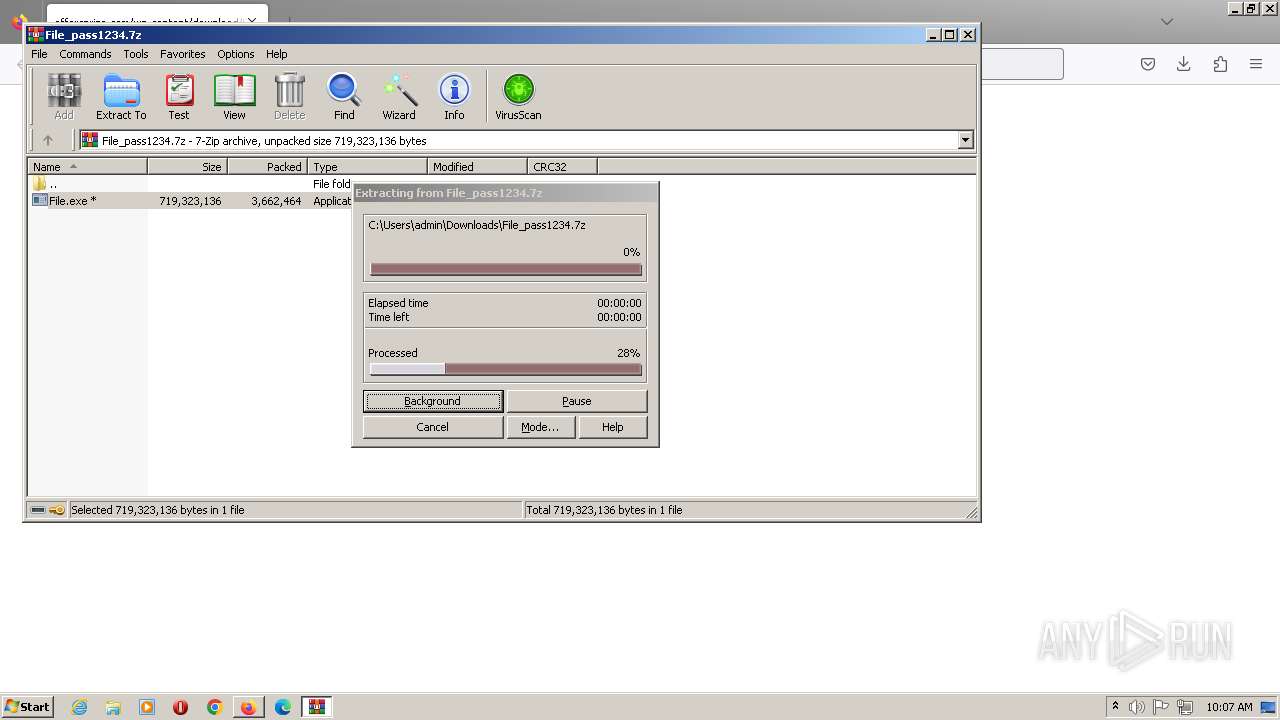
| URL: | https://offersprize.com/wp-content/download/File_pass1234.7z |
| Full analysis: | https://app.any.run/tasks/ae5be014-206d-4e0f-933a-9352984cd93e |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | August 10, 2023, 10:06:38 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 9F44DD5D5F42FCEDC09FFAB18138A718 |
| SHA1: | 6B90A6C7004953484EDCCDB49E24CA1741ADA31C |
| SHA256: | ABF4E027A634A57237511E793FF669ACE7124983651A8E984C352EAC95C2A6E6 |
| SSDEEP: | 3:N8KcXWQALGTKSVOlAQ84m8hWUXTfn:2Kc1JFVOlAUjhW+fn |
MALICIOUS
Creates a writable file the system directory
- File.exe (PID: 2996)
- vbJQbRyHXY7y15PBfpfxQXNs.exe (PID: 3024)
- svchost.exe (PID: 4344)
PRIVATELOADER was detected
- File.exe (PID: 2996)
- QxKx1RCMGGSS0wvhSOArd5qu.exe (PID: 300)
- vbJQbRyHXY7y15PBfpfxQXNs.exe (PID: 3024)
- nNT3NdRQHcgCdTjwQlYWIH_l.exe (PID: 3608)
- psx7r6teT13u3oPWbCVtM0Kj.exe (PID: 4560)
- yafDQdHbd2KXaqptG4rcuMwm.exe (PID: 5104)
Connects to the CnC server
- File.exe (PID: 2996)
- QxKx1RCMGGSS0wvhSOArd5qu.exe (PID: 300)
- vbJQbRyHXY7y15PBfpfxQXNs.exe (PID: 3024)
- LIbXOUyoxmpcgPnZA73tLs4l.exe (PID: 3424)
- mtnGUwV7mjmLG8GqZFMRfrgv.exe (PID: 2904)
- AppLaunch.exe (PID: 1036)
- 9xmFpYtHQiIKK3V4NXQ3TwDo.exe (PID: 3732)
- iF4QRDKP9Pv2wgT0B2QseQiz.exe (PID: 3628)
- nNT3NdRQHcgCdTjwQlYWIH_l.exe (PID: 3608)
- B2B3.exe (PID: 3744)
- B592.exe (PID: 4452)
- d1849563.exe (PID: 4260)
- m3191854.exe (PID: 3640)
- oWQL4nxnrt6kvXGZh760LG0q.exe (PID: 1932)
- i_OrNqmJLEHXF2gEHwkvmxMY.exe (PID: 3952)
- svchost.exe (PID: 4100)
- psx7r6teT13u3oPWbCVtM0Kj.exe (PID: 4560)
- explorer.exe (PID: 1924)
- 1n4fjeFFqQffyxTDtHuNa2qa.exe (PID: 4688)
- yafDQdHbd2KXaqptG4rcuMwm.exe (PID: 5104)
- AppLaunch.exe (PID: 2600)
- pdates.exe (PID: 4996)
Actions looks like stealing of personal data
- File.exe (PID: 2996)
- kWHLSc0DLTlkBxbtclKXUOKH.exe (PID: 2372)
- LIbXOUyoxmpcgPnZA73tLs4l.exe (PID: 3424)
- 9xmFpYtHQiIKK3V4NXQ3TwDo.exe (PID: 3732)
- 9pTDcnRlnijvRhqrAtgb4suS.exe (PID: 3612)
- mtnGUwV7mjmLG8GqZFMRfrgv.exe (PID: 2904)
- AppLaunch.exe (PID: 1036)
- iF4QRDKP9Pv2wgT0B2QseQiz.exe (PID: 3628)
- psx7r6teT13u3oPWbCVtM0Kj.exe (PID: 4560)
- d1849563.exe (PID: 4260)
- B592.exe (PID: 4452)
- B2B3.exe (PID: 3744)
- i2574582.exe (PID: 5108)
- oWQL4nxnrt6kvXGZh760LG0q.exe (PID: 1932)
- m3191854.exe (PID: 3640)
- rLKPmxBqY6jmPrusnP92b4zd.exe (PID: 3680)
- 1n4fjeFFqQffyxTDtHuNa2qa.exe (PID: 4688)
- AppLaunch.exe (PID: 2600)
- jhTxHwd.exe (PID: 2700)
- i_OrNqmJLEHXF2gEHwkvmxMY.exe (PID: 3952)
Application was dropped or rewritten from another process
- M7vlzmhEGqpq4AmnKP16fSfB.exe (PID: 1532)
- 8BmLGqruzmEI1ZzIl89XGQ7a.exe (PID: 1628)
- 9xmFpYtHQiIKK3V4NXQ3TwDo.exe (PID: 3732)
- nNT3NdRQHcgCdTjwQlYWIH_l.exe (PID: 3608)
- LIbXOUyoxmpcgPnZA73tLs4l.exe (PID: 3424)
- mtnGUwV7mjmLG8GqZFMRfrgv.exe (PID: 2904)
- 92xaQvsYNwLgS999n6qoVehG.exe (PID: 1684)
- 0iEBtxu4mMhW_nHKmi2C3vWI.exe (PID: 3268)
- kwebhuay.exe (PID: 4736)
- v4378546.exe (PID: 3660)
- v7460048.exe (PID: 1892)
- v5630650.exe (PID: 3276)
- a8875360.exe (PID: 2128)
- b3282490.exe (PID: 4624)
- pdates.exe (PID: 4996)
- c7955277.exe (PID: 1016)
- d1849563.exe (PID: 4260)
- psx7r6teT13u3oPWbCVtM0Kj.exe (PID: 4560)
- B2B3.exe (PID: 3744)
- B592.exe (PID: 4452)
- pdates.exe (PID: 4660)
- g9213648.exe (PID: 3856)
- h0922718.exe (PID: 4508)
- i2574582.exe (PID: 5108)
- 1E70.exe (PID: 2580)
- k4230746.exe (PID: 1036)
- l3104645.exe (PID: 2996)
- m3191854.exe (PID: 3640)
- 2DC3.exe (PID: 4736)
- oWQL4nxnrt6kvXGZh760LG0q.exe (PID: 1932)
- oSAufQ3uGwRiPZg0z9a_ERhT.exe (PID: 3396)
- rLKPmxBqY6jmPrusnP92b4zd.exe (PID: 3680)
- jbhtujv (PID: 2764)
- pdates.exe (PID: 2792)
- e1704692.exe (PID: 3508)
- Dw3yfZE0O07luP0PxZ7y1QFA.exe (PID: 2148)
- Install.exe (PID: 4480)
- pdates.exe (PID: 3432)
- jhTxHwd.exe (PID: 2700)
- j2185000.exe (PID: 4960)
- n2126362.exe (PID: 572)
Loads dropped or rewritten executable
- rundll32.exe (PID: 3228)
- regsvr32.exe (PID: 1016)
- regsvr32.exe (PID: 3036)
- msiexec.exe (PID: 5096)
- rundll32.exe (PID: 3612)
- rundll32.exe (PID: 2928)
Disables Windows Defender
- a8875360.exe (PID: 2128)
Runs injected code in another process
- 8BmLGqruzmEI1ZzIl89XGQ7a.exe (PID: 1628)
- c7955277.exe (PID: 1016)
Application was injected by another process
- explorer.exe (PID: 1924)
RISEPRO was detected
- kWHLSc0DLTlkBxbtclKXUOKH.exe (PID: 2372)
Uses Task Scheduler to run other applications
- pdates.exe (PID: 4996)
- nNT3NdRQHcgCdTjwQlYWIH_l.exe (PID: 3608)
