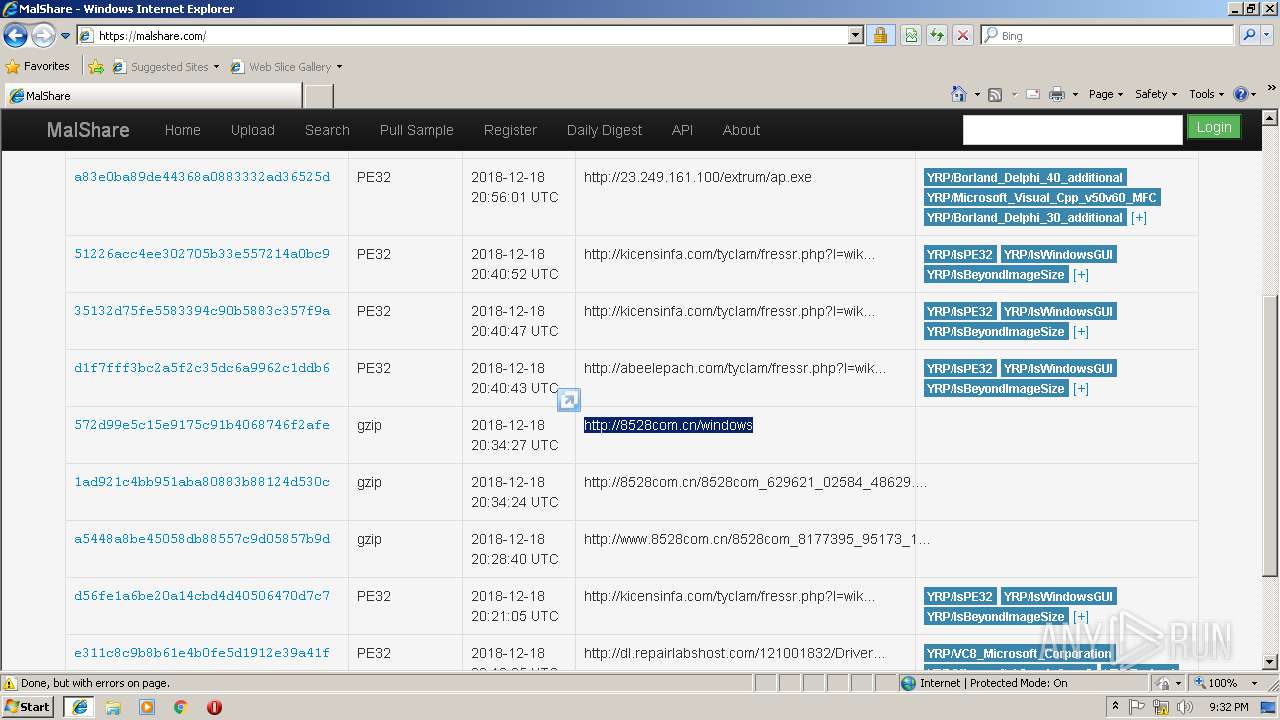
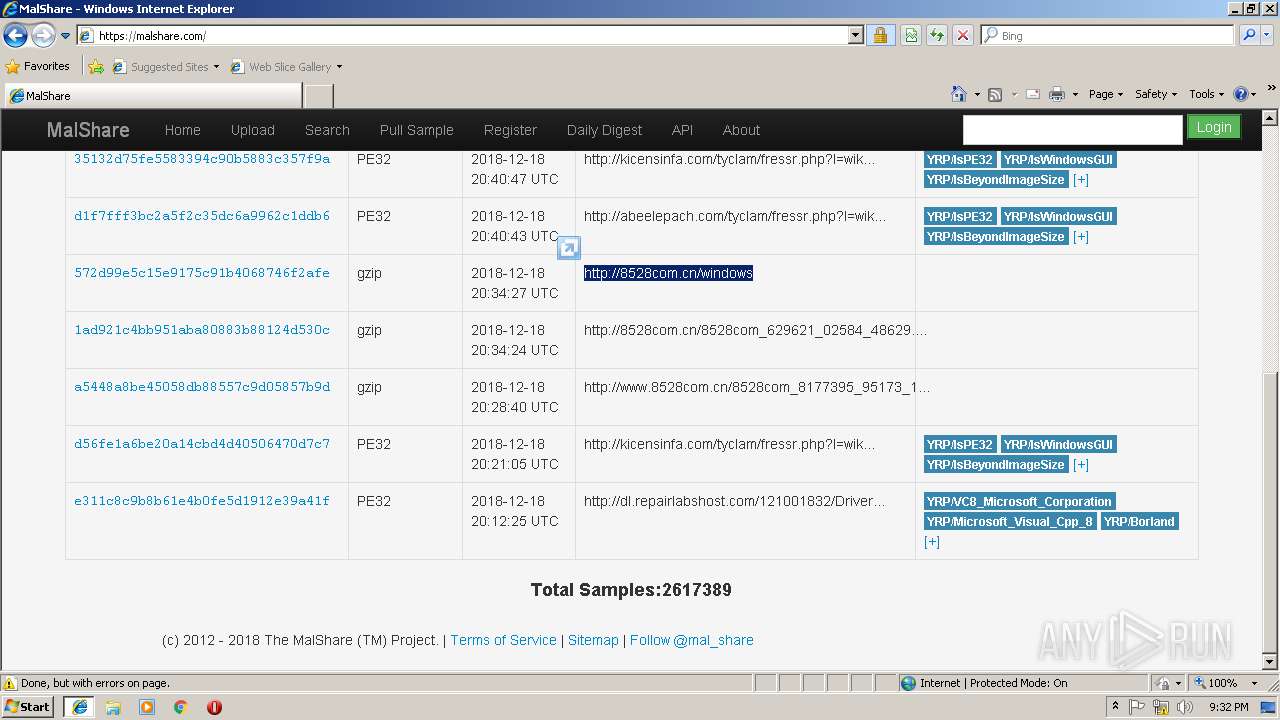
| URL: | https://www.google.com |
| Full analysis: | https://app.any.run/tasks/13d3ecb1-7f61-42f9-ae41-cf50097120ea |
| Verdict: | Malicious activity |
| Threats: | AZORult can steal banking information, including passwords and credit card details, as well as cryptocurrency. This constantly updated information stealer malware should not be taken lightly, as it continues to be an active threat. |
| Analysis date: | December 18, 2018, 21:30:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 8FFDEFBDEC956B595D257F0AAEEFD623 |
| SHA1: | EF7EFC9839C3EE036F023E9635BC3B056D6EE2DB |
| SHA256: | AC6BB669E40E44A8D9F8F0C94DFC63734049DCF6219AAC77F02EDF94B9162C09 |
| SSDEEP: | 3:N8DSLIK:2OLIK |
MALICIOUS
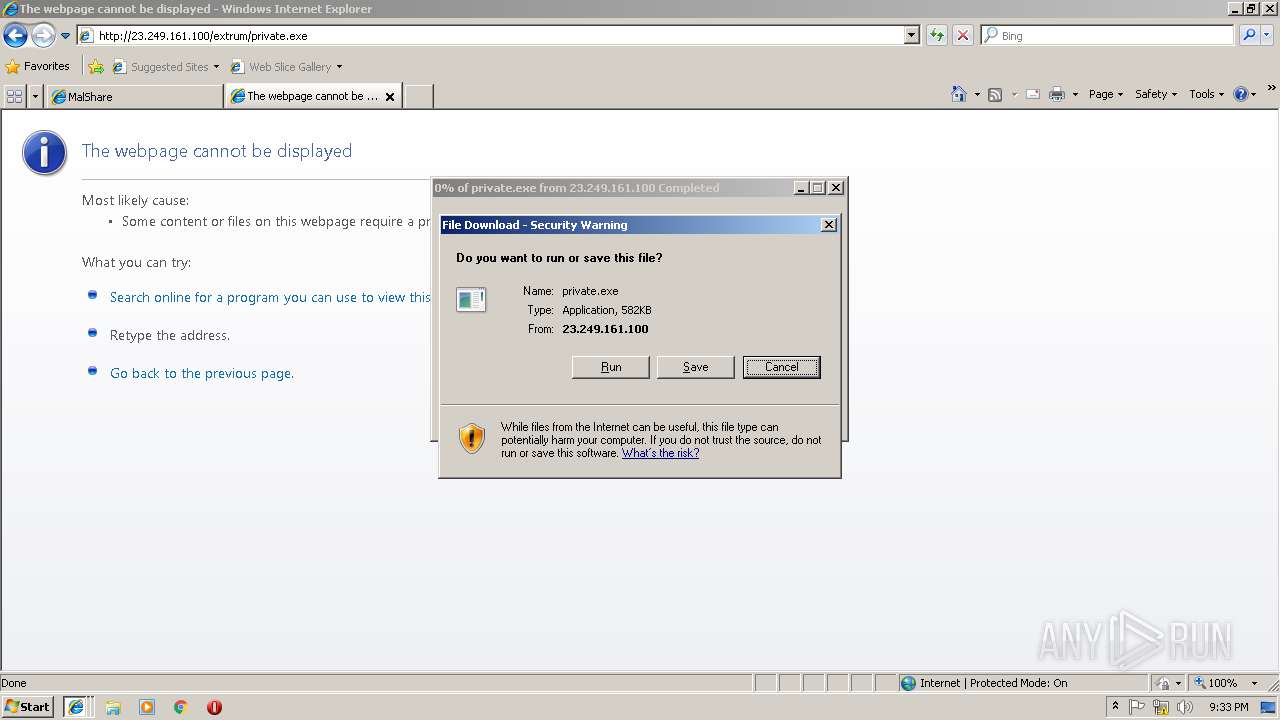
Downloads executable files from the Internet
- iexplore.exe (PID: 2740)
Application was dropped or rewritten from another process
- private[1].exe (PID: 3656)
- private[1].exe (PID: 836)
Downloads executable files from IP
- iexplore.exe (PID: 2740)
Actions looks like stealing of personal data
- private[1].exe (PID: 836)
Loads dropped or rewritten executable
- private[1].exe (PID: 836)
AZORULT was detected
- private[1].exe (PID: 836)
URSNIF was detected
- iexplore.exe (PID: 2740)
Connects to CnC server
- private[1].exe (PID: 836)
SUSPICIOUS
Executable content was dropped or overwritten
- iexplore.exe (PID: 2740)
- iexplore.exe (PID: 3540)
- private[1].exe (PID: 836)
Application launched itself
- private[1].exe (PID: 3656)
Connects to server without host name
- private[1].exe (PID: 836)
INFO
Changes internet zones settings
- iexplore.exe (PID: 2952)
- iexplore.exe (PID: 3540)
Reads Internet Cache Settings
- iexplore.exe (PID: 3096)
- iexplore.exe (PID: 2952)
- iexplore.exe (PID: 772)
- iexplore.exe (PID: 2740)
Creates files in the user directory
- iexplore.exe (PID: 3096)
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 3780)
- iexplore.exe (PID: 772)
- iexplore.exe (PID: 2740)
- iexplore.exe (PID: 3540)
Reads settings of System Certificates
- iexplore.exe (PID: 2952)
- iexplore.exe (PID: 772)
- iexplore.exe (PID: 3540)
Application launched itself
- iexplore.exe (PID: 2952)
- iexplore.exe (PID: 3540)
Reads internet explorer settings
- iexplore.exe (PID: 3096)
- iexplore.exe (PID: 772)
- iexplore.exe (PID: 2740)
