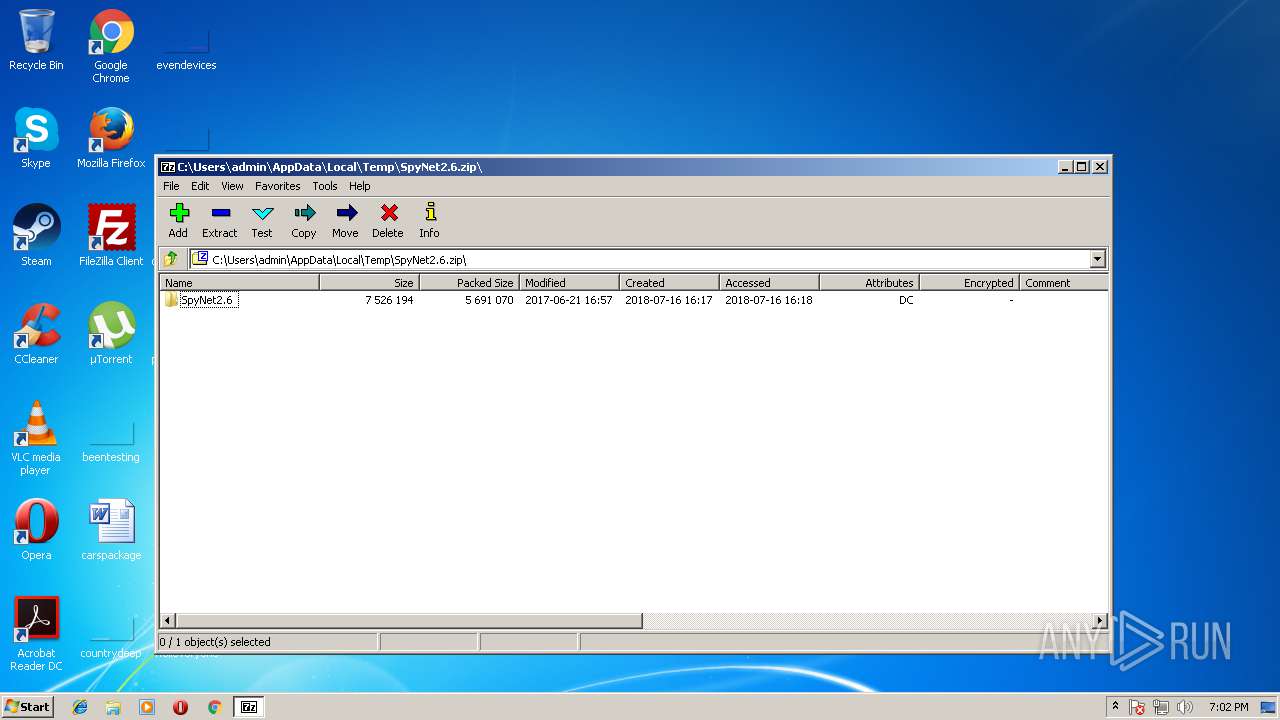
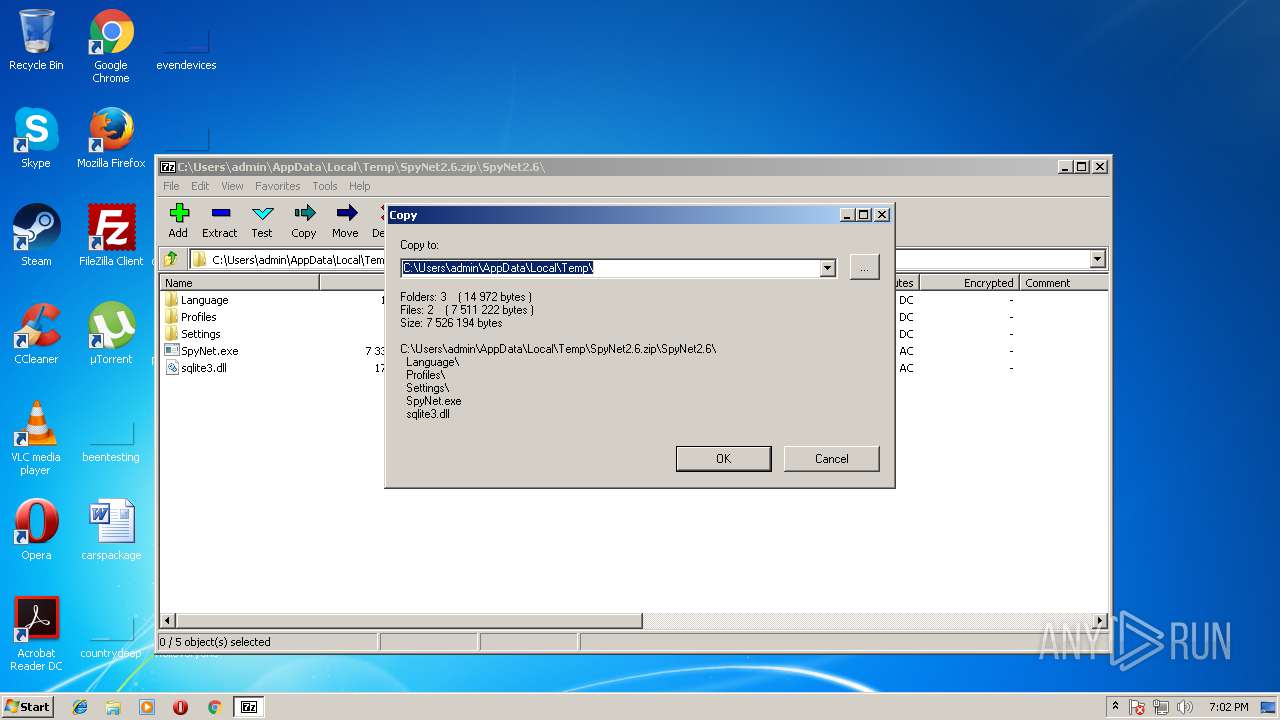
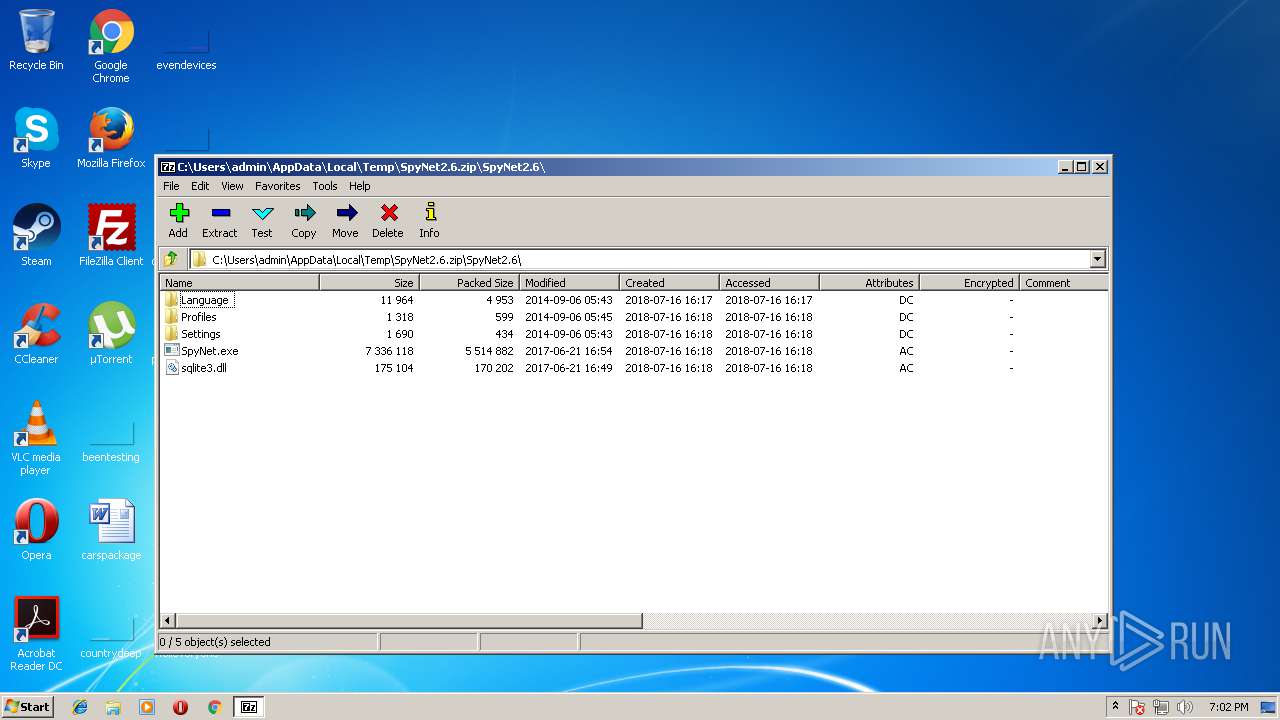
| File name: | SpyNet2.6.zip |
| Full analysis: | https://app.any.run/tasks/50d8d7f7-c69a-44fc-9681-df8a8734b247 |
| Verdict: | Malicious activity |
| Threats: | Quasar is a very popular RAT in the world thanks to its code being available in open-source. This malware can be used to control the victim’s computer remotely. |
| Analysis date: | July 16, 2018, 18:01:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | A1E7143C1A3353C98C9F6BEB987528A0 |
| SHA1: | 9BF3CF3E1FD97C385AEC544F8E2DCB60E483E52D |
| SHA256: | ACA0C13F2625E2912AA434912C2A6165C4EDE7F0F8C00919F4F8D25985F1BDD4 |
| SSDEEP: | 98304:il3QPeWRjYjEym49nQ7KaOumV+LW0DfTHRbqjeaeKNgFqKribswbm4xp9T0i/bS+:mHBBgOt+S+fTHgGKNgF7wq4jiiDdB |
MALICIOUS
Application was dropped or rewritten from another process
- SpyNet.exe (PID: 1588)
- SpyNet.exe (PID: 2372)
- windefender.exe (PID: 3136)
- SpyNet 2.6.exe (PID: 3340)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 1012)
Changes the autorun value in the registry
- SpyNet.exe (PID: 1588)
- windefender.exe (PID: 3136)
SUSPICIOUS
Creates files in the user directory
- SpyNet.exe (PID: 1588)
- windefender.exe (PID: 3136)
Executable content was dropped or overwritten
- SpyNet 2.6.exe (PID: 3340)
- 7zG.exe (PID: 3896)
- SpyNet.exe (PID: 2372)
- SpyNet.exe (PID: 1588)
Starts itself from another location
- SpyNet.exe (PID: 1588)
Checks for external IP
- SpyNet.exe (PID: 1588)
- windefender.exe (PID: 3136)
Executes scripts
- SpyNet 2.6.exe (PID: 3340)
Connects to unusual port
- windefender.exe (PID: 3136)
INFO
Dropped object may contain URL's
- SpyNet.exe (PID: 2372)
- 7zG.exe (PID: 3896)
- SpyNet.exe (PID: 1588)