- Install.exe (PID: 4480)
- jhTxHwd.exe (PID: 2700)
- jmIwrGG.exe (PID: 4340)
Changes the autorun value in the registry
- pdates.exe (PID: 4996)
PRIVATELOADER detected by memory dumps
- nNT3NdRQHcgCdTjwQlYWIH_l.exe (PID: 3608)
Steals credentials from Web Browsers
- mtnGUwV7mjmLG8GqZFMRfrgv.exe (PID: 2904)
- AppLaunch.exe (PID: 1036)
- iF4QRDKP9Pv2wgT0B2QseQiz.exe (PID: 3628)
- d1849563.exe (PID: 4260)
- B2B3.exe (PID: 3744)
- rLKPmxBqY6jmPrusnP92b4zd.exe (PID: 3680)
- m3191854.exe (PID: 3640)
- i_OrNqmJLEHXF2gEHwkvmxMY.exe (PID: 3952)
- AppLaunch.exe (PID: 2600)
- B592.exe (PID: 4452)
- i2574582.exe (PID: 5108)
- 1n4fjeFFqQffyxTDtHuNa2qa.exe (PID: 4688)
REDLINE detected by memory dumps
- mtnGUwV7mjmLG8GqZFMRfrgv.exe (PID: 2904)
- AppLaunch.exe (PID: 1036)
- 5s2B4CcnRx5RsDUH9jmUwa6j.exe (PID: 4024)
- d1849563.exe (PID: 4260)
- B592.exe (PID: 4452)
- B2B3.exe (PID: 3744)
- i2574582.exe (PID: 5108)
- m3191854.exe (PID: 3640)
- juAA1zPJmwVqW1twDb1U4o4D.exe (PID: 4724)
- i_OrNqmJLEHXF2gEHwkvmxMY.exe (PID: 3952)
- 1n4fjeFFqQffyxTDtHuNa2qa.exe (PID: 4688)
- AppLaunch.exe (PID: 2600)
Uses Task Scheduler to autorun other applications
- nNT3NdRQHcgCdTjwQlYWIH_l.exe (PID: 3608)
- jmIwrGG.exe (PID: 4340)
REDLINE was detected
- LIbXOUyoxmpcgPnZA73tLs4l.exe (PID: 3424)
- mtnGUwV7mjmLG8GqZFMRfrgv.exe (PID: 2904)
- AppLaunch.exe (PID: 1036)
- iF4QRDKP9Pv2wgT0B2QseQiz.exe (PID: 3628)
- B592.exe (PID: 4452)
- B2B3.exe (PID: 3744)
- m3191854.exe (PID: 3640)
- d1849563.exe (PID: 4260)
- 1n4fjeFFqQffyxTDtHuNa2qa.exe (PID: 4688)
- i_OrNqmJLEHXF2gEHwkvmxMY.exe (PID: 3952)
- AppLaunch.exe (PID: 2600)
Registers / Runs the DLL via REGSVR32.EXE
- explorer.exe (PID: 1924)
FABOOKIE was detected
- 9xmFpYtHQiIKK3V4NXQ3TwDo.exe (PID: 3732)
- oWQL4nxnrt6kvXGZh760LG0q.exe (PID: 1932)
AMADEY detected by memory dumps
- pdates.exe (PID: 4996)
- pdates.exe (PID: 4660)
- pdates.exe (PID: 2792)
TOFSEE detected by memory dumps
- svchost.exe (PID: 4344)
LUMMA was detected
- 9pTDcnRlnijvRhqrAtgb4suS.exe (PID: 3612)
LUMMA detected by memory dumps
- Install.exe (PID: 1064)
Run PowerShell with an invisible window
- powershell.EXE (PID: 2460)
- powershell.EXE (PID: 3888)
MINER was detected
- svchost.exe (PID: 4100)
TOFSEE was detected
- svchost.exe (PID: 4344)
SMOKE was detected
- explorer.exe (PID: 1924)
Modifies exclusions in Windows Defender
- reg.exe (PID: 4176)
AMADEY was detected
- pdates.exe (PID: 4996)
SUSPICIOUS
Reads settings of System Certificates
- File.exe (PID: 2996)
- kWHLSc0DLTlkBxbtclKXUOKH.exe (PID: 2372)
- QxKx1RCMGGSS0wvhSOArd5qu.exe (PID: 300)
- nNT3NdRQHcgCdTjwQlYWIH_l.exe (PID: 3608)
- vbJQbRyHXY7y15PBfpfxQXNs.exe (PID: 3024)
- psx7r6teT13u3oPWbCVtM0Kj.exe (PID: 4560)
- yafDQdHbd2KXaqptG4rcuMwm.exe (PID: 5104)
- regsvr32.exe (PID: 1016)
Checks Windows Trust Settings
- File.exe (PID: 2996)
- psx7r6teT13u3oPWbCVtM0Kj.exe (PID: 4560)
Checks for external IP
- File.exe (PID: 2996)
- kWHLSc0DLTlkBxbtclKXUOKH.exe (PID: 2372)
- QxKx1RCMGGSS0wvhSOArd5qu.exe (PID: 300)
- vbJQbRyHXY7y15PBfpfxQXNs.exe (PID: 3024)
- nNT3NdRQHcgCdTjwQlYWIH_l.exe (PID: 3608)
- psx7r6teT13u3oPWbCVtM0Kj.exe (PID: 4560)
Reads security settings of Internet Explorer
- File.exe (PID: 2996)
- psx7r6teT13u3oPWbCVtM0Kj.exe (PID: 4560)
Connects to the server without a host name
- File.exe (PID: 2996)
- vbJQbRyHXY7y15PBfpfxQXNs.exe (PID: 3024)
- QxKx1RCMGGSS0wvhSOArd5qu.exe (PID: 300)
- nNT3NdRQHcgCdTjwQlYWIH_l.exe (PID: 3608)
- pdates.exe (PID: 4996)
- psx7r6teT13u3oPWbCVtM0Kj.exe (PID: 4560)
- explorer.exe (PID: 1924)
- yafDQdHbd2KXaqptG4rcuMwm.exe (PID: 5104)
- svchost.exe (PID: 4344)
- j2185000.exe (PID: 4960)
Reads the Internet Settings
- File.exe (PID: 2996)
- 9xmFpYtHQiIKK3V4NXQ3TwDo.exe (PID: 3732)
- M7vlzmhEGqpq4AmnKP16fSfB.exe (PID: 1532)
- control.exe (PID: 2272)
- 0iEBtxu4mMhW_nHKmi2C3vWI.exe (PID: 3268)
- 9pTDcnRlnijvRhqrAtgb4suS.exe (PID: 3612)
- nNT3NdRQHcgCdTjwQlYWIH_l.exe (PID: 3608)
- b3282490.exe (PID: 4624)
- pdates.exe (PID: 4996)
- psx7r6teT13u3oPWbCVtM0Kj.exe (PID: 4560)
- Dw3yfZE0O07luP0PxZ7y1QFA.exe (PID: 2148)
- oWQL4nxnrt6kvXGZh760LG0q.exe (PID: 1932)
- Install.exe (PID: 4480)
- e1704692.exe (PID: 3508)
- regsvr32.exe (PID: 1016)
- powershell.EXE (PID: 2460)
- j2185000.exe (PID: 4960)
Executable content was dropped or overwritten
- File.exe (PID: 2996)
- M7vlzmhEGqpq4AmnKP16fSfB.exe (PID: 1532)
- 92xaQvsYNwLgS999n6qoVehG.exe (PID: 1684)
- v4378546.exe (PID: 3660)
- v7460048.exe (PID: 1892)
- v5630650.exe (PID: 3276)
