| File name: | xxx.exe |
| Full analysis: | https://app.any.run/tasks/8fe7848d-0c5a-4e69-b15b-53dc410f80cb |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | November 17, 2024, 22:28:21 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 8 sections |
| MD5: | E5FC83A59378BD17F1066A3FB877913B |
| SHA1: | C905F28632DD0E21EE282124B44C3AD0B35B33D1 |
| SHA256: | AC0093840FE2AAD75AEA8A8417BB745CE7BFE8075B382938B24B0A15C63A56D4 |
| SSDEEP: | 98304:/M0F9VzVC9oW2vh/7EB4rXEbxTSpoQ3DFvyci3XaGs38RoOh/ildVPcx54OaolmZ:PE6nOmz58+ |
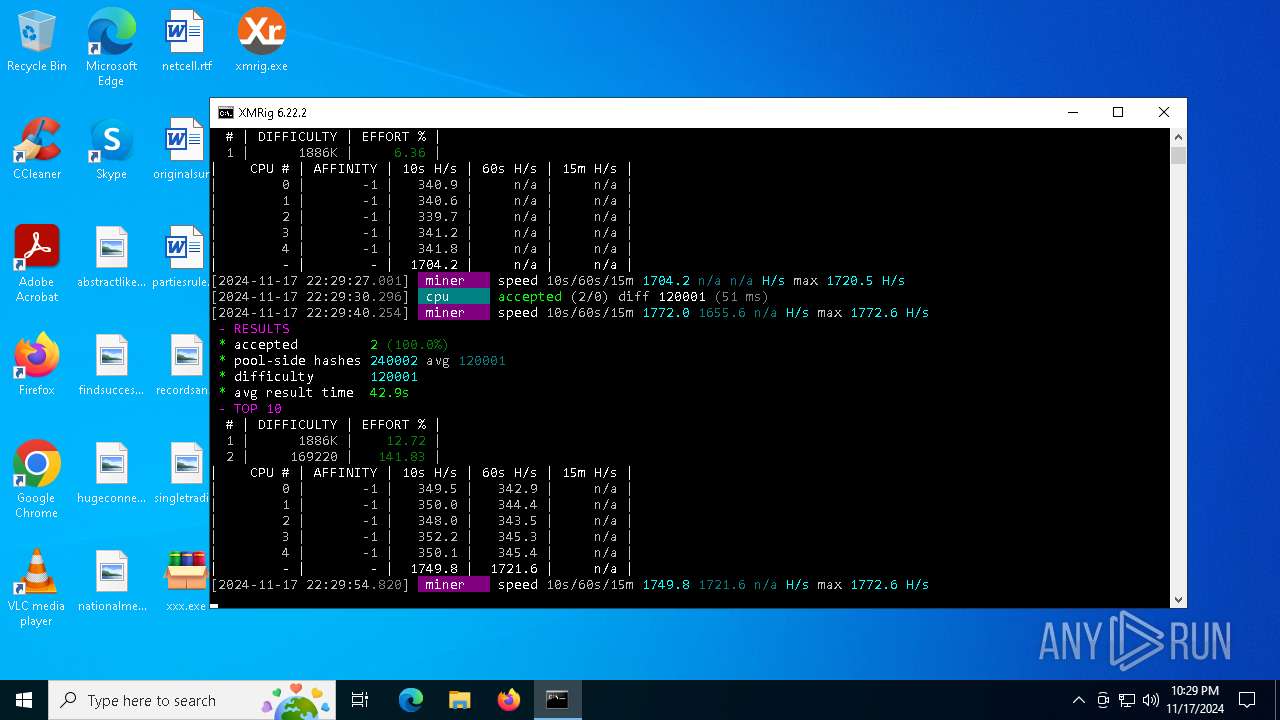
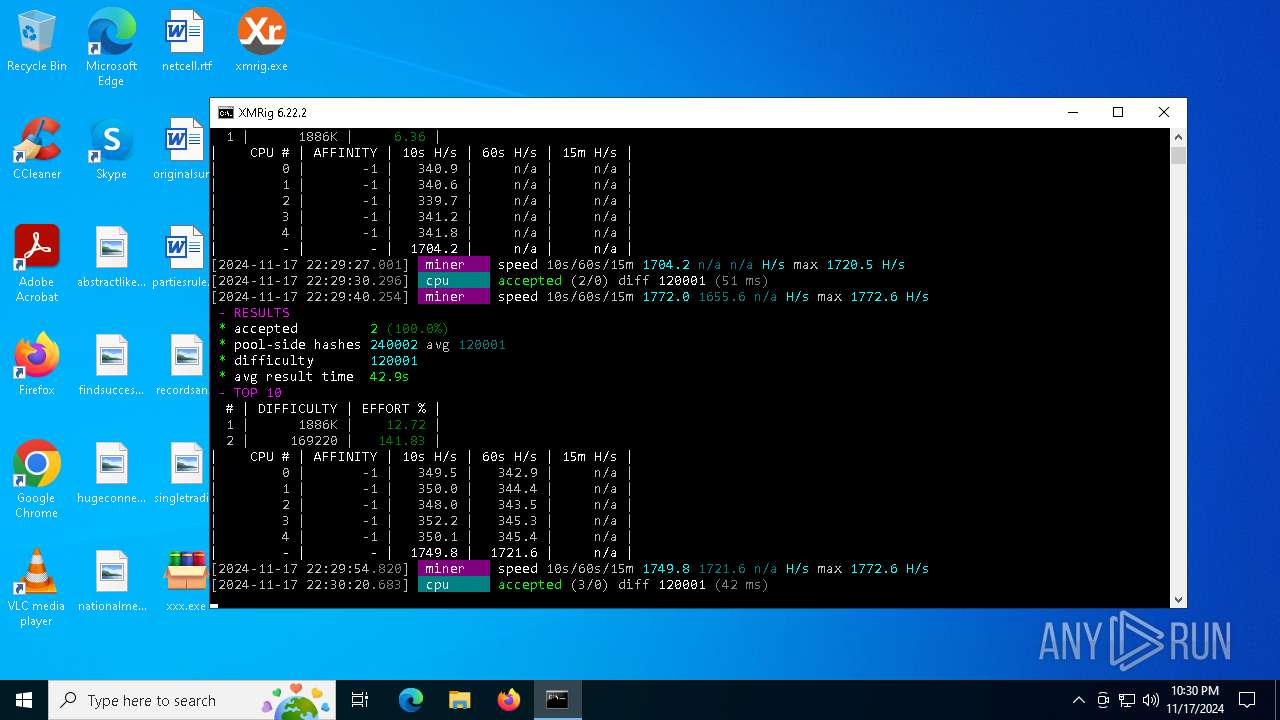
MALICIOUS
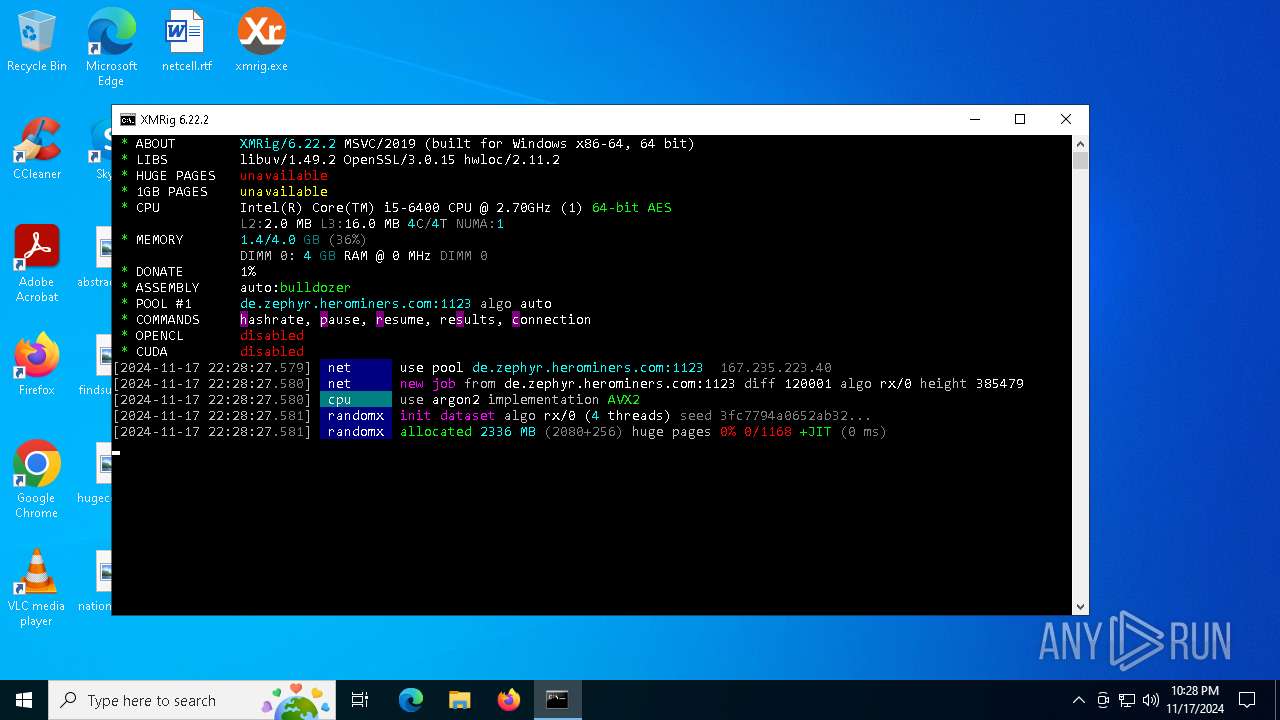
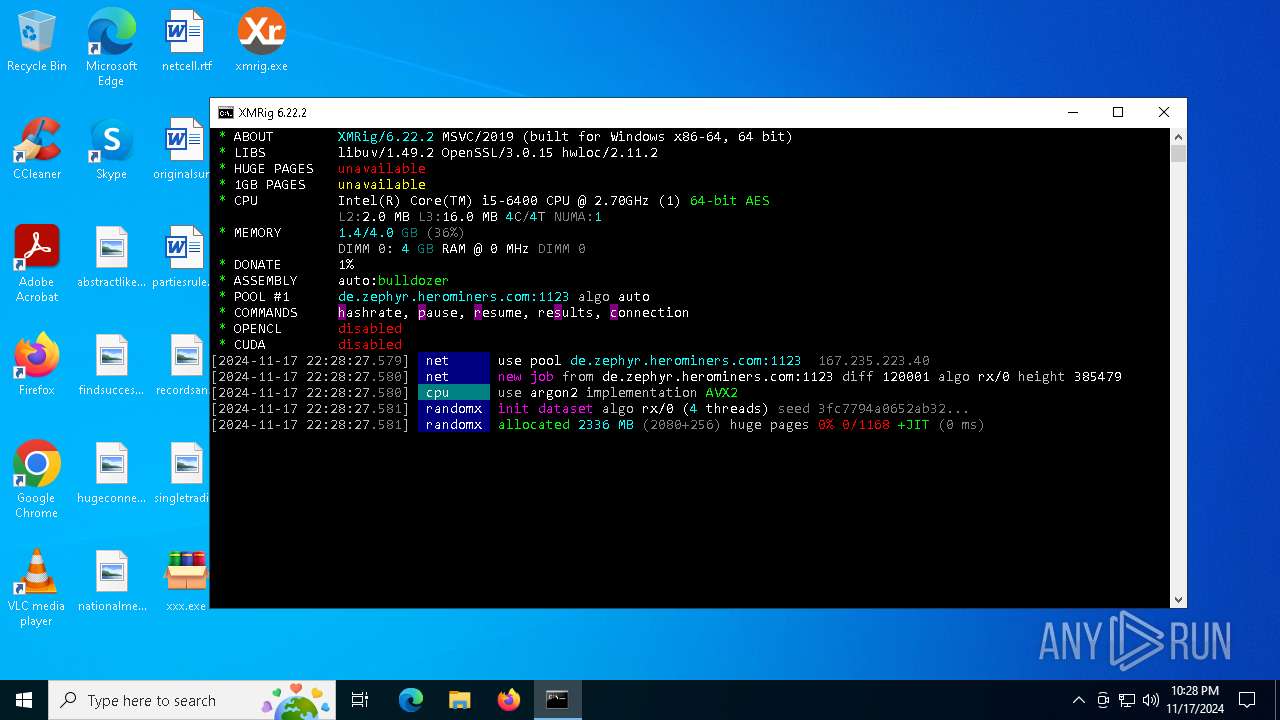
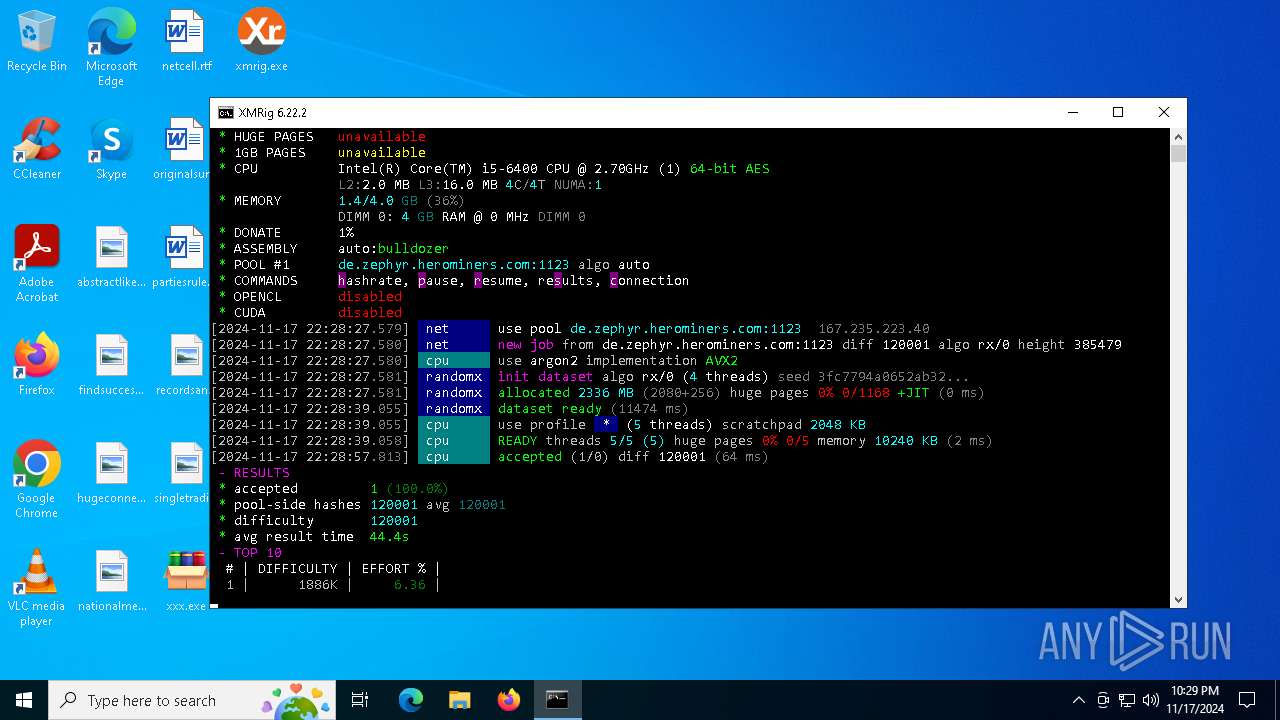
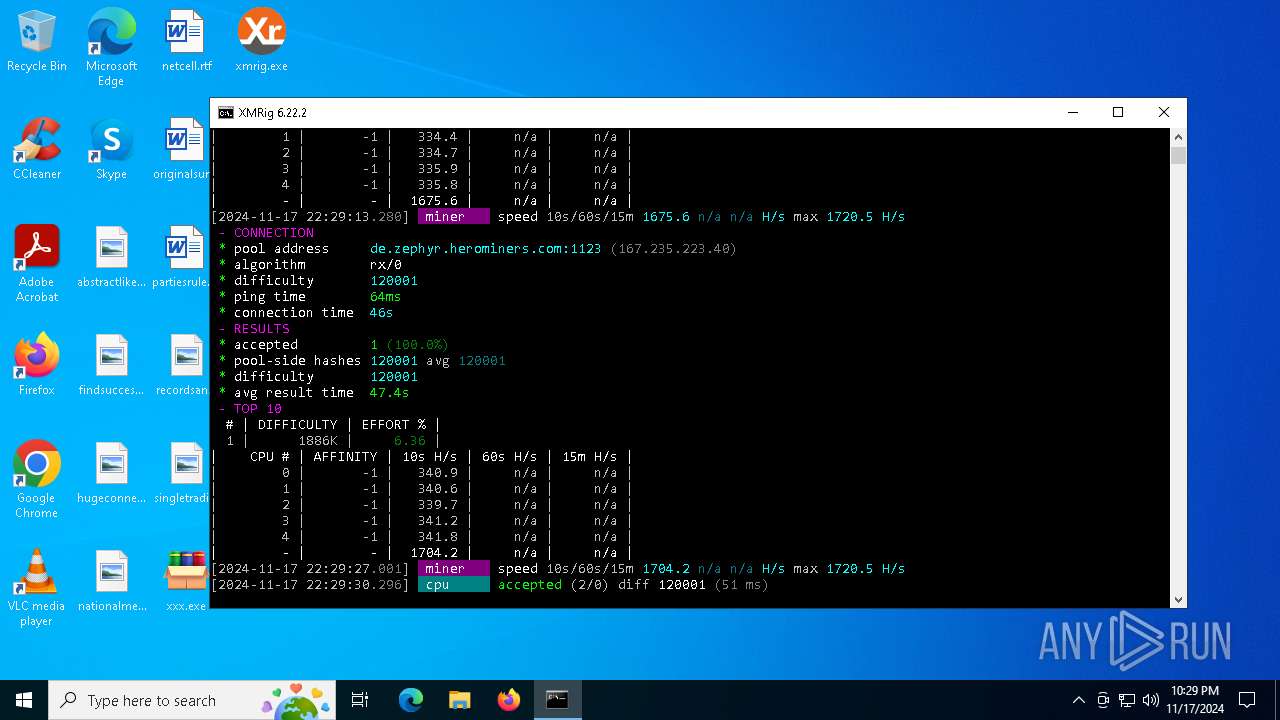