- SpyNet 2.6.exe (PID: 3340)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2017:06:21 22:57:01 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | SpyNet2.6/ |
Total processes
42
Monitored processes
8
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1012 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe3_ Global\UsGthrCtrlFltPipeMssGthrPipe3 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1588 | "C:\Users\admin\AppData\Local\Temp\SpyNet.exe" | C:\Users\admin\AppData\Local\Temp\SpyNet.exe | SpyNet.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 1.3.0.0 Modules
| |||||||||||||||
| 2372 | "C:\Users\admin\Documents\SpyNet2.6\SpyNet2.6\SpyNet.exe" | C:\Users\admin\Documents\SpyNet2.6\SpyNet2.6\SpyNet.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: exeBase Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2592 | "C:\Windows\system32\cscript.exe" "C:\Users\admin\AppData\Local\Temp\teste.vbs" | C:\Windows\system32\cscript.exe | — | SpyNet 2.6.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 3136 | "C:\Users\admin\AppData\Roaming\system\windefender.exe" | C:\Users\admin\AppData\Roaming\system\windefender.exe | SpyNet.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 1.3.0.0 Modules
| |||||||||||||||
| 3280 | "C:\Program Files\7-Zip\7zFM.exe" "C:\Users\admin\AppData\Local\Temp\SpyNet2.6.zip" | C:\Program Files\7-Zip\7zFM.exe | — | explorer.exe | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip File Manager Exit code: 0 Version: 18.01 Modules
| |||||||||||||||
| 3340 | "C:\Users\admin\AppData\Local\Temp\SpyNet 2.6.exe" | C:\Users\admin\AppData\Local\Temp\SpyNet 2.6.exe | SpyNet.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3896 | "C:\Program Files\7-Zip\7zG.exe" x -o"C:\Users\admin\AppData\Local\Temp\SpyNet2.6\" -ad -an -ai#7zMap29503:98:7zEvent5041 | C:\Program Files\7-Zip\7zG.exe | 7zFM.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip GUI Exit code: 0 Version: 18.01 Modules