- 0iEBtxu4mMhW_nHKmi2C3vWI.exe (PID: 3268)
- cmd.exe (PID: 3704)
- nNT3NdRQHcgCdTjwQlYWIH_l.exe (PID: 3608)
- psx7r6teT13u3oPWbCVtM0Kj.exe (PID: 4560)
- explorer.exe (PID: 1924)
- pdates.exe (PID: 4996)
- Install.exe (PID: 4480)
- jhTxHwd.exe (PID: 2700)
- jmIwrGG.exe (PID: 4340)
Process requests binary or script from the Internet
- File.exe (PID: 2996)
- nNT3NdRQHcgCdTjwQlYWIH_l.exe (PID: 3608)
- explorer.exe (PID: 1924)
- psx7r6teT13u3oPWbCVtM0Kj.exe (PID: 4560)
- pdates.exe (PID: 4996)
Executes as Windows Service
- raserver.exe (PID: 2024)
- kwebhuay.exe (PID: 4736)
- raserver.exe (PID: 4708)
- raserver.exe (PID: 3952)
- raserver.exe (PID: 3648)
- raserver.exe (PID: 468)
Connects to unusual port
- File.exe (PID: 2996)
- kWHLSc0DLTlkBxbtclKXUOKH.exe (PID: 2372)
- LIbXOUyoxmpcgPnZA73tLs4l.exe (PID: 3424)
- AppLaunch.exe (PID: 1036)
- iF4QRDKP9Pv2wgT0B2QseQiz.exe (PID: 3628)
- mtnGUwV7mjmLG8GqZFMRfrgv.exe (PID: 2904)
- svchost.exe (PID: 4344)
- d1849563.exe (PID: 4260)
- B2B3.exe (PID: 3744)
- B592.exe (PID: 4452)
- svchost.exe (PID: 4100)
- 1n4fjeFFqQffyxTDtHuNa2qa.exe (PID: 4688)
- explorer.exe (PID: 1924)
- i2574582.exe (PID: 5108)
- i_OrNqmJLEHXF2gEHwkvmxMY.exe (PID: 3952)
- m3191854.exe (PID: 3640)
- AppLaunch.exe (PID: 2600)
Starts CMD.EXE for commands execution
- 0iEBtxu4mMhW_nHKmi2C3vWI.exe (PID: 3268)
- pdates.exe (PID: 4996)
- cmd.exe (PID: 2712)
- rLKPmxBqY6jmPrusnP92b4zd.exe (PID: 3680)
- forfiles.exe (PID: 2308)
- forfiles.exe (PID: 1356)
- jhTxHwd.exe (PID: 2700)
- jmIwrGG.exe (PID: 4340)
Searches for installed software
- kWHLSc0DLTlkBxbtclKXUOKH.exe (PID: 2372)
- LIbXOUyoxmpcgPnZA73tLs4l.exe (PID: 3424)
- mtnGUwV7mjmLG8GqZFMRfrgv.exe (PID: 2904)
- AppLaunch.exe (PID: 1036)
- iF4QRDKP9Pv2wgT0B2QseQiz.exe (PID: 3628)
- 9pTDcnRlnijvRhqrAtgb4suS.exe (PID: 3612)
- m3191854.exe (PID: 3640)
- B592.exe (PID: 4452)
- d1849563.exe (PID: 4260)
- i_OrNqmJLEHXF2gEHwkvmxMY.exe (PID: 3952)
- B2B3.exe (PID: 3744)
- AppLaunch.exe (PID: 2600)
- i2574582.exe (PID: 5108)
- 1n4fjeFFqQffyxTDtHuNa2qa.exe (PID: 4688)
Uses NETSH.EXE to add a firewall rule or allowed programs
- 0iEBtxu4mMhW_nHKmi2C3vWI.exe (PID: 3268)
Detected use of alternative data streams (AltDS)
- svchost.exe (PID: 4344)
Creates or modifies Windows services
- svchost.exe (PID: 4344)
Reads browser cookies
- LIbXOUyoxmpcgPnZA73tLs4l.exe (PID: 3424)
- iF4QRDKP9Pv2wgT0B2QseQiz.exe (PID: 3628)
- mtnGUwV7mjmLG8GqZFMRfrgv.exe (PID: 2904)
- AppLaunch.exe (PID: 1036)
- B592.exe (PID: 4452)
- d1849563.exe (PID: 4260)
- B2B3.exe (PID: 3744)
- 1n4fjeFFqQffyxTDtHuNa2qa.exe (PID: 4688)
- i2574582.exe (PID: 5108)
- m3191854.exe (PID: 3640)
- i_OrNqmJLEHXF2gEHwkvmxMY.exe (PID: 3952)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- nNT3NdRQHcgCdTjwQlYWIH_l.exe (PID: 3608)
Starts itself from another location
- b3282490.exe (PID: 4624)
- Brq7VJfYI79wn8JHfk4qK2iX.exe (PID: 3236)
Application launched itself
- cmd.exe (PID: 2712)
- svchost.exe (PID: 4344)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 2712)
Connects to SMTP port
- svchost.exe (PID: 4344)
Adds/modifies Windows certificates
- nNT3NdRQHcgCdTjwQlYWIH_l.exe (PID: 3608)
The process executes via Task Scheduler
- pdates.exe (PID: 4660)
- powershell.EXE (PID: 2460)
- jbhtujv (PID: 2764)
- pdates.exe (PID: 2792)
- pdates.exe (PID: 3432)
- jhTxHwd.exe (PID: 2700)
- powershell.EXE (PID: 3888)
- rundll32.exe (PID: 1760)
- jmIwrGG.exe (PID: 4340)
- pdates.exe (PID: 4260)
Found strings related to reading or modifying Windows Defender settings
- forfiles.exe (PID: 2308)
- forfiles.exe (PID: 1356)
- jhTxHwd.exe (PID: 2700)
- jmIwrGG.exe (PID: 4340)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 3512)
- cmd.exe (PID: 5076)
- cmd.exe (PID: 3928)
- cmd.exe (PID: 4532)
- cmd.exe (PID: 3568)
- cmd.exe (PID: 4628)
- wscript.exe (PID: 244)
- cmd.exe (PID: 2804)
- cmd.exe (PID: 2000)
Reads the BIOS version
- Install.exe (PID: 4480)
Uses RUNDLL32.EXE to load library
- rundll32.exe (PID: 3228)
INFO
Application launched itself
- firefox.exe (PID: 2124)
Reads the computer name
- File.exe (PID: 2996)
- M7vlzmhEGqpq4AmnKP16fSfB.exe (PID: 1532)
- 9xmFpYtHQiIKK3V4NXQ3TwDo.exe (PID: 3732)
- kWHLSc0DLTlkBxbtclKXUOKH.exe (PID: 2372)
- nNT3NdRQHcgCdTjwQlYWIH_l.exe (PID: 3608)
- AppLaunch.exe (PID: 1036)
- iF4QRDKP9Pv2wgT0B2QseQiz.exe (PID: 3628)
- vbJQbRyHXY7y15PBfpfxQXNs.exe (PID: 3024)
- QxKx1RCMGGSS0wvhSOArd5qu.exe (PID: 300)
- LIbXOUyoxmpcgPnZA73tLs4l.exe (PID: 3424)
- a8875360.exe (PID: 2128)