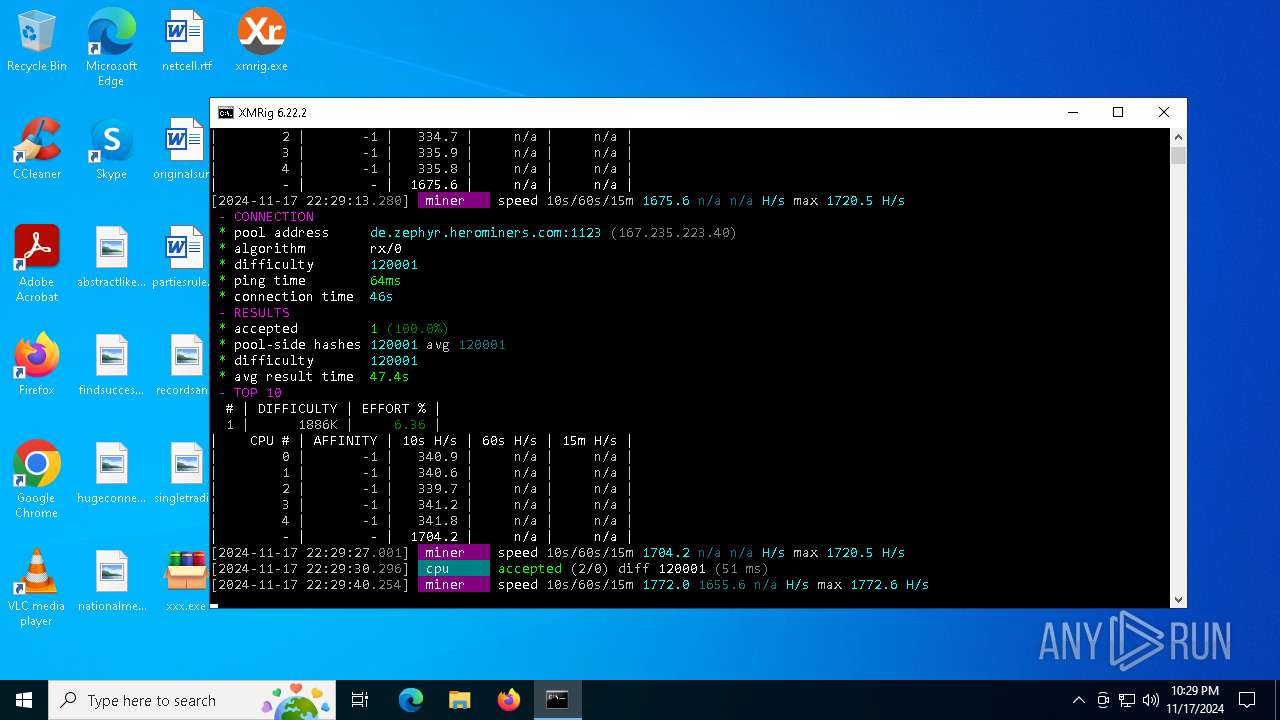
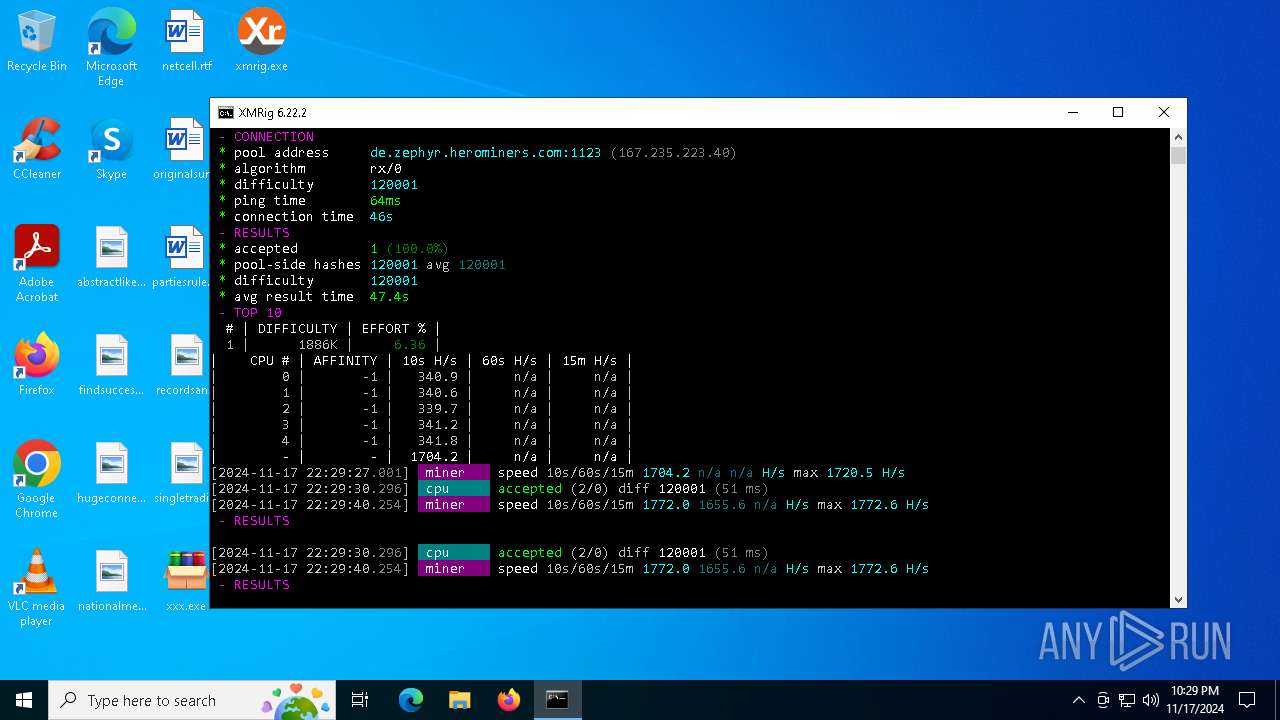
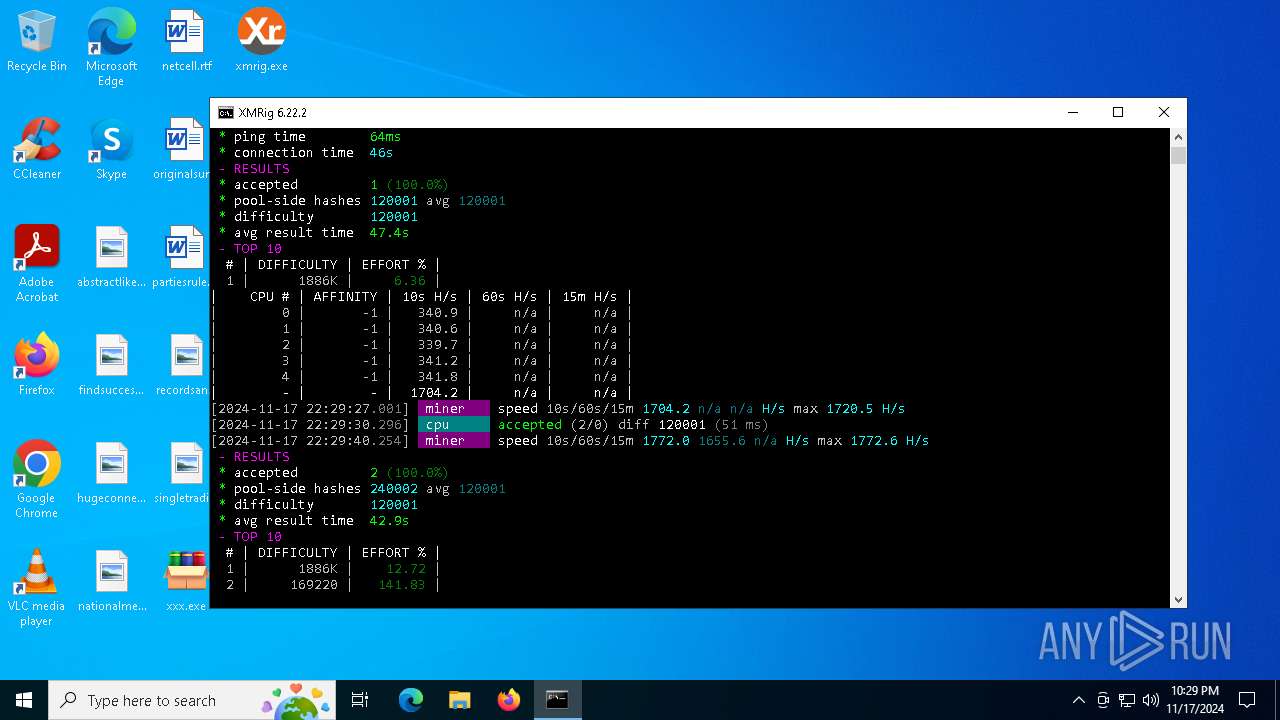
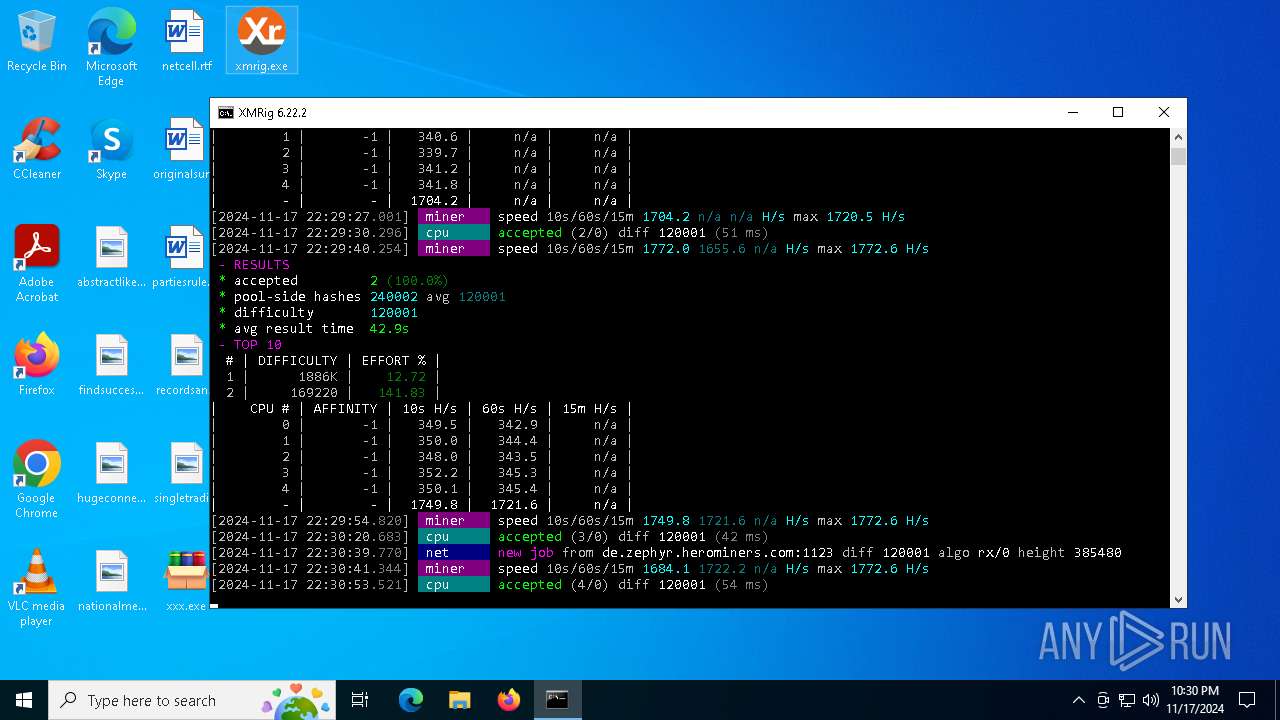
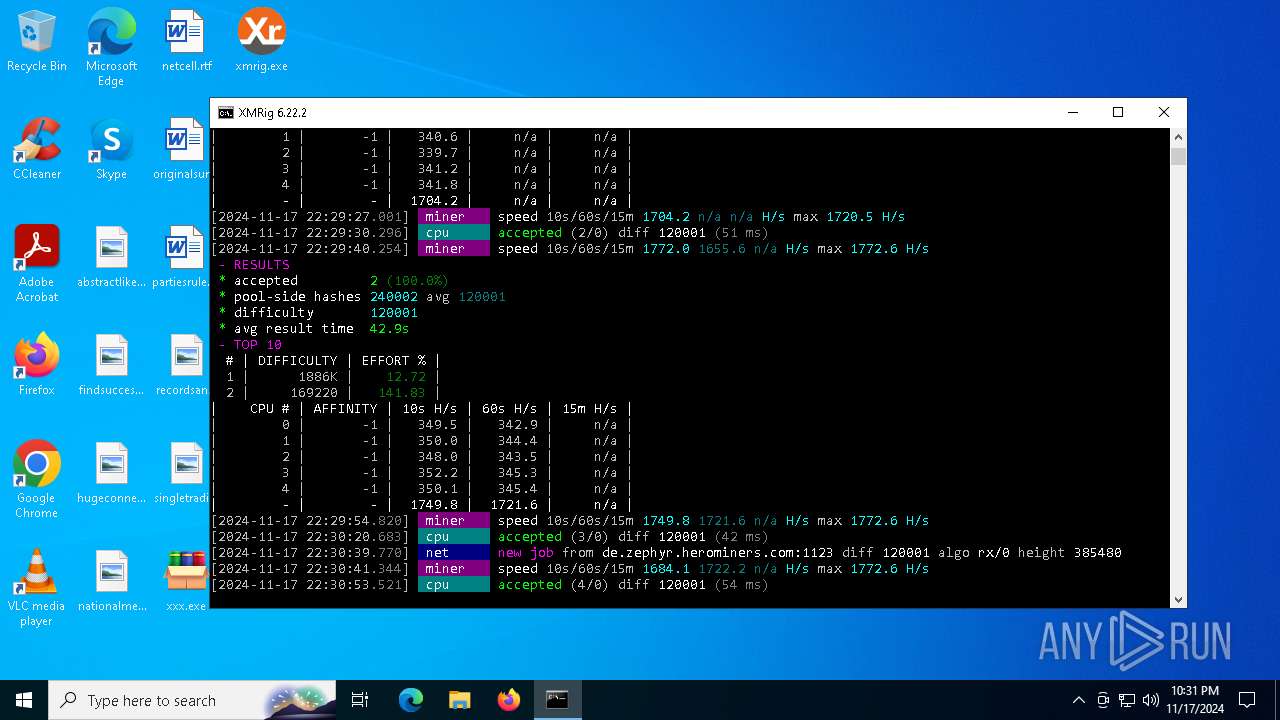
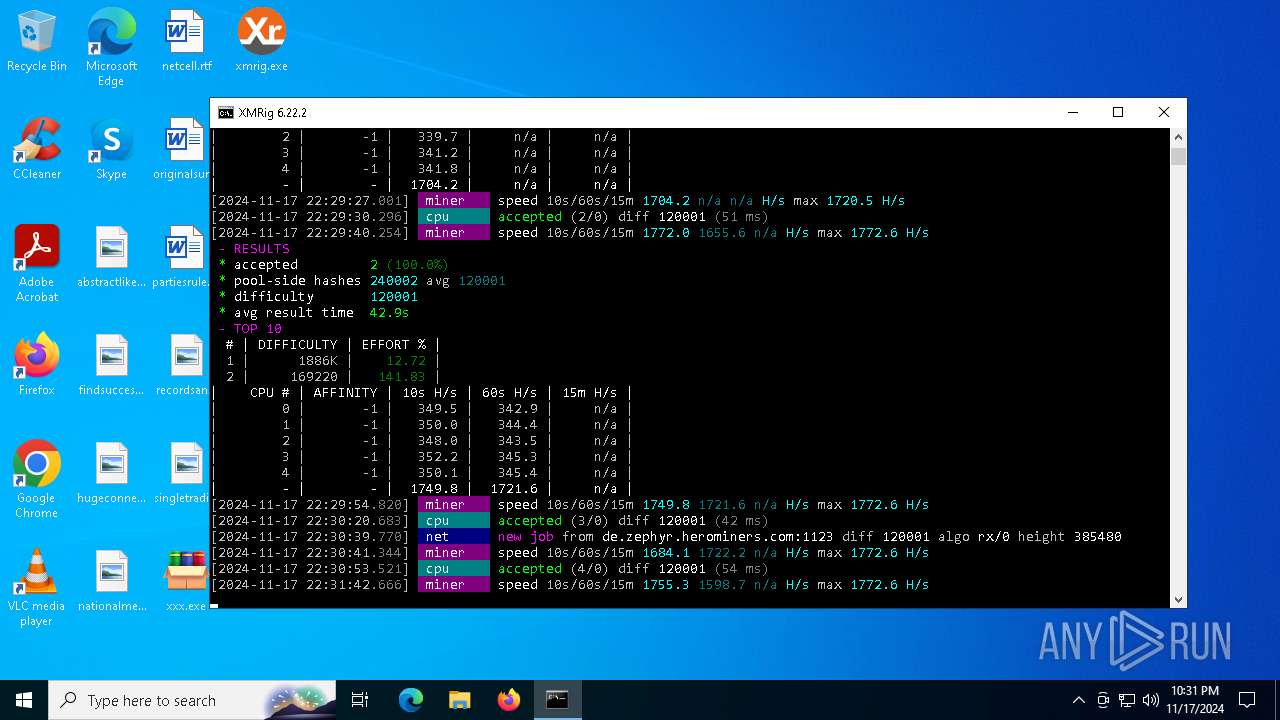
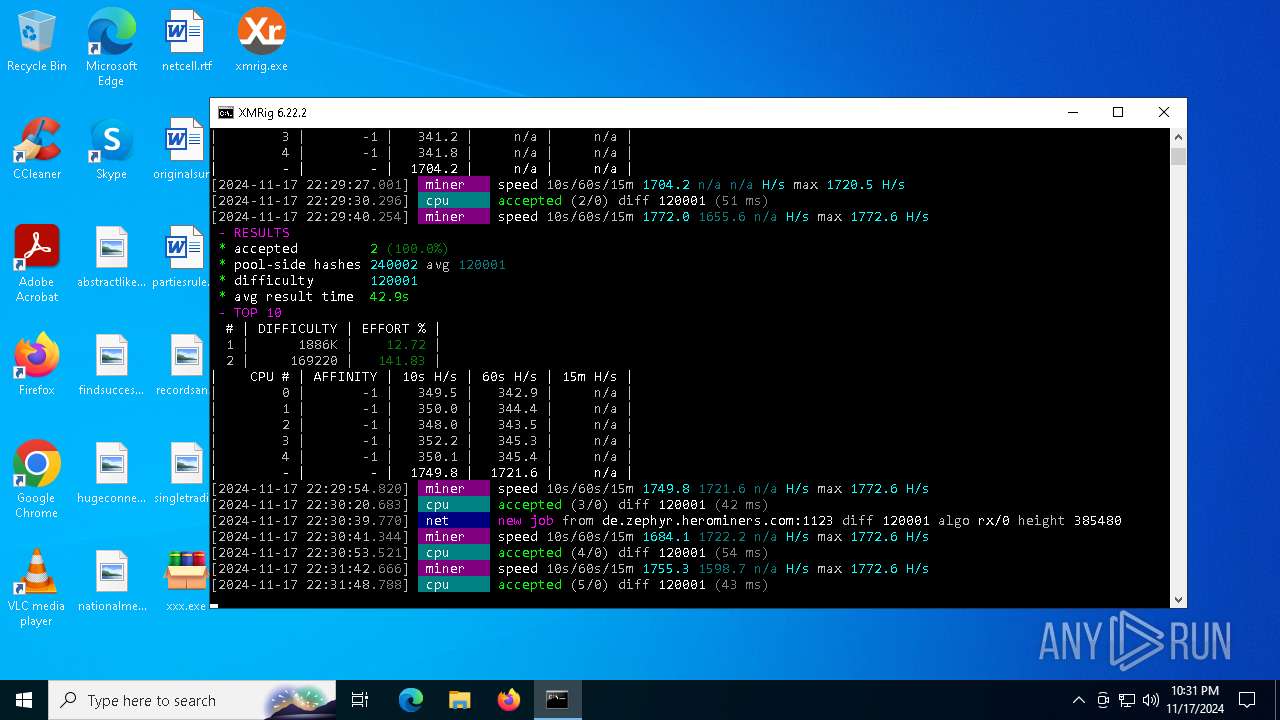
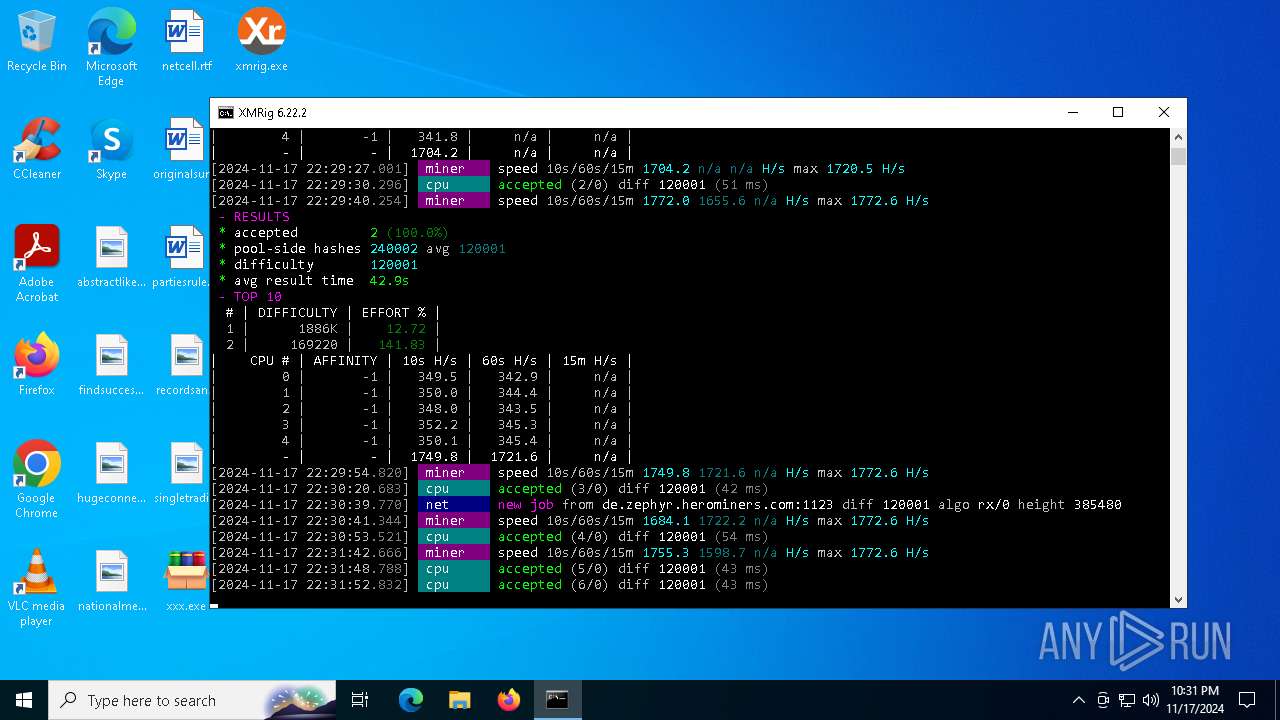
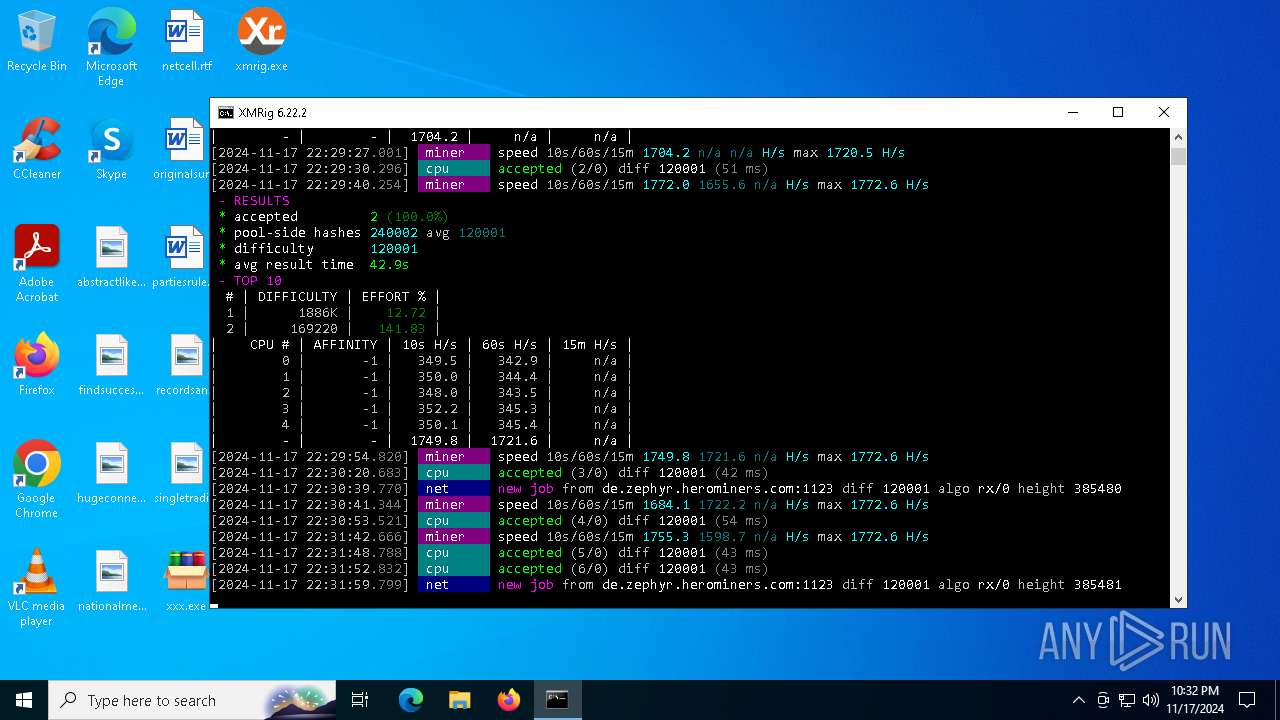
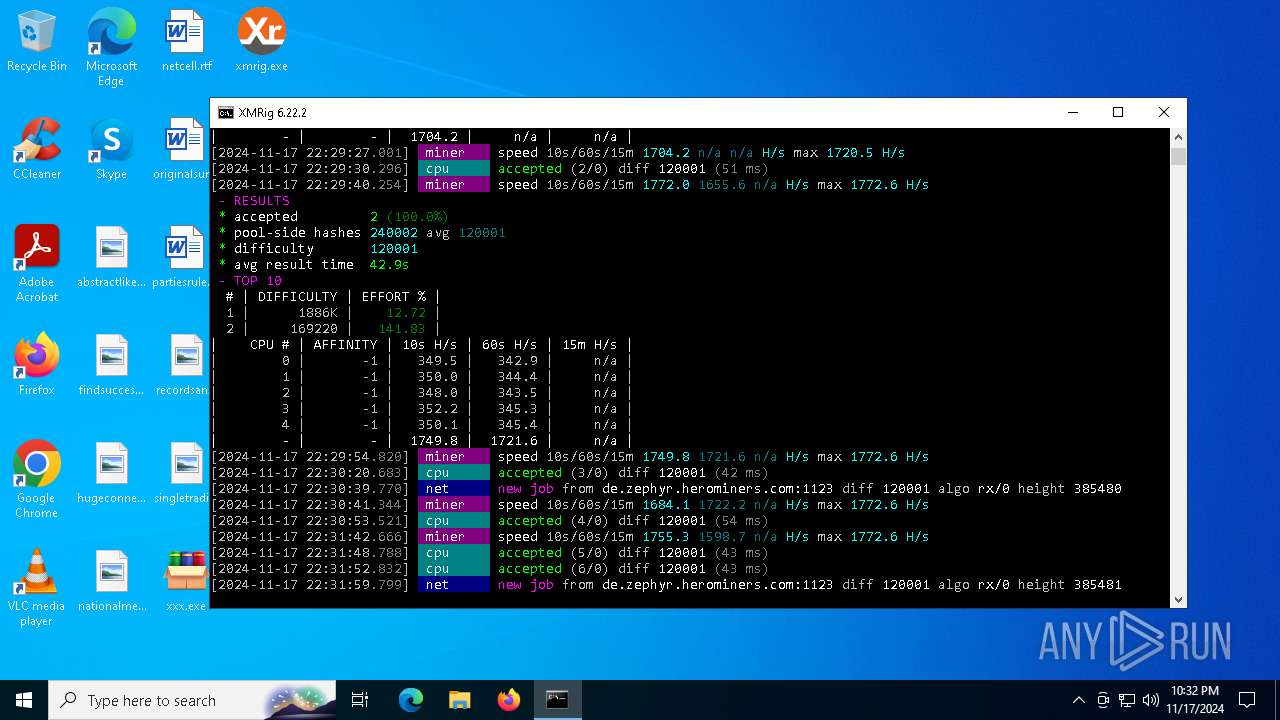
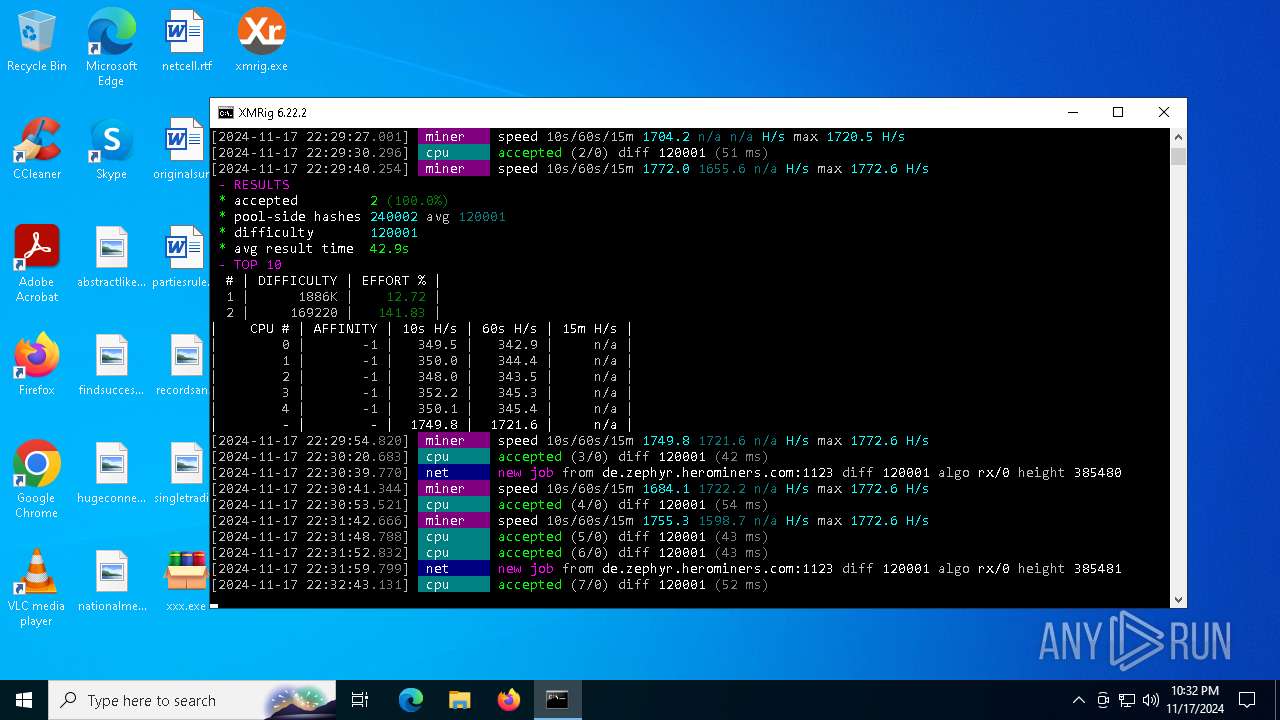
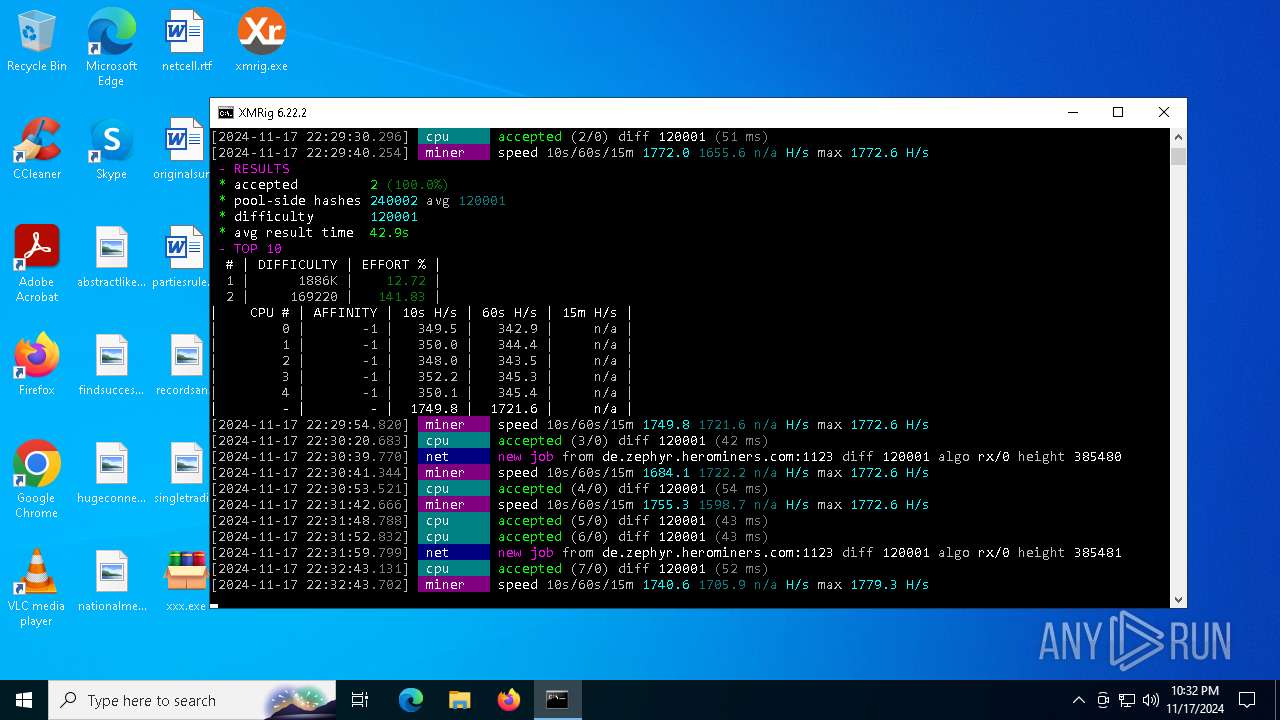
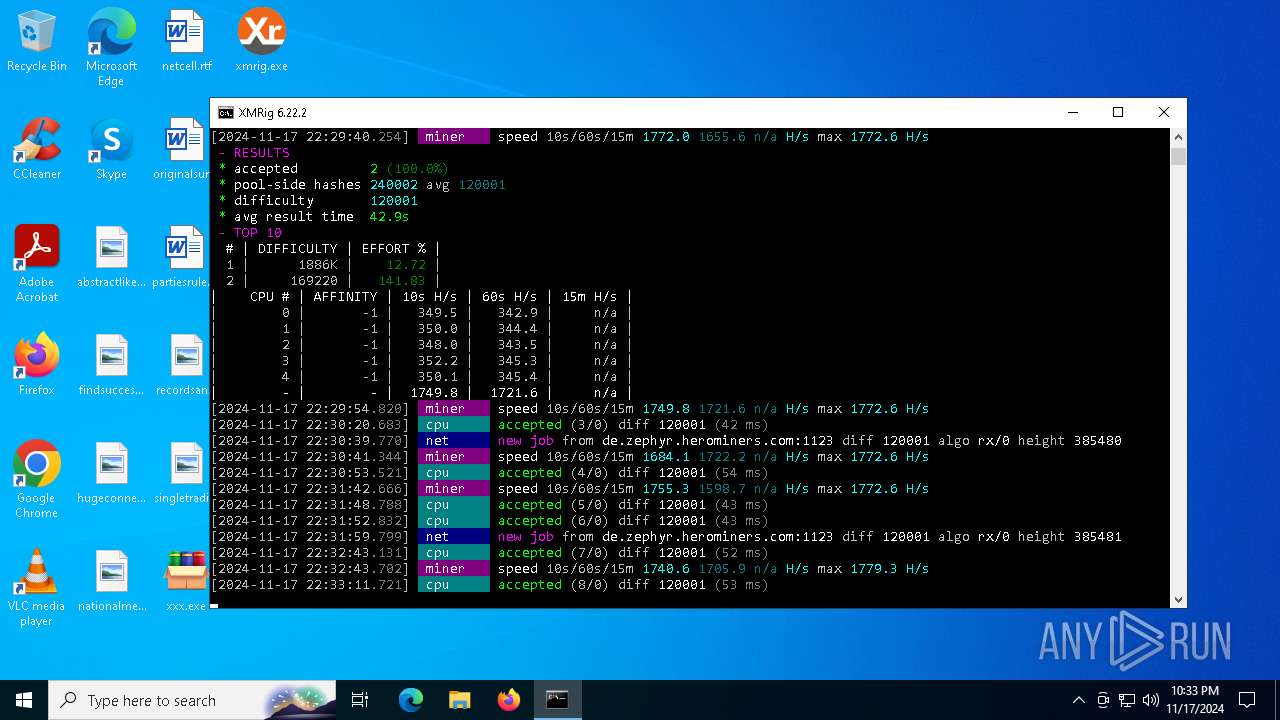
XMRig has been detected
- xmrig.exe (PID: 5100)
MINER has been detected (SURICATA)
- svchost.exe (PID: 2172)
- xmrig.exe (PID: 5100)
Connects to the CnC server
- xmrig.exe (PID: 5100)
XMRIG has been detected (YARA)
- xmrig.exe (PID: 5100)