| |||||||||||||||
Total events
1 430
Read events
1 359
Write events
71
Delete events
0
Modification events
| (PID) Process: | (3280) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM\Columns |
| Operation: | write | Name: | 7-Zip.zip |
Value: 0100000004000000010000000400000001000000A00000000700000001000000640000000800000001000000640000000C00000001000000640000000A00000001000000640000000B00000001000000640000000900000001000000640000000F00000001000000640000001C00000001000000640000001300000001000000640000001600000001000000640000002F00000001000000640000001700000001000000640000002100000001000000640000005000000001000000640000002400000001000000640000001F0000000100000064000000200000000100000064000000 | |||
| (PID) Process: | (3896) 7zG.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\53\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3896) 7zG.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | Browse For Folder Width |
Value: 318 | |||
| (PID) Process: | (3896) 7zG.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | Browse For Folder Height |
Value: 288 | |||
| (PID) Process: | (3896) 7zG.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\Extraction |
| Operation: | write | Name: | PathHistory |
Value: 43003A005C00550073006500720073005C00610064006D0069006E005C0044006F00630075006D0065006E00740073005C005300700079004E006500740032002E0036005C000000 | |||
| (PID) Process: | (2372) SpyNet.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2372) SpyNet.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3280) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM\Columns |
| Operation: | write | Name: | FSFolder |
Value: 0100000004000000010000000400000001000000A00000000700000001000000640000000C00000001000000640000000A00000001000000640000001C00000001000000640000001F00000001000000640000002000000001000000640000000B00000000000000640000000900000000000000640000000800000000000000640000005B0000000000000064000000250000000000000064000000590000000000000064000000 | |||
| (PID) Process: | (1588) SpyNet.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\SpyNet_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (1588) SpyNet.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\SpyNet_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
6
Suspicious files
1
Text files
7
Unknown types
0
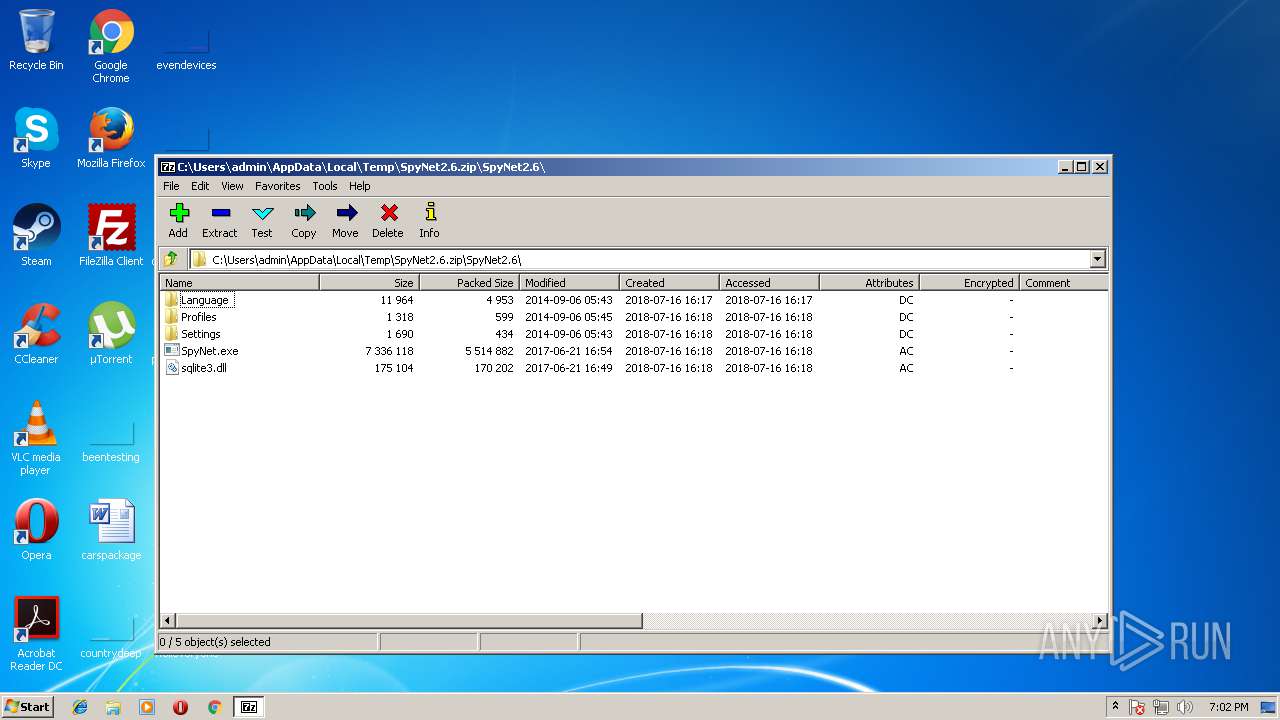
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2592 | cscript.exe | C:\Users\admin\AppData\Local\Temp\teste.txt | — | |
MD5:— | SHA256:— | |||
| 3340 | SpyNet 2.6.exe | C:\Users\admin\Documents\SpyNet2.6\SpyNet2.6\IP.txt | — | |
MD5:— | SHA256:— | |||
| 3896 | 7zG.exe | C:\Users\admin\Documents\SpyNet2.6\SpyNet2.6\Settings\Settings.ini | text | |
MD5:— | SHA256:— | |||
| 2372 | SpyNet.exe | C:\Users\admin\AppData\Local\Temp\SpyNet.exe | executable | |
MD5:— | SHA256:— | |||
| 1588 | SpyNet.exe | C:\Users\admin\AppData\Roaming\system\windefender.exe | executable | |
MD5:— | SHA256:— | |||
| 3340 | SpyNet 2.6.exe | C:\Users\admin\AppData\Local\Temp\Language\Default.ini | text | |
MD5:— | SHA256:— | |||
| 2372 | SpyNet.exe | C:\Users\admin\AppData\Local\Temp\SpyNet 2.6.exe | executable | |
MD5:— | SHA256:— | |||
| 3136 | windefender.exe | C:\Users\admin\AppData\Roaming\Logs\07-16-2018 | binary | |
MD5:— | SHA256:— | |||
| 3340 | SpyNet 2.6.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\XB3OCR2W\ip-adress_com[1].txt | html | |