- 0iEBtxu4mMhW_nHKmi2C3vWI.exe (PID: 3268)
- mtnGUwV7mjmLG8GqZFMRfrgv.exe (PID: 2904)
- kwebhuay.exe (PID: 4736)
- 9pTDcnRlnijvRhqrAtgb4suS.exe (PID: 3612)
- b3282490.exe (PID: 4624)
- pdates.exe (PID: 4996)
- d1849563.exe (PID: 4260)
- psx7r6teT13u3oPWbCVtM0Kj.exe (PID: 4560)
- B592.exe (PID: 4452)
- B2B3.exe (PID: 3744)
- h0922718.exe (PID: 4508)
- i2574582.exe (PID: 5108)
- k4230746.exe (PID: 1036)
- m3191854.exe (PID: 3640)
- Dw3yfZE0O07luP0PxZ7y1QFA.exe (PID: 2148)
- 1n4fjeFFqQffyxTDtHuNa2qa.exe (PID: 4688)
- oWQL4nxnrt6kvXGZh760LG0q.exe (PID: 1932)
- rLKPmxBqY6jmPrusnP92b4zd.exe (PID: 3680)
- AppLaunch.exe (PID: 2600)
- i_OrNqmJLEHXF2gEHwkvmxMY.exe (PID: 3952)
- yafDQdHbd2KXaqptG4rcuMwm.exe (PID: 5104)
- oSAufQ3uGwRiPZg0z9a_ERhT.exe (PID: 3396)
- Install.exe (PID: 4480)
- e1704692.exe (PID: 3508)
- j2185000.exe (PID: 4960)
The process uses the downloaded file
- firefox.exe (PID: 2124)
- WinRAR.exe (PID: 1336)
Checks supported languages
- File.exe (PID: 2996)
- M7vlzmhEGqpq4AmnKP16fSfB.exe (PID: 1532)
- 9xmFpYtHQiIKK3V4NXQ3TwDo.exe (PID: 3732)
- LIbXOUyoxmpcgPnZA73tLs4l.exe (PID: 3424)
- nNT3NdRQHcgCdTjwQlYWIH_l.exe (PID: 3608)
- 8BmLGqruzmEI1ZzIl89XGQ7a.exe (PID: 1628)
- mtnGUwV7mjmLG8GqZFMRfrgv.exe (PID: 2904)
- 0iEBtxu4mMhW_nHKmi2C3vWI.exe (PID: 3268)
- 92xaQvsYNwLgS999n6qoVehG.exe (PID: 1684)
- kWHLSc0DLTlkBxbtclKXUOKH.exe (PID: 2372)
- 9pTDcnRlnijvRhqrAtgb4suS.exe (PID: 3612)
- QxKx1RCMGGSS0wvhSOArd5qu.exe (PID: 300)
- vbJQbRyHXY7y15PBfpfxQXNs.exe (PID: 3024)
- v4378546.exe (PID: 3660)
- 5s2B4CcnRx5RsDUH9jmUwa6j.exe (PID: 4024)
- iF4QRDKP9Pv2wgT0B2QseQiz.exe (PID: 3628)
- v7460048.exe (PID: 1892)
- AppLaunch.exe (PID: 1036)
- v5630650.exe (PID: 3276)
- a8875360.exe (PID: 2128)
- kwebhuay.exe (PID: 4736)
- b3282490.exe (PID: 4624)
- pdates.exe (PID: 4996)
- c7955277.exe (PID: 1016)
- psx7r6teT13u3oPWbCVtM0Kj.exe (PID: 4560)
- d1849563.exe (PID: 4260)
- B592.exe (PID: 4452)
- B2B3.exe (PID: 3744)
- 1E70.exe (PID: 2580)
- x8654103.exe (PID: 3284)
- x8328387.exe (PID: 3236)
- h0922718.exe (PID: 4508)
- g9213648.exe (PID: 3856)
- i2574582.exe (PID: 5108)
- 2DC3.exe (PID: 4736)
- y2548895.exe (PID: 2468)
- y4871434.exe (PID: 4252)
- k4230746.exe (PID: 1036)
- l3104645.exe (PID: 2996)
- m3191854.exe (PID: 3640)
- pdates.exe (PID: 4660)
- Dw3yfZE0O07luP0PxZ7y1QFA.exe (PID: 2148)
- rLKPmxBqY6jmPrusnP92b4zd.exe (PID: 3680)
- oSAufQ3uGwRiPZg0z9a_ERhT.exe (PID: 3396)
- oWQL4nxnrt6kvXGZh760LG0q.exe (PID: 1932)
- 1n4fjeFFqQffyxTDtHuNa2qa.exe (PID: 4688)
- juAA1zPJmwVqW1twDb1U4o4D.exe (PID: 4724)
- yafDQdHbd2KXaqptG4rcuMwm.exe (PID: 5104)
- Brq7VJfYI79wn8JHfk4qK2iX.exe (PID: 3236)
- i_OrNqmJLEHXF2gEHwkvmxMY.exe (PID: 3952)
- AppLaunch.exe (PID: 2600)
- Install.exe (PID: 1064)
- Install.exe (PID: 4480)
- e1704692.exe (PID: 3508)
- pdates.exe (PID: 2792)
- jbhtujv (PID: 2764)
- jhTxHwd.exe (PID: 2700)
- pdates.exe (PID: 3432)
- j2185000.exe (PID: 4960)
- n2126362.exe (PID: 572)
The process checks LSA protection
- File.exe (PID: 2996)
- M7vlzmhEGqpq4AmnKP16fSfB.exe (PID: 1532)
- kWHLSc0DLTlkBxbtclKXUOKH.exe (PID: 2372)
- control.exe (PID: 2272)
- nNT3NdRQHcgCdTjwQlYWIH_l.exe (PID: 3608)
- 9xmFpYtHQiIKK3V4NXQ3TwDo.exe (PID: 3732)
- LIbXOUyoxmpcgPnZA73tLs4l.exe (PID: 3424)
- vbJQbRyHXY7y15PBfpfxQXNs.exe (PID: 3024)
- AppLaunch.exe (PID: 1036)
- 0iEBtxu4mMhW_nHKmi2C3vWI.exe (PID: 3268)
- QxKx1RCMGGSS0wvhSOArd5qu.exe (PID: 300)
- iF4QRDKP9Pv2wgT0B2QseQiz.exe (PID: 3628)
- mtnGUwV7mjmLG8GqZFMRfrgv.exe (PID: 2904)
- netsh.exe (PID: 4892)
- 9pTDcnRlnijvRhqrAtgb4suS.exe (PID: 3612)
- b3282490.exe (PID: 4624)
- pdates.exe (PID: 4996)
- d1849563.exe (PID: 4260)
- psx7r6teT13u3oPWbCVtM0Kj.exe (PID: 4560)
- explorer.exe (PID: 1924)
- B592.exe (PID: 4452)
- B2B3.exe (PID: 3744)
- svchost.exe (PID: 4344)
- i2574582.exe (PID: 5108)
- m3191854.exe (PID: 3640)
- Dw3yfZE0O07luP0PxZ7y1QFA.exe (PID: 2148)
- 1n4fjeFFqQffyxTDtHuNa2qa.exe (PID: 4688)
- oWQL4nxnrt6kvXGZh760LG0q.exe (PID: 1932)
- AppLaunch.exe (PID: 2600)
- oSAufQ3uGwRiPZg0z9a_ERhT.exe (PID: 3396)
- yafDQdHbd2KXaqptG4rcuMwm.exe (PID: 5104)
- i_OrNqmJLEHXF2gEHwkvmxMY.exe (PID: 3952)
- Install.exe (PID: 4480)
- e1704692.exe (PID: 3508)
- regsvr32.exe (PID: 1016)
- j2185000.exe (PID: 4960)
Manual execution by a user
- WinRAR.exe (PID: 1336)
- B2B3.exe (PID: 3744)
- regsvr32.exe (PID: 4940)
- B592.exe (PID: 4452)
- regsvr32.exe (PID: 4340)
Checks proxy server information
- File.exe (PID: 2996)
- 9xmFpYtHQiIKK3V4NXQ3TwDo.exe (PID: 3732)
- 9pTDcnRlnijvRhqrAtgb4suS.exe (PID: 3612)
- nNT3NdRQHcgCdTjwQlYWIH_l.exe (PID: 3608)
- pdates.exe (PID: 4996)
- psx7r6teT13u3oPWbCVtM0Kj.exe (PID: 4560)
- oWQL4nxnrt6kvXGZh760LG0q.exe (PID: 1932)
- e1704692.exe (PID: 3508)
- regsvr32.exe (PID: 1016)
- j2185000.exe (PID: 4960)
Reads the machine GUID from the registry
- File.exe (PID: 2996)
- 9xmFpYtHQiIKK3V4NXQ3TwDo.exe (PID: 3732)
- LIbXOUyoxmpcgPnZA73tLs4l.exe (PID: 3424)
- iF4QRDKP9Pv2wgT0B2QseQiz.exe (PID: 3628)
- AppLaunch.exe (PID: 1036)
- kWHLSc0DLTlkBxbtclKXUOKH.exe (PID: 2372)
- nNT3NdRQHcgCdTjwQlYWIH_l.exe (PID: 3608)
- mtnGUwV7mjmLG8GqZFMRfrgv.exe (PID: 2904)
- QxKx1RCMGGSS0wvhSOArd5qu.exe (PID: 300)
- 9pTDcnRlnijvRhqrAtgb4suS.exe (PID: 3612)
- vbJQbRyHXY7y15PBfpfxQXNs.exe (PID: 3024)
- b3282490.exe (PID: 4624)
- pdates.exe (PID: 4996)
- d1849563.exe (PID: 4260)
- psx7r6teT13u3oPWbCVtM0Kj.exe (PID: 4560)
- B592.exe (PID: 4452)
- B2B3.exe (PID: 3744)
- i2574582.exe (PID: 5108)
- m3191854.exe (PID: 3640)
- oWQL4nxnrt6kvXGZh760LG0q.exe (PID: 1932)
- 1n4fjeFFqQffyxTDtHuNa2qa.exe (PID: 4688)
- AppLaunch.exe (PID: 2600)
- i_OrNqmJLEHXF2gEHwkvmxMY.exe (PID: 3952)
- oSAufQ3uGwRiPZg0z9a_ERhT.exe (PID: 3396)
- yafDQdHbd2KXaqptG4rcuMwm.exe (PID: 5104)
- Install.exe (PID: 4480)
- e1704692.exe (PID: 3508)
- j2185000.exe (PID: 4960)
Process checks computer location settings
- File.exe (PID: 2996)
- psx7r6teT13u3oPWbCVtM0Kj.exe (PID: 4560)
Create files in a temporary directory
- File.exe (PID: 2996)
- 92xaQvsYNwLgS999n6qoVehG.exe (PID: 1684)
- M7vlzmhEGqpq4AmnKP16fSfB.exe (PID: 1532)
- v7460048.exe (PID: 1892)
- v5630650.exe (PID: 3276)
- v4378546.exe (PID: 3660)
- 0iEBtxu4mMhW_nHKmi2C3vWI.exe (PID: 3268)
- kWHLSc0DLTlkBxbtclKXUOKH.exe (PID: 2372)
- b3282490.exe (PID: 4624)
- explorer.exe (PID: 1924)
- 1E70.exe (PID: 2580)
- x8654103.exe (PID: 3284)
- x8328387.exe (PID: 3236)
- 2DC3.exe (PID: 4736)
- y2548895.exe (PID: 2468)
- y4871434.exe (PID: 4252)
- Dw3yfZE0O07luP0PxZ7y1QFA.exe (PID: 2148)
- Brq7VJfYI79wn8JHfk4qK2iX.exe (PID: 3236)
- Install.exe (PID: 1064)
- e1704692.exe (PID: 3508)
- Install.exe (PID: 4480)
- n2126362.exe (PID: 572)
- j2185000.exe (PID: 4960)
Creates files or folders in the user directory
- File.exe (PID: 2996)
- 9xmFpYtHQiIKK3V4NXQ3TwDo.exe (PID: 3732)
- 9pTDcnRlnijvRhqrAtgb4suS.exe (PID: 3612)
- nNT3NdRQHcgCdTjwQlYWIH_l.exe (PID: 3608)
- explorer.exe (PID: 1924)
- psx7r6teT13u3oPWbCVtM0Kj.exe (PID: 4560)
- pdates.exe (PID: 4996)
- oWQL4nxnrt6kvXGZh760LG0q.exe (PID: 1932)
- rLKPmxBqY6jmPrusnP92b4zd.exe (PID: 3680)
Reads Environment values
- kWHLSc0DLTlkBxbtclKXUOKH.exe (PID: 2372)
- LIbXOUyoxmpcgPnZA73tLs4l.exe (PID: 3424)
- AppLaunch.exe (PID: 1036)
- iF4QRDKP9Pv2wgT0B2QseQiz.exe (PID: 3628)
- d1849563.exe (PID: 4260)
- B592.exe (PID: 4452)
- mtnGUwV7mjmLG8GqZFMRfrgv.exe (PID: 2904)
- i2574582.exe (PID: 5108)
- m3191854.exe (PID: 3640)
- 1n4fjeFFqQffyxTDtHuNa2qa.exe (PID: 4688)
- i_OrNqmJLEHXF2gEHwkvmxMY.exe (PID: 3952)
- B2B3.exe (PID: 3744)
- AppLaunch.exe (PID: 2600)
Reads CPU info
- kWHLSc0DLTlkBxbtclKXUOKH.exe (PID: 2372)
Reads product name
- kWHLSc0DLTlkBxbtclKXUOKH.exe (PID: 2372)
Creates files in the program directory
- nNT3NdRQHcgCdTjwQlYWIH_l.exe (PID: 3608)
Reads the Internet Settings
- explorer.exe (PID: 1924)
[YARA] Firewall manipulation strings were found
- oSAufQ3uGwRiPZg0z9a_ERhT.exe (PID: 3396)
Reads security settings of Internet Explorer
- regsvr32.exe (PID: 1016)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
330
Monitored processes
197
Malicious processes
58
Suspicious processes
11
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 244 | wscript "C:\Windows\Temp\csJlaFVcvykHEvap\mMdTlTpp\lsFooIcdQfyOHNEH.wsf" | C:\Windows\SysWOW64\wscript.exe | — | jhTxHwd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 296 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="2124.6.40044424\1517738066" -childID 5 -isForBrowser -prefsHandle 4036 -prefMapHandle 3896 -prefsLen 30211 -prefMapSize 244147 -jsInitHandle 872 -jsInitLen 240908 -parentBuildID 20230710165010 -appDir "C:\Program Files\Mozilla Firefox\browser" - {3fb6871b-a151-408a-b4c7-dfd291faa8f8} 2124 "\\.\pipe\gecko-crash-server-pipe.2124" 4024 16615258 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 9 Version: 115.0.2 Modules
| |||||||||||||||
| 300 | "C:\Users\admin\Pictures\Minor Policy\QxKx1RCMGGSS0wvhSOArd5qu.exe" | C:\Users\admin\Pictures\Minor Policy\QxKx1RCMGGSS0wvhSOArd5qu.exe | File.exe | ||||||||||||
User: admin Company: Advanced Micro Devices, Inc Integrity Level: HIGH Description: AMD GPIO Controller Driver Exit code: 0 Version: 2.2.0.130 Modules
| |||||||||||||||
| 468 | C:\Windows\system32\RAServer.exe /offerraupdate | C:\Windows\System32\raserver.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Remote Assistance COM Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | |||||||||||||||
| 572 | C:\Users\admin\AppData\Local\Temp\IXP004.TMP\n2126362.exe | C:\Users\admin\AppData\Local\Temp\IXP004.TMP\n2126362.exe | — | 2DC3.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 616 | "C:\Windows\System32\reg.exe" ADD "HKLM\SOFTWARE\Microsoft\Windows Defender\Exclusions\Paths" /f /v "C:\Program Files (x86)\NNrZlXoEFWUn" /t REG_DWORD /d 0 /reg:32 | C:\Windows\SysWOW64\reg.exe | — | wscript.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 676 | "C:\Windows\System32\reg.exe" ADD "HKLM\SOFTWARE\Microsoft\Windows Defender\Exclusions\Paths" /f /v "C:\ProgramData\IbVVXpeaMEjnuMVB" /t REG_DWORD /d 0 /reg:32 | C:\Windows\SysWOW64\reg.exe | — | wscript.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 832 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="2124.1.1447123548\647781056" -parentBuildID 20230710165010 -prefsHandle 1408 -prefMapHandle 1404 -prefsLen 29601 -prefMapSize 244147 -appDir "C:\Program Files\Mozilla Firefox\browser" - {f664b9fb-3245-47d2-b510-a6468167e05e} 2124 "\\.\pipe\gecko-crash-server-pipe.2124" 1420 fbd3f58 socket | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 9 Version: 115.0.2 Modules
| |||||||||||||||
| 1016 | C:\Users\admin\AppData\Local\Temp\IXP002.TMP\c7955277.exe | C:\Users\admin\AppData\Local\Temp\IXP002.TMP\c7955277.exe | — | v7460048.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1016 | /s C:\Users\admin\AppData\Local\Temp\AF56.dll | C:\Windows\SysWOW64\regsvr32.exe | regsvr32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
38 857
Read events
37 512
Write events
1 251
Delete events
94
Modification events
| (PID) Process: | (1924) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Action Center\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB01000000088AF72B0747534094337F63DE35C94A00000000020000000000106600000001000020000000DE596CC00FA0CE6036B57F3745DF211B8CEDC7563B5C7C90E189DFBFE4E216FC000000000E800000000200002000000034A09CAFA8980668BD48169E708CCFDA06F4ADAD9A6D0FF324841FD89016AF6F3000000097B2B3329B62DD4C9AB1E283BD9359B999E8411B9FC15AF795BFA67D05007F5CE28F7E84193A17AFEBE2A486810ADC32400000007E5B4D515AE7EE2B367ED77D5D9A272891BC7B3019A3AA7BC4BF2CA5315073E7F321A33013E44AD95CE9A5E9CA3FF01D3584C54FECFB9C1227BA4AE46F87EAF7 | |||
| (PID) Process: | (2124) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Browser |
Value: 0000000000000000 | |||
| (PID) Process: | (1924) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | 308046O0NS4N39PO |
Value: 000000000900000011000000C5C20000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFFD0D677189BC5D90100000000 | |||
| (PID) Process: | (1924) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 00000000B6000000F2000000E2A064001500000007000000251C06007B00310041004300310034004500370037002D0030003200450037002D0034004500350044002D0042003700340034002D003200450042003100410045003500310039003800420037007D005C0063006D0064002E006500780065000000EA02000000000540008000000000542DADFFFE070000000000000000000068006B02000000005C00010000000000000000000000000000003D0000000000EB1A92770000000068006B020000000000000000FE0700002825B6FFFE070000A08886020000000018006B020000000000000000000000000100000000000000BF1DADFFFE07000060E1EA020000000060B888020000000000000000000000003B9462FDFE070000B00C88020000000008006B02000000005C00010000000000869A807700000000BE313C4A62B00000820200000000000000000000000000005C000100000000000000000000000000820200000000000002000000000000005C000100000000000000000000000000820200000000000080A6E0FF00000000C812D2FF00000000B00C88020000000001000000000000000F0000C000000000B000060000000000820200000000000001000000000000008202000000000000DB9B8077000000005C00010000000000000000000000000000000000000000000100000000000000000000000000000081020000000000000000000000000000000000000000000000000000060000002400000067510B004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E0043006F006E00740072006F006C00500061006E0065006C00000000000000000000000000000000008202000000000000010000000000000001000000000000008202000000000000D46905FCFE07000010E2EA020000000016798077000000000000000000000000869A807700000000000000000000000030E14A0000000000010000000000000010E2EA02000000000000000000000000CF41394A62B00000FFFFFFFFFFFFFFFF010000000000000000FF490000000000A0000500000000000000000000000000586705FCFE0700000000000000000000A0000500000000002B10000000000000807580770000000000000000000000000000000000000000000000000000000001000000000000001500000007000000790E06007B00310041004300310034004500370037002D0030003200450037002D0034004500350044002D0042003700340034002D003200450042003100410045003500310039003800420037007D005C0063006D0064002E006500780065000000EA02000000000540008000000000542D8CFFFE070000000000000000000068006C02000000005C0001000000000000000000000000000000280000000000EB1A6E770000000068006C020000000000000000FE070000282595FFFE070000A00D33000000000018006C02000000001B000000C86719007B00310041004300310034004500370037002D0030003200450037002D0034004500350044002D0042003700340034002D003200450042003100410045003500310039003800420037007D005C007400610073006B006D00670072002E00650078006500000041003900440043003700300042004200420034007D000000280000000000340000C000000000D48028000000000080BE28000000000000000000000000003E0040000000000060E3EA0200000000E0A4C30700000000350100C000000000C8037C770000000000000000000000007010000000000000A07D28000000000000000000000000001480280000000000D03B2B000000000048DD6F7700000000360038000000000020EBEA0200000000F8DCEA0200000000E905707700000000F1DCEA0200000000E0A4C30700000000140000000600000098E705007B00310041004300310034004500370037002D0030003200450037002D0034004500350044002D0042003700340034002D003200450042003100410045003500310039003800420037007D005C0063006D0064002E00650078006500000067FEFE0700000000000000000000F012FD020000000000000000000000000000000000000000F012FD020000000012C266FEFE070000010000000000000000000000000000000000000000000000F012FD02000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2124) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Telemetry |
Value: 1 | |||
| (PID) Process: | (2124) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (2124) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Theme |
Value: 1 | |||
| (PID) Process: | (2124) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Enabled |
Value: 1 | |||
| (PID) Process: | (2124) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableTelemetry |
Value: 0 | |||
| (PID) Process: | (2124) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableDefaultBrowserAgent |
Value: 0 | |||
Executable files
54
Suspicious files
409
Text files
155
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2124 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\nltxvmn2.default\datareporting\glean\db\data.safe.tmp | binary | |
MD5:92CB7F414D5F4D5B14F0C41966117F3C | SHA256:2F2D6B0A2F9011CD6F9E291188C36E164BD575B541B6D6FC449B9F6B3C190F84 | |||
| 2124 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\nltxvmn2.default\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 2124 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\nltxvmn2.default\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 2124 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\nltxvmn2.default\datareporting\glean\tmp\3b637b3f-45b1-4de6-bb41-7a3145d293ed | text | |
MD5:D71F1FE3B52016BF8E86BF970F8AAE37 | SHA256:33D34CEF3602CE9CCB3C6255214651CCF05FD1E54898EB1352E3F53CA3D6B1F2 | |||
| 2124 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\nltxvmn2.default\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 2124 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\nltxvmn2.default\datareporting\glean\pending_pings\53151cc5-ac53-4471-b60b-215cbd08f192 | text | |
MD5:E281065B4847ED035C9E7F99DBDAD670 | SHA256:80882CFE315DF75C5354181159E3E4BE6C1F094E8E273E5F43EAD130060D50D8 | |||
| 2124 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\nltxvmn2.default\cache2\entries\ED9826654AE8BD972BDE17A9E0A449D3F881E430 | binary | |
MD5:01CA52C9AD71F08509B35774BA3065B5 | SHA256:E8BE2495E6C8CEB57C4139B4B178ABFAC947137762D7E69DB49A93E68CF06F50 | |||
| 2124 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\nltxvmn2.default\datareporting\glean\tmp\53151cc5-ac53-4471-b60b-215cbd08f192 | text | |
MD5:E281065B4847ED035C9E7F99DBDAD670 | SHA256:80882CFE315DF75C5354181159E3E4BE6C1F094E8E273E5F43EAD130060D50D8 | |||
| 2124 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\nltxvmn2.default\datareporting\glean\pending_pings\3b637b3f-45b1-4de6-bb41-7a3145d293ed | text | |
MD5:D71F1FE3B52016BF8E86BF970F8AAE37 | SHA256:33D34CEF3602CE9CCB3C6255214651CCF05FD1E54898EB1352E3F53CA3D6B1F2 | |||