SUSPICIOUS
Reads security settings of Internet Explorer
- xxx.exe (PID: 5328)
Drops a system driver (possible attempt to evade defenses)
- xxx.exe (PID: 5328)
Executable content was dropped or overwritten
- xxx.exe (PID: 5328)
Reads the date of Windows installation
- xxx.exe (PID: 5328)
Starts CMD.EXE for commands execution
- xxx.exe (PID: 5328)
Executing commands from a ".bat" file
- xxx.exe (PID: 5328)
Crypto Currency Mining Activity Detected
- svchost.exe (PID: 2172)
- xmrig.exe (PID: 5100)
Potential Corporate Privacy Violation
- xmrig.exe (PID: 5100)
Connects to unusual port
- xmrig.exe (PID: 5100)
INFO
Checks supported languages
- xxx.exe (PID: 5328)
- xmrig.exe (PID: 5100)
Reads the computer name
- xxx.exe (PID: 5328)
- xmrig.exe (PID: 5100)
The process uses the downloaded file
- xxx.exe (PID: 5328)
Process checks computer location settings
- xxx.exe (PID: 5328)
Reads the software policy settings
- slui.exe (PID: 3396)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:05:12 10:17:07+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.33 |
| CodeSize: | 288768 |
| InitializedDataSize: | 212480 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x32ee0 |
| OSVersion: | 5.2 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
Total processes
140
Monitored processes
8
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 884 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2172 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3396 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
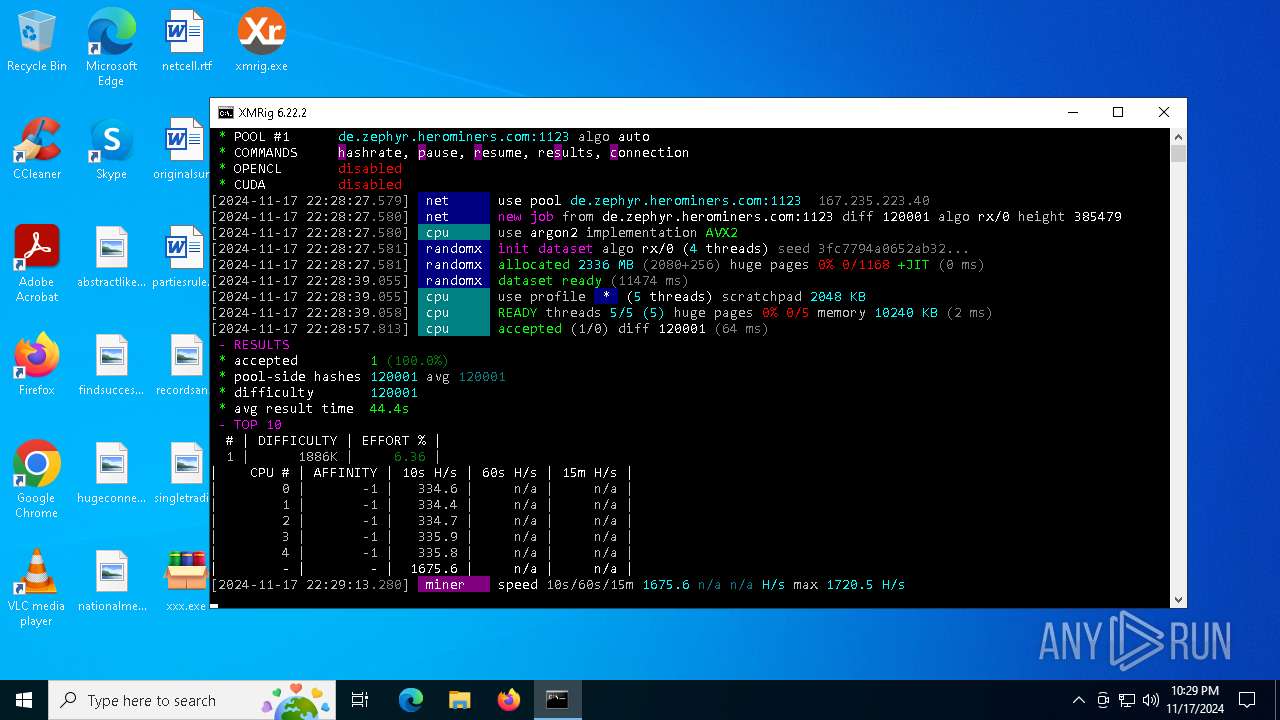