MD5:— | SHA256:— | |||
| 3896 | 7zG.exe | C:\Users\admin\Documents\SpyNet2.6\SpyNet2.6\Language\Default.ini | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
5
DNS requests
3
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3136 | windefender.exe | GET | 200 | 185.194.141.58:80 | http://ip-api.com/json/ | DE | text | 351 b | malicious |
3340 | SpyNet 2.6.exe | GET | 301 | 85.93.89.6:80 | http://www.ip-adress.com/ | DE | html | 234 b | shared |
1588 | SpyNet.exe | GET | 200 | 185.194.141.58:80 | http://ip-api.com/json/ | DE | text | 351 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1588 | SpyNet.exe | 185.194.141.58:80 | ip-api.com | netcup GmbH | DE | unknown |
3136 | windefender.exe | 185.194.141.58:80 | ip-api.com | netcup GmbH | DE | unknown |
3340 | SpyNet 2.6.exe | 85.93.89.6:80 | www.ip-adress.com | Host Europe GmbH | DE | malicious |
3136 | windefender.exe | 88.240.165.5:63 | drkcmtt.duckdns.org | Turk Telekom | TR | unknown |
3340 | SpyNet 2.6.exe | 85.93.89.6:443 | www.ip-adress.com | Host Europe GmbH | DE | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ip-api.com |
| malicious |
drkcmtt.duckdns.org |
| unknown |
www.ip-adress.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1588 | SpyNet.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup ip-api.com |
1588 | SpyNet.exe | A Network Trojan was detected | MALWARE [PTsecurity] Quasar 1.3 RAT IP Lookup ip-api.com (HTTP headeer) |
3136 | windefender.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup ip-api.com |
3136 | windefender.exe | A Network Trojan was detected | MALWARE [PTsecurity] Quasar 1.3 RAT IP Lookup ip-api.com (HTTP headeer) |
1080 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |