: 2848)
- External24.exe (PID: 1548)
- Lawyers.pif (PID: 3016)
Starts CMD.EXE for commands execution
- External24.exe (PID: 2848)
- cmd.exe (PID: 2008)
- Lawyers.pif (PID: 3016)
- External24.exe (PID: 1548)
- cmd.exe (PID: 2356)
Executing commands from ".cmd" file
- External24.exe (PID: 2848)
- External24.exe (PID: 1548)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 2008)
- cmd.exe (PID: 2356)
Get information on the list of running processes
- cmd.exe (PID: 2008)
- cmd.exe (PID: 2356)
Executable content was dropped or overwritten
- cmd.exe (PID: 2008)
- Lawyers.pif (PID: 3312)
Drops a file with a rarely used extension (PIF)
- cmd.exe (PID: 2008)
- Lawyers.pif (PID: 3312)
Suspicious file concatenation
- cmd.exe (PID: 2944)
- cmd.exe (PID: 3280)
Application launched itself
- cmd.exe (PID: 2008)
- cmd.exe (PID: 2356)
- Lawyers.pif (PID: 3312)
The executable file from the user directory is run by the CMD process
- Lawyers.pif (PID: 3016)
- Lawyers.pif (PID: 3312)
Starts the AutoIt3 executable file
- cmd.exe (PID: 2008)
- cmd.exe (PID: 2356)
- Lawyers.pif (PID: 3312)
Starts application with an unusual extension
- cmd.exe (PID: 2008)
- cmd.exe (PID: 2356)
- Lawyers.pif (PID: 3312)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 2008)
- cmd.exe (PID: 2356)
There is functionality for taking screenshot (YARA)
- Lawyers.pif (PID: 3632)
- Lawyers.pif (PID: 3312)
Connects to unusual port
- Lawyers.pif (PID: 3632)
INFO
Reads the computer name
- External24.exe (PID: 2848)
- Lawyers.pif (PID: 3016)
- External24.exe (PID: 1548)
- Lawyers.pif (PID: 3312)
- Lawyers.pif (PID: 3632)
Checks supported languages
- External24.exe (PID: 2848)
- Lawyers.pif (PID: 3016)
- External24.exe (PID: 1548)
- Lawyers.pif (PID: 3312)
- Lawyers.pif (PID: 3632)
Create files in a temporary directory
- External24.exe (PID: 2848)
- External24.exe (PID: 1548)
Creates a new folder
- cmd.exe (PID: 972)
- cmd.exe (PID: 2544)
Reads mouse settings
- Lawyers.pif (PID: 3016)
- Lawyers.pif (PID: 3312)
The sample compiled with english language support
- Lawyers.pif (PID: 3312)
Creates files or folders in the user directory
- Lawyers.pif (PID: 3312)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
RisePro
(PID) Process(3632) Lawyers.pif
C2 (1)3.36.173.8:50500
Strings (55)\OpenVPN Connect
\Growtopia
\GHISLER\wcx_ftp.ini
\Minecraft
\.minecraft\launcher_msa_credentials.bin
\Steam
\Element
\accounts.xml
\TotalCommander
\Growtopia\save.dat
\LunarClient
\.minecraft\launcher_accounts.json
\ICQ\0001
\launcher_profiles.json
\launcher_accounts.json
\config.json
\.feather\accounts.json
WSASend
\ey_tokens.txt
C:\program files\steam
frug?0
\Pidgin
S,{w_6
VaultCloseVault
\.lunarclient\settings\games\accounts.txt
\accounts.txt
\launcher_msa_credentials.bin
\Local Storage
VaultOpenVault
\Element\Local Storage
J~|Hw
\Skype
\save.dat
\.minecraft\launcher_profiles.json
\Signal
\FeatherClient
\.purple
\Battle.net
\databases
VaultGetItem
\Games
\TLauncher
logins
\Messengers
APPDATA
\FileZilla
\OpenVPN Connect\profiles
\accounts.json
\Microsoft\Skype for Desktop\Local Storage
\tlauncher_profiles.json
C:\program files (x86)\steam
\wcx_ftp.ini
\config
UaEt,
\Session Storage
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2012:02:24 19:20:04+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 29696 |
| InitializedDataSize: | 489984 |
| UninitializedDataSize: | 16896 |
| EntryPoint: | 0x38af |
| OSVersion: | 5 |
| ImageVersion: | 6 |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
Total processes
66
Monitored processes
25
Malicious processes
8