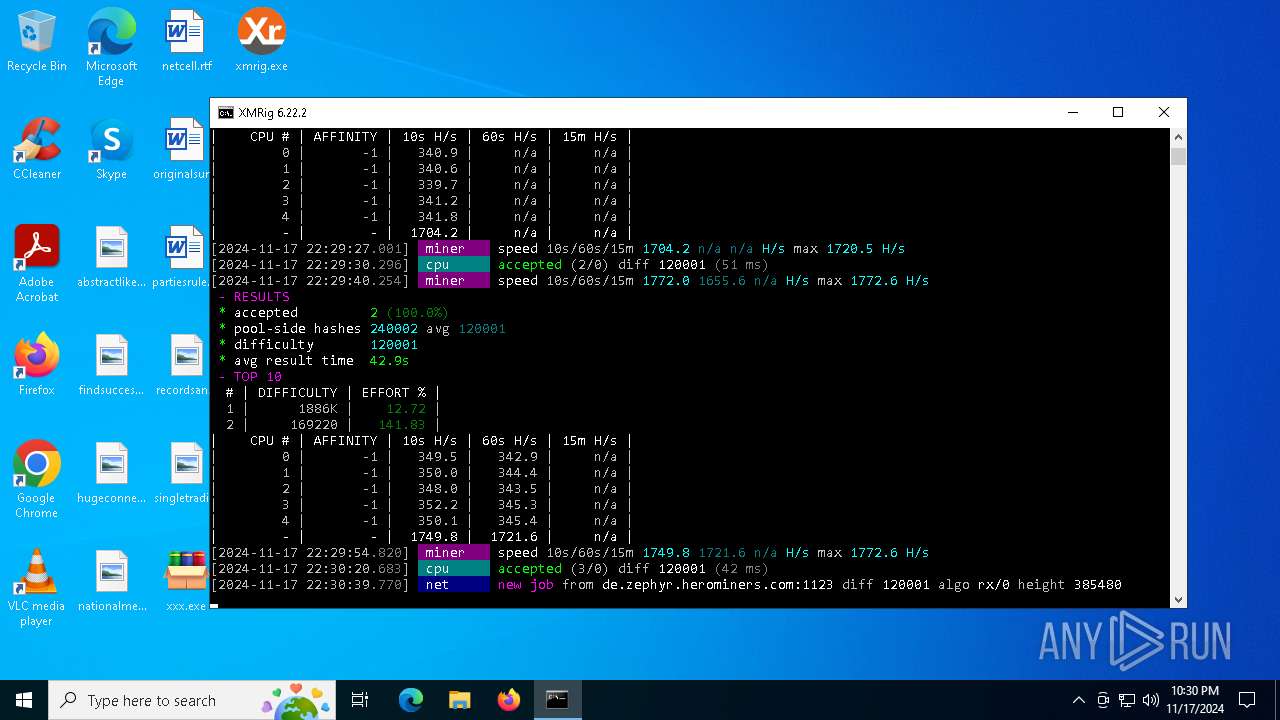
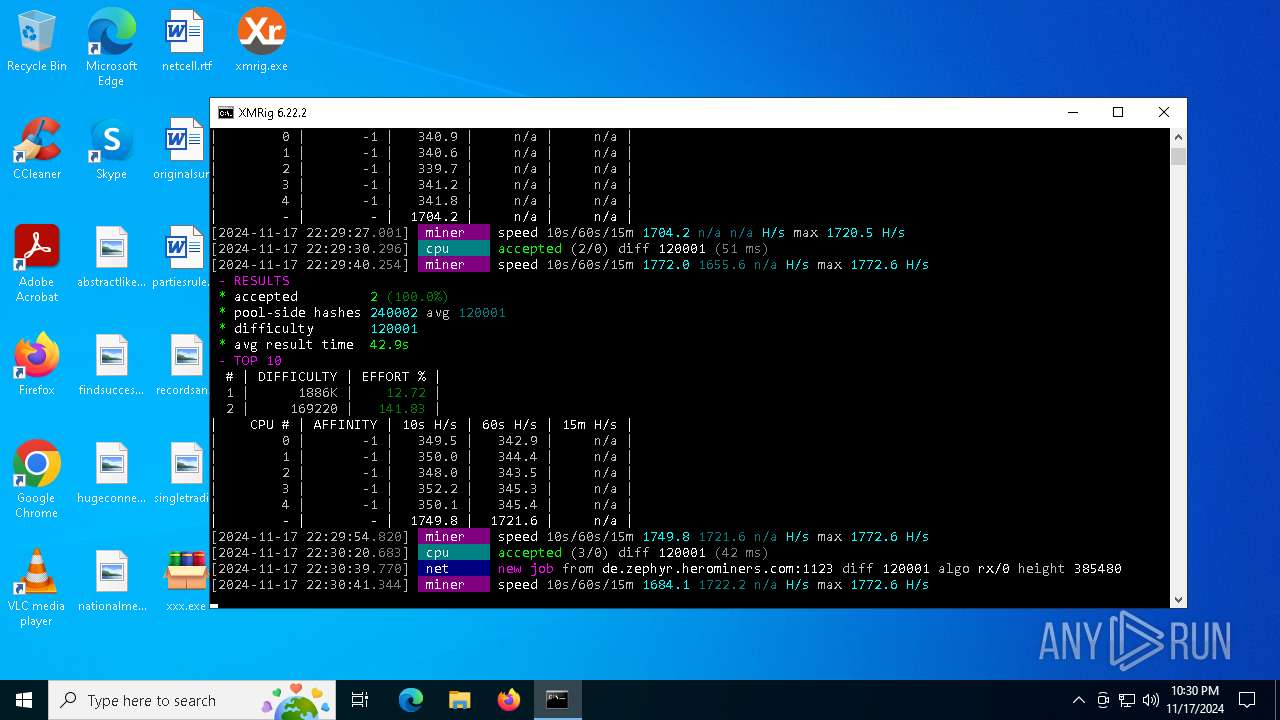
| 5100 | xmrig.exe -o de.zephyr.herominers.com:1123 -u ZEPHYR2V9RpLBN5LtbMYA7BCszk3ZdrGh2q3Cek7kE3uLD8Eu4fztVFHMNk3gJJz5NGsu8uXBTQv22juGNx7KxH5YzagYeJjbsW3W.any -p x --donate-level 0 --max-cpu-usage 100 --threads 5 | C:\Users\admin\Desktop\xmrig.exe | cmd.exe | ||||||||||||
User: admin Company: www.xmrig.com Integrity Level: MEDIUM Description: XMRig miner Version: 6.22.2 Modules
| |||||||||||||||
| 5328 | "C:\Users\admin\Desktop\xxx.exe" | C:\Users\admin\Desktop\xxx.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 6256 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6648 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6660 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\mi.bat" " | C:\Windows\System32\cmd.exe | — | xxx.