Changes settings of System certificates
- iexplore.exe (PID: 2952)
- iexplore.exe (PID: 3540)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2952)
- iexplore.exe (PID: 3540)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 2740)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
41
Monitored processes
8
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 772 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3540 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 836 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\D2YPIJ90\private[1].exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\D2YPIJ90\private[1].exe | private[1].exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2740 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3540 CREDAT:6419 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2952 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3096 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2952 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3540 | "C:\Program Files\Internet Explorer\iexplore.exe" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3656 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\D2YPIJ90\private[1].exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\D2YPIJ90\private[1].exe | — | iexplore.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3780 | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe -Embedding | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe | — | svchost.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe® Flash® Player Installer/Uninstaller 26.0 r0 Exit code: 0 Version: 26,0,0,131 Modules
| |||||||||||||||
Total events
1 604
Read events
1 355
Write events
242
Delete events
7
Modification events
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000069000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {303591C1-030C-11E9-91D7-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 3 | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E2070C000200120015001E0033008A00 | |||
Executable files
50
Suspicious files
10
Text files
192
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2952 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\R9ZEWH8D\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2952 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3096 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@google[2].txt | — | |
MD5:— | SHA256:— | |||
| 3096 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\google_com[1].txt | — | |
MD5:— | SHA256:— | |||
| 2952 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF446B8EE494C2725D.TMP | — | |
MD5:— | SHA256:— | |||
| 2952 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF04DB138F89D52C0E.TMP | — | |
MD5:— | SHA256:— | |||
| 2952 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF14FF8B4BAE1D18A0.TMP | — | |
MD5:— | SHA256:— | |||
| 2952 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{303591C2-030C-11E9-91D7-5254004A04AF}.dat | — | |
MD5:— | SHA256:— | |||
| 2952 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFAC64A099468E902D.TMP | — | |
MD5:— | SHA256:— | |||
| 2952 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\RecoveryStore.{303591C1-030C-11E9-91D7-5254004A04AF}.dat | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
50
TCP/UDP connections
47
DNS requests
20
Threats
12
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
772 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/rs/5m/O4/ic/fea28513/8ad63be1.png | US | image | 603 b | whitelisted |
772 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/fd/ls/l?IG=C974D8E1E54D480DBFB9B9A0290A5360&CID=267E781638EF68D23EEA74DF39AF6984&Type=Event.CPT&DATA={"pp":{"S":"L","FC":93,"BC":218,"SE":-1,"TC":-1,"H":343,"BP":390,"CT":406,"IL":6},"ad":[192,100,1260,560,1260,498,0]}&P=SERP&DA=DUB02 | US | image | 603 b | whitelisted |
772 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/sa/simg/SharedSpriteDesktopRewards_022118.png | US | image | 5.73 Kb | whitelisted |
3540 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
772 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/rs/5m/NX/ic/ead77415/3938fd08.png | US | image | 609 b | whitelisted |
3540 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
772 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/rs/5m/18u/cj,nj/d5712f1a/e58e5083.js | US | text | 800 b | whitelisted |
772 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/search?q=malshare&src=IE-SearchBox&FORM=IE8SRC | US | html | 38.4 Kb | whitelisted |
772 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/rb/5m/cj,nj/3e6a7d75/9a358300.js?bu=EpUesx7eHeEd7gTvHfEdvx7zHfodgh6rHqkenh6THbUcuByWHQ | US | text | 4.95 Kb | whitelisted |