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 752 | findstr /I "avastui.exe avgui.exe nswscsvc.exe sophoshealth.exe" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 972 | cmd /c md 292668 | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 984 | tasklist | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Lists the current running tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1268 | findstr /I "wrsa.exe opssvc.exe" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1396 | findstr /I "avastui.exe avgui.exe nswscsvc.exe sophoshealth.exe" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1548 | C:\Users\admin\Desktop\External24.exe | C:\Users\admin\Desktop\External24.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1800 | tasklist | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1880 | findstr /I "wrsa.exe opssvc.exe" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2008 | "C:\Windows\System32\cmd.exe" /c copy Forgot Forgot.cmd & Forgot.cmd | C:\Windows\System32\cmd.exe | External24.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2272 | tasklist | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
4 025
Read events
3 965
Write events
38
Delete events
22
Modification events
| (PID) Process: | (2848) External24.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2848) External24.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2848) External24.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2848) External24.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3016) Lawyers.pif | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3016) Lawyers.pif | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3016) Lawyers.pif | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3016) Lawyers.pif | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1548) External24.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1548) External24.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
2
Suspicious files
44
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2848 | External24.exe | C:\Users\admin\AppData\Local\Temp\Coated | binary | |
MD5:3705ED69B8EF3ACFA5114F76081EDE86 | SHA256:CF965971F7E3C524C2284AFBF03DCFC33711E54D8A4307D305D3C1059E7E3C20 | |||
| 2848 | External24.exe | C:\Users\admin\AppData\Local\Temp\Anytime | binary | |
MD5:3AC46A4FFC849E4A10C2FC13CE82C5EE | SHA256:AD20A4B3890F44EB9783D4DAF7584C2B82530B3E80CC034B394494ECAEE237A0 | |||
| 2848 | External24.exe | C:\Users\admin\AppData\Local\Temp\Monster | binary | |
MD5:2B9C205FB7211E283CB476BA654DD9E8 | SHA256:F850CCD4E0705E6EB7F8EB93B365D586691B24375BD7F7A1476A4A1A221C7720 | |||
| 2848 | External24.exe | C:\Users\admin\AppData\Local\Temp\Accidents | binary | |
MD5:0E6A2C91997604F59DE9B6DDEC6AFAEA | SHA256:27119FD62B46A840203D09A2CFE60771129A7FACA326F840E1C9E3A2053C8999 | |||
| 2848 | External24.exe | C:\Users\admin\AppData\Local\Temp\Warming | binary | |
MD5:8C0F67222F42DBC8CD40DC1308896C26 | SHA256:AB2B14120114856F5CA25A864D524D73D2945A1B382FA7D608B0FDA302AF93C3 | |||
| 2848 | External24.exe | C:\Users\admin\AppData\Local\Temp\Loc | binary | |
MD5:E82234E64597DF26B82D9F7906CEB5F4 | SHA256:64AC3403F57C4AB0885D1205926DAA8C05B6AE0FBE7A31F21C3FAB9FA3E3F750 | |||
| 2848 | External24.exe | C:\Users\admin\AppData\Local\Temp\Inspections | binary | |
MD5:E21DAD0190A8784C002AD2E6A05BDA5C | SHA256:B8C9371F3FAB03439A3943120A369B4DAB0C719CB83ED2EC0C9D9B73473846B5 | |||
| 2848 | External24.exe | C:\Users\admin\AppData\Local\Temp\Situation | binary | |
MD5:71E552ACF27B7198855203A7A6A25099 | SHA256:73DBE22328916C224F2505C96043C966A74A711490E523A48F7FBBF2D4D90160 | |||
| 2848 | External24.exe | C:\Users\admin\AppData\Local\Temp\Sharon | binary | |
MD5:5CACD6E1936E71B02ACD561266E159CE | SHA256:2BBEDE3474F225FDBAD8358FBB20F82576A3373F76ED363095D81F88FEAC30BA | |||
| 2848 | External24.exe | C:\Users\admin\AppData\Local\Temp\Physical | binary | |
MD5:219D84D2F974CD06FB52FBF1ABB259FC | SHA256:FF846E23D88D73F1124C422A52E65C3A2A1FCA9891D66792E4D6AC3B29E46E2C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
17
DNS requests
3
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
3632 | Lawyers.pif | 3.36.173.8:50500 | — | AMAZON-02 | KR | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
CcUPthUoPgCKIth.CcUPthUoPgCKIth |
| unknown |
dns.msftncsi.com |
| whitelisted |