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
1 383
Read events
1 383
Write events
0
Delete events
0
Modification events
Executable files
2
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5328 | xxx.exe | C:\Users\admin\Desktop\xmrig.exe | executable | |
MD5:F6D520AE125F03056C4646C508218D16 | SHA256:D2FCF28897DDC2137141D838B734664FF7592E03FCD467A433A51CB4976B4FB1 | |||
| 5328 | xxx.exe | C:\Users\admin\Desktop\mi.bat | text | |
MD5:9576AA7181BA02ADE8335661F4D4B323 | SHA256:674BFF27A306C63F65C1EAF99599AD7C2AF50A68B942806FEF651CC4EEAB418C | |||
| 5328 | xxx.exe | C:\Users\admin\Desktop\WinRing0x64.sys | executable | |
MD5:0C0195C48B6B8582FA6F6373032118DA | SHA256:11BD2C9F9E2397C9A16E0990E4ED2CF0679498FE0FD418A3DFDAC60B5C160EE5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
51
DNS requests
30
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1552 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.106:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4232 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4232 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://crl3.digicert.com/DigiCertGlobalRootG3.crl | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6944 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7060 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
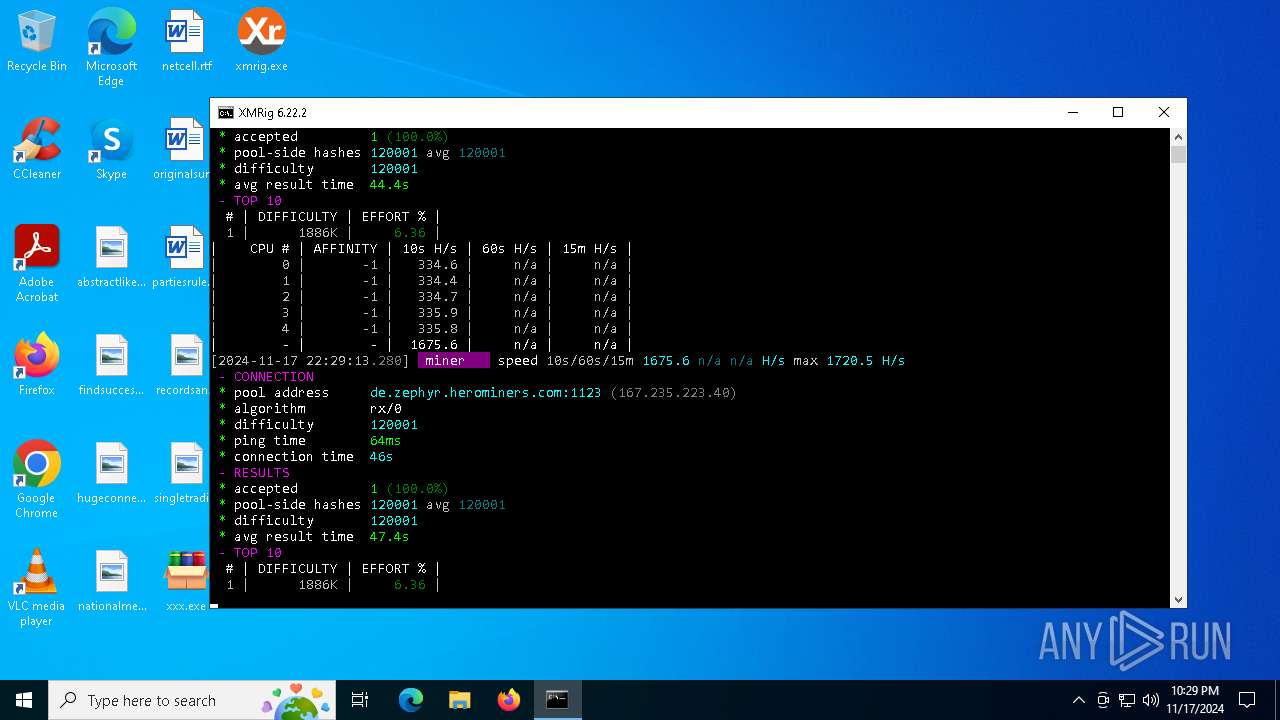
5100 | xmrig.exe | 167.235.223.40:1123 | de.zephyr.herominers.com | Hetzner Online GmbH | DE | malicious |
1552 | svchost.exe | 20.190.159.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1552 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
780 | svchost.exe | 23.35.238.131:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
4360 | SearchApp.exe | 2.23.209.182:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
de.zephyr.herominers.com |
| malicious |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5100 | xmrig.exe | Potential Corporate Privacy Violation | ET POLICY Cryptocurrency Miner Checkin |
2172 | svchost.exe | Crypto Currency Mining Activity Detected | ET COINMINER Observed DNS Query to herominers Domain (herominers .com) |
5100 | xmrig.exe | Potential Corporate Privacy Violation | ET POLICY Cryptocurrency Miner Checkin |
1 ETPRO signatures available at the full report