772 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/rs/4Y/4f/cj,nj/8e81c8c7/37f3511b.js | US | text | 529 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2952 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3096 | iexplore.exe | 172.217.22.68:443 | www.google.com | Google Inc. | US | whitelisted |
2952 | iexplore.exe | 172.217.22.68:443 | www.google.com | Google Inc. | US | whitelisted |
3540 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
772 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
772 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
772 | iexplore.exe | 104.211.96.15:80 | a7d323651ed33eb6586fdc94fdb68a9f.clo.footprintdns.com | Microsoft Corporation | IN | whitelisted |
772 | iexplore.exe | 52.231.32.10:80 | 434f657616bbeeb1d5e9e886fd87f6ef.clo.footprintdns.com | Microsoft Corporation | KR | whitelisted |
772 | iexplore.exe | 65.55.163.82:443 | login.live.com | Microsoft Corporation | US | whitelisted |
772 | iexplore.exe | 204.79.197.222:80 | fp.msedge.net | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
www.google.com |
| malicious |
login.live.com |
| whitelisted |
a7d323651ed33eb6586fdc94fdb68a9f.clo.footprintdns.com |
| unknown |
434f657616bbeeb1d5e9e886fd87f6ef.clo.footprintdns.com |
| unknown |
02d3adc834bffacabd342ab699a81fd4.clo.footprintdns.com |
| unknown |
fp.msedge.net |
| whitelisted |
malshare.com |
| whitelisted |
ssl.google-analytics.com |
| whitelisted |
platform.twitter.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2740 | iexplore.exe | A Network Trojan was detected | ET INFO Executable Download from dotted-quad Host |
2740 | iexplore.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2740 | iexplore.exe | Potentially Bad Traffic | ET INFO SUSPICIOUS Dotted Quad Host MZ Response |
836 | private[1].exe | A Network Trojan was detected | ET TROJAN AZORult Variant.4 Checkin M2 |
836 | private[1].exe | A Network Trojan was detected | MALWARE [PTsecurity] AZORult client request |
836 | private[1].exe | A Network Trojan was detected | MALWARE [PTsecurity] AZORult HTTP Header |
836 | private[1].exe | Potentially Bad Traffic | ET INFO GENERIC SUSPICIOUS POST to Dotted Quad with Fake Browser 1 |
836 | private[1].exe | A Network Trojan was detected | MALWARE [PTsecurity] AZORult HTTP Header |
836 | private[1].exe | A Network Trojan was detected | MALWARE [PTsecurity] AZORult client request |
3 ETPRO signatures available at the full report