| 2124 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\nltxvmn2.default\protections.sqlite-journal | binary | |
MD5:5728B9DCA60C94BEADF556053D8E1C90 | SHA256:204E4F169A6AC69BA210BC2DB853F8358372DDA109C4DD0C8420A7454F61A0FE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
143
TCP/UDP connections
374
DNS requests
204
Threats
277
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2996 | File.exe | GET | 200 | 156.236.72.121:80 | http://zzz.fhauiehgha.com/m/okka25.exe | US | binary | 420 Kb | malicious |
2124 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | US | text | 90 b | whitelisted |
2124 | firefox.exe | POST | 200 | 184.24.77.69:80 | http://r3.o.lencr.org/ | US | binary | 503 b | shared |
2996 | File.exe | GET | 200 | 94.142.138.131:80 | http://94.142.138.131/api/tracemap.php | RU | text | 15 b | malicious |
2124 | firefox.exe | POST | 200 | 172.217.16.195:80 | http://ocsp.pki.goog/gts1c3 | US | binary | 471 b | whitelisted |
2124 | firefox.exe | POST | 200 | 184.24.77.69:80 | http://r3.o.lencr.org/ | US | binary | 503 b | shared |
2124 | firefox.exe | POST | 200 | 184.24.77.71:80 | http://r3.o.lencr.org/ | US | der | 503 b | shared |
2124 | firefox.exe | POST | 200 | 172.217.16.195:80 | http://ocsp.pki.goog/gts1c3 | US | binary | 471 b | whitelisted |
2124 | firefox.exe | POST | 200 | 184.24.77.69:80 | http://r3.o.lencr.org/ | US | der | 503 b | shared |
2996 | File.exe | POST | 200 | 94.142.138.131:80 | http://94.142.138.131/api/firegate.php | RU | text | 108 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2124 | firefox.exe | 34.120.115.102:443 | contile-images.services.mozilla.com | GOOGLE-CLOUD-PLATFORM | US | unknown |
2124 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
2124 | firefox.exe | 34.117.65.55:443 | push.services.mozilla.com | — | — | suspicious |
2124 | firefox.exe | 34.120.208.123:443 | incoming.telemetry.mozilla.org | GOOGLE-CLOUD-PLATFORM | US | malicious |
2124 | firefox.exe | 65.109.122.47:443 | offersprize.com | Hetzner Online GmbH | FI | unknown |
2124 | firefox.exe | 23.22.102.13:443 | spocs.getpocket.com | AMAZON-AES | US | unknown |
2124 | firefox.exe | 34.117.237.239:443 | contile.services.mozilla.com | GOOGLE-CLOUD-PLATFORM | US | suspicious |
2124 | firefox.exe | 184.24.77.69:80 | r3.o.lencr.org | Akamai International B.V. | DE | suspicious |
2124 | firefox.exe | 13.32.113.9:80 | ocsp.r2m02.amazontrust.com | AMAZON-02 | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
detectportal.firefox.com |
| whitelisted |
offersprize.com |
| unknown |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
spocs.getpocket.com |
| shared |
proxyserverecs-1736642167.us-east-1.elb.amazonaws.com |
| shared |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
content-signature-2.cdn.mozilla.net |
| whitelisted |
prod.content-signature-chains.prod.webservices.mozgcp.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2996 | File.exe | Malware Command and Control Activity Detected | ET MALWARE Win32/BeamWinHTTP CnC Activity M2 (GET) |
2996 | File.exe | Device Retrieving External IP Address Detected | ET INFO Observed External IP Lookup Domain in TLS SNI (api .myip .com) |
2996 | File.exe | Device Retrieving External IP Address Detected | ET POLICY Possible External IP Lookup Domain Observed in SNI (ipinfo. io) |
2996 | File.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 21 |
2996 | File.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 8 |
2996 | File.exe | A Network Trojan was detected | ET MALWARE Single char EXE direct download likely trojan (multiple families) |
2996 | File.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2996 | File.exe | Potentially Bad Traffic | ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile |
2996 | File.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2996 | File.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
27 ETPRO signatures available at the full report
Process | Message |
|---|---|
e1704692.exe | 2023-08-10 10:10:02 [e1704692.exe 3508] Trying to connect to http://193.233.254.61/
|
e1704692.exe | 2023-08-10 10:10:04 [e1704692.exe 3508] ERROR in ..\stealer\stealer.cpp, line 156, function Start. Failed to connect to http://193.233.254.61/
|
j2185000.exe | 2023-08-10 10:11:43 [j2185000.exe 4960] Trying to connect to http://193.233.254.61/
|
j2185000.exe | 2023-08-10 10:11:44 [j2185000.exe 4960] ERROR in ..\stealer\stealer.cpp, line 156, function Start. Failed to connect to http://193.233.254.61/
|